Abstract
Mersenne prime numbers, expressed in the form (2n − 1), have long captivated researchers due to their unique properties. The presented work aims to develop a symmetric cryptographic algorithm using a novel technique based on the logical properties of Mersenne primes. Existing encryption algorithms exhibit certain challenges, such as scalability and design complexity. The proposed novel modular multiplicative inverse property over Mersenne primes simplifies the encryption/decryption process. The simplification is achieved by computing the multiplicative inverse using cyclic bit shift operation. The proposed image encryption/decryption scheme involves a series of exor, complement, bit shift, and modular multiplicative inversion operations. The image is segmented into blocks of 521 bits. Each of these blocks is encrypted using a 521-bit key, ensuring high entropy and low predictability. The inclusion of cyclic bit shifting and XOR operations in the encryption/decryption process enhances the diffusion properties and resistance against attacks. This approach was experimentally proven to secure the image data while preserving the image structure. The experimental results demonstrate significant improvements in security metrics, including key sensitivity and correlation coefficients, confirming the technique’s effectiveness against cryptographic attacks. Overall, this method offers a scalable and secure solution for encrypting high-resolution digital images without compromising computational efficiency.
1. Introduction
The exploration of Mersenne primes began anonymously in the 14th century. A significant milestone was achieved in 1588 by Cataldi, who identified M17 and M19. This pursuit continued with contributions from renowned mathematicians and groups, such as Euler, R. E. Powers, Robinson, Gillies, Slowinski, and more recently, the internet-based distributed computing project GIMPS (the Great Internet Mersenne Prime Search) [1,2,3,4]. Mersenne numbers, which honor the French monk Marin Mersenne, follow the formula Mn = 2n− 1, where n is a non-negative integer without a primality requirement. A Mersenne number becomes prime, called a Mersenne prime, when both Mn and its exponent n are prime. However, this is not always the case. For example, although n = 11 is prime, the corresponding Mersenne number Mn = 2047 is not. As of March 2023, the greatest prime number currently known is 282,589,933 − 1, which is a Mersenne prime with 24,862,048 digits. Notably, 12 of the 20 biggest identified primes happen to be Mersenne primes, with a total of 51 that are known as of October 2022. The Mersenne prime 2521 − 1 is recommended by the National Institute of Standards and Technology (NIST) for application in elliptic curve cryptography (ECC). NIST primes [5] are widely utilized in cryptographic systems, supporting technologies like high-speed ECC processors [6] and pipelined modular multipliers [7].
Mersenne primes, due to their large size and unique mathematical properties, have been extensively studied and applied in various cryptographic schemes. These primes are particularly valued for their efficient computation in modular arithmetic, which is crucial for generating secure cryptographic keys and parameters. Such applications are essential for ensuring confidentiality, integrity, and authenticity in communication systems. Cryptographic schemes based on Mersenne primes are frequently discussed in the literature [8,9,10,11,12,13,14,15]. They are used explicitly in algorithms for encryption and decryption, employed as Mersenne Twisters for key generation, and utilized in hash functions and other cryptographic primitives. For example, the RSA (Rivest–Shamir–Adleman) algorithm [8] leverages Mersenne primes to enhance security by introducing additional complexity and resistance against attacks.
However, despite the extensive research on Mersenne primes, a novel property has been identified that further expands their applicability in cryptography. The proposed symmetric cryptographic algorithm involves repeated computation of the multiplicative inverse. This novel property simplifies the repeated computation of the multiplicative inverse using cyclic bit shift operations. Building on this new property, a novel technique for encrypting images has been proposed. Traditional cryptographic algorithms like AES, Blowfish, and RSA are highly effective in text data but often struggle with image encryption due to the spatial correlation of image pixels and the associated computational complexities [14,16,17,18]. This has prompted the development of other image encryption techniques, such as chaotic systems and transform-based methods [17,19]. Chaotic systems leverage the sensitive dependence on the initial conditions to achieve high security. Due to the parameter sensitivity, precise key management is necessary for properly recovering the encrypted image. Transform-based techniques, like the Discrete Cosine Transform (DCT) and the Discrete Wavelet Transform (DWT), offer advantages in data compression and redundancy reduction but may introduce significant computational overhead. By keeping all the latest advancements, including the aforementioned, the proposed image encryption algorithm offers a less sophisticated yet effective cryptographic technique. This novel technique utilizing our newly identified multiplicative inverse property provides a streamlined approach that does not employ s-boxes or any other complex building components but relies on simple logical operations. The encryption and decryption use the same operational blocks in reverse order, which makes the hardware design of the entire cryptosystem spatially efficient.
The contribution of this work is primarily the identification of the modular multiplicative inverse property of Mersenne primes followed by the development of an efficient and scalable cryptographic technique for big-data encryption. The features of the proposed method can be outlined as follows: Firstly, this novel technique does not involve an extremely complicated design phase as seen in chaos-based encryption schemes. It utilizes a symmetric block encryption scheme with a secret key in the cipher block chaining mode. Secondly, diffusion and confusion are achieved through logical operations such as XOR, circular shift, negation, and modular inversion. In contrast, most of the promising schemes mentioned earlier use techniques such as cellular automata, DNA sequencing, and S-boxes to achieve confusion and diffusion. Thirdly, our technique does not employ S-boxes, thereby reducing the design complexity and computational cost. It is well-known that working with S-boxes in cryptographic algorithms is challenging due to the difficulty in designing them to meet stringent cryptographic criteria, such as high non-linearity and the avalanche effect. A poorly designed S-box can make the system more vulnerable to attacks. Finally, the designed encryption method offers excellent scalability and spatial efficiency. This Mersenne prime-based image encryption technique works well with images of any size and type (both color and grayscale). The analysis shows that this method offers a large key space with competitive values for the statistical and quantitative performance measures.
In summary, the contributions of this research work can be listed as follows.
- This work primarily contributes to the identification of a novel modular multiplicative inverse property of Mersenne primes.
- An image encryption technique using this property is proposed that employs symmetric block processing with a secret key in the cipher block chaining mode.
- Shannon’s confusion and diffusion are achieved using simple logic operations such as XOR, circular shift, negation, and modular inversion, rather than the complicated techniques used in other popular algorithms.
- The proposed encryption technique does not employ S-boxes, which in turn reduces the design complexity and computational complexity introduced by them.
- This work offers a highly scalable and spatially efficient technique for encryption, which can be further extended to the efficient hardware implementation of a secure cryptosystem with optimization.
The paper is organized in the following manner: Section 2 embarks on summarizing the existing literature on the properties of Mersenne primes, inversion algorithms, and the fundamentals of image encryption algorithms. Section 3 includes the statement and demonstration of the novel multiplicative inverse property of Mersenne primes. Section 4 explains the image encryption algorithm using the novel property. Section 5 encompasses the simulation outcomes and their evaluation, and Section 6 delivers the conclusion and outlines the potential future research directions.
2. Related Works
Mersenne primes exhibit several properties that are highly relevant to the field of cryptography. Numerous congruence and symmetry properties have been reported in the literature. This section provides a summary of certain cryptographic properties associated with Mersenne primes. One important congruence property of Mersenne primes, proposed by Euler, states that for a prime n > 2, any prime factor of Mn = 2n − 1 must satisfy both the conditions of being congruent to 1 (mod n) and ±1 (mod 8) [20]. In [21], some families of Toeplitz–Hessenberg determinants and permanents, whose elements are Mersenne primes, are studied, and new identities for calculating these determinants and permanents are discovered. Additionally, special sets of moduli are constructed in [22], drawing on the properties of strict Mersenne primes, Mersenne composites, Quasi–Mersenne primes, and Loose Mersenne primes to accelerate the modular reduction phase of large integer modular multiplication operations. A bit-wise property of Mersenne primes, based on the complement operation, is presented in [23]. As mentioned in the introduction, Mersenne prime numbers with these special properties are effectively used in cryptography. For example, [8] proposes a modified version of the RSA algorithm that uses a fixed Mersenne prime number in the factoring problem for medical ultrasound imaging instrumentation, demonstrating improved encryption efficiency. In another study [9], a new public key cryptosystem is developed that relies upon the computational intractability of a Mersenne prime number problem based on its Hamming weight properties. Several papers have also demonstrated the use of New Mersenne Number Transforms (NMNTs) [10,11] for encryption and hashing purposes. These transforms are proven to have powerful data-diffusion capabilities. Additionally, Mersenne matrices and Hadamard matrices [12] have been effectively used in digital image processing. From the literature, it is evident that Mersenne primes possess remarkable properties that can be integrated into cryptography without adding excessive operational complexity. In the proposed symmetric cryptographic algorithm, the multiplicative inverse property over Mersenne primes is used to simplify the encryption/decryption process. It is well known that modular inversion is one of the most computationally demanding cryptographic operations. To address this, a new circular shift property of Mersenne primes has been identified to simplify the repeated computation of multiplicative inverses—a concept not previously explored in the literature. This novel property is utilized to develop a symmetric block encryption technique that has been effectively applied in image encryption.
Since the core operation underlying the proposed encryption/decryption technique is modular multiplicative inversion, a discussion on the highly regarded inversion algorithms in the existing literature is warranted. The majority of multiplicative inversion algorithms are derived from the greatest common divisor (GCD) approach, specifically utilizing the Extended Euclidean Algorithm (EEA) [23,24,25,26,27]. However, algorithms based on modular multiplication (MM) [25,27] and Montgomery inversion [25] are also frequently used. Because shifting operations do not incur any hardware cost, EEA variants based on shifting operations have become popular. The right-shift (RS) modular inverse algorithm by Penk and the left-shift (LS) modular inverse algorithm by Lórencz are two widely used binary-shifting modular inversion algorithms [24,25,26,27]. In [24], a performance comparison of RS, LS, and EEA was conducted, and the simulation results showed that RS outperformed both with respect to both area and processing speed. The proposed block encryption technique based on the multiplicative inverse property of Mersenne primes uses the RS binary inversion algorithm once and is later followed by a loop of inversions that are computed by the novel property. Since we have discussed the motivation for the identification of the new property and the selection of the core component of the algorithm, it is worth gaining insight on the current state of art of image encryption.
As noted in the introduction, different techniques have been suggested for encrypting image data beyond conventional schemes. Image encryption algorithms are generally classified into symmetric key algorithms, asymmetric key algorithms, chaotic encryption schemes, transform-based encryption algorithms, visual cryptography, and hybrid encryption schemes. Popular conventional cryptographic algorithms like DES, Blowfish, AES, and RC5, along with image encryption methods leveraging chaotic functions and mixed transform logistic maps, have been evaluated for performance with different-sized grayscale images in [28]. The results showed that chaotic schemes offer superior scrambling effects, histogram analysis, and correlation coefficient analysis compared with conventional schemes not specifically designed for images. However, AES, RC4, and chaotic schemes were found to have a lower time complexity. Kumar et al. [19] further classify image encryption methods into optical, spatial, transform, and compressive sensing domains. In the spatial domain, techniques like chaotic maps and transform-based encryption operate using manipulating pixel configurations. The core operations for image encryption, similar to traditional cryptography, revolve around permutation and diffusion. Various permutation algorithms such as Arnold-based, Baker-based, cyclic shift, and sort-based, reorder the pixels at different levels like bit-level, DNA-level, or pixel-level [29]. Conversely, diffusion algorithms disperse pixel values to enhance the image security.
Several studies explore advanced image encryption techniques incorporating chaotic systems and DNA encoding. For instance, an image encryption algorithm employing a memristive hyperchaotic system, cellular automata, and DNA sequence operations is presented in [16], utilizing sub-block image diffusion and dynamic DNA encoding to enhance security. Simulations using grayscale images showed an excellent performance, with a key space of 2128, though the correlation coefficients of the encrypted images were slightly higher. A multi-channel image encryption algorithm that leverages pixel reorganization and hyperchaotic maps (MIEA-PRHM) is proposed in [30]. This novel scheme employs two hyperchaotic maps, 2D-SCPM and 2D-ELMM, to jointly generate chaotic sequences and achieves a key space of 2412. Another chaotic image encryption scheme based on the 2D simplified quadratic polynomial hyperchaotic map (2D-SQPM) and pixel fusion strategy is proposed in [31]. This advanced scheme successfully addresses the limitations of other existing chaotic methods, including subpar performance and design flaws, while offering a key space of 2200. Another method uses memristive chaotic systems, elementary cellular automata, and compressive sensing [17], where the SHA-512 hash value of the original image determines the zigzag confusion parameters. This approach effectively reduces the energy required for data transmission while maintaining a key space of 2232. A chaos-based private key block encryption scheme employing the Mersenne Twister with DNA encoding demonstrates high computational efficiency and sensitivity [13]. Additionally, a five-stage color image encryption scheme using Arnold’s Cat map, the Mersenne Twister, Langton’s ant, and S-boxes [14] offers a vast key space and resilience against various attacks. Another color image encryption algorithm for medical applications utilizes Fibonacci Q-matrices, Galois field-based S-boxes, and the hyperchaotic Memristive Coupled Neural Network Model (MCNNM), contributing to a large key space and a high encryption rate, despite some computational costs and overheads [15]. A recent addition to the chaotic image encryption schemes is based on the multi-wing butterfly shape chaotic attractors generated by a Memristive Tabu Learning Neuron (MTLN) model [32]. This scheme, based on the dynamic characteristics of MTLN, performs pixel substitution–scrambling–substitution using chaotic sequences to enhance the security and gives a key space of 1042. Another image encryption algorithm based on plane-level image filtering and discrete logarithmic transformation (IEA-IF-DLT) is proposed in [33]. This scheme provides a key space of 2260 and demonstrates enhanced efficiency by minimizing the overhead associated with repeated chaotic sequence generation while strengthening the resistance to cryptanalytic attacks.
Considering the emphasis on developing advanced image encryption schemes, addressing the importance of cryptanalysis is essential. Cryptanalysis plays a key role in identifying the vulnerabilities within encryption systems, such as susceptibility to brute-force and implementation attacks. Numerous researchers have focused on analyzing recent image encryption techniques, uncovering weaknesses in their designs and proposing enhancements. These efforts aim to guide the development of more robust and secure encryption methods while motivating the creation of flaw-resistant systems. Cryptanalytic attacks make use of the algorithm characteristics to break the cipher using available information such as known plaintext–ciphertext pairs, key, or cipher estimates. In [34], an improved color image cipher (ICIC-DNA), which incorporates multiple deoxyribonucleic acid (DNA) sequence operations with DNA synthetic images and chaos, was cryptanalyzed under a chosen-plaintext attack, revealing vulnerabilities such as equivalent chaotic key streams, smaller operational units for DNA encoding and decoding, and a substitution–permutation network that was susceptible to divide-and-conquer strategies. Similarly, a Feistel network-based image encryption scheme with dynamic DNA encoding was cryptanalyzed in [35], and a 2D logistic-adjusted sine map-based image encryption scheme was analyzed in [36], both under chosen-plaintext attacks. Common weaknesses identified across these studies included flaws in secret key generation, chaotic parameter or matrix generation, permutation and diffusion processes, and the presence of equivalent chaotic key streams. To address these issues, the authors proposed enhancements to the encryption schemes and recommended general practices such as basing encryption security on robust processes and the anonymity of the secret key rather than the key design, avoiding unknown parameters and equivalent sub-key streams, and eliminating the redundant steps in the encryption process.
In summary, numerous promising techniques have been presented in the literature for image encryption, offering high levels of security and efficiency. Cryptosystems utilizing the Mersenne Twister have notably expanded the key space and demonstrated strong statistical and quantitative performance metrics. However, because the proposed technique is built on a fundamentally different concept than these existing schemes, a direct comparison may not be entirely appropriate. Nonetheless, the proposed image encryption method, with its comparable performance metrics, simpler methodology, and resilience to attacks, could be considered a promising candidate among the current approaches.
3. The Novel Modular Multiplicative Inverse Property of Mersenne Primes
Statement: For any integer x in the interval 1 ≤ x ≤ p − 1, where p is a Mersenne prime number, the multiplicative inverse of x cyclically left-shifted (or right-shifted) by 1 bit is the 1-bit cyclically right-shifted (or left-shifted) value of the inverse of x.
Illustration: The multiplicative inverse property of Mersenne primes is illustrated using the Mersenne prime number 25 − 1. Table 1 displays the multiplicative inverse of all the elements in the prime field P31 for the modulus 25 − 1. The multiplicative inverse of any non-zero element in a prime field with modulus n is represented by the relation, x × x−1 ≡ 1 mod (n).

