A Stacked Machine Learning-Based Intrusion Detection System for Internal and External Networks in Smart Connected Vehicles
Abstract
1. Introduction
2. Introduction to Security Analysis and IDS for Smart Connected Vehicles
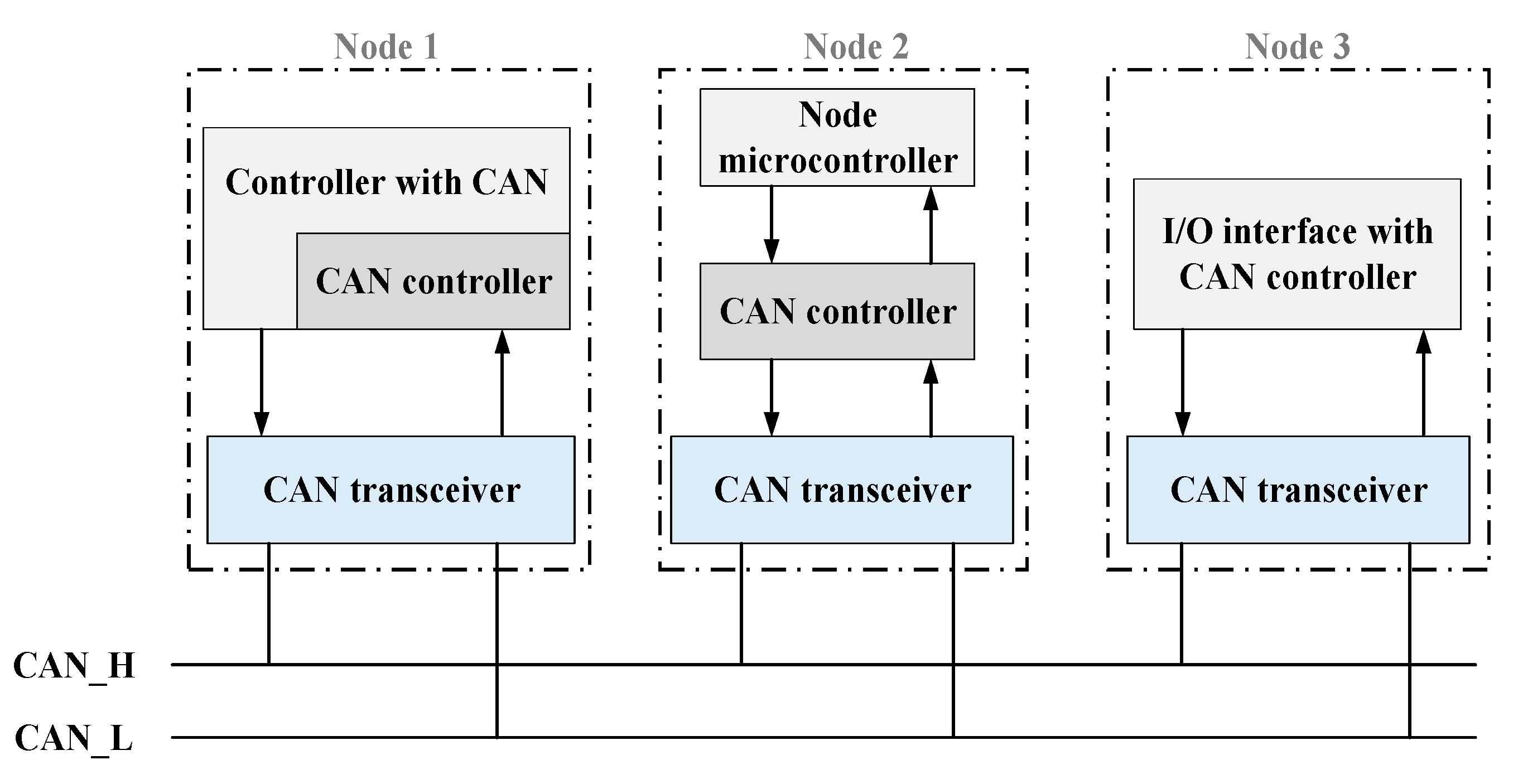
2.1. Vehicle Bus Internal Vulnerability Issues and Related Attacks
- 1.
