SGDID: A Privacy-Enhanced Supervised Distributed Identity Model for Smart Grid and Electric Vehicle Integration
Abstract
1. Introduction
- We propose a distributed identity verification framework for smart grid and electric vehicle scenarios, enabling user identity autonomy and control, while ensuring the unlinkability of identities.
- We propose a method combining ZKP and challenge-based Pedersen commitments to verify masterID ownership and support anonymous identities in V2G settings, thereby enhancing the system’s practical applicability.
- We introduce a revocation mechanism using AND ZKP during registration to allow authorized supervisors to verify the mapping between userID and masterID, ensuring the traceability and effective management of malicious activities.
- Wed demonstrate the efficiency and scalability of the proposed framework through experimental results, comparing it with existing solutions in large-scale user scenarios.
2. Related Work
3. Preliminaries
4. Proposed Scheme
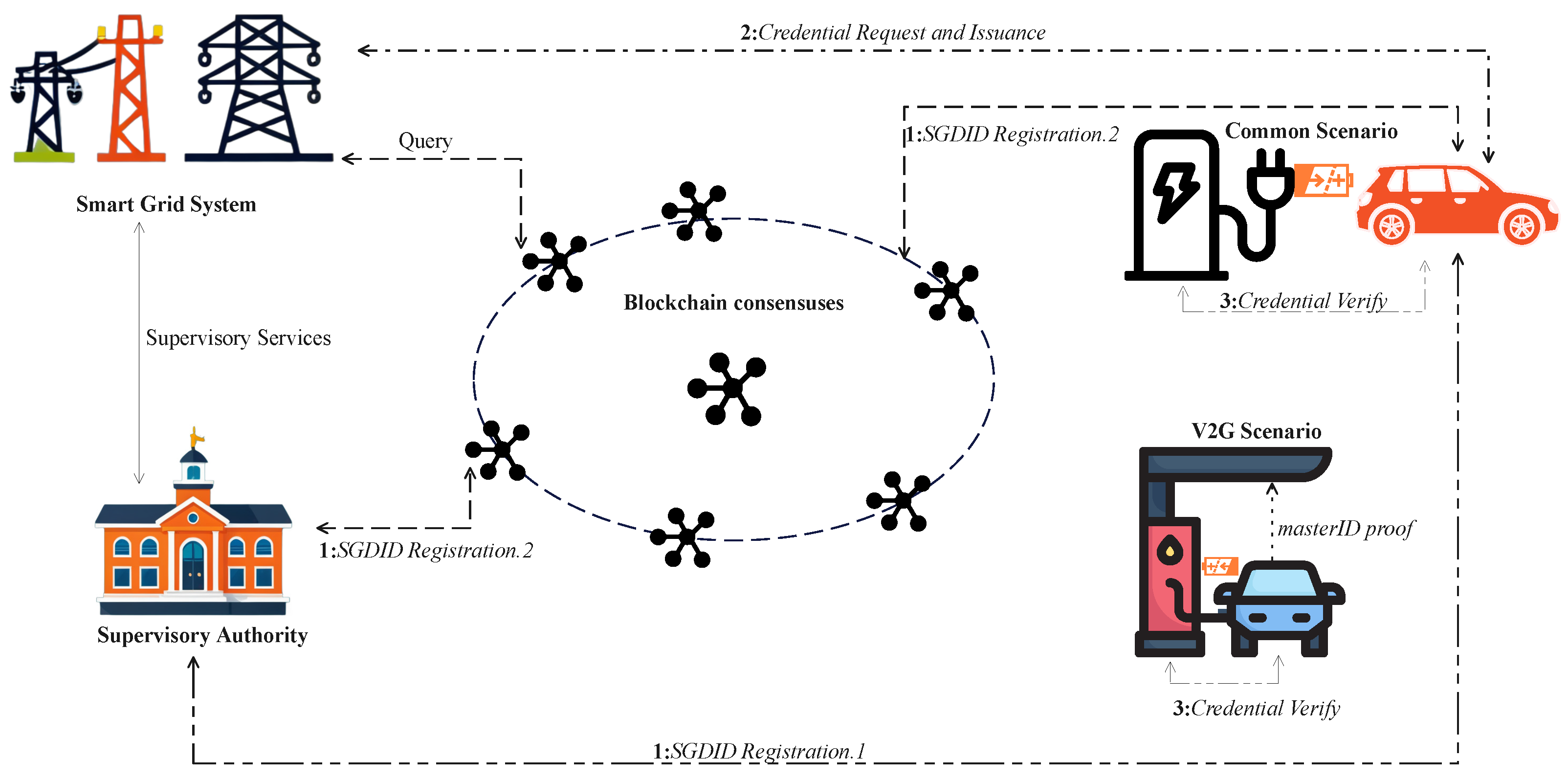
4.1. System Model
4.2. Security Model
- Sybil resistance: An adversary cannot forge valid peer identities from authentic identities, nor can they manipulate the system’s operation through fake (anonymous) identities.