Table 1.
Multiplicative inverses over the Mersenne prime P31.
To demonstrate the property, first consider an integer as x and the modular multiplicative inverse over P31 as x−1. Let us assume that we have a sequence—inverse pair over P31, for example (x1 − x1−1) = ((00001)2 − (00001)2) = ((1)10 − (1)10) over 25 − 1. Starting from this sequence–inverse pair, a consecutive sequence–inverse pair can be easily calculated by applying a one-bit circular shift operation. A 1-bit circular left-shift is performed on the binary sequence to generate the new sequence and a 1-bit circular right-shift is applied on the inverse to obtain the multiplicative inverse of the newly generated binary sequence. In the given sequence–inverse pair, the 1-bit left-shift on the binary sequence x1 = (00001)2 will result in the second binary sequence x2 = (00010)2 = (2)10 and the 1-bit right-shift on the inverse will generate the inverse of the second binary sequence x2 as x2−1 = (10000)2 = (16)10, which is same as calculating 2−1mod 31 = (16)10. Similarly, the binary sequence x can be further left-shifted to a maximum of (n − 1) times until the rollover to the starting sequence occurs and x−1 is right-shifted to obtain the corresponding inverses. So, in the given example, for a Mersenne modulus of (25 − 1), 4 left- and right-shifts are performed to obtain the consecutive sequence–inverse pairs. An illustrative diagram of this property for the starting sequence of 00011 is given in Figure 1. The modular multiplicative inverses over the Mersenne prime P31 generated using the circular shift property are given in Table 2.
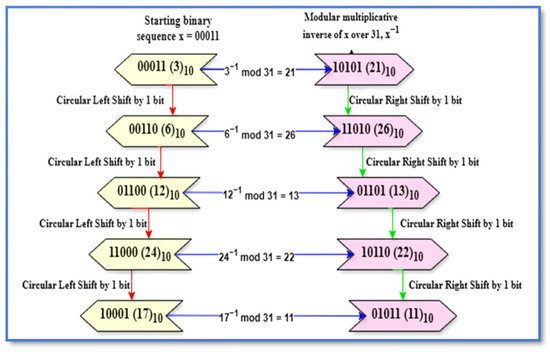
Figure 1.
Illustrative diagram of the modular inverse property of the Mersenne prime modulus 25 − 1.

