Secure and Scalable Device Attestation Protocol with Aggregate Signature
Abstract
1. Introduction
- Bottlenecks due to centralized requests. Numerous peripheral devices are connected to the host platform. Each device receives an authentication request from the central requester and must respond to it. Thus, all authentication responses are concentrated on the requester, which can cause heavy computation and network loads. As the number of connected devices increases, requesters consume more computing resources and bandwidth, increasing the risk of bottlenecks, potentially delaying the system boot time, and degrading the overall performance. This architecture exhibits an inherent asymmetry, where the central requester is solely responsible for verifying all responders, incurring a potential performance bottleneck. Similar phenomena are evident in large-scale computing installations [8,9], where centralized authentication systems have historically suffered from scalability challenges, demonstrating that an optimized approach is critical to mitigating such performance issues.
- Limitations of resource-constrained devices. While the existing X.509 certificates are typically hundreds of bytes to several kilobytes (KB) in size, they are transmitted in chain form, usually including the certificates of the issuing Certificate Authority (CA), rather than as a single certificate, so the data conveyed during the authentication phase are expected to be several KB in size on average. Regarding the web server and the client, sufficient computing resources and network bandwidths are available for addressing such X.509 certificates. However, transmitting and verifying certificates can lead to a substantial network overhead in resource-constrained environments, such as on peripheral devices or IoT devices, potentially degrading system performance. From a scalability perspective, the size of the certificates, which can be several KB, can significantly burden these devices.
- We propose a secure and scalable device attestation protocol based on the SPDM with a chainless-certificate-based aggregate signature scheme;
- The proposed scheme introduces group-based attestation, where the group leader aggregates both signatures and certificates from multiple devices, significantly reducing the computation and communication overhead;
- We replace the traditional X.509 certificates with chainless certificates, reducing the size of the identity and improving the overall performance in resource-constrained environments;
- A formal security model and proof are provided to demonstrate the existential unforgeability of the proposed scheme under an adaptive chosen message attack (EUF-ACMA);
- We present both theoretical and experimental evaluations to demonstrate the efficiency and scalability of SPDM-AggSig compared to those of the SPDM-based implementations, resulting in an approximately 84.18% lower computation overhead and 96.22% lower communication overhead (evaluated using ECC P-384 for 1000 devices);
- The proposed scheme reduces the attestation asymmetry by balancing the burdens between the requesters and responders, leading to a more functionally symmetric attestation system.
2. Background
2.1. Overview of SPDM
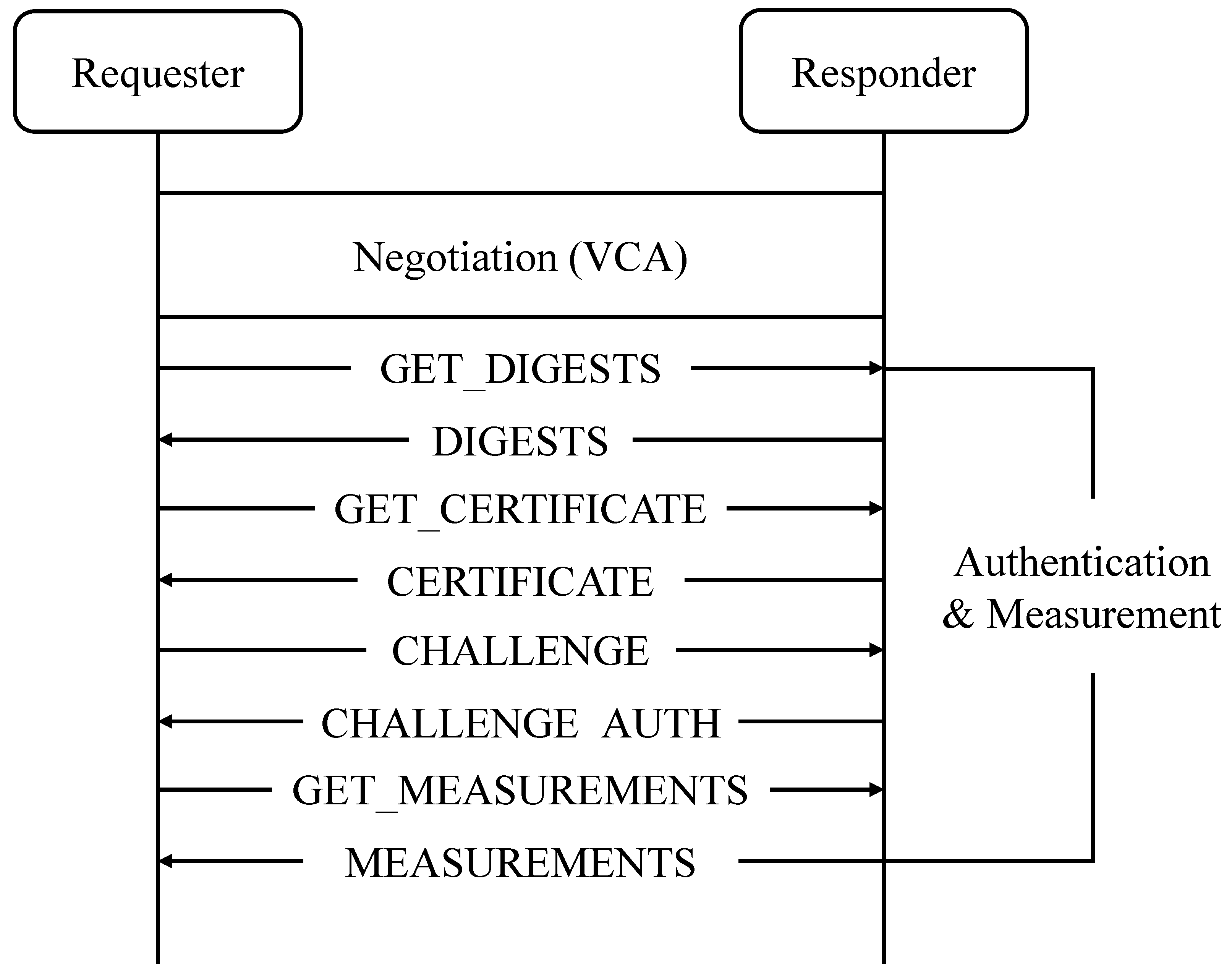
- The negotiation phase. In this phase, SPDM ensures that both the requester and the responder agree on the supported versions, capabilities, and cryptographic algorithms, commonly abbreviated as VCA. The requester and the responder exchange messages to negotiate the compatibility between protocol versions, identify supported features and capabilities, and agree upon the cryptographic algorithms for the device attestation phase.
