Generation and Distribution of Quantum Oblivious Keys for Secure Multiparty Computation
Abstract
Featured Application
Abstract
1. Introduction
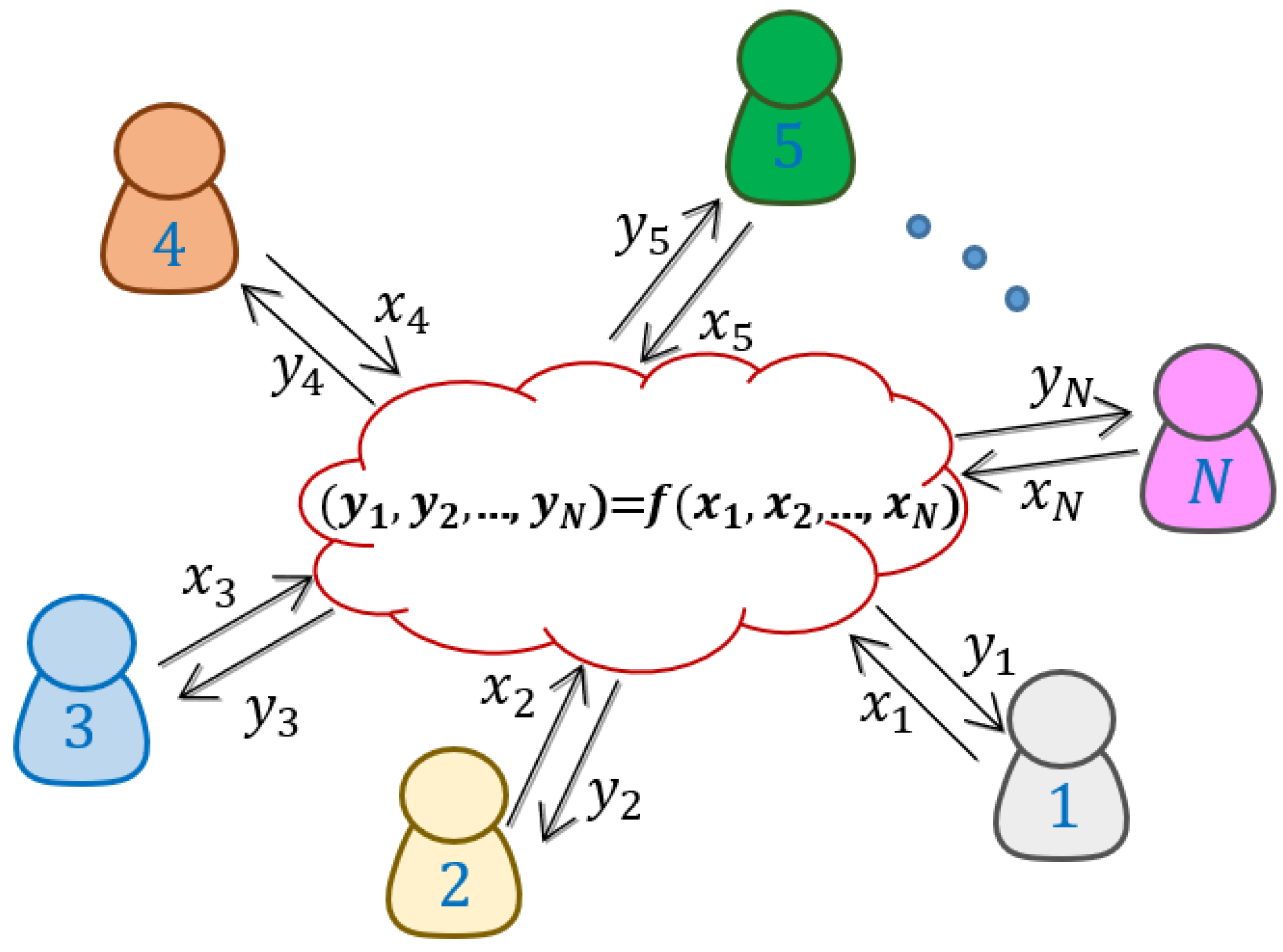
1.1. Secure Multiparty Computation and Oblivious Transfer
1.2. State of the Art
2. Methods
2.1. Generating the OTs
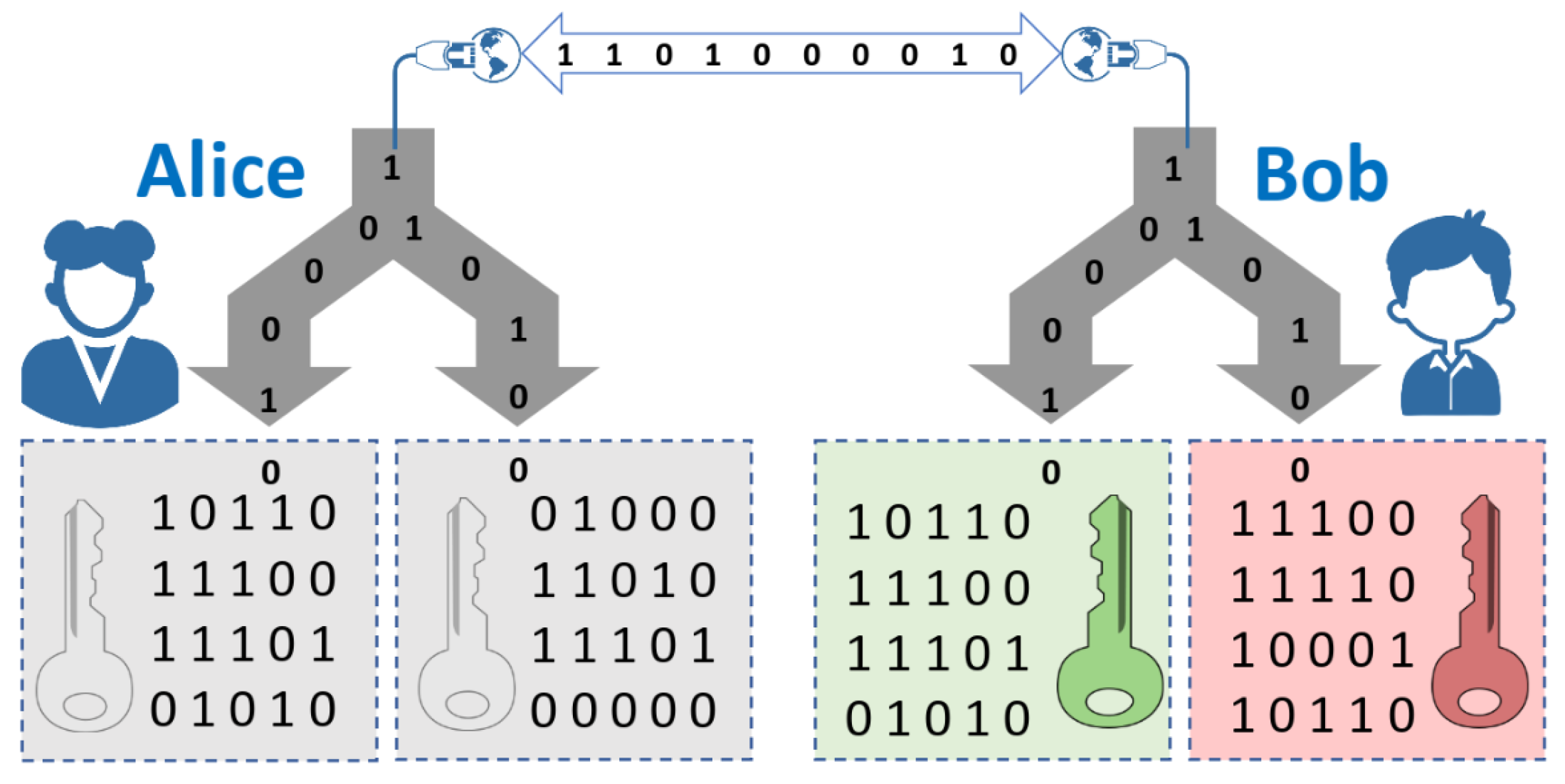
2.2. Oblivious Key Distribution
3. Results and Discussion
3.1. Security
3.2. Efficiency
4. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Lindell, Y.; Pinkas, B. Secure Multiparty Computation for Privacy-Preserving Data Mining. J. Priv. Confid. 2009, 59–98. [Google Scholar] [CrossRef]
- Laud, P.; Kamm, L. Applications of Secure Multiparty Computation; IOS Press: Amsterdam, The Netherlands, 2015; Volume 13. [Google Scholar]
- Asharov, G.; Lindell, Y.; Schneider, T.; Zohner, M. More Efficient Oblivious Transfer Extensions. J. Cryptol. 2017, 30, 805–858. [Google Scholar] [CrossRef]
- Bernstein, D.J.; Lange, T. Post-quantum cryptography. Nature 2017, 549, 188. [Google Scholar] [CrossRef] [PubMed]
- Yao, A.C.C. How to generate and exchange secrets. In Proceedings of the 27th Annual Symposium on Foundations of Computer Science (sfcs 1986), Toronto, ON, Canada, 27–29 October 1986; pp. 162–167. [Google Scholar] [CrossRef]
- Goldreich, O.; Micali, S.; Wigderson, A. How to Play ANY Mental Game. In Proceedings of the Nineteenth Annual ACM Symposium on Theory of Computing, New York, NY, USA, 25–27 May 1987; ACM: New York, NY, USA, 1987; pp. 218–229. [Google Scholar] [CrossRef]
- Schneider, T.; Zohner, M. GMW vs. Yao? Efficient Secure Two-Party Computation with Low Depth Circuits. In Financial Cryptography and Data Security, Proceedings of the 17th International Conference, FC 2013, Okinawa, Japan, 1–5 April 2013; Revised Selected Papers; Sadeghi, A.R., Ed.; Springer: Berlin/Heidelberg, Germany, 2013; pp. 275–292. [Google Scholar]
- Beaver, D.; Micali, S.; Rogaway, P. The round complexity of secure protocols. In Proceedings of the Twenty-Second Annual ACM Symposium on Theory of Computing, Baltimore, MD, USA, 14–16 May 1990; pp. 503–513. [Google Scholar]
- Kilian, J. Founding Cryptography on Oblivious Transfer. In Proceedings of the Twentieth Annual ACM Symposium on Theory of Computing, Chicago, IL, USA, 2–4 May 1988; ACM: New York, NY, USA, 1988; pp. 20–31. [Google Scholar]
