Abstract
This research explores the interplay between violator spaces and greedoids—two distinct theoretical frameworks developed independently. Violator spaces were introduced as a generalization of linear programming, while greedoids were designed to characterize combinatorial structures where greedy algorithms yield optimal solutions. These frameworks have, until now, existed in isolation. This paper bridges the gap by showing that greedoids can be defined using a modified violator operator. The established connections not only deepen our understanding of these theories but also provide a new characterization of antimatroids.
MSC:
52A01; 52B40 (primary); 90C05 (secondary)
1. Preliminaries
The primary objective of the paper is to establish connections between two combinatorial concepts: violator spaces and greedoids. Violator spaces emerged as a generalization of Linear Programming (LP) problems. LP-type problems were introduced and studied by Matoušek, Sharir, and Welzl [1,2] as a combinatorial framework encompassing linear programming and other computational geometric problems. Subsequently, Matoušek [3] introduced violator spaces as a simpler framework that generalizes LP-type problems. Violator spaces provide an abstract structure that facilitates the formulation and design of efficient algorithms for solving optimization problems across diverse areas, such as computational geometry [4], computational algebra [5], and machine learning [6].
Greedoids were introduced in an effort to characterize combinatorial structures where the greedy algorithm yields optimal solutions [7,8]. Numerous examples of greedoids appear in various areas of mathematics [9,10]. This work explores the relationships between violator spaces and greedoids, showing that greedoids can be defined using a variant of the violator operator. These interrelations provide a new characterization of antimatroids.
2. Violator Spaces
Definition 1
([3]). A violator space is a pair , where E is a finite set and ν is a violator operator, i.e., a mapping , such that for all subsets the following properties are satisfied:
V1: (consistency);
V2: and (locality).
Let be a violator space. Let . So, if is defined by (3) then
Theorem 1
([11]). Let E be a finite set and two mappings, such that for all . Then, is a violator space if and only if φ satisfies
C1: (extensivity);
C2: (self-convexity).
Thus, we have two equivalent approaches to defining violator spaces:
- the classic one—, where the ground set E is equipped with the mapping satisfying consistency and locality;
- the dual one—, where the ground set E is equipped with the mapping satisfying extensivity and self-convexity.
In what follows, a pair , where E is a finite set and is a mapping satisfying extensivity and self-convexity, will be considered a violator space as well.
Since a violator operator is extensive it may be interpreted as a type of a “closure” operator. The concept of closure appears in many disciplines, including topology, algebra, logic, geometry, convexity analysis, graph theory, etc. It is also known by other names, such as span, hull, and envelope. For instance, the convex hull operator on the Euclidean space is a classic example of a closure operator.
Definition 2.
Let E be a finite set; is a closure operator on E if for all subsets the following properties are satisfied:
CL1: (extensivity);
CL2: (isotonicity);
CL3: (idempotence).
It is proved that every closure operator is a violator operator, since isotonicity and idempotence imply self-convexity, and extensivity with self-convexity implies idempotence [11]. However, not each violator operator is a closure operator, since it does not have to satisfy isotonicity.
Let us consider some additional properties of violator operators.
Lemma 1.
Let be a violator space. Then, for all .
Proof.
“If”: Let . Since extensivity implies , we conclude with .
“Only if”: If then . Hence, by self-convexity, . □
Proposition 1.
Let E be a finite set. For each extensive operator self-convexity is equivalent to the following property:
C22: for all .
Proof.
1. C2 ⇒ C22: From Lemma 1 . Hence, .
2. C22 ⇒C2: (from extensivity). Then, C22 implies . □
Lemma 2
([11]). Let be a violator space. Then,
2.1. Uniquely Generated Violator Spaces
Let be an arbitrary space with the operator . is a generator of if . A basis of X is an inclusion-minimal set (not necessarily included in X) with . A space is uniquely generated if every set has a unique basis.
Proposition 2
([11]). A violator space is uniquely generated if and only if for every
It is known that a closure operator is uniquely generated if and only if it satisfies the anti-exchange property [10,12,13]:
We extend this characterization to violator spaces in the following:
Theorem 2
([11]). Let be a violator space. Then, is uniquely generated if and only if the operator φ satisfies the anti-exchange property.
