Efficient Cancelable Template Generation Based on Signcryption and Bio Hash Function
Abstract
:1. Introduction
1.1. Problem Statement
1.2. Related Studies
1.3. Contributions
- A novel cancelable template generation method is proposed based on signcryption with hyperelliptic curve cryptography.
- The optimal features are extracted using the HGLD (hybrid grey level distance) feature extraction technique.
- The bio hash function is used to convert the cancelable features to bio hash vectors.
- Original biometric templates are converted into cancelable templates with signcryption and bio hash functions.
- The efficiency of the proposed method is compared with the state-of-the-art existing approaches.
2. Materials and Methods
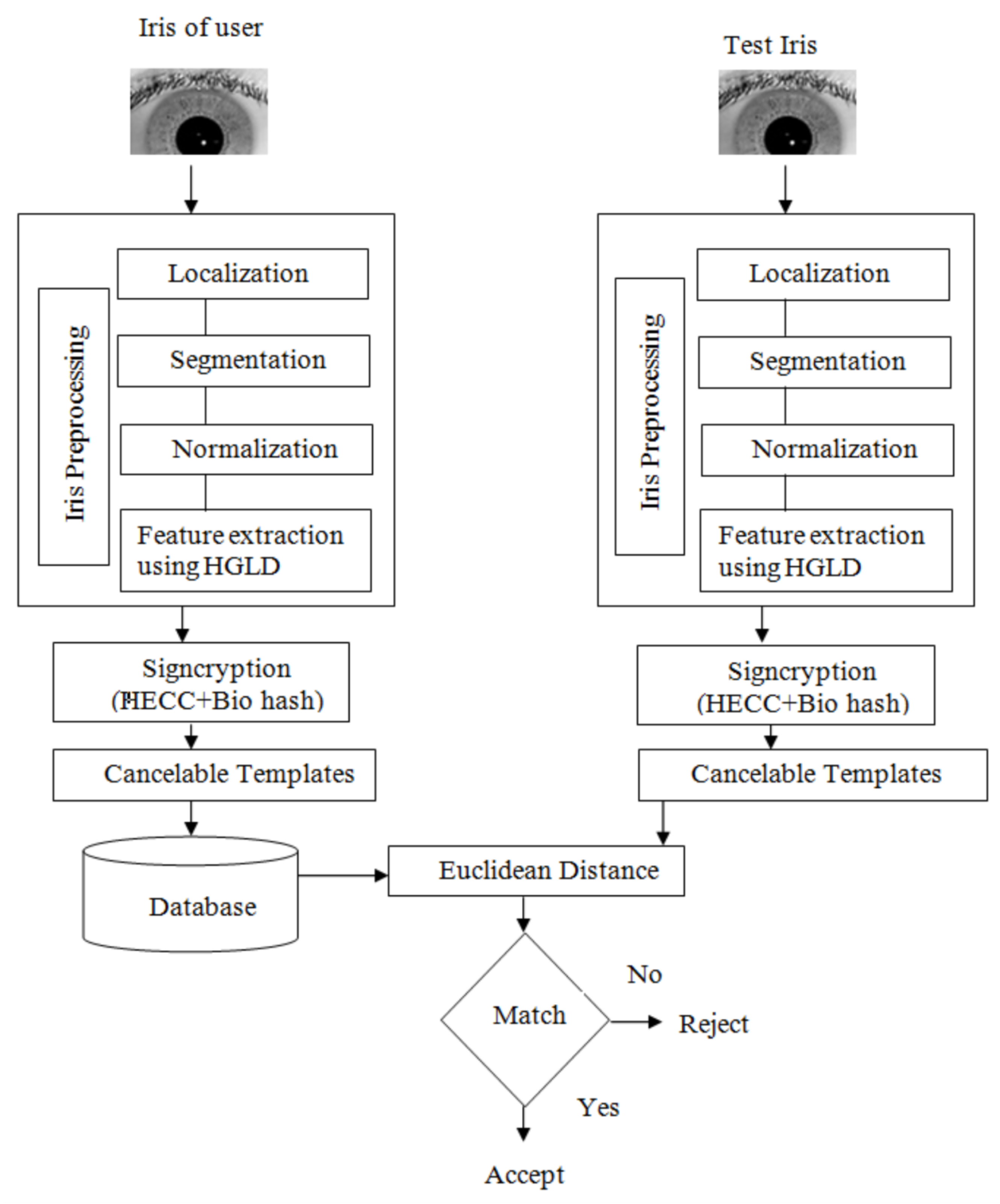
3. Proposed Methodology
3.1. Signcryption
3.2. Iris Pre-Processing
3.2.1. Iris Localization
3.2.2. Iris Segmentation
3.2.3. Iris Normalization
3.2.4. Iris Feature Extraction
3.3. Signcryption for Generating Secure Cancelable Templates
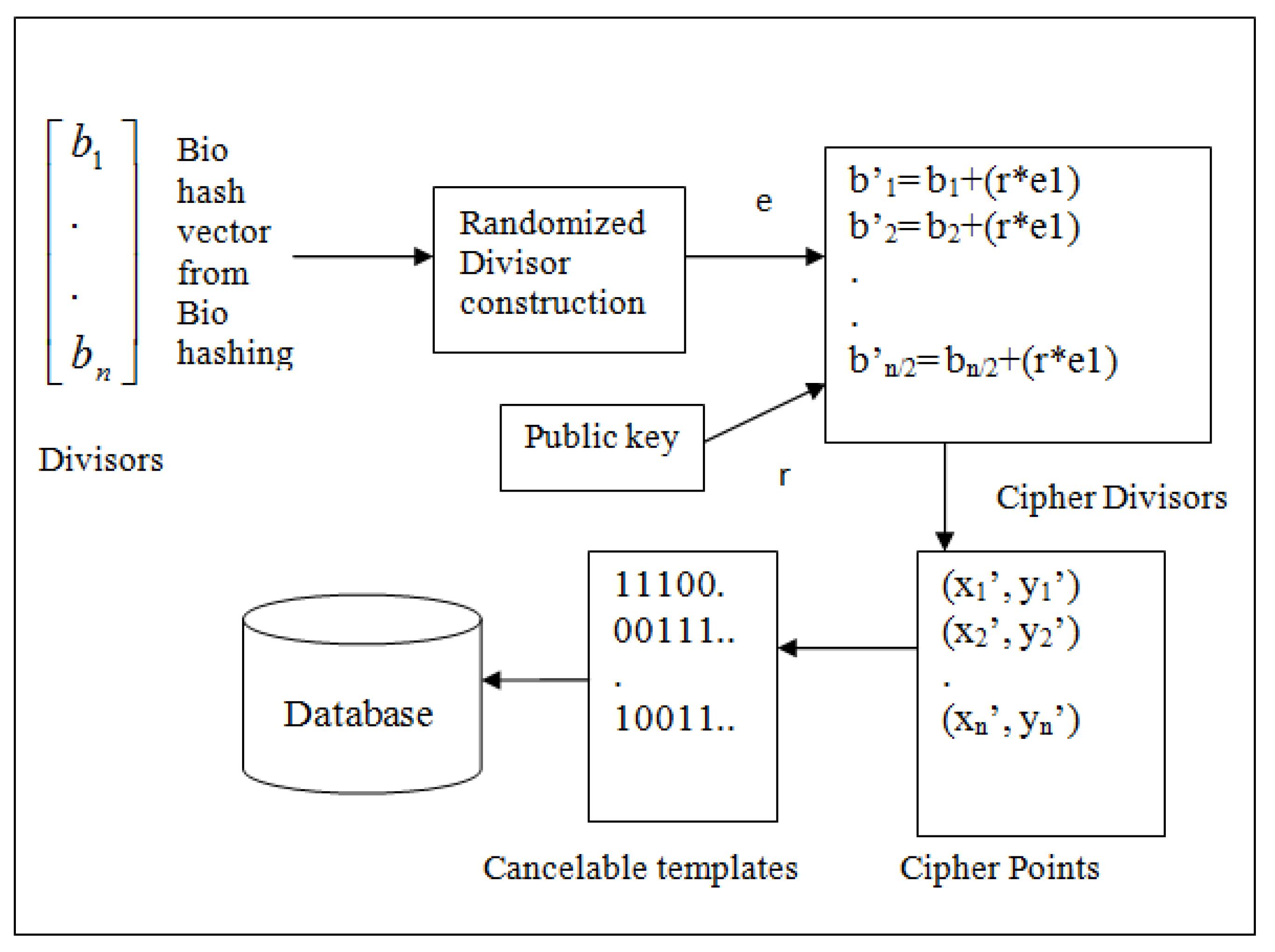
3.3.1. Bio Hashing
| Algorithm 1: Generation of Bio Hash Code through the Bio Hash Function |
|
3.3.2. Signcryption for the Generation of Secure Cancelable Templates
| Algorithm 2: Bio Hash Code Converted into Divisors |
|
4. Results and Discussion
- FAR: It indicates the likelihood that a system would mistakenly accept an unregistered or unauthorized user.
- FRR: It indicates the likelihood that a system may mistakenly reject an unregistered or unauthorized user.
