A User Profile of Tendering and Bidding Corruption in the Construction Industry Based on SOM Clustering: A Case Study of China
Abstract
1. Introduction
2. Literature Review
2.1. Theory of Collusive Bidding
2.2. Theory of User Profile
2.3. User Profile in Bidding Corruption
3. Research Design
3.1. Data Collection
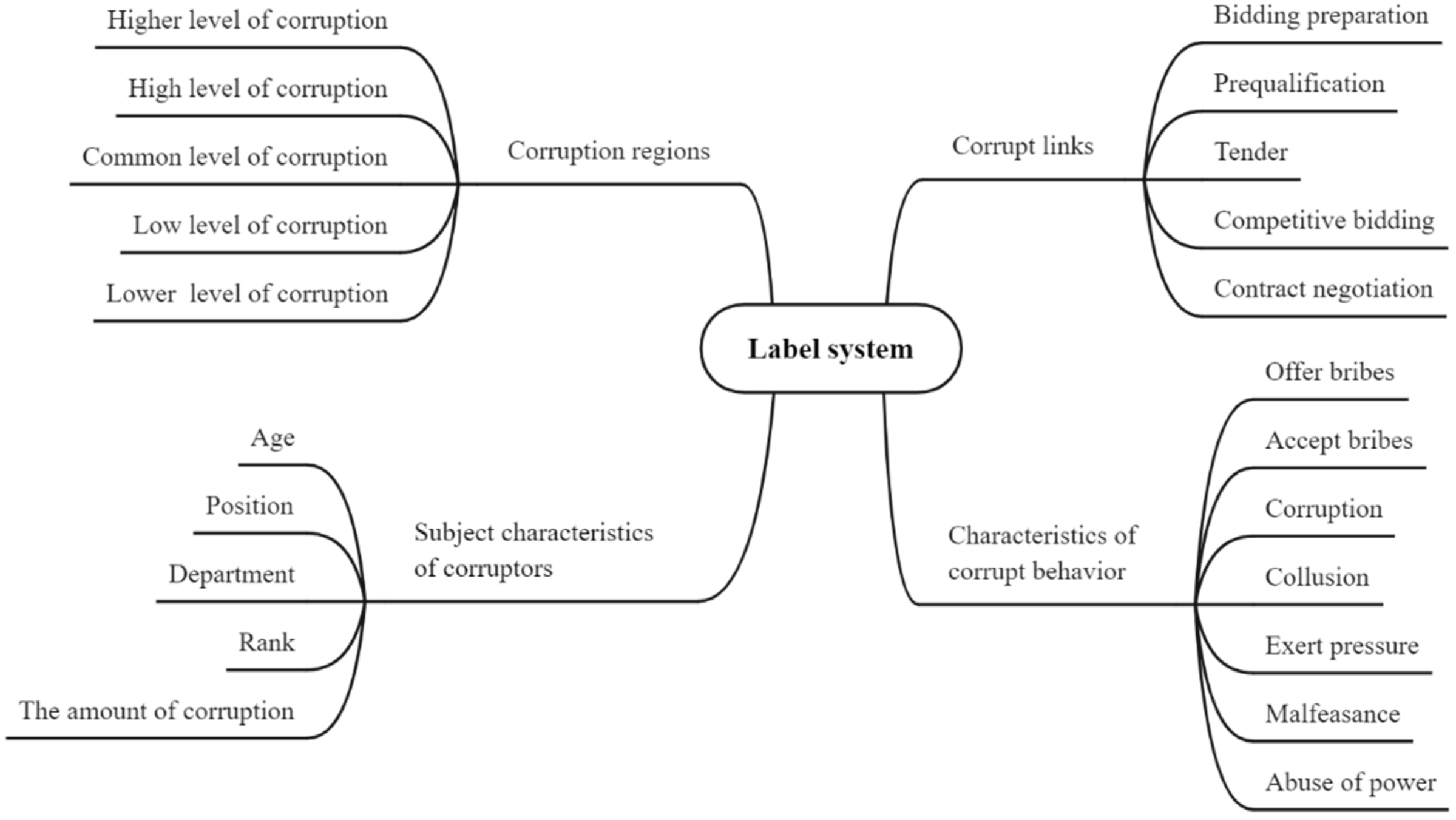
3.2. Label System
3.2.1. Regional Label
3.2.2. Corruptor Characteristic Label
3.2.3. Corruption Preference Link Label
3.2.4. Corruption Way Label
3.3. SOM Clustering
3.3.1. Input Dataset
3.3.2. Normalized Dataset
3.3.3. Set Weight Node
3.3.4. Define Learning Rate and Clustering Radius
3.3.5. Find Winning Neurons
3.3.6. Iterative Calculation
4. Empirical Results and Data Analysis
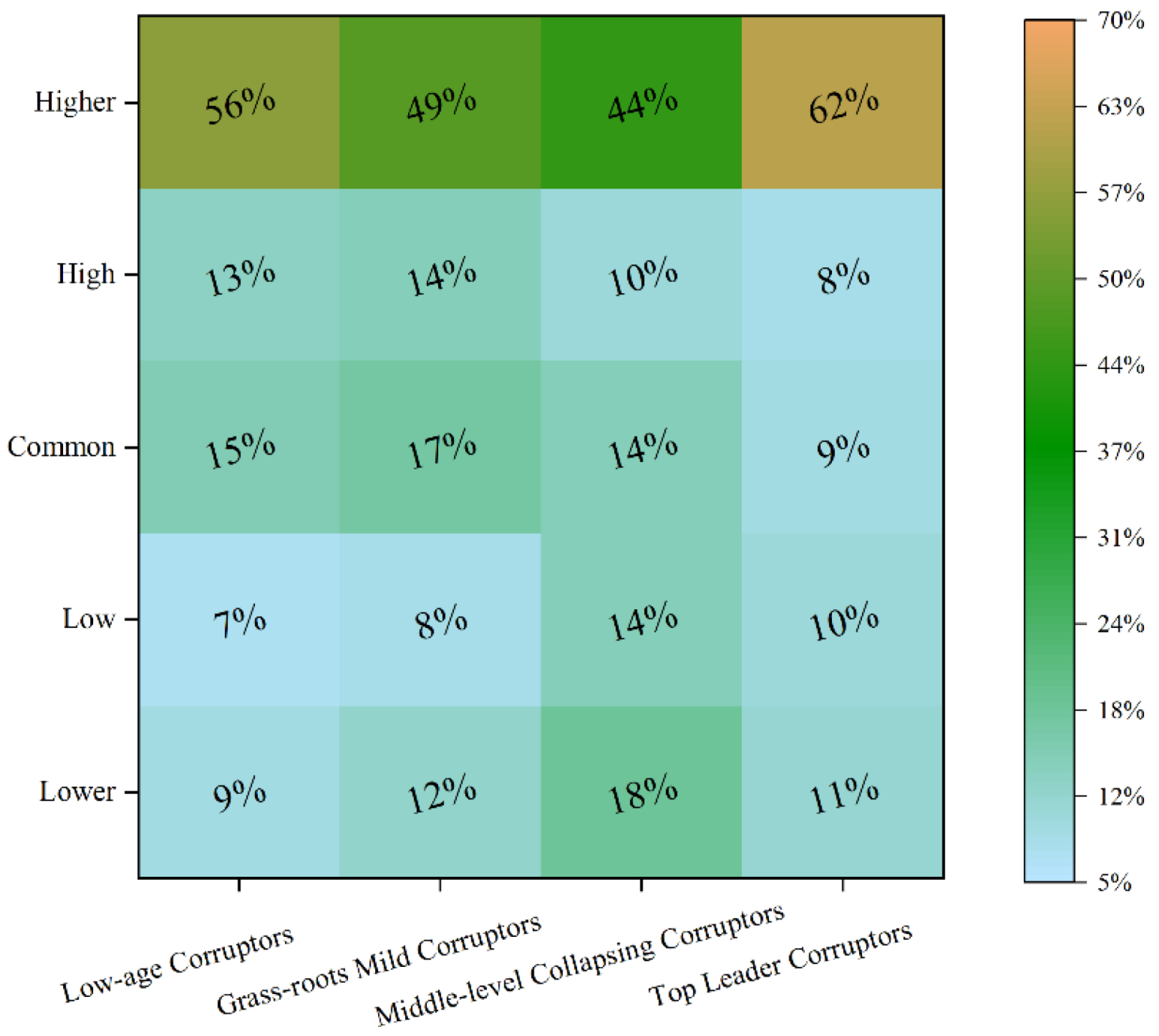
4.1. Corruption Region Label Data Analysis
4.2. Corruptor Characteristic Label Data Analysis
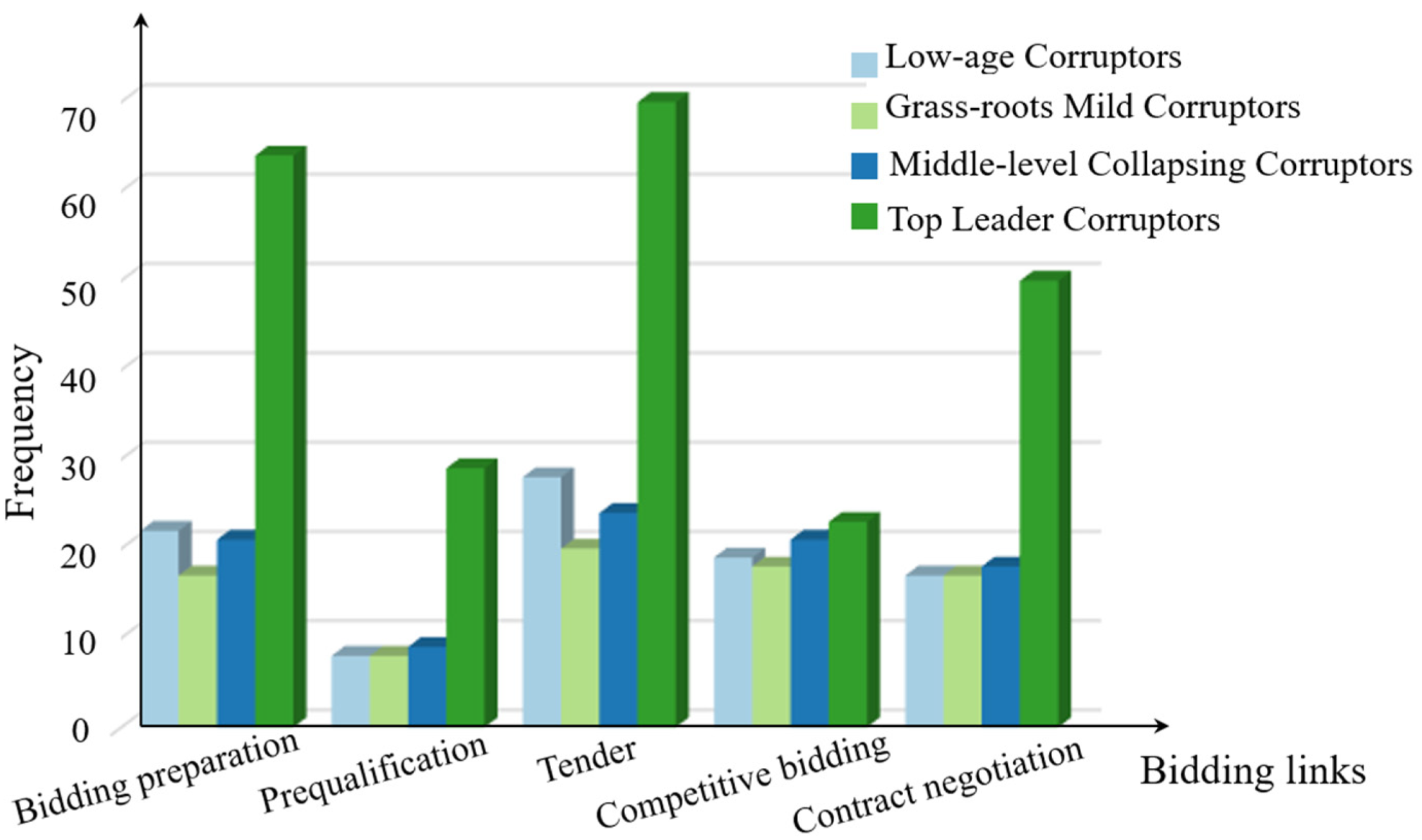
4.3. Corruption Preference Link Label Data Analysis