Table 2.
Multiplicative inverses over the Mersenne prime P31(25 − 1) using binary circular shift.
The binary sequence notated as ‘start’ in Table 2 can be any of the 30 combinations. With a Mersenne prime modulus of Mn, a set of (n − 1) binary sequence–inverse pairs can be generated from a single binary sequence–inverse pair and any x − x−1 can be used to generate any another x − x−1 pair in the same field. This multiplicative inverse property of the Mersenne prime using circular shifts is scalable to any other Mersenne prime modulus. Table 3 and Table 4 justify the property for the Mersenne prime moduli (27 − 1) and (213 − 1), respectively.

Table 3.
Multiplicative inverses over the Mersenne prime P127(27 − 1) using binary circular shift (for 4 starting binary sequences out of 18 available).

Table 4.
Multiplicative inverses over the Mersenne prime P8191(213 − 1) using binary circular shift (for 2 starting binary sequences out of 630 available).
In the proposed encryption/decryption scheme, only the initial inverse calculation relies on conventional modular inversion algorithms, whereas subsequent inversions can be efficiently executed through cyclic bit shift operations. Given that shifting operations do not impose hardware overhead, integrating this innovative multiplicative inverse property into cryptographic algorithms with multiple inversion operations promises the creation of a cryptographic system that is not only more secure and expedient but also highly space-efficient.
Another property that computes the multiplicative inverse over a Mersenne modulus under the same scenario is stated and illustrated in the paper [23]. The property is stated as follows: If x is a number [1 ≤ x ≤ p − 1] and p is a Mersenne prime then the multiplicative inverse of the complement of x is the complement or bit-wise negation of the multiplicative inverse of x. This property of Mersenne primes is also incorporated in the proposed cryptosystem.
4. Image Encryption Technique Using the Proposed Property of Mersenne Primes
Protecting images across vast networks comprising millions of users necessitates the utilization of cryptographic methods or concealment techniques like steganography and watermarking. While the choice between these image-protection approaches hinges on factors such as the desired level of security, the intended application, and the computational complexity, cryptographic algorithms remain the preferred option. Cryptography entails the conversion of data into a secure format and the subsequent retrieval of the original data through authorized means. This novel technique for image encryption incorporates modular multiplicative inverse as a fundamental component, enhancing the resilience of the proposed cryptographic scheme by circumventing the complexities that are inherent in modular arithmetic inversion.
The proposed cryptographic technique embodies a symmetric block encryption/decryption mechanism. Figure 2 represents a flowchart depicting the image encryption process. Algorithm 1 provides a pseudocode for the proposed image encryption technique.
| Algorithm 1 Image encryption algorithm using the proposed technique |
| Input: Plain image P in 521-bit blocks denoted by Pi, i = 1,2,3… B, B = (size of P in bits)/521, Secret key K in a 521-bit block, Last_Sequence = LS. |
| 1: for (i = 1, i ≤ B, i++) 2: { 3: if i = 1, LS = 0; 4: else, LS = Ci−1; 5: S1 = XOR (Pi, K, LS); 6: S2 = S1−1 mod (2521 − 1); 7: Assign L1 = S1; 8: L2 = S2; 9: for j in 1 to 52 10: { 11: Control bit, CBIT = ((j × 10) % 521)th bit of K; 12: if (CBIT = 0) 13: { 14: L1 = bit wise complement (L1); 15: L2 = bit wise complement (L2); 16: } 17: else 18: { 19: L1 = Circular_Left_shift (L1,1); 20: L2 = Circular_Right_shift (L2,1); 17: } 18: } 19: Ci = L2; 20: } 21: C = Ci, Ci+1,…, CB; |
| Output: Cipher image C in binary generated. |
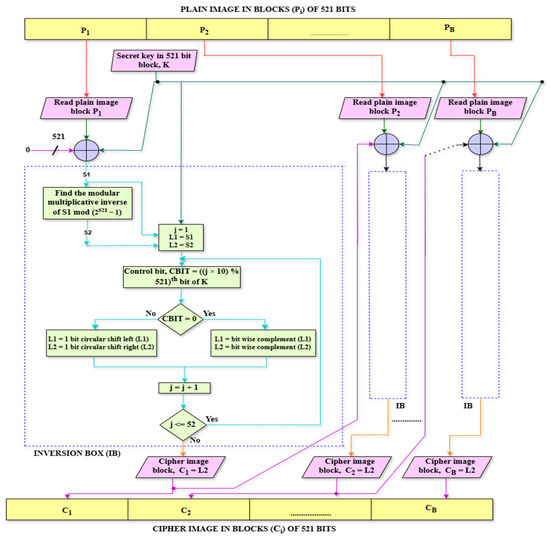
Figure 2.
Flowchart of the proposed image encryption technique.
As depicted, the encryption procedure initiates with the conversion of the original data into binary format. Being a block encryption system, both the data and the key are configured to a block size of 521 bits. This choice stems from the cryptographic scheme operating within a prime field, specifically utilizing a Mersenne prime modulus of 2521 − 1. Larger block sizes are favored as they bolster the security of the overall cryptosystem.
Choosing a 521-bit key size significantly expands the key space, thereby making the system less vulnerable to brute force attacks. For testing the proposed method, a 521-bit key is generated using a cryptographically secure pseudo-random number generator (CSPRNG) through Python’s ‘secrets’ module. Unlike conventional PRNGs, CSPRNGs produce highly unpredictable random numbers. The key generation process can be further enhanced by utilizing methods such as the Mersenne Twister, True Random Number Generators (TRNGs), or cryptographic libraries like OpenSSL and Python’s Cryptography. Since this work aims only to present a new technique for image encryption rather than a full cryptosystem, the key generation and management details are limited to the information provided above.
To prepare the original image for encryption, it undergoes conversion to hexadecimal values then to binary values, enabling the algorithm to operate effectively. The exclusive OR block (EXOR) is used as the initial logic block in the proposed algorithm because its forward and reverse operations do not require different designs and being a keyed operation, it makes the algorithm cryptographically secure at the top level. Since the algorithm operates in 521-bit blocks, the input image in binary form is compartmentalized as blocks of 521 bits each and if the size of the last block is less than 521 bits, additional padding may be performed. In this stage, every 521-bit block of the input data is xored with the 521-bit key block and the cipher block from the previous round except for the first plain image data block, and the output S1 is passed on to the next stage. Performing bit-wise xor on the current plain image block, the secret key and the previous cipher box diffuse the plain image block effectively.
The next stage computes the modular multiplicative inverse of S1 for the Mersenne prime modulus of 2521 − 1 using any of the conventional inversion algorithms, and the result is indicated as S2 in the pseudo-code. In order to favor a hardware-friendly cryptosystem, it is preferable to adopt an inversion algorithm that utilizes less intricate modular arithmetic components. Due to its supremacy to other EEA variants as mentioned in Section 2, the RS algorithm is chosen for experimentation.
For added security in the cryptographic algorithm, an inversion loop is devised to iterate j times, where j is selected to bolster the security without sacrificing the execution speed. The iterative process utilizes the inverse value derived from the prior stage via traditional inversion methods and iteratively calculates its multiplicative inverse using the novel modular multiplicative inverse property of Mersenne primes. This iterative loop performs modular inversion on the binary sequence based on the specific bits chosen from the key stream, bypassing the need for the repetitive execution of complex conventional inversion algorithms. The efficiency and simplicity of the inversion computation within the loop are facilitated by leveraging the complement and cyclic shifting properties of the Mersenne prime modulus 2521 − 1.
To ensure optimal loop performance, the iteration count is carefully selected, balancing between too few and too many iterations, and is set at 52. Given that the key block consists of 521 bits, every 10th bit serves as the control bit for the inversion loop, resulting in 52 iterations. This iteration count is a flexible parameter that should be selected to balance the trade-off between computational efficiency and security.
Denoting every 10th bit as CBIT, it is important to note that both the input (designated as L1) and output (designated as L2) of the inversion stage undergo iterations to determine the multiplicative inverse using the properties of Mersenne primes. The operation of the loop unfolds as follows: when the control bit equals to logic 0, both the loop inputs undergo one’s complement operation or bitwise negation. Conversely, when the control bit equals logic 1, L1 is cyclically shifted left by one bit, while L2 is cyclically shifted right by one bit. In either scenario, L2 emerges as the modular multiplicative inverse of L1 for the Mersenne prime modulus of 2521 − 1. After 52 iterations, L2 represents the encrypted rendition of the original data, or the cipher. By harnessing the unique property of Mersenne primes, the inversion loop iteratively computes the modular multiplicative inverse 52 times, obviating the need for executing the complex conventional inversion algorithm 52 times. After all the plain image blocks are processed, the cipher image is generated. The decryption process, which restores the source image from the encrypted version, is the reverse of the encryption process. Algorithm 2 represents the pseudo code for the proposed image decryption.
