Understanding Mobile OTT Service Users’ Resistance to Participation in Wireless D2D Caching Networks
Abstract
1. Introduction
2. Research Background
2.1. Technical Aspects about Issues and Advancements in Mobile Networks
2.1.1. Mobile OTT Services and Network Traffic in Korea
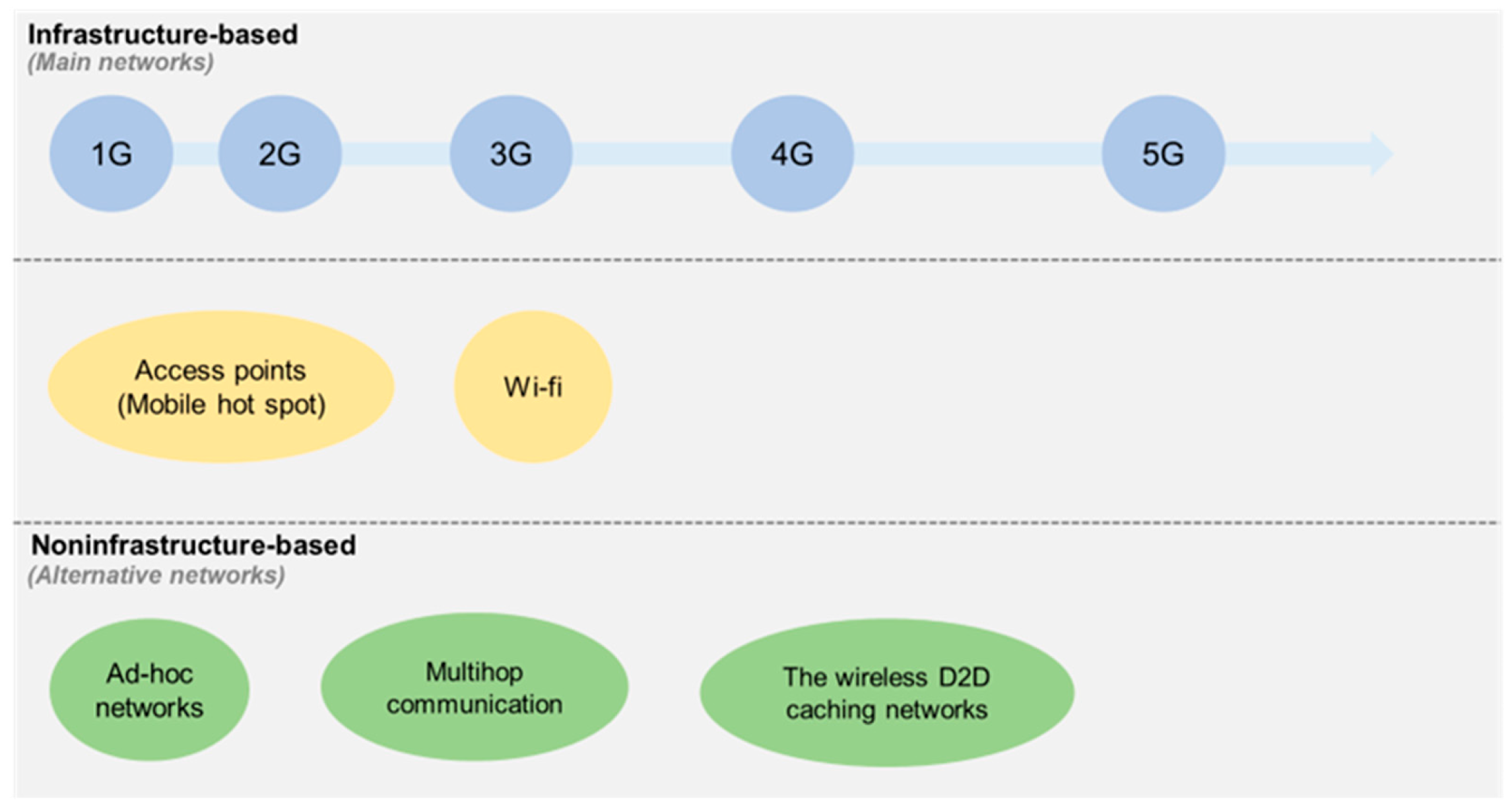
2.1.2. The Advancement of Wireless and Mobile Communication Technology
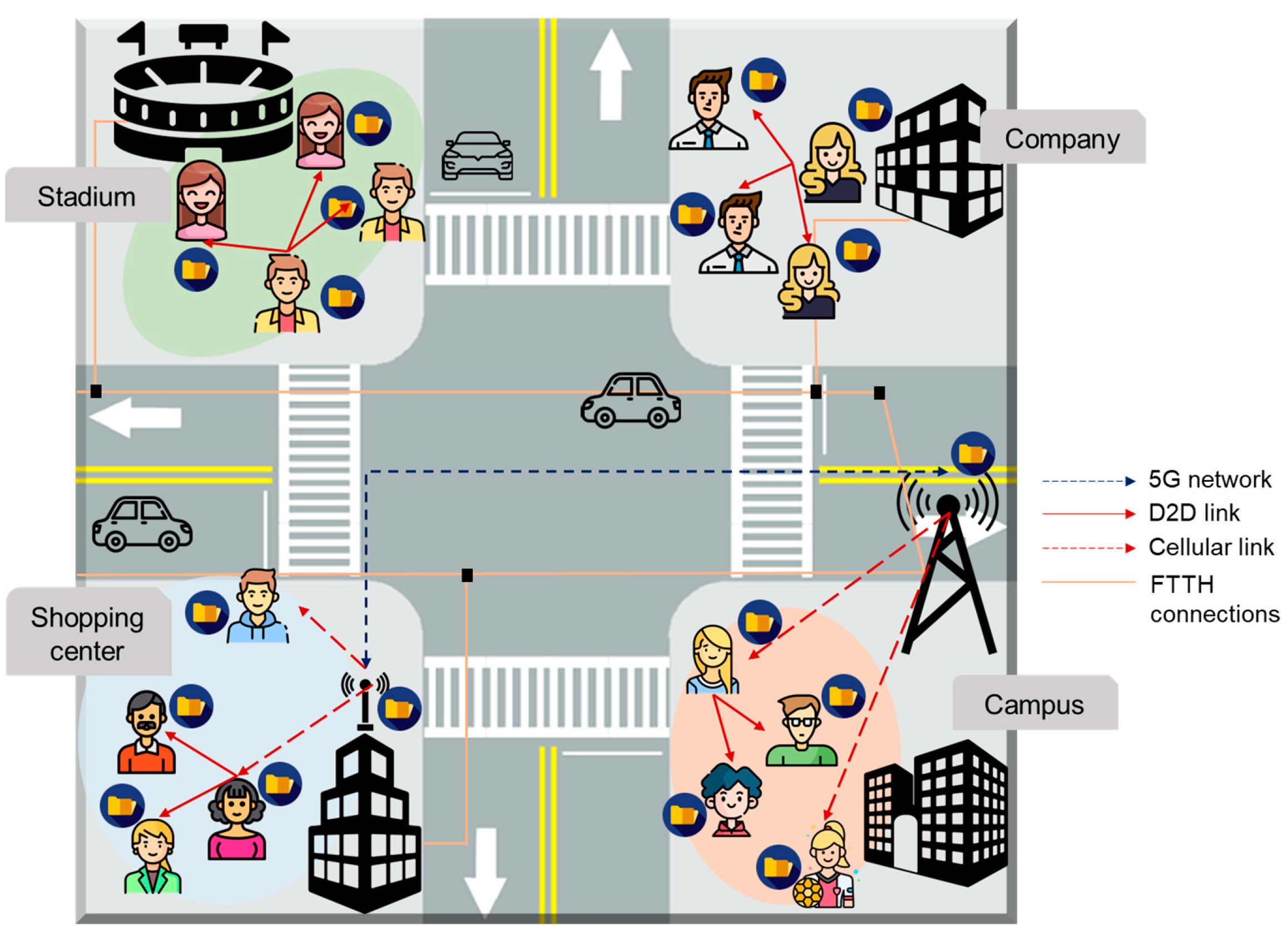
2.1.3. Wireless D2D Caching Networks
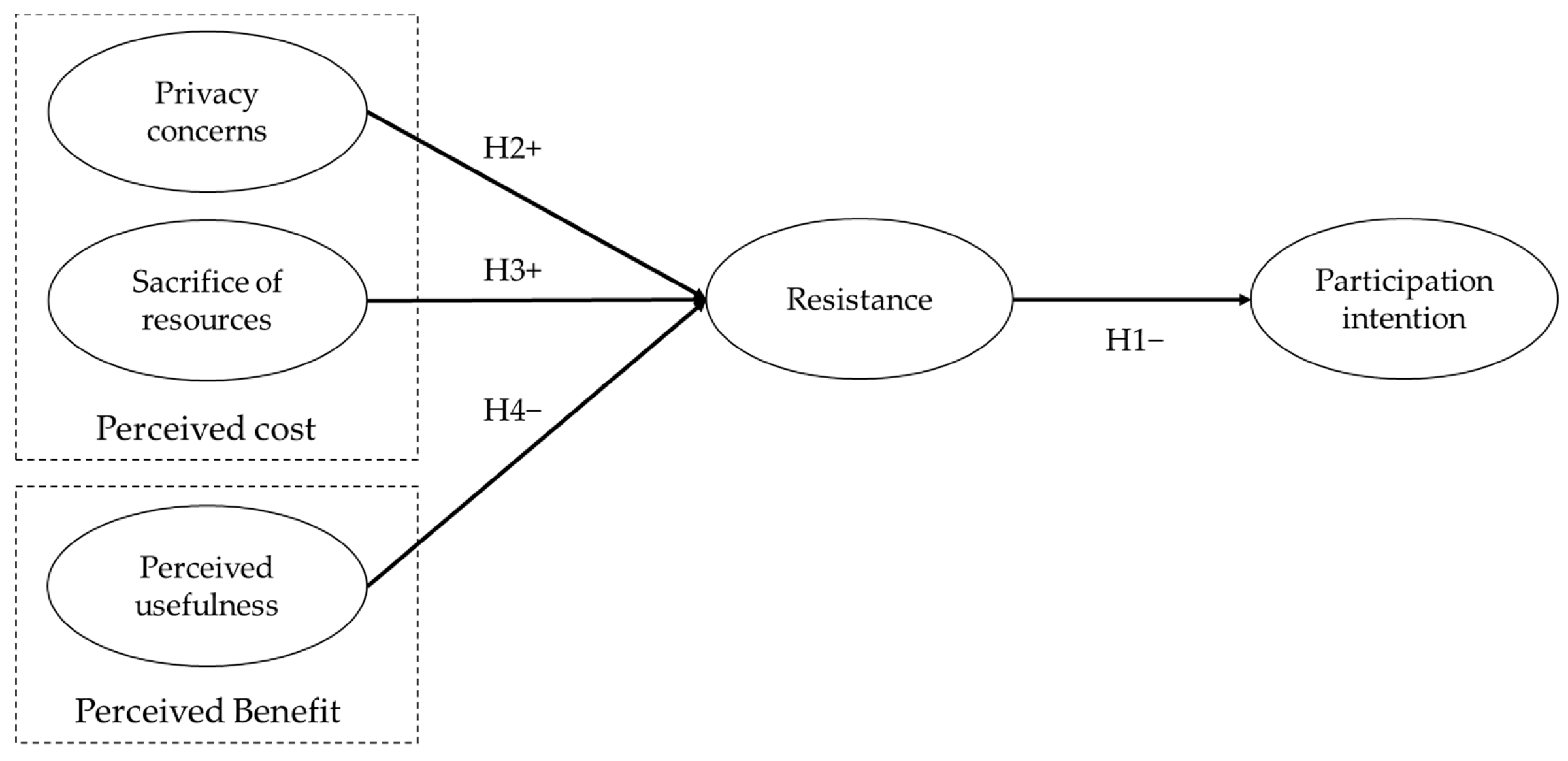
3. Research Hypotheses and Model
3.1. User-Related Aspects about Issues and Advancements in Mobile Networks
3.1.1. Technology Acceptance and Resistance
3.1.2. Perceived Costs
Privacy Concerns
Sacrifice of Resources
3.1.3. Perceived Benefit
Expected Usefulness
4. Research Methodology
4.1. Data Collection and Analysis
4.2. Sample Characteristics
4.3. Testing of Measurement Model
5. Analysis and Results
6. Discussion and Conclusions
6.1. Key Findings and Implications
6.2. Limitations and Future Research
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
| Construct | Item | Reference |
|---|---|---|
| Privacy concerns | It bothers me that my location information, OTT video content viewing history, and preference information may be exposed by adopting the wireless mobile caching networks on my mobile device. | [67] |
| I am concerned that telecommunication operators/OTT platforms are collecting too much information (e.g., location information, OTT video content viewing history, and preference information) about me. | ||
| Agents who pass through my personal mobile device could access other types of information (e.g., SNS, websites, apps, etc.) stored in it. | ||
| Other external agents could retain my personal information while adopting the wireless mobile caching networks. | ||
| Sacrifice of resources | I do not like to provide my personal mobile device storage to communicate with other OTT service users through wireless mobile caching networks. | [30,99] |
