Traceable Attribute-Based Encryption Scheme Using BIM Collaborative Design
Abstract
1. Introduction
2. Related Work
2.1. Security Permissions in BIM Collaborative Design
2.2. Attribute-Based Encryption Scheme
3. Traceable Attribute-Based Encryption Schemes
3.1. Scheme Design
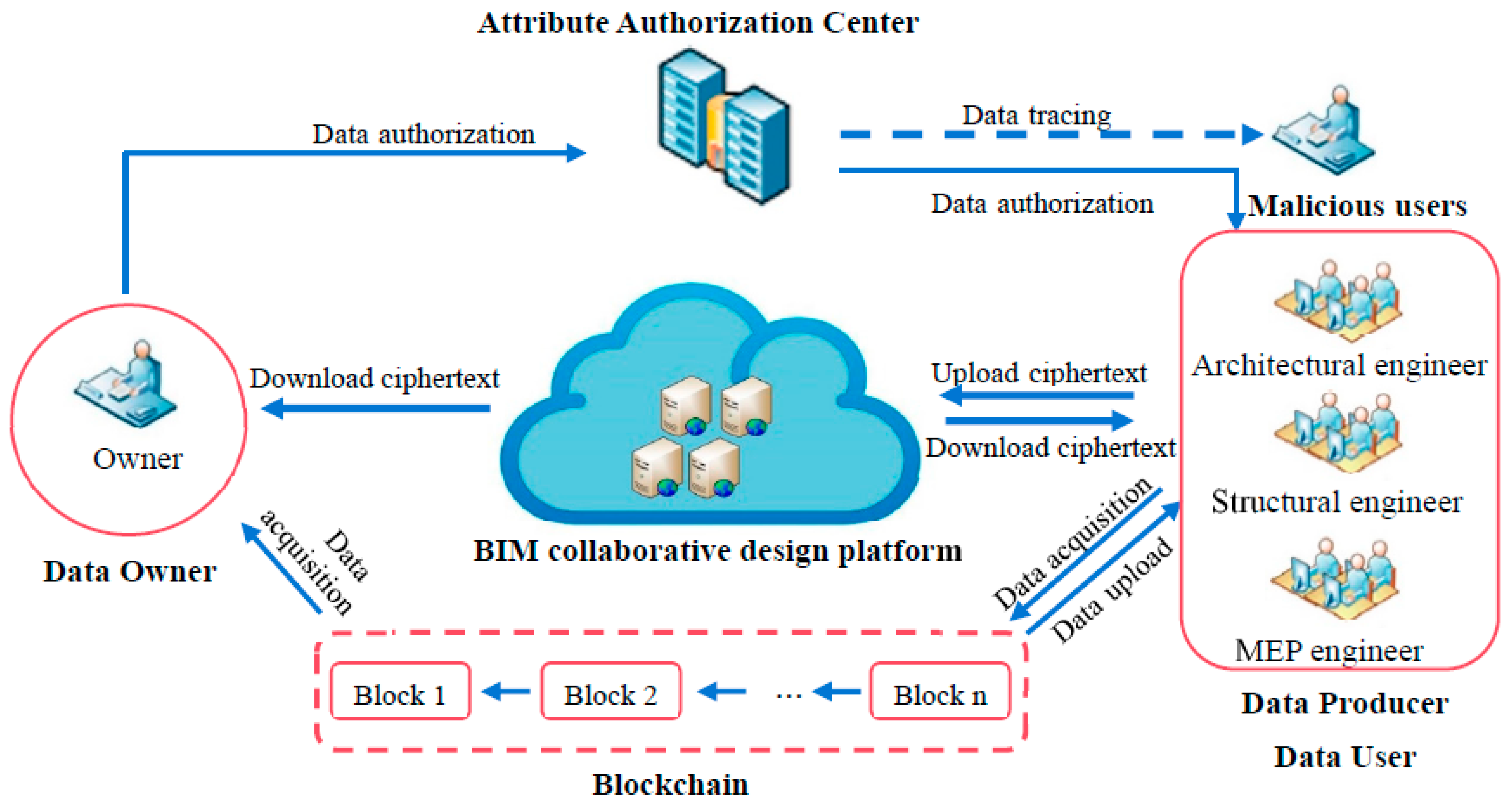
3.1.1. System Model
- (1)
- Data owner: The data owner is the project owner whose permissions include reading data, confirming data, and allocating permissions to other users. They do not have editing rights.