- Harnik, D.; Ishai, Y.; Kushilevitz, E. How many oblivious transfers are needed for secure multiparty computation? In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2007; pp. 284–302. [Google Scholar]
- Rabin, M.O. How To Exchange Secrets; Technical Report TR-81; Aiken Computation Laboratory, Harvad University: Cambridge, MA, USA, 1981. [Google Scholar]
- Goldreich, O. Foundations of Cryptography, Volume I Basic Techniques; Cambridge University Press: Cambridge, UK, 2001. [Google Scholar]
- Paar, C.; Pelzl, J. Understanding Cryptography; Springer: Berlin/Heidelberg, Germany, 2010. [Google Scholar]
- Broadbent, A.; Schaffner, C. Quantum cryptography beyond quantum key distribution. Des. Codes Cryptogr. 2016, 78, 351–382. [Google Scholar] [CrossRef]
- Shenoy-Hejamadi, A.; Pathak, A.; Radhakrishna, S. Quantum cryptography: Key distribution and beyond. Quanta 2017, 6, 1–47. [Google Scholar] [CrossRef]
- Lo, H.K.; Chau, H.F. Is Quantum Bit Commitment Really Possible? Phys. Rev. Lett. 1997, 78, 3410–3413. [Google Scholar] [CrossRef]
- Mayers, D. Unconditionally Secure Quantum Bit Commitment is Impossible. Phys. Rev. Lett. 1997, 78, 3414–3417. [Google Scholar] [CrossRef]
- Wehner, S.; Schaffner, C.; Terhal, B.M. Cryptography from Noisy Storage. Phys. Rev. Lett. 2008, 100, 220502. [Google Scholar] [CrossRef]
- Wehner, S.; Curty, M.; Schaffner, C.; Lo, H.K. Implementation of two-party protocols in the noisy-storage model. Phys. Rev. A 2010, 81, 052336. [Google Scholar] [CrossRef]
- Konig, R.; Wehner, S.; Wullschleger, J. Unconditional Security From Noisy Quantum Storage. IEEE Trans. Inf. Theory 2012, 58, 1962–1984. [Google Scholar] [CrossRef]
- Loura, R.; Almeida, Á.J.; André, P.; Pinto, A.; Mateus, P.; Paunković, N. Noise and measurement errors in a practical two-state quantum bit commitment protocol. Phys. Rev. A 2014, 89, 052336. [Google Scholar] [CrossRef]
- Almeida, Á.J.; Stojanovic, A.D.; Paunković, N.; Loura, R.; Muga, N.J.; Silva, N.A.; Mateus, P.; André, P.S.; Pinto, A.N. Implementation of a two-state quantum bit commitment protocol in optical fibers. J. Opt. 2015, 18, 015202. [Google Scholar] [CrossRef]
- Erven, C.; Ng, N.; Gigov, N.; Laflamme, R.; Wehner, S.; Weihs, G. An experimental implementation of oblivious transfer in the noisy storage model. Nat. Commun. 2014, 5, 3418. [Google Scholar] [CrossRef] [PubMed]
