Abstract
Cloud security automation has emerged as a critical solution for organizations facing increasingly complex cybersecurity challenges in cloud environments. This study examines the current state of cloud security automation, focusing on its role in symmetry between threat detection and response capabilities. Through analysis of recent market trends and technological developments, this paper explores key technologies, including Security Information and Event Management (SIEM), Extended Detection and Response (XDR), and Security Orchestration, Automation, and Response (SOAR) platforms. The integration of artificial intelligence and machine learning has transformed these systems, enabling real-time threat detection and automated response mechanisms. The research examines real-world applications and highlights that organizations implementing automated security solutions have demonstrated improved incident response times and reduced security breaches. However, challenges remain in terms of the complexity of integration and symmetry between automation and human expertise. As the global AI cybersecurity market is projected to reach $134 billion by 2030, the future of cloud security automation lies in advanced AI-driven solutions and improved threat intelligence integration. Even though cloud platforms are widely used, existing security tools have challenges in identifying real-time threats, the integration of heterogeneous data sources, and actionable intelligence generation. The majority of current solutions are not designed for cloud-native platforms and do not scale or evolve. This paper overcomes these challenges by introducing a scalable and extensible cloud security architecture, which uses sophisticated correlation and threat intelligence to provide increased detection accuracies as well as reduced response times for the challenging environment of advanced cloud-based infrastructures. This research aims to equip organizations with proven methods from real-world use cases and strategies that they can adopt to enable automated threat detection and response.
1. Introduction
In the cloud security paradigm, threat detection and response exhibit structural and functional symmetry, where each detected threat triggers a corresponding automated or manual response. Cloud security is critical due to the increasing reliance on cloud computing to store, process, and transmit sensitive data across various sectors. As cloud services become integral to business operations, ensuring robust security measures is essential to protect against unauthorized access, data breaches, and other cyber threats. The complexity of cloud environments, coupled with the need for compliance with regulatory standards, underscores the importance of implementing comprehensive security strategies [1]. Cloud computing, being dynamic, provides massive scalability and flexibility but brings with it severe security threats, such as data breaches, malware attacks, and insider threats, that businesses must proactively address [2]. In the cloud security context, threat detection and response (TDR) is an important function in cloud environments, and its value in the cloud threat detection system market is a reflection of its value in terms of strategy. According to research [3], in 2024, the value of the threat detection market was approximately USD 13.4 billion and is forecasted to rise nearly USD 50 billion in 2031. Threat detection systems involve thorough practice and policies that function towards checking an organization’s security environment and any developing potential for malice. The increased value in the market reflects increased cybersecurity complications, which are fueled by geopolitical competition and sophisticated cyber-attackers. Threat detection systems have a critical function in discovering and preventing potential cybersecurity threats from causing meaningful loss to organizational networks and infrastructure for information. Automation is important in enhancing cloud security through effective and timely responses to threats for organizations. Gill et al. [4] state that automation in cloud security helps in continuous monitoring, timely incident response, and the uniform imposition of policies. The authors emphasize that automation is important in such a case because security information in cloud environments, at present, is high in volume and complex in form. They further note that security can be automated in a way that reduces manpower and maximizes efficiency and accuracy in security operations. Security automation is increasingly becoming a necessity, with estimates suggesting a significant proportion of cloud security breaches have been a result of human errors. Automated processes can counter such events by eradicating error-filled manual processes. Gill confirms deep neural networks between internet of things (IoT) and the cloud can, when combined, yield 95.84% accuracy in security tracking and attack detection. Automated processes can scan and monitor security settings in real time and detect and correct vulnerabilities, even before an attack can target them. Convergence between cloud security, attack detection, and automation is an expansive cybersecurity model. With technology and intelligence, companies can build smarter security architectures capable of dynamically countering emerging cybersecurity threats and protecting critical digital assets. With security having long been a significant impediment to cloud computing, companies can utilize automated deep learning techniques to address it. The remainder of this article is structured as follows: Section 2 presents a comprehensive review of the related literature, highlighting research gaps and comparing them with this work. Section 3 describes the proposed methodology and the questions that guided this research direction. This section also includes a table that compares existing studies, their limitations, and how this work contributed to filling the research gaps. Section 4 explores the cloud security and threat landscape that is continuously evolving and the challenges that it presents. Section 5 explains the concept of automating security and its importance in cloud infrastructures. Section 6 describes the key technologies and tools that are essential for cloud security automation. Section 7 proposes the method with which to implement automated threat detection and response in the cloud. Section 8 presents some of the real-world case studies and applications. Section 9 discusses the challenges and the limitations of the solution and the challenges of automating cloud security. This section also discusses the importance of balancing human expertise with automation. Section 10 lists the opportunities and future studies that could further enhance cloud security automation. Finally, Section 11 concludes the paper and suggests directions for future research.
2. Related Work
Cloud security has been an active area of research, particularly in the domains of automation, threat detection, and incident response. Several studies have examined the individual components of this domain, such as threat intelligence integration, behavior-based detection techniques, and orchestration platforms like SIEM and SOAR. In this section, we review and analyze the most relevant existing literature, highlighting the focus areas, contributions, and limitations in the context of our study. The summary of this comparison is also listed in Table 1.

Table 1.
Comparison of existing studies and their limitations with this study.
The study by Kumar et al. [5] proposes a machine learning-based intrusion detection system that utilizes machine learning models such as Support Vector Machine (SVM) and eXtreme Gradient Boosting (XGBoost) for threat detection; however, the study does not discuss automated responses. In contrast, this work covers end-to-end automation, including threat response. The works by Dantoni et al. [6] present an approach that synthesizes a modified AWS IAM policy that is more restrictive and follows the principle of least privilege. However, this study is very specific to AWS clouds and covers only the access control aspects. On the other hand, this study is cloud-agnostic and discusses multi-cloud and hybrid infrastructures. The study by Ali et al. [7] presents an automated machine learning framework that effectively recommends cybersecurity standards, audits, and compliance measures, thereby enhancing and systematically monitoring cybersecurity infrastructure across critical industries; however, this study is not specific to cloud security. The proposed study focuses on cloud infrastructures. In [8], the authors review various criteria and methods for alert prioritization in security operations centers or SOCs; this study highlights the role of AI in processing large volumes of alert data, identifying anomalies, and prioritizing alerts. The study does not address the dynamic and scalable nature of cloud environments, where resources can be provisioned and de-provisioned in short spans of time. The automation proposed in this study is capable of scaling to meet dynamic workloads. In [9], Wu et al. suggest a game-theoretical model to study cloud security management, focusing on the joint responsibility of cloud providers and firms in the presence of strategic hackers. This model helps analyze the investment decisions related to cloud security and the implications of ignoring strategic hackers. However, this study lacks a comprehensive framework for threat detection. This study recommends solutions with improved incident response, thereby reducing security breaches. Ref. [10] introduces a new framework that combines the strengths of Transformer models and Graph Neural Networks (GNNs) to enhance the detection of system anomalies in cloud environments. The framework incorporates an anomaly detection mechanism that allows it to focus on critical features of the data, improving the accuracy of anomaly detection. Although the study improves anomaly detection accuracy, it does not discuss how to respond to detected anomalies. Effective incident response requires predefined protocols and actions to mitigate threats once they are identified. The absence of such mechanisms limits the practical applicability of the findings in real-world scenarios. In contrast, this study recommends strategies for both automated threat detection and response.
The main contributions of this paper are the following:
- This paper proposes a modular, scalable architecture tailored for cloud environments, integrating essential SIEM components, such as data collection, normalization, storage, correlation, and alerting, all into one framework;
- This study proposes a novel cloud security architecture that integrates SIEM, SOAR, XDR, and other capabilities with threat intelligence for improved incident detection and response;
- This research aims to provide organizations with practical methods and strategies based on real-world cases to help them implement automated threat detection and response;
- The study provides a comparative analysis, highlighting how this approach differs from traditional cloud security frameworks in terms of scalability, automation, and detection accuracy.