- Message injection attack;
- 2.
- DoS attack;
- 3.
- Tampering Attack;
- 4.
- Fuzzing Attack;
2.2. External Network Connections in Vehicles and Related Attacks
2.2.1. V2X Communication Protocols: IEEE 802.11p and VANET
- Dynamic topology resulting from vehicle movement.
- Distributed communication, typically without centralized infrastructure.
- Broadcast-based message dissemination.
- Strict latency requirements for safety-critical information exchange.
- Identity spoofing, where malicious nodes impersonate legitimate vehicles.
- Message tampering and replay attacks, aimed at misleading nearby vehicles.
- Denial-of-Service (DoS) attacks, which aim to saturate the network.
- Location spoofing (e.g., GPS spoofing), used to manipulate a vehicle’s position awareness.
2.2.2. External Network Related Attacks
- 1.
- Rogue Networks;
- 2.
- Data Eavesdropping
- 3.
- Information Forgery, Tampering and Replay
- 4.
- Privacy Leakage
2.3. IDS for Smart Connected Vehicles
2.3.1. Feature-Based IDS (FIDS)
2.3.2. Rule-Based IDS (RIDS)
2.3.3. Statistical-Based IDS (SIDS)
2.3.4. Machine Learning/Deep Learning-Based IDS (M/DIDS)
- Current intrusion detection systems are typically limited to either internal or external detection, and fail to implement a comprehensive detection mechanism for both internal and external threats simultaneously. Even when internal and external detection systems are present, the types of attacks that can be detected are usually limited to no more than four.
- If the training data are limited, deep learning models may suffer from overfitting, leading to poor generalization on new data. Additionally, data bias can cause the model to produce unfair results, while poor or insufficient data quality can cause the model to learn incorrect patterns, thereby reducing its predictive accuracy and reliability.
- Deep learning models for vehicle intrusion detection may introduce a range of issues, including poor real-time performance, high resource consumption, increased energy usage, deployment challenges, and difficulties in maintenance.
3. Stacked Machine Learning Based Intrusion Detection System
3.1. Data Preprocessing Module
3.1.1. Solution for Handling Class Imbalance in Internal Data
3.1.2. Solution for Handling Class Imbalance in External Data
3.1.3. K-Means Clustering
- Data points are assigned to K cluster centers based on their Euclidean distance, Manhattan distance, or Mahalanobis distance;
- Each data point is assigned to the cluster whose center is closest to it;
- Recalculate the center of each cluster by computing the mean of all data points in the cluster;
- Repeat steps 2 and 3 until the cluster centers no longer change or the preset number of iterations is reached.
3.1.4. Class Imbalance
3.1.5. Normalization Procession
3.2. Feature Extraction Module
3.3. Internal and External Network Intrusion Detection Module
3.3.1. Selecting Base-Learner and Optimizing Parameters
3.3.2. Stacked Modeling
- 1.
- First Layer
- 2.
- Second Layer
- 3.
- Third Layer
4. Experimentation and Analysis
4.1. Constructing the Datasets
4.1.1. Internal Datasets
- 1.
- Fuzzy Attack
- 2.
- Dos Attack
- 3.
- Tampering Attack
4.1.2. External Datasets
4.2. Evaluation Metrics for Proposed IDS
- 1.
- Accuracy
- 2.
- Precision
- 3.
- Recall
- 4.
- F1-Score
4.3. Comparative Analysis of Training Time
4.4. Comparative Analysis of IDS
4.5. Hardware Experimental Analysis
- Processor: Broadcom BCM2837B0, Quad-core Cortex-A53 (ARMv8) 64-bit SoC @ 1.4 GHz.