- TPR: It indicates the likelihood that a system will approve the user who has registered in an authentication process. Recall, also known as sensitivity, is the proportion of true positives acquired among the real positives.
- TNR: It indicates the likelihood that a system will reject an unauthorized user. Specificity is another name for it.
- EER: It represents the rate at which FAR and FRR are equivalent.
- Accuracy: The frequency with which the authorized users are given access determines how many tries they make.
4.1. Performance Analysis
4.2. Comparison of the Proposed Approach with Existing Approaches
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Sadhya, D.; Raman, B. Generation of cancelable iris templates via randomized bit sampling. IEEE Trans. Inf. Secur. 2019, 14, 2972–2986. [Google Scholar] [CrossRef]
- Rajasekar, V.; Predić, B.; Saracevic, M.; Elhoseny, M.; Karabasevic, D.; Stanujkic, D.; Jayapaul, P. Enhanced multimodal biometric recognition approach for smart cities based on an optimized fuzzy genetic algorithm. Sci. Rep. 2022, 12, 622. [Google Scholar] [CrossRef] [PubMed]
- Velliangiri, S.; Manoharn, R.; Ramachandran, S.; Venkatesan, K.; Rajasekar, V.; Karthikeyan, P.; Kumar, P.; Dhanabalan, S.S. An Efficient Lightweight Privacy-Preserving Mechanism for Industry 4.0 Based on Elliptic Curve Cryptography. IEEE Trans. Ind. Inform. 2021, 18, 6494–6502. [Google Scholar] [CrossRef]
- Rajasekar, V.; Premalatha, J.; Sathya, K. Cancelable Iris template for secure authentication based on random projection and double random phase encoding. Peer--Peer Netw. Appl. 2021, 14, 747–762. [Google Scholar] [CrossRef]