- The device attestation phase. In this phase, SPDM focuses on verifying the identity of the device and ensuring the integrity of its firmware and hardware configuration. They exchange messages as follows:
- GET_DIGESTS/DIGESTS: The requester initiates the authentication by sending a GET_DIGESTS message to retrieve the hash value of the responder’s certificate chain. If the hash value matches a previously verified identity cached by the requester, the process of retrieving the entire certificate chain can be omitted.
- GET_CERTIFICATE/CERTIFICATE: The requester sends a GET_CERTIFICATE message to retrieve the responder’s X.509 certificate. The responder provides the whole certificate chain in the CERTIFICATE response.
- CHALLENGE/CHALLENGE_AUTH: To verify the responder’s possession of the secret key associated with the certificate, the requester sends a CHALLENGE message. The responder replies with the CHALLENGE_AUTH message containing the signature signed by its own secret key. In SPDM, the message to be signed is referred to as the message transcript.
- GET_MEASUREMENTS/MEASUREMENTS: The requester sends the GET_MEASUR EMENTS message to obtain specific measurements from the responder, such as the current state of the firmware, the hardware configuration, or other security-related data.
2.2. X.509 Certificates
2.3. Aggregate Signatures
3. Description of the System and Security Goals
3.1. The System Model
- Certificate Authority. As the root of trust in the system, the CA issues the device certificates. These certificates are used to bind a device’s public key to its unique identity. Unlike in web environments, the CA in this system is often controlled by the device manufacturer, providing more control over the certificate structures and supply chain security. Furthermore, by adopting short-lived certificates issued securely at the time of manufacturing, the system inherently mitigates the potential risks associated with compromised or vulnerable certificates, as any compromised certificate can be quickly replaced with a newly updated one. This frequent update process effectively eliminates the need for complex revocation mechanisms such as CRLs or OCSP, substantially simplifying the certificate lifecycle management and strengthening the system’s overall resilience. Certificate issuance can conveniently leverage SPDM’s existing identity provisioning mechanisms.
- Requester. As shown in Figure 3, the requester initiates the authentication process to verify the identity and integrity of the responder. For example, in a data center, the host platform may act as the requester when verifying the authenticity of numerous peripheral devices. The primary role of the requester is to authenticate responders by verifying their certificates and ensuring that they possess the secret key corresponding to the public key included in the certificate.
- Responder. The responder sends the information required for authentication to the requester. As shown in Figure 3, each responder obtains a certificate from the CA corresponding to its own key pair. In our scheme, responders can be categorized into group leaders and group members depending on their roles.
- Group leader: The group leader acts as an intermediary between the requester and the group. It collects authentication data—such as certificates or signatures—from group members at different stages. The group leader can aggregate such authentication data into a constant size, reducing the computation and communication overhead for the requester.
- Group member: Group members are individual devices within the group, with each holding a chainless certificate issued by the CA. They provide their authentication data to the group leader in the device attestation phase.
3.2. Preliminaries
3.2.1. The Elliptic Curve Cryptosystem and Assumptions
3.2.2. Algorithm Definition
- : This algorithm takes the security parameter as input. It outputs the public parameter and the secret key of the CA .
- : This algorithm takes the identity as the input. It outputs the public/secret key pair .
- : This algorithm takes , , and as the input. It outputs the corresponding certificate .
- : This algorithm takes as the input. It outputs a commitment that can be used to verify whether corresponds to associated with .
- : This algorithm takes , and as input. It outputs 1 if the commitment is valid, confirming that corresponds to associated with ; otherwise, it outputs 0, indicating that the certificate verification failed.