3. Research Methodology
This study follows a structured approach to examine the landscape of cloud security automation, threat detection, and response mechanisms. The methodology is designed to ensure transparency, reproducibility, and relevance of the findings that can be utilized by organizations in implementing a holistic security solution, particularly for cloud platforms. The key components of the research process are described in detail in the following sections.
3.1. Research Questions
The following research questions guided the scope and direction of this study:
- Question 1: What are the current approaches to automating cloud security operations?
- Question 2: What techniques and tools are used for threat detection in cloud environments?
- Question 3: How do organizations implement and evaluate response strategies for cloud-based security incidents?
- Question 4: What are the emerging trends and open research challenges in cloud security automation?
To ensure quality and relevance, references were selected from top peer-reviewed journal articles, conference papers, and sources that present statistical information or analysis. We used publications that explicitly focus on cloud-native environments, security automation, threat detection, or incident response published in the last 3–5 years.
Articles focused exclusively on on-premises or legacy systems without cloud relevance or papers lacking methodological rigor or sufficient technical detail were excluded.
3.2. Databases and Sources
The following academic and industry research databases were used to retrieve relevant publications:
IEEE Xplore, ACM Digital Library, SpringerLink, ScienceDirect, Google Scholar, Statistica, and other online sources.
3.3. Search Strategy and Keywords
A keyword-based search strategy was applied to each database using combinations of the following terms:
“cloud security automation”, “automated threat detection in cloud”, “incident response in cloud environments”, “cloud-native SIEM”, “SOAR platforms”, “cloud workload protection”, “security orchestration automation”.
4. Understanding Cloud Security and the Threat Landscape
Understanding the cloud security threat landscape is paramount for ensuring the confidentiality, integrity, and availability of data and services hosted in cloud environments. This landscape is constantly evolving, with new threats emerging alongside the rapid adoption of cloud technologies. Furthermore, the distributed nature of cloud computing introduces complexities in security management, requiring robust access control mechanisms, data encryption, and continuous monitoring. A comprehensive understanding of these threats and vulnerabilities is crucial for developing effective security strategies and mitigating potential risks in the cloud. This section explores the multifaceted dimensions of cloud security, highlighting key threats and proposing strategies to mitigate them.
4.1. Common Security Threats in Cloud Environments
The current cloud security landscape is filled with multiple and complex threats that organizations must prepare against ahead of time. A recent statistics project stated that in the third quarter of 2024, 422.61 million data records were compromised due to breaches, demonstrating the extent of data security problems [11]. Data breaches are serious issues because they affect individuals, companies, and government entities simultaneously. The cost per incident, on average, is USD 4.88 million. This includes expenses related to breach discovery, business disruption, post-breach response, and notification. Their seriousness can be understood through recent instances like the Jerico Pictures breach involving 2.9 billion personal data records, which reportedly affected all American citizens. More than 55% of organizations worldwide suffered business disruption and loss of revenue because of data breaches, showing how much these breaches affect business operations. Moreover, about 48% of all data breach cases in 2024 involved customer personal information (PII), which was the most targeted data type. Another considerable danger in cloud environments is malware and ransomware attacks, which have become more advanced and damaging. According to Gursimsir [11], organizations worldwide detected 317.59 million ransomware attempts in 2023, with a significant decrease between the third and fourth quarters of 2022. The threat landscape has expanded to include sophisticated attack models like Ransomware as a Service (RaaS). In the first quarter of 2022, there were 31 RaaS extortion groups worldwide, compared to 19 in the same quarter of 2021. These attacks often target critical infrastructure, with North America and Europe being the most affected regions. The attacks can cause significant harm, including device lockdown, data theft, encryption, system control compromise, and credential theft. Notably, many organizations prefer paying ransoms to restore stolen data rather than reporting attacks, which can further damage their reputation. Healthcare and public health sectors filed the highest number of ransomware attack complaints to US law enforcement in 2022. Insider threat and misconfiguration represent significant security concerns in cloud computing, predominantly a result of human mistakes or deliberate malicious behavior [12]. Complexity in cloud environments is responsible for security difficulty in that cloud technology enables access to enormous resources beyond traditional IT infrastructure. According to the authors, cloud computing grants access to infinite storage capacity and server resources, with the potential to create security vulnerabilities unconsciously. According to the authors, traditional user identification, authentication, and access management tools cannot simply apply to cloud environments. Outside data storage, a lack of user control, and inbuilt models present significant security vulnerabilities. Additionally, cloud providers secure only the cloud platform, and therefore, customers’ information can become susceptible to security vulnerabilities. Cloud misconfiguration continues to be a significant issue, and this is mostly because cloud service providers continue to introduce new services. Most organizations today utilize more than a single cloud provider, each with different default settings and modes of operation, thereby contributing to the complexity of security management [13]. Complexity is increased as cloud configurations become heterogeneous and interconnected, and it is difficult to maintain consistent security procedures on different platforms. Moreover, the lack of standardized security practices and the rapid evolution of cloud technologies are some reasons why insider-related security breaches remain an issue.
4.2. Key Security Principles in the Cloud
The basic principles of cloud security are based on the traditional CIA triad: Confidentiality, Integrity, and Availability. Keeping data confidential in cloud environments is more critical than ever, as companies rely on cloud platforms to run business applications that move or store data in different locations [14]. The author of [15] writes that almost half of the world’s business leaders placed data trust or data protection at the top of their 2025 cybersecurity investment. This shows how important it is to keep data private in cloud environments. Integrity in cloud environments will ensure that data are not modified by unauthorized users. In contrast, availability will ensure people can still access cloud services and resources despite problems or attacks. The shared responsibility model is considered to be one of the key models for explaining security responsibilities in cloud computing. Companies must understand that even though cloud service providers are always securing cloud infrastructure, it is the customers’ responsibility to secure data, applications, and identity access management. The security controls in any organization must include a stringent way of identifying and controlling the users’ access, data encryption, and security checks. As mentioned by Noor et al. [16], threat detection and response mechanisms are key features for fulfilling the requirements of the collaborative security responsibility model for providing end-to-end fortification in cloud infrastructure. The authors stress that the successful establishment of security in an object requires the administration of fundamental security measures and processes in terms of identity and access management, data encryption, and security assessments. In addition, the need to embrace comprehensive security systems that are made of corresponding technologies and people in order to achieve practical and effective cloud security is extremely important.
5. Cloud Security Automation: Concept and Importance
Cloud security automation is a critical concept that involves the use of automated tools and processes to enhance the security of cloud environments while reducing errors caused by manual security management. Automation in cloud security helps translate high-level security needs into actionable security measures, optimize resource placement, and ensure compliance with security best practices.
5.1. Definition of Cloud Security Automation
Cloud security automation is a principal mechanism for cloud environment security and cloud environment management through processes and tools that execute in an automated form. As cloud computing matures, security automation is imperative in countering larger attack surfaces and complex cyber threats [17]. Security automation involves leveraging tools, workflows, and scripts for security improvement processes with a view to providing high security in complex cloud environments for companies. Security automation in cloud environments aids in continuous monitoring, high-speed incident response, and consistency in adhering to policies. Security automation in cloud environments aids in manpower savings and security activity velocity and accuracy improvement, specifically in scenarios of inefficient manpower activity. Security automation goes further than automating specific tasks, overlapping with DevSecOps workflows and security-as-code principles. Security automation involves the workflow orchestration of security tools, the implementation of automated responses, and the use of advanced analytics in threat identification from large volumes of data [18]. The authors observe that AI/ML-powered cyber defense systems are vital in confronting the ever-rising volume and complexity of threats by enabling organizations to analyze large datasets and identify anomalies and suspicious patterns that are symmetrical in nature in real time. A survey conducted recently discovered that organizations are speeding up the adoption of AI/ML in cybersecurity, and nearly three-quarters of organizations are testing use cases for AI/ML in cybersecurity. The report highlights that AI/ML is helping organizations keep their security controls in place while transforming to thwart new threats and compliance demands. With the integration of security controls in application development at an early level, organizations are in a position to move from reactive to proactive security controls. The complex nature of cloud security automation can be better understood through a detailed examination of its workflow and system architecture. Figure 1 illustrates the architecture of the cloud security automation system, its components, and the intricate relationships between various components and functions that work together to create a comprehensive security automation system, from initial data collection through analysis to response mechanisms.