An element x of a subset is an extreme point of X if . The set of extreme points of X is denoted by .
Proposition 3
([11]). For violator spaces: if and only if .
Theorem 3
([11]). Let be a violator space. Then, is uniquely generated if and only if for every set , .
Corollary 1
([11]). Let be a uniquely generated violator space. Then, for every the set is the unique basis of X.
2.2. LP-Type Problems
A different way to define violator spaces, consistent with their historical development, is through their introduction as a framework that generalizes LP-type problems.
An LP-type problem is defined by a finite set E of constraints and a value associated with every subset . These values can be real numbers or elements of any other linearly ordered set. The mapping must satisfy the axioms outlined in the following definition.
Definition 3
([3]). An LP-type problem is a quadruple , where E is a finite set, W is a set linearly ordered by ≤, and w is a mapping , such that for all subsets the following properties are satisfied:
V11: (monotonicity);
V22: for all , if and there exists such that then (locality).
A classic example of an LP-type problem is the computation of the smallest circle that contains all of a given finite set of points in the Euclidean plane. In this case, E represents a set of points in the plane, and is the radius of the smallest circle that encloses all points of X. Monotonicity of w is straightforward. To demonstrate locality, observe that for if then X and Y share the same smallest enclosing circle. If then a lies outside this circle, which, in turn, means .
For an LP-type problem and for , a basis of X is an inclusion-minimal subset B of X with . Solving an LP-type problem means identifying a basis of E.
Let us again illustrate this, using the smallest circle problem. A basis of X is a minimal subset of points that share the same enclosing circle as X. Specifically, all points in this basis lie on the boundary of the circle.
The set of all constraints violating , denoted as , is defined as
This set includes all elements a in the ground set E that are not in X and, when added to X, cause the objective function w to increase. For the smallest circle problem, the violated constraints of X are precisely the points that lie outside the smallest enclosing circle of X.
One can see that the condition generally does not suffice for . For example [3], if for all then any X of the same size will have the same ; however, , and so no distinct sets X share the value of . Thus, we can see that w by itself does not capture the combinatorial structure of the problem. To describe the “structure” of an LP-type problem Matoušek et al. [3] introduced the concept of a violator space and proved that every LP-type problem can naturally be converted into a violator space with violator mapping but that the reverse is not necessarily true.
Proposition 4
([3]). Consider an LP-type problem , and let ν be its violator mapping defined by (3). Then, is a violator space and is basis-equivalent to .
Take a small example, to illustrate how LP-type systems really create a violator space and bases.
Example 1.

Build the simplest LP-type system whose atoms a, b, c, d have weights 1, 2, 2, 3, respectively. The full definition of the function w, the corresponding function ν, and the bases are shown in Table 1.

Table 1.
An example involving four elements.
It is easy to see that the operator w is monotone and satisfies locality. It is not a uniquely generated space, since the subsets and each have two bases.
In the previous example, the violator operator is also a closure operator, as it is monotone. Consider another example, which encapsulates all the previous definitions and illustrates the basic concepts of LP-type problems.
Example 2.