- (: This algorithm takes proofs as input. It outputs the corresponding aggregation proof .
- : This algorithm takes , , and as input. If is valid, it outputs 1; otherwise, it outputs 0.
- (: This algorithm takes , and message m as input. It outputs the signature .
- : This algorithm takes , the public key of the CA , , and m as input. If is valid, it outputs 1; otherwise, it outputs 0.
- (: This algorithm takes the signatures as input. It outputs the corresponding aggregation signature .
- : This algorithm takes , , , and as input. If is valid, it outputs 1; otherwise, it outputs 0.
3.3. The Security Model
- Type I (malicious device) adversary : An external attacker cannot access the master secret key used to generate the certificate (i.e., the secret key of the CA). Instead, it can replace the public keys of other devices.
- Type II (malicious CA) adversary : A malicious or compromised CA can generate a valid certificate for the target public key pair.
- The initialize phase: runs Setup(·) to generate and . keeps securely and sends to .
- The query phase:
- KeyExtract: Upon receiving the identity , == KeyGen(·) to create the key pairs () and send to .
- PubKeyReplace: For an identity , can replace with . It is not required to possess the corresponding secret key, and the process can be performed repeatedly.
- CertExtract: runs CertGen(·) and sends the certificate on the requested () to .
- SecKeyExtract: Upon receiving the identity , checks the recorded output from the KeyExtract query and sends to .
- SignExtract: Upon receiving the identity and message m, can run Sign(·) to generate a signature and send it to .
- The forgery phase: outputs a forged signature for the challenge identity and message , where was never queried during PriKeyExtract and the pair was never queried during SignExtract. The corresponding certificate cannot be captured by . In addition, of cannot be replaced.
- The output phase: Upon receiving the forged signature tuple , if Verify(·) returns 1, then wins the game, and outputs 1; otherwise, it outputs 0.
4. The Proposed Scheme
4.1. SPDM-AggSig
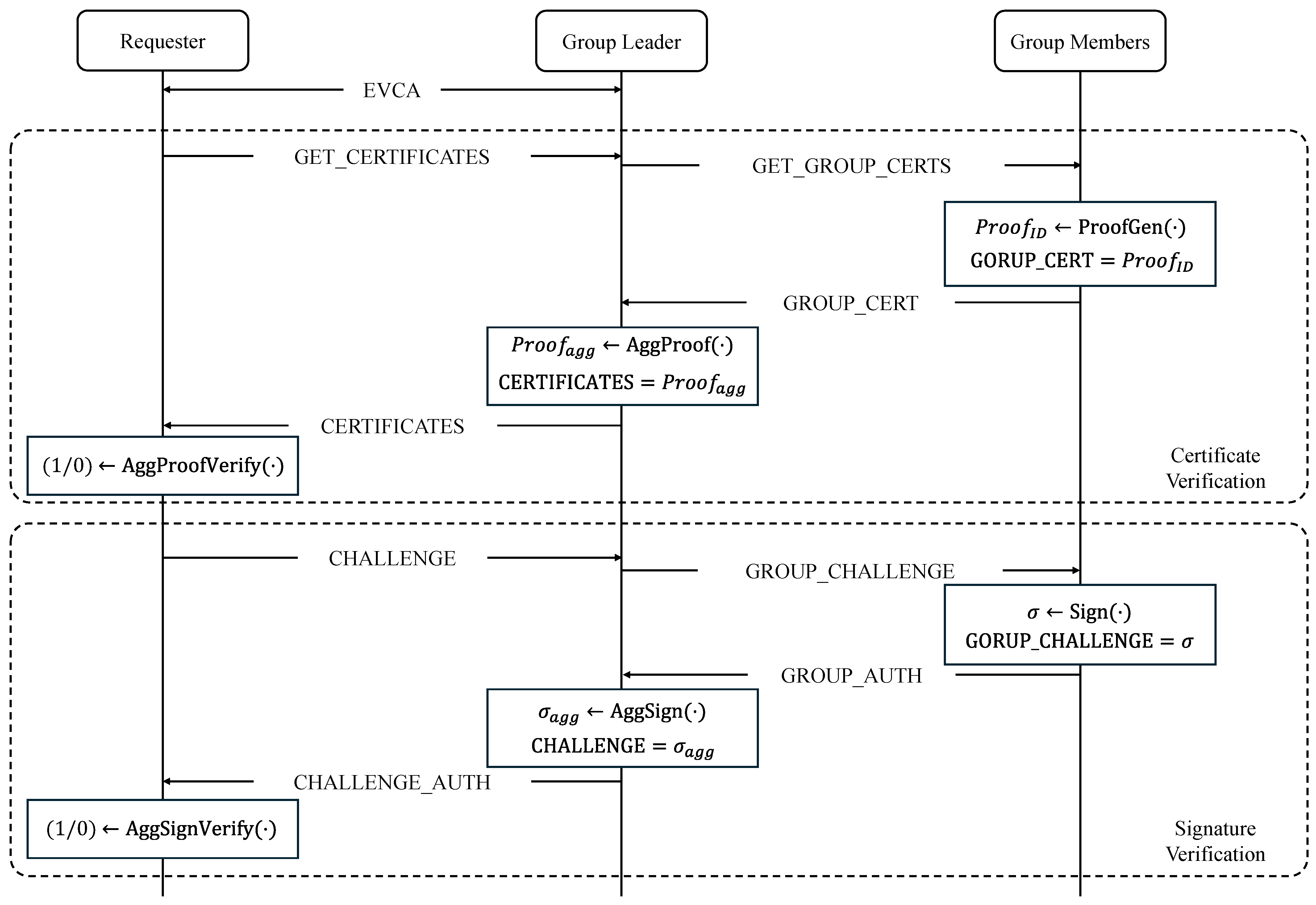
4.1.1. Group-Based Attestation
- EVCA (Extended Version, Capability, Algorithm Negotiation): The requester sends an extended version of VCA to the leader, including group-based authentication parameters, such as group member identifiers.