- Unlinkability: An adversary cannot link different identities across multiple interactions or transactions to determine whether they belong to the same real-world entity.
- Anonymity: Users can choose to conceal their real identity and conduct transactions under an anonymous identity with specific restrictions.
- Unforgeability: Attackers cannot forge valid credentials using public parameters and information, nor can they fabricate a legitimate proof or claim to be associated with a real identity.
- Privacy: An adversary cannot obtain any private information beyond what the user has explicitly disclosed or made publicly available.
- Auditability: Malicious activities can be traced and sanctioned by a trusted supervisory authority, which maintains a list of sanctioned identities.
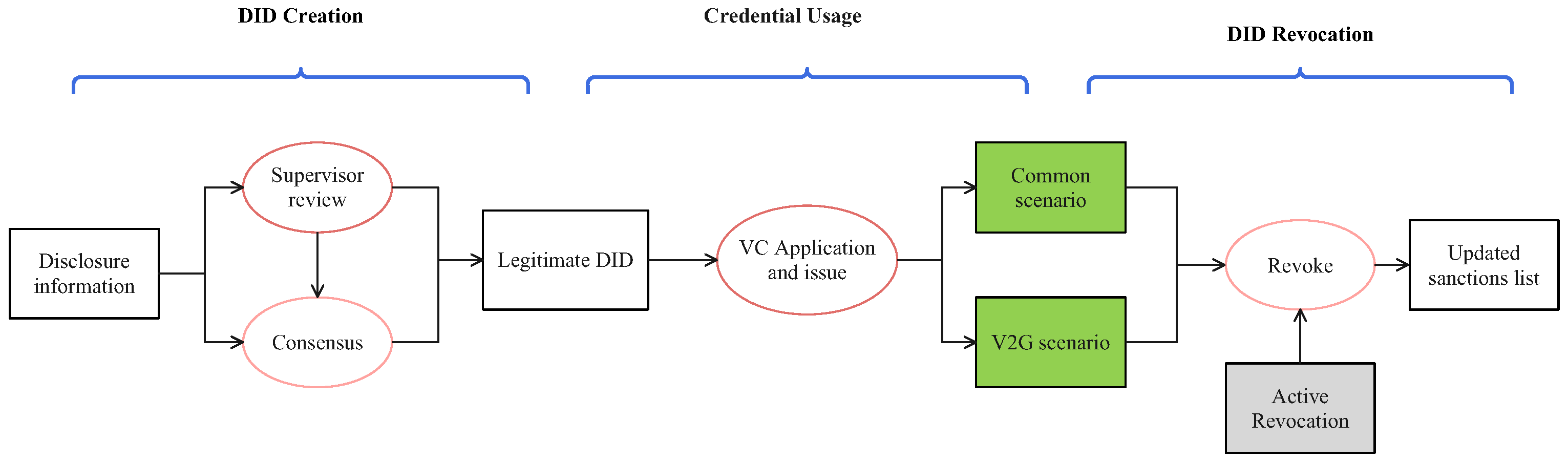
4.3. SGDID Design
4.3.1. Identity Registration Phase
4.3.2. Credential Request and Issuance
4.3.3. Credential Verify
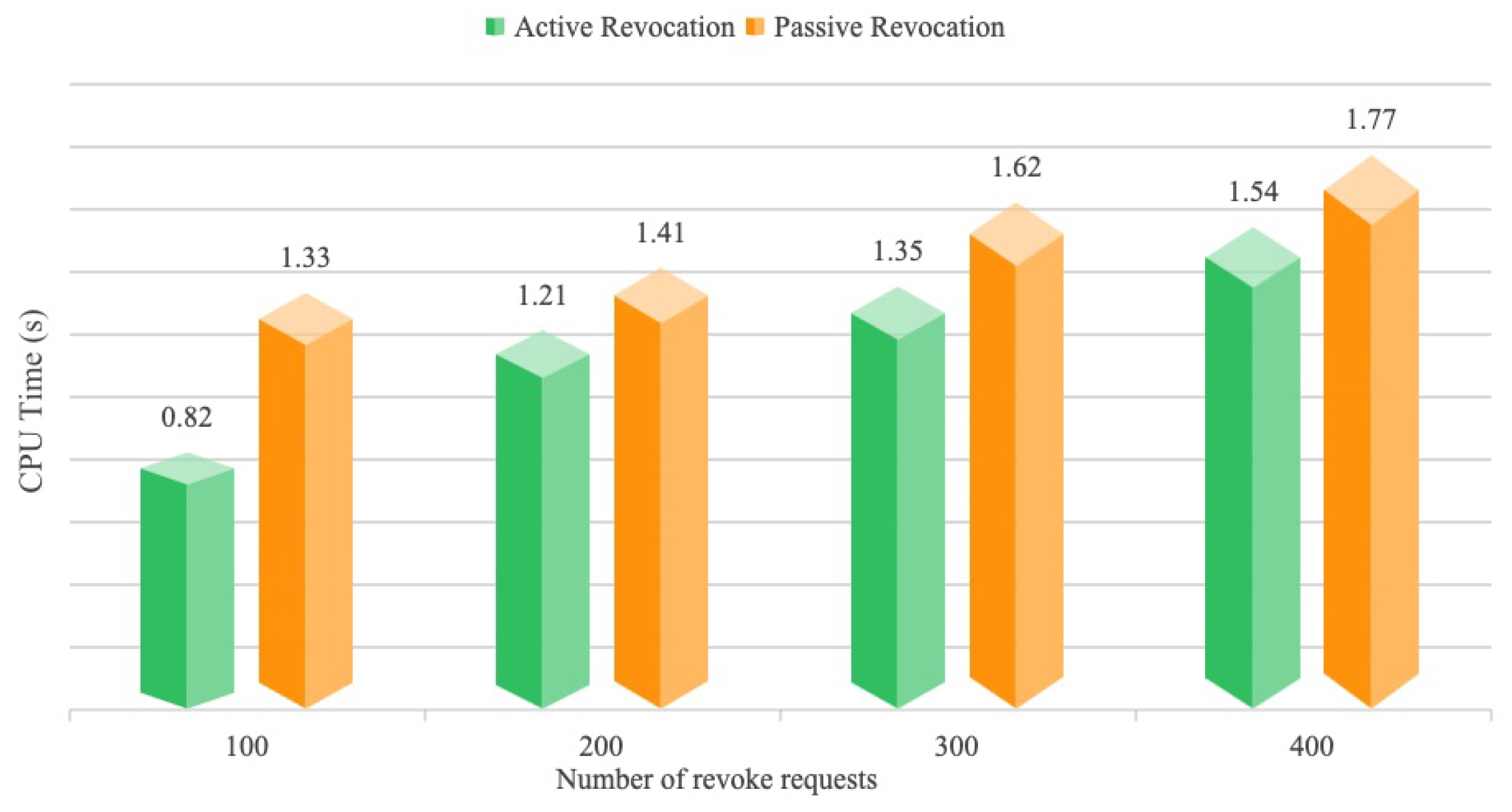