| I feel burdened by providing a significant amount of my personal mobile device storage to adopt wireless mobile caching networks. | ||
| I am worried that I will not be able to use my personal mobile device because of battery shortages when adopting wireless mobile caching networks. | ||
| I feel burdened by consuming a significant amount of my personal mobile device’s battery to adopt wireless mobile caching networks. | ||
| Perceived usefulness | The wireless mobile caching networks will enhance my satisfaction with using OTT services. | [44] |
| The wireless mobile caching networks will help me to easily achieve what I want to do when I use OTT services. | ||
| The wireless mobile caching networks will reduce time and costs when using OTT services. | ||
| I will find adopting the wireless mobile caching networks on my mobile device useful in using OTT services. | ||
| Resistance | I feel uneasy when data associated with OTT service are transmitted by wireless mobile caching networks. | [100] |
| I insist upon using OTT services delivered through fixed infrastructure (base stations, access points, or bandwidth) rather than wireless mobile caching networks. | ||
| The wireless mobile caching networks via OTT service users’ mobile devices deserve criticism. | ||
| I am dissatisfied with the wireless mobile caching networks via OTT service users’ mobile devices. | ||
| Participation intention | I plan to participate as an agent in the wireless mobile caching networks using my mobile device. | [30,44] |
| I plan to provide the information necessary to adopt the wireless mobile caching networks (e.g., location information, OTT video content viewing history, and preference information) on my mobile device. | ||
| I plan to watch OTT video content delivered by others’ mobile devices through wireless mobile caching networks. | ||
| I will advise others to participate in the wireless mobile caching networks. |
| Privacy Concerns (PC) | Sacrifice of Resources (SR) | Perceived Usefulness (PU) | Resistance (RT) | Participation Intention (PI) | |
|---|---|---|---|---|---|
