Abstract
This paper proposes a method whereby a device can transmit and receive information using a beacon, and also describes application scenarios for the proposed method. In a multi-device to multi-device (MD2MD) content-centric networking (CCN) environment, the main issue involves searching for and connecting to nearby devices. However, if a device can’t find another device that satisfies its requirements, the connection is delayed due to the repetition of processes. It is possible to rapidly connect to a device without repetition through the selection of the optimal device using the proposed method. Consequently, the proposed method and scenarios are advantageous in that they enable efficient content identification and delivery in a content-centric Internet of Things (IoT) environment, in which multiple mobile devices coexist.
1. Introduction
With the spread of smartphones and tablet PCs, the volume of mobile traffic has been rapidly increasing, year upon year. The majority of mobile traffic is in video format. Video traffic already accounts for 55% of all mobile traffic, and this is expected to exceed 70% in 2016 [1]. In addition, video traffic should be afforded the greatest consideration in a mobile communications network because it uses much more data than either text or audio. By using a smartphone or a tablet PC, users are able to access video services such as VOD and YouTube while on the move. In other words, users have become able to use large amounts of data at any time, and anywhere.
As a result, the mobile network has become overloaded. To solve the problem of the overloading of base stations, device-to-device (D2D) communication has been attracting attention. D2D communication is a technique whereby devices communicate directly, without going through the network infrastructure [1,2]. Some of the main application services using D2D are Machine-to-Machine (M2M), Internet of Things (IoT), and Cyber-Physical-System (CPS). In particular, it is possible to avoid increasing the load on the Core network because the communication between the devices (located in a certain area) is the main traffic, such as when Smart Factory, Smart Farm, or enterprise/campus Intranet through M2M is used [3]. As a major advantage of using D2D technology in a mobile network, D2D communications bring significant improvements of spectral efficiency by underlaying cellular networks. D2D communication enables users in proximity to exchange information directly, without traversing to the base stations or core network in two hops, and it has attracted increasing attention from both industrial and academic communities. Due to the potential proximity gain, reuse gain, and hop gain, D2D communication can significantly increase system spectral efficiency and energy efficiency and, as such, has been considered a promising candidate technique for next generation cellular networks. Accordingly, many studies have focused on a D2D communications scheme that underlays the cellular network infrastructure in order to increase the cellular capacity, improving the users’ throughput, and extending the battery lifetime of user equipment. However, most conventional D2D-related works are limited to physical layer problems such as spectrum sharing and channel interference [4]. In the meantime, network security technologies based on distributed processing and Peer-to-Peer (P2P) concepts are emerging, and it is necessary to study the higher layers, beyond the research centered on the physical layer [5]. D2D communication can be divided into cellular-network-based D2D communication and autonomous D2D communication. Autonomous D2D communication has attracted considerable attention due to its ability to operate in situations where the cellular network has failed, such as in the wake of a natural disaster.
Also, existing IP-based host-centric network structures incur the problem of bottlenecks caused by the inefficiency of requests and the distribution of content such as video. For these reasons, current network structures cannot handle the trend towards large-volume content. Accordingly, studies of the Internet of the future, which will have to overcome the fundamental limitations of the current Internet structure, have been actively promoted [6]. Content-centric networking (CCN) is one area that Internet-related research will address in the future [7]. CCN is a communication protocol that supports routing and caching based on content names. CCN is suitable for an IoT environment since it can reduce the complexity of the autoconfiguration mechanism, relative to the approach based on the layered protocol stack [8,9,10,11]. Currently, the IoT is mostly related to sensor control, in which small amounts of data, such as sensor values, are communicated to and from a fixed device, such as a sensor. In step with the increasing trend in the use of mobile devices and large amounts of data, it is expected that the IoT environment will advance to organically communicate large-volume content between fixed devices and users’ mobile devices. CCN is very well suited to applications such as a content-centric IoT environment based on mobile devices.
However, previous studies on D2D have mainly dealt with intermittent transmission and reception of small amounts of data using short-range communication, mainly in devices such as sensors and IoTs. Therefore, in 5G mobile communication and the multi-device to multi-device (MD2MD) network based on high-speed WLAN, the transmission and reception of a large amount of multimedia traffic between wireless nodes have not been studied yet. Also, in the case of existing studies, most of the studies focused on transmitting information from a large number of sensors to a specific sink/aggregator node. Thus, most assume a logical tree structure. In this paper, we consider the MD2MD environment in which large-scale mobile stations communicate with each other and study the situation of transmitting and receiving a large amount of multimedia traffic considering the rapidly increasing amount of traffic in mobile communication. Particularly, in a multimedia traffic sending/receiving environment of a large number of terminals, multimedia content is considered to be exchanged through networking between terminals without accessing the Internet. To this end, we utilize content-oriented CCN technology and Bluetooth beacon technology beyond IP technology that performs host-centric communication with the Internet. Using Mobile CCN technology enables the Bluetooth beacon to be used for mutual search and content search between large-scale terminals and to know which content is located in which node in the network in the mobile networking environment of MD2MD. In particular, the application of Mobile CCN technology in the MD2MD environment in mobile communication/wireless communication networks is a very rare topic of study, and we believe that this study can be a basis for future research [12,13,14,15]. In particular, considering the developing mobile terminal, we have studied its operation based on heterogeneous wireless technology using several different wireless technologies. The use of heterogeneous wireless technology also includes intelligent use, such as choosing a wireless link that matches the nature of the traffic, beyond simply raising the transmission rate using multiple wireless transmission links.
Based on this background, this paper presents a discussion of MD2MD Mobile CCN, whereby a mobile device configures a network by actively searching for nearby devices and then connecting to a device with the required content, based on autonomous MD2MD communication and Mobile CCN. In such an MD2MD Mobile CCN environment, there are issues related to device discovery and connection between the mobile devices. To solve these issues, this paper proposes a method of transmitting and receiving device information by using Bluetooth Beacon, more commonly known as iBeacon.