- Rajasekar, V.; Premalatha, J.; Sathya, K.; Saračević, M. Secure remote user authentication scheme on health care, IoT and cloud applications: A multilayer systematic survey. Acta Poly Tech. Hung. 2021, 18, 87–106. [Google Scholar] [CrossRef]
- Singh, A.; Vashist, C.; Gaurav, P.; Nigam, A. A generic framework for deep incremental cancelable template generation. Neurocomputing 2022, 467, 83–98. [Google Scholar] [CrossRef]
- Manisha; Kumar, N. CBRC: A novel approach for cancelable biometric template generation using random permutation and Chinese Remainder Theorem. Multimed Tools Appl. 2022, 81, 22027–22064. [Google Scholar] [CrossRef]
- Pandey, F.; Dash, P.; Sinha, D. Attack-resistant and efficient cancelable codeword generation using random walk-based methods. Arab. J. Sci. Eng. 2022, 47, 2025–2043. [Google Scholar] [CrossRef]
- Asthana, R.; Walia, G.S.; Gupta, A. Random area-perimeter method for generation of unimodal and multimodal cancelable biometric templates. Appl. Intell. 2021, 51, 7281–7297. [Google Scholar] [CrossRef]
- Siddhad, G.; Khanna, P. Max-min threshold-based cancelable biometric templates for low-end devices. J. Electron. Imaging 2022, 31, 033025. [Google Scholar] [CrossRef]
- Ghammam, L.; Karabina, K.; Lacharme, P.; Atighehchi, K. A cryptanalysis of two cancelable biometric schemes based on index-of-max hashing. IEEE Trans. Inf. Secur. 2020, 15, 2869–2880. [Google Scholar] [CrossRef]
