Overview of Jamming Technology for Satellite Navigation
Abstract
1. Introduction
2. Suppression Jamming
2.1. Jamming Classification of Suppression
2.1.1. Type of Suppression Jamming
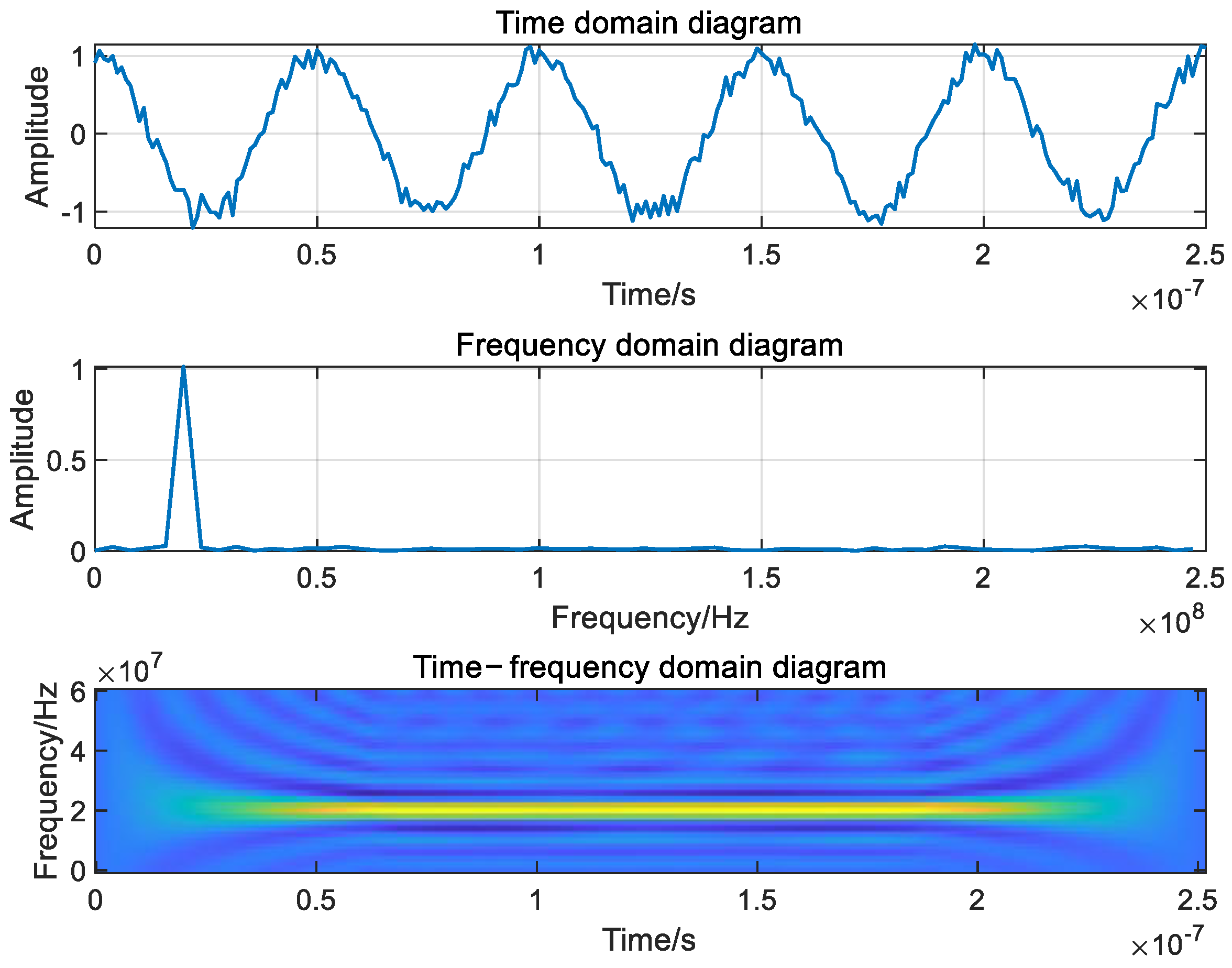
- Single-frequency jamming
- 2
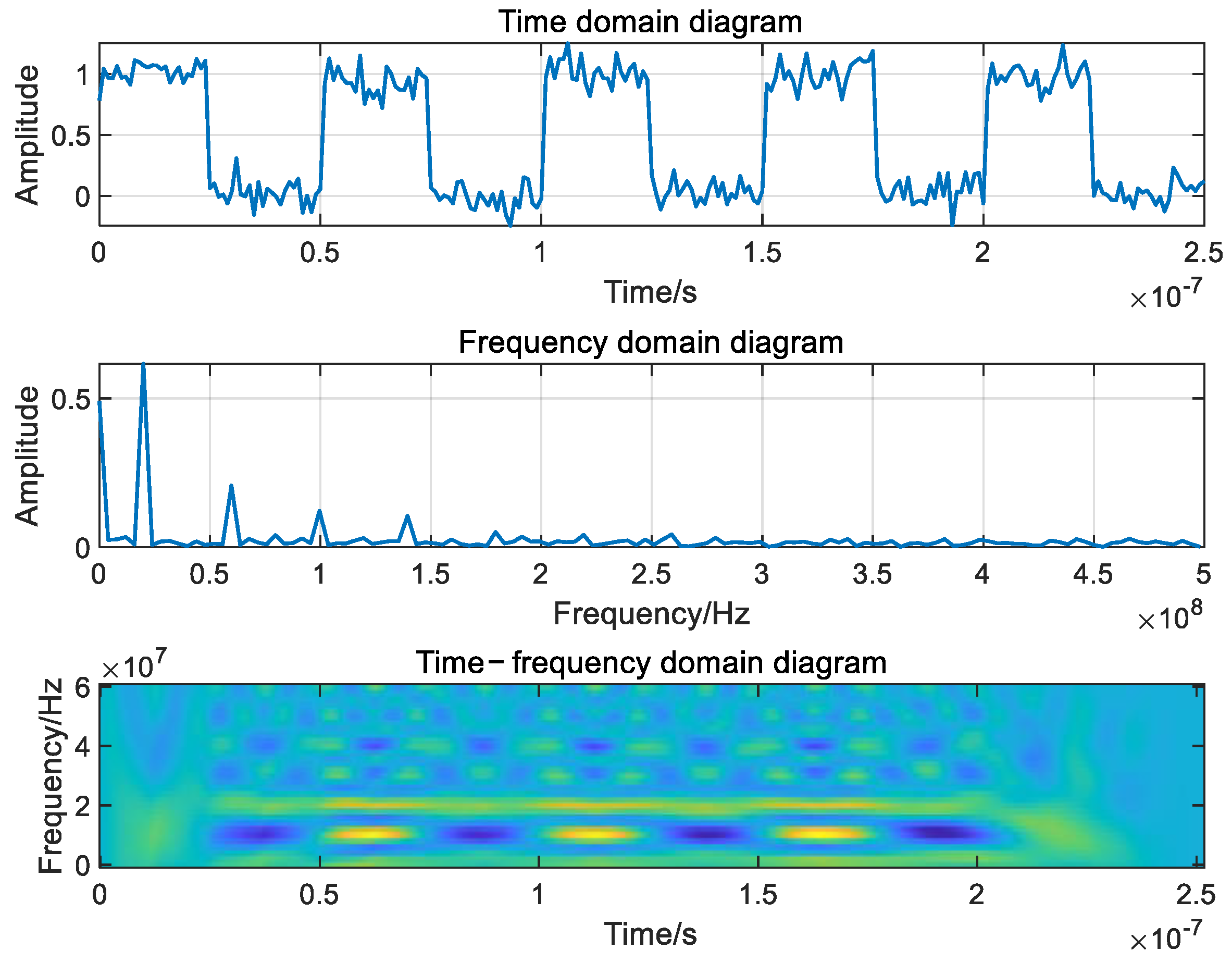
- Pulse jamming
- 3
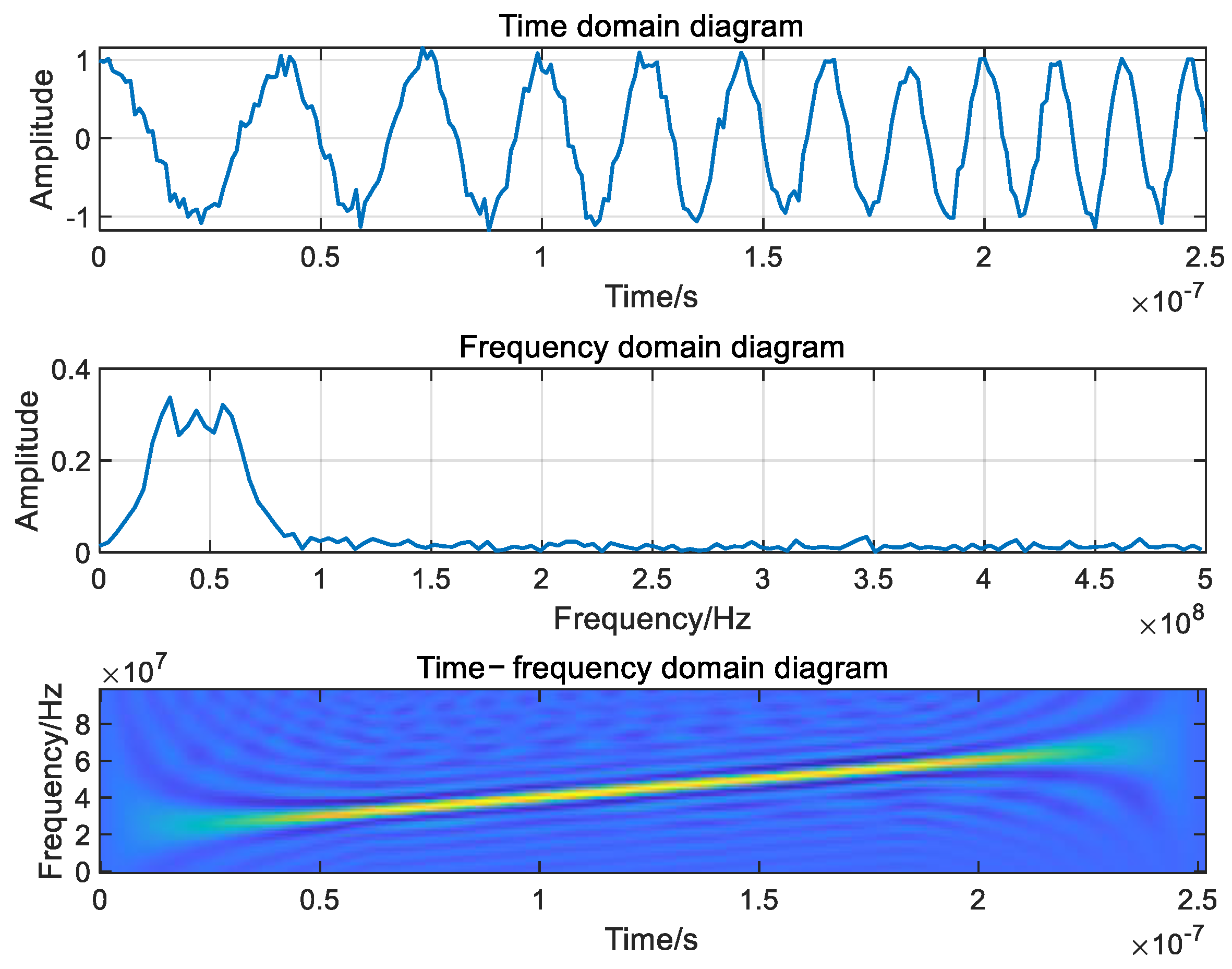
- Sweep jamming
- 4
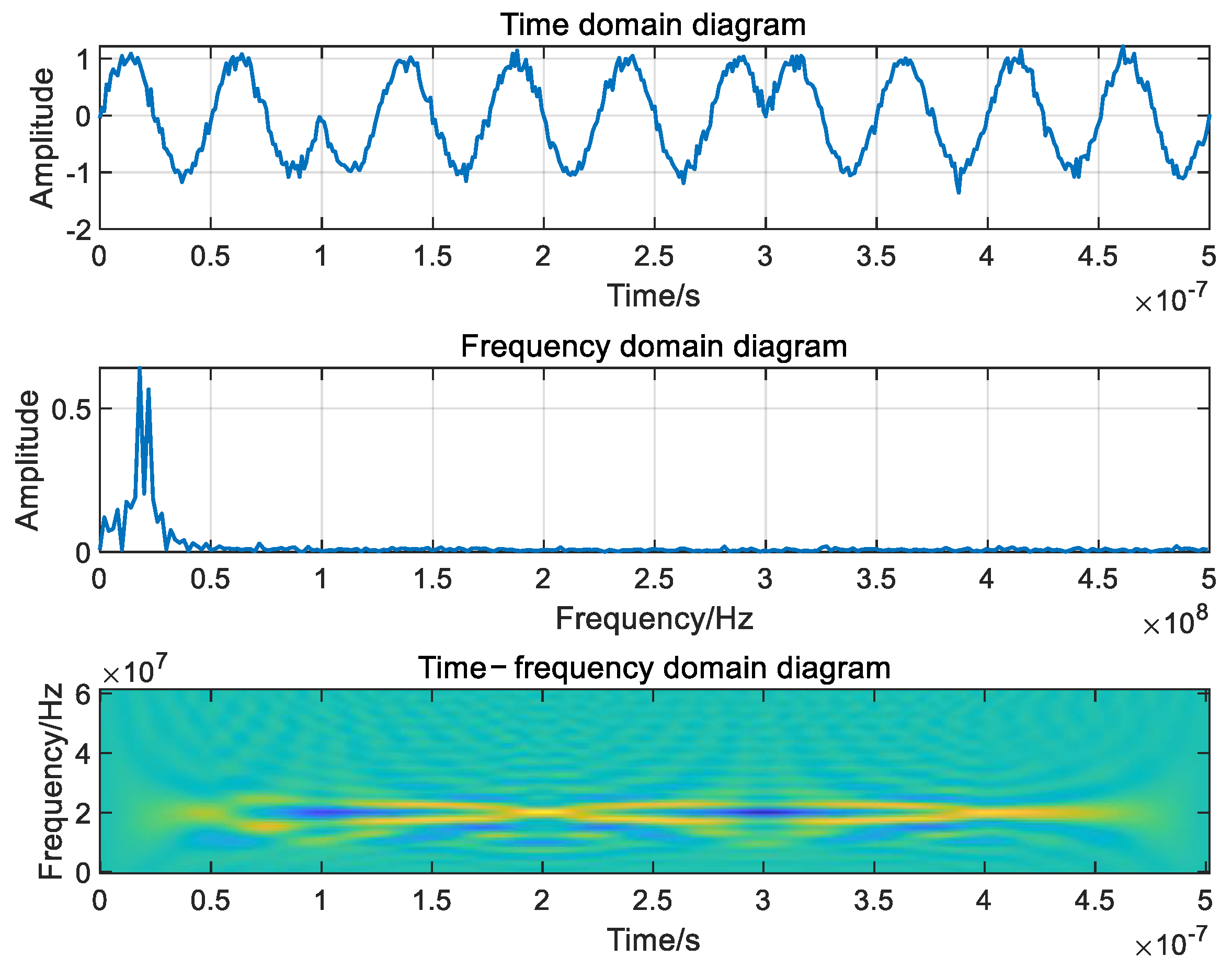
- Matched spectrum jamming