In this paper, we propose a technology to reduce the connection time and content query time by acquiring the content information of wireless codes before accessing and connecting to the terminal with the desired content, in addition to technology development that reduces connection time using Bluetooth Beacon. Also, we propose a technique to reduce query time through Mobile CCN between remote terminals. Our method enables rapid multimedia communication in an MD2MD networking environment that transmits/receives a large amount of multimedia traffic. In this paper, we implemented the proposed method in a real testbed. In particular, we used the CCNx open-source project for mobile, implemented the Raspberry Pi-based Multiple Radio Access Technology (Multi-RAT) node directly, measured the performance of MD2MD, and showed that the proposed method is effective.
The remainder of this paper is organized as follows: Section 2 introduces D2D communication, CCN, and Bluetooth Beacon, and identifies the problems arising in an MD2MD CCN environment. Section 3 proposes a means of transmitting and receiving device information using Bluetooth Beacon, and presents some example scenarios in which this method could be applied. Section 4 evaluates and analyzes the performance of the proposed method as realized in a testbed based on the Raspberry Pi. Finally, Section 5 concludes the paper.
2. Related Works and Problems
There are several related works that address D2D communication, CCN, and Bluetooth Beacon. In this section, D2D communication, CCN, and Bluetooth Beacon are explained. Furthermore, the problems related to a MD2MD content-centric network environment are discussed.
2.1. D2D Communication
D2D communication is a technique whereby communication is established directly between devices without having to go through a network infrastructure [1,2]. As a means of overcoming the overloading of the base station, D2D communication has been attracting the attention of researchers. In the next-generation wireless communication environment, which is expected to support networking between devices, D2D communication will be afforded a much greater level of performance.
D2D communication makes it possible to reduce the load on the cellular network since it relies on direct communication between devices that are in close proximity. Furthermore, it is possible to improve the utilization of radio resources by reusing radio frequencies and extending cell coverage through relay communication between devices. Also, it is possible to reduce the delay and power consumption that arises during communication between devices [2,16,17,18]. D2D communication not only improves the performance of a cellular network, but also creates communications services such as social networking and location-based services [2,18].
As shown in Figure 1, D2D communication can be divided into cellular-network-based D2D communication and autonomous D2D communication. Relative to autonomous D2D communication, cellular-network-based D2D communication is more efficient in terms of the connection time and power consumption [18]. However, autonomous D2D communication can continue to operate in situations in which the cellular network fails, such as in the event of a disaster. Also, it is possible to reduce the overhead of a network and simplify the structure of that network by enabling devices to detect other devices themselves.
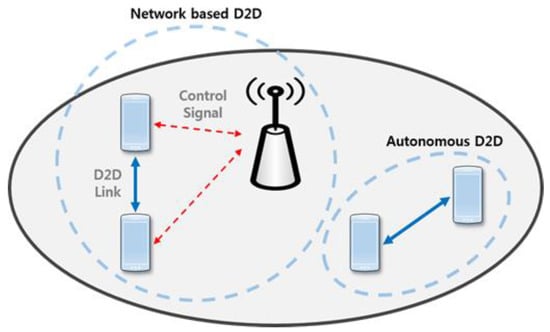
Figure 1.
Device-to-device (D2D) communication in a cellular network.
2.2. Content-Centric Networking
The architectures of the existing Internet and CCN are shown in Figure 2. CCN differs from a conventional IP-based network in that an IP-based network uses the IP to indicate the location of the content, while, in CCN, the device acquires content based on the name of the content [6]. In other words, CCN focuses on the content itself, rather than the location of that content.
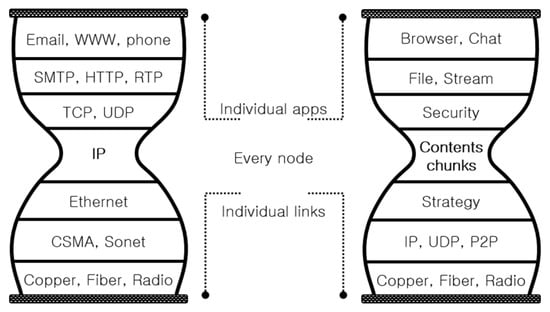
Figure 2.
Architectures of existing Internet and content-centric networking (CCN).
In CCNx, an interest message (which is a request message) and a content object (which is the response data) are used to process requests for content and the subsequent responses. An interest message contains information about the content requested by the user. The content object is the content transmitted in response to a request.
A CCN node consists of a forwarding information base (FIB), pending interest table (PIT), and content store, as shown in Figure 3. The FIB is a table used for the efficient transfer of interest messages. This table stores the information on the face to be transferred in response to a request for specific stored content. The PIT stores interest messages and information on the requested face. The content store is a cache that stores the content object, which can potentially be reused [7]. By virtue of this architecture, when the content store of a router is stored to a cache, it is possible to prevent the duplication of a request for the content in the CCN. Also, the overall amount of traffic is reduced by receiving data from the cache [6].
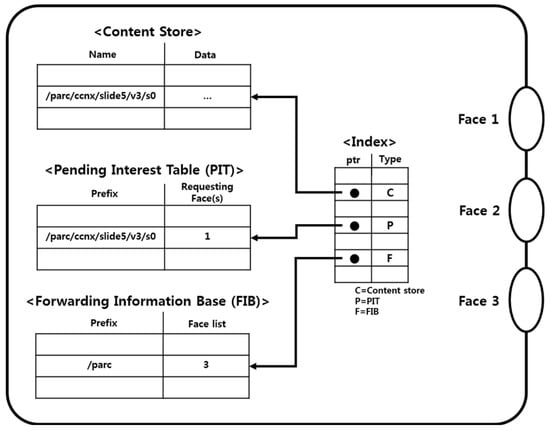
Figure 3.
Architecture of CCN node.
In CCN, content name-based routing, hop-wise replication, and caching are all possible. By caching content in the content store of the router, which exists in the path, the dispersion of content requests and acquisitions is facilitated [8,9,11]. These characteristics of CCN can reduce the complexity of autoconfiguration mechanisms relative to the layered protocol stack-based approach, with CCN being suitable for an IoT environment [10]. Accordingly, various studies have been implemented regarding the applications of CCN in an IoT environment, such as CCN traffic optimization, video streaming, and secure sensing [19,20,21].
CCNx is an open-source project of the Palo Alto Research Center (PARC). It is a developed CCN architecture [7].