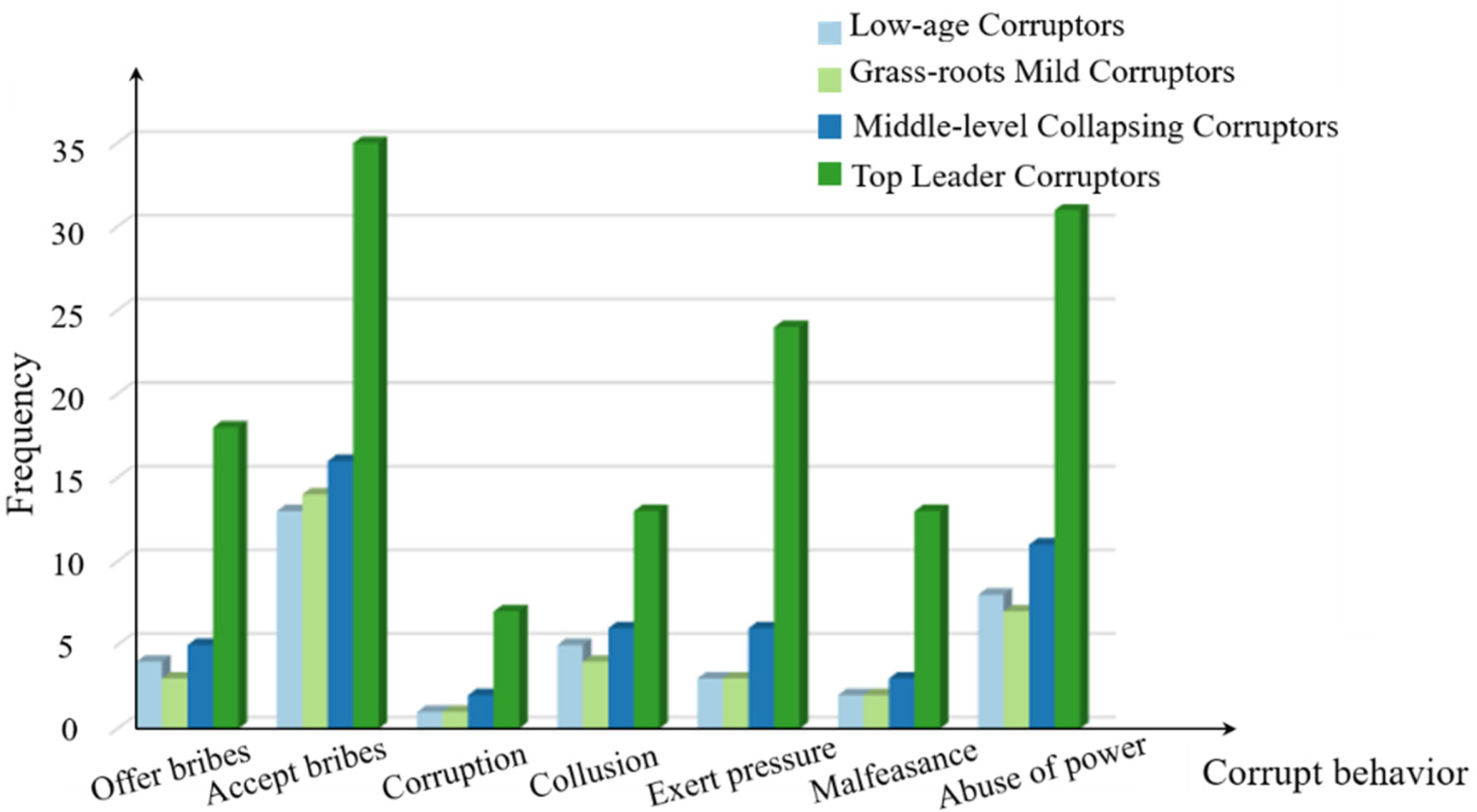
4.4. Corruption Way Label Data Analysis
4.5. SOM Clustering Results
5. Findings and Discussion
5.1. Regional Label-Based Description
5.2. Corruptor Characteristic Label-Based Description
5.3. Preference Link Label-Based Description
5.4. Corrupt Behavior Label-Based Description
5.5. Four Cluster User Profile Description
5.5.1. User Profile of Low-Age Corruptors
5.5.2. User Profile of Grassroots Mild Corruptors
5.5.3. User Profile of Middle-Level Collapsing Corruptors
5.5.4. User Profile of Top Leader Corruptors
6. Conclusions and Limitations
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Stansbury, N. Exposing the foundations of corruption in construction. Transpar. Int. 2005, 36, 40. [Google Scholar]
- Kerridge, S.; Halaris, C.; Mentzas, G.; Kerridge, S. Virtual tendering and bidding in the construction sector. In Electronic Commerce and Web Technologies; Springer: Berlin/Heidelberg, Germany, 2001; pp. 379–388. [Google Scholar]