- Memory: 1 GB LPDDR2 SDRAM.
- Storage: 32 GB microSD card (Class 10) used as the primary storage.
- Networking: 2.4 GHz and 5 GHz IEEE 802.11.b/g/n/ac wireless LAN, Bluetooth 4.2, Gigabit Ethernet (over USB 2.0).
- Operating System: Raspbian OS (Debian-based Linux distribution).
- Power Supply: 5 V/2.5 A DC via micro USB connector.
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Chen, C.; Zhang, B.; Liu, M.; Wei, S.; Zhang, J.; Shen, L. Research on intelligent networking automotive technology and information security based on CAN bus. IOP Conf. Ser. Mater. Sci. Eng. 2019, 688, 044058. [Google Scholar] [CrossRef]
- Bendiab, G.; Hameurlaine, A.; Germanos, G.; Kolokotronis, N.; Shiaeles, S. Autonomous Vehicles Security: Challenges and Solutions Using Blockchain and Artificial Intelligence. IEEE Trans. Intell. Transp. Syst. 2023, 24, 3614–3637. [Google Scholar] [CrossRef]
- Obaidat, M.; Khodjaeva, M.; Holst, J.; Ben Zid, M. Security and Privacy Challenges in Vehicular Ad Hoc Networks. In Connected Vehicles in the Internet of Things; Mahmood, Z., Ed.; Springer: Cham, Switzerland, 2020; pp. 223–251. [Google Scholar] [CrossRef]
- Al-Areqi, A.; Szakács, T. Can Bus Communication Demonstration Tool for Education. In Proceedings of the 2021 IEEE 15th International Symposium on Applied Computational Intelligence and Informatics (SACI), Timisoara, Romania, 19–21 May 2021; pp. 000299–000304. [Google Scholar] [CrossRef]
- Voss, W. A Comprehensible Guide to Controller Area Network; Copperhill Media: Amherst, MA, USA, 2008. [Google Scholar]
- Zhang, X.; Mu, L.; Zhao, J.; Xu, C. An efficient anonymous authentication scheme with secure communication in intelligent vehicular ad-hoc networks. KSII Trans. Internet Inf. Syst. (TIIS) 2019, 13, 3280–3298. [Google Scholar] [CrossRef]
- Mwanje, M.D.; Kaiwartya, O.; Aljaidi, M.; Cao, Y.; Kumar, S.; Jha, D.N.; Naser, A.; Lloret, J. Cyber security analysis of connected vehicles. IET Intell. Transp. Syst. 2024, 18, 1175–1195. [Google Scholar] [CrossRef]
- Boström, A.; Wotawa, F. Wireless Threats Against V2X Communication. In Proceedings of the 2023 IEEE 23rd International Conference on Software Quality, Reliability, and Security (QRS), Chiang Mai, Thailand, 22–26 October 2023; pp. 529–540. [Google Scholar] [CrossRef]
- Staat, P.; Jansen, K.; Zenger, C.; Elders-Boll, H.; Paar, C. Analog Physical-Layer Relay Attacks with Application to Bluetooth and Phase-Based Ranging. In Proceedings of the 15th ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec ‘22), San Antonio, TX, USA, 16–19 May 2022; Association for Computing Machinery: New York, NY, USA, 2022; pp. 60–72. [Google Scholar] [CrossRef]
- Ju, Z.; Zhang, H.; Li, X.; Chen, X.; Han, J.; Yang, M. A Survey on Attack Detection and Resilience for Connected and Automated Vehicles: From Vehicle Dynamics and Control Perspective. IEEE Trans. Intell. Veh. 2022, 7, 815–837. [Google Scholar] [CrossRef]
- Karthikeyan, H.; Usha, G. Real-time DDoS flooding attack detection in intelligent transportation systems. Comput. Electr. Eng. 2022, 101, 107995. [Google Scholar] [CrossRef]
