Threshold Fully Homomorphic Encryption Scheme Based on NGS of Symmetric Encryption
Abstract
1. Introduction
- Additive homomorphism:
- Multiplicative homomorphisms:
- Scalar ciphertext: ;
- Vector ciphertext: ,
1.1. Our Contribution
1.2. Roadmap
2. Preliminaries
2.1. Symbolic Representations
2.2. Hard Problems and Ciphertexts
2.3. Gadget Decomposition
2.4. CS-LISS Scheme
- SS.Share (): Given a distribution matrix for -threshold secret sharing, each party runs the -out-of- secret sharing Alg.1 to create shares on a secret .
- SS.Combine (): The secret key can be reconstructed as
2.5. Key-Switching
- .
3. NGS of Symmetric Encryption
- S-NGS.ParamGen (): Receives the security parameter and outputs the tuple , where is a base used to decompose the ciphertexts and .
- S-NGS.KeyGen: Sample and set until exists in . Output .
- S-NGS.EncS (): Let , , define , and output . The is a “scalar encryption” of .
- S-NGS.EncVec (): Given , sample for . Define and . Output is a “vector encryption” of , where .
- S-NGS.DeS (): Use the secret key and output the message .
- S-NGS.Exp (): Given a scalar encryption of a ternary polynomial and a vector encryption of a message , the “external product” of and is defined as follows:
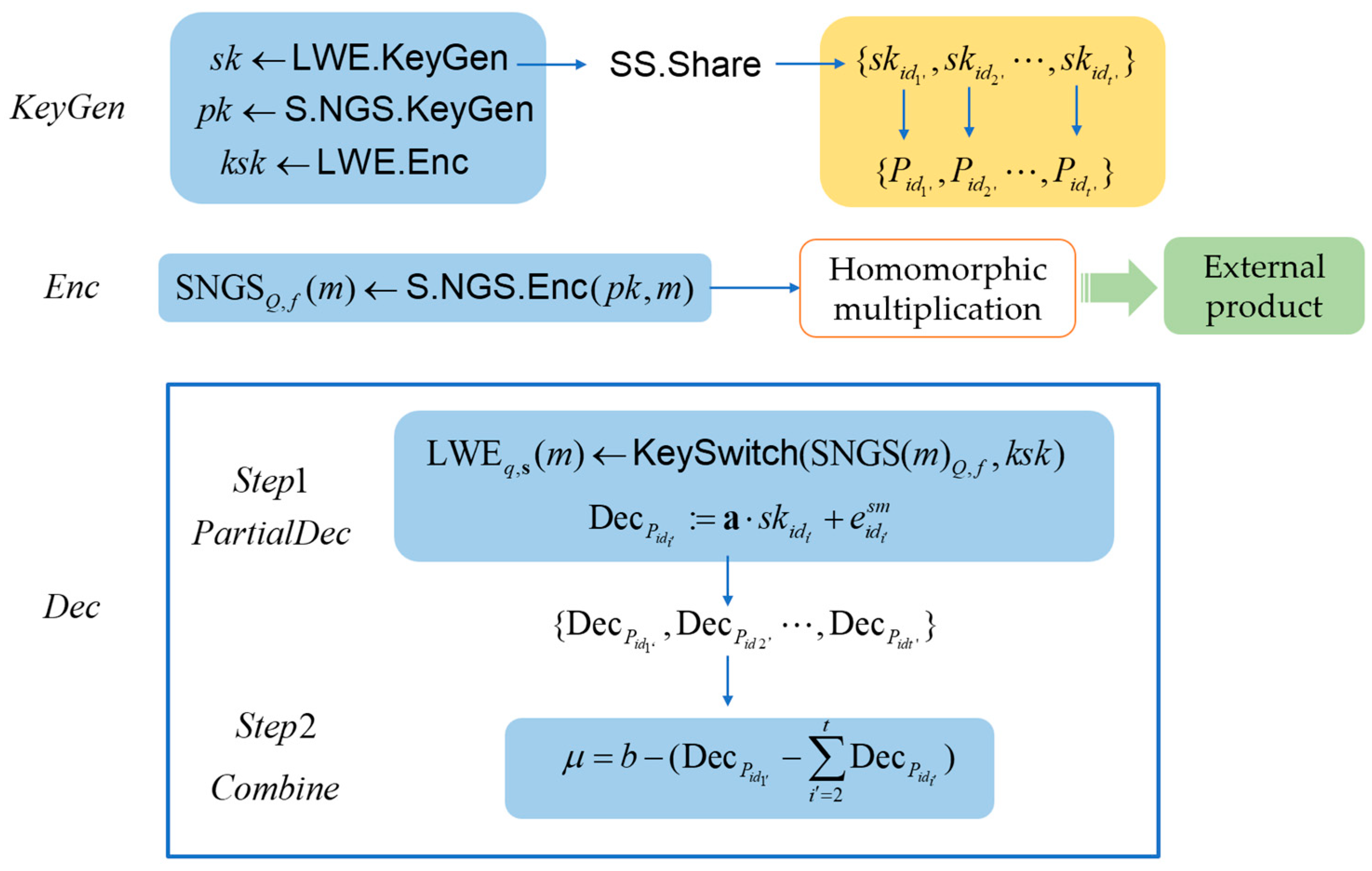
4. NGS-Based ThFHE Scheme
- Th-S-NGS.KeyGen (): The number of participants and the threshold corresponding to the threshold access structure entered by a trusted third party of the key authority. Generate a Th-S-NGS instance withExecute the secret sharing algorithm of CS-LISS scheme to set the secret key shares for parties.