- Rajasekar, V.; Premalatha, J.; Sathya, K. Enhanced biometric recognition for secure authentication using iris preprocessing and hyperelliptic curve cryptography. Wirel. Commun. Mob. Comput. 2020, 2020, 8841021. [Google Scholar] [CrossRef]
- El-Rahiem, A.b.d.; Fathi, E.; El Samie, A.b.d.; Amin, M. Efficient cancellable multi-biometric recognition system based on deep learning and bio-hashing. Appl. Intell. 2022, 1–15. [Google Scholar] [CrossRef]
- Rajasekar, V.; Varadhaganapathy, S.; Sathya, K.; Premalatha, J. An efficient lightweight cryptographic scheme of signcryption based on hyperelliptic curve. In Proceedings of the 2016 3rd International Conference on Recent Advances in Information Technology (RAIT), Dhanbad, India, 3–5 March 2016; pp. 394–397. [Google Scholar]
- Sakr, A.S.; Pławiak, P.; Tadeusiewicz, R.; Hammad, M. Cancelable ECG biometric based on combination of deep transfer learning with DNA and amino acid approaches for human authentication. Inf. Sci. 2022, 585, 127–143. [Google Scholar] [CrossRef]
- Choudhary, S.K.; Naik, A.K. Protected Biometric Identification with Multiple Finger Vein. In Proceedings of the 2022 2nd Asian IEEE Conference on Innovation in Technology (ASIANCON), Ravet, India, 26–28 August 2022; pp. 1–6. [Google Scholar]
- Rathgeb, C.; Wagner, J.; Tams, B.; Busch, C. Preventing the cross-matching attack in Bloom filter-based cancelable biometrics. In Proceedings of the 3rd International Workshop on Biometrics and Forensics (IWBF 2015), Gjovik, Norway, 3–4 March 2015; pp. 1–6. [Google Scholar]
