Abstract
The development of Industry 4.0 has accelerated the adoption of sophisticated technologies, including Digital Twins (DTs), Artificial Intelligence (AI), and cybersecurity, within Additive Manufacturing (AM). Enabling real-time monitoring, process optimization, predictive maintenance, and secure data management can redefine conventional manufacturing paradigms. Although their individual importance is increasing, a consistent understanding of how these technologies interact and collectively improve AM procedures is lacking. Focusing on the integration of digital twins (DTs), modular AI, and cybersecurity in AM, this review presents a comprehensive analysis of over 137 research publications from Scopus, Web of Science, Google Scholar, and ResearchGate. The publications are categorized into three thematic groups, followed by an analysis of key findings. Finally, the study identifies research gaps and proposes detailed recommendations along with a framework for future research. The study reveals that traditional AM processes have undergone significant transformations driven by digital threads, digital threads (DTs), and AI. However, this digitalization introduces vulnerabilities, leaving AM systems prone to cyber-physical attacks. Emerging advancements in AI, Machine Learning (ML), and Blockchain present promising solutions to mitigate these challenges. This paper is among the first to comprehensively summarize and evaluate the advancements in AM, emphasizing the integration of DTs, Modular AI, and cybersecurity strategies.
1. Introduction
The adoption of innovative technologies associated with Industry 4.0, often referred to as the fourth industrial revolution, is driving a significant shift in the manufacturing industry. One of the most significant developments from the more traditional rapid prototyping technique is metal additive manufacturing (MAM) [1,2]. For instance, the GE9X engine used in the Boeing 777X has reduced the number of components that make up a heat exchanger assembly from 300 to just one, resulting in a cheaper and more lightweight solution [3]. As this technology has developed over time, it has become abundantly evident that the phrase “rapid prototyping” does not adequately describe its capabilities. As opposed to traditional methods, MAM creates components in a layer-by-layer fashion, using materials such as metal wire or powder based on 3D designs. This process requires minimum interaction from humans [4,5]. The American Society for Testing and Materials (ASTM) and the International Standards Organization (ISO) claim that seven primary forms of MAM techniques exist. From aerospace to medicine to tools and consumer products, powder bed fusion (PBF) finds applications in many diverse sectors [6]. To create the intended shape, powder particles are heated or sintered under an energy source [7]. PBF technology may be further classified in part by the powder melting techniques they use: While electron beam melting (EBM) defines machines that employ electron beams, the two primary types of laser-based machines are selective laser melting (SLM) and selective laser sintering (SLS) [8,9]. Directed energy deposition (DED) is a typical technique for either adding or repairing material to already-existing components [10,11]. Similar to PBF, this method utilizes lasers for fusion and can operate on either wire or powder. DED differs only in that the printhead typically serves as both the feedstock and the energy source. The system names for DED machines running powder are laser metal deposition (LMD), wire arc additive manufacturing (WAAM), and electron beam additive manufacturing (EBAM), respectively [12,13].
In the scene of AM in this age of Industry 4.0, a significant shift to more modern technologies is underway. Cybersecurity [14], modular AI [15], and the digital twin (DT) [12] have evolved into essential elements that help improve the reliability and efficiency of industrial operations. Modular AI offers flexible modules tailored to specific tasks, enhancing processes and refining decision-making abilities [10,11]. As the number of networked systems continues to increase, it is more crucial than ever to implement stringent cybersecurity measures to safeguard irreplaceable intellectual property and ensure the integrity of industrial processes against cyberattacks [9,13,14]. These advances not only optimize resources but also enhance operational effectiveness, allowing organizations to create unique products unlike those of past years. Still, the adoption of these concepts raises serious challenges [15,16,17]. Moreover, DT technology enables manufacturers to create real-time virtual replicas of their physical assets, thereby facilitating proactive optimization and continuous performance monitoring [18].
Especially in industries such as aerospace, metal AM is beginning to challenge established wisdom and may change traditional manufacturing by looking at the GE9X engine [3]. This meets the high-performance criteria specified by the aviation sector while also reducing manufacturing costs and assembly times. Still, producers must apply rigorous quality assurance procedures to make sure that every item fulfills or surpasses the criteria because materials vary [19]. In addition, DT technology provides another useful tool for the toolbox by allowing producers to create virtual versions of their assets in real-time [20,21]. They might therefore demonstrate initiative in implementing changes and monitoring the situation. IoT devices and sensors enable firms to quickly enhance their operations and identify inefficiencies as they collect vital data from their industrial activities [22,23]. Notwithstanding their difficulties, mass data management projects and computing capacity are required to accurately represent these systems and integrate them with the existing IT infrastructure. Additionally, modular AI offers algorithms tailored to specific industrial needs, thereby enhancing product performance. These AI modules might explore vast amounts of data in search of trends to aid in streamlining processes [24]. By predicting when equipment is likely to break, ML enables quick repairs, thereby helping to better control manufacturing. Still, using AI presents problems [25,26] related to data privacy, the need for high-quality training data, and the possibility of algorithmic bias that could complicate judgments [27]. As manufacturing becomes increasingly networked, strong cybersecurity is crucial to protect private information and ensure that operations proceed as expected [28,29]. Businesses dependent on advanced security systems run the danger of being targets for hackers able to compromise data and disrupt operations. Organizations must continually adapt their security strategies to match the evolving nature of cyber threats, which can be financially taxing [30,31].
Although much has been accomplished in the fields of DTs, AI, and cybersecurity separately, their combined influence in changing AM, especially MAM, remains underexplored in current research. These technologies used together could unleash hitherto unrealized degrees of predictive maintenance, real-time process optimization, and system security. Most current research, however, examines these technologies separately without a consistent framework addressing their synergy, interdependencies, and implementation difficulties in industrial AM systems. Furthermore, as AM becomes more data driven and networked under Industry 4.0, new risks and operational complexities surface, necessitating comprehensive plans. This emphasizes the urgent need to synthesize the current research situation, identify technical gaps, and propose integrated solutions. Future research needs to be guided by industry best practices and supported by the creation of robust, intelligent, and safe AM systems through a targeted, multidisciplinary assessment.
This work attempts to give a comprehensive analysis of the ways in which DT, modular AI, and effective cybersecurity technologies might greatly improve AM processes in the transforming terrain of Industry 4.0. Focusing on these new technologies will allow us to investigate their synergies and cumulative impact inside industrial environments. By focusing on these new technologies, we will examine their synergies and cumulative effects within the context of industrial settings. This will help to better grasp their influences on operational efficiency, product customization, and decision making.
Furthermore, this research will examine the challenges that prevent the effective implementation of these developments and provide an understanding of how professionals in the area can overcome them. The review paper is organized into several interconnected sections, reflecting the concepts expressed in the introduction, to simplify the process of conducting this research. DT technology will be thoroughly discussed in Section 2, with its applications in manufacturing process improvement, primarily in-time performance monitoring and proactive optimization, highlighting its benefits. This part will be based on the already mentioned introduction. Modular AI will be discussed in Section 3, along with its applications in data analytics, predictive maintenance, and the enhancement of operational decision-making capabilities. Section 4 will emphasize the importance of cybersecurity techniques in safeguarding industrial processes against the growing number of cyber hazards resulting from the increasing interconnection of industries. In Section 5, the combined effect of DT, AI and cybersecurity has been discussed. Section 6 will address the challenges that prevent the application of these technologies and offer remedies to overcome them. Section 7, a summary of the most significant results, will be presented in the final part of the study, along with an outline of future research directions aimed at enhancing the robustness and efficiency of AM through the use of DTs, modular AI, and cybersecurity solutions.
2. Digital Twin Technology in Additive Manufacturing
Digital Twin (DT) technology is emerging as a key pillar for achieving several benefits in the era of Industry 4.0, as sectors such as manufacturing undergo digital transformation [1,32]. Although DT technology originated in the aerospace sector [20], where it was used to replicate and track space spacecraft, its ability to transform other sectors is becoming increasingly clear. DT provides applications spanning design, optimization, maintenance, decision making, and training; it also enables the linking of physical and virtual worlds in real time, thereby providing a more realistic and comprehensive perspective of operations [3]. DT is a great tool for improving productivity, competitiveness, and efficiency, as it allows one to replicate, track, and forecast system performance [33]. Within AM, DT technology holds great promise, as it enables the use of virtual duplicates of machinery and processes. By doing so, companies can increase productivity, minimize time to market, reduce maintenance-related costs, and enhance product quality [32,34]. As businesses have come to depend more on digital solutions for remote monitoring and maintenance, the COVID-19 pandemic has accelerated the adoption of DT in the industry [4]. Although the idea of DT is not entirely novel, it originated in early concepts of Product Lifecycle Management (PLM) and NASA’s innovative applications [5]. Its integration with advanced computing, IoT, and AI in modern manufacturing processes has unlocked a new level of operational efficiency [6,8]. DT helps precisely monitor complex production processes by creating virtual replicas of actual physical facilities in the AM, thereby enabling condition-based predictive maintenance, proactive decision making, and better product customization [35,36]. As AM advances, the impact of DT on it is expected to grow, thereby promoting creativity and altering accepted industrial patterns [37].
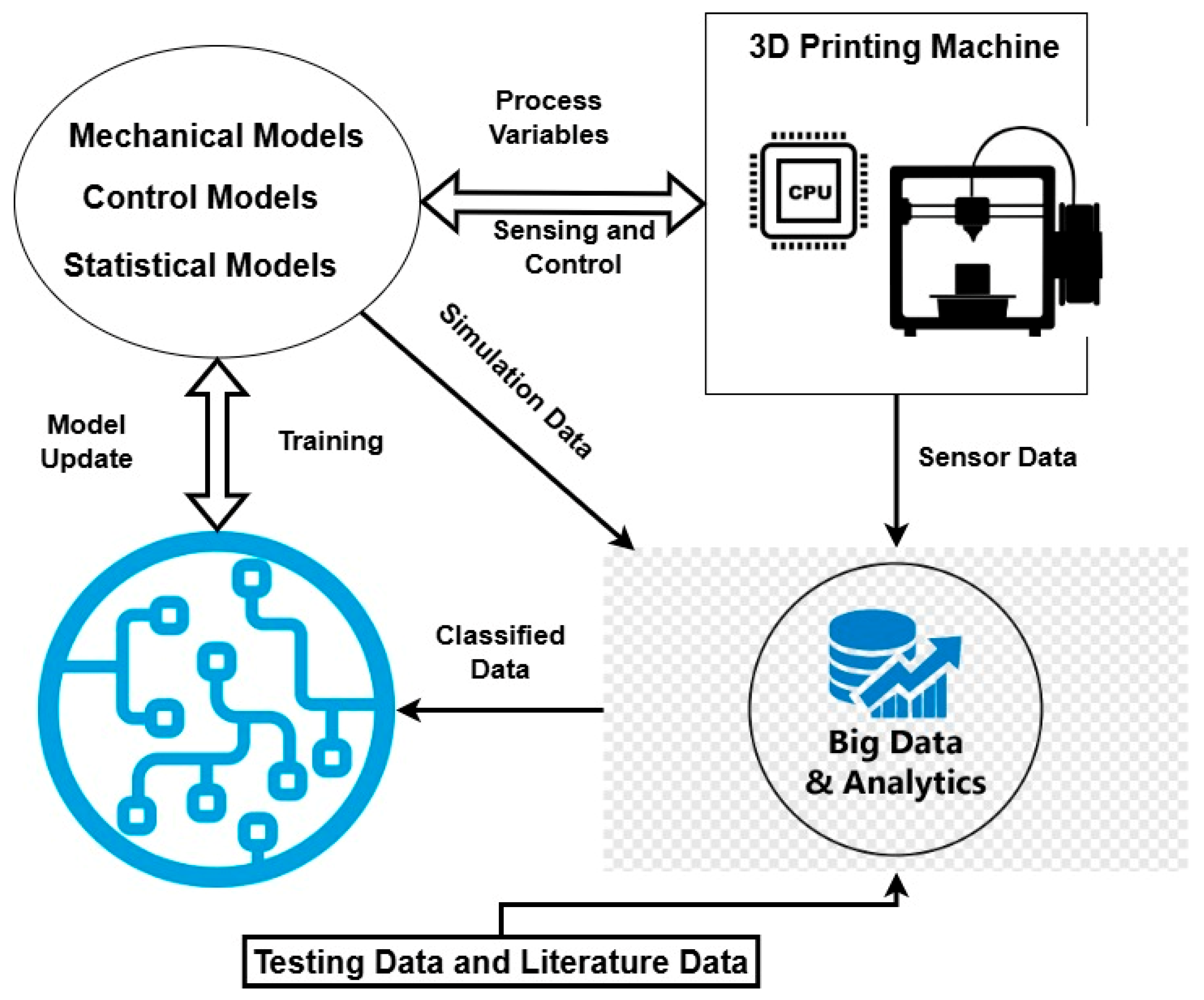
Zhang et al. [14] presented a logical overview of DTs in AM, which is illustrated in Figure 1. This model consists of mechanical models, control models, and some statistical models besides ML models and big data. This framework acts as a base for DT application in AM. Gunasegaram et al. [38] discussed a full overview of DTs by introducing real-time monitoring, predictive control, and process optimization. In addition, the authors argue that DTs, virtual replicas that communicate bidirectionally with physical systems, are particularly well suited to address AM’s inherent challenges of process chaos, variability, and high costs. While acknowledging significant challenges, including the development of robust AI, high-speed sensors, and validated multiscale models, the paper convincingly positions DTs as a transformative step toward achieving more reliable, efficient, and economically viable AM production. Stavropoulos et al. [39] propose a control-oriented DT for AM using robust controllers. It ensures precise temperature tracking and improved process stability under material uncertainties. Compared to PID controllers, this approach achieves faster response and better quality control. Various researchers used different DT frameworks in their research, and Table 1 illustrates different DT applications of AM and shows the author’s contributions with the future scope.
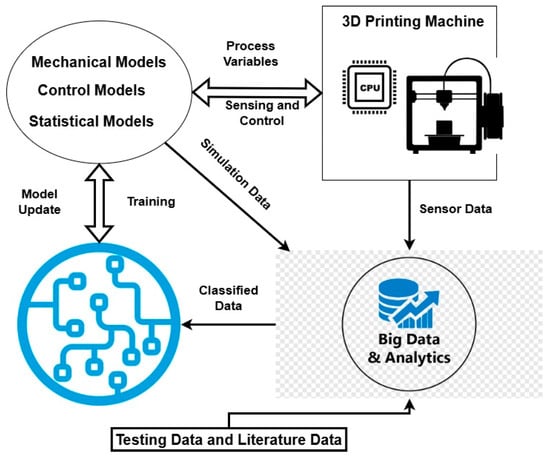
Figure 1.
General framework of DT applications in AM; based on the data [14].

Table 1.
DT current state in different AM applications.