- (2)
- Data producer: Data producers refer to various professional design engineers involved in BIM collaborative design. In terms of access control, they have full control over the data they produce and can edit it. Data producers use symmetric encryption to encrypt data to be shared and then store it on the BIM collaborative design platform. After successful storage, they use a symmetric key, “aeskey”, for attribute-based encryption. Finally, they store the hash value returned by the BIM collaborative design platform and the encrypted symmetric key on the blockchain using a data on-chain algorithm.
- (3)
- Data user: Design engineers are not only data producers, but also data users. They have rights such as viewing, invoking, and reviewing data produced by other design engineers. The decryption key owned by the data user is linked to its own set of attributes. The symmetric key, “aeskey”, is decrypted by the data user who possesses attributes that comply with the access policy after retrieving data from the blockchain using the data-acquisition algorithm. The symmetric key is employed for decryption, and the corresponding encrypted file is downloaded from the BIM collaborative design platform.
- (4)
- Attribute authorization center: The attribute authorization center is responsible for initialization, completing user registration, and issuing keys based on user attributes. In cases of key leakage or misuse, the attribute authorization center can trace the malicious user through the key and hold them accountable.
- (5)
- BIM collaborative design platform: Project participants can engage in live communication and decision making, as well as design and review activities on the BIM collaborative design platform. This enables the design, integration, and sharing of project information. Any authorized user can use the BIM collaborative design platform according to their granted permissions.
- (6)
- Blockchain: As a distributed ledger, the blockchain features consistent data storage, tamper resistance, and nonrepudiation. It ensures secure data sharing through the BIM collaborative design platform hash value and the ciphertext of symmetric keys stored on the chain.
3.1.2. Formal Definitions
- (1)
- Initialization: Setup (1λ) →PK,MSK. The attribute authorization center utilizes this algorithm for scheme initialization. The input for the algorithm is a security parameter 1λ which generates the system common parameters PK and the master secret key MSK.
- (2)
- Key generation: KeyGen (PK,MSK,id,S) → (SKid,S). The attribute authorization center input includes the system common parameters PK, the system master secret key MSK, the user identity id, and user attributes S. It then proceeds to execute the key-generation algorithm which based on the attribute set S to generate the user’s private key SKid,S.
- (3)
- Data encryption: Encrypt (PK,M, ) → CT. The data producer utilizes an encryption algorithm to generate the ciphertext CT by incorporating the common parameters PK, plaintext data M, and access structure as input parameters.
- (4)
- Data upload: GST (id,addr,CT,timestamp) → Txstorage. The data producers execute the data upload algorithm. The algorithm takes the data producer’s id, the address “addr” returned by the BIM collaborative design platform, the ciphertext CT, and the timestamp as inputs and outputs the storage transaction Txstorage.
- (5)
- Data acquisition: GAT (IndexID,id,timestamp) → Txaccess. The data users execute the data-acquisition algorithm. The algorithm’s input comprises the data IndexID, data user’s id, and timestamp, and outputs the acquisition transaction Txaccess.
- (6)
- Data decryption: Decrypt (CT,PK,SKid,S) → M or ⊥. After obtaining ciphertext CT through contract retrieval, the data user executes the decryption algorithm using the ciphertext CT, the system common parameters PK and their private key SKid,S as input. The algorithm generates the plaintext data M only when attribute S of the data user satisfies access structure .
- (7)
- Key integrity check: KeySanityCheck (PK,SKid,S) → 1 or 0. The attribute authorization center inputs the system common parameters PK and the user’s private key SKid,S to check the integrity of the key before tracing it. If the key is deemed valid, an output of 1 is generated; otherwise, an output of 0 is produced.
- (8)
- Key tracing: Trace (PK,SKid,S) → id. After successfully passing the key integrity check, the attribute authorization center utilizes the system common parameters PK and the user’s private key SKid,S as inputs to execute the key-tracking algorithm, thereby generating the id of the key owner.