- Group certificate management (GET_GROUP_CERTS/GROUP_CERT): The group leader retrieves the certificates from all group members using the GET_GROUP_ CERTS message. Each group member responds with their certificate using the GROUP_CERT message. In the proposed scheme, the responder runs ProofGen(·) to generate and transmit a publicly verifiable certificate proof, allowing a third party to validate its authenticity without disclosing sensitive information (see Section 4.1.2 for details). The group leader then collects these certificates from multiple responders, including its own, and produces an aggregated proof . The requester eventually verifies that a trusted CA has issued using AggProofVerify(·). The GET_GROUP_CERTS message additionally includes the negotiated features and the cipher suite, which is determined during the EVCA phase.
- Group-based authentication (GROUP_CHALLENGE/GROUP_AUTH): The group leader issues GROUP_CHALLENGE to all group members, driving each member to run Sign(·) and generate an individual signature for the challenge message. The group leader then collects these signatures through GROUP_AUTH and aggregates them into a constant-size aggregated signature using AggSign(·). On receiving , the requester verifies the signature through AggSignVerify(·) to confirm that each device possesses the secret key corresponding to its certificate, thereby completing the authentication process. The GROUP_CHALLENGE message additionally includes the message transcript to be signed.
4.1.2. Chainless-Certificate-Based Aggregate Signatures
- : The CA can run the setup algorithm with a security parameter . This generates the public parameters , and its key pair , where a random , and P is the generator of the elliptic curve group . The cryptographic hash functions are defined as follows:
- ;
- .
- : The responder can generate its key pair with the identity . The secret key , and the corresponding public key is , where a random .
- : The CA can generate the certificate for the device as follows:
- , where a random ;
- , where .
- : The responder can generate the proof used to verify whether the certificate was issued by the CA as follows:
- , where a random ;
- .
- : This requester can verify the received proof by checking whether the commitment in correctly matches as follows:where . It outputs 1 if the verification succeeds and 0 otherwise.
- (: The group leader can combine n proofs {} into the aggregated proof as follows:
- ;
- and .
- : The requester can verify the aggregated proof as follows:where . It outputs 1 if the verification succeeds and 0 otherwise.
- : The responder can generate a signature on the message m as follows:
- , where a random ;
- where .
- : The requester can verify the signature as follows:where and . It outputs 1 if the verification succeeds and 0 otherwise.
- : The group leader can combine n signatures {} into a single aggregated signature as follows:
- and .
- : The requester can verify the aggregated signature as follows:where , and . It outputs 1 if the verification succeeds and 0 otherwise.
4.2. The Correctness Proof
- Aggregated certificate correctness proof. Given the aggregated certificate proof , the AggProofVerify(·) algorithm computes
- Aggregated signature correctness. Given the aggregated signature , the AggSignVerify(·) algorithm computes
4.3. Discussion and Future Work
4.3.1. Peer-to-Peer Communication
4.3.2. Compatibility with SPDM-Origin
4.3.3. Handling Failure Scenarios
- Network failures. In practical deployment scenarios, network conditions such as latency or packet loss may occasionally lead to attestation failures. However, SPDM inherently resolves such failures through straightforward mechanisms, including session re-initialization and requester-initiated retries. Given these inherent recovery capabilities, SPDM-AggSig naturally achieves sufficient robustness against typical network disruptions without relying on further specialized mechanisms, thus maintaining operational simplicity.
- Device and firmware compromise. SPDM explicitly assumes trust in the manufacturing process, where the devices and firmware are provisioned securely based on hardware RoTs. Consequently, SPDM-AggSig is primarily designed to detect and handle scenarios where a genuine device is replaced with an unauthorized one or a device’s firmware becomes compromised after provisioning. Measurement-based attestation ensures that compromised devices or firmware modifications are readily observable, enabling immediate exclusion and replacement.
- Group leader compromise. Another critical failure scenario involves the potential compromise or failure of group leaders in SPDM-AggSig, which could introduce single-point-of-failure vulnerabilities. Our scheme proactively addresses the issue through built-in measurement validation mechanisms that leverage the hardware RoT, facilitating the rapid detection and immediate exclusion of compromised or faulty leaders. In addition, further enhancements such as deploying fallback mechanisms with secondary leaders pre-designated by the manufacturers or integrating dynamic leader election processes can be readily incorporated to ensure continuous and secure group operation under diverse operational conditions. We will leave these enhancements as directions for future work.