2.1.2. Stability of Suppression Jamming
2.1.3. Bandwidth of Suppression Jamming
2.2. Efficiency Evaluation of Suppression Jamming
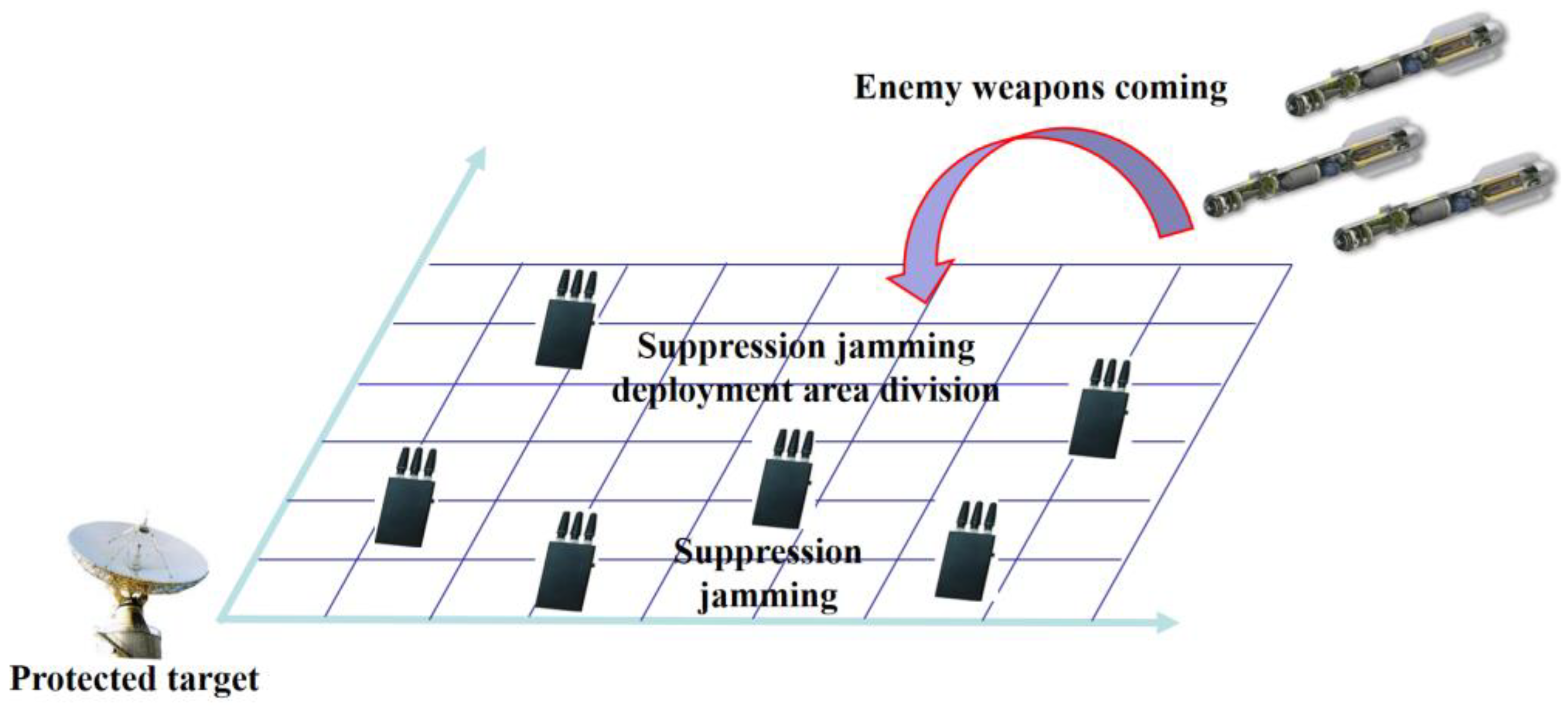
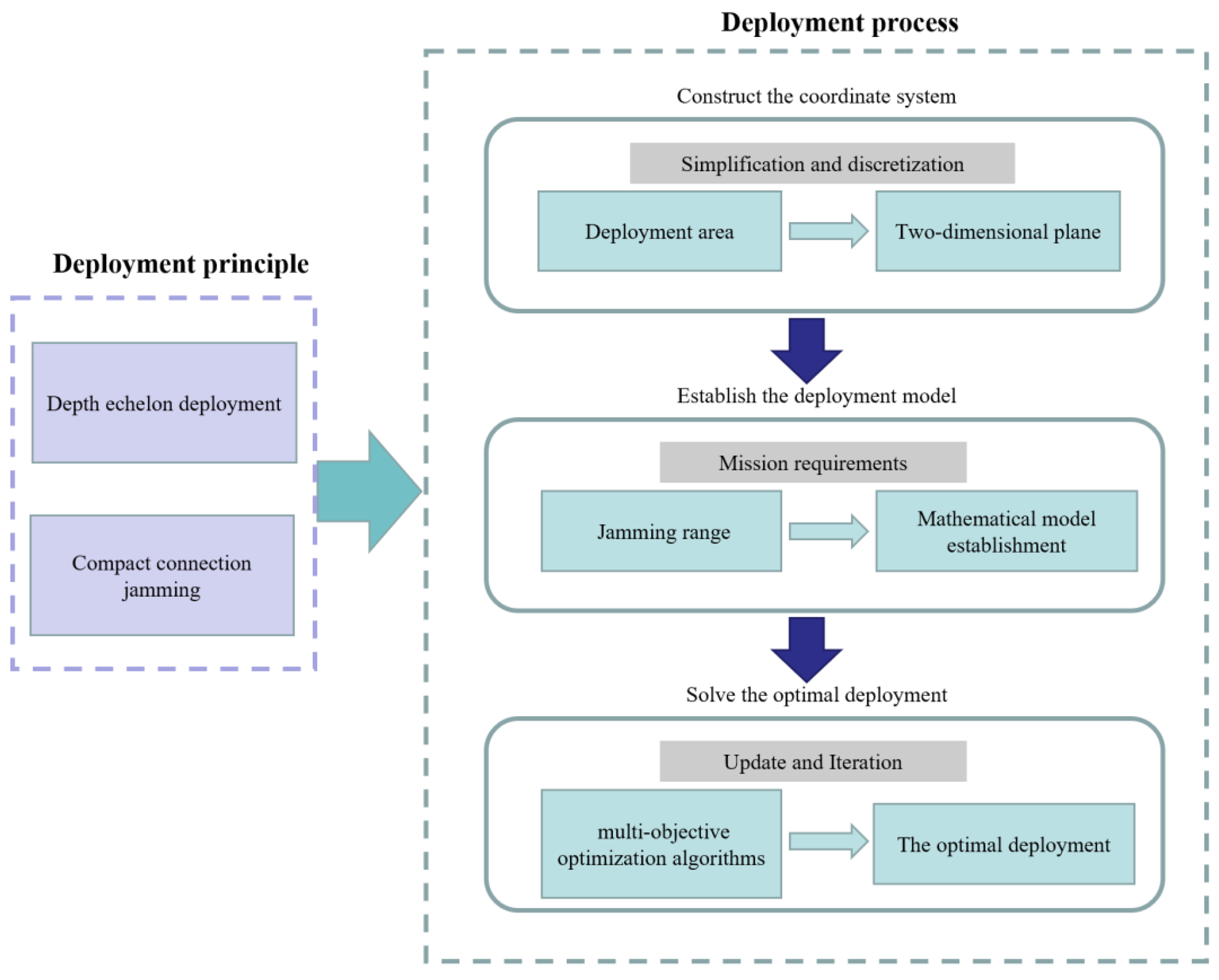
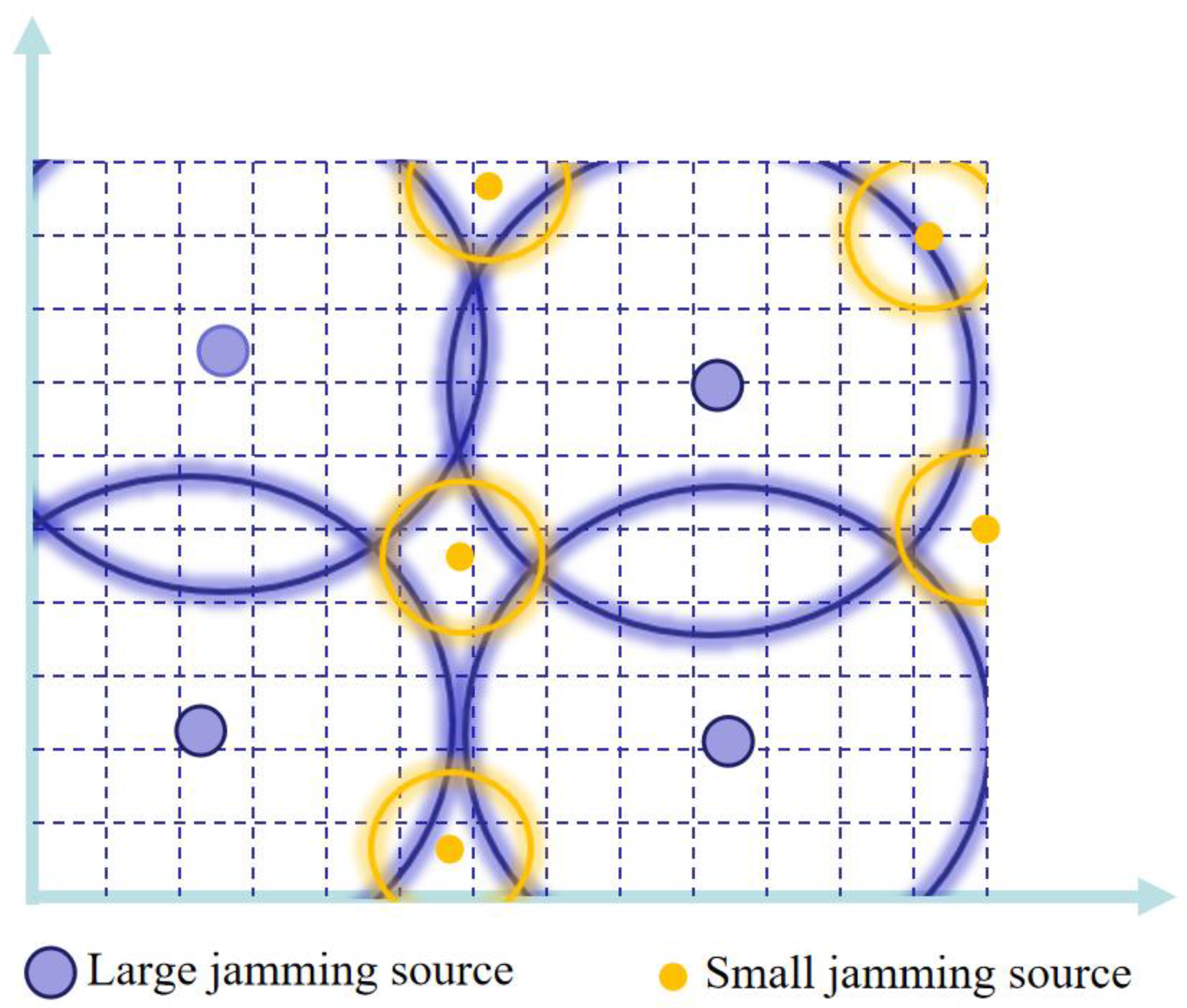
2.3. Jamming Source Deployment of Suppression Jamming
- Construct the coordinate system of suppression jamming deployment area: generally, the deployment area is simplified to a two-dimensional plane and discretized to facilitate labeling and calculating the location and area of the jamming sources;
- Establish a multi-objective optimization deployment model (based on mission requirements, it is usually based on the jamming range);
- Solve the optimal deployment of suppression jamming: iterative calculation using multi-objective optimization algorithms such as genetic algorithm and ant colony algorithm.