- Tarek, M.; Ouda, O.; Hamza, T. Robust cancellable biometrics scheme based on neural networks. IET Biom. 2016, 5, 220–228. [Google Scholar] [CrossRef]
- Tarek, M.; Ouda, O.; Hamza, T. Pre-image Resistant Cancelable Biometrics Scheme Using Bidirectional Memory Model. Int. J. Netw. Secur. 2017, 19, 498–506. [Google Scholar]
- Lai, Y.L.; Jin, Z.; Teoh AB, J.; Goi, B.M.; Yap, W.S.; Chai, T.Y.; Rathgeb, C. Cancellable iris template generation based on Indexing-First-One hashing. Pattern Recognit. 2017, 64, 105–117. [Google Scholar] [CrossRef]
- Gomez-Barrero, M.; Rathgeb, C.; Li, G.; Ramachandra, R.; Galbally, J.; Busch, C. Multi-biometric template protection based on bloom filters. Inf. Fusion 2018, 42, 37–50. [Google Scholar] [CrossRef]
- Soliman, R.F.; Amin, M.; Abd El-Samie, F.E. A double random phase encoding approach for cancelable iris recognition. Opt. Quantum Electron. 2018, 50, 1–12. [Google Scholar] [CrossRef]
- Soliman, R.F.; Amin, M.; Abd El-Samie, F.E. A modified cancelable biometrics scheme using random projection. Ann. Data Sci. 2019, 6, 223–236. [Google Scholar] [CrossRef]
- Soliman, R.F.; Ramadan, N.; Amin, M.; Ahmed, H.H.; El-Khamy, S.; Abd El-Samie, F.E. Efficient cancelable Iris recognition scheme based on modified logistic map. Proc. Natl. Acad. Sci. India Sect. A Phys. Sci. 2020, 90, 101–107. [Google Scholar] [CrossRef]
- Drozdowski, P.; Garg, S.; Rathgeb, C.; Gomez-Barrcro, M.; Chang, D.; Busch, C. Privacy-preserving indexing of Iris-codes with cancelable Bloom filter-based search structures. In Proceedings of the 2018 26th European Signal Processing Conference (EUSIPCO), Rome, Italy, 3–7 September 2018; pp. 2360–2364. [Google Scholar]