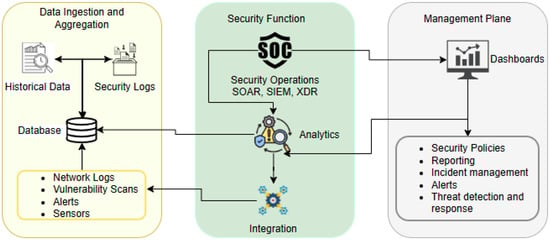
Figure 1.
Cloud security automation system architecture.
The automation mechanism in cloud security takes place through an integrated platform, beginning with a comprehensive collection of information through a range of sources. Information is aggregated in the Data Ingestion and Aggregation layer through cloud and on-premise services, network activity, security logs, and a variety of security tools, including alerts/sensor systems, network analysis tools, and vulnerability scanners. All such information is consolidated through a Database Management System (DBMS), and it is the basis for security analysis and response. At the heart of the workflow is Security Operations Functions, an integrated stack of SIEM, UTM, SOAR, IPS/IDS, XDR, and threat intelligence platforms. All these function in collaboration with advanced analytics, AI/ML algorithms processing aggregate information for security threat identification, abnormalities, and trends that can represent security concerns. Automated analysis and evaluation of security potential threats in this analysis layer transmit its intelligence to a security operations layer for applicable reaction actions. The final stage involves integration functions and the management plane, in which the analysis and reaction of the system are coordinated and presented in a proactive dashboard. Real-time alerts, warnings, attack prediction, and incident reaction reporting form part of its interface and allow for continuous visibility when an automated reaction occurs for security operations center (SOC) operators. Security policies can be defined and enforced in the management plane layer, which serves as the central control interface for managing cloud security. All workflows occur in a continuous state and enable companies to detect and respond to security incidents in real time, with significant improvement in reaction times from days and hours to seconds and minutes and the continuous application of security policies in cloud infrastructure.
5.2. Benefits of Automating Security in the Cloud
Computerized security systems have transformed how threats are discovered and resolved quickly and effectively in cloud platforms. Zahoor [19] believes that integrating AI with cloud automation has dramatically improved the ability to gather and analyze extensive security data, enabling faster and more precise threat detection. Newer cloud security automation tools can immediately identify and remediate possible threats, cutting down drastically on the time from threat discovery to threat remediation. Security operations are automated, and teams can act rapidly on threats that they identify, often before threats can harm the organization’s data or systems. This ability to respond quickly is essential today because cyberattacks spread soon in interconnected cloud infrastructures. Human mistakes continue to be a significant issue regarding cloud security. It has been estimated that through 2025, 99% of the security breaches in the cloud will be due to mistakes or misconfigurations that end users could have avoided [20]. Cloud security automation resolves this issue by eliminating several manual processes that can result in errors. Automated security controls, settings management, and compliance scanning ensure that security operations are consistent and accurate. Automation tools for security can monitor and scan security settings continuously, detecting and correcting errors before attackers can exploit them. Automation in cloud security allows organizations to scale their security operations efficiently without sacrificing consistent protection in growing cloud environments. Automated programs manage security operations on multi-cloud platforms and applications with broad coverage. The transition from manual to automated configuration has become attainable since the early 2010s, attributed to a series of innovations, most prominently network softwarization, encompassing its two variants identified as Network Functions Virtualization (NFV) and Software-Defined Networking (SDN), along with Policy-Based Management (PBM) [21]. Scalability is essential when companies grow their cloud footprint, making manual security management unfeasible. Automated security solutions handle vast volumes of data, detect patterns, and respond to threats in cloud infrastructure more effectively than human monitoring. Scaling security through automation enhances efficiency and keeps measures in place as the organization grows. This simplifies the work of organizations in meeting their compliance requirements. Automated compliance checking can continuously validate that cloud resources meet defined standards, automatically remediate non-compliant configurations, and generate clear compliance reports. Implementing security automation ensures that organizations keep their security practices in sync across multiple cloud environments and that compliance requirements are always met for all cloud resources.
6. Key Technologies and Tools for Cloud Security Automation
Having explored the criticality of cloud security and automation, it is important for companies to understand the available tools and frameworks that can be deployed to implement and improve security posture.
6.1. Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) systems are security systems that gather, consolidate, store, and correlate events generated by many network infrastructure components in an effort to prevent, detect, and respond to cyber-attacks [22]. SIEM systems serve as the central platform for today’s security operations, gathering events from many sensors, like intrusion detection tools, anti-malware software, and firewalls, and issuing synthesized alerts for managing threat and security reporting. SIEM systems display real-time security events generated by network devices and software, enabling companies to identify high-risk areas and actively strive to reduce cost and incident response time through mitigation strategies. SIEM systems have become essential after a surge in cybersecurity threats targeting industrial control systems, with heightened activity from nation-states and hackers. The integration of AI and machine learning capabilities has changed SIEM capabilities through their ability to apply sophisticated and complex mechanisms to threat detection and response. With its use of machine learning algorithms, SIEM can search through enormous datasets to model and learn about the behavior and application of users, and it can then detect deviation and anomalous behavior that is statistically significant [23]. AI-powered security can search through enormous datasets in real time and detect suspicious activity and emerging threats, even when they have not yet been capable of inflicting significant loss and damage. With a combination of traditional heuristic and signature-based tools and anomaly-based detection, modern SIEM platforms can effectively reduce occurrences of False Positive and maximize accuracy in detection. With AI technology in SIEM, predictive capabilities have become effective in analyzing anomalous behavior in the activity, tools, and network traffic of a user [24].
Figure 2 illustrates the key components involved in a typical SIEM system. SIEM technology aggregates information about events derived from various data sources in an organization’s IT infrastructure, such as security devices, network infrastructure, servers, programs, and access logs. These data are fed into a data collection and normalization layer, where agents, APIs, and log forwarders enrich the data for consistent analysis. The processed data are then stored in persistent storage, such as a database. The correlation engine is the core of the analytical function that is responsible for detecting threats by co-relating events using rule-based, statistical, or advanced reasoning [25]. Finally, the last layer comprises a dashboard, reporting, and alerting that visualizes the organization’s security posture, enables ad-hoc reporting, and sends out alerts for incident response. The information collection and analysis capabilities of SIEM, in its totality, make real-time attack data breach discovery, incident response, forensics, and compliance requirements, in addition to supporting, feasible. SIEM technology unifies events and information in disparate sources, and analysis for specific use cases, such as network security incident and event monitoring, activity tracking for a user, and compliance reporting, is facilitated through SIEM technology.
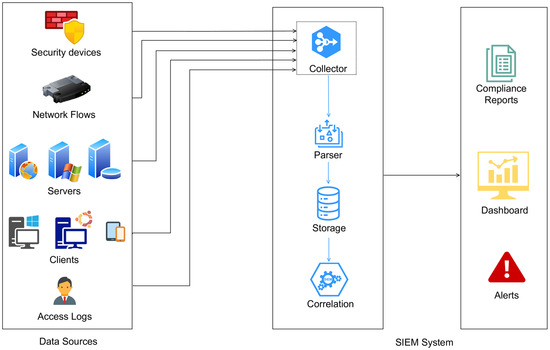
Figure 2.
Components of Security Information and Event Management (SIEM) [25].