- Th-S-NGS.Enc (): A trusted third party runs the encryption algorithm of S-NGS and output the ciphertext.
- Th-S-NGS.Exp (): While entering two ciphertexts, execute S-NGS. Exp.
- Th-S-NGS.PartialDec (): Given the key-switching key , computeUpon input of the LWE ciphertext and a key set , each calculates the following:Then, broadcasts to remaining parties.
- Th-S-NGS.Combine (): Inputting the ciphertext and the predetermined participants, the decryption in this step is computed as
5. Correctness
6. Noise Analysis
7. Security
7.1. IND Security for NGS Ciphertext
7.2. IND Security for NGS-Type ThFHE
- The challenger runs Th-S-NGS.Gen to obtain , and provides the public key to the adversary .
- The adversary outputs a set , and receives the set of secret key shares from .
- The adversary outputs two sets of equal length messages , .
- = Th-S-NGS.Enc is provided by the challenger, for and to .
- The adversary issues .
- receives = Th-S-NGS.PartialDec .
- The adversary eventually outputs a bit .
- If , the game outputs 1, otherwise it outputs 0.
7.3. Discussion of Potential Resistance to Quantum Attacks
8. Performance
8.1. Computation Time
8.2. Parameters
9. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| HE | Homomorphic encryption |
| FHE | Fully homomorphic encryption |
| ThFHE | Threshold fully homomorphic encryption |
| MKFHE | Multi-key fully homomorphic encryption |
| NGS | NTRU-based GSW-like |
| S-NGS | NGS of symmetric encryption |
| Th-S-NGS | ThFHE based on an S-NGS |
| LISS | Linear Secret Sharing |
| CS-LISS | extended version of Linear Secret Sharing |
References
- Hayes, B. Cloud computing. ACM. 2008, 51, 9–11. [Google Scholar] [CrossRef]
- Wang, L.; von Laszewski, G.; Younge, A. Cloud Computing: A Perspective Study. New Gener. Comput. 2010, 28, 137–146. [Google Scholar] [CrossRef]
- Rivest, R.L.; Adleman, L.; Dertouzos, M.L. On data banks and privacy homomorphisms. Found. Secure. Comput. 1978, 4, 169–180. [Google Scholar]
- Gentry, C. A Fully Homomorphic Encryption Scheme; Stanford University: Stanford, CA, USA, 2009; ISBN 978-1-109-44450-6. [Google Scholar]
- Gentry, C. Fully homomorphic encryption using ideal lattices. In Proceedings of the Forty-First Annual ACM Symposium on Theory of Computing, Bethesda, MD, USA, 31–2 June May 2009; pp. 169–178. [Google Scholar]
- Brakerski, Z.; Vaikuntanathan, V. Efficient Fully Homomorphic Encryption from (Standard) LWE; IEEE Computer Society Press: Los Alamitos, CA, USA, 2011; pp. 97–106. [Google Scholar]
- Brakerski, Z.; Vaikuntanathan, V. Fully Homomorphic Encryption from Ring-LWE and Security for Key Dependent Messages. In Proceedings of the Advances in Cryptology—CRYPTO 2011: 31st Annual Conference on Advances in Cryptology, Santa Barbara, CA, USA, 14–18 August 2011; Volume 6841, pp. 505–524. [Google Scholar]
- López-Alt, A.; Tromer, E.; Vaikuntanathan, V. On the-fly multiparty computation on the cloud via multikey fully homomorphic encryption. In Proceedings of the Forty-Fourth Annual ACM Symposium on Theory of Computing, New York, NY, USA, 20–22 May 2012; pp. 1219–1234. [Google Scholar]
- Van Dijk, M.; Gentry, C.; Halevi, S.; Vaikuntanathan, V. Fully Homomorphic Encryption over the Integers. In Proceedings of the Advances in Cryptology—EUROCRYPT 2010: 29th Annual international conference on Theory and Applications of Cryptographic Techniques, French Riviera, France, 30 May–3 June 2010; Volume 6110, pp. 24–43. [Google Scholar]