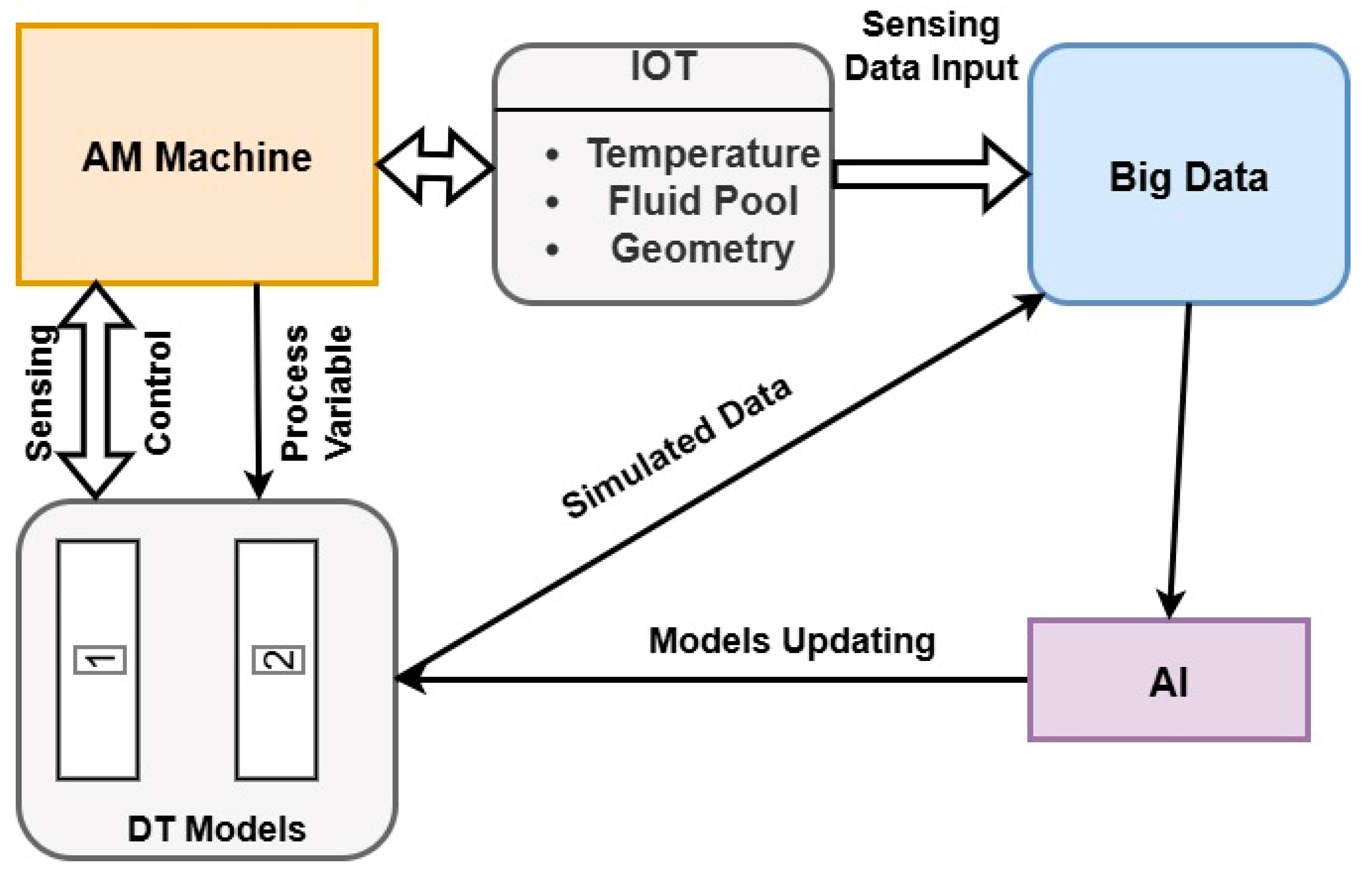
Furthermore, Phanden et al. [24] demonstrated that integrating a DT into AM requires four fundamental elements, as illustrated in Figure 2: AI, big data analytics, machine configuration based on the DT, and the DT models themselves. First, the AM equipment is painstakingly set up to account for temperature and laser power, among other factors. Furthermore, the attached sensors are used to gather real-time data. The DT models, which replicate physical processes, track geometric aspects, and assess past data to identify patterns, are fed into this data. Big data analytics helps identify anomalies in real time, thereby allowing for speedy repairs. AI algorithms help to enhance this process by allowing one to predict future issues and automatically modify operating parameters if deviations occur. This integrated approach not only improves the quality and consistency of the produced components but also ensures that the process is more efficient, thereby reducing the number of mistakes that arise and guaranteeing that the products adhere to the design criteria. Chen et al. [43] developed multi-sensor-based DT in AM for in situ quality monitoring. In this case, they used multisensory fusion to get a more complete understanding of the fundamental process of physics, such as porosity and its growth. Some examples of the sensor-captured process data included in robotic DED are coaxial melt pool images, temperature fields, audio signals, and a three-dimensional point cloud on the component surface. Typically, spatial-temporal data fusion is employed to synchronize and register multisensory features, which are the primary contributions in this discipline.
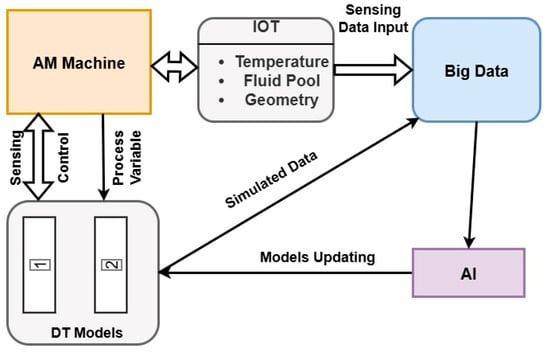
Figure 2.
Representation of DT implementation in AM; based on the data [24].
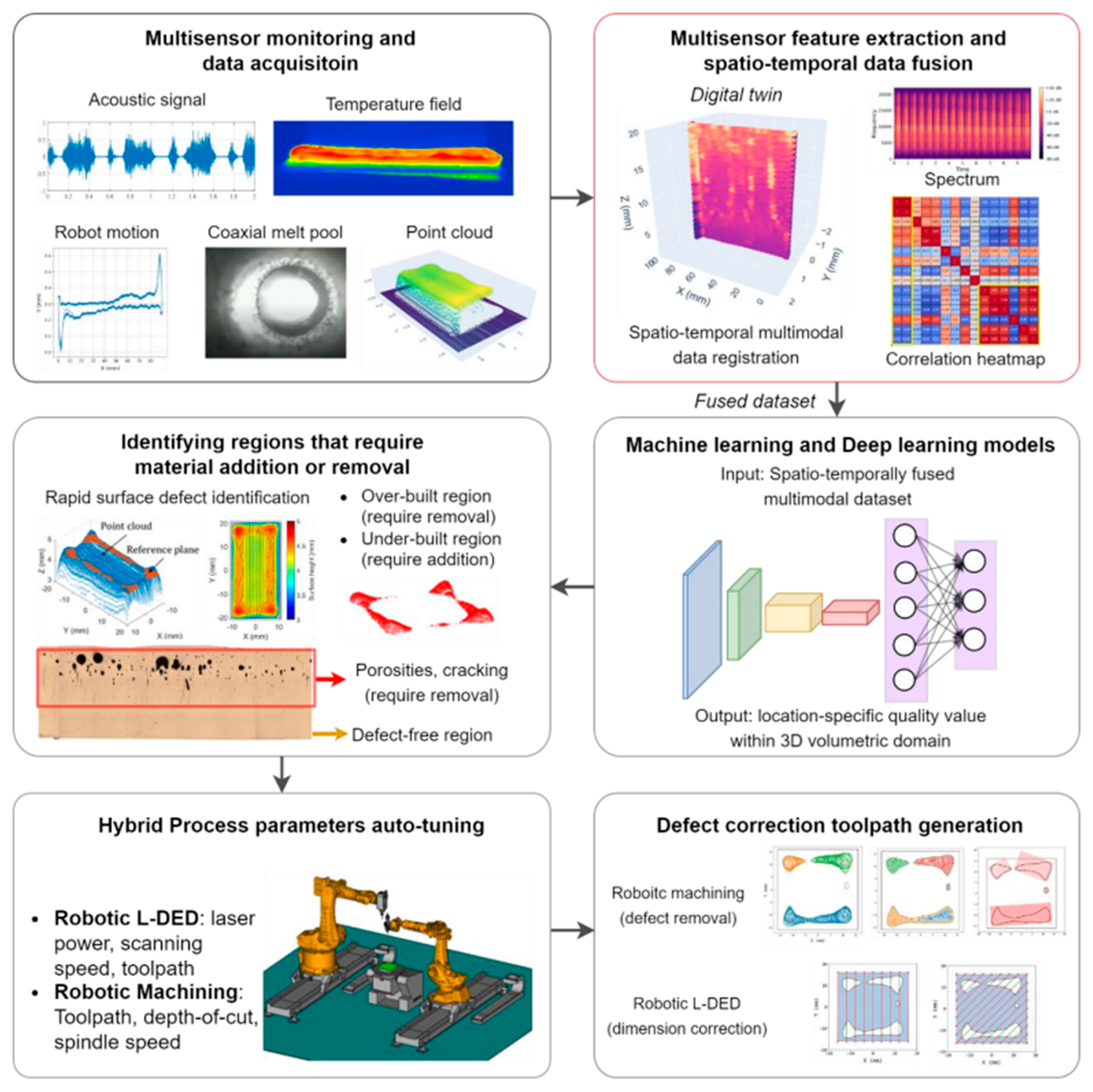
Figure 3 illustrates the entire setup procedure for using multiple sensors. After the LDED process, data from multiple sensors are fused in time and space and resampled at 250 Hz to match the robot’s position data, allowing for detailed quality mapping. Microscopy reveals distinct defects at different part layers, such as keyhole pores in upper layers and cracks in the middle, with these defect types associated with specific sensor features like melt pool width. Each sensor exhibits varying effectiveness in detecting defects, as evidenced by the omission of certain cracking signals identified by melt pool features. This fused data will support training ML models to predict defect locations within the part [43].
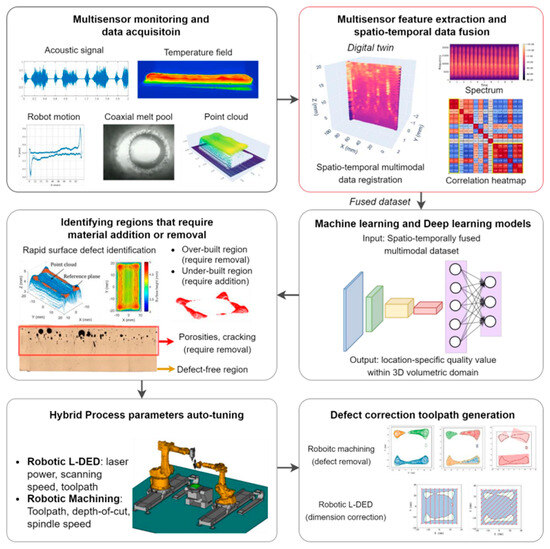
Figure 3.
Multisensory DT in robotic LDED AM for in situ quality monitoring based on the data [43].
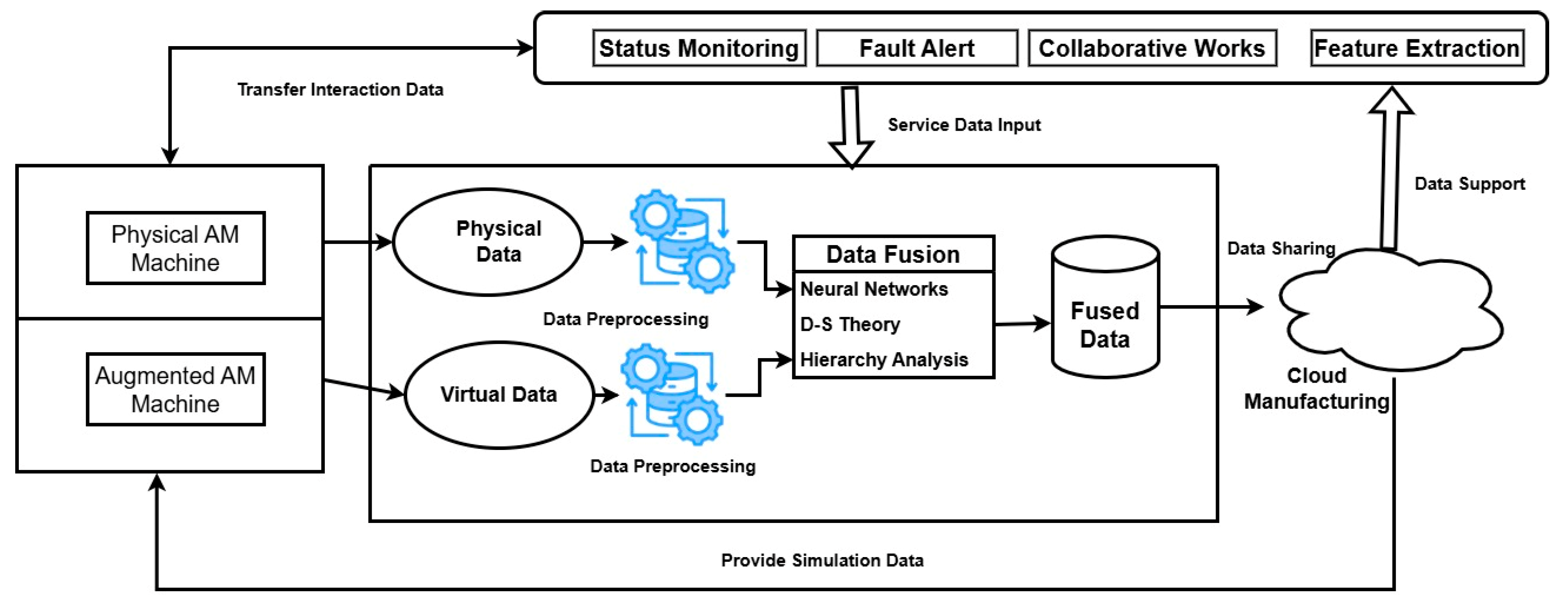
Based on a five-dimensional DT model, Xu et al. [44] proposed an Augmented Reality-assisted Cloud AM (AR-CAM) architecture that integrates actual goods, virtual replicas, data, services, and networking, as illustrated in Figure 4. Through centralizing and distributing real-time data on a Cloud Manufacturing platform, the system improves data security and resource allocation. Utilizing improved and customized products throughout several phases, this setup helps visualize various manufacturing techniques in AR. AR-CAM also promotes a shared knowledge base by facilitating prototyping and knowledge-sharing to speed product upgrades and improve demand responsiveness. For toolpath planning and simulation, Xu et al. [44] also presented an AR-based method to efficiently transfer layout information between a reconfigurable AM system with robotic arms and its DT. Using transformation matrices to establish interactions between the camera, markers, robotic arms, and substrate, a prototype system with two desktop robotic arms proved the potential of the approach to automatically recover spatial data.
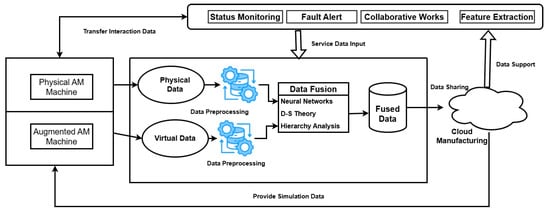
Figure 4.
The framework of augmented reality-assisted cloud AM; based on the data [44].