4.3.4. Further Security Enhancements
5. Security Analysis
5.1. Sketch of the Proof
5.2. Security Proof
- KeyExtract: Upon receiving a public key request query for , the challenger checks for an existing tuple . If such a tuple is found, it responds with . Otherwise, it generates a new key pair , where is chosen uniformly at random, and returns . The newly generated tuple is then added to .
- SecKeyExtract: Upon receiving a secret key request for , the challenger checks for an existing tuple . If such a tuple is found, it responds with . Otherwise, it generates a new key pair , where is chosen uniformly at random, returns , and adds the newly created tuple to .
- CertExtract: Upon receiving a certificate request for and , the challenger first checks whether . If so, aborts. Otherwise, generates the certificate , where , are chosen uniformly at random. It then returns and adds the tuple to .
- PubKeyReplace: Upon receiving a public key replacement request for , the challenger first checks whether . If so, the query is ignored. Otherwise, the challenger searches for the tuple . Once found, it replaces the tuple with , indicating that the corresponding secret key is no longer available.
- : Upon receiving an hash oracle request for , the challenger checks for an existing tuple . If the tuple exists, returns . If the tuple does not exist, follows the same process as for a certificate generation request for , obtaining along with the corresponding certificate tuple . The newly created tuple is then added to , and is returned.
- SignExtract: Upon receiving a signature generation request for , if , the challenger generates the signature , where , with chosen uniformly at random and . The tuple is then added to . The certificate can be obtained through a CertExtract query. Otherwise, aborts the game.
- : does not abort during the query phase;
- : The adversary produces a valid forged signature.;
- : The forgery corresponds to the target identity .
5.3. Security Properties
- Device Authentication.
- Certificate verification: We ensure that the device cannot generate a valid certificate without knowledge of the CA secret key. The certificate proof verification determines whether the certificate is valid and issued by a trusted CA.
- Signature verification: We guarantee that the device holds the secret key corresponding to the public key in the verified certificate. The successful verification of the signature demonstrates proof of possession of the secret key without revealing it.
- Replay attack protection. Since the signature scheme is probabilistic, it produces a different signature each time, even for the same message. This randomness ensures that identical messages do not result in identical signatures, effectively preventing replay attacks. Any attempt to resend a captured old signature will easily be detected and rejected.
- Man-in-the-middle (MITM) attack protection.
- Impersonation attack prevention: The combination of certificate and signature verification ensures that only devices with valid certificates and the correct secret key can participate in the protocol. Without them, any attempt to impersonate a legitimate device is detected at the verification phase.
- Modification attack prevention: We ensure the integrity of the message by verifying each corresponding signature. An alteration in a single bit of the message means that the signature no longer matches, which protects the system from tampering or data injection by malicious attackers.
6. Comparative and Performance Analysis
6.1. A Comparative Analysis with Existing CBAS Schemes
6.1.1. Functionality Comparison
6.1.2. Security Comparison
6.1.3. Performance Comparison
- Theoretical evaluation. Table 3 compares the computation and communication overheads of the three evaluated CBAS schemes. In terms of the computation cost, a critical observation is that the signature verification cost, particularly involving the relatively expensive scalar multiplication operation , is notably higher in Q-CBAS compared to that in the other schemes. The increased overhead in Q-CBAS reflects a trade-off arising from its stronger security assumptions discussed in Section 6.1.2. On the other hand, our scheme and V-CBAS exhibit a similar computational efficiency. Regarding the communication overhead, the aggregate signature size in Q-CBAS increases linearly with the number of devices m, whereas both V-CBAS and the proposed scheme maintain a constant signature size regardless of m. The constant-size characteristic significantly enhances scalability and efficiency, particularly in large-scale deployments, highlighting a clear advantage over Q-CBAS in practical SPDM scenarios.Experimental evaluation. Figure 5 illustrates the results of the experimental evaluation of the CBAS schemes. The left y-axis represents the computation overhead, while the right y-axis indicates the communication overhead. The bar graphs illustrate the computation overhead, divided into the signature generation, signature verification, and overall cost, whereas the green line graph with markers indicates the aggregate signature size, representing the communication overhead. Specifically, Q-CBAS exhibits a significantly higher computational overhead, particularly during the signature verification stage, due to the larger number of costly scalar multiplications. This overhead notably increases as the number of aggregated devices grows from 100 to 1000, demonstrating the scalability limitations of the Q-CBAS scheme. In contrast, V-CBAS and our scheme show a comparable computation overhead, maintaining efficiency across varying device scales. Moreover, regarding the communication overhead, the linear growth in the aggregate signature size of Q-CBAS is evident as the number of devices increases. In contrast, both V-CBAS and our scheme retain constant-size signatures. Consequently, these experimental results underscore the proposed scheme’s prominent scalability and practicality for large-scale SPDM-based attestation deployments.