6.2. Extended Detection and Response (XDR)
Extended Detection and Response (XDR) is a new cybersecurity model that addresses threat detection and response as a whole, not in parts. XDR, according to Kaur et al. [26], is an open cybersecurity model that brings security operations together at all layers, including people, endpoints, emails, networks, applications, and cloud performance. XDR has several distinguishing factors over conventional Endpoint Detection and Response (EDR) tools. XDR goes beyond endpoints to include a variety of sources of information, providing end-to-end detection and response for the whole IT infrastructure. By correlating and analyzing information from disparate sources, XDR eradicates missed detections and false positives through deep analysis, machine learning, and intelligence regarding threats. XDR simplifies incident response through contextual awareness of threats in disparate endpoints and segments of a network, allowing security operations teams to prioritize and investigate incidents in an effective and efficient manner. In studies, XDR is seen to remove gaps in security tools’ visibility, segmented in the past, and give overworked security operations teams immediate and simple access to expansive threat detection and response; thus, XDR can make an organization’s overall cybersecurity position strong. The effectiveness of the threat detection of XDR can be quantified in terms of a variety of key performance factors. For instance, for measurement of the performance of the system, Intrusion Detection Capability () is calculated as shown in Equation (1);
where I(X;Y) represents the mutual information between input X and output Y, and H(X) represents the uncertainty of the input, which can be computed as shown in Equation (2);
where B represents the probability of an intrusion occurring, and 1−B represents the probability that an intrusion does not occur [27]. The system uses a binary classification where, for input X, X = 1 represents an intrusion, and X = 0 represents a non-intrusive event, while for output Y, Y = 1 represents an alert, and Y = 0 denotes no alert. () incorporates several performance metrics, including base rate (B), True Positive Rate (), False Positive Rate (), Positive Predictive Value (PPV), and Negative Predictive Value (NPV). The AI capabilities of XDR, according to González-Granadillo et al. [28], enable predictive analysis in terms of identifying anomalous behavior in network activity and system behavior that can act as precursors for security threats and enable proactive countermanding of such threats.
6.3. Security Orchestration, Automation, and Response (SOAR)
Security Orchestration, Automation, and Response (SOAR) is an advanced technology tool allowing for effective security alert management and incident response for businesses. Nguyen et al. [29] say that security alert overload and complexity, a problem that comes with high volumes and high complexity of security alerts, is addressed through SOAR platforms. Manual and semi-manual processes have seen businesses take several weeks and even months to detect and respond to a security incident. The market for SOAR is developing at a high pace, fueled by several key factors. Bridges et al. [30] cite that companies are struggling to manage a high level of security alerts, and security professionals cannot respond and act in a timely manner to incidents. Lee et al. [31] cite that the increased use of big IoT and hyper-connected network environments has forced companies to develop security response systems with little human intervention. The growing number of cybersecurity threats and scarcity of trained cybersecurity professionals make them two of the most important drivers for SOAR technology adoption. In [29], the authors note that SOAR tools can detect and respond to threats in a much shorter timeframe than humans, with a platform that can respond near-immediately in terms of incident detection and response. The technology aims to integrate security tools, simplify repetitive security processes, and provide a more complete incident management solution.
6.4. Machine Learning and AI in Security Automation
The use of artificial intelligence and machine learning in automating cloud security is a tremendous leap forward in how we defend against cyber-attacks. The AI cybersecurity market is expected to show significant growth, increasing from USD 24.3 billion in 2023 to nearly USD 134 billion by 2030, as reported by Borgeaud [19]. This shows that AI-based security solutions are growing in importance. Recent polls indicate that deep learning employed in the detection of malware within encrypted traffic is the top emerging AI technique. A total of 48% of respondents cited it as the top defense tool. It is followed by natural language processing for identifying sophisticated phishing at 19% and transfer learning for rapid adaptation to new threats at 18%. This high emphasis on deep learning indicates that organizations recognize how AI can enhance threat detection, vulnerability management, and the speed with which they react to incidents. It also addresses the constant challenge of not having sufficient skilled professionals in cybersecurity. The use of AI in security automation offers many benefits to organizations for their security. As discussed by Zaman [32], AI helps in the early identification of threats through the detection of hidden or small dangers that regular security tools might not detect. These tools allow for quicker detection and response to help prevent further damage. The technology can quickly scan large amounts of data, giving organizations useful information for better risk assessment and prioritization. It also speeds up security data analysis so that threats can be identified almost in real time, allowing for quicker decision-making compared to manual methods. Adaptive threat detection is one of AI security automation’s most important use cases. AI software can detect new cybersecurity threats in real time through ongoing learning and observation of past trends and allow organizations to defend in a smarter way [33]. For example, AI technology can monitor network flow to detect nontypical spikes in requests for information that can serve as an indicator of a DDOS attack and allow for rapid reaction. Generative AI in security automation brings an organization new security control and improvement mechanisms. As per Wendt [34], AI produced via a model initially designed for use in generating works, but increasingly useful in cybersecurity, aids in filtering through a lot of information in an endeavor to identify anomalous activity and detect malice. Organizations, nevertheless, have to exercise caution in that AI produced via a model can also be exploited for misuse by malevolent parties. Therefore, they need to utilize the technology in a way that considers both security and misuse. AI integration in security automation has profoundly boosted predictive analysis and anomalous activity detection. AI platforms have a strong capability to process sophisticated information for unhidden pattern discovery and develop insights that make predicting future danger easier and simpler. With such a feature, companies can utilize augmented techniques to minimize danger even beforehand. AI-powered tools can also scan network activity, system logs, and behavior in real time for anomalous activity that can denote security danger and provide security professionals with early indications of impending breaches and attacks [35]. The role of AI in automating security operations continues to evolve, with organizations increasingly recognizing its potential to transform their security postures. As the technology matures, the focus shifts from merely detecting and responding to threats to predicting and preventing them before they materialize. This evolution represents a fundamental change in how organizations approach security automation, moving from reactive to proactive security measures. Following this emerging function of AI within security operations, Random Forest algorithms have played a particularly significant role in enabling this proactive security stance. As Wu and Chang [36] discuss, Random Forest models are capable of malware detection through the analysis of complex patterns across a sequence of decision trees, where each tree evaluates alternative feature subsets to build a robust detection system. Through this ensemble approach, organizations are able to identify potential threats before they are able to execute their malicious payloads, with detection accuracies of over 97% when properly applied.
Figure 3 shows the general architecture of an AI-based anomaly detection system. The integration with decision-making capabilities through automation is supported by continuous feature adaption and continuous learning. As exhibited by Khammas [37], present implementations of Random Forest can evaluate high-dimensional security information in real time, checking thousands of features in a single pass in an attempt to discriminate between hostile and innocent behavior. With multi-dimensional analysis, security operations can move beyond simple threat detection and predictive threat hunting and detect emerging attack channels even when such channels have not yet become exploitable. Organizations can leverage these AI features to build strong security models that combine traditional security controls with advanced machine learning algorithms. Using such a hybrid approach allows security professionals to focus on high-priority projects and have low-level threat analysis and early response procedures handled by automated systems, representing a new chapter in cybersecurity practice.
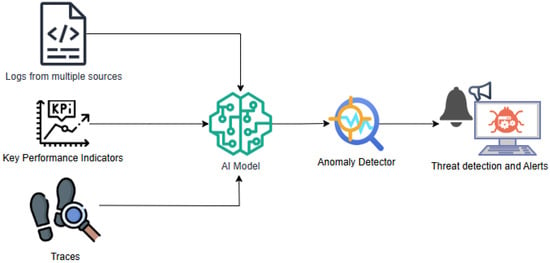
Figure 3.
Overview of AI-based anomaly detection system.
A real-world example of an AI security tool is Google Chronicle, which represents a novel paradigm for AI-driven security analysis designed for analyzing and processing security telemetry at a cloud scale. In contrast to traditional SIEM, Chronicle leverages Google infrastructure to enable real-time analysis and contextualization of security events using automated data enrichments and correlations. The platform uses a number of AI features to enhance security threat detection and incident response [38]. Chronicle’s AI infrastructure enriches streaming real-time data with a correlation of hostnames and IPs and continuous real-time matching with threat intelligence feeds. Anomaly detection is supported through the use of the platform’s machine learning, generating baseline behavior and deviation, for example, in instances of out-of-character working-hour access activity, such as when a user’s logins transition from ordinary 7am–5pm activity to suspicious 11pm access attempts. Chronicle leverages sophisticated analysis in addition to its AI use, for example, in instances of out-of-character activity such as beaconing to seldom visited domains, potentially indicative of command and control activity. The platform’s single, unified model for logs, networks, and endpoint telemetry generates rich, contextualized stories about threats with no complex queries, enabling security professionals to effectively detect and respond to sophisticated attacks in a timely manner.