| PC1 | 0.876 | 0.482 | −0.205 | 0.436 | −0.326 |
| PC2 | 0.871 | 0.525 | −0.187 | 0.490 | −0.281 |
| PC3 | 0.885 | 0.453 | −0.118 | 0.425 | −0.227 |
| PC4 | 0.888 | 0.462 | −0.112 | 0.472 | −0.240 |
| SR1 | 0.503 | 0.828 | −0.208 | 0.694 | −0.308 |
| SR2 | 0.388 | 0.824 | −0.103 | 0.583 | −0.182 |
| SR3 | 0.498 | 0.834 | −0.185 | 0.571 | −0.290 |
| SR4 | 0.428 | 0.850 | −0.225 | 0.575 | −0.322 |
| PU1 | −0.187 | −0.218 | 0.921 | −0.185 | 0.709 |
| PU2 | −0.188 | −0.185 | 0.912 | −0.171 | 0.693 |
| PU3 | −0.125 | −0.164 | 0.872 | −0.125 | 0.628 |
| PU4 | −0.126 | −0.217 | 0.924 | −0.143 | 0.734 |
| RT1 | 0.393 | 0.691 | −0.164 | 0.830 | −0.267 |
| RT2 | 0.475 | 0.551 | −0.089 | 0.795 | −0.252 |
| RT3 | 0.466 | 0.565 | −0.127 | 0.830 | −0.253 |
| RT4 | 0.401 | 0.611 | −0.197 | 0.864 | −0.282 |
| PI1 | −0.295 | −0.359 | 0.711 | −0.344 | 0.934 |
| PI2 | −0.335 | −0.317 | 0.669 | −0.267 | 0.900 |
| PI3 | −0.233 | −0.244 | 0.713 | −0.263 | 0.904 |
| PI4 | −0.251 | −0.282 | 0.701 | −0.276 | 0.923 |
| Privacy Concerns (PC) | Sacrifice of Resources (SR) | Perceived Usefulness (PU) | Resistance (RT) | Participation Intention (PI) | |
|---|---|---|---|---|---|
| PC | (0.880) | ||||
| SR | −0.305 | (0.834) | |||
| PU | −0.177 | −0.218 | (0.908) | ||
| RT | 0.520 | 0.732 | −0.175 | (0.830) | |
| PI | −0.305 | −0.332 | 0.763 | −0.318 | (0.915) |
References
- Perugini, V. Anytime, Anywhere: The Social Impact of Emerging Communication Technology. IEEE Trans. Prof. Commun. 1996, 39, 4–15. [Google Scholar] [CrossRef]
- Korea Communications Commission. Available online: https://www.kcc.go.kr/user.do;jsessionid=-MuHoukQytSCF6n7c1ZI3tcg1So3T0MOa0xl97Iw.servlet-aihgcldhome10?mode=view&page=A02060400&dc=60400&boardId=1027&cp=1&boardSeq=52581 (accessed on 5 June 2022).
- Korea Communications Commission. Available online: https://www.kcc.go.kr/user.do;jsessionid=f0BZa4KrNjZJNCao58yVl-HlyXeSafOYSWLiQL1B.servlet-aihgcldhome10?mode=view&page=A02060100&dc=K02060100&boardId=1027&cp=2&boardSeq=50589 (accessed on 5 June 2022).