Features of the Proposed Encryption Technique
The proposed encryption technique, utilizing the novel modular multiplicative inverse property of Mersenne primes, offers an efficient and unconventional way to secure data. The encryption scheme relies on a few simple operations: XOR, modular multiplicative inverse, bit-wise negation, and binary circular shifting.
The exclusive OR (XOR) operation is used as the initial logic block in the algorithm because its forward and reverse operations are identical, eliminating the need for separate designs. As a keyed operation, XOR adds a layer of cryptographic security at the top level. Since XOR is an involutory function, the same key can be utilized for both encryption and decryption. Unlike other logical operations, XOR can easily randomize the biased input, preventing any information leakage that could be exploited in statistical cryptanalysis. Moreover, XOR is computationally inexpensive, faster to execute, and creates confusion by transforming the plaintext statistics in a complex and non-linear manner based on the key.
| Algorithm 2 Image decryption algorithm using the proposed technique |
| Input: Cipher image C in 521-bit blocks denoted by Ci, i = 1, 2, 3… B, B = (size of C in bits)/521, Secret key K in a 521 bit block, Last_Sequence = LS. |
| 1: for (i = 1, i ≤ B, i++) 2: { 3: S1 = Ci−1 mod (2521 − 1); 4: Assign L1 = Ci; 5: L2 = S1; 6: for j in 1 to 52 7: { 8: Control bit, CBIT = ((j × 10) % 521)th bit of K; 9: if (CBIT = 0) 10: { 11: L1 = bit wise complement (L1); 12: L2 = bit wise complement (L2); 13: } 15: else 16: { 17: L1 = Circular_Left_shift (L1,1); 18: L2 = Circular_Right_shift (L2,1); 19: } 20: } 21: S2 = L2; 22: if i = 1, LS = 0; 23: else, LS = Ci-1; 24: Pi = XOR (S2, K, LS); 25: } 26: P = Pi, Pi+1, …, PB; |
| Output: Plain image P in binary is recovered. |
The next block is the modular multiplicative inversion using conventional algorithms. Since inversion in finite field is a slow operation, an algorithm that utilizes less intricate modular arithmetic components is preferred for this block. The Extended Euclidean Algorithm (EEA) typically involves division operations; however, variations of the EEA that replace division with shifts and addition/subtraction operations, such as the binary right-shift inversion algorithm, are more suitable. These variants leverage the minimal space requirements of shift operations in hardware. Additionally, modular inversion is a non-linear and complex operation, making it a reliable option for encryption.
To enhance the robustness of the proposed cryptographic method, iterations of the fundamental primitives are employed. However, repeatedly running the inversion algorithm in an iterative loop can negatively impact the area/speed trade-offs, even with optimizations in area and time complexity. To mitigate this, the proposed algorithm performs the iterative computation of the modular multiplicative inverse in a prime field without the overhead of repeatedly executing traditional inversion algorithms. Instead, the conventional inversion algorithm is applied only once at the start of the inversion loop. Subsequent inverse computations are handled using the newly identified property in the prime field.
Within the inversion loop, circular shifting and bit-wise negation are employed for computing inverses. Circular shifting, or rotation, is crucial in cryptography because it provides diffusion from higher- to lower-order bits. It is extremely efficient, requiring no additional gates and having no timing dependency. Bit-wise negation is also a time-independent operation, making the algorithm less vulnerable to timing attacks. Together, these operations add both diffusion and confusion to the proposed encryption scheme, as suggested by Shannon’s theory.
5. Results and Discussions
The cryptographic technique presented in this study utilizes the modular multiplicative inverse property of Mersenne primes. The proposed method is employed for encrypting both grayscale and color images of various dimensions, including 128 × 128, 256 × 256, 512 × 512, and 720 × 720. Test images such as Mandrill (Baboon), Cameraman, Pepper, and Boat, in different sizes, are used for this purpose. The image encryption technique is implemented using PyCharm version 2023.3.5 and MATLAB R2015a on a personal computer running Windows 11, powered by a 1.6 GHz Intel Core i5 processor and 8 GB of RAM. Initially, the image file is converted into a binary format to facilitate the subsequent processing steps. The encryption process effectively transforms the original image into a visually scrambled output, demonstrating successful encryption.
5.1. Visual Inspection
Visual assessment [28] is one of the primary methods used to evaluate the effectiveness of the encryption process. Figure 3 shows the grayscale images of Mandrill (256 × 256 and 512 × 512), Cameraman (256 × 256), Pepper (128 × 128 and 512 × 512), and Boat (720 × 720), along with their corresponding encrypted images and histograms. Figure 4 presents the color image of Pepper (256 × 256) alongside its encrypted image and RGB channel-wise histograms. The encrypted images clearly demonstrate that the proposed encryption technique effectively scrambles the plain image pixels, rendering it impossible to discern any details of the original images through visual inspection. It is also visible that the encrypted images get smoother as the image size increases.
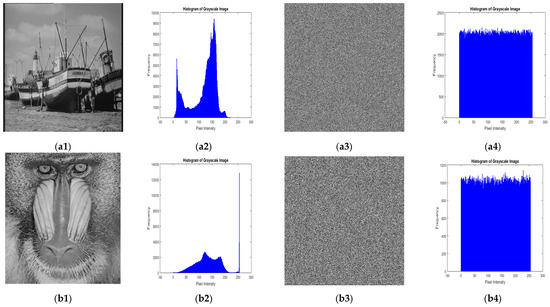
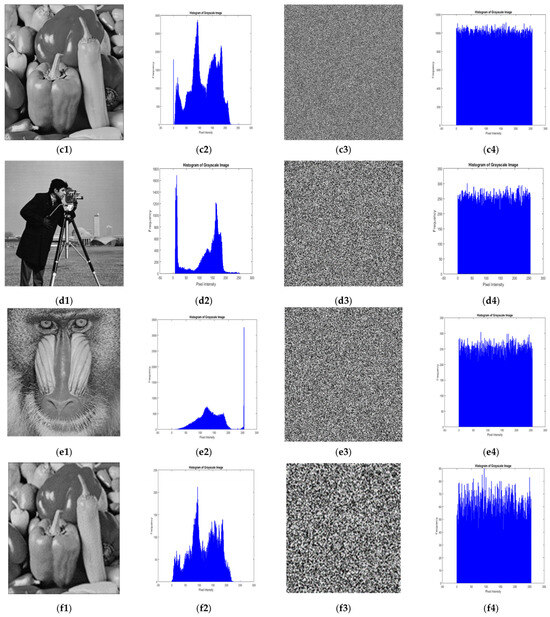
Figure 3.
Plain image, histogram of plain image, encrypted image, and histogram of encrypted image of various grey scale test images of varying sizes: (a1–a4) Boat (720 × 720); (b1–b4) Mandrill Baboon (512 × 512); (c1–c4) Pepper (512 × 512); (d1–d4) Cameraman (256 × 256); (e1–e4) Mandrill Baboon (256 × 256); (f1–f4) Pepper (128 × 128).
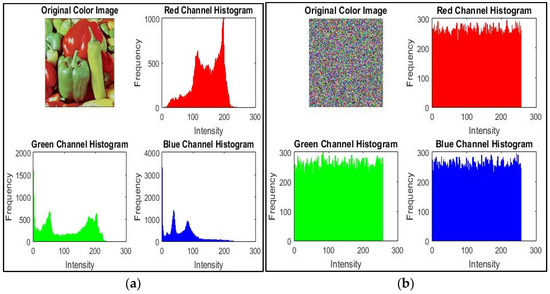
Figure 4.
Pepper color image (256 × 256) with RGB channel-wise histograms: (a) plain image; (b) encrypted image.
5.2. Statstical Analysis
A statistical analysis [19,28,37] is conducted to assess the performance, security, and reliability of the proposed technique for image encryption through the examination of the diverse statistical properties.
5.2.1. Histogram Analysis
The histogram analysis [16,17,19,28,37,38] is employed to evaluate the effectiveness of a cryptographic algorithm in thwarting statistical attacks such as histogram-based cryptanalysis on AES [28]. An image histogram illustrates the spread of pixel intensities across the image and hence a naturally captured image histogram is non-uniform in nature. As the histogram analysis reveals key statistical properties, such as contrast and brightness, the histogram of an image after encryption must be distributed uniformly for effective encryption. Figure 3 displays the histograms of test images post encryption, which are evenly distributed as necessary for randomness and security and are completely distinct from the original image’s histogram. As the image size changes from 128 × 128 to 720 × 720, the cipher image becomes smoother and the histogram becomes more uniform. This proves the linearity and scalability of the proposed techniques with the increasing image size. Figure 4 shows the RGB channel-wise histograms for both the Pepper color image (256 × 256) and its encrypted version, which exhibit a uniform distribution of pixels across all the three-color channels, similar to the histograms of the grayscale images.
In addition to visually assessing the histogram, the variance of a histogram quantifies the evenness of the pixel intensity distribution in the images. Higher values of variance indicate a wider range and lower values indicate a more uniform distribution, which is crucial for secure image encryption. The variance is calculated using Equation (1) as given in [16].
Here, N denotes the total pixel count in the image, n specifies the number of intensity levels (typically 256 for 8-bit grayscale images), and Ii and Ij signify the pixel count at intensity levels i and j, respectively. The variances for the different test images and their corresponding encrypted versions are provided in Table 5. The encrypted images are shown to have considerably lower variances than those of the original images, demonstrating the efficiency and security offered by the proposed technique. It can also be observed that the variances of the encrypted images linearly increase with the image size, which ensures the scalability of the proposed technique.