6.2. Performance Analysis in SPDM-Based Implementations
6.2.1. Theoretical Evaluation
- The computational overhead. The computational overhead incurred during the certificate and signature verification phases for the four schemes is shown in Table 5 and Table 6, respectively. When calculating the overall cost, we include the overhead introduced by all m devices in the system. In other words, the overall cost is represented as the sum of the requester’s cost and the cost of m responders. In schemes employing a group leader, the overall cost is revised to account for the leader’s overheads: .
6.2.2. Experimental Evaluation
- The communication overhead. As shown in Figure 6, the communication cost for the four schemes—SPDM-Origin, SPDM-Group, SPDM-Chainless, and SPDM-AggSig—is analyzed across different numbers of devices (1, 200, 400, 600, 800, and 1000). The size of the X.509 certificate is set to 600 bytes, following the example provided in the SPDM v1.3 standard document [5]. In the case of EVCA, the main difference from VCA is the inclusion of a group member identifier (4 bytes each) (Typically, 2 bytes are used as device identifiers in PCIe and CXL, but 4 bytes are chosen here for scalability.).
- Computation overhead. In Figure 7, the computation cost for SPDM-Origin, SPDM-Chainless, and SPDM-AggSig is analyzed across different numbers of devices (100, 500, and 1000) and the ECC curves P-256 and P-384. Since the overall computation cost of SPDM-Origin and SPDM-Group is equivalent, as shown in Table 5 and Table 6, only the cost for SPDM-Origin is presented.
7. Conclusions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Ryan, C. Tech Tampering: Are Hardware Supply Chain Attacks on the Rise? 2024. Online Resource. Available online: https://www.siliconrepublic.com/enterprise/hp-wolf-security-hardware-attacks-tampering (accessed on 29 April 2025).
- Plumb, T. HP Wolf: Not Just Software Attacks; Hackers Are Coming for Enterprise Hardware, Too. Online Resource. 2024. Available online: https://venturebeat.com/security/hp-wolf-not-just-software-attacks-hackers-are-coming-for-enterprise-hardware-too/ (accessed on 29 April 2025).
- Holland, A. Hardware Supply Chain Threats Can Undermine Your Endpoint Infrastructure. Online Resource. 2025. Available online: https://www.techradar.com/pro/hardware-supply-chain-threats-can-undermine-your-endpoint-infrastructure (accessed on 29 April 2025).
- DMTF. Distributed Management Task Force. Online Resource. Available online: https://www.dmtf.org/ (accessed on 29 April 2025).
- DMTF. DSP0274 Security Protocol and Data Model (SPDM) Specification. Version 1.3. Online Resource. 2023. Available online: https://www.dmtf.org/sites/default/files/standards/documents/DSP0274_1.3.0.pdf (accessed on 29 April 2025).
- Rescorla, E. The Transport Layer Security (TLS) Protocol Version 1.3. RFC 8446. 2018. Available online: https://www.rfc-editor.org/info/rfc8446 (accessed on 29 April 2025).
- Boeyen, S.; Santesson, S.; Polk, T.; Housley, R.; Farrell, S.; Cooper, D. Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile. RFC 5280. 2008. Available online: https://www.rfc-editor.org/info/rfc5280 (accessed on 29 April 2025).
- Niu, Z.; Jiang, H.; Zhou, K.; Yang, T.; Yan, W. Identification and authentication in large-scale storage systems. In Proceedings of the 2009 IEEE International Conference on Networking, Architecture, and Storage, Zhangjiajie, China, 9–11 July 2009; IEEE: New York, NY, USA, 2009; pp. 421–427. [Google Scholar]
- Goel, A.; Rahulamathavan, Y. A Comparative Survey of Centralised and Decentralised Identity Management Systems: Analysing Scalability, Security, and Feasibility. Future Internet 2024, 17, 1. [Google Scholar] [CrossRef]
- Qiao, Z.; Yang, Q.; Zhou, Y.; Yang, B.; Xia, Z.; Zhang, M.; Wang, T. An efficient certificate-based aggregate signature scheme with provable security for Industrial Internet of Things. IEEE Syst. J. 2022, 17, 72–82. [Google Scholar] [CrossRef]
- Verma, G.K.; Singh, B.; Kumar, N.; Chamola, V. CB-CAS: Certificate-based efficient signature scheme with compact aggregation for industrial Internet of Things environment. IEEE Internet Things J. 2019, 7, 2563–2572. [Google Scholar] [CrossRef]
- CXL. Compute Express Link. Online Resource. Available online: https://computeexpresslink.org/ (accessed on 29 April 2025).
- MIPI. Mobile Industry Processor Interface. Online Resource. Available online: https://www.mipi.org/ (accessed on 29 April 2025).
- TCG. Trusted Computing Group. Online Resource. Available online: https://trustedcomputinggroup.org/ (accessed on 29 April 2025).
- Intel Corporation. Intel® Trust Domain Extensions (Intel® TDX); Technical Report; Intel Corporation: Santa Clara, CA, USA, 2022; Available online: https://www.intel.com/content/www/us/en/developer/articles/technical/intel-trust-domain-extensions.html (accessed on 29 April 2025).