- Furrer, F.; Gehring, T.; Schaffner, C.; Pacher, C.; Schnabel, R.; Wehner, S. Continuous-variable protocol for oblivious transfer in the noisy-storage model. Nat. Commun. 2018, 9, 1450. [Google Scholar] [CrossRef] [PubMed]
- Ng, N.H.Y.; Joshi, S.K.; Chen Ming, C.; Kurtsiefer, C.; Wehner, S. Experimental implementation of bit commitment in the noisy-storage model. Nat. Commun. 2012, 3, 1326. [Google Scholar] [CrossRef] [PubMed]
- Lunghi, T.; Kaniewski, J.; Bussières, F.; Houlmann, R.; Tomamichel, M.; Wehner, S.; Zbinden, H. Practical Relativistic Bit Commitment. Phys. Rev. Lett. 2015, 115, 030502. [Google Scholar] [CrossRef] [PubMed]
- Verbanis, E.; Martin, A.; Houlmann, R.; Boso, G.; Bussières, F.; Zbinden, H. 24-Hour Relativistic Bit Commitment. Phys. Rev. Lett. 2016, 117, 140506. [Google Scholar] [CrossRef]
- Pitalúa-García, D.; Kerenidis, I. Practical and unconditionally secure spacetime-constrained oblivious transfer. Phys. Rev. A 2018, 98, 032327. [Google Scholar] [CrossRef]
- Halevi, S.; Micali, S. Practical and Provably-Secure Commitment Schemes from Collision-Free Hashing. In Advances in Cryptology—CRYPTO ’96, Proceedings of the 16th Annual International Cryptology Conference Santa Barbara, California, CA, USA, 18–22 August 1996; Koblitz, N., Ed.; Springer: Berlin/Heidelberg, Germany, 1996; pp. 201–215. [Google Scholar]
- Pinto, A.N.; Ramos, M.F.; Silva, N.A.; Muga, N.J. Generation and Distribution of Oblivious Keys through Quantum Communications. In Proceedings of the 2018 20th International Conference on Transparent Optical Networks (ICTON), Bucharest, Romania, 1–5 July 2018; pp. 1–3. [Google Scholar] [CrossRef]
- Ramos, M.F.; Silva, N.A.; Muga, N.J.; Pinto, A.N. Reversal operator to compensate polarization random drifts in quantum communications. Opt. Express 2020, 28, 5035–5049. [Google Scholar] [CrossRef]
- Lindell, Y.; Pinkas, B. An efficient protocol for secure two-party computation in the presence of malicious adversaries. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Barcelona, Spain, 20–24 May 2007; pp. 52–78. [Google Scholar]
- Yao, A.C.C. Security of Quantum Protocols Against Coherent Measurements. In Proceedings of the Twenty-Seventh Annual ACM Symposium on Theory of Computing, Las Vegas, NV, USA, 29 May–1 June 1995; ACM: New York, NY, USA, 1995; pp. 67–75. [Google Scholar]