2.3. Bluetooth Beacon
Bluetooth Beacon is a short-distance data communications technology that is based on Bluetooth low-energy (BLE) technology. iBeacon is a typical example of Bluetooth Beacon. The iBeacon technology has expanded Apple’s iOS location-based functionality through the incorporation of BLE technology. Bluetooth Beacon is capable of sending signals over a limited range of up to 50 m. When the user is approaching or moving away from a certain location, this can be estimated, and notification of the proximity of the user can be posted by using Bluetooth Beacon [22]. Furthermore, since Bluetooth Beacon tracks the location of a device on the basis of the transmitted and received signal strength, using the Bluetooth proximity profile instead of GPS, the location of the user can also be determined indoors [23,24,25,26]. When using the near field communication (NFC) or quick response (QR) technologies, both of which are similar to Bluetooth Beacon, the user has to perform an action, namely, positioning or operating a device in order to recognize a tag or code [27]. On the other hand, with Bluetooth Beacon, it is possible to provide location-based services to the user after automatically recognizing the user and determining his/her location through the Beacon, without any need for the user to perform specific actions [28,29].
Considering these advantages, not only Apple—which has already commercialized Bluetooth Beacon through an alliance with various companies—but also other companies such as Qualcomm, PayPal, and SKT have shown a serious interest in launching related businesses. Moreover, the number of service companies adopting technologies based on Bluetooth Beacon is gradually increasing. In particular, the application scope of Bluetooth Beacon, which was initially focused on offline distribution companies, has gradually been extended to the likes of digital content, mobile games, smart cars, and smart homes. In brief, many different companies have been showing a growing interest in Bluetooth Beacon.
The Bluetooth Beacon technology supports simple functions such as distance awareness, location awareness, and push messaging. Moreover, there are various methods of using Bluetooth Beacon. Bluetooth Beacon sets up a connection between a back-end server and the user’s smartphone. Therefore, location-based customized information and services can be provided through the server [30].
In addition, various studies are currently underway to address the applications of Bluetooth Beacon. The identification of the location of the user, as well as simple authentication, is possible by transmitting and receiving an encrypted Bluetooth Beacon signal and exchanging a key value [28]. Furthermore, location identification of the user, as well as simple authentication, is also possible by transmitting and receiving a Bluetooth Beacon signal and exchanging an encrypted key value [31].
For iBeacon, certain fields are specified in the BLE advertising packet. The data fields of iBeacon are iBeacon Prefix, Universally Unique Identifier (UUID), Major, Minor, and TX Power [32]. The iBeacon Prefix indicates the iBeacon packet. TX Power is used to identify the distance based on the transmission power of the transmitter. The UUID is a unique value designating a company. Major and Minor are used as identifiers for providing detailed company information. For example, if UUID indicates a specific company, then Major would indicate a certain branch of the company, and Minor would indicate a certain store inside the branch. Since the UUID designates a company, it cannot be used. Only Major and Minor can be used for practical applications. iBeacon can be used as an identifier indicating the type of institution or the building. However, its use is limited to a field requiring detailed information.
2.4. Problems with Existing Environments
In an MD2MD CCN environment, mobile devices actively search for and connect to nearby devices, configure a network, and then connect to the device with the content such that that content can be retrieved. In such an environment, the main issues relate to searching for and connecting to the nearby device. Without the assistance of any infrastructure, it should be possible for a device to search for a nearby device itself and establish a connection to a device with the specific content. In an MD2MD CCN environment, it is necessary to perceive information such as the possession of desired content and whether the device supports CCN. Additionally, there can be situations in which it is necessary to connect to devices satisfying certain conditions depending on the user’s requirements. For example, if the user desires to connect to the Internet through a connection with another device, information such as whether there is a backhaul is also necessary. Therefore, recognition of the device’s information is essential when establishing a connection between devices.
IEEE 802.11 states that it is possible to determine the Access Point (AP) information through the Beacon frame and the Prove Request/Response frame that includes the information required for establishing an AP connection. Also, it is possible to add optional fields in addition to the fields defined in the standard for these Beacon and Probe Request/Response frames. However, many restrictions are imposed on additions and corrections since the optional field is not standard. A problem arises in that it may be erroneously recognized in a device.
With typical search methods, the device obtains the information on the other device by sending and receiving messages after a connection between the devices has been established. Therefore, it is impossible to obtain detailed information on a device prior to establishing a connection. As such, the establishment of a connection is delayed due to the repetition of unnecessary processes such as the connections and disconnections that occur until a device satisfying the user requirements is found.
The connection process of a CCNx device for connecting to a device through a WLAN is illustrated in Figure 4. After scanning the nearby APs, the user device obtains detailed information on the device by establishing a direct connection to the AP. Therefore, if the connected device does not satisfy the user requirements, the device must first disconnect and then reconnect to another device.
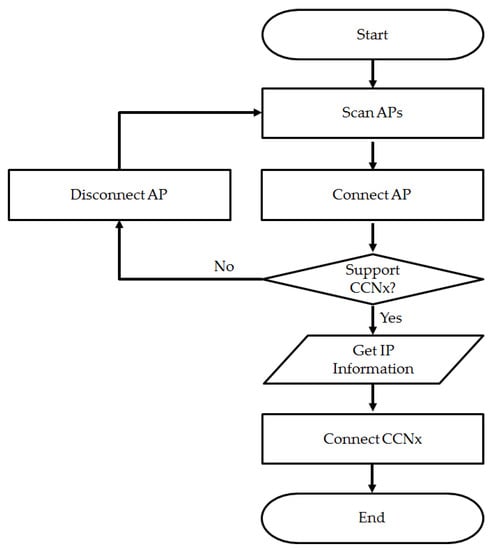
Figure 4.
Existing process for connection between devices.
3. Proposed Method
This section proposes a method for solving the previously described problem encountered in an MD2MD CCN environment. First, a method for transmitting and receiving device information using Bluetooth Beacon is proposed. Furthermore, application scenarios for the proposed method in terms of content delivery and network configuration between mobile devices are proposed.
3.1. Proposed Method
This paper proposes a method of transmitting and receiving device information using the broadcasting abilities of Bluetooth Beacon. Bluetooth Beacon includes detailed information for a device, such as CCNx support, the owned content, and the communications interface.