4.3.4. Revocation Mechanism
5. Security Analysis
5.1. Sybil Attack Resistance
5.2. Unlinkability
5.3. Conditional Anonymity
5.4. Unforgeability
5.5. Privacy Preservation
5.6. Auditability
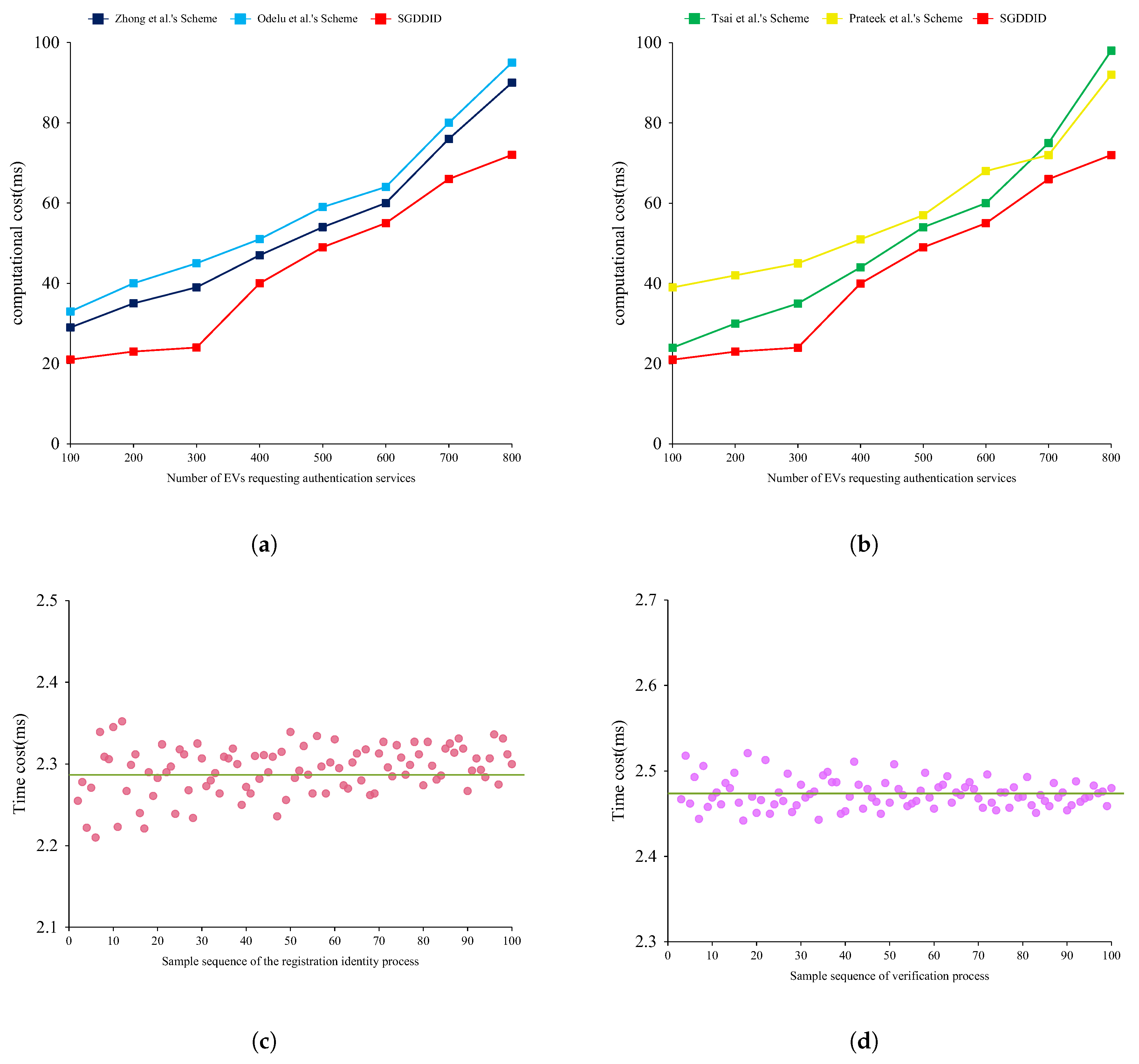
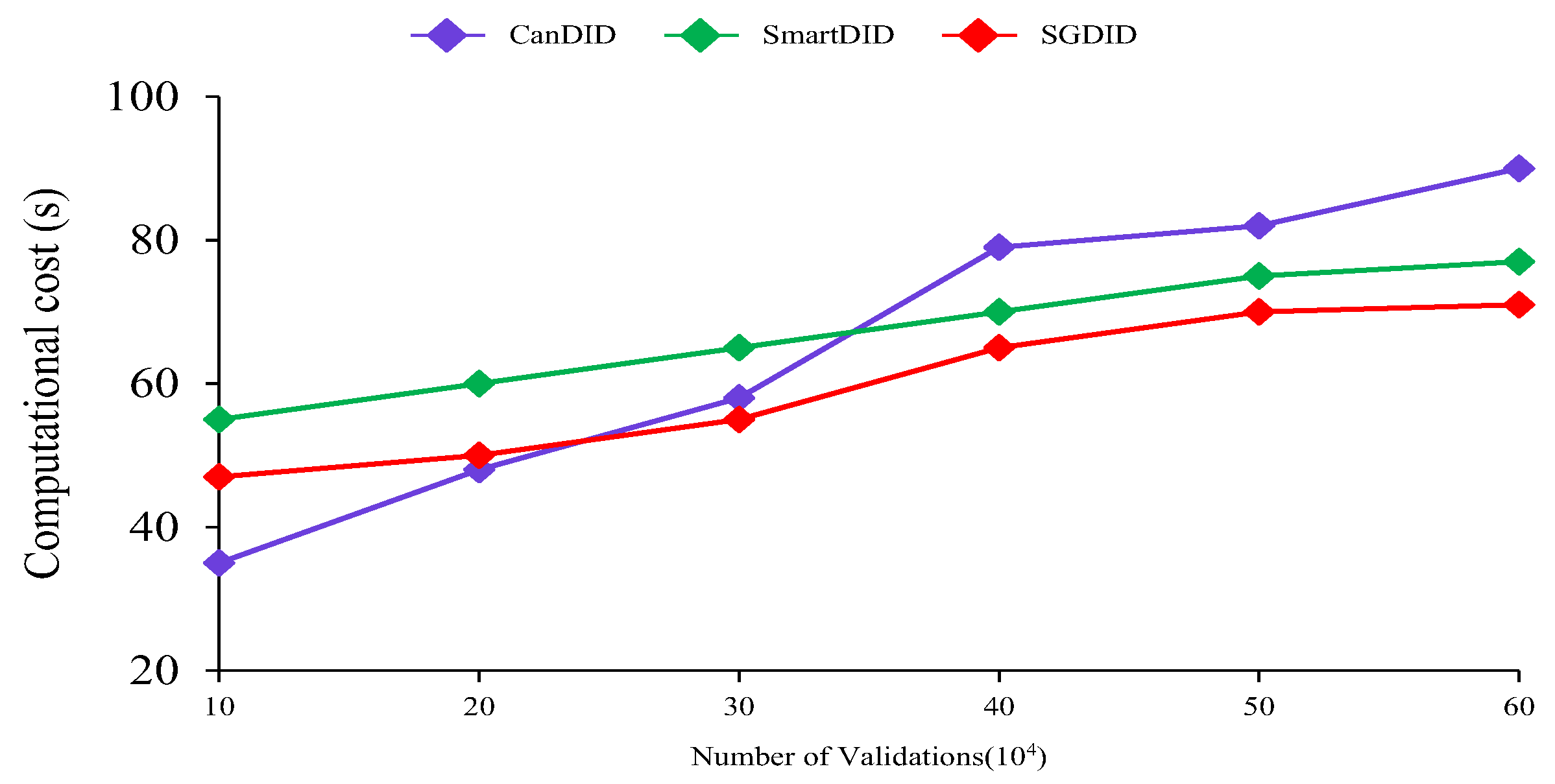
6. Performance Evaluation
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A. AND Zero-Knowledge Proof Process
Appendix A.1. Completeness
- 1.
- The user selects random nonces and computes the following commitments:
- 2.
- The user sends to the verifier.
- 3.
- The verifier generates a random challenge and sends it to the user.
- 4.
- The user computes the following responses:
- 5.
- The user sends to the verifier.
- 6.
- The verifier verifies the following equations:
Appendix A.2. Soundness
- 1.
- Assume that a dishonest prover attempts to generate valid responses and without knowing and .
- 2.
- To produce valid responses, the prover would need to solve the discrete logarithm problem to find and given and .
- 3.