- Brakerski, Z.; Gentry, C.; Vaikuntanathan, V. (Leveled) fully homomorphic encryption without bootstrapping. ACM Trans. Comput. Theory 2012, 6, 309–325. [Google Scholar]
- Fan, J.; Vercauteren, F. Somewhat practical fully homomorphic encryption. Int. Assoc. Cryptologic Res. 2012, 144. [Google Scholar]
- Brakerski, Z. Fully Homomorphic Encryption without Modulus Switching from Classical GapSVP. In Proceedings of the Advances in Cryptology—CRYPTO 2012: 32nd Annual Cryptology Conference on Advances in Cryptology, Santa Barbara, CA, USA, 19–23 August 2012; Volume 7417, pp. 868–886. [Google Scholar]
- Kim, E.; Lee, H.S.; Park, J. Towards Round-Optimal Secure Multiparty Computations: Multikey FHE Without a CRS. In Proceedings of the 23rd Australasian Conference, ACISP 2018, Wollongong, NSW, Australia, 11–13 July 2018; pp. 101–113. [Google Scholar]
- Jain, A.; Rasmussen, P.M.R.; Sahai, A. Threshold fully homomorphic encryption. Int. Assoc. Cryptologic Res. 2017, 257. [Google Scholar]
- Boneh, D.; Gennaro, R.; Goldfeder, S.; Jain, A.; Kim, S.; Rasmussen, P.M.R.; Sahai, A. Threshold cryptosystems from threshold fully homomorphic encryption. In Proceedings of the Advances in Cryptology—CRYPTO 2018: 38th Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2018; Volume 10991, pp. 565–596. [Google Scholar]
- Cheon, J.H.; Cho, W.; Kim, J. Improved universal thresholdizer from threshold fully homomorphic encryption. Int. Assoc. Cryptologic Res. 2023, 545. [Google Scholar]
- Asharov, G.; Jain, A.; López-Alt, A.; Tromer, E.; Vaikuntanathan, V.; Wichs, D. Multiparty Computation with Low Communication, Computation and Interaction via Threshold FHE. In Proceedings of the Advances in Cryptology—EUROCRYPT 2012: 31st Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, 15–19 April 2012; Volume 7237, pp. 483–501. [Google Scholar]
- Mouchet, C.; Troncoso-Pastoriza, J.; Bossuat, J.P.; Hubaux, J.P. Multiparty Homomorphic Encryption from Ring-Learning-with-Errors. Proc. Priv. Enhancing Technol. 2021, 4, 291–311. [Google Scholar] [CrossRef]
- Park, J. Homomorphic encryption for multiple users with less communications. IEEE Access 2021, 9, 135915–135926. [Google Scholar] [CrossRef]
- Chen, H.; Chillotti, I.; Song, Y. Multi-Key Homomorphic Encryption from TFHE. In Proceedings of the Advances in Cryptology—ASIACRYPT 2019: 25th International Conference on the Theory and Application of Cryptology and Information Security, Kobe, Japan, 8–12 December 2019; Volume 11922, pp. 446–472. [Google Scholar]
- Mukherjee, P.; Wichs, D. Two Round Multiparty Computation via Multi-key FHE. In Proceedings of the Advances in Cryptology—EUROCRYPT 2016: 35th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Vienna, Austria, 8–12 May 2016; Volume 9666, pp. 735–763. [Google Scholar]
- Clear, M.; McGoldrick, C. Multi-identity and Multi-key Leveled FHE from Learning with Errors. In Proceedings of the Advances in Cryptology —CRYPTO 2015: 35th Annual Cryptology Conference, Santa Barbara, CA, USA, 16–20 August 2015; Volume 9216, pp. 630–656. [Google Scholar]
- Peikert, C.; Shiehian, S. Multi-key FHE from LWE. In Theory of Cryptography Conference; Springer: Berlin/Heidelberg, Germany, 2016; Volume 9986, pp. 217–238. [Google Scholar]
- Li, C.R.; Chun, C.F.; Wang, Y.F. Multi-key homomorphic proxy re-encryption scheme based on NTRU and its applications. J. Commun. 2021, 42, 11–22. [Google Scholar]
- Che, X.L.; Zhou, T.P.; Li, N.B.; Zhou, H.N.; Liu, L.F.; Yang, X.Y. Optimisation of NTRU-type multi-key fully homomorphic encryption schemes. Adv. Eng. Sci. 2020, 52, 186–193. [Google Scholar]