- Kaplan, D.; Powell, J.; Woller, T. AMD memory encryption. White Pap. 2016, 13, 12. [Google Scholar]
- DigiCert. DigiCert Website. Online Resource. 2024. Available online: https://www.digicert.com/ (accessed on 29 April 2025).
- Encrypt, L. Let’s Encrypt Website. Online. 2017. Available online: https://letsencrypt.org/ (accessed on 29 April 2025).
- GlobalSign. GlobalSign Website. Online Resource. 2024. Available online: https://www.globalsign.com/en (accessed on 29 April 2025).
- TCG. Device Identifier Composition Engine (DICE). Online Resource. 2024. Available online: https://trustedcomputinggroup.org/wp-content/uploads/DICE-Layering-Architecture-r19_pub.pdf (accessed on 29 April 2025).
- Samsung. Root CA Certificate for SSD Attestation. Online Resource. 2024. Available online: https://download.semiconductor.samsung.com/resources/certificate/Samsung_Memory_RootCA.crt (accessed on 29 April 2025).
- Netflix. Bless: SSH Certificate Authority. 2023. Available online: https://github.com/Netflix/bless (accessed on 29 April 2025).
- Horng, S.J.; Tzeng, S.F.; Huang, P.H.; Wang, X.; Li, T.; Khan, M.K. An efficient certificateless aggregate signature with conditional privacy-preserving for vehicular sensor networks. Inf. Sci. 2015, 317, 48–66. [Google Scholar] [CrossRef]
- Kumar, P.; Kumari, S.; Sharma, V.; Sangaiah, A.K.; Wei, J.; Li, X. A certificateless aggregate signature scheme for healthcare wireless sensor network. Sustain. Comput. Inform. Syst. 2018, 18, 80–89. [Google Scholar] [CrossRef]
- Cheng, L.; Wen, Q.; Jin, Z.; Zhang, H.; Zhou, L. Cryptanalysis and improvement of a certificateless aggregate signature scheme. Inf. Sci. 2015, 295, 337–346. [Google Scholar] [CrossRef]
- Han, Y.; Song, W.; Zhou, Z.; Wang, H.; Yuan, B. eCLAS: An efficient pairing-free certificateless aggregate signature for secure VANET communication. IEEE Syst. J. 2021, 16, 1637–1648. [Google Scholar] [CrossRef]
- Thumbur, G.; Rao, G.S.; Reddy, P.V.; Gayathri, N.; Reddy, D.K.; Padmavathamma, M. Efficient and secure certificateless aggregate signature-based authentication scheme for vehicular ad hoc networks. IEEE Internet Things J. 2020, 8, 1908–1920. [Google Scholar] [CrossRef]
- Wu, W.; Ye, F. IPCAS: An improved conditional privacy-preserving certificateless aggregate signature scheme without bilinear pairing for VANETs. J. Syst. Archit. 2024, 152, 103175. [Google Scholar] [CrossRef]
- Xu, R.; Zhou, Y.; Yang, Q.; Yang, K.; Han, Y.; Yang, B.; Xia, Z. An efficient and secure certificateless aggregate signature scheme. J. Syst. Archit. 2024, 147, 103030. [Google Scholar] [CrossRef]
- Hwang, Y.W.; Lee, Y. A Lightweight Certificate-Based Aggregate Signature Scheme Providing Key Insulation. Comput. Mater. Contin. 2021, 69, 1747. [Google Scholar] [CrossRef]
- Verma, G.K.; Singh, B.; Kumar, N.; Kaiwartya, O.; Obaidat, M.S. PFCBAS: Pairing free and provable certificate-based aggregate signature scheme for the e-healthcare monitoring system. IEEE Syst. J. 2019, 14, 1704–1715. [Google Scholar] [CrossRef]
- Verma, G.K.; Kumar, N.; Gope, P.; Singh, B.; Singh, H. SCBS: A short certificate-based signature scheme with efficient aggregation for industrial-internet-of-things environment. IEEE Internet Things J. 2021, 8, 9305–9316. [Google Scholar] [CrossRef]
- Verma, G.K.; Gope, P.; Saxena, N.; Kumar, N. CB-DA: Lightweight and escrow-free certificate-based data aggregation for smart grid. IEEE Trans. Dependable Secur. Comput. 2022, 20, 2011–2024. [Google Scholar] [CrossRef]
- Chen, J.N.; Huang, Z.J.; Zhou, Y.P.; Zou, F.M.; Chen, C.M.; Wu, J.M.T.; Wu, T.Y. Efficient certificate-based aggregate signature scheme for vehicular ad hoc networks. IET Netw. 2020, 9, 290–297. [Google Scholar] [CrossRef]
- Miller, V.S. Use of elliptic curves in cryptography. In Conference on the Theory and Application of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1985; pp. 417–426. [Google Scholar]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- NVIDIA. GPUDirect RDMA. Online Resource. Available online: https://docs.nvidia.com/cuda/gpudirect-rdma/ (accessed on 29 April 2025).