In the case of a WLAN connection between devices, the connection process between CCNx-enabled devices that utilize the proposed method is as shown in Figure 5. When the host device (which creates the AP) transmits information using Bluetooth Beacon, another device that attempts to connect to the AP receives the Bluetooth Beacon signals transmitted by the host device. The device attempting to connect to the AP checks whether the host device supports CCNx, and then subsequently establishes a CCNx connection by connecting to the AP based on the SSID and IP information received via the Bluetooth Beacon signal. Furthermore, it is possible to select and connect the most optimal AP or device by comparing the information for all the Beacon signals received. Because the proposed method transmits the information required for establishing a connection using Bluetooth Beacon, a connection can be established between devices quickly, without a physical connection between those devices.
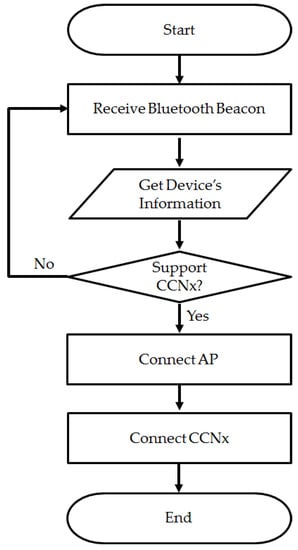
Figure 5.
Proposed process for connection between devices.
The existing method can be divided into AP scan, AP connection, and AP disconnection processes. Upon the first connection attempt, AP scan and AP connection are performed, after which a connection is established, then AP disconnection and scan are performed again. When the number of connection attempts is X, AP scan and AP connection are repeated X times in the existing method and AP disconnection is repeated X − 1 times. In the existing method, the time required to establish a connection with a target device can be determined from the following Equation (1):
In the proposed method, after a device receives the Bluetooth Beacon signals one at a time, if the device satisfies the user’s requirements, then a method for connecting the AP and CCNx is implemented. Therefore, in the existing method, the average number of received Beacon signals is identical to the number of connection attempts. Suppose the average number of received Beacon signals is Y; then, in the proposed method, after preparing to receive Bluetooth Beacon signals, Y Bluetooth Beacon signals are received. After that, the AP connection is performed. In the proposed method, the time consumed for connecting to a target device is expressed by the following Equation (2):
With the existing method, each time an attempt is made to connect to another device, the entire process is repeated. In the proposed method, since only the Bluetooth Beacon scan process is repeated, the repetition of any unnecessary processes does not occur.
In BLE, the advertising and scan processes are performed by using only the three channels in the 2.4 GHz band. For this reason, the BLE scan process consumes less time than that of WLAN.
3.2. Scenario for the Proposed Method
In this section, scenarios that can be utilized in an MD2MD CCN environment are described. Scenarios consist of MD2MD content delivery and network configuration between mobile devices.
3.2.1. MD2MD Content Delivery
There is an MD2MD content delivery scenario which uses CCNx and the previously proposed method. Using the proposed method, effective content delivery between mobile devices is possible. The device consists of a content transmission module, a Multi-RAT module that controls the interfaces, and a Bluetooth module that transmits and receives Bluetooth Beacon. In this scenario, it is assumed that a connection is established between the devices by using WLAN. The methods of content delivery are divided into Transmit/Receive and Request/Response.
First, the Transmit/Receive method involves one device sharing its owned content and the other device receiving that content. As shown in Figure 6, the transmitter sends a Transmit Beacon including interface information for communicating and the content to be shared. The receiver receiving a Transmit Beacon including the desired content information will connect to the transmitter and then receive the content. With this method, the main agent providing the content delivery is the transmitter. This method can also be a Broadcast/Receive method since it is shared by the transmitter. The operation process of the Transmit/Receive method is shown in Figure 7. In this process, it will transfer and receive content using ccnputfile and ccngetfile of CCNx.
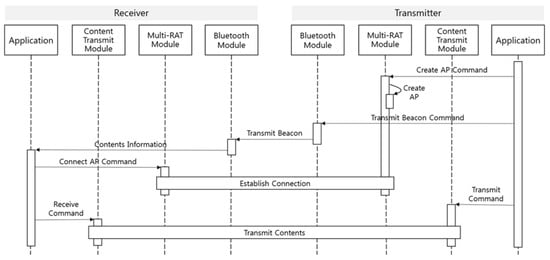
Figure 6.
Content delivery process of the Transmit/Receive method.
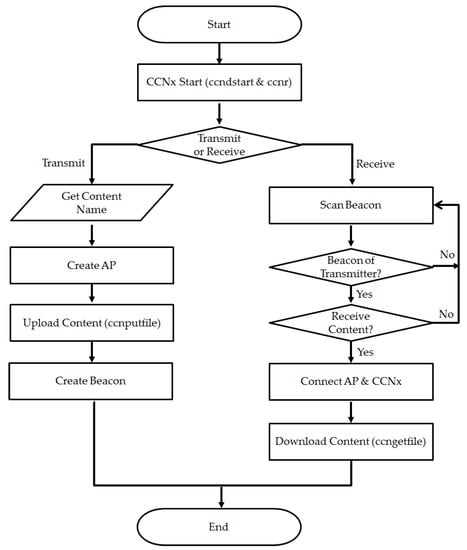
Figure 7.
Operation process of the Transmit/Receive method.
The Request/Response method is that whereby one side issues a request to share specific content and the other side transfers the requested content. As shown in Figure 8, the requester sends a Request Beacon including information related to the content request. The responder receives the Request Beacon and sends a Transmit Beacon in response. The next process is similar to the aforementioned Transmit/Receive method. In this method, the main agent responsible for the content delivery is the requester. The operation process of the Request/Receive method is shown in Figure 9.
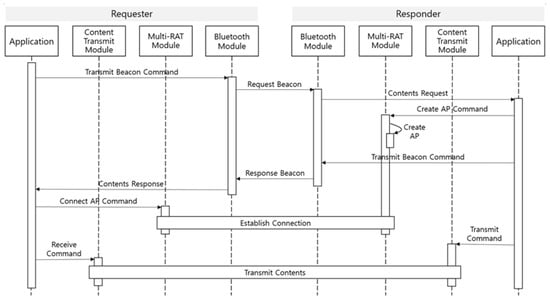
Figure 8.