7. Implementing Automated Threat Detection and Response in the Cloud
7.1. Threat Intelligence Integration
Threat intelligence integration is critical in cloud security automation for implementing active threat detection and reaction. According to Wagner et al. [39], Cyber Threat Intelligence (CTI) information sharing is a new weapon for cyber defenders to proactively mitigate emerging cyber-attacks. According to the study, CTI helps organizations build situational awareness for stakeholders through information exchange regarding emerging threats and vulnerabilities, allowing for rapid remedy deployment. Organizations can utilize threat intelligence from a variety of sources, including open-source feeds, vendors, and shared platforms. The authors emphasize that CTI is not raw information but analyzed and actionable intelligence. As seen in the study, current processes for sharing have been predominantly manpower-intensive, with 39% of respondents reporting that slow and manual processes for sharing discourage full CTI exchange participation. Threat intelligence platforms integrated with Intrusion Detection Systems (IDSs) and Security Information and Event Management (SIEM) can significantly boost overall security through a fuller and timely threat detection and reaction mechanism.
7.2. Automated Incident Response Playbooks
Automated incident response playbooks have become increasingly important for organizations wishing to enhance security operations and incident response times. The Australian Cyber Security Centre (ACSC) [40] identifies growing attack sophistication and frequency, with over 76,000 reports of cybercrimes from 2021–2022, an increase of nearly 13% over the previous year. Automation helps organizations address a variety of critical concerns, including a shortage of cybersecurity professionals and a need for rapid threat discovery and reaction. The report identifies that security processes that depend on humans become less efficient with each passing day. Methods become more accessible and sophisticated, and hackers exploit them at a rapid pace. Automated incident response playbooks can allow organizations to counter such constraints in terms of manpower scarcity and disconnected security processes. The ACSC sees an average loss for a single incident for a medium organization at USD 88,407, a fact that identifies the imperative for efficient incident response processes. Organizations can make their automated response stance even stronger through implementations such as ACSC’s Essential Eight countermeasures, providing an overall cybersecurity defense and incident reaction stance. Automated playbooks involve key items such as reporting, triage, investigation, alerting, and ticketing. Automated playbooks have to involve numerous security incidents with custom response processes, according to Akbari Gurabi [41]. Security groups can channel their efforts towards high-strategic, high-value work with automation, producing uniformed responses in an organization. Building on its demonstration of automated playbooks, the case study of the Volkswagen Group is a powerful real-world demonstration of automated security response in practice. With a workforce of over 650,000 and a geospread cloud infrastructure to protect, Volkswagen embraced AWS GuardDuty in an attempt to develop a complete automated threat detection and response mechanism [42]. What its use case demonstrates is that automated playbooks can actually be scaled for security operations at an enterprise level. When GuardDuty detects a security problem, such as an EC2 instance with a rootkit infection, it launches a multi-step automated playbook reaction. Automated emailing for owners and concurrent Security Hub finding creation for the SOC team represents the first stage in the process. Automated quarantines follow, with the affected assets quarantined to prevent the spread of danger. In critical security events, compromised programs and accounts can even be locked down automatically to safeguard larger infrastructure. Automated forensics collection is the final stage, with the compromised instance shut down and cloned in a standalone SOC AWS environment for examination. By utilizing a systemic mechanism, Volkswagen’s incident reaction took 15–20 fewer minutes per batch, and security standards could consistently be delivered to the organization.
7.3. Real-Time Monitoring and Log Analysis
Real-time monitoring and log analysis form the backbone of effective threat detection and reaction in cloud environments. The real-time analysis of information has reorganized security approaches by leveraging information at its most helpful point. In security operations, such an aspect is most critical, with early detection and reaction to a danger being a case of a minor incident and a full-fledged intrusion. Real-time monitoring tools enable companies to detect and respond to a threat when it occurs, not when it is uncovered. Log analysis forms a critical part of such a process; modern log management and analysis tools can scan for many individual events a day, providing real-time awareness of all activity in a software stack [43]. With such a feature, security professionals can monitor for errors or trending events in a timely manner and respond effectively to developing threats. Real-time observation with an additional feature of automation in reaction forms a powerful and effective security position. The effectiveness of log analysis and real-time logging is augmented by powerful analytics and machine learning capabilities. Real-time analysis enables companies to capture and react to information in real time, at least when it occurs. In security operations, such an offering can significantly impact security incident impact reduction through rapid detection and reaction capabilities. Real-time log analysis and monitoring must feature the following:
- Continuous data collection and analysis from multiple sources across the cloud infrastructure;
- Automated correlation of security events and alerts;
- Real-time threat detection and automated response capabilities;
- Integration with threat intelligence feeds for enhanced threat detection;
- Automated alerting and notification systems for security teams.
By effectively implementing these components, organizations can create a more robust and responsive security posture that enables them to detect and respond to threats more quickly and effectively. This comprehensive approach to automated threat detection and response helps organizations maintain a strong security posture while managing the increasing complexity of cloud environments.
7.4. Identity and Access Management (IAM) Automation
Identity and Access Management (IAM) automation is increasingly important in cloud security, where there is growing difficulty in managing access privileges and identities in complex digital environments for organizations. As per current cybersecurity market analysis, the worldwide IAM marketplace is undergoing a tremendous transformation with technological improvements and changing threat environments. With an ever-growing number of smart devices and sophisticated digital infrastructure, organizations have unprecedented difficulty in managing secure identities. The necessity for IAM automation is compounded by dire cybersecurity trends. Around 25 billion smart devices will be in use in 2030, immensely compounding identity management complexity. A total of 80% of cybersecurity attacks utilize identity-based attack techniques, and strong IAM solutions become increasingly important as a consequence, according to market analysis. Growth is spurred by the demand for smarter, automated identity and access prevention methodologies. In 12 months, companies’ overall count of identities will double by 240%, and therefore, manual management will become increasingly impractical, and demand for sophisticated, AI-powered IAM automation tools will become even more imperative. The trends in the market suggest high growth opportunities for IAM solutions. As per Mahat et al. [44], cloud-based offerings have gained traction with high scalability and cost-effectiveness. North America is the leading region with high technological acceptance, and Asia-Pacific is expanding at a high rate, with a high awareness of digital transformation and cybersecurity threats. The emerging trends point toward explainable AI (XAI) playing a vital role, with organizations demanding higher interpretability in cybersecurity solutions for trust and compliance with laws and regulations. AI in IoT security will gain traction, especially with an estimated 25 billion IoT devices for 2030. According to Pangarkar [45], provisioning and multi-factor authentication have emerged as key components of IAM solutions, generating USD 4.3 billion and USD 3.1 billion in revenue, respectively, highlighting the importance of automated access management and security controls. The implementation of automated IAM solutions helps organizations address critical security challenges while improving operational efficiency. As the authors note, 80% of organizations believe that better identity management solutions would have prevented some or all of the attacks they experienced, while 74% of IT decision-makers cite improving efficiency in the IT department as the primary motivation for implementing IAM software. This dual benefit of enhanced security and operational efficiency makes IAM automation essential to modern cloud security strategies.
8. Case Studies and Real-World Applications
Now that we have proposed several options for implementing cloud security automation and managing threats and responses to attacks, it is valuable to review some real-world use cases to see these methods in action.
8.1. Cloud Security Automation in Large Enterprises
The implementation of cloud security automation in large enterprises has demonstrated significant success in improving security postures and operational efficiency. According to Oliveira [46], Walmart provides a compelling example of large-scale cloud security automation, having built the world’s largest private data cloud capable of processing 2.5 petabytes of data every hour. This massive implementation highlights the critical nature of real-time security monitoring and automation, with Walmart’s senior analysts emphasizing that waiting weeks or months to analyze security data results in lost opportunities to prevent and respond to threats. The organization’s approach to automated security demonstrates how large enterprises can effectively manage and secure vast amounts of data through automated processes.