- Kim, Y. Impact of OTT service on the content creation, distribution and consumption. Stud. Broadcast. Cult. 2015, 27, 75–102. [Google Scholar]
- Lee, J.; Lee, S.H.; Rim, M.; Kang, C.G. System-Level Spatiotemporal Offloading with Inter-Cell Mobility Model for Device-to-Device (D2D) Communication-Based Mobile Caching in Cellular Network. IEEE Access 2020, 8, 51570–51581. [Google Scholar] [CrossRef]
- Erricson. Available online: https://www.ericsson.com/en/reports-and-papers/mobility-report/dataforecasts/mobile-traffic-update (accessed on 15 June 2023).
- Sudtasan, T.; Mitomo, H. Effects of OTT Services on Consumer’s Willingness to Pay for Optical Fiber Broadband Connection in Thailand. Cost Efficiency, Energy Efficiency, Service Transparency, Flexibility and Salability. In Proceedings of the 27th European Regional Conference of the International Telecommunications Society (ITS), Cambridge, UK, 7–9 September 2016. [Google Scholar]
- Utilities One. Available online: https://utilitiesone.com/exploring-global-case-studies-in-successful-ftth-planning (accessed on 22 December 2023).
- Maier, M. FTT-5G Networks: Low-Latency FiWi Enhanced Mobile Networks With Edge Intelligence. In Proceedings of the 2019 IEEE Photonics Society Summer Topical Meeting Series (SUM), Ft. Lauderdale, FL, USA, 8–10 July 2019; pp. 1–2. [Google Scholar] [CrossRef]
- Ali, A.S.; Naguib, K.M.; Mahmoud, K.R. Optimized Resource and Power Allocation for Sum Rate Maximization in D2D- Assisted Caching Networks. In Proceedings of the 2019 14th International Conference on Computer Engineering and Systems (ICCES), Cairo, Egypt, 17 December 2019; pp. 438–444. [Google Scholar] [CrossRef]
- Korea Consumer Agency. 5G Consumer Damage Status; Korea Consumer Agency: Suwon-si, Republic of Korea, 2020. [Google Scholar]
- Qian, F.; Quah, K.S.; Huang, J.; Erman, J.; Gerber, A.; Mao, Z.; Sen, S.; Spatscheck, O. Web Caching on Smartphones: Ideal vs. Reality. In Proceedings of the 10th International Conference on Mobile Systems, Applications and Services, New York, NY, USA, 25–29 June 2012; pp. 127–140. [Google Scholar] [CrossRef]
- Kim, J.; Kim, S.; Nam, C. Competitive Dynamics in the Korean Video Platform Market: Traditional Pay TV Platforms vs. OTT Platforms. Telemat. Inform. 2016, 33, 711–721. [Google Scholar] [CrossRef]
- Moyler, A.; Hooper, M. Over the Top TV (OTT TV) Platform Technologies; BCi Ltd.: Southampton, UK; Endurance Technology Ltd.: West Sussex, UK, 2009. [Google Scholar]
- BBC News Korea. Available online: https://www.bbc.com/korean/news-62979836 (accessed on 3 March 2023).
- Reuters. Available online: https://www.reuters.com/business/media-telecom/skorea-broadband-firm-sues-netflix-after-traffic-surge-squid-game-2021-10-01/ (accessed on 12 October 2023).
- Korea Herald. Available online: https://www.koreaherald.com/view.php?ud=20210628000798 (accessed on 10 June 2022).
- Bush, S. A Survey of Audience Reaction to NHK 1125 Line Color Television; Advanced Television: East Sussex, UK, 1987. [Google Scholar]
- Lee, M.R.; Choi, S.J.; Lee, Y.J. A Study on the Adoption of UHD for Users Perceived usefulness and ease of use of UHDTV. J. Broadcas Eng. 2015, 20, 48–56. [Google Scholar] [CrossRef]
- Kim, M.S.; Kim, E.; Hwang, S.; Kim, J.; Kim, S. Willingness to Pay for Over-the-Top Services in China and Korea. Telecommun. Policy 2017, 41, 197–207. [Google Scholar] [CrossRef]
- Neuman, W.R. The Mass Audience Looks at HDTV: An Early Experiment. In Proceedings of the Annual Convention of the National Association of Broadcasters, Las Vegas, NV, USA, 8–12 April 1988. [Google Scholar]
- The Joong Ang. Available online: https://www.joongang.co.kr/article/25160752#home (accessed on 8 June 2023).