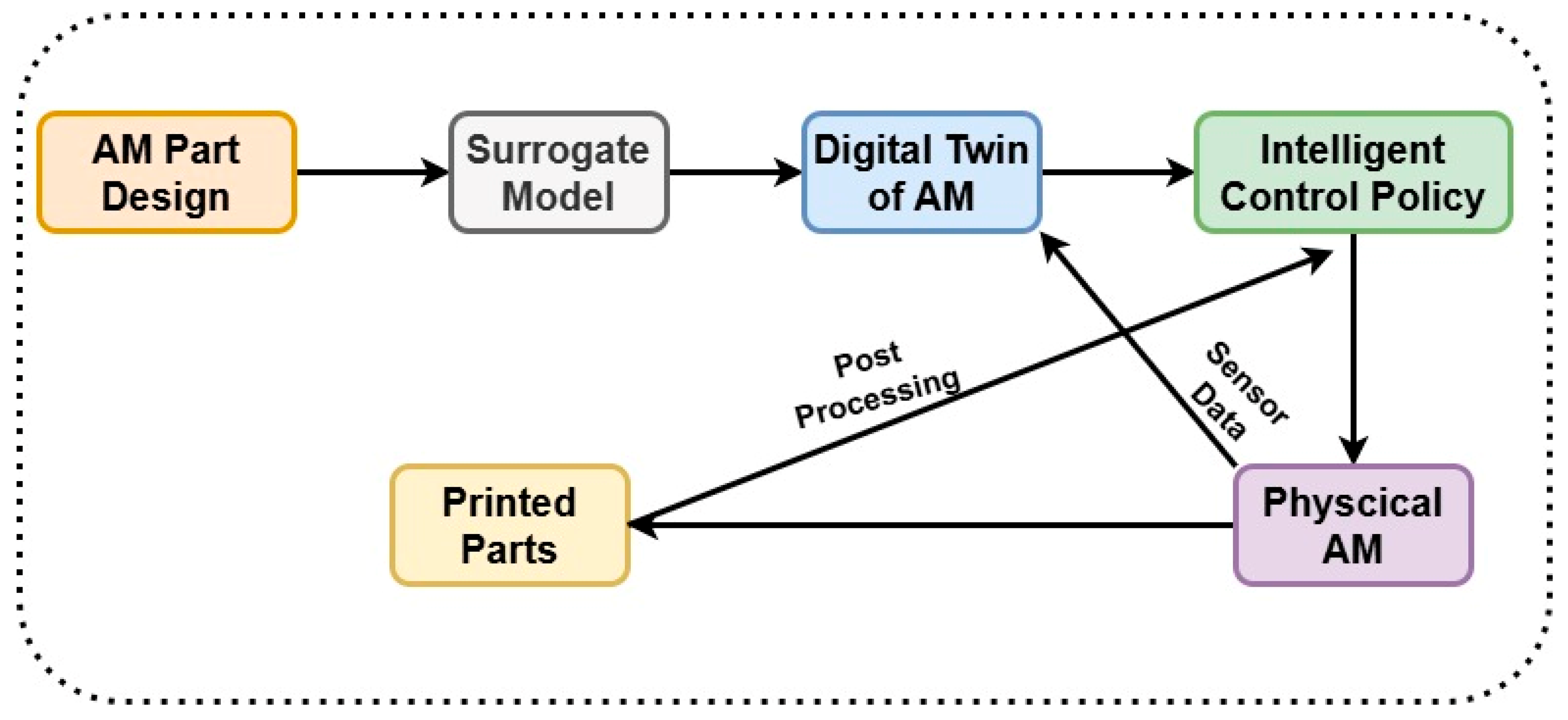
Phua et al. [28] also contributed by proposing a hierarchical framework for developing DTs specifically for metal AM, categorizing them into four levels of increasing complexity. This hierarchy consists of surrogate modeling, in situ sensing, hardware control, and intelligent control policies needed to achieve effective, real-time control of the AM process. Another issue the authors addressed was the “intelligent DT” level displayed in Figure 5, where better control rules allow independent, adaptive decision making, free from influence. Seeking to maximize print quality, defect management, and design customization, this offers a uniform platform for aggregating simulations, sensor data, and control systems. Promoting more universal scalability and integration in industrial settings, the framework also provides concepts pertinent to several AM approaches and advanced manufacturing systems.
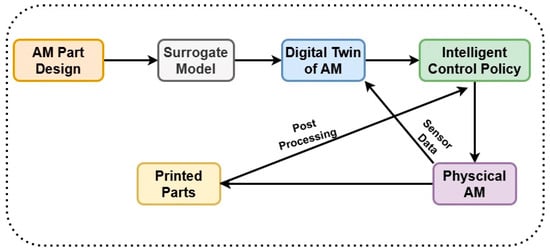
Figure 5.
Framework for the intelligent DT; based on the data [28].
DT technology has already shown clear value in real-world metal additive manufacturing applications. For example, GE Additive integrated DTs into their laser powder bed fusion (LPBF) systems to simulate thermal gradients and layer distortions in real time, and it achieved a 25% reduction in porosity-related defects and a 30% improvement in dimensional accuracy. Moreover, it also reduces post-processing efforts, resulting in annual savings of over USD 1 million per line [45]. Similarly, Siemens Energy applied DTs to optimize DED repairs for gas turbine blades, reducing distortion by 35% and shortening repair cycle times by 20%, while improving component reliability [46]. In another case, Safran used DTs in aerospace bracket production to predict geometric deviations and improve process stability, which reduced non-conformance rates by 22% and lowered post-processing times by 25%, enabling faster throughput and certification [47]. These industrial successes clearly demonstrate the practical impact and economic benefits of Digital Twin integration in advanced metal additive manufacturing environments.
In AM, DT designs can be simple or complex, with different levels of intelligence and control. Selecting an appropriate framework for an AM application requires a clear understanding of the underlying DT architectures. Figure 5 (taken from Phua et al. [28]) displays a hierarchical structure with stages for surrogate modeling, in situ sensing, hardware control, and intelligent control. Each layer adds increasingly advanced capabilities, which lets the system become more autonomous over time. But when it comes to layered systems DT implementations, they first receive data from IoT sensors, evaluate it, simulate the model, and then make decisions. These systems are modular and easy to use and are less flexible and responsive, but they do not have deep layer integration. In real-time AM workplaces where quick decisions are needed, feedback loops may not be two-way or real-time, which makes them less valuable. Cloud-based architectures, such as Xu et al.’s [44] AR-CAM’s 5D DT model, rely on remote access, sharing of resources, and working together to make things. This platform combines real-world objects, virtual models, data, services, and networking to control big systems and operate with AR. This architecture is good for production ecosystems that are spread out and for AR-enabled visualization, but it has problems with latency, data privacy, and always being connected. These problems are better solved by hierarchical or edge-computing DT models.
Chen et al. [43] suggest modular hybrid DT systems with localized decision-making units and multi-sensor fusion that use spatiotemporal data to find problems and predict quality in real time; however, it can be hard to calibrate and sync data streams. Sensor-centric models put more emphasis on detection accuracy and physical insight than Figure 5 does. Lastly, Stavropoulos et al. [39] put more importance on strong process control using advanced controllers, and these are better at keeping an eye on things and keeping things stable than typical PID schemes; however, they employ deterministic rules and do not have the ability to learn and forecast like intelligent DT frameworks do.
In short, layered and cloud-based architectures are flexible; on the other hand, sensor-centric and control-based systems are precise and stable. However, the intelligent hierarchical DT architecture may be the best solution for real-time, autonomous, and adaptive control in AM. Since it combines sensing, modeling, control, and learning, it works especially effectively in manufacturing settings that are complicated and full of data.
Based on the various literature summaries and critical comparison of DT development in AM, it has become clear that DT integration with AI has played a significant role in data management, early fault detection, in situ monitoring, and sensor data analysis. So, the next section will briefly discuss the role of AI in AM system reconfiguration and optimization.
3. Modular AI for System Reconfiguration and Optimization (AI/ML Algorithms)
AI has revolutionized AM by enhancing and ensuring the quality of production processes and products [48]. With flexible and adaptable technology and modular AI, manufacturing companies can respond quickly to evolving manufacturing needs and challenges. Within the scope of in situ process monitoring, material and process optimization, workflow automation, and real-time decision making, AI is a highly valuable technology [48,49,50]. AI models, for example, can dynamically adjust machine parameters while the machine is running [51], assess sensor data to identify flaws or anomalies, optimize resource usage to minimize waste, and autonomously perform industrial processes. This adaptability also drives predictive maintenance by enabling the analysis of machine data to identify problems, thereby saving downtime and extending equipment lifetime [52,53].
Data collection, AI model building, dynamic algorithms, and feedback systems collectively ensure efficient manufacturing through modular AI-driven optimization frameworks [54]. Real-time preprocessing of sensor data for training ML models maximizes process parameters, including laser power, layer thickness, and printing speed [55,56]. These models change over time using feedback loops, which also contribute to making production even more dependable. Modular AI systems increase versatility by easily adapting for different materials, setups, or production goals. Tools including DTs, cloud computing, and edge computing further help AI-driven optimization by providing simulations, large-scale data processing, and low-latency decision making.
AI-powered automation has streamlined AM processes, increased productivity, and enabled innovative ideas to flourish [57]. For example, AI-driven vision systems can detect manufacturing defects, thereby saving inspection time and improving standards. Dynamic process reconfiguration enables systems to adjust parameters in real time, depending on ambient conditions or material properties. Likewise, mass customization driven by AI enables the scalable production of tailored components without compromising manufacturing efficiency. Table 2 depicts the different AI models used in AM development.

Table 2.
AI model contribution in the development of AM.
While discussing with DTs and AI in AM, it means that it opens the opportunity to utilize cyberspace for better PLM in AM. However, the management of cyberspace is important, as it integrates lots of digital threads, sensors, and networks.
Renken et al. [67] used a closed-loop control system to keep the temperature of the melt pool steady in an LPBF configuration, and they were able to reduce temperature changes by up to 50% compared to open-loop control systems. Similarly, Chen et al. [68] used thermal imaging, artificial neural networks, and powder layer monitoring to aggregate data from different sensors. As a result, this design reduced the average departure from the planned shape by around 40% and this allowed the configuration of the process to be adjusted in real time. The results show that adding smart sensing and control to modular AI systems makes parts more accurate and cuts down on mistakes. There will be less work to perform after the incident, and manufacturing will be more dependable. The next chapter will discuss cybersecurity, considering different cyber attacks in AM and possible solutions.
4. Cyber Security in Additive Manufacturing
A Cyber Manufacturing System envisions fully integrated physical and computational processes in a connected manufacturing ecosystem. By leveraging IoT [69], cloud computing [70], ML [71,72], sensor networks and ML application at advanced manufacturing [73,74], these systems enable smart capabilities like self-awareness, self-prediction, and self-organization, fostering a responsive and adaptive production environment [74,75]. In this context, AM significantly expands design flexibility, supporting complex geometries that conventional methods cannot achieve [76,77]. Cyber-enabled AM platforms further enhance capabilities through rapid communication, iterative design updates, and remote information sharing on setup and processing parameters [77,78]. However, this interconnectedness also heightens the risk of cyber-physical attacks [79,80,81], presenting critical security challenges in the deployment of cyber-physical AM systems [82]. This section covers research articles on cyber-physical attacks in manufacturing, covering incident investigations and research studies. Intrusion detection approaches are examined across the cyber-physical manufacturing domains. Additionally, physical detection methods that use side-channel data—such as acoustic signals, imagery, and acceleration—to detect attacks during manufacturing processes are discussed.
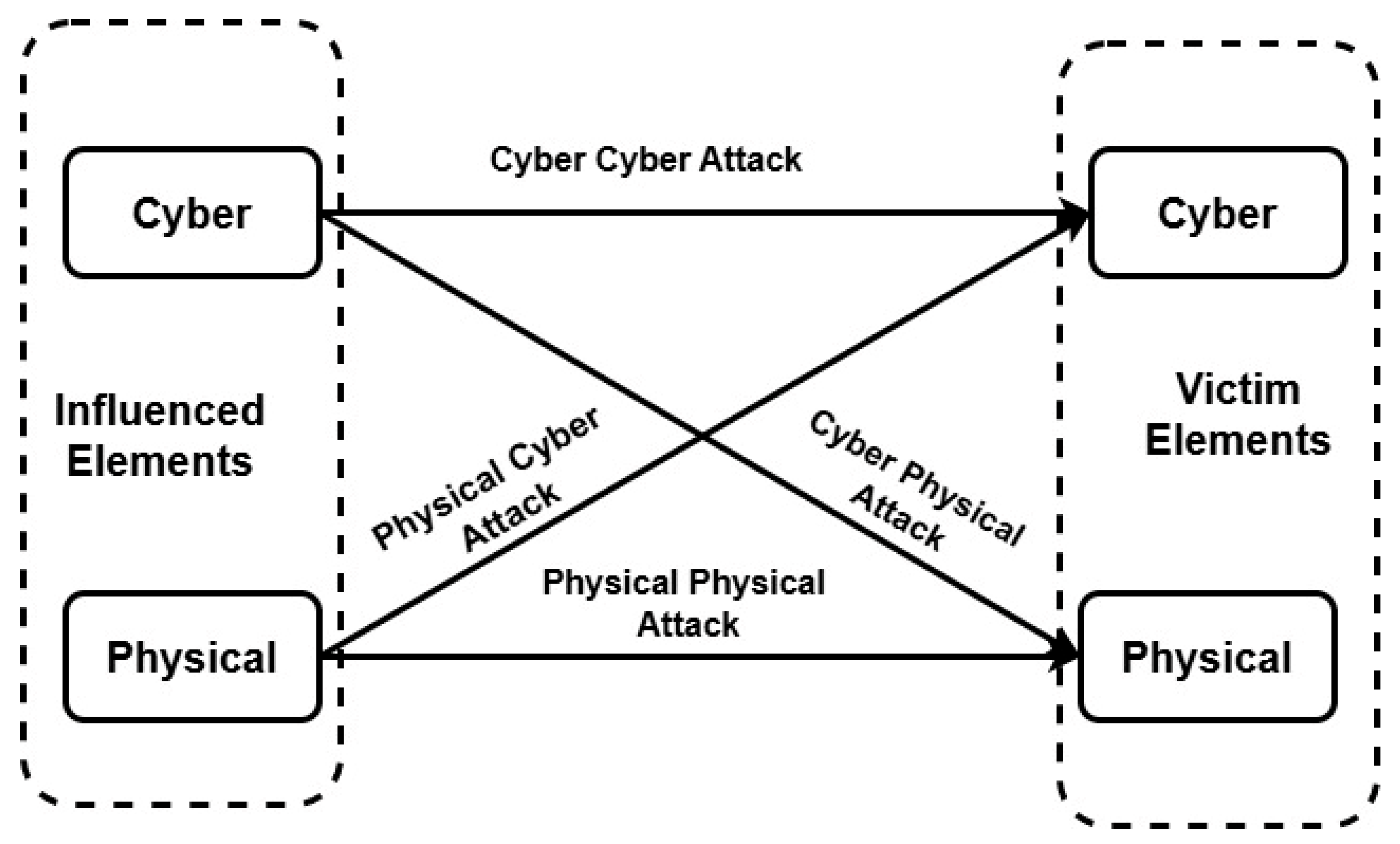
Figure 6 illustrates a taxonomy of attacks in cyber manufacturing systems based on the data [83,84,85,86,87]. The influenced area represents where attacks originate or target first. In the cyber domain, attacks can compromise servers, files such as STL and G-code (used in 3D printing), cloud-based manufacturing systems, and wireless sensor networks. In the physical domain, attacks could affect raw materials, parts, assemblies, equipment, and machines, as well as the power supply needed for operations. Victim elements represent areas impacted by the attacks, either directly or indirectly due to compromised influenced elements. In the cyber domain, attacks compromise sensor data, ML processes, intellectual property, and real-time simulation capabilities. In the physical domain, the impacts extend to final products, human safety, the functioning of equipment and machinery, and customer satisfaction and loyalty. Table 3 illustrates major attacks classification, sub-classification, and existing remedy.
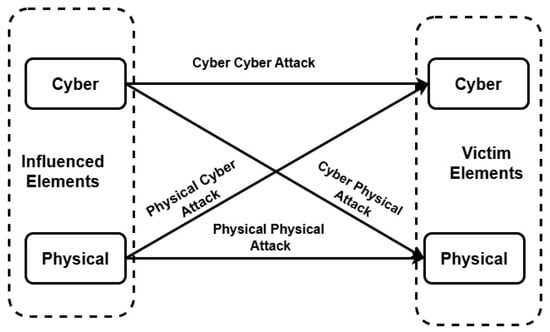
Figure 6.
Taxonomy of attacks in cyber manufacturing systems based on the data [83,84,85,86,87].

Table 3.
Major attacks classification and existing solutions.
Table 4 summarizes the various types of cyber-attacks in AM and the possible solutions authors experimented with in their studies.

Table 4.
Cyber-physical attack in AM.
Wu et al. [84] demonstrated a vision-based security mechanism in a 3D printing setup to detect and alert administrators of potential defects in real time. Five different infill defect patterns were designed: seam, irregular polygon, circle, rectangle, and triangle to simulate attacks. The proposed framework uses supervised ML to help detect the attack more accurately and speedily. The entire process, from image capture, syncing, downloading, feature extraction, classification, and alert generation, took around 1 min, although network conditions may affect this timing. Anomaly detection has been found to be a more accurate method among RNNs, Random Forest, and anomaly detection. The accuracy of anomaly detection is 96.6%.