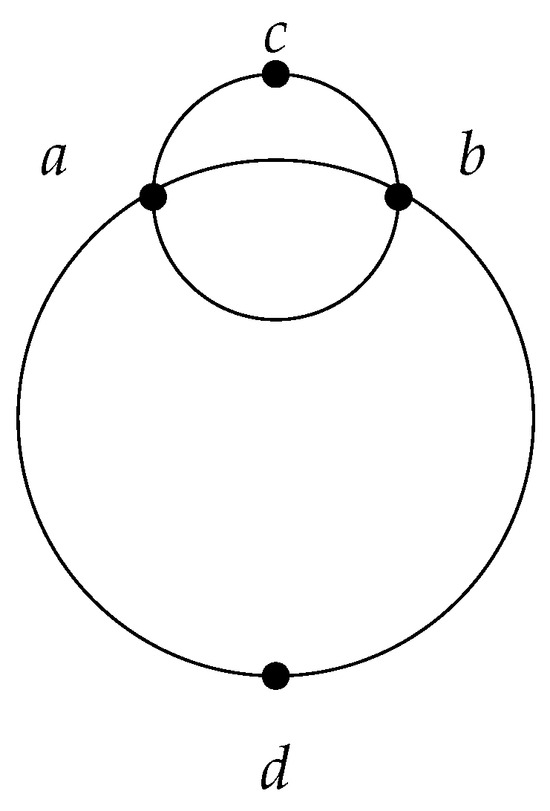
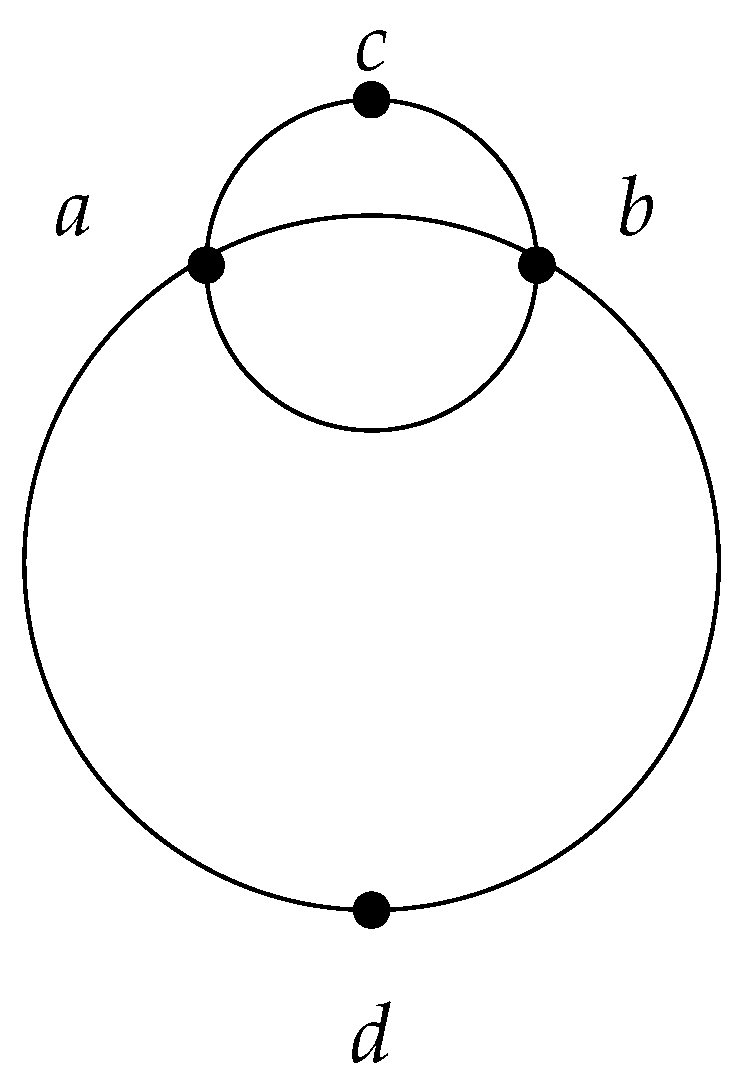
Let be four points in the Euclidean plane, such that point c lies on the boundary of the circle passing through points a and b.
Let us sort the radii of the enclosing circles by size. For each point from E, the radius of its circle is 0. The radius of the circle that encloses the pair of points or is half the distance between the two points. The radius of the circle that encloses both points a and b is equal to the radius of the circle that encloses all three points a, b, and c, making it the third-largest radius. The next-largest radius is for the pairs and , and so on.
The full definitions of the function w and the corresponding functions ν and φ are shown in Table 2.

Table 2.
An example of four points in a coordinate system.