3. Deception Jamming
3.1. Classification of Deception Jamming
3.1.1. Generation Mode of Deception Jamming
- Generated deception jamming
- 2
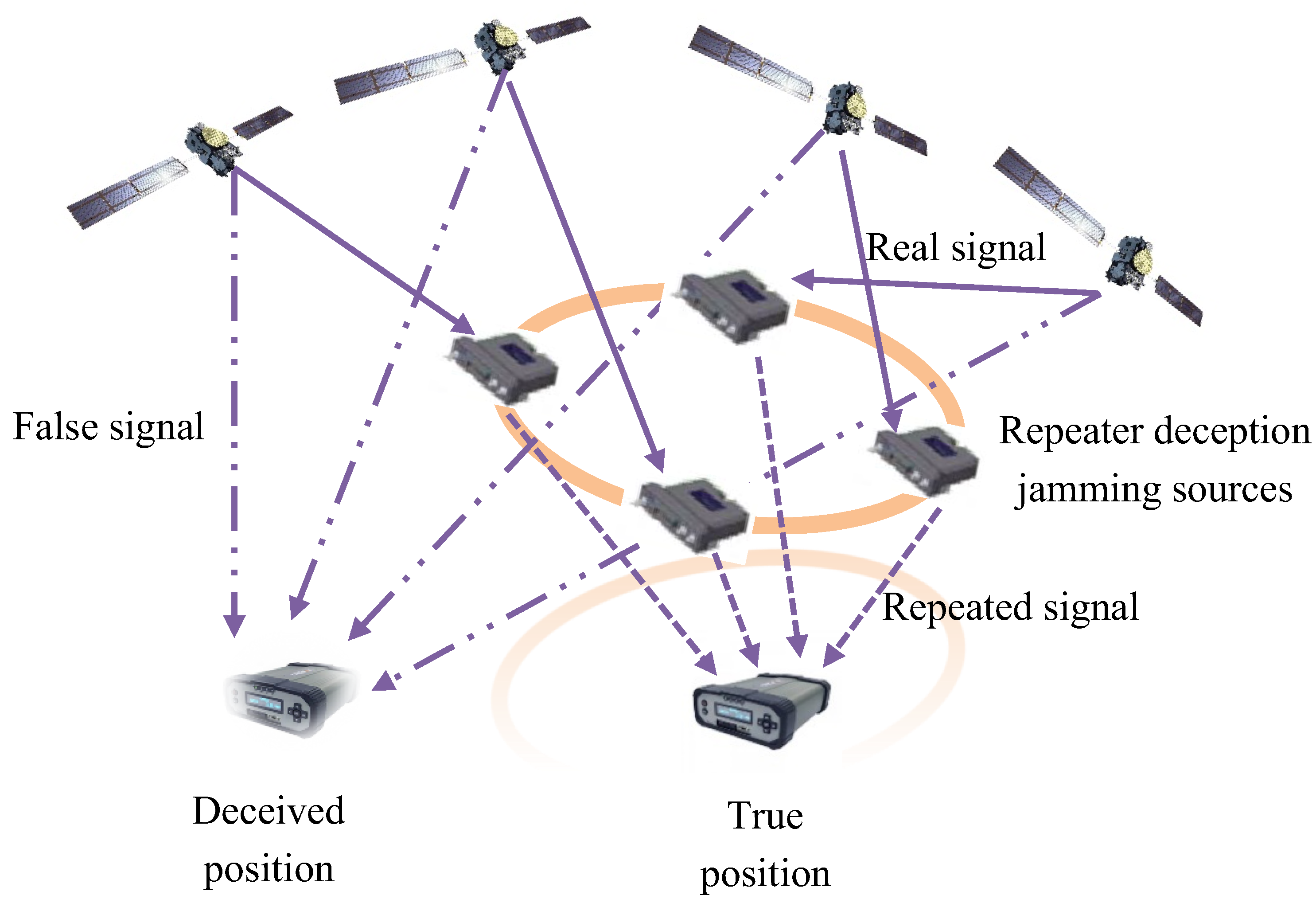
- Repeater deception jamming
3.1.2. Implementation Stage of Deception Jamming
- Signal acquisition stage
- 2
- Signal tracking stage
3.1.3. Implementation Difficulty of Deception Jamming
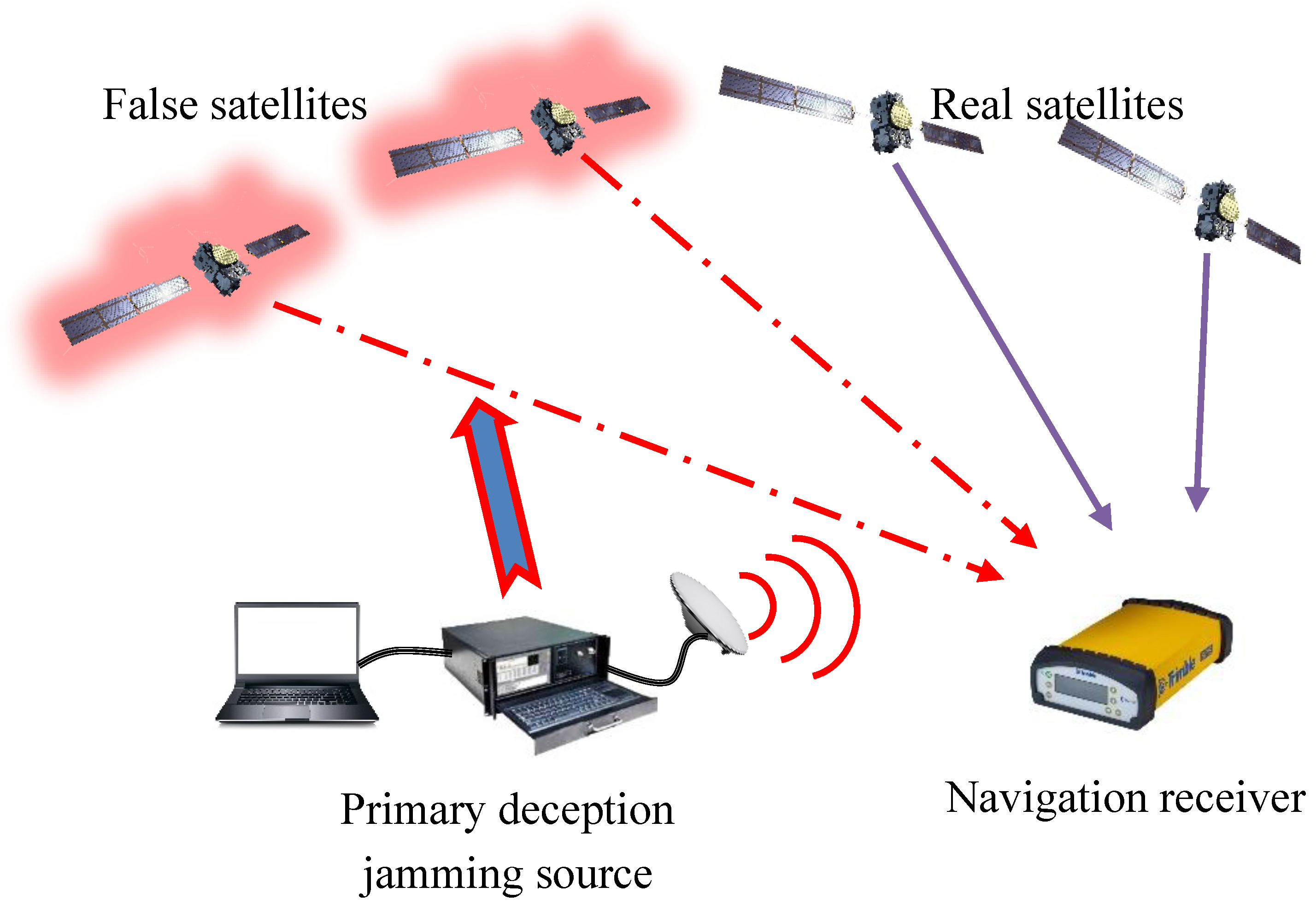
- Primary navigation deception jamming
- 2
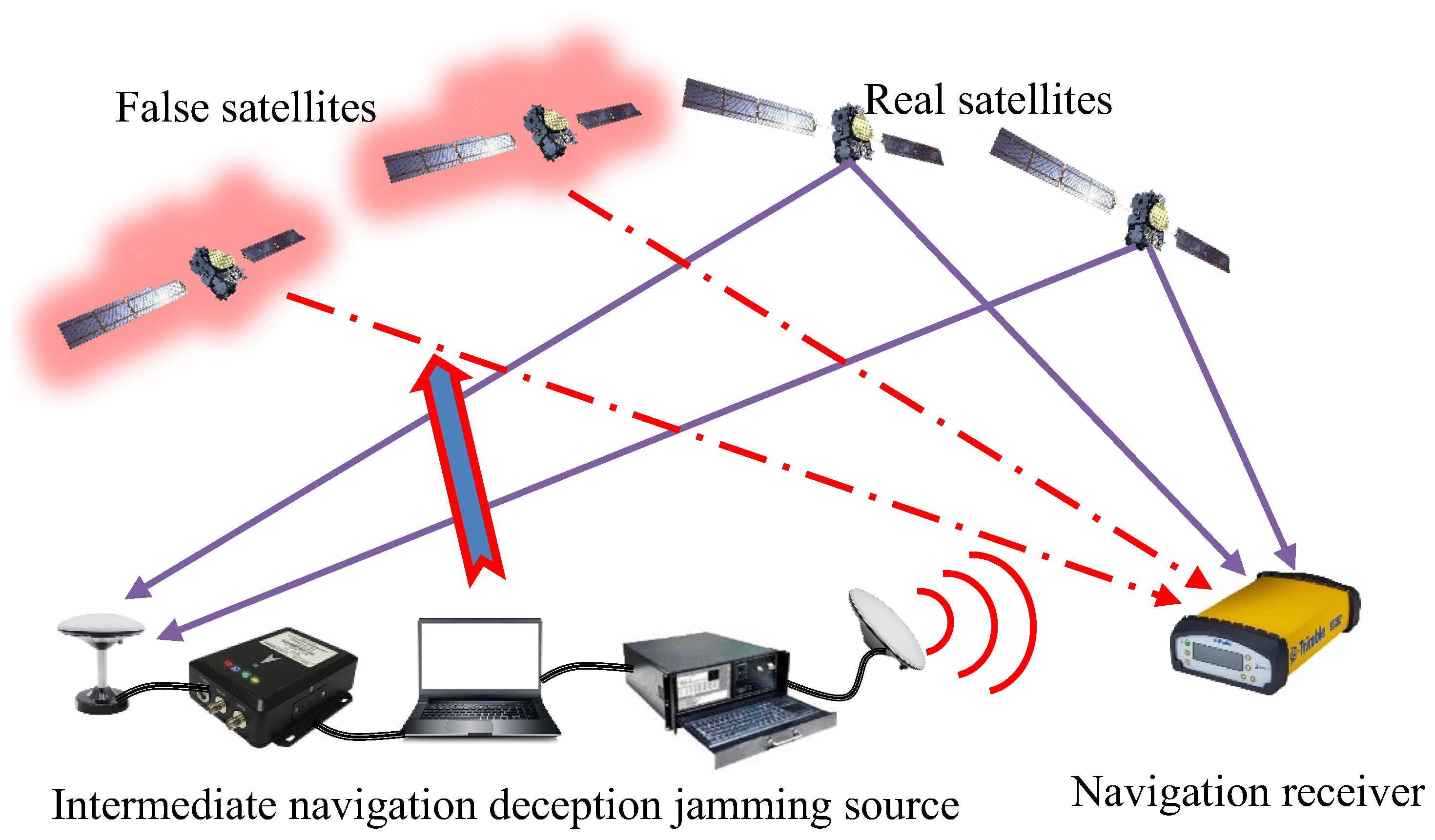
- Intermediate navigation deception jamming
- 3
- Advanced navigation deception jamming
3.2. Efficiency Evaluation of Deception Jamming
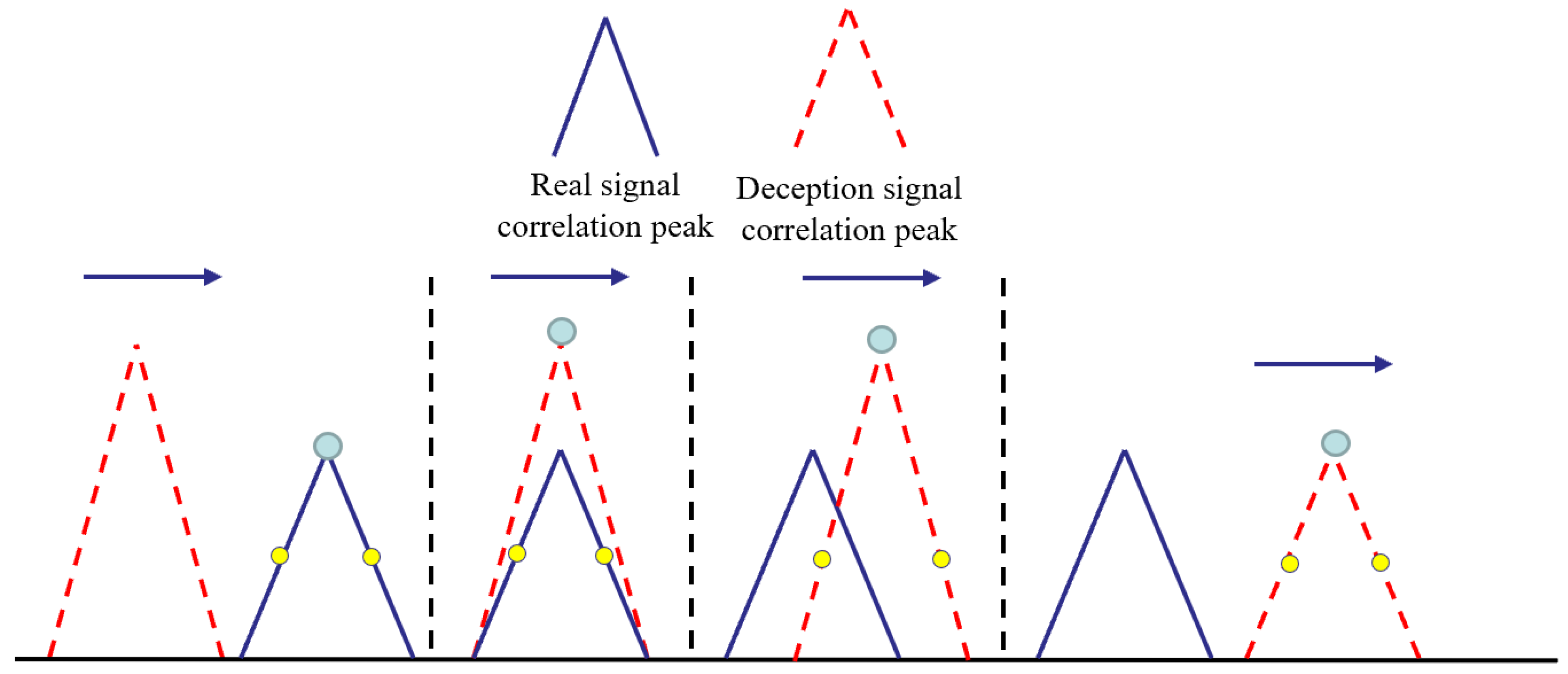
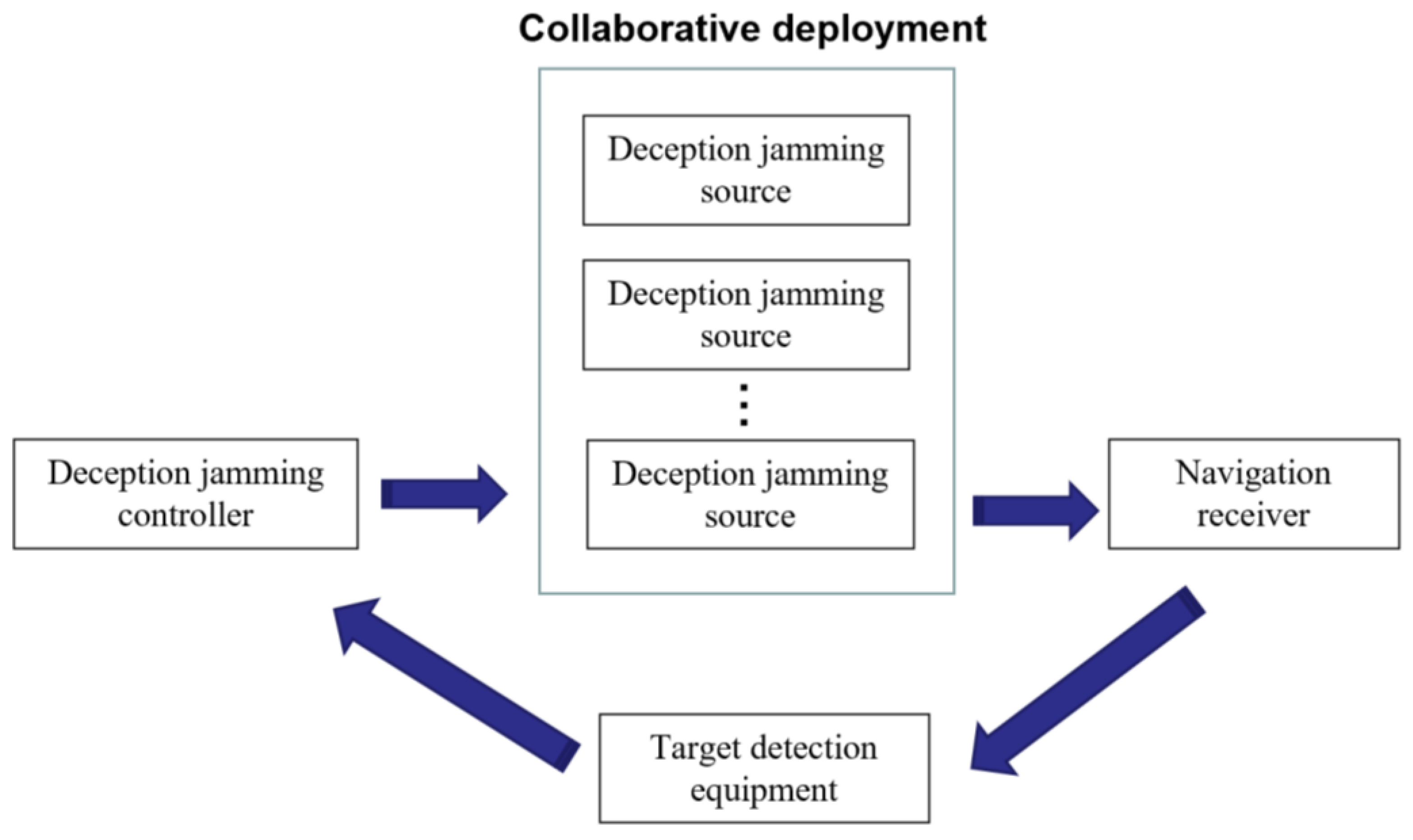
3.3. Jamming Source Deployment of Deception Jamming
4. Future Research Direction and Development Trend
4.1. Research on Evaluation System for Satellite Navigation Jamming
4.2. Research on Jamming Suppression Method for Antenna Array
4.3. Research on Deception Jamming Method for Integrated Navigation
4.4. Research on Deception Jamming Method for Military Signals
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Lu, J.; Guo, X.; Su, C. Global capabilities of BeiDou navigation satellite system. Satell. Navig. 2020, 1, 27. [Google Scholar] [CrossRef]
- Ma, C.; Yang, J.; Chen, J.; Qu, Z.; Zhou, C. Effects of a Navigation Spoofing Signal on a Receiver Loop and a UAV Spoofing Approach. GPS Solut. 2020, 24, 16. [Google Scholar]
- Psiaki, M.L.; Humphreys, T.E. GNSS Spoofing and Detection. Proc. IEEE 2016, 104, 1258–1270. [Google Scholar] [CrossRef]
- Lorraine, K.; Ramarakula, M.A. Comprehensive Survey on GNSS Interferences and the Application of Neural Networks for Anti-jamming. IETE J. Res. 2021, 0, 1–20. [Google Scholar] [CrossRef]
- Wang, Y.; Wang, Y.; Sun, X. Study on Index System of Satellite Navigation Jamming Effect Evaluation. Commun. Countermeas. 2013, 32, 33–37. [Google Scholar]
- Wang, Y.; Hao, J.; Liu, W. Evaluation Method for Effectiveness of GNSS Spoofer. Acta Armamentarii 2020, 41, 108–117. [Google Scholar]
- Zhang, X. GPSIII Satellite Navigation Interference Scheme and Interference Source Optimization Deployment Method Design; Research Institute of Electronic Science and Technology: Chengdu, China, 2017; pp. 5–76. [Google Scholar]
- Oshman, Y.; Koifman, M. Robust GPS navigation in the presence of jamming and spoofing. In Proceedings of the AIAA Guidance Navigation and Control Conference and Exhibit, Austin, TX, USA, 11–14 August 2003; pp. 1–11. [Google Scholar]
- Hu, H.; Wei, N. A study of GPS jamming and anti-jamming. In Proceedings of the 2nd International Conference on Power Electronics and Intelligent Transportation System, Shenzhen, China, 19–20 December 2009; pp. 388–391. [Google Scholar]
- Wang, H.; Chang, Q.; Xu, Y. An Integrated Beam Anti-Jamming Algorithm for Low-Orbit Navigation Augmentation. IEEE Commun. Lett. 2022, 26, 877–881. [Google Scholar] [CrossRef]
- Sun, Y.; Chen, F.; Lu, Z.; Wang, F. Anti-Jamming Method and Implementation for GNSS Receiver Based on Array Antenna Rotation. Remote Sens. 2022, 14, 4774. [Google Scholar] [CrossRef]
- Islam, S.; Bhuiyan, M.; Thombre, S.; Kaasalainen, S. Combating Single-Frequency Jamming through a Multi-Frequency Multi-Constellation Software Receiver A Case Study for Maritime Navigation in the Gulf of Finland. Sensors 2022, 22, 2294. [Google Scholar] [CrossRef]
- Karsi, M.; Lindsey, W. Effects of CW interference on phase-locked loop performance. Commun. IEEE Trans. 2000, 48, 886–896. [Google Scholar] [CrossRef]
- Mao, H.; Wu, D.; Lu, H.; Yan, Z. Analysis of a New Wideband Blanket Jamming Type to GPS Receiver. J. Electron. Inf. Technol. 2014, 36, 2930–2933. [Google Scholar]
- Qin, W.; Dovis, F. Situational Awareness of Chirp Jamming Threats to GNSS Based on Supervised Machine Learning. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 1707–1720. [Google Scholar] [CrossRef]
- Li, B.; Qiao, J.; Lu, Z.; Yu, X.; Song, J.; Lin, B.; Li, X. Influence of sweep jamming on satellite navigation time-domain anti-jamming. Front. Phys. 2023, 10, 1063474. [Google Scholar] [CrossRef]
- Mitch, R.H.; Dougherty, R.C.; Psiaki, M.L.; Powell, S.P.; O’Hanlon, B.W.; Bhatti, J.A.; Humphreys, T.E. Signal Characteristics of Civil GPS Jammers. In Proceedings of the International Technical Meeting of Satellite Division of the Institute of Navigation, Portland, OR, USA, 20–23 September 2011; pp. 364–371. [Google Scholar]