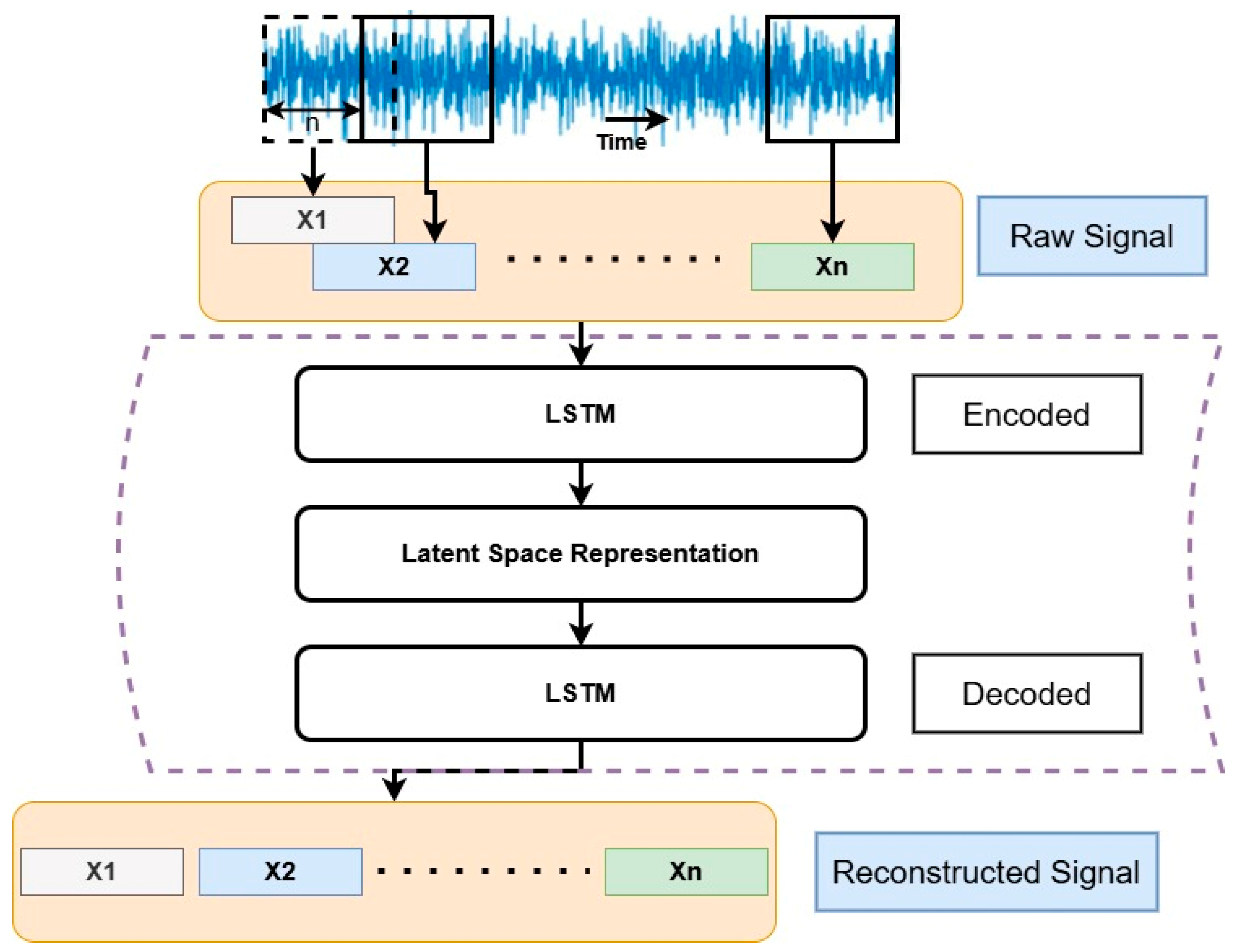
Shi et al. [95] discussed the limitations of current monitoring methods, which focus on process anomalies such as material flow or overheating but often miss cyber-physical attack-induced alterations. Different key challenges have been found, including difficulty measuring certain process attributes, the complexity of AM physics, and the vast, unpredictable range of possible process alterations. This work presents a feature extraction method based on LSTM-autoencoder to efficiently capture the attack-induced changes in online collected sensor signals; its suggested framework is shown in Figure 7.
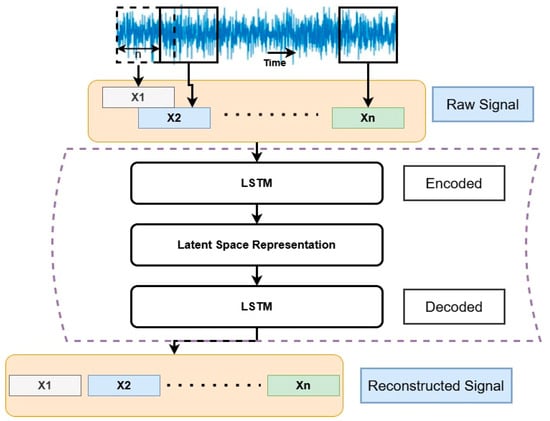
Figure 7.
Proposed framework for feature extraction approach; based on the data [95].
Two potential cyber-physical attack scenarios were investigated to validate the monitoring approach, with design parameters:
Case 1: Attack on the design geometry in the “STL” stage aimed at adding a little square-shaped void in the construction. In 1 to 41 layers kept solid, but 42–67 layers had a square hole inside.
Case 2: During the “slicing” stage, the layer thickness was taken into consideration to modify the thickness of particular layers. In case 02, layers 1–40, 41–56, and 57–67 were 0.3 mm, 0.25 mm, and 0.35 mm thick, respectively.
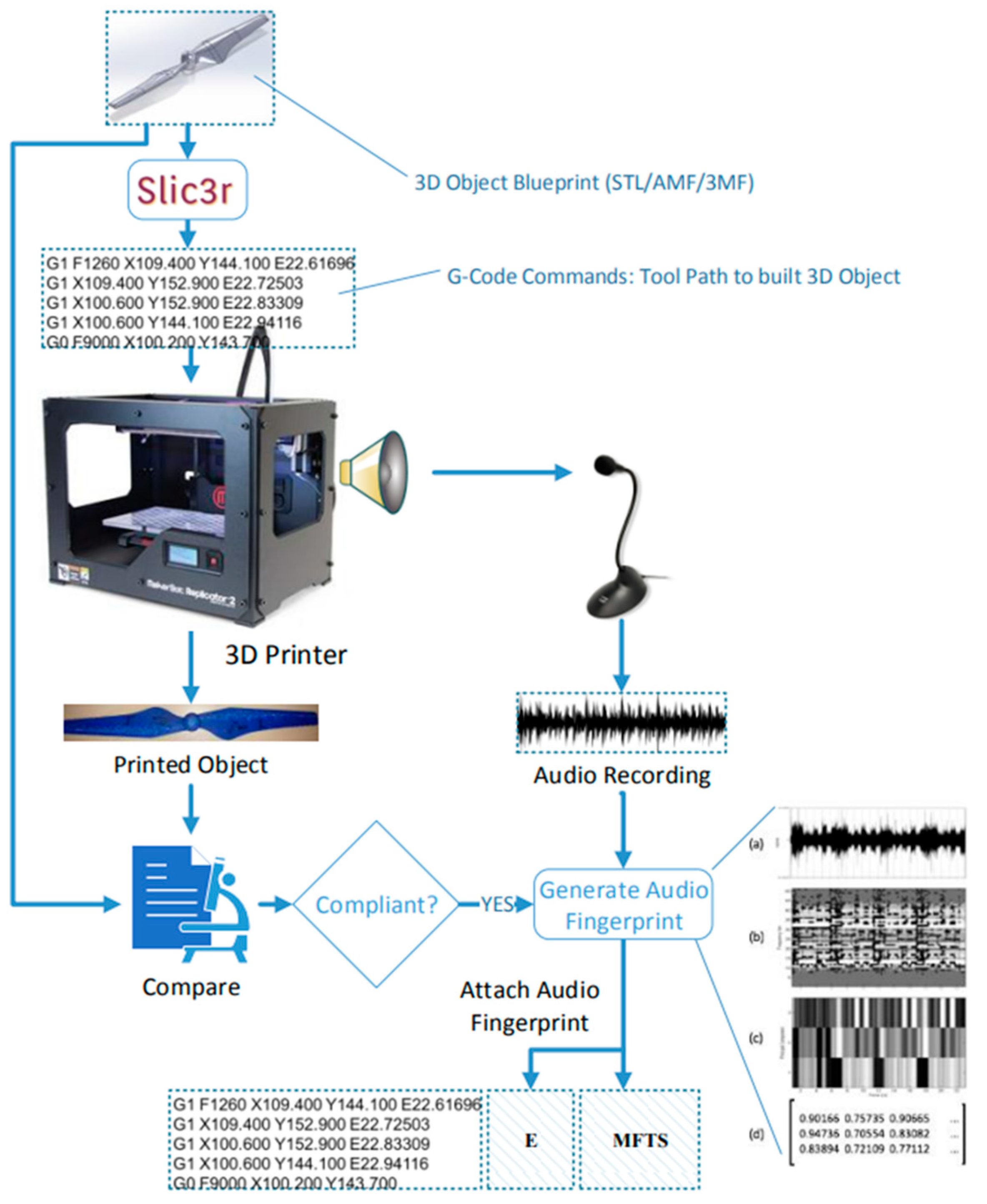
After capturing data and data extraction, they implemented both unsupervised and supervised monitoring approaches for online cyber-physical attack detection. Among different algorithms, both case 01 and LSTM-AE + AdaBoost showed a higher score in precision, recall, and F-score that is 0.9479, 0.9460, and 0.9469, respectively, for case 01 and 0.9477, 0.9790, and 0.9631, respectively. Moreover, they also proposed LSTM-AE + OCSVM-EWMA for unsupervised monitoring. Sofia Belikovetsky et al. [97] concentrated exclusively on sabotage attacks, proposing a detection method using side-channel audio verification to enhance AM security against cyber-physical threats, as shown in Figure 8. They proposed a detection method whose workflow is:
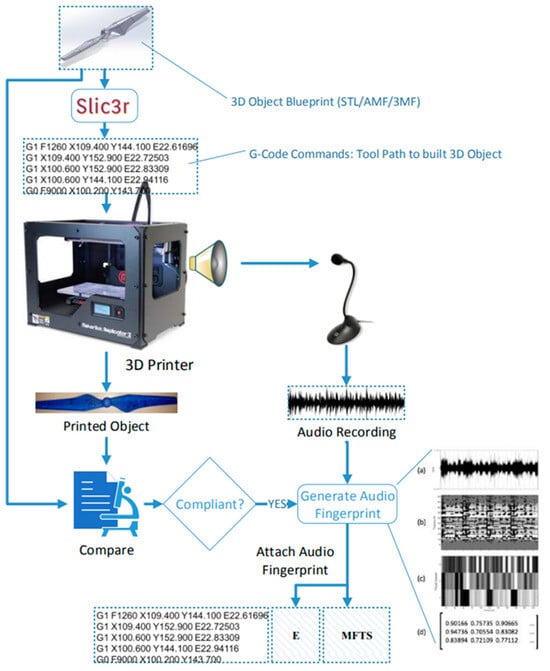
Figure 8.
Overview of audio fingerprint generation; based on [96] (a) row signal (b) spectrum after FFT running (c) gray scale representation (d) numeric presentation.
- STL or G-code file of the object produced in a lab environment.
- The audio signal was recorded during manufacturing.
- The audio fingerprint was calculated, encrypted, and appended to the G-code file.
Then, they compared the sound generated during the new manufacturing process to the signed audio fingerprint to verify the object’s authenticity.
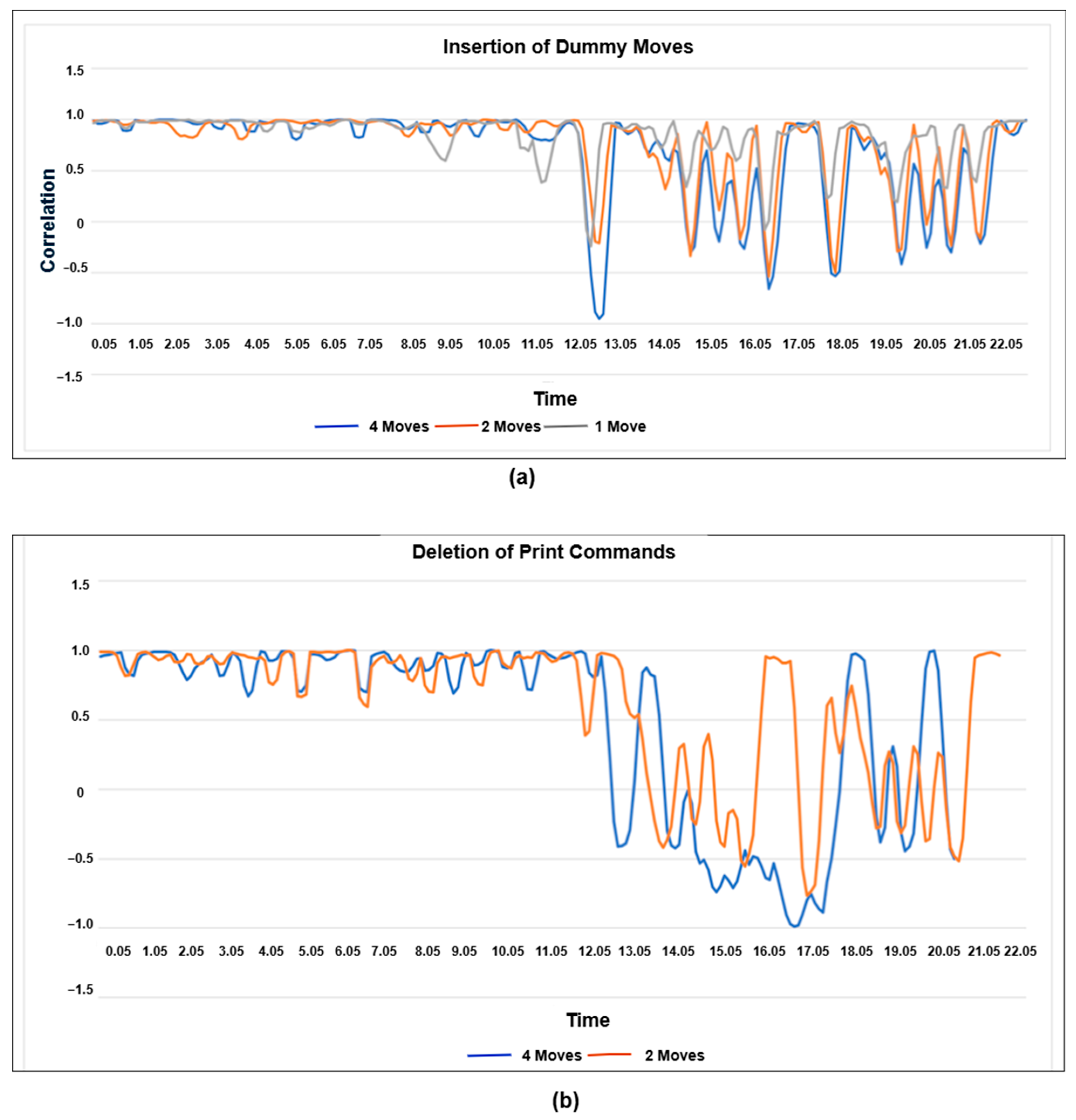
To test these limits, they evaluated various G-code alterations, including inserting extra G-code, deleting benign G-code, modifying individual movement parameters, changing the extruder speed, and reordering G-code commands. The results are summarized below in Figure 9.
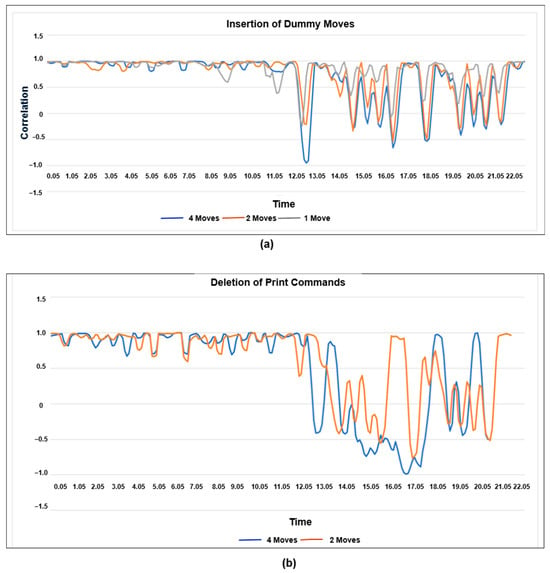
Figure 9.