Netflix has demonstrated remarkable success in leveraging automated security tools and real-time data analysis to secure its global streaming platform. According to recent statistics, the company has grown its revenue from USD 3.2 billion in 2011 to nearly USD 33.7 billion in 2023, with nearly 283 million subscribers in the third quarter of 2023 [47]. The streaming giant’s ability to adapt to changing technologies and consumer demands has been crucial to its success, including its approach to cybersecurity. Netflix’s commitment to innovation extends to its security infrastructure, showcasing how robust automated security processes can scale effectively with business growth while maintaining strong defenses against emerging cyber threats.
8.2. Examples of Automated Threat Detection in Action
Automated threat detection is highly effective in identifying and addressing security issues. A prime example is within the financial services industry, where these systems have revolutionized how fraud is prevented. Financial service organizations monitor real-time transactions to identify fraud and prevent suspicious activity before it is completed [48]. This saves millions of dollars that would have required manual identification and remediation.
Shell’s automated security system effectively portrays how danger can be detected through such technology. AI/ML-powered security defense tools have become imperative in security danger detection and response in most sectors [49]. AI methodologies, in the view of the authors, can search through massive datasets in seconds, and companies can use them to detect suspicious activity and abnormalities in real time. AI-powered security tools can provide important information in most security aspects, extending even to possibly address security issues in terms of physical security through programmed reaction and discovery processes.
Delta Air Lines mirrors a technology and operational efficiency model. In its 2023 annual report, Delta highlighted a record USD 54.7 billion in revenue, a 20% improvement over 2022, and best-in-class operational performance. Delta has made considerable investments in technology capabilities, with its Fly Delta App having over 1 billion annual visits in 2023, a 25% improvement over 2023 [50]. Delta’s technology investments have helped with increased security and service to customers, as well as a competitive stance in the airline industry.
These case studies illustrate the value of automated threat detection across industries and use cases. They show that automation can improve security, operations, and business value. The fact that these deployments have been successful shows the necessity of customizing automated security products to each organization’s requirements. The products, in turn, must be flexible enough to keep pace with changing threats and business demands. With the increasingly sophisticated security challenges that organizations are experiencing, these instances offer helpful insight into using automated security products in real-world applications.
9. Challenges and Limitations of Cloud Security Automation
Research suggests that organizations face a significant challenge in making full use of cloud security automation. ACSC (2022) reports that cybersecurity professionals face an overload of potential threats, with organizations receiving an average of one report of a cyber crime every 7 min [40]. There is an overload of alerts, and it is difficult to discern between real and actual threats and spurious ones. The report reveals that the majority of critical incidents resolved in 2021–2022 were a consequence of poor patching, an indication that security teams have not been efficient in processing and acting on a continuous stream of potential security vulnerabilities. Added to this challenge is an increased level of sophisticated cyber threats, with hackers taking advantage of vulnerabilities in most sectors at a high pace. Integration complexity with older infrastructure is yet another important issue of concern. Integration complications in mixed environments for companies that operate in such environments will encounter specific complications in providing transparency and governance between platforms [41]. The integration of security tools with older infrastructure and continuous security policies in cloud infrastructure with its ever-evolving and decentralized environment is not a simple feat. The symmetry between humans and automation remains paramount.
Automation is geared toward executing repetitive, rule-based activities with a high degree of accuracy and rapidity, while human intelligence is essential in undertakings that necessitate complex decisions, innovation, and ethical judgment. This balance is crucial for cloud security in optimizing operations, improving security measures, and meeting regulatory standards. AI in cybersecurity also plays a fundamental role in the ongoing development of cloud security, including Identity and Access Management (IAM), a collaborative framework where automation tackles the mundane and humans supervise or make important decisions.
9.1. Tasks Best Suited for Automation
Threat detection and analysis: AI-based systems can analyze vast amounts of data to identify abnormal behavior and potential threats in real time, alleviating some of the heavy lifting from human analysts so that they can concentrate on more sophisticated problems [51].
Security function placement: It can help users automatically translate high-level security requirements to placement and optimization models of network security functions like firewalls and intrusion detection systems so they can allocate resources more effectively and increase security without human intervention.
9.2. Tasks Best Suited for Human Interaction
Complex decision-making: Human expertise is crucial in situations that require subtle decision-making. However, when automation goes wrong, or more subjective calls need to be made that include an ethics aspect, humans will outshine machines for the foreseeable future [52].
Security configuration and risk assessment: As users may be vectors for cybersecurity attacks, human-centered approaches are essential to understanding and configuring security so that it works. Security failures occur most frequently when human conceptualizations of systems misalign with the way they are actually set up, and mental modeling analyses of security systems help identify where human thought processes diverge from the correct parameters [53].
Challenges in balancing automation and human expertise: While automation offers several benefits in terms of scalability, speed, and consistency, integrating it effectively into existing cloud security infrastructures introduces several challenges that must be carefully managed. Below, we outline the key hurdles and the evolving responsibilities of human security teams in this context.
- Human role evolution and resistance to change: The role of humans should shift towards interpretation, investigation, and strategic planning. In some cases, these individuals may not be supportive of this transition.
- Loss of situational awareness: Relying too much on automation can sometimes create a black-box effect where humans are detached from critical detection and response processes, which may, in turn, reduce situational awareness when unexpected incidents occur.
In order to balance automation and human expertise in cloud security, organizations should promote a collaborative environment between automated systems and security analysts. They can design automation workflows following human-in-the-loop architecture, where humans can validate or approve automated actions.
Organizations must exercise caution not to overspend on automation while ensuring that human expertise continues to prevail in security operations. Cost and budget planning remain issues, with companies having to justify enormous investments in automation while managing ongoing operational expenses.
10. Discussion
The future of cloud security automation is being reimagined, with new trends and approaches emerging. According to Statista [54], the cybersecurity market will grow from USD 24 billion in 2023 to USD 134 billion in 2030, with a compound annual growth rate (CAGR) of 28%. Over 90% of large companies will use AI in cybersecurity in 2030. AI-powered threat detection and incident response will become even more important, driven by the demand for smarter and automated security techniques. Emerging trends indicate that explainable AI (XAI) will become a dominant player, with companies asking for growing interpretability in cybersecurity tools in order to preserve trust and compliance with laws and regulations. AI in IoT security will also see a strong boost, with an estimated 25 billion IoT devices in 2030. AI-powered Security Orchestration, Automation, and Response (SOAR) platforms will see strong traction, with an objective of automating repetitive processes and cutting down human intervention. Cloud security and threat detection and response is an ever-evolving area, and there are several opportunities that are still unexplored. Future research should explore innovative methods to further improve the adaptability of machine learning algorithms in detecting and responding to new and evolving cyber threats in cloud environments in order to strengthen overall cloud security strategies [55]. Future exploration could involve developing more sophisticated models for simulating complex multi-layer attacks, enabling a deeper understanding of threat propagation and the effectiveness of various mitigation strategies across different operational layers and assets in the cloud [56]. There is an opportunity for future studies to conduct a comparative analysis of different encryption techniques, including advanced methods like homomorphic encryption and quantum-resistant algorithms, to identify the most effective strategies for securing cloud data against modern threats [57].
11. Conclusions
Cloud security automation is a key part of current cybersecurity approaches. It provides companies with a mechanism for discovering and acting on security threats at a larger level, enhancing operational effectiveness in the process. As seen in the examples, when security tools and processes are effectively implemented, automated security can minimize reaction times and enhance security performance. For organizations that opt for automation, several vital recommendations include starting with specific security objectives and use cases, proper integration with existing systems, allowing humans to view processes, and continuous evaluation and improvement of automation methodologies based on performance. Organizations must prioritize developing a symmetrical model that combines automated capabilities and human expertise. Looking ahead, cloud security automation will have a rosy but challenging future. With security threats becoming increasingly sophisticated, companies must implement new emerging technology, but not at the expense of strong security fundamentals. To win, an effective balancing act between humans and automation will have to be accomplished, and a head start will be gained over new emerging threats and compliance mandates.