- Seymour, T.; Shaheen, A. History of Wireless Communication. Int. J. Bus. Inf. Syst. 2011, 15, 37–42. [Google Scholar] [CrossRef][Green Version]
- Zaber, M.; Sirbu, M. Impact of spectrum management policy on the penetration of 3G technology. Telecommun. Policy 2012, 36, 762–782. [Google Scholar] [CrossRef]
- Cave, M. How Disruptive Is 5G? Telecommun. Policy 2018, 42, 653–658. [Google Scholar] [CrossRef]
- Ramanathan, R.; Redi, J. A Brief Overview of Ad Hoc Networks: Challenges and Directions. IEEE Commun. Mag. 2002, 40, 20–22. [Google Scholar] [CrossRef]
- Iwata, A.; Chiang, C.-C.; Pei, G.; Gerla, M.; Chen, T.-W. Scalable Routing Strategies for Ad Hoc Wireless Networks. IEEE J. Sel. Areas Commun. 1999, 17, 1369–1379. [Google Scholar] [CrossRef]
- Ramanathan, R.; Steenstrup, M. Hierarchically-organized, Multihop Mobile Wireless Networks for Quality-of-service Support. Mob. Netw. Appl. 1998, 3, 101–119. [Google Scholar] [CrossRef]
- Zhou, L.; Haas, Z.J. Securing Ad Hoc Networks. IEEE Netw. 1999, 13, 24–30. [Google Scholar] [CrossRef]
- Kang, Y.; Kim, S. Understanding User Resistance to Participation in Multihop Communications. J. Comput. Mediat. Commun. 2009, 14, 328–351. [Google Scholar] [CrossRef]
- Li, H.; Lott, M.; Weckerle, M.; Zirwas, W.; Schulz, E. Multihop Communications in Future Mobile Radio Networks. In Proceedings of the 13th IEEE International Symposium on Personal, Indoor and Mobile Radio Communications, Lisbon, Portugal, 10 December 2002; pp. 54–58. [Google Scholar] [CrossRef]
- Chlamtac, I.; Conti, M.; Liu, J.J.-N. Mobile Ad Hoc Networking: Imperatives and Challenges. Ad Hoc Netw. 2003, 1, 13–64. [Google Scholar] [CrossRef]
- Feng, L.; Zhao, P.; Zhou, F.; Yin, M.; Yu, P.; Li, W.; Qiu, X. Resource Allocation for 5G D2D Multicast Content Sharing in Social-Aware Cellular Networks. IEEE Commun. Mag. 2018, 56, 112–118. [Google Scholar] [CrossRef]
- Jiang, W.; Feng, G.; Qin, S.; Yum, T.S.P.; Cao, G. Multi-Agent Reinforcement Learning for Efficient Content Caching in Mobile D2D Networks. IEEE Trans. Wirel. Commun. 2019, 18, 1610–1622. [Google Scholar] [CrossRef]
- Passarella, A. A Survey on Content-Centric Technologies for the Current Internet: CDN and P2P Solutions. Comput. Commun. 2012, 35, 1–32. [Google Scholar] [CrossRef]
- Wilson, C.; Ballani, H.; Karagiannis, T.; Rowtron, A. Better Never than Late: Meeting Deadlines in Datacenter Networks. SIGCOMM Comput. Commun. Rev. 2011, 41, 50–61. [Google Scholar] [CrossRef]
- Atieh, A.; Kanwal, B.; Ghafoor, S.; Sajid, M.; Mirza, J. Design and Analysis of Redundant Optical Comb for Data Center Networks. Opt. Quant. Electron. 2023, 55, 58. [Google Scholar] [CrossRef]
- Ali, A.S.; Mahmoud, K.R.; Naguib, K.M. Optimal Caching Policy for Wireless Content Delivery in D2D Networks. J. Netw. Comput. Appl. 2020, 150, 102467. [Google Scholar] [CrossRef]
- Sheraz, M.; Ahmed, M.; Li, Y.; Jin, D.; Han, Z.; Jiang, T. Artificial Intelligence for Wireless Caching: Schemes, Performance, and Challenges. IEEE Commun. Surv. Tutor. 2021, 23, 631–661. [Google Scholar] [CrossRef]
- Javed, M.A.; Zeadally, S. AI-Empowered Content Caching in Vehicular Edge Computing: Opportunities and Challenges. IEEE Netw. 2021, 35, 109–115. [Google Scholar] [CrossRef]
- Choi, M. Device Caching Strategy Maximizing Expected Content Quality. J. Korea Soc. Comput. Inf. 2021, 26, 111–118. [Google Scholar] [CrossRef]
- He, Y.; Lee, I.; Guan, L. Distributed Throughput Maximization in P2P VoD Applications. IEEE Trans. Multimed. 2009, 11, 509–522. [Google Scholar] [CrossRef]
- Marangunić, N.; Granić, A. Technology Acceptance Model: A Literature Review from 1986 to 2013. Univs. Access. Inf. Soc. 2015, 14, 81–95. [Google Scholar] [CrossRef]
- Davis, F.D.; Bagozzi, R.P.; Warshaw, P.R. User Acceptance of Computer Technology: A Comparison of Two Theoretical Models. Manag. Sci. 1989, 35, 982–1003. [Google Scholar] [CrossRef]
- Venkatesh, V.; Morris, M.G.; Davis, G.B.; Davis, F.D. User Acceptance of Information Technology: Toward a Unified View. MIS Q. 2003, 27, 425–478. [Google Scholar] [CrossRef]
- Fishbein, M.; Ajzen, I. Belief, Attitude, Intention, and Behavior: An Introduction to Theory and Research; Wiley: Boston, MA, USA, 1975. [Google Scholar]
- Rogers, E.M. Diffusiuon of Innovation, 4th ed.; Free Press: Washington, DC, USA, 1995. [Google Scholar]
- Karahanna, E.; Straub, D.W.; Chervany, N.L. Information Technology Adoption Across Time: A Cross-Sectional Comparison of Pre-Adoption and Post-Adoption Beliefs. MIS Q. 1999, 23, 183–213. [Google Scholar] [CrossRef]
- Kwon, H.S.; Chidambaram, L. A Test of the Technology Acceptance Model: The Case of Cellular Telephone Adoption. In Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, Maui, HI, USA, 7 January 2000; pp. 1–10. [Google Scholar]
- Khalifa, M.; Cheng, K.N. Adoption of Mobile Commerce: Role of Exposure. In Proceedings of the Hawaii International Conference on System Sciences, Big Island, HI, USA, 7–10 January 2002; pp. 1–7. [Google Scholar]
- Gefen, D.; Straub, D. The Relative Importance of Perceived Ease of Use in IS Adoption: A Study of E-Commerce Adoption. J. Assoc. Inf. Syst. 2000, 1, 1–30. [Google Scholar] [CrossRef]
- Kim, H.-W.; Chan, H.C.; Gupta, S. Value-Based Adoption of Mobile Internet: An Empirical Investigation. Decis. Support Syst. 2007, 43, 111–126. [Google Scholar] [CrossRef]