- Derhab, A.; Belaoued, M.; Mohiuddin, I.; Kurniawan, F.; Khan, M.K. Histogram-Based Intrusion Detection and Filtering Framework for Secure and Safe In-Vehicle Networks. IEEE Trans. Intell. Transp. Syst. 2022, 23, 2366–2379. [Google Scholar] [CrossRef]
- Twardokus, G.; Rahbari, H. Vehicle-to-Nothing? Securing C-V2X Against Protocol-Aware DoS Attacks. In Proceedings of the IEEE INFOCOM 2022—IEEE Conference on Computer Communications, London, UK, 2–5 May 2022; pp. 1629–1638. [Google Scholar] [CrossRef]
- Abdullah, M.; Raza, I.; Zia, T.; Hussain, S.A. Interest flooding attack mitigation in a vehicular named data network. IET Intell. Transp. Syst. 2021, 15, 525–537. [Google Scholar] [CrossRef]
- Farivar, F.; Haghighi, M.S.; Jolfaei, A.; Wen, S. Covert Attacks Through Adversarial Learning: Study of Lane Keeping Attacks on the Safety of Autonomous Vehicles. IEEE/ASME Trans. Mechatron. 2021, 26, 1350–1357. [Google Scholar] [CrossRef]
- Swessi, D.; Idoudi, H. Comparative Study of Ensemble Learning Techniques for Fuzzy Attack Detection in In-Vehicle Networks. In Advanced Information Networking and Applications; AINA 2022. Lecture Notes in Networks and Systems; Barolli, L., Hussain, F., Enokido, T., Eds.; Springer: Cham, Switzerland, 2022; Volume 450, pp. 598–610. [Google Scholar] [CrossRef]
- Singh, A.; Singh, B. A Study of the IEEE802.11p (WAVE) and LTE-V2V Technologies for Vehicular Communication. In Proceedings of the 2020 International Conference on Computation, Automation and Knowledge Management (ICCAKM), Dubai, United Arab Emirates, 9–11 January 2020; pp. 157–160. [Google Scholar] [CrossRef]
- IEEE 802.11p; IEEE Standard for Information Technology—Local and Metropolitan Area Networks—Specific Requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment 6: Wireless Access in Vehicular Environments. IEEE: New York, NY, USA, 2010.
- Santamaria, A.F.; Sottile, C.; Lupia, A.; Raimondo, P. An efficient traffic management protocol based on IEEE802.11p standard. In Proceedings of the International Symposium on Performance Evaluation of Computer and Telecommunication Systems (SPECTS 2014), Monterey, CA, USA, 6–10 July 2014; pp. 634–641. [Google Scholar] [CrossRef]
- Qureshi, K.N.; Din, S.; Jeon, G.; Piccialli, F. Internet of Vehicles: Key Technologies, Network Model, Solutions and Challenges with Future Aspects. IEEE Trans. Intell. Transp. Syst. 2021, 22, 1777–1786. [Google Scholar] [CrossRef]
- Liu, Z.; Weng, J.; Ma, J.; Guo, J.; Feng, B.; Jiang, Z.; Wei, K. TCEMD: A Trust Cascading-Based Emergency Message Dissemination Model in VANETs. IEEE Internet Things J. 2020, 7, 4028–4048. [Google Scholar] [CrossRef]
- Guo, J.; Liu, Z.; Tian, S.; Huang, F.; Li, J.; Li, X.; Igorevich, K.K.; Ma, J. TFL-DT: A Trust Evaluation Scheme for Federated Learning in Digital Twin for Mobile Networks. IEEE J. Sel. Areas Commun. 2023, 41, 3548–3560. [Google Scholar] [CrossRef]
- Sedar, R.; Kalalas, C.; Vázquez-Gallego, F.; Alonso, L.; Alonso-Zarate, J. A Comprehensive Survey of V2X Cybersecurity Mechanisms and Future Research Paths. IEEE Open J. Commun. Soc. 2023, 4, 325–391. [Google Scholar] [CrossRef]