Audio comparison by (a) original cube vs three different cubes (b) original cube vs two different cubes deletion of G1 code; based on the data [96].
Yu et al. [97] discussed the research challenges of designing such a defense system, including (1) accurate modeling and estimation of the status of the AM machine utilizing side-channel information to help one distinguish between ordinary operational faults with tolerances and intrusions and attacks; (2) at the core of this work is the construction of an accurate detection system capable of spotting intrusions and attacks occurring at several phases in the AM digital production chain while following the limits of low-cost sensors; and (3) designing the system to be non-intrusive such that it can be implemented with current AM systems. The authors demonstrated vulnerability in critical components, namely gear and wrench, emphasizing the need for robust detection systems to prevent structural failures. The proposed system continuously monitored analog side-channel emissions (O) and compared them to inferred control signals (Y) derived from the AM system. The system used supervised ML to establish estimation functions based on the benchmark printer’s analog emissions and control signals derived from G-code. Various sensors (current, electromagnetic, vibration, and acoustic) have been utilized to gather emissions, and the system compared real control signals against those estimated by the system. In addition, the system compared real control signals against those estimated by the system.
Zeltmann et al. [94] examined two cyber-physical attack strategies targeting 3D printing: embedding internal defects within printed structures and altering the orientation during the printing process. These manipulations can compromise structural integrity, leading to weakened products with reduced strength and lower failure strain. Zeltmann’s findings indicate that these attacks introduce defects in different locations than those identified by Sturm [92], suggesting variation in attack methodologies and effects on printed components. Moreover, the study revealed that ultrasonic detection, a common non-destructive evaluation technique, struggled to identify both types of alterations effectively. This limitation underscores a significant security vulnerability, as undetected embedded defects and orientation changes could degrade performance in critical applications, potentially leading to premature failure in high-stakes fields such as aerospace, automotive, and medical devices.
Wu and Moon [98] demonstrated a complete cyber-physical attack chain within a manufacturing environment, tracing the process from an initial cyber intrusion to the physical destruction of the target system. In this study, the attack was designed to weaken a 3D-printed drone propeller by subtly altering its structural integrity, ultimately reducing the component’s fatigue life. As a result, the compromised propeller failed during flight, underscoring the real-world risks associated with cyber-physical vulnerabilities in manufacturing systems. The findings underscore the potential dangers of cyber-attacks in environments reliant on AM, where even minor digital alterations can lead to significant mechanical failures. This case illustrates how cyber-physical attacks pose tangible threats, particularly in fields that require high reliability, such as aerospace and defense, where compromised components can lead to operational hazards and safety risks.
Above all the scenario considerations, cyberspace is now vulnerable, and many researchers have proposed various solutions based on different attack scenarios. In the next section, we will discuss the synergistic integration regarding DTs, including AI integration with cybersecurity considerations.
5. Synergistic Integration of Digital Twins, AI, and Cybersecurity in Additive Manufacturing
While Digital Twins (DT), Artificial Intelligence (AI), and Cybersecurity have each demonstrated substantial individual contributions to Additive Manufacturing (AM), their true transformative potential lies in a synergistic, integrated deployment. Recent studies emphasize that a combined approach not only enhances process optimization but also fortifies AM systems against emerging cyber-physical threats, enabling fully autonomous and resilient production environments. Sajadieh and Noh [99] highlighted the progression from simulation to autonomy through the integration of AI with DTs. Alfaro-Viquez et al. [100] explored the role of AI-based DTs across operator, product, and process layers, emphasizing holistic optimization. In addition, Abdoune et al. [101] investigated AI’s impact throughout the lifecycle of industrial DTs, focusing on operational efficiency and adaptability. Meanwhile, Hossain and Molla [102] proposed a theoretical framework for integrating additive and subtractive manufacturing processes, laying groundwork for resilient and intelligent AM systems.
5.1. Feedback-Driven Predictive Optimization
DT and AI work together to move AM systems from making repairs after the fact to making improvements in real time. The DT continually mimics the physical AM process in this synergistic method, gathering a wide range of multi-physics data streams, such as temperature gradients, melt pool dynamics, solidification patterns, residual stress development, and geometric distortions. This high-fidelity virtual model gives operators and automated controllers a far better idea of how the system will behave than standard monitoring does.
AI models, especially deep learning (DL) architectures like Convolutional Neural Networks (CNNs) and Long Short-Term Memory (LSTM) networks, have been used to look at these huge data sets in real time. These models learn from past builds and simulated DT events to find small signs of faults, such as early delamination, porosity development, balling, or distortion between layers. The AI may suggest or carry out immediate remedial steps (such as changing the scan approach, increasing the laser strength, or changing the hatch spacing) as soon as it sees these patterns. This stops faults from getting worse before they do. Also, Physics-Informed Neural Networks (PINNs) are getting a lot of interest in putting controlling physical rules (including heat transport and solidification kinetics) into AI models. These mixed methods make forecasts easier to understand and make sure that suggestions stay physically possible, which is very important for important uses in aerospace and biomedical AM components [99,101].
Recent pilot tests in industry have demonstrated good results. For instance, in an LPBF system that makes high-stress aerospace brackets, combining a DT with an LSTM-based AI module led to a 27% drop in rejections due to porosity and a 32% drop in construction failures over a six-month trial [103]. Another study on DED for fixing turbine blades showed that feedback-driven optimization cut the average deviation from the design geometry by up to 40%, which made the overall dimensional accuracy better and cut down on the time needed for post-processing [68]. It is important to note that this feedback loop is not one-way; it goes around and around and strengthens itself. The DT gets information from in situ sensors, including coaxial cameras, pyrometers, and acoustic emission sensors. It then updates its simulations all the time. The AI then uses both simulated and real data to make its predictions and changes better, which means it learns and gets better over time. This closed-loop method is an example of “self-learning manufacturing systems,” which provide systems more independence and strength.
In short, the combination of DT and AI makes a living, learning manufacturing ecosystem that can not only respond to problems but also stop them from happening in the first place. This leads to better products, less waste, and better use of resources. This capacity fits well with the goals of Industry 4.0, which is to move toward additive manufacturing systems that are completely autonomous, durable, and cost-effective.
5.2. Adaptive Cybersecurity Through AI-Enhanced Monitoring
Combining DT and AI not only helps optimize manufacturing processes but also introduces a powerful new way to protect AM systems from cyber threats. Moreover, traditional cybersecurity approaches rely on static rule sets or simple signature matching and are no longer enough to keep up with increasingly sophisticated attacks. In contrast, the integration of DT and AI allows manufacturers to move toward intelligent, proactive, and adaptive security measures.
In this approach, AI models continuously analyze the real-time data streams generated by the DT. This includes information on temperature distributions, melt pool behavior, scan patterns, and machine status. These AI models can quickly figure out even subtle deviations, like a cyber-attack manipulating process parameters that may indicate something is wrong. A major strength of this approach is the ability to test different attack scenarios virtually. Manufacturers can simulate potential intrusions, for example, changes in laser path strategies or layer thickness inside the DT, without any physical risk. This “safe testing ground” helps AI models learn how to recognize and respond to attacks before they ever happen on the shop floor. In practice, this capability has shown impressive results. For instance, Alfaro-Viquez et al. [100] demonstrated that AI-enhanced DT systems achieved more than 95% accuracy in detecting cyber intrusions, while also significantly reducing false alarms in metal AM settings. Other studies on laser powder bed fusion LPBF processes have reported that integrated DT-AI frameworks can detect unauthorized code changes within seconds that enable corrective actions without having to stop production. For example, Hossain and Uddin [104] discussed how DTs in AM can support real-time monitoring and anomaly detection, and Azambuja et al. [105] presented intrusion detection for manufacturing systems with a comprehensive survey of AI-driven cybersecurity applications in Industry 4.0. Moreover, Sarker et al. [106] highlighted fast threat identification and response in enhancing trust and automation within DT-enabled cybersecurity systems.
An equally important advantage is the system’s ability to respond in real time. When an anomaly is detected, AI algorithms can automatically adjust process parameters, and this adaptive capability ensures that the production can continue safely with no big damage. In addition, these systems act as “self-defending” manufacturing environments that do not just detect problems but actively correct them. Adding blockchain technology to this setup takes security and transparency a step further. Blockchain creates an unchangeable record of all process data, decisions made by the AI, simulation results from the DT, and any detected anomalies [107]. This ensures that every action is documented and verifiable, which is particularly important in industries like aerospace and medical device manufacturing, where traceability and certification are critical.
In short, using AI-enhanced DT monitoring transforms cybersecurity in additive manufacturing from a static, reactive task into a dynamic, proactive, and intelligent strategy. It allows manufacturers to maintain high production quality and safety, even as cyber threats continue to evolve. In the next section, we will discuss the current challenges regarding DTs, including AI integration with cybersecurity considerations.
6. Challenges and Possible Solutions
A transformation, including DTs, AI, and cybersecurity, into AM systems creates numerous challenges as well. Solving these problems will help us fully realize the advantages that contemporary technology has to offer.
6.1. Cybersecurity Vulnerabilities
AM systems are particularly prone to cyber-physical attacks since their components—digital and physical ones connected—are vulnerable. Targeting key components, such as STL files, G-code, cloud networks, and AI models, will help mitigate operational downtime, ensure product integrity, and address safety concerns. Although intrusion detection systems are experiencing advancements, identifying minute, process-level changes resulting from attackers remains challenging.
6.2. Possible Solutions
- Shi et al. [95] proposed using side-channel data—such as acoustic signals and vibrations—in combination with AI-based anomaly detection to increase the accuracy of attack detection and hence support real-time monitoring operations.
- Blockchain technology is recommended for inclusion to create unalterable audit trails for important design files, including STL and G-code. Blockchain technology’s distributed ledger enables the verification of manufacturing operations’ legality by preventing unauthorized access and ensuring the authenticity of files throughout the production process [108,109].
- Developing advanced encryption techniques in conjunction with blockchain technology will help ensure the security of the transport and storage of design files and sensitive data.
6.2.1. AI-Driven System Reliability
AI models might not function accurately if they are not trained or validated on a range of high-quality datasets. Overstocking AI could lead to errors, especially in cases when input data or feedback loops are defective. The possible solutions are:
- Regularly updating AI models with real-world data helps increase the accuracy of forecasts and flexibility in adapting to changing AM conditions.
- Using blockchain-based smart contracts can help AI become more dependable, as these contracts can automate model modifications and validate the integrity of training data. Haw et al. [110] and Westphal et al. [111] introduced a foundation of blockchain with a blockchain-based quality management system that ensures data traceability in AM. Lupi et al. [112] proposed a shared manufacturing approach leveraging blockchain for decentralized production validation. Additionally, Alkhader et al. [113] demonstrated a comprehensive framework for blockchain-enabled traceability and management in AM that reinforces the trustworthiness of AI-driven process improvements.
6.2.2. The Challenge in Combining Physical and Digital Systems
To achieve seamless integration between physical production systems, data transmission systems (DTs), sensors, and AI frameworks, precise calibration is required. The intricacy of this process stems from changes in the material’s properties, variations in the surroundings, and equipment limitations. The possible solutions are:
- Wang et al. [59] have proposed the application of modular AI frameworks that can adjust to unexpected environments, including material discrepancies.
- Traceability solutions by blockchain technology can closely track the whole production process, and this guarantees that the data obtained from sensors, DTs, and AI models is preserved in a safe manner and can be validated, therefore helping with system synchronization and the resolution of any potential errors [114,115,116,117,118,119].
- Edge computing can enable rapid changes within AM processes and facilitate real-time data processing, thereby helping to minimize the number of delays generated by centralized technology [120,121].
6.2.3. High Costs and Resource Requirements
Implementing deep learning systems, AI systems, and robust cybersecurity measures requires substantial computational resources and significant financial investment. Regarding small and medium-sized companies eager to use innovative AM technologies, these limitations create significant challenges [122,123]. The possible solutions are:
- Use cloud-based systems to lower starting costs and enable less privileged people to access highly performing technologies. Simeone et al. [124] focused on improving resource efficiency in additive manufacturing services via introducing a smart cloud manufacturing platform. Later on, Rahman et al. [125] proposed a cloud-based cyber-physical system that provides advanced manufacturing capabilities. Furthermore, Haghnegahdar et al. [126] highlighted the critical role of industrial IoT-based cloud approaches in democratizing intelligent additive manufacturing.
- Promote the creation of blockchain-based cooperative networks that enable small and medium-sized businesses to exchange resources and access verified manufacturing data, thereby reducing the cost of individual investments. Shared additive manufacturing model [112], blockchain integration with supply chain [119], and cognitive analytics framework [127] contribute to sustainability and resilience in e-commerce-driven additive manufacturing supply chains.
- Encouragement of open-source projects and industrial partnerships helps enable the distribution of resources, accelerate development, and lower total costs for stakeholders [128,129].
6.3. Shortcomings and Proposed Framework
The increasing challenge of high-quality, traceable, and self-sufficient manufacturing in significant industries such as aerospace, biomedical, and defense has prompted AM to move ahead of traditional layer-by-layer fabrication. Developing challenges involving lack of process comprehensibility, sensitivity to defects, IP theft, and system-level inflexibility now demand the integration of advanced digital technologies. In response, we propose a comprehensive framework that combines Blockchain, Artificial Intelligence (AI), and Digital Twin technologies into an interactive ecosystem designed to advance the intelligence, security, and self-sufficiency of AM processes.
6.3.1. Framework Overview and Architecture
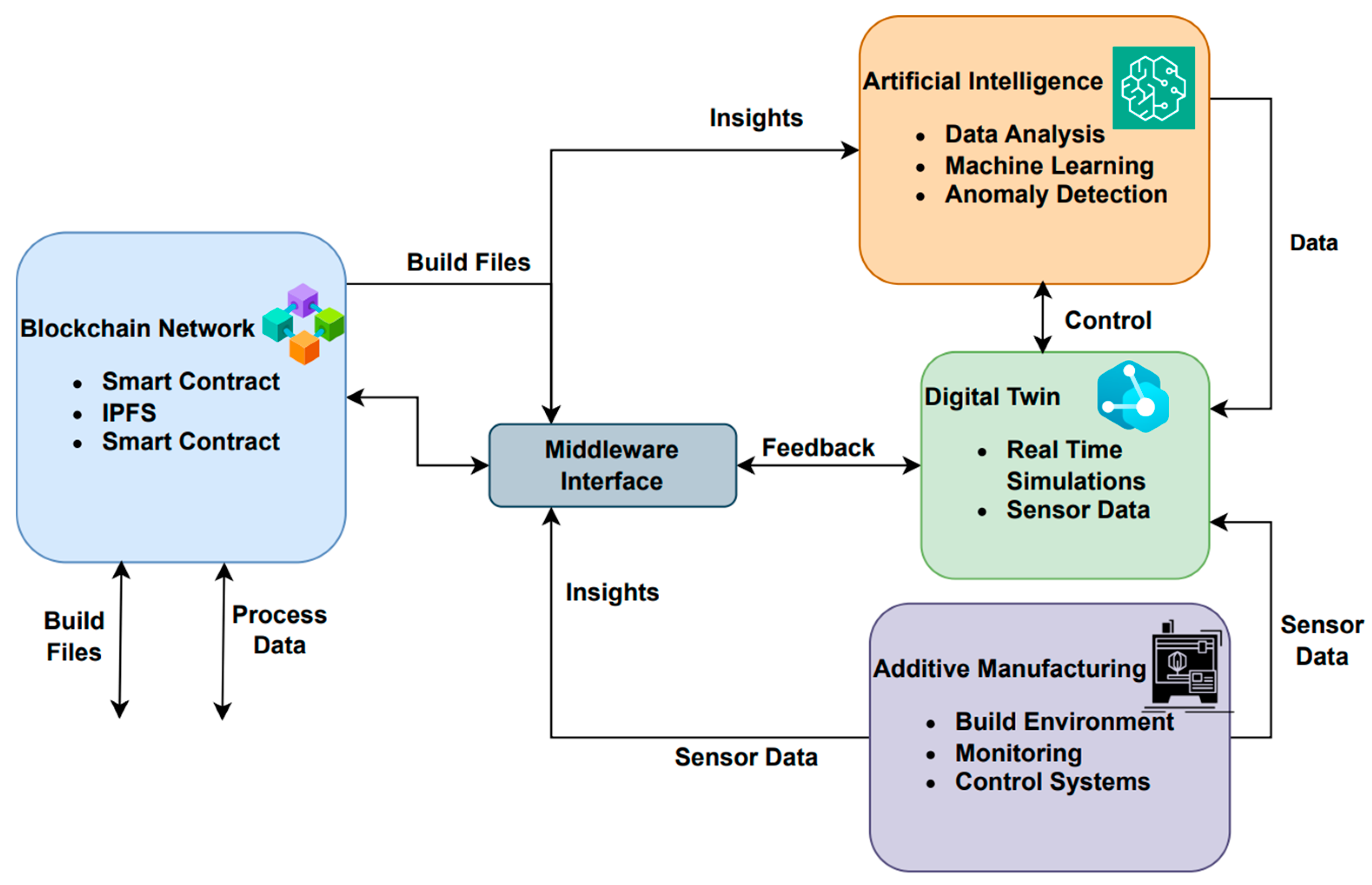
Figure 10 demonstrates the architecture of the proposed framework. The system is comprised of four core components: (i) a high-reliability digital twin module, (ii) an AI-driven analytics and controller engine, (iii) a blockchain-based distributed network, and (iv) a transposition middleware that permits real-time synchronization and data integrity across subsystems. These components mutually form a closed-loop, intelligent AM self-control system capable of predictive optimization, secure traceability, and combined decision making.