- Chen, H.; Dai, W.; Kim, M.; Song, Y. Efficient multi-key homomorphic encryption with packed ciphertexts with application to oblivious neural network inference. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 395–412. [Google Scholar]
- Jiang, B. Multi-key FHE without ciphertext-expansion in two-server model. Front. Comput. Sci. 2022, 16, 161809. [Google Scholar] [CrossRef]
- Chen, Y.L.; Dong, S.; Li, T.; Wang, Y.L.; Zhou, H.Y. Dynamic multi-key FHE in asymmetric key setting from LWE. IEEE Trans. Inf. Forensics Secur. 2021, 16, 5239–5249. [Google Scholar] [CrossRef]
- Bos, J.W.; Lauter, K.; Loftus, J.; Naehrig, M. Improved Security for a Ring-Based Fully Homomorphic Encryption Scheme. In Proceedings of the Cryptography and Coding: 14th IMA International Conference, IMACC 2013, Oxford, UK, 17–19 December 2013; Volume 8308, pp. 45–64. [Google Scholar]
- Xu, K.X.; Tan, B.H.M.; Wang, L.P.; Aung, K.M.M.; Wang, H. Threshold Homomorphic Encryption From Provably Secure NTRU. Comput. J. 2023, 66, 2861–2873. [Google Scholar] [CrossRef]
- Kirchner, P.; Fouque, P.A. Revisiting Lattice Attacks on Overstretched NTRU Parameters. In Proceedings of the Advances in Cryptology—EUROCRYPT 2017: 36th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Paris, France, 30 April–4 May 2017; Volume 10210, pp. 3–26. [Google Scholar]
- Albrecht, M.; Bai, S.; Ducas, L. A subfield lattice attack on overstretched NTRU assumptions-cryptanalysis of some FHE and graded encoding schemes. In Proceedings of the Advances in Cryptology—CRYPTO 2016: 36th Annual International Cryptology Conference on Advances in Cryptology, Santa Barbara, CA, USA, 14–18 August 2016; Volume 9814, pp. 153–178. [Google Scholar]
- Cheon, J.H.; Jeong, J.; Lee, C. An algorithm for NTRU problems and cryptanalysis of the GGH multilinear map without an encoding of zero. LMS J. Comput. Math. 2016, 19, 255–266. [Google Scholar] [CrossRef]
- Genise, N.; Gentry, C.; Halevi, S.; Li, B.; Micciancio, D. Homomorphic Encryption for Finite Automata. In Proceedings of the Advances in Cryptology—ASIACRYPT 2019: 25th International Conference on the Theory and Application of Cryptology and Information Security, Kobe, Japan, 8–12 December 2019; Volume 11922, pp. 473–502. [Google Scholar]
- Lee, C.; Wallet, A. Lattice analysis on MiNTRU problem. Int. Assoc. Cryptologic Res. 2020, 230. [Google Scholar]
- Ducas, L.; Woerden, W.V. NTRU Fatigue: How Stretched is Overstretched? In Proceedings of the Advances in Cryptology—ASIACRYPT 2021: 27th International Conference on the Theory and Application of Cryptology and Information Security, Singapore, 6–10 December 2021; Volume 13093, pp. 3–32. [Google Scholar]
- Bonte, C.; Iliashenko, I.; Park, J.; Pereira, H.V.L.; Smart, N.P. FINAL: Faster FHE Instantiated with NTRU and LWE. In Proceedings of the Advances in Cryptology—ASIACRYPT 2022: 28th International Conference on the Theory and Application of Cryptology and Information Security, Taipei, Taiwan, 5–9 December 2022; Volume 13792, pp. 188–215. [Google Scholar]
- Ducas, L.; Micciancio, D. FHEW: Bootstrapping Homomorphic Encryption in Less Than a Second. In Proceedings of the Advances in Cryptology—EUROCRYPT 2015—34th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Sofia, Bulgaria, 26-30 April 2015; Volume 9056, pp. 617–640. [Google Scholar]