- Gupta, S.; Maple, C.; Passerone, R. An Investigation of Cyber-Attacks and Security Mechanisms for Connected and Autonomous Vehicles. IEEE Access 2023, 11, 90641–90669. [Google Scholar] [CrossRef]
- Zhu, P.; Zhu, K.; Zhang, L. Security Analysis of LTE-V2X and A Platooning Case Study. In Proceedings of the IEEE INFOCOM 2020—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 6–9 July 2020; pp. 532–537. [Google Scholar] [CrossRef]
- Bajracharya, C. Performance Evaluation for Secure Communications in Mobile Internet of Vehicles with Joint Reactive Jamming and Eavesdropping Attacks. IEEE Trans. Intell. Transp. Syst. 2022, 23, 22563–22570. [Google Scholar] [CrossRef]
- da Silva, L.B.; Fernández, E.M.G.; Camponogara, Â. Physical Layer Security Techniques Applied to Vehicle-to-Everything Networks. arXiv 2023, arXiv:2301.05123. [Google Scholar] [CrossRef]
- Dibaei, M.; Zheng, X.; Jiang, K.; Abbas, R.; Liu, S.; Zhang, Y.; Xiang, Y.; Yu, S. Attacks and defences on intelligent connected vehicles: A survey. Digit. Commun. Netw. 2020, 6, 399–421. [Google Scholar] [CrossRef]
- Liu, X.; Yang, L. Analysis of Typical Attacks on Intelligent and Connected Vehicle Cyber Security. In Green, Smart and Connected Transportation Systems: Proceedings of the 9th International Conference on Green Intelligent Transportation Systems and Safety; Springer: Singapore, 2020; pp. 1039–1048. [Google Scholar] [CrossRef]
- Xu, X.; Li, X.; Dong, P.; Liu, Y.; Zhang, H. Robust Reset Speed Synchronization Control for an Integrated Motor-Transmission Powertrain System of a Connected Vehicle Under a Replay Attack. IEEE Trans. Veh. Technol. 2021, 70, 5524–5536. [Google Scholar] [CrossRef]
- Panda, S.; Panaousis, E.; Loukas, G.; Kentrotis, K. Privacy Impact Assessment of Cyber Attacks on Connected and Autonomous Vehicles. In Proceedings of the 18th International Conference on Availability, Reliability and Security (ARES ′23), Benevento, Italy, 29 August–1 September 2023; Association for Computing Machinery: New York, NY, USA, 2023; pp. 1–9. [Google Scholar] [CrossRef]
- Khan, S.; Sharma, I.; Aslam, M.; Khan, M.Z.; Khan, S. Security Challenges of Location Privacy in VANETs and State-of-the-Art Solutions: A Survey. Future Internet 2021, 13, 96. [Google Scholar] [CrossRef]
- Ghimire, B.; Rawat, D.B. Recent Advances on Federated Learning for Cybersecurity and Cybersecurity for Federated Learning for Internet of Things. IEEE Internet Things J. 2022, 9, 8229–8249. [Google Scholar] [CrossRef]
- D’Angelo, G.; Castiglione, A.; Palmieri, F. A Cluster-Based Multidimensional Approach for Detecting Attacks on Connected Vehicles. IEEE Internet Things J. 2021, 8, 12518–12527. [Google Scholar] [CrossRef]
- Khan, J.; Lim, D.-W.; Kim, Y.-S. Intrusion Detection System CAN-Bus In-Vehicle Networks Based on the Statistical Characteristics of Attacks. Sensors 2023, 23, 3554. [Google Scholar] [CrossRef] [PubMed]