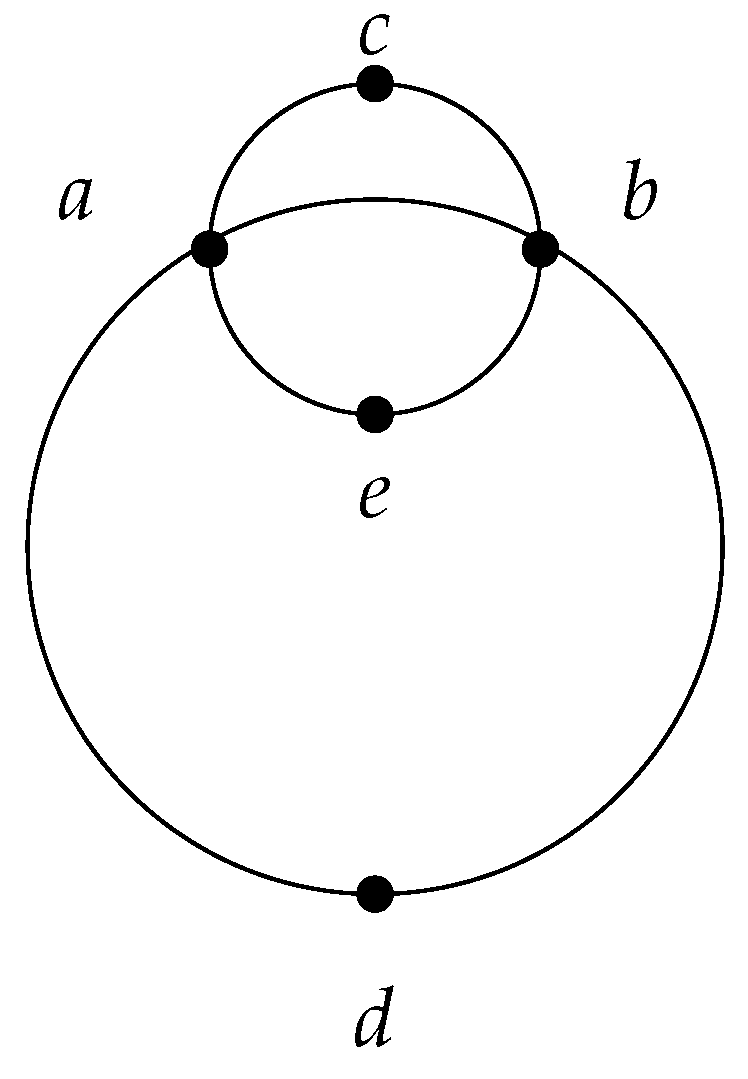
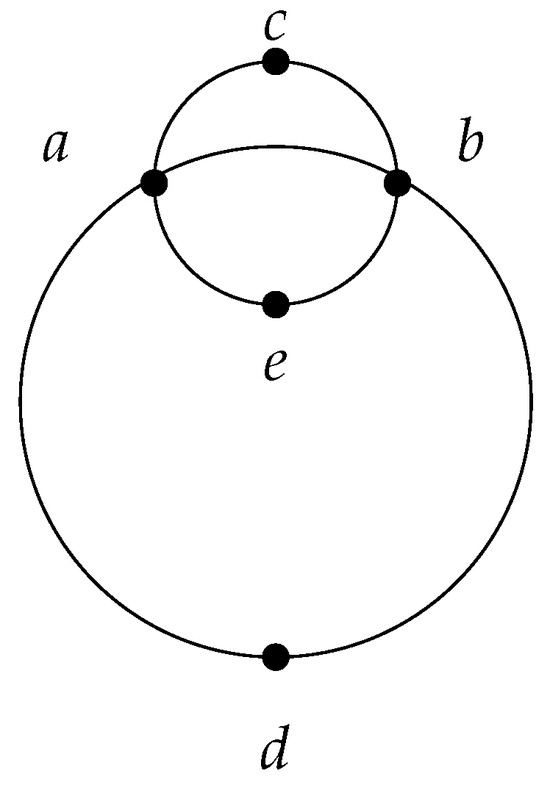
It is easy to see that the operator w is monotone and satisfies locality. However, the operator does not satisfy monotonicity. Indeed, while , (see Table 1 and Figure 1). From this example, we can also gain a better understanding of the notion of basis. Thus, the basis of the subset is the pair , and the basis of E is a pair . Note that a unique basis is not always guaranteed. If we add another point e on the circle passing through points , exactly opposite point c, we obtain two bases for : the pair and the pair (see Figure 2).