- Zhao, X.; Huang, X.; Tang, X.; Feng, X.; Sun, G. Chirp pseudo-noise signal and its receiving scheme for LEO enhanced GNSS. IET Radar Sonar Navig. 2022, 16, 1751–1758. [Google Scholar] [CrossRef]
- Baek, J.; Seungsoo, Y.; Sun, Y. Jamming Effect Analysis of Two Chinese GNSS BeiDou-II Civil Signals. Int. J. Electr. Comput. Eng. 2012, 2, 840–845. [Google Scholar] [CrossRef]
- Wang, J.; Sun, Z.; Zhang, Y. Study on Optimal Jamming Signal of GPS System. Comput. Meas. Control 2016, 24, 257–260. [Google Scholar]
- Konovaltsev, A.; Lorenzo, D.; Hornbostel, A.; Enge, P. Mitigation of continuous and pulsed radio jamming with GNSS antenna arrays. In Proceedings of the 21st International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS 2008), Savannah, GA, USA, 16–19 September 2008; pp. 2786–2795. [Google Scholar]
- Olivier, B. Analysis of the SNR Loss Distribution With Covariance Mismatched Training Samples. IEEE Trans. Signal Process. 2020, 68, 5759–5768. [Google Scholar]
- Wang, J.; Liu, W.; Ou, G.; Xiao, W.; Wang, H.; Dong, T. Channel scintillations of array global navigation satellite system receiver under distributed intermittent jammings. IET Radar Sonar Navig. 2022, 17, 227–235. [Google Scholar] [CrossRef]
- Li, Y. Research on Jamming and Anti-Jamming about Satellite Navigation Receiver with Array Antenna; Xidian University: Xi’an, China, 2017; pp. 19–27. [Google Scholar]
- Huang, L.; Lu, Z.; Ren, C.; Liu, Z.; Xiao, Z.; Song, J.; Li, B. Research on Detection Technology of Spoofing under the Mixed Narrowband and Spoofing Interference. Remote Sens. 2022, 14, 2506. [Google Scholar] [CrossRef]
- Moussa, M.; Osman, A.; Tamazin, M.; Korenberg, M.; Noureldin, A. Enhanced GPS narrowband jamming detection using high-resolution spectral estimation. GPS Solut. 2017, 21, 475–485. [Google Scholar] [CrossRef]
- Gong, Y.; Wang, L.; Yao, R.; Zhang, Z. A Robust Method to Suppress Jamming for GNSS Array Antenna Based on Reconstruction of Sample Covariance Matrix. Int. J. Antennas Propag. 2017, 2017, 9764283. [Google Scholar] [CrossRef]
- Wu, R.; Dong, J.; Wang, M. Wearable Polarization Conversion Metasurface MIMO Antenna for Biomedical Applications in 5 GHz WBAN. Biosensors 2023, 13, 73. [Google Scholar] [CrossRef] [PubMed]
- Fan, G.; Tang, X.; Nie, J.; Huang, Y.; Sun, G. A Zero Bias Frequency-Domain Jamming Suppressor for GNSS Receivers. IEICE Trans. Commun. 2016, 99, 2081–2086. [Google Scholar] [CrossRef]
- Pan, Y.; Dong, J. Design and optimization of an ultrathin and broadband polarization-insensitive fractal FSS using the improved bacteria foraging optimization algorithm and curve fitting. Nanomaterials 2023, 13, 191. [Google Scholar] [CrossRef]
- Huo, S.; Nie, J.; Tang, X.; Wang, F. Minimum Energy Block Technique Against Pulsed and Narrowband Mixed Interferers for Single Antenna GNSS Receivers. IEEE Commun. Lett. 2015, 19, 1933–1936. [Google Scholar] [CrossRef]
- Betz, J.W.; Kolodziejski, K.R. Generalized Theory of Code Tracking with an Early-late Discriminator Part 1 Lower Bound and Coherent Processing. IEEE Trans. Aerosp. Electron. Syst. 2009, 45, 1538–1550. [Google Scholar] [CrossRef]
- Betz, J.W.; Kolodziejski, K.R. Generalized Theory of Code Tracking with an Early-late Discriminator Part 2 Noncoherent Processing and Numerical Results. IEEE Trans. Aerosp. Electron. Syst. 2009, 45, 1551–1564. [Google Scholar] [CrossRef]
- Bek, M.K.; Shaheen, E.M.; Elgamel, S.A. Classification and Mathematical Expression of Different Jamming Signals on a GPS Receiver. Navigation 2015, 62, 23–37. [Google Scholar] [CrossRef]
- Balaei, A.T.; Dempster, A.G.; Presti, L.L. Characterization of the Effects of CW and Pulse CW Jamming on the GPS Signal Quality. IEEE Trans. Aerosp. Electron. Syst. 2009, 45, 1418–1431. [Google Scholar] [CrossRef]
- Jaegyu, J.; Matteo, P.; Bernd, E. CW Jamming Effects on Tracking Performance of GNSS Receivers. IEEE Trans. Aerosp. Electron. Syst. 2012, 48, 243–258. [Google Scholar] [CrossRef]
- Bek, M.K.; Shaheen, E.M.; Elgamel, S.A. Mathematical analyses of pulse jamming signal on post-correlation carrier-to-noise ratio for the global positioning system receivers. IET Radar Sonar Navig. 2015, 9, 266–275. [Google Scholar] [CrossRef]
- Hu, X.; Liu, Y.; Ran, Y.; Ke, T. Tracking performance evaluation of GNSS signals in CW jamming. J. Huazhong Univ. Sci. Technol. 2010, 38, 5–8. [Google Scholar]