- Yang, Y.; Duan, Z.; Tehranipoor, M. Identify a spoofing attack on an in-vehicle CAN bus based on the deep features of an ECU fingerprint signal. Smart Cities 2020, 3, 17–30. [Google Scholar] [CrossRef]
- Islam, R.; Refat, R.U.D.; Yerram, S.M.; Malik, H. Graph-Based Intrusion Detection System for Controller Area Networks. IEEE Trans. Intell. Transp. Syst. 2022, 23, 1727–1736. [Google Scholar] [CrossRef]
- van Wyk, F.; Wang, Y.; Khojandi, A.; Masoud, N. Real-Time Sensor Anomaly Detection and Identification in Automated Vehicles. IEEE Trans. Intell. Transp. Syst. 2020, 21, 1264–1276. [Google Scholar] [CrossRef]
- Liu, S.; Liu, L.; Tang, J.; Yu, B.; Wang, Y.; Shi, W. Edge Computing for Autonomous Driving: Opportunities and Challenges. Proc. IEEE 2019, 107, 1697–1716. [Google Scholar] [CrossRef]
- Yu, Z.; Liu, Y.; Xie, G.; Li, R.; Liu, S.; Yang, L.T. TCE-IDS: Time Interval Conditional Entropy- Based Intrusion Detection System for Automotive Controller Area Networks. IEEE Trans. Ind. Inform. 2023, 19, 1185–1195. [Google Scholar] [CrossRef]
- Markovitz, M.; Wool, A. Field classification, modeling and anomaly detection in unknown CAN bus networks. Veh. Commun. 2017, 9, 43–52. [Google Scholar] [CrossRef]
- Olufowobi, H.; Ezeobi, U.; Muhati, E.; Robinson, G.; Young, C.; Zambreno, J.; Bloom, G. Anomaly Detection Approach Using Adaptive Cumulative Sum Algorithm for Controller Area Network. In Proceedings of the ACM Workshop on Automotive Cybersecurity (AutoSec ‘19); Association for Computing Machinery: New York, NY, USA, 2019; pp. 25–30. [Google Scholar] [CrossRef]
- Young, C.; Olufowobi, H.; Bloom, G.; Zambreno, J. Automotive Intrusion Detection Based on Constant CAN Message Frequencies Across Vehicle Driving Modes. In Proceedings of the ACM Workshop on Automotive Cybersecurity (AutoSec ‘19); Association for Computing Machinery: New York, NY, USA, 2019; pp. 9–14. [Google Scholar] [CrossRef]
- Song, H.M.; Woo, J.; Kim, H.K. In-vehicle network intrusion detection using deep convolutional neural network. Veh. Commun. 2020, 21, 100198. [Google Scholar] [CrossRef]
- Ayyagari, M.R.; Kesswani, N.; Kumar, M.; Kumar, K. Intrusion detection techniques in network environment: A systematic review. Wirel. Netw. 2021, 27, 1269–1285. [Google Scholar] [CrossRef]
- Tariq, S.; Lee, S.; Woo, S.S. CANTransfer: Transfer learning based intrusion detection on a controller area network using convolutional LSTM network. In Proceedings of the 35th Annual ACM Symposium on Applied Computing (SAC ′20), Brno, Czech Republic, 30 March–3 April 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 1048–1055. [Google Scholar] [CrossRef]
- Longari, S.; Valcarcel, D.H.N.; Zago, M.; Carminati, M.; Zanero, S. CANnolo: An Anomaly Detection System Based on LSTM Autoencoders for Controller Area Network. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1913–1924. [Google Scholar] [CrossRef]
- Duan, X.; Yan, H.; Tian, D.; Zhou, J.; Su, J.; Hao, W. In-Vehicle CAN Bus Tampering Attacks Detection for Connected and Autonomous Vehicles Using an Improved Isolation Forest Method. IEEE Trans. Intell. Transp. Syst. 2023, 24, 2122–2134. [Google Scholar] [CrossRef]