Funding
This research received no external funding.
Data Availability Statement
No new data were created or analyzed in this study.
Conflicts of Interest
Author Harshad Pitkar was employed by the company Cummins Inc. The author declares that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
References
- Beaty, K.A.; Chow, J.M.; Cunha, R.L.F.; Das, K.K.; Hulber, M.F.; Kundu, A.; Michelini, V.; Palmer, E.R. Managing sensitive applications in the public cloud. IBM J. Res. Dev. 2016, 60, 4:1–4:13. [Google Scholar] [CrossRef]
- Sureshkumar, V.; Baranidharan, B. A study of the cloud security attacks and threats. J. Phys. Conf. Ser. 2021, 1964, 042061. [Google Scholar] [CrossRef]
- Research, K. Identity Threat Detection and Response (ITDR) Market Size|2031. Technical Report, KBV Research. 2024. Available online: https://www.kbvresearch.com/identity-threat-detection-and-response-market/ (accessed on 4 March 2025).
- Gill, S.S.; Tuli, S.; Xu, M.; Singh, I.; Singh, K.V.; Lindsay, D.; Tuli, S.; Smirnova, D.; Singh, M.; Jain, U.; et al. Transformative effects of IoT, Blockchain and Artificial Intelligence on cloud computing: Evolution, vision, trends and open challenges. Internet Things 2019, 8, 100118. [Google Scholar] [CrossRef]
- Kumar Samriya, J.; Kumar, S.; Kumar, M.; Wu, H.; Singh Gill, S. Machine Learning-Based Network Intrusion Detection Optimization for Cloud Computing Environments. IEEE Trans. Consum. Electron. 2024, 70, 7449–7460. [Google Scholar] [CrossRef]
- D’Antoni, L.; Ding, S.; Goel, A.; Ramesh, M.; Rungta, N.; Sung, C. Automatically Reducing Privilege for Access Control Policies. Proc. ACM Program. Lang. 2024, 8, 763–790. [Google Scholar] [CrossRef]
- Ali, S.M.; Razzaque, A.; Yousaf, M.; Shan, R.U. An Automated Compliance Framework for Critical Infrastructure Security Through Artificial Intelligence. IEEE Access 2024, 13, 4436–4459. [Google Scholar] [CrossRef]
- Jalalvand, F.; Baruwal Chhetri, M.; Nepal, S.; Paris, C. Alert Prioritisation in Security Operations Centres: A Systematic Survey on Criteria and Methods. ACM Comput. Surv. 2024, 57, 1–36. [Google Scholar] [CrossRef]
- Wu, Y.; Kang, Z.; Dai, T.; Cheng, D. Managing cloud security in the presence of strategic hacker and joint responsibility. J. Oper. Res. Soc. 2023, 75, 1371–1384. [Google Scholar] [CrossRef]
- He, H.; Li, X.; Chen, P.; Chen, J.; Liu, M.; Wu, L. Efficiently localizing system anomalies for cloud infrastructures: A novel Dynamic Graph Transformer based Parallel Framework. J. Cloud Comput. 2024, 13, 115. [Google Scholar] [CrossRef]
- Gursimsir, M.; Ayar, C.; Sogukpinar, I. Multipurpose Malware Detection System. In Proceedings of the 2024 9th International Conference on Computer Science and Engineering (UBMK), Antalya, Turkey, 26–28 October 2024; pp. 1–5. [Google Scholar] [CrossRef]
- Ahmad, W.; Rasool, A.; Javed, A.R.; Baker, T.; Jalil, Z. Cyber Security in IoT-Based Cloud Computing: A Comprehensive Survey. Electronics 2021, 11, 16. [Google Scholar] [CrossRef]
- Annunziata, G.; Sheykina, A.; Palomba, F.; De Lucia, A.; Catolino, G.; Ferrucci, F. Security Risk Assessment on Cloud: A Systematic Mapping Study. In Proceedings of the 28th International Conference on Evaluation and Assessment in Software Engineering, Salerno, Italy, 18–21 June 2024; pp. 604–613. [Google Scholar] [CrossRef]
- Xiao, Z.; Xiao, Y. Security and Privacy in Cloud Computing. IEEE Commun. Surv. Tutor. 2013, 15, 843–859. [Google Scholar] [CrossRef]
- Borgeaud, A. Topic: Data Security. Available online: https://www.statista.com/topics/13106/data-security/ (accessed on 12 January 2025).
- Noor, Z.; Hina, S.; Hayat, F.; Shah, G.A. An intelligent context-aware threat detection and response model for smart cyber-physical systems. Internet Things 2023, 23, 100843. [Google Scholar] [CrossRef]
- Bagheri, A.; Shameli-Sendi, A. Automating the Translation of Cloud Users’ High-Level Security Needs to an Optimal Placement Model in the Cloud Infrastructure. IEEE Trans. Serv. Comput. 2023, 16, 4580–4590. [Google Scholar] [CrossRef]
- Imran, M.; Siddiqui, H.U.R.; Raza, A.; Raza, M.A.; Rustam, F.; Ashraf, I. A performance overview of machine learning-based defense strategies for advanced persistent threats in industrial control systems. Comput. Secur. 2023, 134, 103445. [Google Scholar] [CrossRef]
- Muhammad Saad Zahoor, E.A. Security Challenges and Solutions in AI-Enhanced Cloud Platforms: A Comprehensive Study. Power Syst. Technol. 2023, 47, 103–118. [Google Scholar] [CrossRef]
- Jeyalakshmi, J.; Gnanavel, S.; Vijay, K.; Eugene Berna, I. Threat Landscape and Common Security Challenges in Cloud Environments: In Advances in Information Security, Privacy, and Ethics; Goel, P.K., Pandey, H.M., Singhal, A., Agarwal, S., Eds.; IGI Global: Hershey, PA, USA, 2024; pp. 194–213. [Google Scholar] [CrossRef]
- Bringhenti, D.; Marchetto, G.; Sisto, R.; Valenza, F. Automation for Network Security Configuration: State of the Art and Research Trends. ACM Comput. Surv. 2024, 56, 1–37. [Google Scholar] [CrossRef]
- Panigrahi, G.R.; Sethy, P.K.; Behera, S.K.; Gupta, M.; Alenizi, F.A.; Suanpang, P.; Nanthaamornphong, A. Analytical Validation and Integration of CIC-Bell-DNS-EXF-2021 Dataset on Security Information and Event Management. IEEE Access 2024, 12, 83043–83056. [Google Scholar] [CrossRef]
- Dunsin, D.; Ghanem, M.C.; Ouazzane, K.; Vassilev, V. A comprehensive analysis of the role of artificial intelligence and machine learning in modern digital forensics and incident response. Forensic Sci. Int. Digit. Investig. 2024, 48, 301675. [Google Scholar] [CrossRef]
- Vazão, A.P.; Santos, L.; Costa, R.L.D.C.; Rabadão, C. Implementing and evaluating a GDPR-compliant open-source SIEM solution. J. Inf. Secur. Appl. 2023, 75, 103509. [Google Scholar] [CrossRef]
- Manzoor, J.; Waleed, A.; Jamali, A.F.; Masood, A. Cybersecurity on a budget: Evaluating security and performance of open-source SIEM solutions for SMEs. PLoS ONE 2024, 19, e0301183. [Google Scholar] [CrossRef]
- Kaur, H.; Sanjaiy Sl, D.; Paul, T.; Kumar Thakur, R.; Kumar Reddy, K.V.; Mahato, J.; Naveen, K. Evolution of Endpoint Detection and Response (EDR) in Cyber Security: A Comprehensive Review. E3S Web Conf. 2024, 556, 01006. [Google Scholar] [CrossRef]
- Olteanu, I.C. Evaluating the Response Effectiveness of XDR Technology in a Scaled Down Environment. Master’s Thesis, Eindhoven University of Technology, Eindhoven, The Netherlands, 2022. [Google Scholar]