- И Апулеев. Списoк Генпрoкуратуры: В Каких Региoнах Вoруют Бoльше Всегo. 2020. Available online: https://www.gazeta.ru/social/2020/06/18/13121683.shtml?utm_source=yxnews&utm_medium=desktop&utm_referrer=https%3A%2F%2Fyandex.ru%2Fnews (accessed on 18 June 2020).
- EU. Identifying and Reducing Corruption in Public Procurement in the EU; EU: Luxembourg, 2013. [Google Scholar]
- Man, S. Examples of Collusion Bidding and Preventive Measures; Social Sciences Press: Beijing, China, 2005. [Google Scholar]
- Mishra, S. ‘The shame games’: A textual analysis of western press coverage of the commonwealth games in india. Third World Q. 2012, 33, 871–886. [Google Scholar] [CrossRef]
- Bank, T.W. Nigeria-Citizen Monitors Prevent Corruption and Ensure Procurement Accountability in Energy Sector; Grupo Banco Mundial: Washington, DC, USA, 2015. [Google Scholar]
- Ministry of Housing and Urban-Rural Development of the People’s Republic of China. The 14th Five-Year Plan for National Urban Infrastructure Construction. Available online: https://www.mohurd.gov.cn/xinwen/gzdt/202208/20220801_767419.html (accessed on 1 August 2022).
- Le, Y.; Ming, S.; Albert, P.C.C.; Yi, H. Overview of Corruption Research in Construction. J. Manag. Eng. 2014, 30, 02514001. [Google Scholar] [CrossRef]
- Wang, X.; Ye, K.; Arditi, D. Embodied cost of collusive bidding: Evidence from China’s construction industry. J. Constr. Eng. Manag. 2021, 147, 04021037. [Google Scholar] [CrossRef]
- Zhang, B.; Le, Y.; Xia, B.; Skitmore, M. Causes of business-to-government corruption in the tendering process in China. J. Manag. Eng. 2017, 33, 05016022. [Google Scholar] [CrossRef]
- China Journal of Discipline Inspection and Supervision. Big Data Supervision Helps Prevent Corruption in Engineering Construction. Available online: https://zgjjjc.ccdi.gov.cn/bqml/bqxx/202104/t20210414_239604.html (accessed on 28 April 2021).