- Ilango, H.S.; Ma, M.; Su, R. A misbehavior detection system to detect novel position falsification attacks in the Internet of Vehicles. Eng. Appl. Artif. Intell. 2022, 116, 105380. [Google Scholar] [CrossRef]
- Vijayanand, R.; Devaraj, D.; Kannapiran, B. Intrusion detection system for wireless mesh network using multiple support vector machine classifiers with genetic-algorithm-based feature selection. Comput. Secur. 2018, 77, 304–314. [Google Scholar] [CrossRef]
- Yang, L.; Moubayed, A.; Shami, A. MTH-IDS: A Multitiered Hybrid Intrusion Detection System for Internet of Vehicles. IEEE Internet Things J. 2022, 9, 616–632. [Google Scholar] [CrossRef]
- Odaibo, S. Tutorial: Deriving the standard variational autoencoder (vae) loss function. arXiv 2019, arXiv:1907.08956. [Google Scholar]
- Ahmed, M.; Seraj, R.; Islam, S.M.S. The k-means algorithm: A comprehensive survey and performance evaluation. Electronics 2020, 9, 1295. [Google Scholar] [CrossRef]
- Pradipta, G.A.; Wardoyo, R.; Musdholifah, A.; Sanjaya, I.N.H.; Ismail, M. SMOTE for Handling Imbalanced Data Problem: A Review. In Proceedings of the 2021 Sixth International Conference on Informatics and Computing (ICIC), Jakarta, Indonesia, 3–4 November 2021; pp. 1–8. [Google Scholar] [CrossRef]
- Curtis, A.; Smith, T.; Ziganshin, B.; Elefteriades, J. The mystery of the Z-score. Aorta 2016, 4, 124–130. [Google Scholar] [CrossRef] [PubMed]
- Azhagusundari, B.; Thanamani, A.S. Feature selection based on information gain. Int. J. Innov. Technol. Explor. Eng. (IJITEE) 2013, 2, 18–21. [Google Scholar]
- Breiman, L.; Friedman, J.; Olshen, R.A.; Stone, C.J. Classification and Regression Trees; Routledge: London, UK, 2017. [Google Scholar]
- Mitchell, R.; Frank, E. Accelerating the XGBoost algorithm using GPU computing. PeerJ Comput. Sci. 2017, 3, e127. [Google Scholar] [CrossRef]
- Yoshua, B.; Grandvalet, Y. No unbiased estimator of the variance of k-fold cross-validation. J. Mach. Learn. Res. 2004, 5, 1089–1105. [Google Scholar]
- Alpaydin, E. Machine Learning; MIT Press: Cambridge, MA, USA, 2021. [Google Scholar]















| Type of Attack | Rogue Networks | Data Eavesdropping | Information Forgery, Tampering and Replay | Privacy Leakage |
|---|---|---|---|---|
| DoS | √ | |||
| GPS Spoofing | √ | |||
| Jamming | √ | |||
| Sniffing | √ | |||
| Brute-force | √ | |||
| Botnets | √ | |||
| Infiltration | √ | |||
| Web Attack | √ |
| IDS Types | Reference | Internal Network | External Network | Detection Targets | Types of Attacks |
|---|---|---|---|---|---|
| FIDS | [34] | √ | ID | DOS, Tampering, Fuzzy | |
| [35] | √ | ID | DOS, Fuzzy | ||
| [36] | √ | ID | Tampering | ||
| [37] | √ | ID | DOS, Tampering, Fuzzy | ||
| RIDS | [38] | √ | ID | Web attack | |
| [39] | √ | ID | DOS | ||
| SIDS | [40] | √ | Data field | Web attack | |
| [41] | √ | ID | DOS, Tampering, Fuzzy | ||
| [42] | √ | Data field | Inject | ||
| [43] | √ | ID | Inject, DOS | ||
| M/DIDS | [44] | √ | ID | Inject | |