Table 5.
Histogram variance for different test images.
5.2.2. Correlation Coefficient Analysis
Any naturally captured image exhibits a significant correlation among the adjacent pixels in the horizontal, vertical, and diagonal directions and this correlation is a security measure for cryptographic algorithms known as the correlation coefficient [16,19,28,29,37,38]. The correlation coefficients vary between −1 and 1, with values nearing zero being ideal as they indicate no correlation or linear relationship between adjacent pixels. The correlation coefficient is determined using Equation (2) as provided in [19].
In the Equations (2)–(5), a and b represent the gray scale values of adjacent pixels, E(a) and D(a) (as in Equations (4) and (5)) are the mean and variance, respectively, of the variable a, and N is the pixel count under consideration. Figure 5 illustrates the correlation graph between the adjacent pixels for the Mandrill Baboon (256 × 256) (Figure 3) and its encrypted version, examined along the vertical, horizontal, and diagonal orientations. The correlation coefficients for various test images and their corresponding encrypted versions are provided in Table 6.
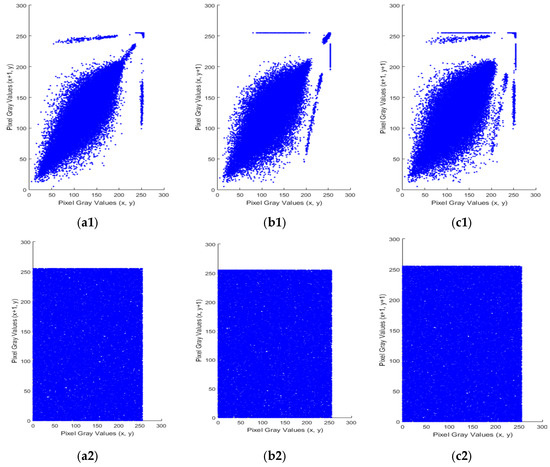
Figure 5.
Correlation plots of Mandrill Baboon (256 × 256): (a1–a2) horizontal correlation of plain and encrypted image; (b1–b2) vertical correlation of plain and encrypted image; (c1–c2) diagonal correlation of plain and encrypted image.

Table 6.
Correlation coefficients between adjacent pixels of both the original and encrypted images.
Figure 6 displays the correlation plots for the Pepper color image (256 × 256) along the RGB channels in all three directions separately. A comparison of the correlation coefficients of the Cameraman image (Figure 3) using the proposed method with various chaos-based image encryption algorithms is provided in Table 7. Table 8 provides the correlation coefficients for the Pepper color image (Figure 4) along the RGB channels using both the proposed and other encryption schemes [39,40,41]. Both the Table 6 and Table 8 highlight that the correlation coefficients of the plain images are nearly 1, suggesting highly connected pixels, while those for the encrypted images are close to zero (all values less than 0.01), indicating little to no correlation. These results suggest that adversaries cannot extract useful data from the encrypted image through statistical attacks. The references used for comparison in Table 7 include [42], which presents a hyperchaotic scheme with a Chebyshev map and SHA-256, achieving a key space of 2339. Reference [43] suggests a hybrid compression–encryption scheme using compressive sensing with a key space of 1034. Reference [44] combines double chaotic maps with SHA-3, resulting in a key space of 1056. Finally, [18] introduces a hyperchaotic system using compressive sensing and SHA-512 with a key space of 2398. The proposed method demonstrates comparable results with the above-mentioned works.
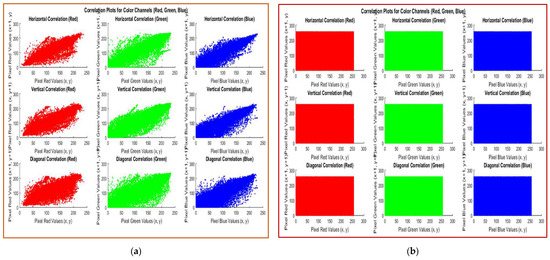
Figure 6.
Correlation plots of color Pepper image (256 × 256) for red, green, and blue channels along horizontal, vertical, and diagonal directions: (a) plain image; (b) encrypted image.

Table 7.
Comparison of the correlation coefficients of the Cameraman image (256 × 256) using the proposed technique versus other image encryption techniques.

Table 8.
Comparison of the correlation coefficients between the adjacent pixels of the color Pepper image (256 × 256) color-channel wise.
In Table 9, a comparison of the average correlation coefficients for the Pepper color image (Figure 4) using the proposed method and other image encryption algorithms is presented. Among these, references [45,46] represent chaotic-based systems, while [14] is based on the Mersenne Twister algorithm.

Table 9.
Comparison of the average correlation coefficients between the adjacent pixels of the color Pepper (256 × 256).
5.3. Security Analysis
5.3.1. Key Space
An effective cryptographic algorithm must feature an extensive key space to make brute-force attacks impractical for adversaries. Ideally, the key space for a cryptographic algorithm should exceed 2100 [16,29].
The proposed algorithm based on the modular multiplicative inverse property of Mersenne primes performs the operation for a Mersenne prime modulus of 2521 − 1. That is, enciphering and deciphering in the prime field employs 521-bit long secret key. Hence, the key space of the proposed cryptographic technique is 2521, far surpassing 2100. This algorithm’s key space is larger than most of the conventional cryptographic algorithms as studied in the survey paper [28].
5.3.2. Key Sensitivity
Key sensitivity [16,17,28,29,37,38] has a great influence on the strength of a cryptographic algorithm, which means that the encryption technique should produce a completely distinct image even with a minimal modification in the secret key. To assess the proposed technique’s key sensitivity, the Mandrill Baboon image (256 × 256) (Figure 3) is first encrypted with the secret key K1, producing the cipher image C1 (Figure 3). Then a new key K2 is generated by altering one bit of the key K1 and the test image is encrypted using K2 to achieve a cipher C2 (Figure 7). Another bit of K1 in a different position is altered to achieve the key K3 and then cipher C3 (Figure 7) is generated. Keys K1, K2, and K3 are 521 bits long and their values used for simulation are as follows.