3.1.3. Tracking Security Model
3.2. System Implementation
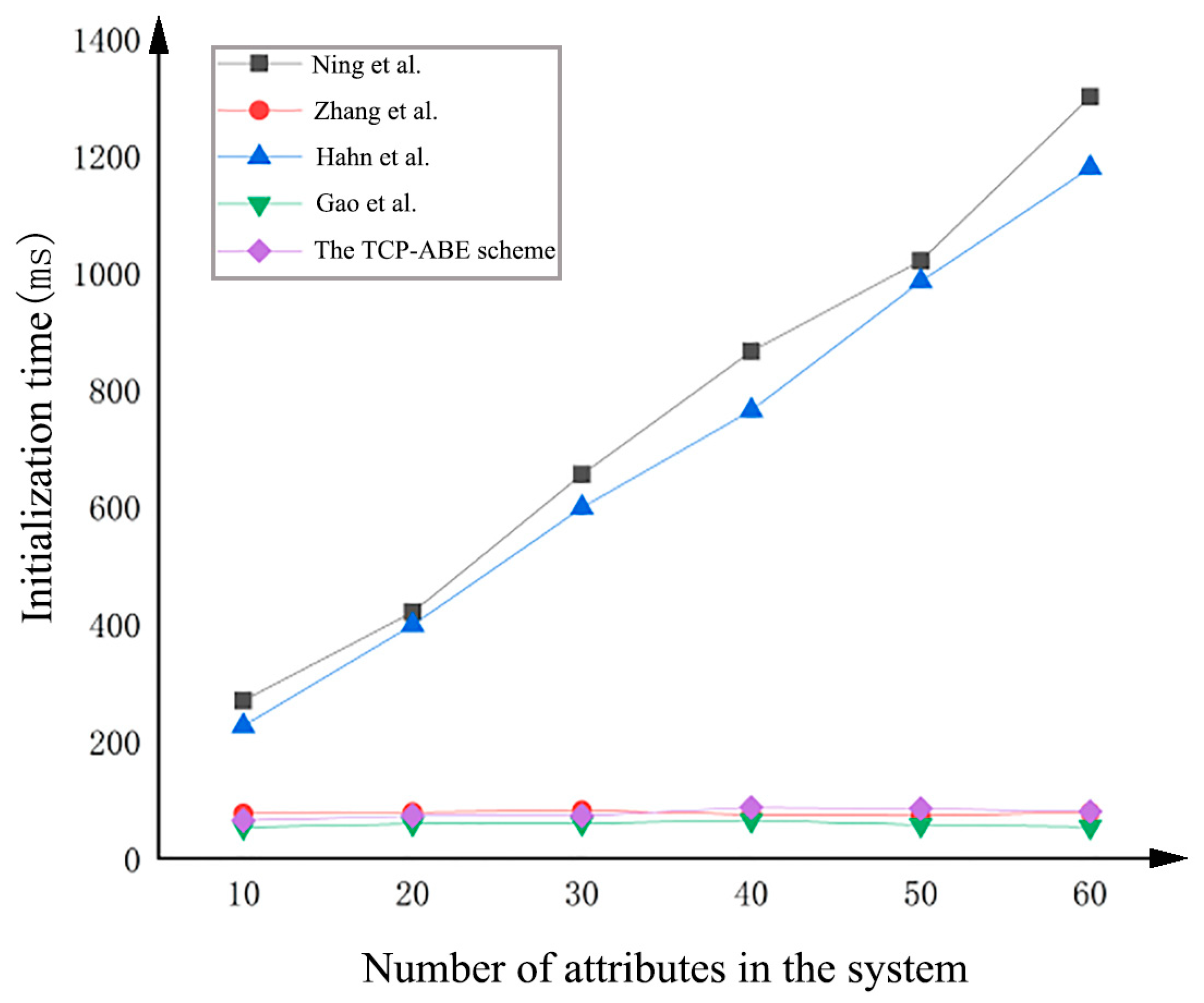
3.2.1. Initialization
3.2.2. Key Generation
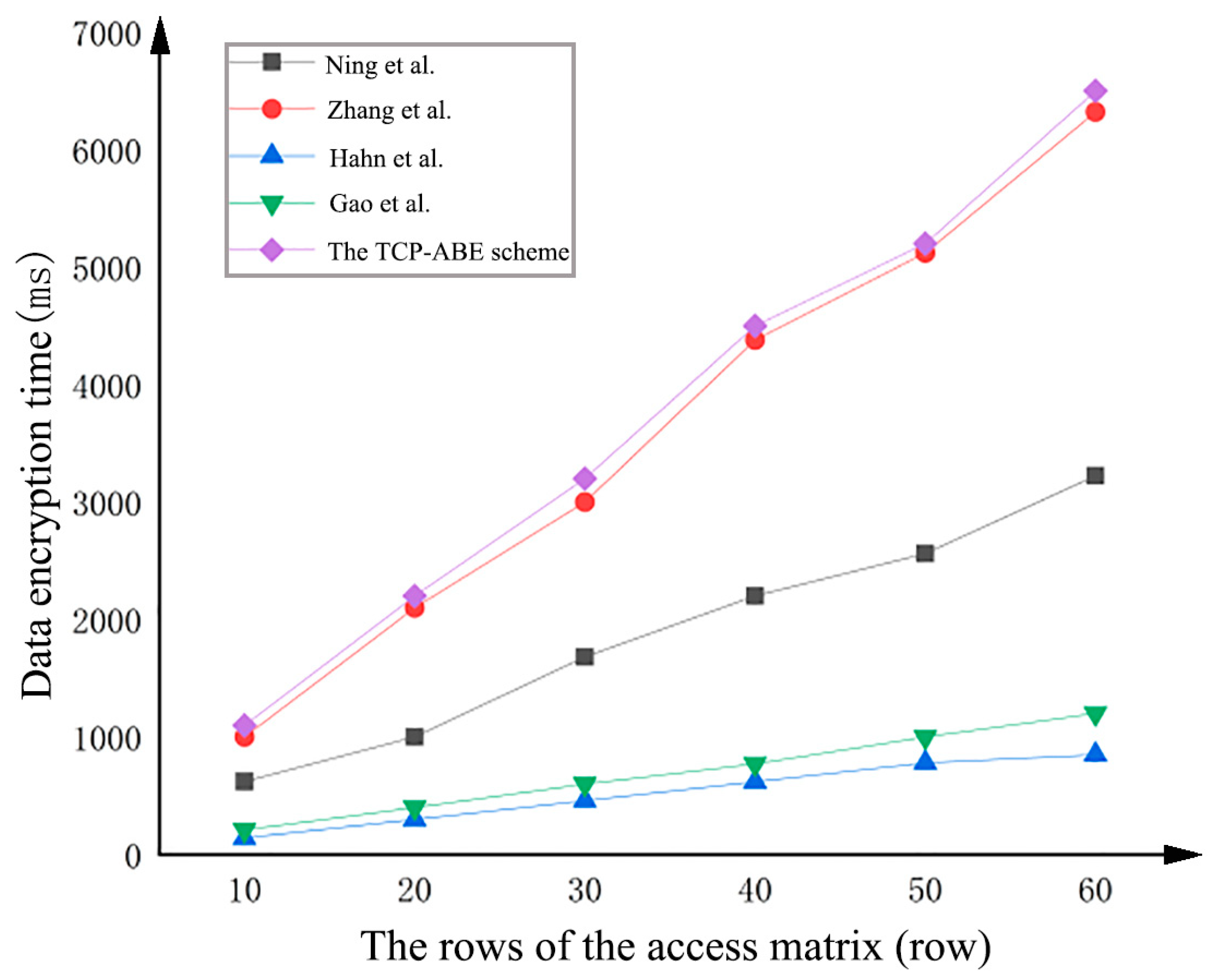
3.2.3. Data Encryption
| Algorithm 1: Generate storage transaction |
| Input: id of data producer, addr of BIM collaborative design platform, ciphertext CT, timestamp Output: Storage transaction Tx 1. indexID = H(id || timestamp) // Calculate the data IndexID 2. MD = H(IndexID, id, addr, CT, timestamp) // Calculate the message digest MD 3. sign = Sign(MD) // The digest is signed 