- Chillotti, I.; Gama, N.; Georgieva, M.; Izabachène, M. Faster Fully Homomorphic Encryption: Bootstrapping in Less Than 0.1 Seconds. In Proceedings of the Advances in Cryptology—ASIACRYPT 2016: 22nd International Conference on the Theory and Application of Cryptology and Information Security, Hanoi, Vietnam, 4–8 December 2016; Volume 10031, pp. 3–33. [Google Scholar]
- Xiang, B.; Zhang, J.; Deng, Y.; Dai, Y.; Feng, D. Fast Blind Rotation for Bootstrapping FHEs. In Proceedings of the Advances in Cryptology—CRYPTO 2023: 43rd Annual International Cryptology Conference, CRYPTO 2023, Santa Barbara, CA, USA, 20–24 August 2023; Volume 14084, pp. 3–36. [Google Scholar]
- Chowdhury, S.; Sinha, S.; Singh, A.; Mishra, S.; Chaudhary, C.; Patranabis, S.; Mukherjee, P.; Chatterjee, A.; Mukhopadhyay, D. Efficient Threshold FHE with Application to Real-Time Systems. Int. Assoc. Cryptologic Res. 2022, 1625. [Google Scholar]
- Damgard, I.; Thorbe, R.K. Linear Integer Secret Sharing and Distributed Exponentiation. In International Workshop on Public Key Cryptography; Springer: Berlin/Heidelberg, Germany, 2006; pp. 75–90. [Google Scholar]
- Regev, O. On lattices, learning with errors, random linear codes, and cryptography. J. ACM 2009, 56, 34. [Google Scholar] [CrossRef]
- Lyubashevsky, V.; Peikert, C.; Regev, O. On Ideal Lattices and Learning with Errors over Rings. In Proceedings of the Advances in Cryptology—EUROCRYPT 2010: 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques, French Riviera, France, 30 May–3 June 2010; Volume 6110, pp. 1–23. [Google Scholar]
- Pereira, H.V.L. Bootstrapping Fully Homomorphic Encryption over the Integers in Less than One Second. In Proceedings of the IACR International Conference on Public-Key Cryptography, Edinburgh, UK, 5–13 May 2021; Volume 12710, pp. 331–359. [Google Scholar]
- Alagic, G.; Apon, D.; Cooper, D.; Dang, Q.; Dang, T.; Kelsey, J.; Lichtinger, J.; Miller, C.; Moody, D.; Peralta, R.; et al. Status Report on the Third Round of the NIST Post-Quantum Cryptography Standardization Process. NIST IR 2022. [Google Scholar] [CrossRef]
- Ducas, L.; Lyubashevsky, V.; Prest, T. Efficient Identity-Based Encryption over NTRU Lattices. Int. Assoc. Cryptologic Res. 2014, 794. [Google Scholar]
- Chen, Y. Quantum Algorithms for Lattice Problems. Int. Assoc. Cryptologic Res. 2024, 555. [Google Scholar]
| Abbreviation | Implication |
|---|---|
| S-NGS | NGS of symmetric encryption |
| Th-S-NGS | ThFHE based on S-NGS scheme |
| scalar ciphertext | |
| vector ciphertext |
| Phase | Form of Ciphertext |
|---|---|
| Encrypted ciphertext | |
| Decrypted ciphertext |
| Scheme | Based | Homomorphic Multiplication | Computation Time |
|---|---|---|---|
| Li [24] | NTRU | Tensor product | |
| Xu [25] | g-NTRU | Tensor product | |
| TFHE [38] | GSW | External product | |
| Th-S-NGS | S-NGS | External product |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhao, X.; Yuan, Z. Threshold Fully Homomorphic Encryption Scheme Based on NGS of Symmetric Encryption. Symmetry 2025, 17, 737. https://doi.org/10.3390/sym17050737
Zhao X, Yuan Z. Threshold Fully Homomorphic Encryption Scheme Based on NGS of Symmetric Encryption. Symmetry. 2025; 17(5):737. https://doi.org/10.3390/sym17050737
Chicago/Turabian StyleZhao, Xu, and Zheng Yuan. 2025. "Threshold Fully Homomorphic Encryption Scheme Based on NGS of Symmetric Encryption" Symmetry 17, no. 5: 737. https://doi.org/10.3390/sym17050737
APA StyleZhao, X., & Yuan, Z. (2025). Threshold Fully Homomorphic Encryption Scheme Based on NGS of Symmetric Encryption. Symmetry, 17(5), 737. https://doi.org/10.3390/sym17050737