Figure 7.
Key sensitivity analysis outcomes for the Mandrill Baboon image (256 × 256): (a1) encrypted image C2 by K2; (b1) encrypted image C3 by K3; (a2) difference between image C1 and C2 (C1–C2); (b2) difference between image C1 and C3 (C1–C3).
- K1 = D9 DA 7B EA 1A 31 D8 AB E2 A2 7B 4E 85 5C 5C 5C 50 ED 00 C4 83 88 EA 9B 0F B7 C2 04 C2 C1 2D 39 97 15 7A 6F C8 E4 BB E4 32 C4 0D 35 F2 71 60 92 EB A0 2E 37 98 17 D6 36 A1 44 55 1D F4 9A DE 37 F0 0
- K2 = 59 DA 7B EA 1A 31 D8 AB E2 A2 7B 4E 85 5C 5C 5C 50 ED 00 C4 83 88 EA 9B 0F B7 C2 04 C2 C1 2D 39 97 15 7A 6F C8 E4 BB E4 32 C4 0D 35 F2 71 60 92 EB A0 2E 37 98 17 D6 36 A1 44 55 1D F4 9A DE 37 F0 0
- K3 = D9 9A 7B EA 1A 31 D8 AB E2 A2 7B 4E 85 5C 5C 5C 50 ED 00 C4 83 88 EA 9B 0F B7 C2 04 C2 C1 2D 39 97 15 7A 6F C8 E4 BB E4 32 C4 0D 35 F2 71 60 92 EB A0 2E 37 98 17 D6 36 A1 44 55 1D F4 9A DE 37 F0 0
To find the percentage of pixels changed from C1 to C2 and C1 to C3, the difference between C1, C2 and C1, C3 are found out, as given in Figure 7. From the results, it is found that the pixel change ratio from C1 to C2 is 49.8% and from C1 to C3 is 50.02%, which is a competitive measure with other image encryption algorithms [16,38].
Another way to quantify the extent of the pixel changes in the cipher images due to a single bit change in the secret key is by measuring two parameters: NPCR (number of pixel change rate) and UACI (unified average changing intensity). As shown in Table 10, NPCR values exceed 99% and UACI values are above 33%, which are considered desirable. Table 11 presents a comparison of the NPCR and UACI values for the color Pepper image (256 × 256) across RGB channels with other image encryption algorithms. The proposed algorithm produces comparable results, demonstrating its high sensitivity to the secret key.

Table 10.
Key sensitivity test results for various test images (NPCR and UACI values for a one-bit change in the key).

Table 11.
Comparison of key sensitivity test results for the color Pepper image (256 × 256).
5.4. Quantitative Analysis
5.4.1. Information Entropy
Information entropy [16,19,28,29,37,38] quantifies the amount of information stored. A plain image with an unscrambled and ordered distribution of pixels will result in lower entropy, whereas the image after encryption with a scrambled and random distribution of pixels will have a higher entropy. For a random image with 256 gray levels, the entropy is approximately 8. Information entropy is calculated using Equation (6) as given in [16,29,37].
where p(si) is the symbol probability of (si) and is measured in bits/symbol. Table 12 lists the entropies for various test images and their corresponding encrypted images, with all the values exceeding 7.98. Table 13 compares the entropy of Mandrill (512 × 512) and its encrypted image from the proposed method with the chaotic image encryption schemes [16,38,47] and a parallel diffusion-based algorithm [29]. The proposed method showed superior or comparable results with others. Table 14 presents the comparison of the channel-wise entropy of the color Pepper image with other image encryption algorithms and the results are found to be comparable.

Table 12.
Information entropies for various test images and their encrypted images.

Table 13.
Comparison of the information entropy of the Baboon image (512 × 512) with other image encryption algorithms.

Table 14.
Comparison of the information entropy of the color Pepper image (256 × 256) with other image encryption algorithms along three-color channels.
5.4.2. Mean Squared Error
While visually inspecting both the plain and encrypted images can provide an indication of how well the encryption has worked, a quantitative analysis is required to verify that the encrypted image varies significantly from the original. One measure used for this evaluation is the mean squared error (MSE), which calculates the average squared difference between the corresponding pixels in the original and encrypted images. For an original image O and its encrypted image E of size m × n, Equation (7) is used to calculate MSE as defined in [39,41].
Here, O(i,j) and E(i,j) denote the pixels from the original and encrypted images, respectively, at location (i,j). A higher MSE value indicates a larger difference between the plain and encrypted images. Table 15 presents the MSE values for the different test images.

Table 15.
MSE, PSNR, and SSM values for both the grayscale and color test images.
5.4.3. Peak Signal-to-Noise Ratio
Similar to MSE, the peak signal-to-noise ratio (PSNR) is another measure for evaluating the disparity between the encrypted image and the original image. PSNR indicates the ratio between the highest possible signal power, which is represented by the maximum pixel intensity of the original image and the noise power introduced by the encryption process [14]. It is measured in decibels (dB). The PSNR of encrypted image E relative to the original image O of size m × n is calculated using Equation (8) as defined in [46].
where OMAX is the maximum pixel intensity of the original image O. Since PSNR is derived from the inverse of MSE, a lower value suggests a better encryption performance. Table 15 lists the PSNR values for various test images. Table 16 provides a comparison of the average MSE and PSNR values for the color Pepper image with those of other image encryption algorithms.

Table 16.
Comparison of the MSE and PSNR of the color Pepper image (256 × 256) with other image encryption algorithms.
5.4.4. Structural Similarity Index
The structural similarity index (SSIM) assesses how similar the original image is to the encrypted image. It quantifies the extent of the structural information altered in the original image due to encryption [39]. Ideally, its value should be low, approaching zero. For the original image patch x and encrypted image patch y, SSIM is calculated using Equation (9).
where µx and µy are the means, σx and σy are the variances, and σxy is the covariance of the image patches x and y. Constants C1 and C2 stabilize the division. Table 15 presents the SSIM values for various test images. Additionally, Table 17 compares the SSIM and PSNR of the color Pepper image across three color channels with those of other image encryption algorithms.

Table 17.
Comparison of the PSNR and SSIM of the color Pepper image (256 × 256) with other image encryption algorithms channel-wise.
5.5. Differential Attack Analysis
A robust image encryption method should react to even small modifications in the original image. The NPCR (number of pixel change rate) and UACI (unified average changing intensity) [16,17,19,28,29,37,38] are used to assess how sensitive the algorithm is to pixel changes in the unencrypted image. These metrics aid in evaluating the cryptographic strength of encryption algorithms in the face of differential attacks. The NPCR and UACI are determined using Equations (10) and (11) as given in [28].
where M and N denote the dimensions (rows and columns) of the images, and the delta function δij equals 1 if the two images differ in pixels at position (i,j), and equals 0 if they are the same.
where M and N denote the dimensions of the images, and Pij and Pij′ represent the pixel intensities at position (i,j) in the original image and altered image, respectively. Desirable values for NPCR (%) are around 99, and for UACI (%) they are approximately 33. In the test image Mandrill Baboon (256 × 256), alteration is performed to the pixel at position (2,4) and yielded an NPCR of 99% and a UACI of 33.12%. Similarly, changing the pixel at position (10,12) in the Cameraman image (256 × 256) resulted in NPCR and UACI values of 99.61% and 33.5%, respectively.
5.6. Computational Complexity, Efficiency, and Peak Memory Usage
The computational complexity of a cryptographic algorithm provides insight into how the algorithm scales with an increasing input size, which is crucial for the performance analysis. It is commonly represented using the Big O notation, which denotes the maximum growth rate of the algorithm’s resource consumption. For the proposed algorithm, the computational complexity is O(n), where n is the total number of bits in the image’s binary file. This complexity is comparable with that of other image encryption algorithms [15,39].
The computational efficiency of a cryptographic algorithm encompasses time complexity, scalability, and throughput. The proposed method demonstrates a high scalability and is effectively applicable in big data encryption. In this context, time complexity is measured based on encryption and/or decryption times. The proposed image encryption technique achieves an average block encryption time of 0.00053 s. Table 18 presents the encryption times for various image sizes and compares them with other image encryption schemes. Our technique shows moderate values compared with other advanced encryption schemes. It is well known that the encryption time depends on the speed and capabilities of the machine executing the algorithm, the software implementation—including the programming language and code optimization—and the system load environment, in addition to the cryptographic specifications. Therefore, the encryption time of the proposed method can still be optimized by considering these factors.