| [45] | √ | Data field | Tampering, DOS | ||
| [46] | √ | Data field | Tampering, DOS | ||
| [47] | √ | ID | Tampering | ||
| [48] | √ | Data field | Forgery | ||
| [49] | √ | Data field | Tampering | ||
| [50] | √ | ID | Tampering, DOS | ||
| [51] | √ | √ | ID, Data field | DOS, Fuzzy, Gear, RPM |
| Data Types | Original Data Size | Generated Data Size |
|---|---|---|
| Normal | 1,048,575 | 5,242,875 |
| DoS | 447,978 | 2,239,890 |
| Fuzzy | 259,676 | 1,798,380 |
| RPM | 384,300 | 1,921,500 |
| Gear | 499,020 | 2,495,100 |
| WS | 499,425 | 2,497,125 |
| ABS | 744,385 | 3,721,925 |
| BSI | 434,375 | 2,171,875 |
| BV | 555,625 | 2,778,125 |
| Data Types | Original Data Size | After Preprocessing Size |
|---|---|---|
| Normal | 2,273,097 | 2,273,097 |
| DoS | 380,699 | 380,699 |
| Port-Scan | 158,930 | 158,930 |
| Brute-Force | 13,835 | 13,835 |
| Web-Attack | 2180 | 10,000 |
| Botnet | 1966 | 10,000 |
| Infiltration | 36 | 10,000 |
| Proposed IDS | Accuracy (%) | Precision (%) | Recall (%) | F1-Score | Training Time (S) |
|---|---|---|---|---|---|
| using the original feature extraction | 100 | 100 | 100 | 1 | 1237.1 |
| Using IG-NF feature extraction | 99.99 | 99.99 | 99.99 | 0.999 | 331.6 |
| Proposed IDS | Accuracy (%) | Precision (%) | Recall (%) | F1-Score | Training Time (S) |
|---|---|---|---|---|---|
| using the original feature extraction | 99.86 | 99.8 | 99.77 | 0.9978 | 3519.3 |
| Using IG-NF feature extraction | 99.83 | 99.75 | 99.76 | 0.9977 | 2786.8 |
| IDS | Accuracy (%) | Precision (%) | Recall (%) | F1-Score |
|---|---|---|---|---|
| DCNN | 96.62 | 93.38 | 96.62 | 0.949 |
| Proposed | 99.99 | 99.99 | 99.99 | 0.999 |
| IDS | Accuracy (%) | Precision (%) | Recall (%) | F1-Score | Time (s) |
|---|---|---|---|---|---|
| MTH-IDS | 99.88 | 99.81 | 98.25 | 0.998 | 1563.4 |
| Proposed | 99.83 | 99.75 | 99.76 | 0.997 | 352.8 |
| Datasets Type | Accuracy (%) | Precision (%) | Recall (%) | F1-Score |
|---|---|---|---|---|
| Internal | 99.97 | 99.97 | 99.97 | 0.9997 |
| External | 99.81 | 98.33 | 91.95 | 0.9467 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhou, X.; Wu, Y.; Lin, J.; Xu, Y.; Woo, S. A Stacked Machine Learning-Based Intrusion Detection System for Internal and External Networks in Smart Connected Vehicles. Symmetry 2025, 17, 874. https://doi.org/10.3390/sym17060874
Zhou X, Wu Y, Lin J, Xu Y, Woo S. A Stacked Machine Learning-Based Intrusion Detection System for Internal and External Networks in Smart Connected Vehicles. Symmetry. 2025; 17(6):874. https://doi.org/10.3390/sym17060874
Chicago/Turabian StyleZhou, Xinlei, Yujing Wu, Junhao Lin, Yinan Xu, and Samuel Woo. 2025. "A Stacked Machine Learning-Based Intrusion Detection System for Internal and External Networks in Smart Connected Vehicles" Symmetry 17, no. 6: 874. https://doi.org/10.3390/sym17060874
APA StyleZhou, X., Wu, Y., Lin, J., Xu, Y., & Woo, S. (2025). A Stacked Machine Learning-Based Intrusion Detection System for Internal and External Networks in Smart Connected Vehicles. Symmetry, 17(6), 874. https://doi.org/10.3390/sym17060874