- Bendib, I.; Meraoumia, A.; Haouam, M.Y.; Laimeche, L. A New Cancelable Deep Biometric Feature Using Chaotic Maps. Pattern Recognit. Image Anal. 2022, 32, 109–128. [Google Scholar] [CrossRef]
- Kabir, W.; Ahmad, M.O.; Swamy, M.N.S. Normalization and weighting techniques based on genuine-impostor score fusion in multi-biometric systems. IEEE Trans. Inf. Secur. 2018, 13, 1989–2000. [Google Scholar] [CrossRef]
- Kaur, H.; Khanna, P. Privacy preserving remote multi-server biometric authentication using cancelable biometrics and secret sharing. Future Gener. Comput. Syst. 2020, 102, 30–41. [Google Scholar] [CrossRef]
- Kaur, H.; Khanna, P. Random distance method for generating unimodal and multimodal cancelable biometric features. IEEE Trans. Inf. Secur. 2018, 14, 709–719. [Google Scholar] [CrossRef]

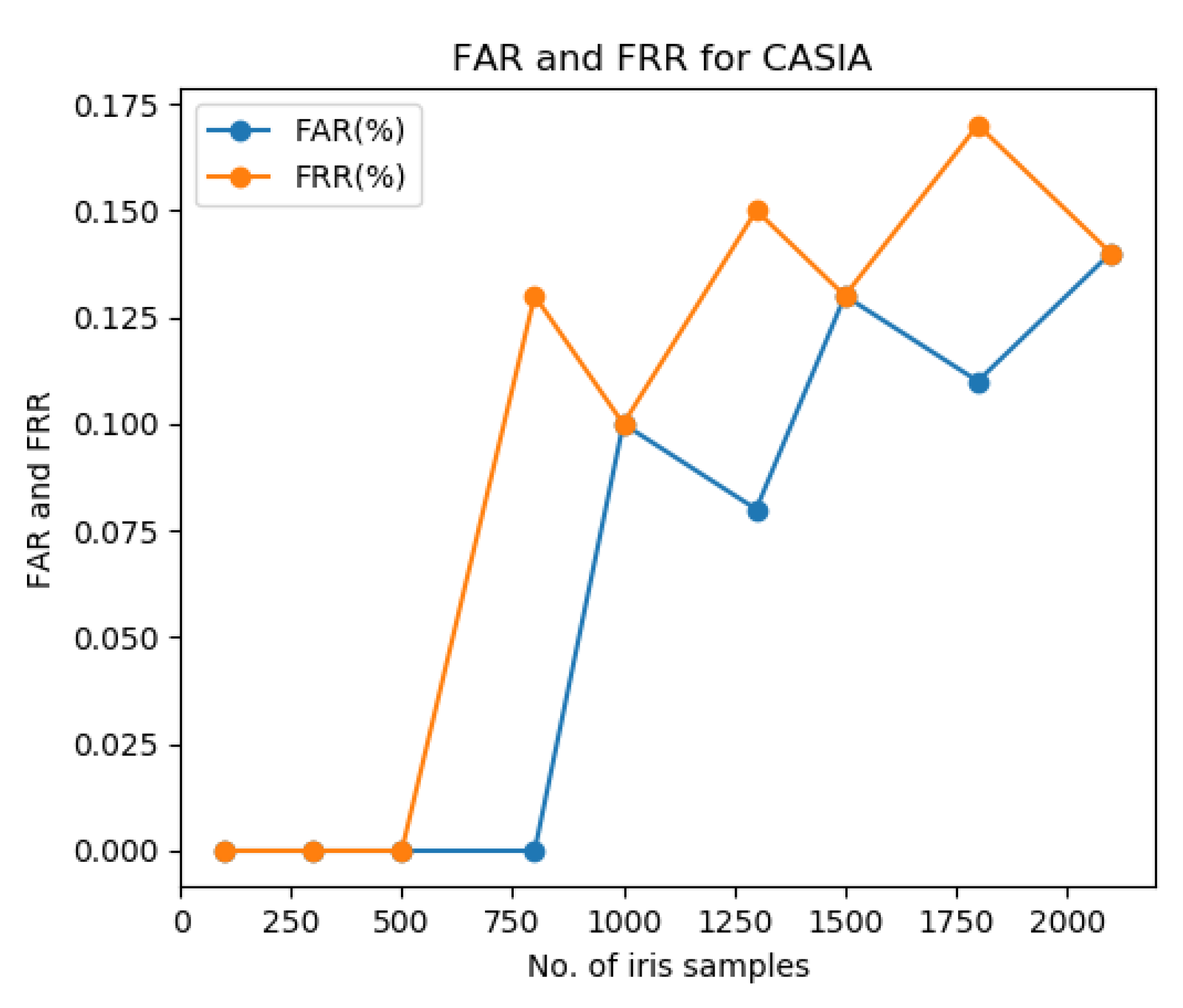
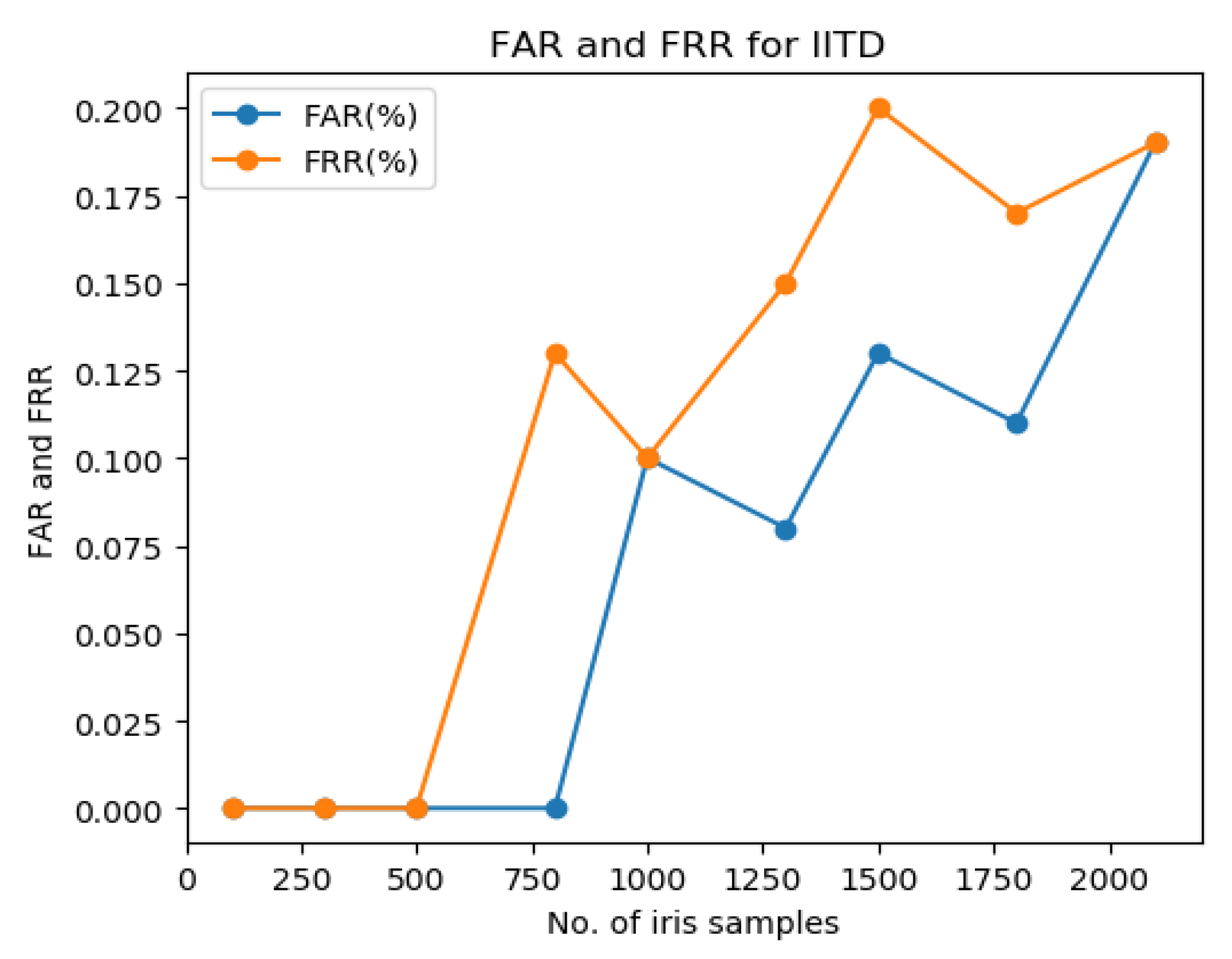
| No. of Iris Samples | TP | FN | FP | TN | FAR (%) | FRR (%) | TPR (%) | TNR (%) | F-Score |
|---|---|---|---|---|---|---|---|---|---|
| 100 | 100 | 0 | 0 | 100 | 0 | 0 | 100 | 100 | 100 |
| 300 | 300 | 0 | 0 | 300 | 0 | 0 | 100 | 100 | 100 |
| 500 | 500 | 0 | 0 | 500 | 0 | 0 | 100 | 100 | 100 |
| 800 | 799 | 1 | 0 | 800 | 0 | 0.13 | 99.88 | 100 | 99.94 |
| 1000 | 999 | 1 | 1 | 999 | 0.1 | 0.1 | 99.9 | 99.9 | 99.9 |
| 1300 | 1298 | 2 | 1 | 1299 | 0.08 | 0.15 | 99.85 | 99.92 | 99.88 |