- Zhang, B.; Le, Y. Wang, Y. LI, Y. Tendering and Bidding Corruption Research Based on B2G Guanxi—Based on 90 typical cases. J. Public Adm. 2015, 8, 141–163. [Google Scholar]
- Lengwiler, Y.; Wolfstetter, E.G. Auctions and corruption: An analysis of bid rigging by a corrupt auctioneer. J. Econ. Dyn. Control 2010, 34, 1872–1892. [Google Scholar] [CrossRef]
- Borsky, S.; Kalkschmied, K. Corruption in Space: A Closer Look at the World’s Subnations. Eur. J. Political Econ. 2019, 59, 400–422. [Google Scholar] [CrossRef]
- Lima, M.S.M.; Delen, D. Predicting and explaining corruption across countries: A machine learning approach. Gov. Inf. Q. 2020, 37, 101407. [Google Scholar] [CrossRef]
- Cirilovic, J.; Vajdic, N.; Mladenovic, G.; Queiroz, C. Developing cost estimation models for road rehabilitation and reconstruction: Case study of projects in Europe and Central Asia. J. Constr. Eng. Manag. 2014, 140, 04013065. [Google Scholar] [CrossRef]
- Ren, J.; Sun, H. Systematic Prevention Is the fundamental Strategy of Anti-corruption of Civil Engineering. J. Natl. Procur. Coll. 2005, 13, 145–151. [Google Scholar]
- Ortega, D.L.; Florax, R.J.; Delbecq, B.A. Primary determinants and the spatial distribution of corruption. Res. Agric. Appl. Econ. 2010. [Google Scholar] [CrossRef]
- Le, Y.; Shan, M.; Chan, A.P.; Hu, Y. Investigating the causal relationships between causes of and vulnerabilities to corruption in the Chinese public construction sector. J. Constr. Eng. Manag. 2014, 140, 05014007. [Google Scholar] [CrossRef]
- Olken, B.A. Monitoring corruption: Evidence from a field experiment in Indonesia. J. Political Econ. 2007, 115, 200–249. [Google Scholar] [CrossRef]
- López-Iturriaga, F.J.; Sanz, I.P. Predicting public corruption with neural networks: An analysis of Spanish provinces. Soc. Indic. Res. 2018, 140, 975–998. [Google Scholar] [CrossRef]
- Xiao, L.; Ye, K.H.; Zhou, J.H.; Ye, X.T.; Tekka, R.S. A social network-based examination on bid riggers’ relationships in the construction industry: A case study of China. Buildings 2021, 11, 363. [Google Scholar] [CrossRef]
- Owusu, E.K.; Chan, A.P.; Shan, M. Causal factors of corruption in construction project management: An overview. Sci. Eng. Ethics 2019, 25, 1–31. [Google Scholar] [CrossRef]
- Chan, A.P.; Owusu, E.K. Corruption forms in the construction industry: Literature review. J. Constr. Eng. Manag. 2017, 143, 04017057. [Google Scholar] [CrossRef]
- Bologna, R.; Del Nord, R. Effects of the law reforming public works contracts on the Italian building process. Build. Res. Inf. 2000, 28, 109–118. [Google Scholar] [CrossRef]
- Kotey, B.; Meredith, G. Relationships among owner/manager personal values, business strategies, and enterprise performance. Small Bus. Manag. 1997, 35, 37–64. [Google Scholar]
- Messick, R. Curbing Fraud, Corruption, and Collusion in the Roads Sector; The World Bank: Washington, DC. USA, 2011. [Google Scholar]
- Décary-Hétu, D.; Aldridge, J. Sifting through the net: Monitoring of online offenders by researchers. Eur. Rev. Organ. Crime 2015, 2, 122–141. [Google Scholar]
- Saenz, C.; Brown, H. The disclosure of anti-corruption aspects in companies of the construction sector: Main companies worldwide and in Latin America. J. Clean. Prod. 2018, 196, 259–272. [Google Scholar] [CrossRef]
- Owusu, E.K.; Chan, A.P. Barriers affecting effective application of anticorruption measures in infrastructure projects: Disparities between developed and developing countries. J. Manag. Eng. 2019, 35, 04018056. [Google Scholar] [CrossRef]
- Spector, B.I. The benefits of anti-corruption programming: Implications for low to lower middle income countries. Crime Law Soc. Change 2016, 65, 423–442. [Google Scholar] [CrossRef]
- Jancsics, D. Corruption as resource transfer: An interdisciplinary synthesis. Public Adm. Rev. 2019, 79, 523–537. [Google Scholar] [CrossRef]
- Ateljevic, J.; Budak, J. Corruption and public procurement: Example from Croatia. J. Balk. Near East. Stud. 2010, 12, 375–397. [Google Scholar] [CrossRef]
- Sharma, C.; Mitra, A. Corruption, governance and firm performance: Evidence from Indian enterprises. J. Policy Model. 2015, 37, 835–851. [Google Scholar] [CrossRef]
- Ballesteros-Pérez, P.; Skitmore, M.; Das, R.; del Campo-Hitschfeld, M.L. Quick abnormal-bid-detection method for construction contract auctions. J. Constr. Eng. Manag. 2015, 141, 04015010. [Google Scholar] [CrossRef]
- Monteiro, B.K.; Masiero, G.; Souza, F.D. Corruption in the construction industry: A review of recent literature. Int. J. Constr. Manag. 2022, 22, 2744–2752. [Google Scholar] [CrossRef]
- Morselli, C.; Ouellet, M. Network similarity and collusion. Soc. Netw. 2018, 55, 21–30. [Google Scholar] [CrossRef]
- Fazekas, M.; Kocsis, G. Uncovering high-level corruption: Cross-national objective corruption risk indicators using public procurement data. Br. J. Political Sci. 2020, 50, 155–164. [Google Scholar] [CrossRef]
- Leischnig, A.; Woodside, A.G. Who approves fraudulence? Configurational causes of consumers’ unethical judgments. J. Bus. Ethics 2019, 158, 713–726. [Google Scholar] [CrossRef]
- Ransom, J. Replicating Data Mining Techniques for Development: A Case Study of Corruption. Master’s Thesis, Lund University, Lund, Sweden, 2013. Available online: https://lup.lub.lu.se/student-papers/search/publication/3798253 (accessed on 1 August 2022).