- Zhang, J.; Lohan, E.S. Effect of Narrowband Jamming on Galileo E1 Signal Receiver Performance. Int. J. Navig. Obs. 2011, 2011, 959871. [Google Scholar] [CrossRef]
- Zhang, K.; Zeng, F.; Ou, X.; Zhao, Y. Analysis of GPS Blanket Jamming Effects. Commun. Technol. 2018, 51, 2544–2548. [Google Scholar]
- Mojtaba, H.; Hamid, R.; Mahmood, S. Robust adaptive beamforming in impulsive noise environments. IET Radar Sonar Navig. 2019, 13, 2145–2150. [Google Scholar]
- Cheng, L.; Zhang, S.; Zeng, F. A Study on Optimized Deployment of Satellite Navigation Jammers. Fire Control Command Control 2015, 40, 43–46. [Google Scholar]
- Huang, Y.; Huang, L. Design and Simulation of the Algorithm on the Distribution and Coverage of GPS Jamming Shells. In Proceedings of the International Conference on Intelligent Networks & Intelligent Systems, Shenyang, China, 1–3 November 2010; pp. 634–637. [Google Scholar]
- Yang, E.; Erdogan, A.; Arslan, T.; Barton, N. Multi-objective evolutionary optimizations of a space-based reconfigurable sensor network under hard constraints. Soft Comput. A Fusion Found. Methodol. Appl. 2011, 15, 25–36. [Google Scholar] [CrossRef]
- Quintao, F.; Nakamura, F.; Mateus, G. Evolutionary algorithm for the dynamic coverage problem applied to wireless sensor networks design. In Proceedings of the 2005 IEEE Congress on Evolutionary Computation, Edinburgh, UK, 2–5 September 2005; pp. 21–25. [Google Scholar]
- Yan, Z.; Wu, D.; Jiang, W.; Liu, H.; Mao, H. Deployment of Aerial Jammers in Network-Type GPS Jamming System. Electron. Opt. Control 2013, 20, 37–39. [Google Scholar]
- Fu, Y.; Zhu, K.; Han, Q.; Xu, Y. A deployment method of navigation signal jammers. J. Navig. Position. 2020, 8, 110–114. [Google Scholar]
- Ni, S.; Cui, J.; Cheng, N.; Liao, Y. Detection and elimination method for deception jamming based on an antenna array. Int. J. Distrib. Sens. Netw. 2018, 14, 1550147718774466. [Google Scholar] [CrossRef]
- Todd, E.; Brent, M.; Mark, L.; Brady, W.; Paul, M. Assessing the Spoofing Threat Development of a Portable GPS Civilian Spoofer. In Proceedings of the 21st International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS 2008), Savannah, GA, USA, 16–19 September 2008; pp. 1–6. [Google Scholar]
- Todd, H.; Jahshan, B.; Daniel, S.; Kyle, W. The Texas Spoofing Test Battery Toward a Standard for Evaluating GPS Signal Authentication Techniques. In Proceedings of the International Technical Meeting of Satellite Division of the Institute of Navigation, Nashville, TN, USA, 17–21 September 2012; pp. 1–7. [Google Scholar]
- Hanlon, B.; Psiaki, M.; Humphreys, T.; Bahatti, J.A. Real-Time Spoofing Detection Using Correlation Between Two Civil GPS Receivers. In Proceedings of the International Technical Meeting of Satellite Division of the Institute of Navigation, Nashville, TN, USA, 17–21 September 2012; pp. 2–4. [Google Scholar]
- He, L.; Li, W.; Guo, G. Study on GPS generated spoofing attacks. Appl. Res. Comput. 2016, 33, 2405–2408. [Google Scholar]
- Sheng, Y.; Li, H.; Zhou, S.; Zhang, B. Research of GPS Generated Spoofing Method. Foreign Electron. Meas. Technol. 2018, 37, 39–43. [Google Scholar]
- He, X.; Liao, K.; Peng, S.; Tian, Z.; Huang, J. Interrupted-Sampling Repeater Jamming-Suppression Method Based on a Multi-Stages Multi-Domains Joint Anti-Jamming Depth Network. Remote Sens. 2022, 14, 3445. [Google Scholar] [CrossRef]
- Wang, H.; Yao, Z.; Fan, Z.; Zheng, T. A Negative Time-delay Correction Method for Repeater Deception Jamming Signal. Telecommun. Eng. 2015, 55, 1255–1259. [Google Scholar]
- Guo, Y.; Wu, M.; Tang, K.; Tie, J.; Li, X. Covert Spoofing Algorithm of UAV Based on GPS/INS-Integrated Navigation. IEEE Trans. Veh. Technol. 2019, 68, 6557–6564. [Google Scholar] [CrossRef]
- Zhen, C.; Wang, Q.; Jiang, Y.; Wang, X. Time Delay Control Method for GNSS Repeater Deception Jamming. Mod. Navig. 2022, 13, 79–84. [Google Scholar]
- Daniel, P.S.; Jahshan, A.B.; Todd, E.H.; Aaron, A.F. Evaluation of smart grid and civilian UAV vulnerability to GPS spoofing attacks. In Proceedings of the International Technical Meeting of Satellite Division of the Institute of Navigation, Nashville, TN, USA, 17–21 September 2012; pp. 1–15. [Google Scholar]
- Costa, F.; Glauberto, L.; Silveira, L.F.; Valderrama, C.; Xavier-de-Souza, S. Variance-Triggered Two-Step GPS Acquisition. Sensors 2019, 19, 3177. [Google Scholar] [CrossRef]