| 1500 | 1498 | 2 | 2 | 1498 | 0.13 | 0.13 | 99.87 | 99.87 | 99.87 |
| 1800 | 1797 | 3 | 2 | 1798 | 0.11 | 0.17 | 99.83 | 99.89 | 99.86 |
| 2100 | 2097 | 3 | 3 | 2097 | 0.14 | 0.14 | 99.86 | 99.86 | 99.86 |
| No. of Iris Samples | TP | FN | FP | TN | FAR (%) | FRR (%) | TPR (%) | TNR (%) | F-Score |
|---|---|---|---|---|---|---|---|---|---|
| 100 | 100 | 0 | 0 | 100 | 0 | 0 | 100 | 100 | 100 |
| 300 | 300 | 0 | 0 | 300 | 0 | 0 | 100 | 100 | 100 |
| 500 | 500 | 0 | 0 | 500 | 0 | 0 | 100 | 100 | 100 |
| 800 | 799 | 1 | 0 | 800 | 0 | 0.13 | 99.88 | 100 | 99.94 |
| 1000 | 999 | 1 | 1 | 999 | 0.1 | 0.1 | 99.9 | 99.9 | 99.9 |
| 1300 | 1298 | 2 | 1 | 1299 | 0.08 | 0.15 | 99.85 | 99.92 | 99.88 |
| 1500 | 1497 | 3 | 2 | 1498 | 0.13 | 0.2 | 99.8 | 99.87 | 99.83 |
| 1800 | 1797 | 3 | 2 | 1798 | 0.11 | 0.17 | 99.83 | 99.89 | 99.86 |
| 2100 | 2096 | 4 | 4 | 2096 | 0.19 | 0.19 | 99.81 | 99.81 | 99.81 |
| Method | Dataset Used | Algorithm Used | EER in (%) |
|---|---|---|---|
| Tarek et al. [18] | CASIA V3 | BAM neural network | 3.56 |
| Tarek et al. [19] | CASIA V3 | Bidirectional memory model | 2.00 |
| Lai et al. [20] | CASIA V3 | Index first one hashing | 0.54 |
| Kaur et al. [29] | IITD | Random distance | 0.60 |
| Gomez-Barrero et al. [21] | IITD | Bloom filter | 4.3 |
| Random projection | 0.58 | ||
| Soliman et al. [22] | CASIA V3 | Fractional Fourier transform | 0.63 |
| Modified logistic map | 1.17 | ||
| Drozdowski et al. [25] | CASIA and IITD | Random permutation to iris code | 1.99 |
| Gomez-Barrero et al. [21] | CASIA | Bloom filter | 0.7 |