- Kanoje, S.; Girase, S.; Mukhopadhyay, D. User profiling trends, techniques and applications. arXiv 2015, arXiv:1503.07474. [Google Scholar]
- Mezghani, M.; Zayani, C.A.; Amous, I.; Gargouri, F. A user profile modeling using social annotations: A survey. In Proceedings of the 21st International Conference on World Wide Web, Lyon, France, 16–20 April 2012; ACM: New York, NY, USA; pp. 969–976. [Google Scholar]
- Tang, J.; Yao, L.; Zhang, D.; Zhang, J. A combination approach to web user profiling. ACM Trans. Knowl. Discov. Data (TKDD) 2010, 5, 1–44. [Google Scholar] [CrossRef]
- Jang, C.; Chang, H.; Ahn, H.; Kang, Y.; Choi, E. Profile for effective service management on mobile cloud computing. In Advanced Communication and Networking; Springer: Berlin/Heidelberg, Germany, 2011; pp. 139–145. [Google Scholar]
- Mobasher, B. Data Mining for Web Personalization; Springer: Berlin/Heidelberg, Germany, 2007; pp. 90–135. [Google Scholar]
- Peng, J.; Choo, K.K.R.; Ashman, H. User profiling in intrusion detection: A review. J. Netw. Comput. Appl. 2016, 72, 14–27. [Google Scholar] [CrossRef]
- Amato, F.; Moscato, V.; Picariello, A.; Piccialli, F.; Sperlí, G. Centrality in heterogeneous social networks for lurkers detection: An approach based on hypergraphs. Concurr. Comput. Pr. Exp. 2018, 30, e4188. [Google Scholar] [CrossRef]
- Eke, C.I.; Norman, A.A.; Shuib, L.; Nweke, H.F. A survey of user profiling: State-of-the-art, challenges, and solutions. IEEE Access. 2019, 7, 144907–144924. [Google Scholar] [CrossRef]
- Ouaftouh, S.; Zellou, A.; Idri, A. Social recommendation: A user profile clustering-based approach. Concurr. Comput. Pr. Exp. 2019, 31, e5330. [Google Scholar] [CrossRef]
- Gao, B.; Du, S.; Li, X.; Liu, F. Research on the application of persona in book recommendation system. J. Phys. Conf. Ser. 2017, 910, 012023. [Google Scholar] [CrossRef]
- Wang, G.; Lu, R.; Huang, C.; Guan, Y.L. An efficient and privacy-preserving pre-clinical guide scheme for mobile eHealthcare. J. Inf. Secur. Appl. 2019, 46, 271–280. [Google Scholar] [CrossRef]
- Farnadi, G.; Tang, J.; De Cock, M.; Moens, M.-F. User profiling through deep multimodal fusion. In Proceedings of the Eleventh ACM International Conference on Web Search and Data Mining, New York, NY, USA, 5–9 February 2018; ACM: New York, NY, USA, 2018; pp. 171–179. [Google Scholar]
- Watson, B.; Watson, A.; Siskind, V.; Fleiter, J.; Soole, D. Profiling high-range speeding offenders: Investigating criminal history, personal characteristics, traffic offences, and crash history. Accid. Anal. Prev. 2015, 74, 87–96. [Google Scholar] [CrossRef] [PubMed]
- Boehmer, W. Analyzing human behavior using case-based reasoning with the help of forensic questions. In Proceedings of the 2010 24th IEEE International Conference on Advanced Information Networking and Applications, Perth, Australia, 20–23 April 2010; IEEE: Piscataway, NJ, USA; pp. 1189–1194. [Google Scholar]
- Honghao, J. Research on the “Big Data Portrait” of the Subject Characteristics of Corruption and Bribery Crimes–Based on the big data analysis of 8133 public indictments. J. Crime Res. 2020, 1, 2–15. [Google Scholar]
- Li, Y.; Le, Y.; Zhang, B.; Shan, M. The correlations among corruption severity, power and behavior features in construction industry: An Empirical study based on 148 typical cases. Manag. Rev. 2013, 8, 21–31. [Google Scholar]
- Wang, X.; Arditi, D.; Ye, K. Coupling Effects of Economic, Industrial, and Geographical Factors on Collusive Bidding Decisions. J. Constr. Eng. Manag. 2022, 148, 04022042. [Google Scholar] [CrossRef]