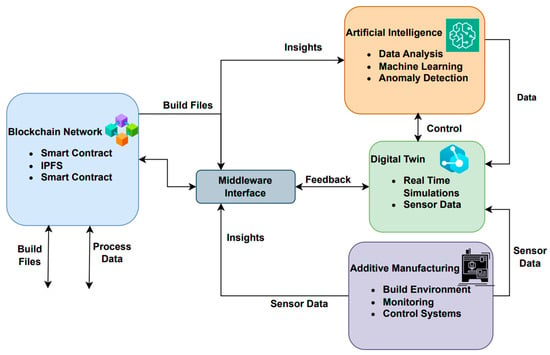
Figure 10.
Integrating Blockchain, AI, and Digital Twin in AM.
6.3.2. Digital Twin Layer: Real-Time Process Replication and Simulation
The Digital Twin module controls an active, bi-directionally coupled virtual replica of the physical AM system. It reflects the thermal, mechanical, and geometrical development of parts during fabrication by integrating physics-based models with real-time sensor data gathered from the build platform, comprising temperature fields, scan paths, melt pool dimensions, laser energy input, and part distortion [130,131].
The twin supports:
- Real-time checking of in-process abnormalities (e.g., overheating, delamination, recoater failures),
- Predictive simulations handling finite element or reduced-order simulations for thermal and residual stress inference,
- Control validation by evaluating expected results against live sensor feedback.
This digital model also supports virtual commissioning of toolpath approaches, new process parameters, or part designs with no risk to physical hardware, decreasing downtime and cost [132].
6.3.3. AI Layer: Data-Driven Intelligence and Control Optimization
Built on top of the digital twin, the AI layer transforms raw sensor and simulation data into actionable insights. The module incorporates:
- Physics-Informed Neural Networks (PINNs) for explaining inverse problems such as rebuilding indefinite boundary conditions from partial thermal data [133].
- Deep learning models (e.g., CNNs, LSTMs) trained on prior process data to estimate defect formation, porosity zones, or layer-wise quality differences [134].
- Reinforcement Learning (RL) drivers learn to independently adjust laser power, scan speed, or hatch spaces in real time to enhance process results [135].
For example, if the AI detects irregular thermal gradients indicating potential part distortion, it can request the digital twin for simulated effects of parameter variations, identify the optimal solution, and revise the controller all within a single build cycle. This establishes a cyber-physical feedback loop, where the AI continually improves itself through real-world experimentation and simulated scenarios.
6.3.4. Blockchain Layer: Secure Traceability, IP Management, and Smart Contracts
The Blockchain layer tackles two primary concerns in AM: data reliability and intellectual property protection. In this framework, every critical task, such as creating a G-code toolpath, sensor data logging, anomaly detection, or final part authorization, is timestamped and hashed using SHA-256 and logged on a private blockchain network. This ledger:
- Generates a tamper-proof audit trail for build records, parameter changes, and failure events [136].
- Implements access control using smart contracts to guarantee only authorized personnel or collaborators can view/edit critical data [137].
- Enables IP protection by combining design files, toolpaths, and quality metrics to unique blockchain logs, preventing unauthorized access or modifications.
For storage scalability, large datasets (e.g., STL files, thermal maps) are stored on the Interplanetary File System (IPFS), and only the cryptographic hash is stored on the blockchain. This framework considers immutability in conjunction with performance and confirms the non-repudiation of all manufacturing data in both shared and distributed AM environments.
6.3.5. Middleware Orchestration: Real-Time Integration and Interoperability
At the core of the framework sits the middleware orchestration layer, which delivers the communication interface and synchronization protocols joining the digital twin, AI engine, blockchain, and physical AM machine. This layer controls:
- Event-driven interaction, allowing data triggers (e.g., thermal anomaly detection) to use blockchain transactions or AI-based control updates,
- Standardized data formats and ontologies for inferring sensor feedback, simulation outputs, and blockchain metadata throughout subsystems,
- APIs and microservices for integrating external systems, such as PLM systems, ERP tools, or connected manufacturing networks.
It guarantees low-latency, cyber-physically combined feedback loops, admitting real-time control actions (e.g., modifying scan strategy or deposition speed) centered on insights obtained from predictive simulations or AI inference, while recording all operations securely via smart contracts. Such middleware-aided integration aligns with the Industry 4.0 concept of connected, intelligent systems [136] and confirms the advancement of cyber-physical production systems as defined by Monostori [137].
6.3.6. Implementation Cost Considerations
AM would absolutely benefit from using advanced technologies like DT, AI, and blockchain’ for example, they would help with process control, product quality, and cybersecurity. While setting up these systems, we should also consider other important cost-related things. To make a good DT system, we need to buy good sensors, be able to interpret data in real time, and carefully integrate it with the way things are made now. Adding blockchain to make sure that data is correct and can be tracked back safely also makes it harder to set up and run the system. The technologies related to this system might be varied depending upon the choice of technology. Furthermore, small and medium-sized organizations (SMEs) can start implementing these technologies cautiously by using free open-source software and then add more capabilities as they need them. This step-by-step method helps companies stay competitive and come up with noble concepts without having to deal with significant money problems right away.
7. Conclusions
In this paper, the development and progress of DTs and AI over time in AM are discussed, and it is concluded that the integration of DTs, AI, and cybersecurity into AM systems is transforming the industry through process optimization and enhanced decision making. Importantly, these integrated approaches can empower not only large enterprises but also SMEs to achieve higher quality, efficiency, and competitiveness. However, the paper also pointed out that the application of these technologies generates various difficulties, most notably threats to cybersecurity, the difficulty of proper integration with both cyber and physical components, and the significant expenses involved in their implementation. For SMEs in particular, these barriers may seem daunting as well. To handle these challenges, one must adopt a comprehensive strategy, which could incorporate new technologies such as blockchain technology to enhance security, AI-based detection systems for reliability, and cloud-based platforms to remove financial barriers. The integration of DTs, AI, cybersecurity, and blockchain technology will lead to a manufacturing ecosystem that is stronger, safer, and more productive. The key points are:
- This paper summarizes and critically analyzes multiple data-driven (DT) architectures for additive manufacturing (AM), including mechanical, control, and machine learning-based models, and discusses their role in in situ monitoring and process optimization.
- This paper reviews the role of dynamic and modular AI frameworks, including PINNs, CNNs, LSTMs, and RL algorithms, in adjusting real-time AM process parameters, such as laser power and scan speed, to optimize build quality.
- The paper proposes a holistic closed-loop architecture that combines a Digital Twin, AI, a blockchain network, and real-time middleware orchestration to enable intelligent control, predictive process optimization, and secure cyber-physical interaction in additive manufacturing (AM) production systems.
The continuous convergence and development of frameworks for DTs, AI, cybersecurity, and blockchain technologies will cause significant change in the AM sector in the not-too-distant future. The possibility of adaptive manufacturing systems will create chances for new business models, supply chains, and manufacturing processes. It will be imperative to conduct continuous research and development if we are to realize this promise in terms of addressing the technical challenges related to data security and system integration. Establishing industry-wide standards and open-source projects will be crucial to ensuring equitable access to these transformative technologies, particularly supporting SMEs in adopting advanced manufacturing practices. Working together, the manufacturing community can propel the next wave of industrial innovation. Unlocking new degrees of efficiency, sustainability, and resilience in AM systems can help one achieve this.
Author Contributions
Conceptualization, M.S.A. and M.A.M.; methodology, M.S.A., L.K. and M.A.M.; software, M.S.A.; validation, M.S.A., L.K. and M.A.M.; formal analysis, M.S.A. and M.A.M.; investigation, M.A.M. and F.L.; resources, F.L.; data curation, M.S.A., L.K. and M.A.M.; writing—original draft preparation, M.S.A., L.K. and M.A.M.; writing—review and editing, M.S.A., L.K. and M.A.M. and F.L.; visualization, M.S.A. and L.K.; supervision, F.L.; project administration, F.L.; funding acquisition, F.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research was partially funded by NSF EEC 1937128, and the Intelligent Systems Center at Missouri University of Science and Technology.
Data Availability Statement
No new data was created.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Singh, M.; Fuenmayor, E.; Hinchy, E.P.; Qiao, Y.; Murray, N.; Devine, D. Digital Twin: Origin to Future. Appl. Syst. Innov. 2021, 4, 36. [Google Scholar] [CrossRef]
- Armstrong, M.; Mehrabi, H.; Naveed, N. An overview of modern metal additive manufacturing technology. J. Manuf. Process. 2022, 84, 1001–1029. [Google Scholar] [CrossRef]
- Tao, F.; Zhang, M.; Nee, A.Y.C. Digital Twin Driven Smart Manufacturing; Academic Press: Cambridge, MA, USA, 2019. [Google Scholar]
- Erol, T.; Mendi, A.F.; Dogan, D. Digital Transformation Revolution with Digital Twin Technology. In Proceedings of the 2020 4th International Symposium on Multidisciplinary Studies and Innovative Technologies (ISMSIT), Istanbul, Turkey, 22–24 October 2020; pp. 1–7. [Google Scholar] [CrossRef]
- Zuo, X.; Zhou, Y.; Hao, K.; Liu, C.; Yu, R.; Huang, A.; Wu, C.; Yang, Y. 3D Printed All-Natural Hydrogels: Flame-Retardant Materials Toward Attaining Green Sustainability. Adv. Sci. 2024, 11, 2306360. [Google Scholar] [CrossRef]
- Yao, S.; Chen, F.; Wang, Y.; Zhou, H.; Liu, K. Manufacturing defect-induced multiscale weakening mechanisms in carbon fiber reinforced polymers captured by 3D CT-based machine learning and high-fidelity modeling. Compos. Part A Appl. Sci. Manuf. 2025, 197, 109052. [Google Scholar] [CrossRef]
- Glaessgen, E.; Stargel, D. The Digital Twin Paradigm for Future NASA and U.S. Air Force Vehicles. In Proceedings of the 53rd AIAA/ASME/ASCE/AHS/ASC Structures, Structural Dynamics and Materials Conference, Honolulu, HI, USA, 23–26 April 2012; American Institute of Aeronautics and Astronautics: Reston, VA, USA. [Google Scholar] [CrossRef]
- Grieves, M. Back to the Future: Product Lifecycle Management and the Virtualization of Product Information. In Product Realization; Springer: Boston, MA, USA, 2009; pp. 1–13. [Google Scholar] [CrossRef]
- Zhang, Z.; Wan, L.; Wen, Q.; Shi, Y.; Feng, Z. Wire-based friction stir additive manufacturing of TiC reinforced Al-Cu-Mg composite: Particle refinement and dispersion. Compos. Part A Appl. Sci. Manuf. 2025, 196, 109009. [Google Scholar] [CrossRef]
- Ahn, D.-G. Directed Energy Deposition (DED) Process: State of the Art. Int. J. Precis. Eng. Manuf.-Green Technol. 2021, 8, 703–742. [Google Scholar] [CrossRef]
- Yang, H.; Wei, S.; Zhou, H.; Hu, F.; Chen, Y.; Hu, H. The Global Industrial Robot Trade Network: Evolution and China’s Rising International Competitiveness. Systems 2025, 13, 361. [Google Scholar] [CrossRef]
- Lim, K.Y.H.; Zheng, P.; Chen, C.-H. A state-of-the-art survey of Digital Twin: Techniques, engineering product lifecycle management and business innovation perspectives. J. Intell. Manuf. 2020, 31, 1313–1337. [Google Scholar] [CrossRef]
- Yu, H.; Zhao, Q.; Fu, J.; Hu, Y.; Liang, J.; Li, J.; Xu, W. The design of oxidation resistant Ni superalloys for additive manufacturing. Addit. Manuf. 2025, 97, 104616. [Google Scholar] [CrossRef]
- Zhang, L.; Chen, X.; Zhou, W.; Cheng, T.; Chen, L.; Guo, Z.; Han, B.; Lu, L. Digital Twins for Additive Manufacturing: A State-of-the-Art Review. Appl. Sci. 2020, 10, 8350. [Google Scholar] [CrossRef]
- Gaikwad, A.; Yavari, R.; Montazeri, M.; Cole, K.; Bian, L.; Rao, P. Toward the digital twin of additive manufacturing: Integrating thermal simulations, sensing, and analytics to detect process faults. IISE Trans. 2020, 52, 1204–1217. [Google Scholar] [CrossRef]
- Liu, C.; Le Roux, L.; Körner, C.; Tabaste, O.; Lacan, F.; Bigot, S. Digital Twin-enabled Collaborative Data Management for Metal Additive Manufacturing Systems. J. Manuf. Syst. 2022, 62, 857–874. [Google Scholar] [CrossRef]
- Chhetri, S.R.; Faezi, S.; Al Faruque, M.A. Digital Twin of Manufacturing Systems; Center for Embedded & Cyber-Physical Systems: Irvine, CA, USA, 2017. [Google Scholar]
- Ning, F.; Shi, Y.; Tong, X.; Cai, M.; Xu, W. Manufacturing cost estimation based on similarity. Int. J. Comput. Integr. Manuf. 2023, 36, 1238–1253. [Google Scholar] [CrossRef]
- Li, T.; Shi, H.; Bai, X.; Li, N.; Zhang, K. Rolling bearing performance assessment with degradation twin modeling considering interdependent fault evolution. Mech. Syst. Signal Process 2025, 224, 112194. [Google Scholar] [CrossRef]
- Mukherjee, T.; DebRoy, T. A digital twin for rapid qualification of 3D printed metallic components. Appl. Mater. Today 2019, 14, 59–65. [Google Scholar] [CrossRef]
- Wang, Z.; Li, J.; Yuan, Y.; Zhang, S.; Hu, W.; Ma, J.; Tan, J. Digital-twin-enabled online wrinkling monitoring of metal tube bending manufacturing: A multi-fidelity approach using forward-convolution-GAN. Appl. Soft Comput. 2025, 171, 112684. [Google Scholar] [CrossRef]
- Thejane, K.; du Preez, W.; Booysen, G. Implementing digital twinning in an additive manufacturing process chain. MATEC Web Conf. 2023, 388, 10001. [Google Scholar] [CrossRef]
- Ding, C.; Li, C.; Xiong, Z.; Li, Z. Computer big data technology in additive manufacturing and product design in sustainable manufacturing. Int. J. Adv. Manuf. Technol. 2024, 135, 4855–4863. [Google Scholar] [CrossRef]
- Phanden, R.K.; Aditya, S.V.; Sheokand, A.; Goyal, K.K.; Gahlot, P.; Jacso, A. A state-of-the-art review on implementation of digital twin in additive manufacturing to monitor and control parts quality. Mater. Today Proc. 1150, 56, 88–93. [Google Scholar] [CrossRef]
- Choudhary, A.; Chaudhary, A.; Devi, S. Cyber Security With Emerging Technologies & Challenges. In Proceedings of the 2022 4th International Conference on Advances in Computing, Communication Control and Networking (ICAC3N), Greater Noida, India, 16–17 December 2022; pp. 1875–1879. [Google Scholar] [CrossRef]