- Chow, M.; Herold, D.K.; Choo, T.-M.; Chan, K. Extending the Technology Acceptance Model to Explore the Intention to Use Second Life for Enhancing Healthcare Education. Comput. Educ. 2012, 59, 1136–1144. [Google Scholar] [CrossRef]
- Ashforth, B.E.; Mael, F.A. Sustaining Valued Identities. Power and Influence in Organizations. In Power and Influence in Organizations; Kramer, R.M., Neale, M.A., Eds.; Thousand Oaks: Sage, CA, USA, 1998. [Google Scholar]
- Kim, H.-W.; Kankanhalli, A. Investigating User Resistance to Information Systems Implementation: A Status Quo Bias Perspective. MIS Q. 2009, 33, 567–582. [Google Scholar] [CrossRef]
- Ali, M.; Zhou, L.; Miller, L.; Ieromonachou, P. User Resistance in IT: A Literature Review. Int. J. Inf. Manag. 2016, 36, 35–43. [Google Scholar] [CrossRef]
- Ram, S. A Model of Innovation Resistance. Adv. Consum. Res. 1987, 14, 208–212. [Google Scholar]
- Szmigin, I.; Foxall, G. Three Forms of Innovation Resistance: The Case of Retail Payment Methods. Technovation 1998, 18, 459–468. [Google Scholar] [CrossRef]
- Kuisma, T.; Laukkanen, T.; Hiltunen, M. Mapping the Reasons for Resistance to Internet Banking: A Means-End Approach. Int. J. Inf. Manag. 2007, 27, 75–85. [Google Scholar] [CrossRef]
- Markus, M.L. Power, Politics, and MIS Implementation. Commun. ACM 1983, 26, 430–444. [Google Scholar] [CrossRef]
- Hirschheim, R.; Newman, M. Information Systems and User Resistance: Theory and Practice. Comput. J. 1988, 31, 398–408. [Google Scholar] [CrossRef]
- Jiang, J.J.; Muhanna, W.A.; Klein, G. User Resistance and Strategies for Promoting Acceptance across System Types. Inf. Manag. 2000, 37, 25–36. [Google Scholar] [CrossRef]
- Rumelt, R.P. Inertia and Transformation. In Resource-Based and Evolutionary Theories of the Firm: Towards a Synthesis; Montgomery, C.A., Ed.; Springer: Boston, MA, USA, 1995; pp. 101–132. [Google Scholar]
- Kim, H.-W. The Effects of Switching Costs on User Resistance to Enterprise Systems Implementation. IEEE Trans. Eng. Manag. 2011, 58, 471–482. [Google Scholar] [CrossRef]
- Olson, J.C.; Dover, P.A. Disconfirmation of Consumer Expectations through Product Trial. J. Appl. Psychol. 1979, 64, 179–189. [Google Scholar] [CrossRef]
- Heinssen, R.K.; Glass, C.R.; Knight, L.A. Assessing Computer Anxiety: Development and Validation of the Computer Anxiety Rating Scale. Comput. Hum. Behav. 1987, 3, 49–59. [Google Scholar] [CrossRef]
- Pavlou, P.A.; Liang, H.; Xue, Y. Understanding and Mitigating Uncertainty in Online Exchange Relationships: A Principal-Agent Perspective. MIS Q. 2007, 31, 105–136. [Google Scholar] [CrossRef]
- Machogu, A.M.; Okiko, L. The Perception of Bank Employees towards Cost of Adoption, Risk of Innovation, and Staff Training’s Influence on The Adoption of Information and Communication Technology in The Rwandan Commercial Banks. J. Internet Bank. Commer. 2012, 17, 1–15. [Google Scholar]
- Bauer, R.A. Consumer Behavior as Risk Taking in Risk Taking and Information handling in Consumer Behavior; Cox, D., Ed.; Harvard University Press: Cambridge, MA, USA, 1960; pp. 389–398. [Google Scholar]
- Dowling, G.R.; Staelin, R. A Model of Perceived Risk and Intended Risk-Handling Activity. J. Consum. Res. 1994, 21, 119–134. [Google Scholar] [CrossRef]
- AlSoufi, A.; Ali, H. Customers Perception of Mbanking Adoption in Kingdom of Bahrain: An Empirical Assessment of an Extended Tam Model. Int. J. Manag. Inf. Technol. 2014, 6, 1–13. [Google Scholar] [CrossRef]
- Zainab, B.; Awais Bhatti, M.; Alshagawi, M. Factors Affecting E-Training Adoption: An Examination of Perceived Cost, Computer Self-Efficacy and the Technology Acceptance Model. Behav. Inf. Technol. 2017, 36, 1261–1273. [Google Scholar] [CrossRef]
- Lewin, K.; Dembo, T.; Festinger, L.; Sears, P.S. Level of Aspiration; Ronald Press: New York, NY, USA, 1944. [Google Scholar]
- Fishbein, M. Attitude and the Prediction of Behavior in Attitude Theory and Measurement; Wiley: New York, NY, USA, 1967; pp. 477–492. [Google Scholar]
- Featherman, M. Extending the Technology Acceptance Model by Inclusion of Perceived Risk. In Proceedings of the Americas Conference on Information Systems (AMCIS 2001), Boston, MA, USA, 2 August 2001. [Google Scholar]
- Arnould, E.; Price, L.; Zinkhan, G. Consumers, 2nd ed.; McGraw-Hill: New York, NY, USA, 2004. [Google Scholar]
- Featherman, M.S.; Pavlou, P.A. Predicting E-Services Adoption: A Perceived Risk Facets Perspective. Int. J. Hum. Comput. 2003, 59, 451–474. [Google Scholar] [CrossRef]
- Wan, K.; Sun, H.; Ji, M.; Tuninetti, D.; Caire, G. Fundamantal Limits of Device-to-Device Private Caching with Trusted Server. arXiv 2019, arXiv:1912.09985. [Google Scholar]
- Zhang, A.; Lin, X. Security-Aware and Privacy-Preserving D2D Communications in 5G. IEEE Netw. 2017, 31, 70–77. [Google Scholar] [CrossRef]
- Van Slyke, C.; Shim, J.T.; Johnson, R.; Jiang, J.J. Concern for Information Privacy and Online Consumer Purchasing. J. Assoc. Inf. Syst. 2006, 7, 414–444. [Google Scholar] [CrossRef]
- Nam, C.; Song, C.; Lee, E.; Park, C. Consumers’ Privacy Concerns and Willingness to Provide Marketing-Related Personal Information Online. Adv. Consum. 2006, 33, 212–217. [Google Scholar]
- Institute of Information & Communications Technology Planning & Evaluation. Available online: https://www.itfind.or.kr/publication/regular/weeklytrend/weekly/view.do?boardParam1=7925&boardParam2=7925 (accessed on 20 May 2022).