Content delivery process of the Request/Response method.
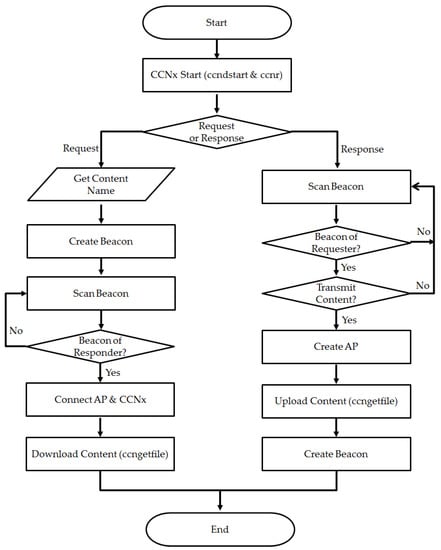
Figure 9.
Operation process of the Request/Response method.
The Transmit/Receive method is used only for public sharing because it is a unilateral sharing method. The Request/Response method can be used for private sharing among specific users as well as for public sharing since message exchange is possible.
3.2.2. Network Configuration between Devices
We can find an example of a network configuration between devices that uses the method proposed earlier. In much the same way as in an IoT environment, it is assumed that there is a sink node, which performs the role of server or AP. The network topology is such that one sink node is connected to several nodes, in much the same way as a tree topology. The device is equipped with one or more WLAN interfaces and one Bluetooth interface. The connection between the devices is established through WLAN. If the device is equipped with two or more WLAN interfaces, it is possible to set up a wireless relay. The sink node not only establishes the AP mode, but also broadcasts Bluetooth Beacon, including information on the sink node. The distance can be estimated on the basis of the WLAN and Bluetooth Beacon signal strength. As shown in Figure 10, given rough values for the distance from the sink node, the area around the AP is divided into immediate, near, and far sections.
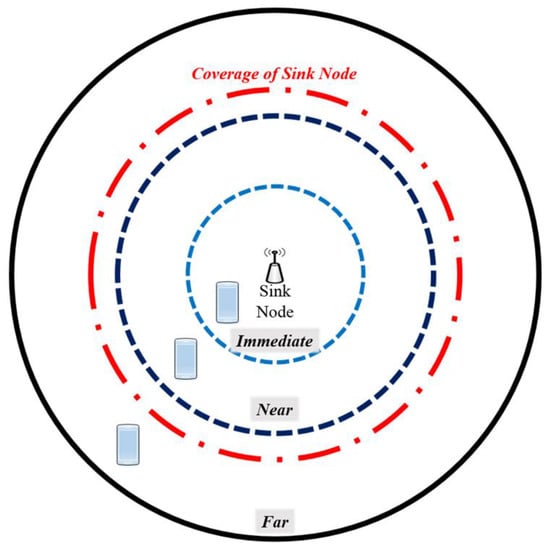
Figure 10.
Architecture for network configuration.
The first section is immediate, which is the case when the device is inside the coverage area of the sink node and the signal from the sink node is strong. As there are several APs in this section, the communication performance declines owing to interference from the different APs. To prevent this, when the signal from the sink node is strong, other devices do not enter AP mode and connect to the sink node only. The second section is nearby, as occurs when the device is inside the coverage area of the sink node and the strength of the signal from the main AP is normal. To connect with a device outside the coverage area of the sink node, but where the strength for the signal from the sink node is reasonably strong or acceptable, a device within the sink node coverage area acts as an AP node. It therefore provides coverage for the device outside the sink node coverage area and, therefore, the new AP acts as the main AP for the target device. To maintain the stability of the connection between devices, when the signal strength of the sink node is very weak, the devices do not operate in AP mode. The third section is far, that is, when the device is inside the coverage area of the sink node but the signal strength of the main AP is weak, or when the device is outside the coverage area of the sink node. To prevent the occurrence of a radio shadow area, the device operates as a wireless relay node.
Because the three sections are variable depending on the location of the device, they are modified to fit each circumstance by periodically monitoring the AP signal strength and Beacon signal depending on the situation, as shown in Figure 11. By using Bluetooth Beacon, it is possible to identify the sink node and the device. Since Bluetooth Beacon is suitable for identifying a location, it is possible to more accurately estimate the distance between devices. When a WLAN interface is being used, the Bluetooth interface instead performs a scanning process. For these reasons, the proposed network configuration scenario is suitable for an IoT environment incorporating many mobile devices. This scenario can be adopted when transmitting and receiving content between people having similar interests. For example, it would be possible to share materials such as lecture notes and reference materials.
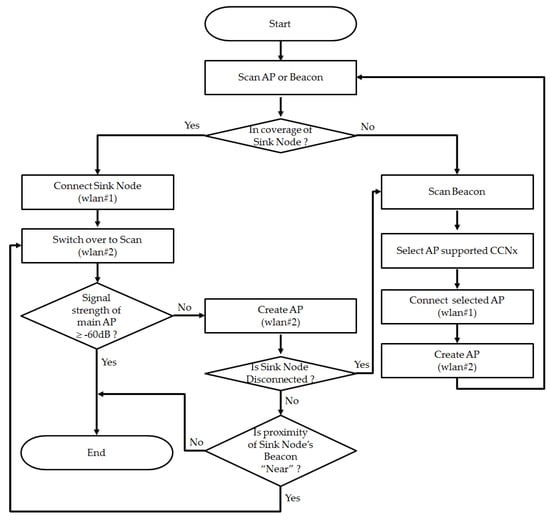
Figure 11.
Process of network configuration between devices.
4. Performance Evaluation and Analysis
As described above, a testbed based on the Raspberry Pi was constructed to evaluate the proposed method. In this section, the structure of the testbed is described, together with an evaluation of its performance.