- Unruh, D. Universally composable quantum multi-party computation. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, French Riviera, France, 30 May–3 June 2010; pp. 486–505. [Google Scholar]
- Hofheinz, D.; Müller-Quade, J. Universally Composable Commitments Using Random Oracles. In Theory of Cryptography; Naor, M., Ed.; Springer: Berlin/Heidelberg, Germany, 2004; pp. 58–76. [Google Scholar]
- Aaronson, S.; Shi, Y. Quantum Lower Bounds for the Collision and the Element Distinctness Problems. J. ACM 2004, 51, 595–605. [Google Scholar] [CrossRef]
- Asharov, G.; Lindell, Y.; Schneider, T.; Zohner, M. More Efficient Oblivious Transfer and Extensions for Faster Secure Computation. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; ACM: New York, NY, USA, 2013; pp. 535–548. [Google Scholar] [CrossRef]
- Menezes, A.J.; Katz, J.; Van Oorschot, P.C.; Vanstone, S.A. Handbook of Applied Cryptography; CRC Press, Inc.: Boca Raton, FL, USA, 1996. [Google Scholar]
- Ding, J.; Xie, X.; Lin, X. A Simple Provably Secure Key Exchange Scheme Based on the Learning with Errors Problem. Iacr Cryptol. Eprint Arch. 2012, 2012, 688. [Google Scholar]
- Martinez-Mateo, J.; Elkouss, D.; Martin, V. Key reconciliation for high performance quantum key distribution. Sci. Rep. 2013, 3, 1576. [Google Scholar] [CrossRef] [PubMed]
- Brassard, G.; Salvail, L. Secret-key reconciliation by public discussion. In Workshop on the Theory and Application of of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1993; pp. 410–423. [Google Scholar]
- Naor, M.; Pinkas, B. Computationally secure oblivious transfer. J. Cryptol. 2005, 18, 1–35. [Google Scholar] [CrossRef]
- Chou, T.; Orlandi, C. The simplest protocol for oblivious transfer. In Proceedings of the International Conference on Cryptology and Information Security in Latin America, Guadalajara, Mexico, 23–26 August 2015; pp. 40–58. [Google Scholar]
- Comandar, L.; Fröhlich, B.; Lucamarini, M.; Patel, K.; Sharpe, A.; Dynes, J.; Yuan, Z.; Penty, R.; Shields, A. Room temperature single-photon detectors for high bit rate quantum key distribution. Appl. Phys. Lett. 2014, 104, 021101. [Google Scholar] [CrossRef]