Figure 1.
An example of four points in a coordinate system.

Figure 2.
An example of five points in a coordinate system.
3. Greedoids
The concept of a greedoid was introduced by Bernhard Korte and László Lovász around 1980 as a way to generalize the notion of structures that can be optimized using greedy algorithms [7].
Definition 4.
A set system is a greedoid if the following properties are satisfied:
(i) ;
(ii) , such that (augmentation property).
Elements of are called feasible sets.
The rank function of a greedoid is defined as follows:
Theorem 4
([10]). A function is the rank function of a greedoid if and only if for all and all the following conditions hold:
(1.1)
(1.2) (subcardinality)
(1.3) implies (monotonicity)
(1.4) implies (local submodularity).
Moreover, the greedoid is uniquely determined by its rank function:
So, the pair may be considered as a greedoid with defined by (4).
3.1. LP-Type Problems and Greedoids
The rank function r of a greedoid satisfies all the properties of the mapping w of an LP-type problem. It is monotone (Theorem 4) and satisfies the locality.
Proposition 5.
Let be a greedoid with rank function r. Then, and implies for all and .
Proof.
If and there is a maximal feasible set , with . In addition, there is a feasible set , with . Since A is a maximal feasible set in Y, , and . Then (from the augmentation property), there exists for which . Since A is a maximal feasible set in Y, , and so , i.e., is a feasible set, and then . □
Thus, each greedoid may be considered as an LP-type problem .
Note that the family is the family of all the bases of an LP-type problem, since for each proper subset A of a feasible set,
However, if the bases of an LP-type problem form a greedoid, a function w does not have to be a greedoid’s rank function. For example, every monotone function w with different values on each element of turns all subsets of E to bases. While the bases constitute a greedoid, a function w does not have to satisfy subcardinality.
Let us build a specific LP-type problem , where E is a finite set and w is a mapping , such that for all subsets the following properties are satisfied:
(1) ;
(2) (subcardinality);
(3) implies (monotonicity);
(4) For all if and there exists such that then (locality).
The property (4) may be reformulated as follows:
(5) For all and with and we have .
Proposition 6.
Let w be a monotone mapping on . Then, locality (5) is equivalent to local submodularity (1.4).
Proof.
1. Let w satisfy locality and . Denote . Then, , and ; then, (from (5)) we have .
2. Let w satisfy local submodularity, , , , and . By repeatedly applying local submodularity we prove that . It is easy to see that the proposition is correct for . Let . From monotonicity it follows that . Hence, . Local submodularity implies . Denote .
Prove by induction on n that for each . From monotonicity it follows that for each . Then, implies . Thus, . □
In fact, the property of local submodularity may be extended as follows.
Corollary 2.
If such that then .
Theorem 4 implies that an LP-type problem with mapping and determines a greedoid by .
3.2. Violator and Rank Closure Operators on Greedoids
Define (rank) closure operator of greedoids ([10]): . The operator is extensive () and idempotent (), but it does not have to be an isotone operator. So, is not always a closure operator. At the same time, the definition of coincides with the definition of a violator operator (1). The following theorem supports the interpretation of greedoids as a subclass of violator spaces, since Properties (i) and (ii) define a violator operator.
Theorem 5
([14]). A mapping is the closure operator of some greedoid if and only if
(i)
(ii)
(iii) if for all and then .
Moreover, if σ satisfies (i), (ii), and (iii) then
.
Based on the definition of extreme points, we have
Then, the following condition for all is equivalent to , and so the property (iii) may be rewritten as follows:
Define —the family of bases with respect to operator .
Proposition 7.
for each violator operator σ.
Proof.
If , i.e., for all then for all holds , and so (from Proposition 3) . Then, . If then there exists , such that . Hence, for each self-convexity implies , i.e., . This concludes the proof, with . □
It is worth mentioning that Property (iii) is not necessary for to be a greedoid.
Example 3.