4.1. Testbed for Performance Evaluation
The specifications of the device used for the test are as listed in Table 1. The device is a Raspberry Pi module running the Raspbian OS and is equipped with WLAN and Bluetooth interfaces. Figure 12 shows the testbed used for testing the connection between devices. The device is equipped with two WLAN interfaces and one Bluetooth interface. As shown in Figure 12, the device satisfying the user requirements incurs a backhaul by connecting an AP and supporting CCNx. Devices transmit the Bluetooth Beacon, which includes information on the backhaul and CCNx support. A device satisfying the user requirements establishes a wireless relay mode. One WLAN interface is used to connect to the AP, while the other is used to operate the AP mode by using the hostapd package. Furthermore, by simultaneously using the BlueZ package, Bluetooth Beacon signals are transmitted. The transmission cycle for the Bluetooth Beacon signal was set to 0.1 s.

Table 1.
Equipment for testbed configuration.
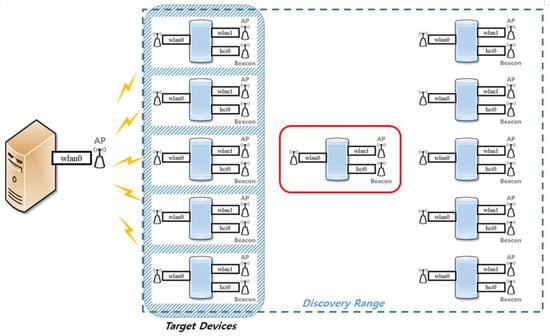
Figure 12.
Architecture of testbed for performance evaluation.
4.2. Result of Performance Evaluation
To evaluate the performance of the existing and proposed methods, an experiment was performed to analyze the connections between devices. A change in the number of devices and the ratio of the number of devices satisfying the user requirements, relative to the total number of devices, was found to affect the performance. First, based on a probability, the average number of connection attempts was obtained for each circumstance. Then, after obtaining the average length of time consumed by repetitively measuring the actual consumed time for each process, the average consumed time was substituted into the formula for obtaining the length of time consumed for each circumstance. Consequently, the connection time was obtained for both the existing method and the proposed method.
The changes in the ratio of the number of devices satisfying the user requirements to the total number of devices, and the changes in the total number of devices, are shown in Figure 13. Figure 13 is a graph showing the number of connection attempts according to the ratio change when the total number of devices was assumed to be 10. As the proportion of devices satisfying the user requirements increases, the average number of connection attempts increases exponentially.
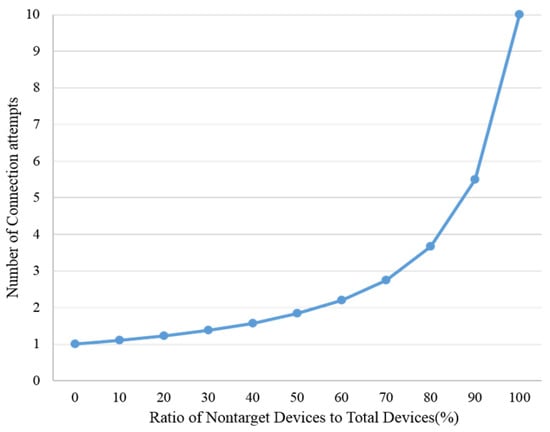
Figure 13.
Average number of connection attempts according to ratio change.
Figure 14 is a graph showing the increases in the total number of devices when the ratio of the number of devices satisfying the user requirements to the total number of devices is 1:1. The rate of increase was large when the total number of devices was small. Because the ratio was consistent, as the total number of devices increased, the rate of increase became smaller and smaller and ultimately converged to a certain value.
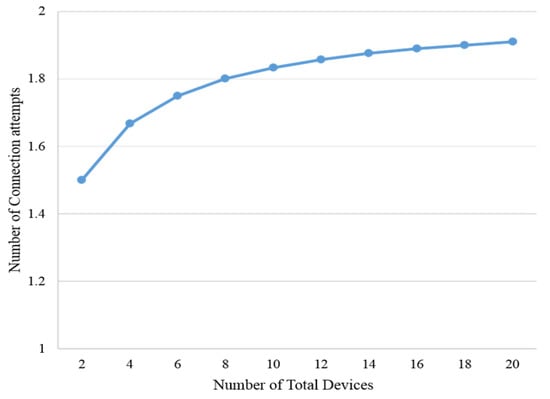
Figure 14.
Average number of connection attempts according to total number of changes.
As shown in Table 2, the actual length of time consumed by each process on the testbed was measured. The average length of time consumed by each process was obtained by repeating each process 200 times: the AP scan time was about 1582 ms; the Bluetooth Beacon scan preparation time was about 152 ms; the Bluetooth Beacon signal scan time was about 148 ms per signal; the AP connection time was about 450 ms; and the AP disconnection time was about 95 ms. The AP or Beacon scan time may vary according to the measurement environment. However, the difference was small.

Table 2.
Measured lengths of time consumed by each process.
Based on the average number of connections and measured length of time, the results obtained through the equation defining the average connection time for the existing and proposed methods, as well as the results obtained through actual experiment, are shown in Figure 15 and Figure 16. With the existing method, a difference could be observed between the experimental and theoretical values, despite many repetitions. Furthermore, because the value that changes based on the number of connection attempts is large, it can have a major effect on the probability. However, with the proposed method, an experimental value similar to the theoretical value was obtained because the value changed when there was only a small number of receiving Beacons, which was a value that could change through probability. When the total number of devices changes, and when the ratio of the number of devices satisfying the user requirements changes, it was found that the average connection time was smaller with the proposed method than with the existing method. With the proposed method, because there is no need for the AP scan process, which consumes the most time among the many processes, a fast connection can be established in an environment in which only target devices are present, as well as in an environment in which both target and non-target devices are present. With both the existing method and proposed method, there are slight variations depending on the environment. However, the proposed method was found to be superior to the existing method in various circumstances because there are relatively few values that change due to environmental factors.
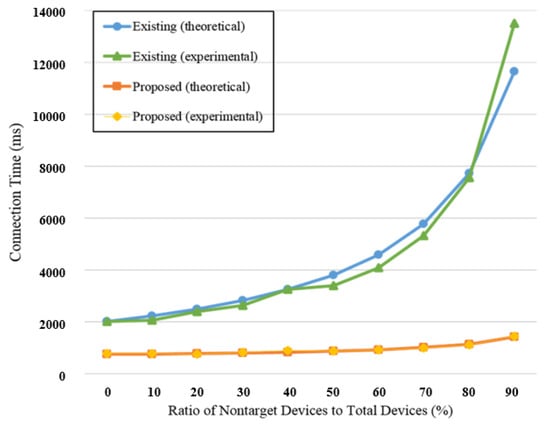
Figure 15.