- Faruk, M.J.H.; Tahora, S.; Tasnim, M.; Shahriar, H.; Sakib, N. A Review of Quantum Cybersecurity: Threats, Risks and Opportunities. In Proceedings of the 2022 1st International Conference on AI in Cybersecurity (ICAIC), Victoria, TX, USA, 24–26 May 2022; pp. 1–8. [Google Scholar] [CrossRef]
- Jiang, W.; Zheng, B.; Sheng, D.; Li, X. A compensation approach for magnetic encoder error based on improved deep belief network algorithm. Sens. Actuators A Phys. 2024, 366, 115003. [Google Scholar] [CrossRef]
- Phua, A.; Davies, C.H.J.; Delaney, G.W. A digital twin hierarchy for metal additive manufacturing. Comput. Ind. 2022, 140, 103667. [Google Scholar] [CrossRef]
- Wu, X.; Zou, B.; Lu, C.; Wang, L.; Zhang, Y.; Wang, H. Dynamic Security Computing Framework with Zero Trust Based on Privacy Domain Prevention and Control Theory. IEEE J. Sel. Areas Commun. 2025, 43, 2266–2278. [Google Scholar] [CrossRef]
- Rajasekharaiah, K.M.; Dule, C.S.; Sudarshan, E. Cyber Security Challenges and its Emerging Trends on Latest Technologies. IOP Conf. Ser. Mater. Sci. Eng. 2020, 981, 022062. [Google Scholar] [CrossRef]
- Kanthimathi, T.; Rathika, N.; Fathima, A.J.; Rajesh, K.S.; Srinivasan, S.; Thamizhamuthu, R. Robotic 3D Printing for Customized Industrial Components: IoT and AI-Enabled Innovation. In Proceedings of the 2024 14th International Conference on Cloud Computing, Data Science & Engineering (Confluence), Noida, India, 18–19 January 2024; pp. 509–513. [Google Scholar] [CrossRef]
- Hossain, M.; Uddin, M.B. Digital Twins and Federated Learning for Industrial Internet of Things. Int. J. Sci. Res. Arch. 2025, 16, 729–736. [Google Scholar] [CrossRef]
- Wang, Q.; Chen, L.; Xiao, G.; Wang, P.; Gu, Y.; Lu, J. Elevator fault diagnosis based on digital twin and PINNs-e-RGCN. Sci. Rep. 2024, 14, 30713. [Google Scholar] [CrossRef] [PubMed]
- Jin, L.; Zhai, X.; Wang, K.; Zhang, K.; Wu, D.; Nazir, A.; Jiang, J.; Liao, W.-H. Big data, machine learning, and digital twin assisted additive manufacturing: A review. Mater. Des. 2024, 244, 113086. [Google Scholar] [CrossRef]
- Li, R.; Ma, H.; Wang, R.; Song, H.; Zhou, X.; Wang, L.; Zhang, H.; Zeng, K.; Xia, C. Application of unsupervised learning methods based on video data for real-time anomaly detection in wire arc additive manufacturing. J. Manuf. Process 2025, 143, 37–55. [Google Scholar] [CrossRef]
- Gong, Y.; Yao, H.; Liu, X.; Bennis, M.; Nallanathan, A.; Han, Z. Computation and Privacy Protection for Satellite-Ground Digital Twin Networks. IEEE Trans. Commun. 2024, 72, 5532–5546. [Google Scholar] [CrossRef]
- Nie, F.; Fang, H.; Wang, J.; Zhao, L.; Jia, C.; Ma, S.; Wu, F.; Zhao, W.; Yang, S.; Wei, S.; et al. An Adaptive Solid-State Synapse with Bi-Directional Relaxation for Multimodal Recognition and Spatio-Temporal Learning. Adv. Mater. 2025, 37, 2412006. [Google Scholar] [CrossRef]
- Gunasegaram, D.R.; Murphy, A.B.; Matthews, M.J.; DebRoy, T. The case for digital twins in metal additive manufacturing. J. Phys. Mater. 2021, 4, 040401. [Google Scholar] [CrossRef]
- Stavropoulos, P.; Papacharalampopoulos, A.; Michail, C.K.; Chryssolouris, G. Robust Additive Manufacturing Performance through a Control Oriented Digital Twin. Metals 2021, 11, 708. [Google Scholar] [CrossRef]
- Knapp, G.L.; Mukherjee, T.; Zuback, J.S.; Wei, H.L.; Palmer, T.A.; De, A.; DebRoy, T. Building blocks for a digital twin of additive manufacturing. Acta Mater. 2017, 135, 390–399. [Google Scholar] [CrossRef]
- DebRoy, T.; Zhang, W.; Turner, J.; Babu, S.S. Building digital twins of 3D printing machines. Scr. Mater. 2017, 135, 119–124. [Google Scholar] [CrossRef]
- Li, T.; Chai, H.; Zhang, S.; Jiang, F.; Liu, H.; Huang, W.; Jin, D.; Li, Y. Generative AI Empowered Network Digital Twins: Architecture, Technologies, and Applications. ACM Comput. Surv. 2025, 57, 43. [Google Scholar] [CrossRef]
- Chen, L.; Yao, X.; Liu, K.; Tan, C.; Moon, S.K. Multisensor fusion-based digital twin in additive manufacturing for in-situ quality monitoring and defect correction. Proc. Des. Soc. 2023, 3, 2755–2764. [Google Scholar] [CrossRef]
- Xu, S.; Lu, Y.; Yu, C. Augmented reality-assisted cloud additive manufacturing with digital twin technology for multi-stakeholder value Co-creation in product innovation. Heliyon 2024, 10, e25722. [Google Scholar] [CrossRef]
- Roidl, B.; Fauner, T. Continuous Improvement in Gas Flow Design. Available online: https://go.additive.ge.com/rs/706-JIU-273/images/GE%20Additive_Gas%20Flow_WP_US_EN-high%20res.pdf (accessed on 1 March 2022).
- Siemens Energy, Additive Manufacturing for the Energy Industry. Available online: https://www.siemens-energy.com/us/en/home/products-services/service/additive-manufacturing.html#Download (accessed on 1 March 2022).
- Safran Aircraft Engines Uses a Predictive Digital Twin to Direct Millions in Investment. Available online: https://www.haskoning.com/en/twinn/impact-stories/safran-aircraft-engines (accessed on 1 January 2025).
- Ladani, L.J. Applications of artificial intelligence and machine learning in metal additive manufacturing. J. Phys. Mater. 2021, 4, 042009. [Google Scholar] [CrossRef]
- Aziz, N.A.; Adnan, N.A.A.; Wahab, D.A.; Azman, A.H. Component design optimisation based on artificial intelligence in support of additive manufacturing repair and restoration: Current status and future outlook for remanufacturing. J. Clean. Prod. 2021, 296, 126401. [Google Scholar] [CrossRef]
- He, F.; Yuan, L.; Mu, H.; Ros, M.; Ding, D.; Pan, Z.; Li, H. Research and application of artificial intelligence techniques for wire arc additive manufacturing: A state-of-the-art review. Robot. Comput. Integr. Manuf. 2023, 82, 102525. [Google Scholar] [CrossRef]
- Arinez, J.F.; Chang, Q.; Gao, R.X.; Xu, C.; Zhang, J. Artificial Intelligence in Advanced Manufacturing: Current Status and Future Outlook. J. Manuf. Sci. Eng. 2020, 142, 110804. [Google Scholar] [CrossRef]
- Çınar, Z.M.; Nuhu, A.A.; Zeeshan, Q.; Korhan, O.; Asmael, M.; Safaei, B. Machine Learning in Predictive Maintenance towards Sustainable Smart Manufacturing in Industry 4.0. Sustainability 2020, 12, 8211. [Google Scholar] [CrossRef]
- Soori, M.; Arezoo, B.; Dastres, R. Artificial intelligence, machine learning and deep learning in advanced robotics, a review. Cogn. Robot. 2023, 3, 54–70. [Google Scholar] [CrossRef]
- Wang, C.; Tan, X.P.; Tor, S.B.; Lim, C.S. Machine learning in additive manufacturing: State-of-the-art and perspectives. Addit. Manuf. 2020, 36, 101538. [Google Scholar] [CrossRef]
- Guo, K.; Yang, Z.; Yu, C.-H.; Buehler, M.J. Artificial intelligence and machine learning in design of mechanical materials. Mater. Horiz. 2021, 8, 1153–1172. [Google Scholar] [CrossRef]
- Qin, J.; Hu, F.; Liu, Y.; Witherell, P.; Wang, C.C.L.; Rosen, D.W.; Simpson, T.W.; Lu, Y.; Tang, Q. Research and application of machine learning for additive manufacturing. Addit. Manuf. 2022, 52, 102691. [Google Scholar] [CrossRef]
- Zhang, Z.; Chen, G.; Chen, W.; Jia, R.; Chen, G.; Zhang, L.; Pan, J.; Zhou, P. A Joint Learning of Force Feedback of Robotic Manipulation and Textual Cues for Granular Materials Classification. IEEE Robot. Autom. Lett. 2025, 10, 7166–7173. [Google Scholar] [CrossRef]
- Banerjee, D.K.; Kumar, A.; Sharma, K. Artificial Intelligence on Additive Manufacturing. Int. IT J. Res. 2024, 2, 200198. [Google Scholar]
- Wang, Y.; Zheng, P.; Peng, T.; Yang, H.; Zou, J. Smart additive manufacturing: Current artificial intelligence-enabled methods and future perspectives. Sci. China Technol. Sci. 2020, 63, 1600–1611. [Google Scholar] [CrossRef]
- Masinelli, G.; Shevchik, S.A.; Pandiyan, V.; Quang-Le, T.; Wasmer, K. Artificial Intelligence for Monitoring and Control of Metal Additive Manufacturing. In Industrializing Additive Manufacturing; Springer International Publishing: Cham, Switzerland, 2021; pp. 205–220. [Google Scholar] [CrossRef]
- Heiden, B.; Alieksieiev, V.; Volk, M.; Tonino-Heiden, B. Framing Artificial Intelligence (AI) Additive Manufacturing (AM). Procedia Comput. Sci. 2020, 186, 387–394. [Google Scholar] [CrossRef]
- Jin, Z.; Zhang, Z.; Gu, G.X. Automated Real-Time Detection and Prediction of Interlayer Imperfections in Additive Manufacturing Processes Using Artificial Intelligence. Adv. Intell. Syst. 2020, 2, 1900130. [Google Scholar] [CrossRef]
- Elambasseril, J.; Brandt, M. Artificial intelligence: Way forward to empower metal additive manufacturing product development—An overview. Mater. Today Proc. 2022, 58, 461–465. [Google Scholar] [CrossRef]
- Gu, S.; Choi, M.; Park, H.; Jeong, S.; Doh, J.; Park, S. Application of artificial intelligence in additive manufacturing. JMST Adv. 2023, 5, 93–104. [Google Scholar] [CrossRef]
- Johnson, M.V.; Garanger, K.; Hardin, J.O.; Berrigan, J.D.; Feron, E.; Kalidindi, S.R. A generalizable artificial intelligence tool for identification and correction of self-supporting structures in additive manufacturing processes. Addit. Manuf. 2021, 46, 102191. [Google Scholar] [CrossRef]
- Choi, W.; Advincula, R.C.; Wu, H.F.; Jiang, Y. Artificial intelligence and machine learning in the design and additive manufacturing of responsive composites. MRS Commun. 2023, 13, 714–724. [Google Scholar] [CrossRef]
- Renken, V.; von Freyberg, A.; Schünemann, K.; Pastors, F.; Fischer, A. In-process closed-loop control for stabilising the melt pool temperature in selective laser melting. Progress Addit. Manuf. 2019, 4, 411–421. [Google Scholar] [CrossRef]
- Chen, L.; Bi, G.; Yao, X.; Tan, C.; Su, J.; Ng, N.P.H.; Chew, Y.; Liu, K.; Moon, S.K. Multisensor fusion-based digital twin for localized quality prediction in robotic laser-directed energy deposition. Robot. Comput. Integr. Manuf. 2023, 84, 102581. [Google Scholar] [CrossRef]
- Hartmann, S.; Vykhtar, B.; Möbs, N.; Kelbassa, I.; Mayr, P. IoT-Based Data Mining Framework for Stability Assessment of the Laser-Directed Energy Deposition Process. Processes 2024, 12, 1180. [Google Scholar] [CrossRef]
- Ahmadi, F.; Song, J.; Zoughi, R. Electromagnetic Scattering Properties of Metal Powder Cloud for Laser Powder Bed Fusion (LPBF) Additive Manufacturing (AM). IEEE Open J. Antennas Propag. 2024, 5, 1639–1648. [Google Scholar] [CrossRef]
- Zhu, Q.; Liu, Z.; Yan, J. Machine learning for metal additive manufacturing: Predicting temperature and melt pool fluid dynamics using physics-informed neural networks. Comput. Mech. 2021, 67, 619–635. [Google Scholar] [CrossRef]
- Meng, L.; McWilliams, B.; Jarosinski, W.; Park, H.-Y.; Jung, Y.-G.; Lee, J. Machine Learning in Additive Manufacturing: A Review. JOM 2020, 72, 2363–2377. [Google Scholar] [CrossRef]
- Goh, G.D.; Sing, S.L.; Yeong, W.Y. A review on machine learning in 3D printing: Applications, potential, and challenges. Artif. Intell. Rev. 2021, 54, 63–94. [Google Scholar] [CrossRef]
- Throne, O.; Lăzăroiu, G. Internet of Things-enabled Sustainability, Industrial Big Data Analytics, and Deep Learning-assisted Smart Process Planning in Cyber-Physical Manufacturing Systems. Econ. Manag. Financ. Mark. 2020, 15, 49. [Google Scholar] [CrossRef]
- Andronie, M.; Lăzăroiu, G.; Ștefănescu, R.; Uță, C.; Dijmărescu, I. Sustainable, Smart, and Sensing Technologies for Cyber-Physical Manufacturing Systems: A Systematic Literature Review. Sustainability 2021, 13, 5495. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Zeadally, S.; Vuduthala, A.B. Cyber-Physical Cloud Manufacturing Systems With Digital Twins. IEEE Internet Comput. 2022, 26, 15–21. [Google Scholar] [CrossRef]
- Zhang, Z.; Wan, L.; Meng, X.; Xie, Y.; Tian, H.; Mao, D.; Dong, W.; Sun, X.; Ma, X.; Huang, Y. Robotic wire-based friction stir additive manufacturing. Addit. Manuf. 2024, 88, 104261. [Google Scholar] [CrossRef]
- Balta, E.C.; Pease, M.; Moyne, J.; Barton, K.; Tilbury, D.M. Digital Twin-Based Cyber-Attack Detection Framework for Cyber-Physical Manufacturing Systems. IEEE Trans. Autom. Sci. Eng. 2024, 21, 1695–1712. [Google Scholar] [CrossRef]
- Wu, Y.; Cao, H.; Yang, G.; Lu, T.; Wan, S. Digital Twin of Intelligent Small Surface Defect Detection with Cyber-manufacturing Systems. ACM Trans. Internet Technol. 2023, 23, 1–20. [Google Scholar] [CrossRef]
- Dafflon, B.; Moalla, N.; Ouzrout, Y. The challenges, approaches, and used techniques of CPS for manufacturing in Industry 4.0: A literature review. Int. J. Adv. Manuf. Technol. 2021, 113, 2395–2412. [Google Scholar] [CrossRef]
- Corallo, A.; Lazoi, M.; Lezzi, M.; Pontrandolfo, P. Cybersecurity Challenges for Manufacturing Systems 4.0: Assessment of the Business Impact Level. IEEE Trans. Eng. Manag. 2023, 70, 3745–3765. [Google Scholar] [CrossRef]
- Wu, M.; Song, Z.; Moon, Y.B. Detecting cyber-physical attacks in CyberManufacturing systems with machine learning methods. J. Intell. Manuf. 2019, 30, 1111–1123. [Google Scholar] [CrossRef]
- Yampolskiy, M.; Horvath, P.; Koutsoukos, X.D.; Xue, Y.; Sztipanovits, J. Taxonomy for description of cross-domain attacks on CPS. In Proceedings of the 2nd ACM International Conference on High Confidence Networked Systems, New York, NY, USA, 9 April 2013; pp. 135–142. [Google Scholar] [CrossRef]
- Wu, M.; Moon, Y.B. Taxonomy for Secure CyberManufacturing Systems. In Proceedings of the Advanced Manufacturing, American Society of Mechanical Engineers, Pittsburgh, PA, USA, 9–15 November 2018; Volume 2. [Google Scholar] [CrossRef]
- Dave, M. Internet of Things Security and Forensics: Concern and Challenges for Inspecting Cyber Attacks. In Proceedings of the 2022 Second International Conference on Next Generation Intelligent Systems (ICNGIS), Kottayam, India, 29–31 July 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Wang, L.; Mosher, R.L.; Duett, P. Cyberattacks and Cybersecurity in Additive Manufacturing. In Proceedings of the SoutheastCon 2024, Atlanta, GA, USA, 15–24 March 2024; pp. 1040–1045. [Google Scholar] [CrossRef]
- Mahan, T.; Menold, J. Simulating cyber-physical systems: Identifying vulnerabilities for design and manufacturing through simulated additive manufacturing environments. Addit. Manuf. 2020, 35, 101232. [Google Scholar] [CrossRef]
- Mullet, V.; Sondi, P.; Ramat, E. A Review of Cybersecurity Guidelines for Manufacturing Factories in Industry 4.0. IEEE Access 2021, 9, 23235–23263. [Google Scholar] [CrossRef]
- Raza, A.; Memon, S.; Nizamani, M.A.; Shah, M.H. Machine Learning-Based Security Solutions for Critical Cyber-Physical Systems. In Proceedings of the 2022 10th International Symposium on Digital Forensics and Security (ISDFS), Istanbul, Turkey, 6–7 June 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Torbacki, W. A Hybrid MCDM Model Combining DANP and PROMETHEE II Methods for the Assessment of Cybersecurity in Industry 4.0. Sustainability 2021, 13, 8833. [Google Scholar] [CrossRef]
- Daim, T.; Yalcin, H.; Mermoud, A.; Mulder, V. Exploring cybertechnology standards through bibliometrics: Case of National Institute of Standards and Technology. World Pat. Inf. 2024, 77, 102278. [Google Scholar] [CrossRef]
- Sturm, L.D.; Williams, C.B.; Camelio, J.A.; White, J.; Parker, R. Cyber-Physical Vulnerabilities in Additive Manufacturing Systems. In Proceedings of the 2014 International Solid Freeform Fabrication Symposium, Austin, TX, USA, 4–6 August 2014; pp. 951–963. Available online: https://hdl.handle.net/2152/89238 (accessed on 13 November 2024).