4. Tx = {IndexID, id, addr, CT, timestamp, sign} // Create a transaction Tx 5. return Tx |
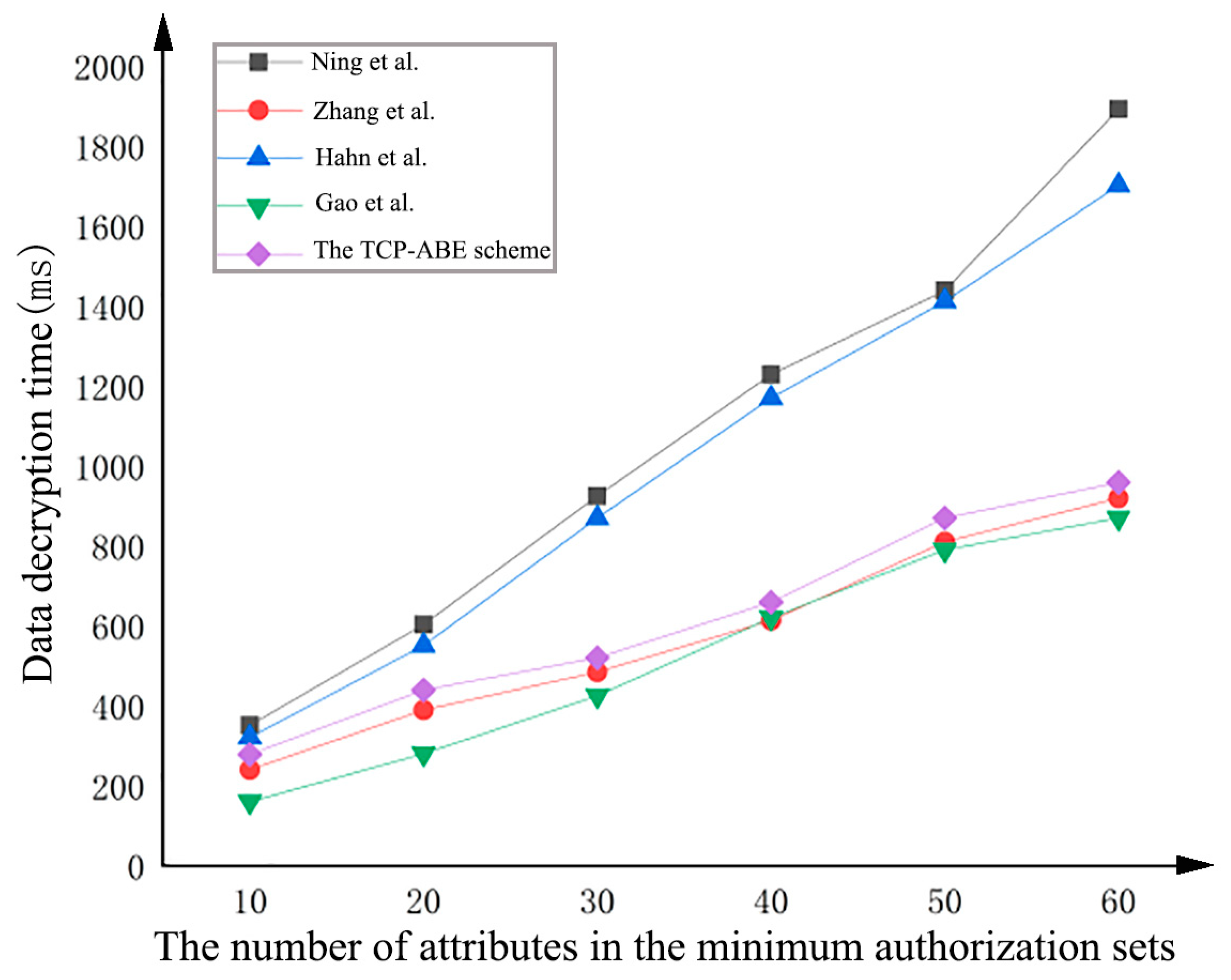
3.2.4. Data Decryption
| Algorithm 2: Generate obtain transaction |
| Input: the data IndexID, the data user’s id, timestamp Output: obtain transaction Tx 1. ChaincodeStub stub = ctx.getStub(); 2. stub.getState(IndexID); // Obtain data based on data IndexID 3. MD’ = H(IndexID, id, addr, CT, timestamp) // Calculate and obtain data message digest MD′ 4. MD = VerifySign(sign) // Verifying data signatures 5. if MD’ == MD then 6. return Tx 7. else // Signature verification failure 8. return Error |
3.2.5. Key Tracing
4. Performance Analysis
4.1. Theoretical Analysis
4.2. Experimental Analysis
5. Conclusions
- (1)
- The development of quantum computers poses a significant threat to the security of conventional encryption algorithms. Quantum computers have the potential to break traditional public key cryptosystems, such as bilinear pairing-based attribute-based encryption schemes. Therefore, it is imperative to investigate attribute-based encryption schemes resilient against quantum attacks.