Average connection times according to ratio change.
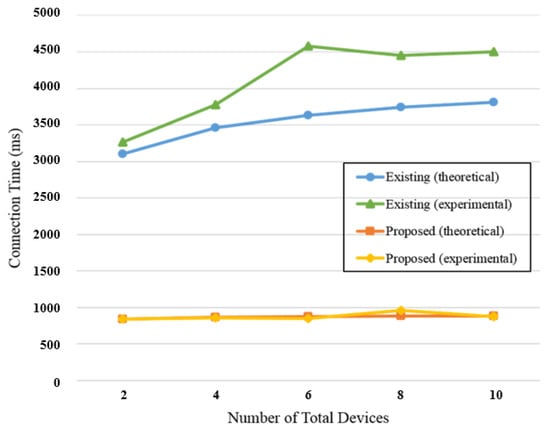
Figure 16.
Average connection times according to total number change.
The lengths of time consumed by requests and responses by Bluetooth Beacon were also measured to verify the scenario of MD2MD content delivery. The average consumed time was obtained by repeating each process 200 times. The result is as shown in Figure 17. The time required for the device to receive a Response Beacon after sending a Request Beacon is 0.69 s.
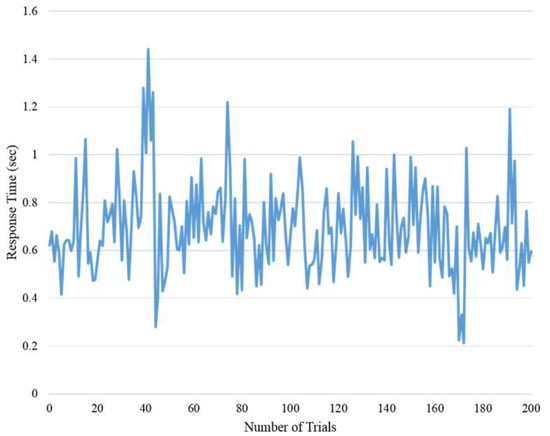
Figure 17.
Average lengths of time consumed by request/response.
5. Conclusions
This paper has proposed a method of transmitting and receiving a device’s information using Bluetooth Beacon in order to solve the issues faced in an MD2MD CCN environment in which mobile devices actively search for and connect to nearby devices, configure a network, and then connect to the device that owns the content, so as to enable its retrieval. A performance evaluation of the proposed method was also performed on a testbed. It is possible to rapidly connect to a device satisfying the user’s requirements without any unnecessarily repetitive processes, through the selection of the optimal device based on the detailed information received using the proposed method. Moreover, application scenarios for efficient content identification and delivery, as well as network configuration between devices in an environment in which multiple mobile devices coexist, have been proposed.
The proposed method offers the advantage of enabling fast and efficient connection to the optimal device, and can also be extended to various other areas. However, it is subject to limitations in that there is a need for an additional Bluetooth interface and the issue of possible interference with the WLAN signal. However, these are not significant limitations because most mobile devices support Bluetooth along with WLAN, while Bluetooth Beacon was designed with an emphasis on low power consumption using BLE. Moreover, Bluetooth minimizes interference through the adoption of a frequency-hopping technique which rapidly transmits small packets through multiple channels.
As a result, the proposed method and application scenarios offer the advantages of enabling efficient content identification and delivery in a content-centric IoT environment in which multiple mobile devices coexist. Furthermore, an MD2MD CCN environment based on these methods and scenarios offers various benefits to both users and the telecommunications company. The users can transmit and receive content by configuring a network with devices only, even if there is no Internet access or additional servers. The telecommunications company can reduce the network overhead and simplify the structure since the mobile devices actively search for and communicate with nearby devices.
The MD2MD/MCCN/Heterogeneous networking-based multimedia content transmission technology proposed in this research shows better performance than the existing research. Moreover, in contrast to the existing research which has produced only theoretical results, the result of this research was developed in a form that can be operated on an actual network.
Our laboratory is currently working on the openwincon project, which is based on open-source software for anyone to create and operate a mobile communication/wireless network, and also working on the GOTHAM project which supports networking and multimedia transmission in an integrated network. Open-source software resulting from the two projects has been released on GitHub [33,34].
Acknowledgments
This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (NRF-2015R1D1A1A01059147).
Author Contributions
All the authors contributed equally to this work. All authors read and approved the final manuscript.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Cisco Visual Networking Index: Global Mobile Data Traffic Forecast Update, 2015–2020 White Paper. 2016. Available online: http://goo.gl/ylTuVx (accessed on 17 April 2017).
- Hong, J.; Seong, S.; Park, S.; Park, C.; Kim, J.; Choi, S.; Lee, K. D2D communication technology and standardization trends. Mag. IEEE 2013, 4, 77–87. [Google Scholar]
- Jang, U.; Lim, H.; Kim, H. Privacy-enhancing security protocol in LTE initial attack. Symmetry 2014, 6, 1011–1025. [Google Scholar] [CrossRef]
- Dun, H.; Ye, F.; Li, Y. Transmission power adaption for full-duplex relay-aided device-to-device communication. Symmetry 2017, 9, 38. [Google Scholar] [CrossRef]
- Yin, S.; Bao, J.; Zhang, Y.; Huang, X. M2M security technology of cps based on blockchains. Symmetry 2017, 9, 193. [Google Scholar] [CrossRef]
- Jacobson, V.; Smetters, D.K.; Thornton, J.D.; Plass, M.F.; Briggs, N.H.; Braynard, R.L. Networking named content. In Proceedings of the 5th International Conference on Emerging Networking Experiments and Technologies, Rome, Italy, 1–4 December 2009; pp. 1–12. [Google Scholar]
- CCNx. Available online: http://www.ccnx.org (accessed on 17 April 2017).