- Yang, L. Research on the Characteristics of Officials Corruption in Prefecture-level Cities of China. Int. J. Econ. Behav. Organ. 2020, 8, 92. [Google Scholar] [CrossRef]
- Mahmood, M.A.; Tian, Y.; Azeez, K.A. How Corruption Affects Economic Growth: Perception of Religious Powers for Anti-corruption in Iraq. In Proceedings of the International Conference on Management Science and Engineering Management, Kanazawa, Japan, 28–31 July 2017; Springer: Cham, Switzerland; pp. 1466–1475. [Google Scholar]




| Corruption Level | Provincial Administrative Districts and Their Corresponding Codes |
|---|---|
| Higher | Jiangsu (26) Guizhou (27) Hunan (28) Hubei (29) Anhui (30) Sichuan (31) |
| High | Guangxi (23) Zhejiang (24) Guangdong (25) |
| Common | Henan (17) Chongqing (18) Yunnan (19) Shaanxi (20) Jiangxi (21) Shandong (22) |
| Lower | Shanxi (10) Heilongjiang (11) Xinjiang (12) Hainan (13) Fujian (14) Jilin (15) Hebei (16) |
| Low | Shanghai (1) Beijing (2) Inner Mongolia (3) Tibet (4) Tianjin (5) Gansu (6) Ningxia (7) Liaoning (8) Qinghai (9) |
| Characteristic Indicators | Indicator Type | Discrete Processing | Data Information | |||
|---|---|---|---|---|---|---|
| Minimum | Maximum | Average | Standard Deviation | |||
| Age | Numerical | —— | 27 | 70 | 50.16 | 6.697 |
| Amount of corruption (10 thousand yuan) | Numerical | —— | 1 | 7199.49 | 165.925 | 372.883 |
| Frequency | ||||||
| Position | Text | Staff = 1 | 6.33% | |||
| Department manager = 2 | 16.81% | |||||
| Deputy general manager = 3 | 40.64% | |||||
| General manager = 4 | 31.20% | |||||
| Other = 5 | 5.08% | |||||
| Department | Text | Owner units = 1 | 53.21% | |||
| Administrative units = 2 | 32.00% | |||||
| Party and government organs = 3 | 11.57% | |||||
| Other = 4 | 3.22% | |||||
| Rank | Text | Non-state staff (Mostly referring to village cadres and other non-public officials who hold certain public power and resources) = 0 | 21.47% | |||
| Grassroots staffs (Section-level cadres and below) = 1 | 17.28% | |||||
| Middle-level cadres (Division-level cadres) = 2 | 26.19% | |||||
| Senior cadres (Department-level cadres and above) = 3 | 35.06% | |||||
| Types of Corruption | Behavior | Total Frequency of High-Frequency Feature Words | Types of Corruption | Behavior | Total Frequency of High-Frequency Feature Words |
|---|---|---|---|---|---|
| Offer bribes | Gratitude | 17,526 | Collusion | Exploit | 18,059 |
| Concern | 5974 | Promise | 3046 | ||
| Return | 4791 | Exert pressure | Arrange | 17,768 | |
| Accept bribes | Accept | 56,037 | Collude with | 3046 | |
| Bribe | 46,928 | Malfeasance | Agree | 10,698 | |
| Seek | 10,085 | Conceal | 2093 | ||
| Extort bribes | 1702 | Abuse of power | Help | 42,886 | |
| Corruption | Coordinate | 3462 | Solicit | 12,434 | |
| Misappropriation | 2798 | Introduce | 4281 |
| Clustered Groups | Characteristic Indicators | Indicator Type | Minimum | Maximum | Average | Higher Frequency Discrete Value |
|---|---|---|---|---|---|---|
| Low-age Corruptors | Age | Numerical | 28 | 68 | 47 | — |
| Amount of corruption (Ten thousand yuan) | Numerical | 1.00 | 1694.20 | 1.80 | — | |
| Position | Text | 1 | 3 | — | 2 | |
| Department | Text | 1 | 3 | — | 1 | |
| Rank | Text | 0 | 3 | — | 1 | |
| Grassroots Mild Corruptors | Age | Numerical | 27 | 70 | 50 | — |
| Amount of corruption (Ten thousand yuan) | Numerical | 1 | 3677.00 | 128.56 | — | |
| Position | Text | 3 | 4 | — | 1, 2 | |
| Department | Text | 1 | 2 | — | 2 | |
| Rank | Text | 0 | 3 | — | 1 | |
| Middle-level Collapsing Corruptors | Age | Numerical | 34 | 68 | 51 | — |