- Since the discrete logarithm problem is computationally hard, the probability that the prover can correctly compute and without the private keys is negligible.
- 4.
- Therefore, the verifier will reject any such invalid proofs with high probability.
Appendix A.3. Zero-Knowledge
- 1.
- To demonstrate the zero-knowledge property, we construct a simulator that can generate a convincing proof without knowing and .
- 2.
- The simulator proceeds as follows:
- (a)
- selects random values and from .
- (b)
- computes the following commitments:where c is the challenge received from the verifier.
- (c)
- sends to the verifier.
- (d)
- The verifier sends back a challenge c.
- (e)
- responds with .
- 3.
- Since and are computed using random Z-values, the simulated proof is indistinguishable from a real proof generated by an honest prover.
- 4.
- Therefore, the verifier gains no additional knowledge about or beyond the fact that the user possesses valid masterID and userID.
Appendix B. Unlinkability Between Multiple userIDs
- 1.
- is given access to a challenge function , which is either the real hash function H or a truly random function R.
- 2.
- randomly selects a secret value s from uniformly at random and generates two userIDs as follows:where is a fixed constant ensuring s and are distinct.
- 3.
- provides both and to and asks whether they belong to the same user.
- 4.
- outputs a guess indicating whether the provided userIDs belong to the same user.
- 5.
- uses ’s guess to determine whether is H or R.
Appendix C. Indistinguishability Between masterID and userID
- 1.
- is given access to a challenge function , which is either the real hash function H or a truly random function R.
- 2.
- randomly selects two secret values and from uniformly at random and computes the following:
- 3.
- randomly chooses a bit and provides with the corresponding specific-id as follows:
- 4.
- outputs a guess indicating whether corresponds to masterID or userID.
- 5.
- uses to guess whether is H or R.