- (2)
- Currently, there is no effective method for managing the private key associated with the public key in DID documents. If the private key is lost, users must reapply for registration. Hence, it is essential to explore efficient key backup schemes for managing users’ private keys.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Nomenclature
| |I| | The number of attributes in the minimum authorization sets. |
| l | The rows of the access matrix. |
| The time required to perform an exponential operation on group G. | |
| The time required to perform an exponential operation on group GT. | |
| Tp | The time required to perform bilinear mapping operations. |
References
- Zheng, J. Analysis of collaborative design and construction collaborative mechanism of cloud bim platform construction project based on green computing technology. J. Intell. Fuzzy Syst. 2018, 34, 819–829. [Google Scholar] [CrossRef]
- Logothetis, S.; Karachaliou, E.; Valari, E.; Stylianidis, E. Open source cloud-based technologies for BIM. Int. Arch. Photogramm. Remote Sens. Spat. Inf. Sci. 2018, 42, 607–614. [Google Scholar] [CrossRef]
- Lu, S.C.Y.; Cai, J. A collaborative design process model in the sociotechnical engineering design framework. AI EDAM 2001, 15, 3–20. [Google Scholar] [CrossRef]
- Zhao, X. Theory and Practice of BIM Technology; Mechanical Industry Publishing House: Beijing, China, 2020; pp. 94–95. [Google Scholar]
- Sun, P. Security and privacy protection in cloud computing: Discussions and challenges. J. Netw. Comput. Appl. 2020, 160, 102642. [Google Scholar] [CrossRef]
- Nawari, N.O.; Ravindran, S. Blockchain and the built environment: Potentials and limitations. J. Build. Eng. 2019, 25, 100832. [Google Scholar] [CrossRef]
- Tao, X.; Das, M.; Liu, Y.; Cheng, J.C. Distributed common data environment using blockchain and Interplanetary File System for secure BIM-based collaborative design. Autom. Constr. 2021, 130, 103851. [Google Scholar] [CrossRef]
- Tao, X.; Liu, Y.; Wong, P.K.-Y.; Chen, K.; Das, M.; Cheng, J.C. Confidentiality-minded framework for blockchain-based BIM design collaboration. Autom. Constr. 2022, 136, 104172. [Google Scholar] [CrossRef]
- Das, M.; Tao, X.; Cheng, J.C. BIM security: A critical review and recommendations using encryption strategy and blockchain. Autom. Constr. 2021, 126, 103682. [Google Scholar] [CrossRef]
- Sahai, A.; Waters, B. Fuzzy identity-based encryption. In Advances in Cryptology–EUROCRYPT 2005: 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 457–473. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October 2006–3 November 2006; pp. 89–98. [Google Scholar] [CrossRef]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07), Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar] [CrossRef]
- Kiayias, A.; Tang, Q. How to keep a secret: Leakage deterring public-key cryptosystems. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 943–954. [Google Scholar] [CrossRef]
- Ning, J.; Dong, X.; Cao, Z.; Wei, L.; Lin, X. White-box traceable ciphertext-policy attribute-based encryption supporting flexible attributes. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1274–1288. [Google Scholar] [CrossRef]
- Liu, Z.; Duan, S.; Zhou, P.; Wang, B. Traceable-then-revocable ciphertext-policy attribute-based encryption scheme. Future Gener. Comput. Syst. 2019, 93, 903–913. [Google Scholar] [CrossRef]
- Zhang, K.; Li, Y.; Song, Y.; Lu, L.; Zhang, T.; Jiang, Q. A traceable and revocable multiauthority attribute-based encryption scheme with fast access. Secur. Commun. Netw. 2020, 2020, 6661243. [Google Scholar] [CrossRef]