Table 18.
Comparison of the encryption time of the proposed algorithm with other image encryption algorithms.
In addition to computational efficiency, memory or resource usage is another indicator of encryption quality. The peak memory usage of the proposed technique was measured using a Python IDE for various image sizes: 1.13 MB for a 128 × 128 image, 4 MB for a 256 × 256 image, 17 MB for a 512 × 512 image, and 38.4 MB for a 720 × 720 image. The linear increase in memory usage suggests that the proposed technique is scalable with the image size. These values are reasonable, though they can be significantly optimized when implemented on an FPGA using HDL.
5.7. Chosen Plaintext Attack Analysis
Certain adversaries exploit the vulnerability of encryption methods by employing pure white and pure black images to render the permutation process ineffective, aiming to extract valuable information. The proposed technique circumvents this threat by eliminating the permutation step, thereby demonstrating a robust performance against such attacks. To assess this resilience, pure black and pure white (Figure 8) images, each sized at 256 × 256, are encrypted using the proposed method. The results, including scrambled cipher images, uniform histograms (Figure 8), entropy values above 7.99, and correlation coefficients close to zero (as shown in Table 19), confirm the robustness and security of the proposed image encryption technique.
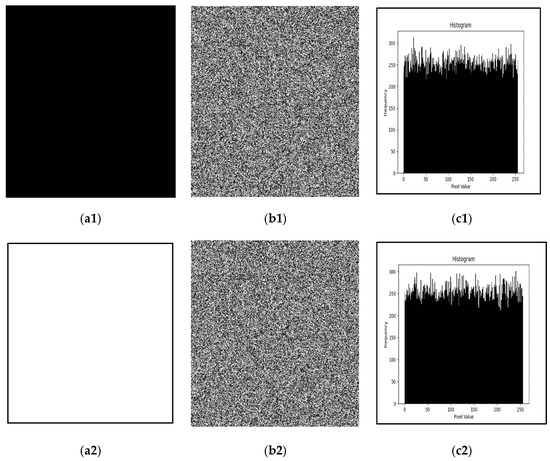
Figure 8.
Known and chosen plaintext attack analysis results with pure black and pure white images: (a1–a2) plain images; (b1–b2) encrypted images; (c1–c2) histograms of encrypted images.

Table 19.
Information entropy and correlation coefficients of pure black and pure white images.
Most of the metrics that evaluate the performance of image encryption algorithms were experimentally found out for the proposed technique. Based on these measures, a general comparison of the proposed technique with AES and chaotic schemes is presented in Table 20.