- Bijlani, A.; Ramachandran, U.; Campbell, R. Where Did My 256 GB Go? A Measurement Analysis of Storage Consumption on Smart Mobile Devices. In Proceedings of the ACM on Measurement and Analysis of Computing Systems, New York, NY, USA, 31 May 2021; pp. 1–28. [Google Scholar]
- Ferreira, D.; Dey, A.K.; Kostakos, V. Understanding Human-Smartphone Concerns: A Study of Battery Life. In Pervasive Computing; Lyons, K., Ed.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 19–33. [Google Scholar] [CrossRef]
- Oliver, E. The Challenges in Large-Scale Smartphone User Studies. In Proceedings of the 2nd ACM International Workshop on Hot Topics in Planet-Scale Measurement, San Francisco, CA, USA, 15–18 June 2010; pp. 1–5. [Google Scholar] [CrossRef]
- Bhattacherjee, A.; Hikmet, N. Physicians’ Resistance toward Healthcare Information Technology: A Theoretical Model and Empirical Test. Eur. J. Inf. Syst. 2007, 16, 725–737. [Google Scholar] [CrossRef]
- Laumer, S.; Maier, C.; Eckhardt, A.; Weitzel, T. User Personality and Resistance to Mandatory Information Systems in Organizations: A Theoretical Model and Empirical Test of Dispositional Resistance to Change. J. Inf. Technol. 2016, 31, 67–82. [Google Scholar] [CrossRef]
- Laumer, S.; Maier, C.; Eckhardt, A.; Weitzel, T. Work Routines as an Object of Resistance during Information Systems Implementations: Theoretical Foundation and Empirical Evidence. Eur. J. Inf. Syst. 2016, 25, 317–343. [Google Scholar] [CrossRef]
- Gefen, D.; Straub, D.; Boudreau, M.-C. Structural Equation Modeling and Regression: Guidelines for Research Practice. J. Assoc. Inf. Syst. 2000, 4, 7. [Google Scholar] [CrossRef]
- Werts, C.E.; Linn, R.L.; Jöreskog, K.G. Intraclass Reliability Estimates: Testing Structural Assumptions. Educ. Psychol. Meas. 1974, 34, 25–33. [Google Scholar] [CrossRef]
- Hair, J.; Black, B.; Babin, B.; Anderson, R.; Tatham, R. Multivariate Data Analysis, 6th ed.; Prentice-Hall: Upper Saddle River, NJ, USA, 2006. [Google Scholar]
- Fornell, C.; Larcker, D.F. Evaluating structural equation models with unobservable variables and measurement error. J. Marketing. Res. 1981, 18, 39–50. [Google Scholar] [CrossRef]
- Benbasat, I.; Barki, H. Quo Vadis TAM? J. Assoc. Inf. Syst. 2007, 8, 211–218. [Google Scholar] [CrossRef]
- Park, J.; Lee, D.; Ahn, J. Risk-Focused E-Commerce Adoption Model: A Cross-Country Study. J. Glob. Inf. Technol. Manag. 2004, 7, 6–30. [Google Scholar] [CrossRef]
- Kim, D.J. Cognition Based versus Affect-Based Trust Determinations in e-Commerce: A Cross-Cultural Comparison Study. In Proceedings of the 26th International Conference on Information Systems, Las Vegas, NV, USA, 11–14 December 2005. [Google Scholar]
- Vigneri, L.; Spyropoulos, T.; Barakat, C. Low Cost Video Streaming through Mobile Edge Caching: Modelling and Optimization. IEEE Trans. Mob. Comput. 2019, 18, 1302–1315. [Google Scholar] [CrossRef]
- Zhang, N.; Kimmerlin, M.; Costa-Requena, J.; Hämmäinen, H. Cost Efficiency of Mobile In-network Caching. Int. J. Network. Mgmt. 2016, 26, 44–55. [Google Scholar] [CrossRef]
- Lee, E.; Lee, J.; Eastwood, D. A Two-Step Estimation of Consumer Adoption of Technology-Based Service Innovations. J. Consum. Aff. 2003, 37, 256–282. [Google Scholar] [CrossRef]