Let . Define for each except . It is easy to check that the space is a uniquely generated violator space (it satisfies both extensivity and convexity) where the family of bases forms a greedoid. At the same time, operator φ does not satisfy (5), which is equivalent to (iii). Indeed, if then , , but .
If we consider the rank function of the greedoid, we can see that , and so . Then, for this function σ the property (iii) holds and we have a not-uniquely-generated violator space.
Thus, the same family of bases may be obtained by different mappings.
3.3. Antimatroids—Uniquely Generated Greedoids
An antimatroid is a combinatorial structure related to the concept of a greedoid, and it describes a process where elements are added to a set in a sequential manner, subject to certain constraints. Antimatroids have many applications. Thus, game theory provides a framework in which antimatroids are interpreted as permission structures for coalitions [15]. In mathematical psychology, antimatroids are used to describe the feasible states of knowledge of a human learner [16,17].
Antimatroids have various definitions. We will use the following.
Definition 5.
An antimatroid is a greedoid closed under union.
To provide an equivalent definition, we need to introduce the concept of accessibility.
Definition 6.
An accessible set system is a set system in which every non-empty feasible set contains an element x, such that is feasible.
By definition, the family of feasible sets of a greedoid is an accessible set system.
Lemma 3
([10]). For an accessible set system the following statements are equivalent:
(A1) is an antimatroid
(A2) is closed under union
(A3) implies .
Proposition 8.
An antimatroid is a uniquely generated greedoid.
Proof.
Let be an antimatroid. Since each antimatroid is a greedoid, it remains to prove that the greedoid is uniquely generated. Suppose there are two bases, and , such that . Since is a family of bases then . Hence, , because is an antimatroid. But (see Lemma 2). Contradiction. □
Since, for each greedoid is a violator operator, Theorem 2 implies the following.
Corollary 3.
The operator σ of each antimatroid satisfies the anti-exchange property.
Theorem 6.
The family is an antimatroid if and only if is a uniquely generated greedoid.
Proof.
It remains to be proven that each uniquely generated greedoid is an antimatroid. Suppose but . Then, , and . Contradiction to anti-exchange property. □
4. Conclusions
We have shown that greedoids can be defined using a variant of the violator operator. The connections between violator spaces and greedoids have enabled us to provide a new characterization of antimatroids.
To gain further structural insights into antimatroids, one can explore co-spanning relations. Given an operator , two sets X and Y are co-spanning if . The equivalence relation known as co-spanning has been studied for greedoids [10], and it has been shown that this relation uniquely determines greedoids.
Similar equivalence relations have also been explored for violator spaces [11,18,19]. It is known that violator operators are closed under union (Lemma 2) and satisfy the following property [11]:
which we refer to as convexity, in accordance with Monjardet [20], since this property addresses all sets lying between two given sets.
Based on this property, it was proved [19] that the equivalence classes of a co-spanning relation are closed under union and convex if and only if they arise from a co-spanning relation of a violator space. Moreover, a co-spanning partition to intervals corresponds to a uniquely generated violator space. We extended this approach to antimatroids and convex geometries, with the initial results available in [21]. Further investigation of these structures could lead to new characterizations of antimatroids and other combinatorial structures.
It seems very appealing to generalize our findings to the infinite case. As we see it, topological spaces may provide the main motivation for such a generalization [22].
Author Contributions
Writing—Original draft, Y.K.; Writing—Review and editing, V.E.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
There is no data to be shared for this article.