| Kabir et al. [27] | IITD | Normalization | 0.62 |
| Sadhya et al. [1] | CASIA V3 | Randomized bit sampling | 1.4 |
| Ghammam et al. [11] | CASIA | Index of max hashing | 1.47 |
| Rajasekar et al. [12] | CASIA and IITD Iris Dataset | RP and DRPE | 0.46 |
| 2D Gabor + HECC approach | 0.27 | ||
| Proposed Cancelable Template Generation based on signcryption | CASIA and IITD Iris Datasets | HGLD + signcryption (HECC + bio hash function) | 0.1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rajasekar, V.; Saračević, M.; Karabašević, D.; Stanujkić, D.; Dobardžić, E.; Krishnamoorthi, S. Efficient Cancelable Template Generation Based on Signcryption and Bio Hash Function. Axioms 2022, 11, 684. https://doi.org/10.3390/axioms11120684
Rajasekar V, Saračević M, Karabašević D, Stanujkić D, Dobardžić E, Krishnamoorthi S. Efficient Cancelable Template Generation Based on Signcryption and Bio Hash Function. Axioms. 2022; 11(12):684. https://doi.org/10.3390/axioms11120684
Chicago/Turabian StyleRajasekar, Vani, Muzafer Saračević, Darjan Karabašević, Dragiša Stanujkić, Eldin Dobardžić, and Sathya Krishnamoorthi. 2022. "Efficient Cancelable Template Generation Based on Signcryption and Bio Hash Function" Axioms 11, no. 12: 684. https://doi.org/10.3390/axioms11120684
APA StyleRajasekar, V., Saračević, M., Karabašević, D., Stanujkić, D., Dobardžić, E., & Krishnamoorthi, S. (2022). Efficient Cancelable Template Generation Based on Signcryption and Bio Hash Function. Axioms, 11(12), 684. https://doi.org/10.3390/axioms11120684