- Quevedo, J.; Corujo, D.; Aguiar, R. A case for ICN usage in IoT environments. In Proceedings of the 2014 IEEE Global Communications Conference (GLOBECOM), Austin, TX, USA, 8–12 December 2014; pp. 2770–2775. [Google Scholar]
- Ghodsi, A.; Ohlman, B.; Ott, J.; Solis, I.; Wählisch, M. Information-Centric Networking—Ready for the Real World? (Dagstuhl Seminar 12361); Dagstuhl Reports; Schloss Dagstuhl-Leibniz-Zentrum für Informatik: Wadern, Germany, 2013. [Google Scholar]
- Baccelli, E.; Mehlis, C.; Hahm, O.; Schmidt, T.C.; Wählisch, M. Information centric networking in the IoT: Experiments with NDN in the wild. In Proceedings of the 1st International Conference on Information-Centric Networking, Paris, France, 24–26 September 2014; pp. 77–86. [Google Scholar]
- Quevedo, J.; Corujo, D.; Aguiar, R. Consumer driven information freshness approach for content centric networking. In Proceedings of the 2014 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 27 April–2 May 2014; pp. 482–487. [Google Scholar]
- You, D.; Kim, D.H. Multi-device-to-multi-device communication in cellular network for efficient contents distribution. In Proceedings of the 2014 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 10–13 January 2014; pp. 244–247. [Google Scholar]
- Iqbal, J.; Giaccone, P. Interest-based cooperative caching in multi-hop wireless networks. In Proceedings of the 2013 IEEE Globecom Workshops (GC Wkshps), Atlanta, GA, USA, 9–13 December 2013; pp. 617–622. [Google Scholar]
- Hasan, K.; Jeong, S.-H. Fast content access in the wireless networks. In Proceedings of the 2017 International Conference on Information and Communications (ICIC), Surabaya, Indonesia, 31 October 2017; pp. 278–280. [Google Scholar]
- Park, G.S.; Kim, W.; Jeong, S.H.; Song, H. Smart base station-assisted partial-flow device-to-device offloading system for video streaming services. IEEE Trans. Mob. Comput. 2017, 16, 2639–2655. [Google Scholar] [CrossRef]
- Bang, S.; Hong, S.; Song, J.; Kim, I.; Park, E.; Lee, M.; Jang, S. Direction of 5G Mobile Communication Technology. KICS Inf. Commun. Mag. 2013, 30, 25–36. [Google Scholar]
- Lin, X.; Andrews, J.; Ghosh, A.; Ratasuk, R. An overview of 3GPP device-to-device proximity services. IEEE Commun. Mag. 2014, 52, 40–48. [Google Scholar] [CrossRef]
- Seong, S.; Hong, J.; Kim, K.; Park, S.; Choi, S.; Lee, G. Cellular Network based D2D Communication Technologies. KICS Inf. Commun. Mag. 2012, 29, 97–105. [Google Scholar]
- François, J.; Cholez, T.; Engel, T. CCN traffic optimization for IoT. In Proceedings of the 2013 Fourth International Conference on the Network of the Future (NOF), Pohang, Korea, 23–25 October 2013; pp. 1–5. [Google Scholar]
- Martinez-Julia, P.; Garcia, E.T.; Murillo, J.O.; Skarmeta, A.F. Evaluating video streaming in network architectures for the internet of things. In Proceedings of the 2013 Seventh International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS), Taichung, Taiwan, 3–5 July 2013; pp. 411–415. [Google Scholar]
- Burke, J.; Gasti, P.; Nathan, N.; Tsudik, G. Secure sensing over named data networking. In Proceedings of the 2014 IEEE 13th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 21–23 August 2014; pp. 175–180. [Google Scholar]
- iOS Developer Library. Available online: https://developer.apple.com (accessed on 17 April 2017).
- iBeacons Bible 2.0. Available online: https://meetingofideas.files.wordpress.com/2014/06/ibeacon-bible-2-0.pdf (accessed on 17 April 2017).
- Chawathe, S.S. Beacon placement for indoor localization using Bluetooth. In Proceedings of the 2008 11th International IEEE Conference on Intelligent Transportation Systems, Beijing, China, 12–15 October 2008; pp. 980–985. [Google Scholar]
- Kajioka, S.; Mori, T.; Uchiya, T.; Takumi, I.; Matsuo, H. Experiment of indoor position presumption based on rssi of bluetooth le beacon. In Proceedings of the 2014 IEEE 3rd Global Conference on Consumer Electronics (GCCE), Tokyo, Japan, 7–10 October 2014; pp. 337–339. [Google Scholar]
- Li, S.; Lou, Y.; Liu, B. Bluetooth aided mobile phone localization: A nonlinear neural circuit approach. ACM Trans. Embed. Comput. Syst. (TECS) 2014, 13. [Google Scholar] [CrossRef]
- Ryu, H.; Park, S.; Jang, Y. Communication technology trends between terminals for proximity service. Inf. Commun. Mag. 2013, 30, 97–104. [Google Scholar]
- Takalo-Mattila, J.; Kiljander, J.; Soininen, J.-P. Advertising semantically described physical items with bluetooth low energy beacons. In Proceedings of the 2013 2nd Mediterranean Conference on Embedded Computing (MECO), Budva, Montenegro, 15–20 June 2013; pp. 211–214. [Google Scholar]
- Ben Abdesslem, F.; Lindgren, A. Mobile opportunistic system for experience sharing (MOSES) in indoor exhibitions. In Proceedings of the 20th Annual International Conference on Mobile Computing and Networking, Maui, HI, USA, 7–11 September 2014; pp. 267–270. [Google Scholar]
- IDG TechLibrary, New Evolution of the Signal Device, Understanding of Beacon and iBeacon. Available online: http://www.itworld.co.kr/techlibrary/86699 (accessed on 17 April 2017).
- Portnoi, M.; Shen, C.-C. Location-aware sign-on and key exchange using attribute-based encryption and bluetooth beacons. In Proceedings of the 2013 IEEE Conference on Communications and Network Security (CNS), National Harbor, MD, USA, 14–16 October 2013; pp. 405–406. [Google Scholar]
- DevFright. Available online: http://www.devfright.com (accessed on 17 April 2017).
- GOTHAM. Available online: https://github.com/OpenWinCon/Fun5G/tree/master/Mesh (accessed on 17 April 2017).
- OpenWinCon. Available online: https://github.com/OpenWinCon/Fun5G (accessed on 17 April 2017).
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).