Acknowledgments
We would like to thank the anonymous reviewers for their helpful suggestions. Special thanks to the reviewer who significantly contributed to the revision of Section 2 by adding examples to illustrate the new concepts.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Matoušek, J.; Sharir, M.; Welzl, E. A subexponential bound for linear programming. Algorithmica 1996, 16, 498–516. [Google Scholar] [CrossRef]
- Sharir, M.; Welzl, E. A combinatorial bound for linear programming and related problems. In STACS 1992—9th Annual Symposium on Theoretical Aspects of Computer Science, Proceedings; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1992; Volume 577, pp. 569–579. [Google Scholar]
- Gärtner, B.; Matoušek, J.; Rüst, L.; Škovroň, P. Violator spaces: Structure and algorithms. Discret. Appl. Math. 2008, 156, 2124–2141. [Google Scholar] [CrossRef]
- Har-Peled, S. Shortest path in a polygon using sublinear space. J. Comput. Geom. 2016, 7, 19–45. [Google Scholar]
- De Loera, J.A.; Petrovic, S.; Stasi, D. Random sampling in computational algebra: Helly numbers and violator spaces. J. Symb. Comput. 2016, 77, 1–15. [Google Scholar] [CrossRef]
- Esposito, G.; Martin, M. A Randomized algorithm for the exact solution of transductive support vector machines. Appl. Artif. Intell. 2015, 29, 459–479. [Google Scholar] [CrossRef]
- Korte, B.; Lovász, L. Mathematical structures underlying greedy algorithms. In Fundamentals of Computation Theory; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1981; Volume 117, pp. 205–209. [Google Scholar]
- Szeszlér, D. Sufficient conditions for the optimality of the greedy algorithm in greedoids. J. Comb. 2022, 44, 287–302. [Google Scholar] [CrossRef]
- Björner, A.; Ziegler, G.M. Introduction to Greedoids. In Matroid Applications; White, N., Ed.; Cambridge University Press: Cambridge, UK, 1992. [Google Scholar]
- Korte, B.; Lovász, L.; Schrader, R. Greedoids; Springer: New York, NY, USA; Berlin/Heidelberg, Germany, 1991. [Google Scholar]
- Kempner, Y.; Levit, V.E. Violator spaces vs. closure spaces. Eur. J. Comb. 2019, 80, 203–213. [Google Scholar] [CrossRef]
- Edelman, P.H.; Jamison, R.E. The theory of convex geometries. Geom. Dedicata 1985, 19, 247–270. [Google Scholar] [CrossRef]
- Pfaltz, J. Closure Lattices. Discret. Math. 1996, 154, 217–236. [Google Scholar] [CrossRef][Green Version]
- Goecke, O.; Korte, B.; Lovász, L. Examples and algorithmic properties of greedoids. In Combinatorial Optimization; Simone, B., Ed.; Lecture Notes in Mathematics; Springer: New York, NY, USA; Berlin/Heidelberg, Germany, 2006; Volume 1403, pp. 113–161. [Google Scholar]
- Algaba, E.; Bilbao, J.M.; van den Brink, R.; Jimenez-Losada, A. Cooperative Games on Antimatroids. Discret. Math. 2004, 282, 1–15. [Google Scholar] [CrossRef]
- Falmagne, J.-C.; Doignon, J.-P. Learning Spaces: Interdisciplinary Applied Mathematics; Springer: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Yoshikawa, H.; Hirai, H.; Makino, K. A representation of antimatroids by Horn rules and its application to educational systems. J. Math. Psychol. 2017, 77, 82–93. [Google Scholar] [CrossRef]
- Brise, Y.; Gärtner, B. Clarkson’s algorithm for violator spaces. Comput. Geom. 2011, 44, 70–81. [Google Scholar] [CrossRef]
- Kempner, Y.; Levit, V.E. Cospanning characterizations of violator and co-violator spaces. In Combinatorics, Graph Theory and Computing. SEICCGTC 2021; Springer Proceedings in Mathematics & Statistics; Hoffman, F., Holliday, S., Rosen, Z., Shahrokhi, F., Wierman, J., Eds.; Springer: Cham, Switzerland, 2024; Volume 448, pp. 109–117. [Google Scholar] [CrossRef]
- Monjardet, B.; Raderanirina, V. The duality between the anti-exchange closure operators and the path independent choice operators on a finite set. Math. Soc. Sci. 2001, 41, 131–150. [Google Scholar] [CrossRef]
- Kempner, Y.; Levit, V.E. Cospanning characterizations of antimatroids and convex geometries. arXiv 2021, arXiv:2107.08556. [Google Scholar]
- Lei, Y.; Zhang, J. Closure system and its semantics. Axioms 2021, 10, 198. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).