References
- Mutarraf, M.U.; Guan, Y.; Xu, L.; Su, C.L.; Vasquez, J.C.; Guerrero, J.M. Electric cars, ships, and their charging infrastructure—A comprehensive review. Sustain. Energy Technol. Assess. 2022, 52, 102177. [Google Scholar] [CrossRef]
- Safdar, I.; Raza, A.; Khan, A.Z.; Ali, E. Feasibility, emission and fuel requirement analysis of hybrid car versus solar electric car: A comparative study: Hybrid versus solar electric car comparison. Int. J. Environ. Sci. Technol. 2017, 14, 1807–1818. [Google Scholar] [CrossRef]
- Zhang, X.; Chen, C.; Qin, K.; Wang, Y.; Qu, S.; Wang, T.; Zhang, C.; Gu, D. Armored Core of PKI: Remove Signing Keys for CA via Efficient and Trusted Physical Certification. arXiv 2024, arXiv:2404.15582. [Google Scholar]
- Wu, Y.; Wang, Z.; Huangfu, Y.; Ravey, A.; Chrenko, D.; Gao, F. Hierarchical Operation of Electric Vehicle Charging Station in Smart Grid Integration Applications—An Overview. Int. J. Electr. Power Energy Syst. 2022, 139, 108005. [Google Scholar] [CrossRef]
- Ali, M.S.; Tongia, R. Electrifying Mobility in India: Future Prospects for the Electric and EV Ecosystem; Brookings Institution Reports; The Brookings Institution: Washington, DC, USA, 2018. [Google Scholar]
- Uddin, K.; Dubarry, M.; Glick, M.B. The viability of vehicle-to-grid operations from a battery technology and policy perspective. Energy Policy 2018, 113, 342–347. [Google Scholar] [CrossRef]
- World Forum for Harmonization of Vehicle Regulations (WP.29). UN R155: Cybersecurity and Cybersecurity Management System for Road Vehicles; United Nations Economic Commission for Europe (UNECE): Geneva, Switzerland, 2021. [Google Scholar]
- ISO 21434; Road Vehicles—Cybersecurity Engineering. ISO: Geneva, Switzerland, 2021.
- Hariri, A.M.; Hejazi, M.A.; Hashemi-Dezaki, H. Investigation of impacts of plug-in hybrid electric vehicles’ stochastic characteristics modeling on smart grid reliability under different charging scenarios. J. Clean. Prod. 2021, 287, 125500. [Google Scholar] [CrossRef]
- Rizwan, M.; Ali, M.; Hawbani, A.; Xingfu, W.; Anjum, A.; Angin, P.; Popoola, O.; Imran, M.A. IOTA-Based Game-Theoretic Energy Trading With Privacy-Preservation for V2G Networks. IEEE Trans. Sustain. Comput. 2024, 1, 1–14. [Google Scholar] [CrossRef]
- Rodrigues, C.; Oliveira, D.; Pinto, S. BUSted!!! Microarchitectural Side-Channel Attacks on the MCU Bus Interconnect. In Proceedings of the 2024 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 19–23 May 2024; pp. 3679–3696. [Google Scholar]
- Chaudhry, S.A.; Yahya, K.; Garg, S.; Kaddoum, G.; Hassan, M.M.; Zikria, Y.B. LAS-SG: An Elliptic Curve-Based Lightweight Authentication Scheme for Smart Grid Environments. IEEE Trans. Ind. Inform. 2023, 19, 1504–1511. [Google Scholar] [CrossRef]
- Faheem, M.; Kuusniemi, H.; Eltahawy, B.; Bhutta, M.S.; Raza, B. A lightweight smart contracts framework for blockchain-based secure communication in smart grid applications. IET Gener. Transm. Distrib. 2024, 18, 625–638. [Google Scholar] [CrossRef]
- Khalid, M. Smart grids and renewable energy systems: Perspectives and grid integration challenges. Energy Strategy Rev. 2024, 51, 101299. [Google Scholar] [CrossRef]
- Sadique, K.M.; Rahmani, R.; Johannesson, P. DIdM-EIoTD: Distributed Identity Management for Edge Internet of Things (IoT) Devices. Sensors 2023, 23, 4046. [Google Scholar] [CrossRef]
- Ferdous, M.S.; Cali, U.; Halden, U.; Prinz, W. Leveraging self-sovereign identity & distributed ledger technology in renewable energy certificate ecosystems. J. Clean. Prod. 2023, 422, 138355. [Google Scholar]