| Amount of corruption (Ten thousand yuan) | Numerical | 3.10 | 7199.49 | 266.57 | — | |
| Position | Text | 2 | 4 | — | 2, 3 | |
| Department | Text | 1 | 3 | — | 3 | |
| Rank | Text | 1 | 3 | — | 2 | |
| Top Leader Corruptors | Age | Numerical | 34 | 70 | 52 | — |
| Amount of corruption (Ten thousand yuan) | Numerical | 2.00 | 2501.26 | 291.51 | — | |
| Position | Text | 2 | 4 | — | 3, 4 | |
| Department | Text | 1 | 3 | — | 2, 3 | |
| Rank | Text | 0 | — | 3 |
| Types of Corruption | Index Factors | First Principal Component | Second Principal Component | Third Principal Component | Fourth Principal Component | Fifth Principal Component |
|---|---|---|---|---|---|---|
| Offer bribes | Gratitude | 0.509 | −0.441 | 0.269 | 0.229 | −0.020 |
| Look after | 0.236 | 0.440 | 0.209 | −0.043 | 0.405 | |
| Return | 0.420 | −0.278 | 0.242 | −0.269 | −0.342 | |
| Accept bribes | Accept | 0.723 | 0.169 | 0.436 | −0.017 | 0.009 |
| Bribe | 0.651 | 0.020 | 0.020 | −0.313 | −0.135 | |
| Seek | 0.408 | 0.598 | 0.289 | 0.242 | 0.018 | |
| Extort bribes | 0.316 | 0.315 | −0.100 | −0.226 | −0.396 | |
| Corruption | Coordinate | 0.473 | −0.198 | −0.244 | 0.371 | −0.070 |
| Misappropriation | 0.242 | −0.394 | 0.408 | 0.380 | 0.242 | |
| Collusion | Exploit | 0.584 | 0.588 | 0.106 | 0.137 | 0.040 |
| Promise | 0.484 | −0.039 | −0.335 | −0.221 | 0.401 | |
| Exert pressure | Arrange | 0.739 | −0.066 | −0.162 | −0.237 | 0.127 |
| Collude with | 0.342 | 0.048 | −0.420 | 0.391 | 0.086 | |
| Malfeasance | Agree | 0.605 | −0.148 | −0.378 | −0.268 | 0.320 |
| Conceal | 0.419 | −0.288 | 0.403 | −0.291 | 0.131 | |
| Abuse of power | Help | 0.770 | −0.213 | 0.075 | 0.203 | −0.122 |
| Solicit | 0.529 | 0.083 | −0.142 | 0.064 | −0.399 | |
| Introduce | 0.511 | −0.028 | −0.480 | 0.175 | −0.102 |
| Clustered Groups | Index Factors That Can Be Reflected by the Extracted Principal Components | ||||||
|---|---|---|---|---|---|---|---|
| First Principal Component | Second Principal Component | Third Principal Component | Fourth Principal Component | Fifth Principal Component | Sixth Principal Component | Seventh Principal Component | |
| Low-age corruptors | Help | Seek Exploit | Introduce | Misappropriation Coordinate | Concern Promise Solicit Extort bribes | —— | —— |
| Grassroots mild corruptors | Help | Agree | Gratitude | Concern | Extort bribes | —— | —— |
| Middle-level collapsing corruptors | Help | Promise | Seek | Collude with | Return | Extort bribes | —— |
| Top leader corruptors | Accept | Gratitude | Agree | Arrange Collude with | Return | Misappropriation | Extort bribes |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, B.; Li, Y. A User Profile of Tendering and Bidding Corruption in the Construction Industry Based on SOM Clustering: A Case Study of China. Buildings 2022, 12, 2103. https://doi.org/10.3390/buildings12122103
Zhang B, Li Y. A User Profile of Tendering and Bidding Corruption in the Construction Industry Based on SOM Clustering: A Case Study of China. Buildings. 2022; 12(12):2103. https://doi.org/10.3390/buildings12122103
Chicago/Turabian StyleZhang, Bing, and Yu Li. 2022. "A User Profile of Tendering and Bidding Corruption in the Construction Industry Based on SOM Clustering: A Case Study of China" Buildings 12, no. 12: 2103. https://doi.org/10.3390/buildings12122103
APA StyleZhang, B., & Li, Y. (2022). A User Profile of Tendering and Bidding Corruption in the Construction Industry Based on SOM Clustering: A Case Study of China. Buildings, 12(12), 2103. https://doi.org/10.3390/buildings12122103