- Turner, H.; White, J.; Camelio, J.A.; Williams, C.; Amos, B.; Parker, R. Bad Parts: Are Our Manufacturing Systems at Risk of Silent Cyberattacks? IEEE Secur. Priv. 2015, 13, 40–47. [Google Scholar] [CrossRef]
- Zeltmann, S.E.; Gupta, N.; Tsoutsos, N.G.; Maniatakos, M.; Rajendran, J.; Karri, R. Manufacturing and Security Challenges in 3D Printing. JOM 2016, 68, 1872–1881. [Google Scholar] [CrossRef]
- Shi, Z.; Al Mamun, A.; Kan, C.; Tian, W.; Liu, C. An LSTM-autoencoder based online side channel monitoring approach for cyber-physical attack detection in additive manufacturing. J. Intell. Manuf. 2023, 34, 1815–1831. [Google Scholar] [CrossRef]
- Belikovetsky, S.; Solewicz, Y.; Yampolskiy, M.; Toh, J.; Elovici, Y. Detecting Cyber-Physical Attacks in Additive Manufacturing using Digital Audio Signing. arXiv 2017, arXiv:1705.06454. [Google Scholar]
- Yu, S.-Y.; Malawade, A.V.; Chhetri, S.R.; Al Faruque, M.A. Sabotage Attack Detection for Additive Manufacturing Systems. IEEE Access 2020, 8, 27218–27231. [Google Scholar] [CrossRef]
- Wu, M.; Moon, Y.B. Intrusion Detection of Cyber-Physical Attacks in Manufacturing Systems: A Review. In Proceedings of the ASME 2019 International Mechanical Engineering Congress and Exposition, Salt Lake City, UT, USA, 11–14 November 2019. [Google Scholar] [CrossRef]
- Sajadieh, S.M.M.; Noh, S.D. From Simulation to Autonomy: Reviews of the Integration of Artificial Intelligence and Digital Twins. Int. J. Precis. Eng. Manuf.-Green Technol. 2025, 1–32. [Google Scholar] [CrossRef]
- Alfaro-Viquez, D.; Zamora-Hernandez, M.; Fernandez-Vega, M.; Garcia-Rodriguez, J.; Azorin-Lopez, J. A Comprehensive Review of AI-Based Digital Twin Applications in Manufacturing: Integration Across Operator, Product, and Process Dimensions. Electronics 2025, 14, 646. [Google Scholar] [CrossRef]
- Abdoune, F.; Nouiri, M.; Cardin, O.; Castagna, P. Integration of Artificial Intelligence in the life cycle of industrial Digital Twins. IFAC-PapersOnLine 2022, 55, 2545–2550. [Google Scholar] [CrossRef]
- Al Hossain, M.F.; Molla, M.S. Future manufacturing integrating additive and subtractive processes: A theoretical framework. World J. Adv. Eng. Technol. Sci. 2025, 16, 289–297. [Google Scholar] [CrossRef]
- Wang, L. Digital Twin and Cybersecurity in Additive Manufacturing. J. Cybersecur. Educ. Res. Pract. 2024, 2024, 32. [Google Scholar] [CrossRef]
- Hossain, M.; Uddin, M.B. Digital twins in additive manufacturing. World J. Adv. Eng. Technol. Sci. 2024, 13, 909–918. [Google Scholar] [CrossRef]
- De Azambuja, A.J.G.; Plesker, C.; Schützer, K.; Anderl, R.; Schleich, B.; Almeida, V.R. Artificial Intelligence-Based Cyber Security in the Context of Industry 4.0—A Survey. Electronics 2023, 12, 1920. [Google Scholar] [CrossRef]
- Sarker, I.H.; Janicke, H.; Mohsin, A.; Gill, A.; Maglaras, L. Explainable AI for cybersecurity automation, intelligence and trustworthiness in digital twin: Methods, taxonomy, challenges and prospects. ICT Express 2024, 10, 935–958. [Google Scholar] [CrossRef]
- Uddin, M.B.; Hossain, M.; Das, S. Advancing manufacturing sustainability with industry 4.0 technologies. Int. J. Sci. Res. Arch. 2022, 6, 358–366. [Google Scholar] [CrossRef]
- Haridas, A.; Samad, A.A.; Vysakh, D.; Lawrence, K.D.; Pathari, V. A blockchain-based platform for smart contracts and intellectual property protection for the additive manufacturing industry. In Proceedings of the 2022 IEEE International Conference on Signal Processing, Informatics, Communication and Energy Systems (SPICES), Thiruvananthapuram, India, 10–12 March 2022; pp. 223–230. [Google Scholar] [CrossRef]
- Shi, Z.; Kan, C.; Tian, W.; Liu, C. A Blockchain-Based G-Code Protection Approach for Cyber-Physical Security in Additive Manufacturing. J. Comput. Inf. Sci. Eng. 2021, 21, 041007. [Google Scholar] [CrossRef]
- Haw, J.; Dola, T.A.; Sing, S.L.; Tan, E.Y.S.; Liu, A.Z. Blockchain for Additive Manufacturing. In Additive Manufacturing Design and Applications; ASM International: Almere, The Netherlands, 2023; pp. 582–587. [Google Scholar] [CrossRef]
- Westphal, E.; Leiding, B.; Seitz, H. Blockchain-based quality management for a digital additive manufacturing part record. J. Ind. Inf. Integr. 2023, 35, 100517. [Google Scholar] [CrossRef]
- Lupi, F.; Cimino, M.G.C.A.; Berlec, T.; Galatolo, F.A.; Corn, M.; Rožman, N.; Rossi, A.; Lanzetta, M. Blockchain-based Shared Additive Manufacturing. Comput. Ind. Eng. 2023, 183, 109497. [Google Scholar] [CrossRef]
- Alkhader, W.; Alkaabi, N.; Salah, K.; Jayaraman, R.; Arshad, J.; Omar, M. Blockchain-Based Traceability and Management for Additive Manufacturing. IEEE Access 2020, 8, 188363–188377. [Google Scholar] [CrossRef]
- Xu, Y.; Xu, H.; Chen, X.; Zhang, H.; Chen, B.; Han, Z. Blockchain-Based AR Offloading in UAV-Enabled MEC Networks: A Trade-off Between Energy Consumption and Rendering Latency. IEEE Trans. Veh. Technol. 2025, 1–16. [Google Scholar] [CrossRef]
- Xiong, Z.; Lou, Q.; Li, Y.; Chen, H.; Zhang, X.; Li, Y.; Li, J. NDLSC: A New Deep Learning-based Approach to Smart Contract Vulnerability Detection. J. Signal Process Syst. 2025, 97, 49–68. [Google Scholar] [CrossRef]
- Guo, D.; Ling, S.; Li, H.; Ao, D.; Zhang, T.; Rong, Y.; Huang, G.Q. A framework for personalized production based on digital twin, blockchain and additive manufacturing in the context of Industry 4.0. In Proceedings of the 2020 IEEE 16th International Conference on Automation Science and Engineering (CASE), Hong Kong, China, 20–21 August 2020; pp. 1181–1186. [Google Scholar] [CrossRef]
- Ghimire, T.; Joshi, A.; Sen, S.; Kapruan, C.; Chadha, U.; Selvaraj, S.K. Blockchain in additive manufacturing processes: Recent trends & its future possibilities. Mater. Today Proc. 2022, 50, 2170–2180. [Google Scholar] [CrossRef]
- Chadha, U.; Abrol, A.; Vora, N.P.; Tiwari, A.; Shanker, S.K.; Selvaraj, S.K. Performance evaluation of 3D printing technologies: A review, recent advances, current challenges, and future directions. Progress Addit. Manuf. 2022, 7, 853–886. [Google Scholar] [CrossRef]
- Kurpjuweit, S.; Schmidt, C.G.; Klöckner, M.; Wagner, S.M. Blockchain in Additive Manufacturing and its Impact on Supply Chains. J. Bus. Logist. 2021, 42, 46–70. [Google Scholar] [CrossRef]
- Nain, G.; Pattanaik, K.K.; Sharma, G.K. Towards edge computing in intelligent manufacturing: Past, present and future. J. Manuf. Syst. 2022, 62, 588–611. [Google Scholar] [CrossRef]
- Long, J.; Zhou, Y.; Lin, J.; Luo, B.; Wu, Z.; Su, X. Printing dense and low-resistance copper microstructures via highly directional laser-induced forward transfer. Addit. Manuf. 2025, 103, 104755. [Google Scholar] [CrossRef]
- Sæterbø, M.; Arnarson, H.; Yu, H.; Solvang, W.D. Expanding the horizons of metal additive manufacturing: A comprehensive multi-objective optimization model incorporating sustainability for SMEs. J. Manuf. Syst. 2024, 77, 62–77. [Google Scholar] [CrossRef]
- Haug, A.; Wickstrøm, K.A.; Stentoft, J.; Philipsen, K. Adoption of additive manufacturing: A survey of the role of knowledge networks and maturity in small and medium-sized Danish production firms. Int. J. Prod. Econ. 2023, 255, 108714. [Google Scholar] [CrossRef]
- Simeone, A.; Caggiano, A.; Zeng, Y. Smart cloud manufacturing platform for resource efficiency improvement of additive manufacturing services. Procedia CIRP 2020, 88, 387–392. [Google Scholar] [CrossRef]
- Rahman, M.A.; Shakur, M.S.; Ahamed, M.S.; Hasan, S.; Rashid, A.A.; Islam, M.A.; Haque, M.S.S.; Ahmed, A. A Cloud-Based Cyber-Physical System with Industry 4.0: Remote and Digitized Additive Manufacturing. Automation 2022, 3, 400–425. [Google Scholar] [CrossRef]
- Haghnegahdar, L.; Joshi, S.S.; Dahotre, N.B. From IoT-based cloud manufacturing approach to intelligent additive manufacturing: Industrial Internet of Things—An overview. Int. J. Adv. Manuf. Technol. 2022, 119, 1461–1478. [Google Scholar] [CrossRef]
- Shukla, S.; KC, S. Leveraging Blockchain for sustainability and supply chain resilience in e-commerce channels for additive manufacturing: A cognitive analytics management framework-based assessment. Comput. Ind. Eng. 2023, 176, 108995. [Google Scholar] [CrossRef]
- Xu, K.; Xiao, X.; Wang, L.; Lou, M.; Wang, F.; Li, C.; Ren, H.; Wang, X.; Chang, K. Data-Driven Materials Research and Development for Functional Coatings. Adv. Sci. 2024, 11, 2405262. [Google Scholar] [CrossRef]
- Wang, Z.; Gao, D.; Lu, Y.; Deng, K.; Yuan, Z.; Huang, M.; Jiang, T. A mutual cross-attention fusion network for surface roughness prediction in robotic machining process using internal and external signals. J. Manuf. Syst. 2025, 82, 284–300. [Google Scholar] [CrossRef]
- Tao, F.; Zhang, H.; Liu, A.; Nee, A.Y.C. Digital Twin in Industry: State-of-the-Art. IEEE Trans. Ind. Inform. 2019, 15, 2405–2415. [Google Scholar] [CrossRef]
- Qi, Q.; Tao, F. Digital Twin and Big Data Towards Smart Manufacturing and Industry 4.0: 360 Degree Comparison. IEEE Access 2018, 6, 3585–3593. [Google Scholar] [CrossRef]
- Leng, J.; Zhang, H.; Yan, D.; Liu, Q.; Chen, X.; Zhang, D. Digital twin-driven manufacturing cyber-physical system for parallel controlling of smart workshop. J. Ambient. Intell. Humaniz. Comput. 2019, 10, 1155–1166. [Google Scholar] [CrossRef]
- Raissi, M.; Perdikaris, P.; Karniadakis, G.E. Physics-informed neural networks: A deep learning framework for solving forward and inverse problems involving nonlinear partial differential equations. J. Comput. Phys. 2019, 378, 686–707. [Google Scholar] [CrossRef]
- Equbal, M.A.; Equbal, A.; Khan, Z.A.; Badruddin, I.A. Machine learning in additive manufacturing: A comprehensive insight. Int. J. Lightweight Mater. Manuf. 2025, 8, 264–284. [Google Scholar] [CrossRef]
- Li, C.; Zheng, P.; Yin, Y.; Wang, B.; Wang, L. Deep reinforcement learning in smart manufacturing: A review and prospects. CIRP J. Manuf. Sci. Technol. 2023, 40, 75–101. [Google Scholar] [CrossRef]
- Christidis, K.; Devetsikiotis, M. Blockchains and Smart Contracts for the Internet of Things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Monostori, L. Cyber-physical Production Systems: Roots, Expectations and R & D Challenges. Procedia CIRP 2014, 17, 9–13. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).