- Bagozzi, R.P.; Dholakia, U.M. Open Source Software User Communities: A Study of Participation in Linux User Groups. Manag. Sci. 2006, 52, 1099–1115. [Google Scholar] [CrossRef]
- Klein, K.J.; Sorra, J.S. The Challenge of Innovation Implementation. Acad. Manag. Rev. 1996, 21, 1055–1088. [Google Scholar] [CrossRef]

| Characteristics | Frequency | Valid Percent |
|---|---|---|
| Number of mobile OTT service in use | ||
| 1 | 151 | 48.4 |
| 2 | 92 | 29.5 |
| 3 | 45 | 14.4 |
| More than 4 | 24 | 7.7 |
| Most used mobile OTT service (multiple response) | ||
| Netflix | 213 | 68.3 |
| Tving | 28 | 9.0 |
| Wavve | 26 | 8.3 |
| Coupangplay | 17 | 5.4 |
| Disney+ | 15 | 4.8 |
| Watcha | 5 | 1.6 |
| AppleTV | 3 | 1.0 |
| Seezn | 2 | 0.6 |
| Others | 3 | 1.0 |
| Age | ||
| 20 s | 78 | 25.0 |
| 30 s | 80 | 25.6 |
| 40 s | 78 | 25.0 |
| 50 s | 76 | 24.4 |
| Gender | ||
| Male | 156 | 50.0 |
| Female | 156 | 50.0 |
| Occupation: | ||
| Student | 28 | 9.0 |
| Housewife | 28 | 9.0 |
| Office worker | 192 | 61.5 |
| Professional | 33 | 10.6 |
| Self-employed | 23 | 7.4 |
| Other | 8 | 2.6 |
| Education: | ||
| High school | 33 | 10.6 |
| College | 241 | 77.2 |
| Advanced degree | 38 | 12.2 |
| Income (per month, USD): | ||
| ≤1000 | 2 | 2.1 |
| >1000, ≤2000 | 4 | 4.3 |
| >2000, ≤3000 | 22 | 23.4 |
| >3000, ≤4000 | 11 | 11.7 |
| >4000, ≤5000 | 13 | 13.8 |
| >5000 | 42 | 44.7 |
| Variable Name | Code | No of Items | Mean (Std. Dev) | Cronbach’s Alpha | AVE | Composite Reliability |
|---|---|---|---|---|---|---|
| Privacy concerns | PC | 4 | 5.39 (1.09) | 0.903 | 0.774 | 0.905 |
| Sacrifice of resources | SR | 4 | 4.86 (1.09) | 0.855 | 0.696 | 0.859 |
| Expected usefulness | PU | 4 | 4.32 (1.09) | 0.929 | 0.825 | 0.932 |
| Resistance | RT | 4 | 4.64 (1.06) | 0.849 | 0.689 | 0.852 |
| Participation intention | PI | 4 | 3.89 (1.33) | 0.936 | 0.839 | 0.937 |
| Total items | 20 | |||||
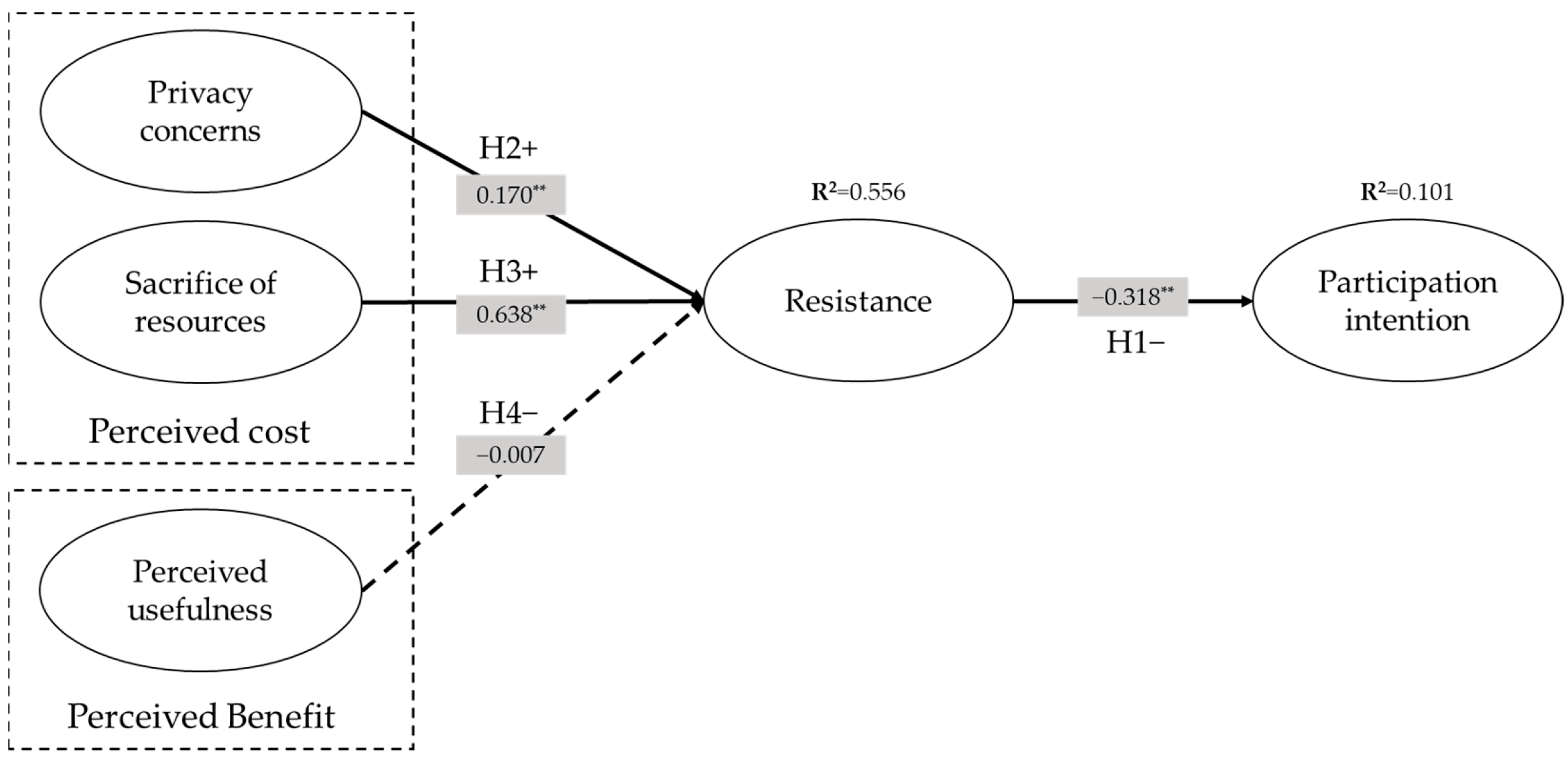
| H | Relations | Std. Estimate | S.E | T-Value | p-Value |
|---|---|---|---|---|---|
| H1 | RT → PI | −0.318 | 0.069 | 4.587 | 0.000 |
| H2 | PC → RT | 0.170 | 0.048 | 3.528 | 0.000 |
| H3 | SR → RT | 0.638 | 0.041 | 15.432 | 0.000 |
| H4 | PU → RT | −0.007 | 0.049 | 0.134 | 0.893 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jang, Y.; Kim, S. Understanding Mobile OTT Service Users’ Resistance to Participation in Wireless D2D Caching Networks. Behav. Sci. 2024, 14, 158. https://doi.org/10.3390/bs14030158
Jang Y, Kim S. Understanding Mobile OTT Service Users’ Resistance to Participation in Wireless D2D Caching Networks. Behavioral Sciences. 2024; 14(3):158. https://doi.org/10.3390/bs14030158
Chicago/Turabian StyleJang, Yumi, and Seongcheol Kim. 2024. "Understanding Mobile OTT Service Users’ Resistance to Participation in Wireless D2D Caching Networks" Behavioral Sciences 14, no. 3: 158. https://doi.org/10.3390/bs14030158
APA StyleJang, Y., & Kim, S. (2024). Understanding Mobile OTT Service Users’ Resistance to Participation in Wireless D2D Caching Networks. Behavioral Sciences, 14(3), 158. https://doi.org/10.3390/bs14030158