- Islam, N.T.; Lim, C.C.W.; Cahall, C.; Kim, J.; Gauthier, D.J. Provably secure and high-rate quantum key distribution with time-bin qudits. Sci. Adv. 2017, 3, e1701491. [Google Scholar] [CrossRef]
- Ko, H.; Choi, B.S.; Choe, J.S.; Kim, K.J.; Kim, J.H.; Youn, C.J. High-speed and high-performance polarization-based quantum key distribution system without side channel effects caused by multiple lasers. Photonics Res. 2018, 6, 214–219. [Google Scholar] [CrossRef]
- Wang, T.; Huang, P.; Zhou, Y.; Liu, W.; Ma, H.; Wang, S.; Zeng, G. High key rate continuous-variable quantum key distribution with a real local oscillator. Opt. Express 2018, 26, 2794–2806. [Google Scholar] [CrossRef]
- Pirandola, S.; Andersen, U.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Englund, D.; Gehring, T.; Lupo, C.; Ottaviani, C.; et al. Advances in Quantum Cryptography. arXiv 2019, arXiv:1906.01645. [Google Scholar] [CrossRef]
- Loura, R.; Arsenović, D.; Paunković, N.; Popović, D.B.; Prvanović, S. Security of two-state and four-state practical quantum bit-commitment protocols. Phys. Rev. A 2016, 94, 062335. [Google Scholar] [CrossRef]


© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lemus, M.; Ramos, M.F.; Yadav, P.; Silva, N.A.; Muga, N.J.; Souto, A.; Paunković, N.; Mateus, P.; Pinto, A.N. Generation and Distribution of Quantum Oblivious Keys for Secure Multiparty Computation. Appl. Sci. 2020, 10, 4080. https://doi.org/10.3390/app10124080
Lemus M, Ramos MF, Yadav P, Silva NA, Muga NJ, Souto A, Paunković N, Mateus P, Pinto AN. Generation and Distribution of Quantum Oblivious Keys for Secure Multiparty Computation. Applied Sciences. 2020; 10(12):4080. https://doi.org/10.3390/app10124080
Chicago/Turabian StyleLemus, Mariano, Mariana F. Ramos, Preeti Yadav, Nuno A. Silva, Nelson J. Muga, André Souto, Nikola Paunković, Paulo Mateus, and Armando N. Pinto. 2020. "Generation and Distribution of Quantum Oblivious Keys for Secure Multiparty Computation" Applied Sciences 10, no. 12: 4080. https://doi.org/10.3390/app10124080
APA StyleLemus, M., Ramos, M. F., Yadav, P., Silva, N. A., Muga, N. J., Souto, A., Paunković, N., Mateus, P., & Pinto, A. N. (2020). Generation and Distribution of Quantum Oblivious Keys for Secure Multiparty Computation. Applied Sciences, 10(12), 4080. https://doi.org/10.3390/app10124080