- Kim, T.; Sin, C.S.; Lee, S. Analysis of Effect of Spoofing Signal in GPS Receiver. In Proceedings of the 12th International Conference on Control Automation and Systems, Jeju, Republic of Korea, 17–21 October 2012; pp. 2083–2087. [Google Scholar]
- Yan, Z.; Wu, D.; He, J.; Liu, H.; Mao, H. Deployment Method of Jammer in GPS Repeater Deception Jamming. Mod. Radar 2015, 37, 375–379. [Google Scholar]
- Ali, J.J.; Ali, B.; John, N.; Gérard, L. GPS Spoofer Countermeasure Effectiveness Based on Signal Strength Noise Power and C/N0 Measurements. Int. J. Satell. Commun. Netw. 2012, 30, 181–191. [Google Scholar]
- Pang, J.; Nie, S.; Nie, J.; Ou, G. An Overview to GNSS Spoofing Technologies. Fire Control Command Control 2016, 41, 1–4. [Google Scholar]
- Wang, H.; Yao, Z.; Fan, Z.; Zhen, T. Experiment Study of Spoofing Jamming on GPS Receiver. Fire Control Command Control 2016, 41, 184–187. [Google Scholar]
- Liu, Y.; Sun, W.; Yan, S. Efficiency Analysis of Repeater Deception Jamming GPS Repeater. J. Air Force Radar Acad. 2004, 4, 44–46. [Google Scholar]
- Tippenhauer, N.O.; Pöpper, C.; Rasmussen, K.B.; Čapkun, S. On the Requirements for Successful GPS Spoofing Attacks. In Proceedings of the 18th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 17–21 October 2011; pp. 1–11. [Google Scholar]
- Ma, K.; Sun, X.; Nie, Y. Research on Key Technologies of GPS Generated Spoofing. Aerosp. Electron. Warf. 2014, 30, 624–626. [Google Scholar]
- Hu, Y.; Bian, S.; Cao, K.; Feng, G. Spoofing power control strategy for GNSS receiver. J. Chin. Inert. Technol. 2015, 23, 207–210. [Google Scholar]
- Humphreys, T.E.; Ledvina, B.M.; Psiaki, M.L.; O’Hanlon, B.W.; Kintner, J.P. Assessing the Spoofing Threat. GPS World 2009, 20, 28–38. [Google Scholar]
- Lv, H.; Zhai, J.; Wang, W. The Spoofing Threat and Anti-Spoofing Measurements Analysis for Satellite Navigation Receiver. In Proceedings of the Fourth China Satellite Navigation Academic Annual Conference, Wuhan, China, 15–17 May 2013; pp. 1–5. [Google Scholar]
- Kerns, A.; Shepard, D.; Bhatti, J.; Humphreys, T. Unmanned aircraft capture and control via GPS spoofing. J. Field Robot. 2014, 31, 617–636. [Google Scholar] [CrossRef]
- Ali, B.; Ali, J.; Vahid, D.; John, N.; Gerard, L. GNSS spoofing detection in handheld receivers based on signal spatial correlation. In Proceedings of the 2012 IEEE/ION Position, Myrtle Beach, SC, USA, 23–26 April 2012; pp. 1–4. [Google Scholar]
- Psiaki, M.; Hanlon, B.; Bhatti, J.; Shepard, D.; Humphreys, T. GPS Spoofing Detection via Dual-Receiver Correlation of Military Signals. IEEE Trans. Aerosp. Electron. Syst. 2013, 49, 2250–2267. [Google Scholar] [CrossRef]
- Humphreys, T. Detection Strategy for Cryptographic GNSS Anti-Spoofing. Aerosp. Electron. Syst. IEEE Trans. 2013, 49, 1073–1090. [Google Scholar] [CrossRef]
- Kyle, W.; Daniel, S.; Todd, H. Straight Talk on Anti-Spoofing Securing the Future of PNT. GPS World 2012, 23, 32–43. [Google Scholar]
- Todd, E.; Jahshan, A.; Brent, M. The GPS Assimilator a Method for Upgrading Existing GPS User Equipment to Improve Accuracy Robustness and Resistance to Spoofing. In Proceedings of the International Technical Meeting of Satellite Division of the Institute of Navigation, Portland, OR, USA, 21–24 September 2010; p. 13. [Google Scholar]
- Kyle, D.; Daniel, P.; Jahshan, A.; Todd, E. An Evaluation of the Vestigial Signal Defense for Civil GPS Anti-Spoofing. In Proceedings of the International Technical Meeting of Satellite Division of the Institute of Navigation, Portland, OR, USA, 20–23 September 2011; Volume 4, pp. 2–6. [Google Scholar]
- Gao, Y.; Li, H.; Lu, M.; Feng, Z. Intermediate Spoofing Strategies and Countermeasures. Tsinghua Sci. Technol. 2013, 18, 599–605. [Google Scholar]
- Huang, L.; Lv, Z.; Wang, F. Spoofing Pattern Research on GNSS Receivers. J. Astronaut. 2012, 33, 884–890. [Google Scholar]
- Li, B.; Zhu, Y.; Cao, K.; Li, S.; Li, J. Modeling and Test on Spoof Jamming for Beidou Navigation Signal. J. Nav. Univ. Eng. 2019, 31, 23–27. [Google Scholar]
- Zhang, L.; Zhang, C.; Gao, Y. GNSS Spoofing and Detection(I): Typical Events and Development of Spoofing Technology. J. Navig. Position. 2021, 9, 1–7. [Google Scholar]
- Liu, Q.; Cheng, Y.; Wang, G.; Ma, Y.; Chen, S. Discussion on Deception and Anti-deception Technology of Beidou Satellite Navigation. Navig. Control 2021, 20, 24–32. [Google Scholar]
- Zhang, S.; Cheng, L.; Wang, B. Efficiency Analysis of Jamming on Cruise Missile Guided by GPS. Fire Control Command Control 2015, 40, 66–69. [Google Scholar]