- Meier, S.; Schmidt, B.; Cremers, C.; Basin, D. The TAMARIN prover for the symbolic analysis of security protocols. In Proceedings of the Computer Aided Verification: 25th International Conference, CAV 2013, Saint Petersburg, Russia, 13–19 July 2013; Proceedings 25. Springer: Berlin/Heidelberg, Germany, 2013; pp. 696–701. [Google Scholar]
- Cremers, C.; Dax, A.; Naska, A. Formal Analysis of {SPDM}: Security Protocol and Data Model version 1.2. In Proceedings of the 32nd USENIX Security Symposium (USENIX Security 23), Anaheim, CA, USA, 9–11 August 2023; pp. 6611–6628. [Google Scholar]
- Yao, J.; Matusiewicz, K.; Zimmer, V. Post quantum design in SPDM for device authentication and key establishment. Cryptography 2022, 6, 48. [Google Scholar] [CrossRef]
- Pointcheval, D.; Stern, J. Security arguments for digital signatures and blind signatures. J. Cryptol. 2000, 13, 361–396. [Google Scholar] [CrossRef]
- OpenSSL. OpenSSL Library 3.4.0. Online Resource. Available online: https://openssl-library.org/source/ (accessed on 29 April 2025).
- NIST. Elliptic Curve Cryptographic Curve. Online Resource. Available online: https://csrc.nist.gov/projects/elliptic-curve-cryptography (accessed on 29 April 2025).





| Symbols | Description |
|---|---|
| Size of VCA message | |
| Size of EVCA message | |
| Size of X.509 certificate | |
| Size of chainless certificate | |
| Size of request message for certificates and signatures | |
| Size of additional messages for group-based attestation | |
| Size of element in | |
| Size of element in | |
| d | X.509 certificate chain length |
| m | Number of members in group |
| Scalar multiplication | |
| Point addition | |
| Modular multiplication | |
| Modular addition | |
| Modulo operation | |
| Modular inverse | |
| Cryptographic hash function |
| Scheme | Public Verifiability * | Certificate Aggregation | Signature Aggregation | SPDM Applicability | Secure Against | Secure Against |
|---|---|---|---|---|---|---|
| Q-CBAS [10] | × | × | ✓ | × | ✓ | ✓ |
| V-CBAS [11] | × | × | ✓ | × | ✓ | × |
| Ours | ✓ | ✓ | ✓ | ✓ | ✓ | − |
| Computation Cost | Aggregate Signature | |||
|---|---|---|---|---|
| Scheme | Individual Signature Generation | Signature Aggregation | Signature Verification | Size |
| Q-CBAS [10] | ||||
| V-CBAS [11] | ||||
| Ours |
| Scheme | Entity | Negotiation | Certificate Retrieval | Group Task | Authentication | Entity Cost | Overall Cost |
|---|---|---|---|---|---|---|---|
| SPDM | Requester | - | |||||
| -Origin | Leader | - | |||||
| Responder | - | ||||||
| SPDM | Requester | - | |||||
| -Group | Leader | ||||||
| Responder | - | ||||||
| SPDM | Requester | - | |||||
| -Chainless | Leader | - | |||||
| Responder | - | ||||||
| SPDM | Requester | - | |||||
| -AggSig | Leader | ||||||
| Responder | - | ||||||
| Scheme | Entity | Proof Generation | Group Task | Certificate Verification | Entity Cost | Overall Cost |
|---|---|---|---|---|---|---|
| SPDM | Requester | - | - | |||
| -Origin | Leader | - | ||||
| Responder | - | - | - | - | ||
| SPDM | Requester | - | - | |||
| -Group | Leader | - | ||||
| Responder | - | - | - | - | ||
| SPDM | Requester | - | - | |||
| -Chainless | Leader | - | ||||
| Responder | - | - | ||||
| SPDM | Requester | - | - | |||
| -AggSig | Leader | - | ||||
| Responder | - | - | ||||
| Scheme | Entity | Signature Generation | Group Task | Signature Verification | Entity Cost | Overall Cost |
|---|---|---|---|---|---|---|
| Requester | - | - | ||||
| SPDM | ||||||
| -Origin | Leader | - | ||||
| Responder | - | - | ||||
| Requester | - | - | ||||
| SPDM | Leader | |||||
| -Group | ||||||
| Responder | - | - | ||||
| Requester | - | - | ||||
| SPDM | ||||||
| -Chainless | Leader | - | ||||
| Responder | - | - | ||||
| Requester | - | - | ||||
| SPDM | Leader | - | ||||
| -AggSig | ||||||
| Responder | - | - | ||||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kwon, H. Secure and Scalable Device Attestation Protocol with Aggregate Signature. Symmetry 2025, 17, 698. https://doi.org/10.3390/sym17050698
Kwon H. Secure and Scalable Device Attestation Protocol with Aggregate Signature. Symmetry. 2025; 17(5):698. https://doi.org/10.3390/sym17050698
Chicago/Turabian StyleKwon, Hyunsoo. 2025. "Secure and Scalable Device Attestation Protocol with Aggregate Signature" Symmetry 17, no. 5: 698. https://doi.org/10.3390/sym17050698
APA StyleKwon, H. (2025). Secure and Scalable Device Attestation Protocol with Aggregate Signature. Symmetry, 17(5), 698. https://doi.org/10.3390/sym17050698