- Han, D.; Pan, N.; Li, K.C. A traceable and revocable ciphertext-policy attribute-based encryption scheme based on privacy protection. IEEE Trans. Dependable Secur. Comput. 2020, 19, 316–327. [Google Scholar] [CrossRef]
- Bouchaala, M.; Ghazel, C.; Saidane, L.A. Trak-cpabe: A novel traceable, revocable and accountable ciphertext-policy attribute-based encryption scheme in cloud computing. J. Inf. Secur. Appl. 2021, 61, 102914. [Google Scholar] [CrossRef]
- Ning, J.; Huang, X.; Wei, L.; Ma, J.; Rong, J. Tracing malicious insider in attribute-based cloud data sharing. Chin. J. Comput. 2022, 45, 1431–1445. [Google Scholar] [CrossRef]
- Ning, J.; Cao, Z.; Dong, X.; Wei, L. White-box traceable CP-ABE for cloud storage service: How to catch people leaking their access credentials effectively. IEEE Trans. Dependable Secur. Comput. 2018, 15, 883–897. [Google Scholar] [CrossRef]
- Zhang, Y.; Zheng, D.; Deng, R.H. Security and privacy in smart health: Efficient policy-hiding attribute-based access control. IEEE Internet Things J. 2018, 5, 2130–2145. [Google Scholar] [CrossRef]
- Hahn, C.; Kwon, H.; Hur, J. Efficient attribute-based secure data sharing with hidden policies and traceability in mobile health networks. Mob. Inf. Syst. 2016, 2016, 6545873. [Google Scholar] [CrossRef]
- Gao, S.; Piao, G.; Zhu, J.; Ma, X.; Ma, J. Trustaccess: A trustworthy secure ciphertext-policy and attribute hiding access control scheme based on blockchain. IEEE Trans. Veh. Technol. 2020, 69, 5784–5798. [Google Scholar] [CrossRef]
- Sun, J.; Xiong, H.; Liu, X.; Zhang, Y.; Nie, X.; Deng, R.H. Lightweight and privacy-aware fine-grained access control for IoT-oriented smart health. IEEE Internet Things J. 2020, 7, 6566–6575. [Google Scholar] [CrossRef]
- Zhang, W.; Zhang, Z.; Xiong, H.; Qin, Z. PHAS-HEKR-CP-ABE: Partially policy-hidden CP-ABE with highly efficient key revocation in cloud data sharing system. J. Ambient. Intell. Humaniz. Comput. 2022, 13, 613–627. [Google Scholar] [CrossRef]

| Scheme | Access Structure | Large Attribute Domain | Policy Hiding | Key Tracking | Decryption Test | Blockchain |
|---|---|---|---|---|---|---|
| Ning et al. [20] | LSSS | × | × | √ | × | × |
| Zhang et al. [21] | LSSS | √ | √ | × | √ | × |
| Hahn et al. [22] | AND | × | √ | √ | × | × |
| Gao et al. [23] | AND | √ | √ | √ | × | √ |
| The TCP-ABE scheme | LSSS | √ | √ | √ | √ | √ |
| Scheme | Ciphertext Encryption | Decryption Testing | Ciphertext Decryption |
|---|---|---|---|
| Ning et al. [20] | - | (2|I| + 2) | |
| Zhang et al. [21] | 2 | (2|I| + 1) | |
| Hahn et al. [22] | - | (2|I| + 1) | |
| Gao et al. [23] | - | (|I| + 1) | |
| The TCP-ABE scheme | 3 | (2|I| + 1) |
| Operation | |||
|---|---|---|---|
| Time (ms) | 14.637 | 18.769 | 2.341 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, J.; Xiang, G.; Li, C.; Xie, W. Traceable Attribute-Based Encryption Scheme Using BIM Collaborative Design. Buildings 2024, 14, 731. https://doi.org/10.3390/buildings14030731
Liu J, Xiang G, Li C, Xie W. Traceable Attribute-Based Encryption Scheme Using BIM Collaborative Design. Buildings. 2024; 14(3):731. https://doi.org/10.3390/buildings14030731
Chicago/Turabian StyleLiu, Jie, Guangli Xiang, Chengde Li, and Weiping Xie. 2024. "Traceable Attribute-Based Encryption Scheme Using BIM Collaborative Design" Buildings 14, no. 3: 731. https://doi.org/10.3390/buildings14030731
APA StyleLiu, J., Xiang, G., Li, C., & Xie, W. (2024). Traceable Attribute-Based Encryption Scheme Using BIM Collaborative Design. Buildings, 14(3), 731. https://doi.org/10.3390/buildings14030731