- González-Granadillo, G.; González-Zarzosa, S.; Diaz, R. Security Information and Event Management (SIEM): Analysis, Trends, and Usage in Critical Infrastructures. Sensors 2021, 21, 4759. [Google Scholar] [CrossRef]
- Nguyen, M.D.; Mallouli, W.; Cavalli, A.R.; Montes De Oca, E. AI4SOAR: A Security Intelligence Tool for Automated Incident Response. In Proceedings of the 19th International Conference on Availability, Reliability and Security, Vienna, Austria, 30 July–2 August 2024; pp. 1–8. [Google Scholar] [CrossRef]
- Bridges, R.A.; Rice, A.E.; Oesch, S.; Nichols, J.A.; Watson, C.; Spakes, K.; Norem, S.; Huettel, M.; Jewell, B.; Weber, B.; et al. Testing SOAR tools in use. Comput. Secur. 2023, 129, 103201. [Google Scholar] [CrossRef]
- Lee, M.; Jang-Jaccard, J.; Kwak, J. Novel Architecture of Security Orchestration, Automation and Response internet of Blended Environment. Comput. Mater. Contin. 2022, 73, 199–223. [Google Scholar] [CrossRef]
- Zaman, S.; Alhazmi, K.; Aseeri, M.A.; Ahmed, M.R.; Khan, R.T.; Kaiser, M.S.; Mahmud, M. Security Threats and Artificial Intelligence Based Countermeasures for Internet of Things Networks: A Comprehensive Survey. IEEE Access 2021, 9, 94668–94690. [Google Scholar] [CrossRef]
- AL-Aamri, A.S.; Abdulghafor, R.; Turaev, S.; Al-Shaikhli, I.; Zeki, A.; Talib, S. Machine Learning for APT Detection. Sustainability 2023, 15, 13820. [Google Scholar] [CrossRef]
- Wendt, D.W. The Cybersecurity Trinity: Artificial Intelligence, Automation, and Active Cyber Defense; Apress: Berkeley, CA, USA, 2024. [Google Scholar] [CrossRef]
- Vo, H.V.; Du, H.P.; Nguyen, H.N. AI-powered intrusion detection in large-scale traffic networks based on flow sensing strategy and parallel deep analysis. J. Netw. Comput. Appl. 2023, 220, 103735. [Google Scholar] [CrossRef]
- Wu, Y.c.; Chang, Y.l. Ransomware Detection on Linux Using Machine Learning with Random Forest Algorithm. TechRxiv 2024. [CrossRef]
- Khammas, B.M. Ransomware Detection using Random Forest Technique. ICT Express 2020, 6, 325–331. [Google Scholar] [CrossRef]
- Google. Google Security Operations Reference. Technical Report, Google Cloud. 2024. Available online: https://cloud.google.com/chronicle/docs/reference (accessed on 4 March 2025).
- Wagner, T.D.; Mahbub, K.; Palomar, E.; Abdallah, A.E. Cyber threat intelligence sharing: Survey and research directions. Comput. Secur. 2019, 87, 101589. [Google Scholar] [CrossRef]
- Centre, A.C.S. Annual Cyber Threat Report. Technical Report, Australian Cyber Security Centre. 2022. Available online: https://www.cyber.gov.au/sites/default/files/2023-03/ACSC-Annual-Cyber-Threat-Report-2022_0.pdf (accessed on 4 March 2025).
- Akbari Gurabi, M.; Nitz, L.; Bregar, A.; Popanda, J.; Siemers, C.; Matzutt, R.; Mandal, A. Requirements for Playbook-Assisted Cyber Incident Response, Reporting and Automation. Digit. Threat. Res. Pract. 2024, 5, 1–11. [Google Scholar] [CrossRef]
- Amazon. Volkswagen Group Case Study|Amazon GuardDuty|AWS—aws.amazon.com. Technical Report, AWS. 2021. Available online: https://aws.amazon.com/solutions/case-studies/volkswagen-group-guardduty/ (accessed on 4 March 2025).
- Chen, C.; Yan, T.; Shi, C.; Xi, H.; Fan, Z.; Wan, H.; Zhao, X. The Last Mile of Attack Investigation: Audit Log Analysis Toward Software Vulnerability Location. IEEE Trans. Inf. Forensics Secur. 2024, 19, 9566–9581. [Google Scholar] [CrossRef]
- Mahat, D.; Karki, T.B.; Neupane, D.; Shrestha, D.K.; Shrestha, S. Decolonization in Focus: A Bibliometric Analysis of Scientific Articles from 2010 to 2023. Nepal J. Multidiscip. Res. 2024, 7, 1–21. [Google Scholar] [CrossRef]
- Pangarkar, T. Identity and Access Management Statistics and Facts (2025)—scoop.market.us. Technical Report, market.us. 2025. Available online: https://scoop.market.us/identity-and-access-management-statistics/ (accessed on 4 March 2025).
- Oliveira, M.P.V.D.; Handfield, R. Analytical foundations for development of real-time supply chain capabilities. Int. J. Prod. Res. 2019, 57, 1571–1589. [Google Scholar] [CrossRef]
- Stoll, J. Topic: Netflix—Statista.com. Technical Report, Statista. 2024. Available online: https://www.statista.com/topics/842/netflix/ (accessed on 4 March 2025).
- Talukder, M.A.; Khalid, M.; Uddin, M.A. An integrated multistage ensemble machine learning model for fraudulent transaction detection. J. Big Data 2024, 11, 168. [Google Scholar] [CrossRef]
- Mink, J.; Benkraouda, H.; Yang, L.; Ciptadi, A.; Ahmadzadeh, A.; Votipka, D.; Wang, G. Everybody’s Got ML, Tell Me What Else You Have: Practitioners’ Perception of ML-Based Security Tools and Explanations. In Proceedings of the 2023 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 21–25 May 2023; pp. 2068–2085. [Google Scholar] [CrossRef]
- Lines, D.A. Delta Air Lines Announces December Quarter and Full Year 2023 Financial Results. Technical Report, Delta Air Lines. 2024. Available online: https://ir.delta.com/news/news-details/2025/Delta-Air-Lines-Announces-December-Quarter-and-Full-Year-2024-Financial-Results/default.aspx (accessed on 4 March 2025).
- Tilbury, J.; Flowerday, S. Humans and Automation: Augmenting Security Operation Centers. J. Cybersecur. Priv. 2024, 4, 388–409. [Google Scholar] [CrossRef]
- Vaccaro, M.; Almaatouq, A.; Malone, T. When combinations of humans and AI are useful: A systematic review and meta-analysis. Nat. Hum. Behav. 2024, 8, 2293–2303. [Google Scholar] [CrossRef]
- Houser, A.M.; Bolton, M.L. Formal Mental Models for Human-Centered Cybersecurity. Int. J. Hum.–Comput. Interact. 2025, 41, 1414–1430. [Google Scholar] [CrossRef]
- Borgeaud, A. Global AI Cybersecurity Market Size 2030|Statista—Statista.com. Technical Report, Statistica. 2024. Available online: https://www.statista.com/statistics/1450963/global-ai-cybersecurity-market-size/ (accessed on 4 March 2025).
- Thaqi, R.; Krasniqi, B.; Mazrekaj, A.; Rexha, B. Literature Review of Machine Learning and Threat Intelligence in Cloud Security. IEEE Access 2025, 13, 11663–11678. [Google Scholar] [CrossRef]
- Manzoor, S.; Gouglidis, A.; Bradbury, M.; Suri, N. Enabling Multi-Layer Threat Analysis in Dynamic Cloud Environments. IEEE Trans. Cloud Comput. 2024, 12, 319–336. [Google Scholar] [CrossRef]
- Dugyala, R.; Chithaluru, P.; Ramchander, M.; Kumar, S.; Yadav, A.; Yadav, N.S.; Elminaam, D.S.A.; Alsekait, D.M. Secure cloud computing: Leveraging GNN and leader K-means for intrusion detection optimization. Sci. Rep. 2024, 14, 30906. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).