- Liu, Y. INS/GNSS Integrated Navigation System Spoofing Detection Techniques; Northwestern Polytechnical University: Xian, China, 2019; pp. 17–40. [Google Scholar]
- Zhen, Y. Research on Deceptive Jamming Strategy of Satellite Navigation Receiver and Its Performance Evaluation; Hebei University of Science & Technology: Shijiazhuang, China, 2019; pp. 53–57. [Google Scholar]
- Wang, Y.; Hao, J.; Liu, W.; Wang, X.; Gao, Y. Indicator Detection Method of Spoofing Effectiveness of GNSS. Geomat. Spat. Inf. Technol. 2019, 42, 51–56. [Google Scholar]
- Wang, Y. Evaluation Indexes and Evaluation Methods of GNSS Spoofing Efficacy; Information Engineering University: Zhengzhou, China, 2020; pp. 23–74. [Google Scholar]
- Yang, J.; Zeng, F.; Sheng, H.; Zhu, L. A Jamming System Through Section Mapping for GPS Navigation. Chin. J. Electron. 2005, 33, 1036–1038. [Google Scholar]
- Zhang, S.; Yang, J.; Pan, G.; Zeng, F. GPS Inducing Jamming System through a Single Transmitter. Mod. Radar 2010, 32, 19–22. [Google Scholar]
- Zhen, S.; Zhen, Z.; Cao, Y. Single-station Forwarding Spoofing Scheme Based on Time Delay. Mod. Radar 2010, 9, 963–968. [Google Scholar]
- Zhang, S.; Miao, M.; Hou, S.; Han, Z.; Peng, D. A Study on the Performance Between Multi-transmitters and Single Transmitter GPS Inducing System. Mod. Radar 2013, 35, 11–15. [Google Scholar]
- Wan, Y.; Ma, P.; Nie, J.; Sun, G. Study of Multi-Station Retransmission Spoofing Methods Based on Protection of Fixed Target. GNSS World China 2016, 41, 60–65. [Google Scholar]
| Signal Processing | Basic Indicator |
|---|---|
| Signal acquisition | Signal acquisition time |
| Signal acquisition sensitivity | |
| Signal acquisition probability | |
| Signal tracking | Number of channels |
| Pseudo-range precision | |
| Tracking sensitivity | |
| Signal demodulation | Error rate |
| Signal positioning | Positioning accuracy |
| Influence Factor | Efficiency Evaluation Index |
|---|---|
| Influence of jamming on signal acquisition | Relationship between jamming-to-signal ratio and acquisition probability |
| Relationship between jamming-to-signal ratio and the first acquisition time of the signal | |
| Influence of jamming on signal tracking | Relationship between jamming-to-signal ratio and pseudo-range accuracy |
| Influence of jamming on signal demodulation | Relationship between jamming-to-signal ratio and error rate |
| Influence of jamming on signal positioning | Relationship between jamming-to-signal ratio and positioning accuracy |
| Deception Type | Advantage | Disadvantage | Scope of Applications |
|---|---|---|---|
| Generated deception Jamming [50,51,52,53] | High flexibility and controllable parameters | Unable to deceive military code signal | Civilian signal deception |
| Repeater deception Jamming [56,57] | Can deceive military code signals | Low success rate of deception | Military signal deception |
| Implementation Stage | Advantage | Disadvantage | Research Focus |
|---|---|---|---|
| Signal acquisition stage | Implementation is relatively simple | Relatively poor concealment | The power control [63,64,65,66,67] The deception strategy [53,63,68,69,70,71] |
| Signal tracking stage | Relatively better concealment | Implementation is relatively difficulty | The traction deception technology [49,52,67,71,79] |
| Implementation Difficulty | Deceptive Effect | Deception Scope | Deception Cost |
|---|---|---|---|
| Primary deception | Poor | Wide | High |
| Intermediate deception | Medium | Narrow | Higher |
| Advanced deception | High | Narrower | Highest |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, X.; Chen, L.; Lu, Z.; Wang, F.; Liu, W.; Xiao, W.; Liu, P. Overview of Jamming Technology for Satellite Navigation. Machines 2023, 11, 768. https://doi.org/10.3390/machines11070768
Li X, Chen L, Lu Z, Wang F, Liu W, Xiao W, Liu P. Overview of Jamming Technology for Satellite Navigation. Machines. 2023; 11(7):768. https://doi.org/10.3390/machines11070768
Chicago/Turabian StyleLi, Xiangjun, Lei Chen, Zukun Lu, Feixue Wang, Wenxiang Liu, Wei Xiao, and Peiguo Liu. 2023. "Overview of Jamming Technology for Satellite Navigation" Machines 11, no. 7: 768. https://doi.org/10.3390/machines11070768
APA StyleLi, X., Chen, L., Lu, Z., Wang, F., Liu, W., Xiao, W., & Liu, P. (2023). Overview of Jamming Technology for Satellite Navigation. Machines, 11(7), 768. https://doi.org/10.3390/machines11070768