- Yuan, Q.; Yuan, H.; Zhao, J.; Zhou, M.; Shao, Y.; Wang, Y.; Zhao, S. Distributed Identity Authentication with Lenstra-Lenstra-Lovász Algorithm-Ciphertext Policy Attribute-Based Encryption from Lattices: An Efficient Approach Based on Ring Learning with Errors Problem. Entropy 2024, 26, 729. [Google Scholar] [CrossRef] [PubMed]
- Bunz, B.; Bootle, J.; Boneh, D.; Poelstra, A.; Wuille, P.; Maxwell, G. Bulletproofs: Short Proofs for Confidential Transactions and More. In Proceedings of the 2018 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–24 May 2018; pp. 315–334. [Google Scholar]
- Koulianos, A.; Paraskevopoulos, P.; Litke, A.; Papadakis, N.K. Enhancing Unmanned Aerial Vehicle Security: A Zero-Knowledge Proof Approach with Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge for Authentication and Location Proof. Sensors 2024, 24, 5838. [Google Scholar] [CrossRef] [PubMed]
- Yin, W. Zero-Knowledge Proof Intelligent Recommendation System to Protect Students’ Data Privacy in the Digital Age. Appl. Artif. Intell. 2023, 37, 1–14. [Google Scholar] [CrossRef]
- Guan, Z.; Wan, Z.; Yang, Y.; Zhou, Y.; Huang, B. BlockMaze: An Efficient Privacy-Preserving Account-Model Blockchain Based on zk-SNARKs. IEEE Trans. Dependable Secur. Comput. 2022, 19, 1446–1463. [Google Scholar] [CrossRef]
- Hu, X.; Zhou, W.; Yin, J.; Cheng, G.; Yan, S.; Wu, H. Towards verifiable and privacy-preserving account model on a consortium blockchain based on zk-SNARKs. Peer-to-Peer Netw. Appl. 2023, 16, 1834–1851. [Google Scholar] [CrossRef]
- Oude Roelink, B.; El-Hajj, M.; Sarmah, D. Systematic review: Comparing zk-SNARK, zk-STARK, and bulletproof protocols for privacy-preserving authentication. Secur. Priv. 2024, 7, 101–115. [Google Scholar] [CrossRef]
- Lavaur, T.; Detchart, J.; Lacan, J.; Chanel, C.P. Modular zk-rollup on-demand. J. Netw. Comput. Appl. 2023, 217, 103678. [Google Scholar] [CrossRef]
- Metere, R.; Dong, C. Automated Cryptographic Analysis of the Pedersen Commitment Scheme. arXiv 2017, arXiv:1705.05897. [Google Scholar]
- Franck, C.; Großschädl, J.; Banerjee, S.; Bouzefrane, S.; Boumerdassi, S.; Renault, E.; Sailhan, F. Efficient Implementation of Pedersen Commitments Using Twisted Edwards Curves. In Mobile, Secure, and Programmable Networking; Springer International Publishing AG: Cham, Switzerland, 2017; Volume 10566, pp. 1–17. [Google Scholar]
- Mallare, D.; Dani, N.; Bonaci, T. Decentralized identifiers. IEEE Potentials 2023, 42, 18–24. [Google Scholar] [CrossRef]
- Yan, Z.; Zhao, X.; Liu, Y.A.; Luo, X.R. Blockchain-driven decentralized identity management: An interdisciplinary review and research agenda. Inf. Manag. 2024, 61, 104026. [Google Scholar] [CrossRef]
- Miyahara, D.; Robert, L.; Lafourcade, P.; Mizuki, T. ZKP Protocols for Usowan, Herugolf, and Five Cells. Tsinghua Sci. Technol. 2024, 29, 1651–1666. [Google Scholar] [CrossRef]
- Das, S.; Acharjee, P.; Bhattacharya, A. Charging Scheduling of Electric Vehicle Incorporating Grid-to-Vehicle and Vehicle-to-Grid Technology Considering in Smart Grid. IEEE Trans. Ind. Appl. 2021, 57, 1688–1702. [Google Scholar] [CrossRef]
- van der Kam, M.; Bekkers, R. Mobility in the Smart Grid: Roaming Protocols for EV Charging. IEEE Trans. Smart Grid 2023, 14, 810–822. [Google Scholar] [CrossRef]
- Zhong, Y.; Zhou, M.; Li, J.; Chen, J.; Liu, Y.; Zhao, Y.; Hu, M.; Islam, S.H.; Islam, S.H. Distributed Blockchain-Based Authentication and Authorization Protocol for Smart Grid. Wirel. Commun. Mob. Comput. 2021, 2021, 5560621. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Wazid, M.; Conti, M. Provably Secure Authenticated Key Agreement Scheme for Smart Grid. IEEE Trans. Smart Grid 2018, 9, 1900–1910. [Google Scholar] [CrossRef]
- Tsai, J.L.; Lo, N.W. Secure Anonymous Key Distribution Scheme for Smart Grid. IEEE Trans. Smart Grid 2016, 7, 906–914. [Google Scholar] [CrossRef]