Table 20.
Comparison of the proposed technique with AES and other chaotic-based encryption schemes.
6. Conclusions and Future Scope
This paper presented a novel Modular multiplicative inverse property of Mersenne primes based on circular shift operation. Inverse calculation using the proposed property was demonstrated for the M5, M7, and M13 moduli. Being a very simple step facilitating one of most complex and expensive modular operations, the multiplicative inverse property of Mersenne primes can favor researchers focusing on secure, fast, and area-efficient cryptographic system design. Later, a new technique for image encryption using this novel property of Mersenne primes is also proposed. The encryption technique is performed on different test images of various sizes. The simulation was performed using MATLAB and PYTHON, and various security metrics have been analyzed. The proposed encryption technique has proven to have desirable values for key sensitivity, correlation coefficient, information entropy, MSE, PSNR, and variance. The values of these metrics are comparable with other image encryption algorithms. Since the algorithm uses simple elements such as xor, shift, and bit-wise negation, the hardware design of the same favors area-efficient implementation. Decryption is the reverse process of what happens in encryption and hence, the design of the entire cryptosystem becomes space-efficient. Furthermore, the visual assessment and histogram analysis of the cipher images show randomness, which is an indication of security. The proposed encryption technique is also shown to withstand known plaintext attacks.
The proposed technique demonstrates high NPCR and UACI values for both key bit changes and changes in plain image pixels, which is desirable for resisting differential attacks. However, there is room for improvement in stabilizing the NPCR and UACI values when the position of the pixel change varies. While the algorithm currently operates at a moderate speed, further optimization could enhance the performance. Future research will focus on refining this encryption method into a robust cryptosystem, including Verilog implementation for power and throughput analysis, and increased resistance to emerging security threats.
Future studies could focus on the following improvements: Since the proposed technique operates on 521-bit blocks of image data, it can be optimized for parallel processing on FPGA, making it feasible for real-time video stream encryption. With further speed optimizations, the algorithm could be adapted for secure network transmission through adaptive encryption. Finally, optimizing the computationally complex modular inversion on FPGA could position this algorithm as a strong candidate for lightweight cryptography.
Author Contributions
Conceptualization, S.M.A. and A.K.M.N.; methodology, S.M.A. and A.K.M.N.; software (simulation), S.M.A.; validation, A.K.M.N.; formal analysis, S.M.A. and A.K.M.N.; writing—original draft preparation, S.M.A.; writing—review and editing, A.K.M.N.; supervision, A.K.M.N. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The original contributions presented in this study are included in the article. The flowchart and pseudocode presented in this article can be used to code the proposed encryption/decryption technique in any high-level programming language, such as Python or MATLAB. Further inquiries can be directed to the authors.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Great Internet Mersenne Prime Search (GIMPS). Available online: https://www.mersenne.org (accessed on 1 April 2022).
- Hoque, A.; Saikia, H.K. On generalized Mersenne prime. SeMA J. 2014, 66, 1–7. [Google Scholar] [CrossRef]
- Kraft, J.; Washington, L. An Introduction to Number Theory with Cryptography; CRC Press: Boca Raton, FL, USA, 2018. [Google Scholar]
- Wojciechowski, J. Mersenne Primes, an Introduction and Overview, 2003, Academia.edu. Available online: https://www.academia.edu/9995980/Mersenne_Primes_An_Introduction_and_Overview (accessed on 22 March 2022).
- FIPS 186-5; Digital Signature Standard (DSS), Federal Information Processing Standards 186-5. National Institute of Standards and Technology: Gaithersburg, MD, USA, 2023.
- Ding, J.; Li, S.; Gu, Z. High-speed ECC processor over NIST prime fields applied with Toom–Cook multiplication. IEEE Trans. Circuits Syst. I Regul. Pap. 2018, 66, 1003–1016. [Google Scholar] [CrossRef]
- Alrimeih, H.; Rakhmatov, D. Pipelined modular multiplier supporting multiple standard prime fields. In Proceedings of the 2014 IEEE 25th International Conference on Application-Specific Systems, Architectures and Processors, Zurich, Switzerland, 18–20 June 2014; pp. 48–56. [Google Scholar]
- Shin, S.-H.; Yoo, W.S.; Choi, H. Development of modified RSA algorithm using fixed Mersenne prime numbers for medical ultrasound imaging instrumentation. Comput. Assist. Surg. 2019, 24, 73–78. [Google Scholar] [CrossRef] [PubMed]
- Aggarwal, D.; Joux, A.; Prakash, A.; Santha, M. A new public-key cryptosystem via Mersenne numbers. In Proceedings of the Advances in Cryptology–CRYPTO 2018: 38th Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2018; pp. 459–482. [Google Scholar]
- Yang, X.B.; Boussakta, S.; Al-Gailani, M.; Ngadiran, R. A new development of cryptosystem using New Mersenne Number Transform. In Proceedings of the 2010 7th International Symposium on Communication Systems, Networks & Digital Signal Processing (CSNDSP 2010), Newcastle Upon Tyne, UK, 21–23 July 2010; pp. 701–705. [Google Scholar]
- Maetouq, A.; Daud, S.M. HMNT: Hash function based on new Mersenne number transform. IEEE Access 2020, 8, 80395–80407. [Google Scholar] [CrossRef]
- Vostrikov, A.; Sergeev, M.; Balonin, N.; Sergeev, A. Use of symmetric Hadamard and Mersenne matrices in digital image processing. Procedia Comput. Sci. 2018, 126, 1054–1061. [Google Scholar] [CrossRef]
- Masood, F.; Boulila, W.; Ahmad, J.; Sankar, S.; Rubaiee, S.; Buchanan, W.J. A novel privacy approach of digital aerial images based on Mersenne twister method with DNA genetic encoding and chaos. Remote Sens. 2020, 12, 1893. [Google Scholar] [CrossRef]
- Alexan, W.; Gabr, M.; El-Aasser, M.; Maher, E.A.; El-Damak, D.; Aboshousha, A. Anteater: When Arnold’s cat meets Langton’s ant to encrypt images. IEEE Access 2023, 11, 106249–106276. [Google Scholar] [CrossRef]
- El-Damak, D.; Alexan, W.; Mamdouh, E.; El-Aasser, M.; Fathy, A.; Gabr, M. Fibonacci Q-Matrix, Hyperchaos, and Galois Field (28) for augmented medical image encryption. IEEE Access 2024, 12, 102718–102744. [Google Scholar] [CrossRef]
- Chai, X.; Gan, Z.; Yang, K.; Chen, Y.; Liu, X. An image encryption algorithm based on the memristive hyperchaotic system, cellular automata and DNA sequence operations. Signal Process. Image Commun. 2017, 52, 6–19. [Google Scholar] [CrossRef]
- Chai, X.; Zheng, X.; Gan, Z.; Han, D.; Chen, Y. An image encryption algorithm based on chaotic system and compressive sensing. Signal Process. 2018, 148, 124–144. [Google Scholar] [CrossRef]
- Xu, Q.; Sun, K.; He, S.; Zhu, C. An effective image encryption algorithm based on compressive sensing and 2D-SLIM. Opt. Lasers Eng. 2020, 134, 106178. [Google Scholar] [CrossRef]
- Kaur, M.; Kumar, V. A comprehensive review on image encryption techniques. Arch. Comput. Methods Eng. 2020, 27, 15–43. [Google Scholar] [CrossRef]
- Crandall, R.; Pomerance, C. “Primes!” Prime Numbers: A Computational Perspective; Springer: New York, NY, USA, 2005; pp. 1–82. [Google Scholar]
- Goy, T. On new identities for Mersenne numbers. Appl. Math. E-Notes 2018, 18, 100–105. [Google Scholar]
- Sreehari, S.; Wu, H.; Ahmadi, M. Application of new classes of Mersenne primes for fast modular reduction for large-integer multiplication. Int. J. Cyber-Secur. Digit. Forensics (IJCSDF) 2012, 1, 15–19. [Google Scholar]
- Sridhar, V.; Kumar, A. A Technique to Speed up the Modular Multiplicative Inversion over GF(P) Applicable to Elliptic Curve Cryptography. Int. J. Comput. Appl. 2012, 47, 16. [Google Scholar] [CrossRef]
- Choi, P.; Lee, M.-K.; Kong, J.-T.; Kim, D.K. Efficient design and performance analysis of a hardware right-shift binary modular inversion algorithm in GF(P). J. Semicond. Technol. Sci. 2017, 17, 425–437. [Google Scholar]
- Lu, J.; Li, S. A multibit left-shift modular inverse hardware algorithm and its implementation. In Proceedings of the 2021 IEEE International Symposium on Circuits and Systems (ISCAS), Daegu, Republic of Korea, 22–28 May 2021; pp. 1–5. [Google Scholar]
- Choi, P.; Kong, J.-T.; Kim, D.K. Analysis of hardware modular inversion modules for elliptic curve cryptography. In Proceedings of the 2015 International SoC Design Conference (ISOCC), Gyeongju, Republic of Korea, 2–5 November 2015; pp. 313–314. [Google Scholar]
- Hars, L. Modular inverse algorithms without multiplications for cryptographic applications. EURASIP J. Embed. Syst. 2006, 2006, 032192. [Google Scholar] [CrossRef]
- Kumari, M.; Gupta, S.; Sardana, P. A survey of image encryption algorithms. 3D Res. 2017, 8, 37. [Google Scholar] [CrossRef]
- Wang, X.; Feng, L.; Zhao, H. Fast image encryption algorithm based on parallel computing system. Inf. Sci. 2019, 486, 340–358. [Google Scholar] [CrossRef]
- Feng, W.; Yang, J.; Zhao, X.; Qin, Z.; Zhang, J.; Zhu, Z.; Wen, H.; Qian, K. A Novel Multi-Channel Image Encryption Algorithm Leveraging Pixel Reorganization and Hyperchaotic Maps. Mathematics 2024, 12, 3917. [Google Scholar] [CrossRef]
- Feng, W.; Zhang, J.; Chen, Y.; Qin, Z.; Zhang, Y.; Ahmad, M.; Woźniak, M. Exploiting robust quadratic polynomial hyperchaotic map and pixel fusion strategy for efficient image encryption. Expert Syst. Appl. 2024, 246, 123190. [Google Scholar] [CrossRef]
- Deng, Q.; Wang, C.; Sun, Y.; Deng, Z.; Yang, G. Memristive tabu learning neuron generated multi-wing attractor with FPGA implementation and application in encryption. IEEE Trans. Circuits Syst. I Regul. Pap. 2024, 72, 300–311. [Google Scholar] [CrossRef]
- Feng, W.; Zhao, X.; Zhang, J.; Qin, Z.; Zhang, J.; He, Y. Image Encryption Algorithm Based on Plane-Level Image Filtering and Discrete Logarithmic Transform. Mathematics 2022, 10, 2751. [Google Scholar] [CrossRef]
- Wen, H.; Lin, Y. Cryptanalyzing an Image Cipher Using Multiple Chaos and DNA Operations. J. King Saud Univ.-Comput. Inf. Sci. 2023, 35, 101612. [Google Scholar] [CrossRef]
- Feng, W.; Qin, Z.; Zhang, J.; Ahmad, M. Cryptanalysis and improvement of the image encryption scheme based on Feistel network and dynamic DNA encoding. IEEE Access 2021, 9, 145459–145470. [Google Scholar] [CrossRef]
- Feng, W.; He, Y.; Li, H.; Li, C. Cryptanalysis and improvement of the image encryption scheme based on 2D logistic-adjusted-sine map. IEEE Access 2019, 7, 12584–12597. [Google Scholar] [CrossRef]
- Chai, X.; Yang, K.; Gan, Z. A new chaos-based image encryption algorithm with dynamic key selection mechanisms. Multimed. Tools Appl. 2017, 76, 9907–9927. [Google Scholar] [CrossRef]
- Wang, X.; Xu, D. A novel image encryption scheme based on Brownian motion and PWLCM chaotic system. Nonlinear Dyn. 2014, 75, 345–353. [Google Scholar] [CrossRef]
- Shaista, M.; Parsa, S.; Parah, S.A.; Ullah, H.; Hijji, M.; Muhammad, K. Adaptive color image encryption scheme based on multiple distinct chaotic maps and DNA computing. Mathematics 2022, 10, 2004. [Google Scholar] [CrossRef]
- Li, N.; Xie, S.; Zhang, J. A color image encryption algorithm based on double fractional order chaotic neural network and convolution operation. Entropy 2022, 24, 933. [Google Scholar] [CrossRef]
- Alghafis, A.; Firdousia, F.; Khan, M.; Batool, S.I.; Amin, M. An efficient image encryption scheme based on chaotic and Deoxyribonucleic acid sequencing. Math. Comput. Simul. 2020, 177, 441–466. [Google Scholar] [CrossRef]
- Zhu, S.; Zhu, C.; Wang, W. A new image encryption algorithm based on chaos and secure hash SHA-256. Entropy 2018, 20, 716. [Google Scholar] [CrossRef] [PubMed]
- Zhou, N.; Zhang, A.; Zheng, F.; Gong, L. Novel image compression–encryption hybrid algorithm based on key-controlled measurement matrix in compressive sensing. Opt. Laser Technol. 2014, 62, 152–160. [Google Scholar] [CrossRef]
- Ye, G.; Huang, X. A secure image encryption algorithm based on chaotic maps and SHA-3. Secur. Commun. Netw. 2016, 9, 2015–2023. [Google Scholar] [CrossRef]
- Younas, I.; Khan, M. A new efficient digital image encryption based on inverse left almost semi group and Lorenz chaotic system. Entropy 2018, 20, 913. [Google Scholar] [CrossRef] [PubMed]
- Alexan, W.; Chen, Y.-L.; Por, L.Y.; Gabr, M. Hyperchaotic maps and the single neuron model: A novel framework for chaos-based image encryption. Symmetry 2023, 15, 1081. [Google Scholar] [CrossRef]
- Ye, G.; Zhao, H.; Chai, H. Chaotic image encryption algorithm using wave-line permutation and block diffusion. Nonlinear Dyn. 2016, 83, 2067–2077. [Google Scholar] [CrossRef]
- Mohamed, H.I.; Alhammad, S.M.; Khafaga, D.S.; Hosny, K.M. A new image encryption scheme based on the hybridization of Lorenz Chaotic map and Fibonacci Q-matrix. IEEE Access 2023, 12, 14764–14775. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).