- Prateek, K.; Das, M.; Surve, S.; Maity, S.; Amin, R. Q-Secure-P2-SMA: Quantum-Secure Privacy- Preserving Smart Meter Authentication for Unbreakable Security in Smart Grid. IEEE Trans. Netw. Serv. Manag. 2024, 21, 5149–5163. [Google Scholar] [CrossRef]
- De Caro, A.; Iovino, V. jPBC: Java pairing based cryptography. In Proceedings of the 2011 IEEE Symposium on Computers and Communications (ISCC), Kerkyra, Greece, 28 June–1 July 2011; pp. 850–855. [Google Scholar]
- Lee, S.; Kim, M.; Lee, J.; Hsu, R.H.; Kim, M.S.; Quek, T.Q.S. Facing to Latency of Hyperledger Fabric for Blockchain-Enabled IoT: Modeling and Analysis. IEEE Netw. 2023, 37, 232–239. [Google Scholar] [CrossRef]
- Mitra, S. Infineon Considers Entering India’s Chip Market, Says IT Minister; Electron Bazaar; Athena Information Solutions Pvt. Ltd.: New Delhi, India, 2024. [Google Scholar]
- Yin, J.; Xiao, Y.; Pei, Q.; Ju, Y.; Liu, L.; Xiao, M.; Wu, C. SmartDID: A Novel Privacy-Preserving Identity Based on Blockchain for IoT. IEEE Internet Things J. 2023, 10, 6718–6732. [Google Scholar] [CrossRef]
- Maram, D.; Malvai, H.; Zhang, F.; Jean-Louis, N.; Frolov, A.; Kell, T.; Lobban, T.; Moy, C.; Juels, A.; Miller, A. CanDID: Can-Do Decentralized Identity with Legacy Compatibility, Sybil-Resistance, and Accountability. In Proceedings of the 2021 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 24–27 May 2021; pp. 1348–1366. [Google Scholar]


| Notations | Meaning | Notations | Meaning |
|---|---|---|---|
| Vehicle authentication data | r | Random nonce for Pedersen commitment | |
| Vehicle registration request | Vehicle’s public and private key | ||
| Vehicle’s master public and private key | Smart grid’s signature on credential | ||
| C | Pedersen commitment | Vehicle user’s public and private key | |
| Response for nonce in ZKP | Vehicle’s verifiable credential | ||
| H | Hash function | R | Intermediate value in ZKP for masterID |
| Two random generators of | Response for masterID in ZKP | ||
| Finite field of order q | Response for nonce in ZKP | ||
| A cyclic group of order q | DID | Distributed identifier, | |
| Sanctioned blacklist | Timestamp, (valid time set) |
| Schemes | [32] | [33] | [34] | [35] | SGDID | |
|---|---|---|---|---|---|---|
| Security Features | ||||||
| Sybil attack resistance | ✓ | ✓ | ✓ | ✓ | ✓ | |
| Unlinkability | ✓ | ✓ | × | × | ✓ | |
| Conditional anonymity | ✓ | ✓ | × | ✓ | ✓ | |
| Unforgeability | × | ✓ | ✓ | ✓ | ✓ | |
| Privacy preservation | ✓ | ✓ | ✓ | ✓ | ✓ | |
| Auditability | ✓ | × | × | ✓ | ✓ | |
| Performance | CanDID | SmartDID | SGDID |
|---|---|---|---|
| Credentials generation | 3.97 s | 0.031 s | 0.028 s |
| Proof generation | 1.2 s | 0.29 s | 0.41 s |
| Proof time | 0.006 s | 0.023 s | 0.016 s |
| Identity revocation | 1.5 s | N/A | 0.057 s |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tang, B.; Yao, S.; Su, L.; Xu, F. SGDID: A Privacy-Enhanced Supervised Distributed Identity Model for Smart Grid and Electric Vehicle Integration. Symmetry 2025, 17, 253. https://doi.org/10.3390/sym17020253
Tang B, Yao S, Su L, Xu F. SGDID: A Privacy-Enhanced Supervised Distributed Identity Model for Smart Grid and Electric Vehicle Integration. Symmetry. 2025; 17(2):253. https://doi.org/10.3390/sym17020253
Chicago/Turabian StyleTang, Bo, Shixiong Yao, Ling Su, and Fuxiang Xu. 2025. "SGDID: A Privacy-Enhanced Supervised Distributed Identity Model for Smart Grid and Electric Vehicle Integration" Symmetry 17, no. 2: 253. https://doi.org/10.3390/sym17020253
APA StyleTang, B., Yao, S., Su, L., & Xu, F. (2025). SGDID: A Privacy-Enhanced Supervised Distributed Identity Model for Smart Grid and Electric Vehicle Integration. Symmetry, 17(2), 253. https://doi.org/10.3390/sym17020253






