A Symmetry-Enhanced Secure and Traceable Data Sharing Model Based on Decentralized Information Flow Control for the End–Edge–Cloud Paradigm
Abstract
1. Introduction
- Data confidentiality is essential, as the shared data often contain sensitive information. This property prevents unauthorized data users or malicious entities from accessing the data during its transmission and storage across the edge and cloud layers. By ensuring confidentiality, data owners will be willing to share their data.
- Data integrity guarantees the accuracy and reliability of data throughout the entire sharing process, from the original data owner to the end user. This ensures that the data has not been altered or tampered with, maintaining its trustworthiness.
- Identity traceability is equally critical, as it enables the system to track the identity of data users in the event of illegal access or for accountability purposes. This capability acts as a deterrent against misuse and provides a mechanism for forensic analysis should a security incident occur.
- (1)
- The confidentiality and integrity of the shared data are preserved:To preserve data confidentiality and integrity, the secrecy label and integrity label are attached on the share data before the data are uploaded to the edge servers and the cloud center. Here, the secrecy label restricts read access for unauthorized users, while the integrity label blocks write operations by unauthorized users, thereby preserving data confidentiality and integrity.
- (2)
- Identity traceability is achieved by STDSM:In order to achieve identity traceability, STDSM introduces the owner tag and trace data. Furthermore, owner tags serve as identifiers for both data owner and user, while trace data capture user identities during data sharing. When data sharing occurs, the data owner’s owner tag attached on the shared data and the owner tag of data user are used to generate trace data. Such trace data records data flow information, thereby enabling STDSM to enable identity traceability.
- (3)
- The security of STDSM is formally verified and performance evaluation is conducted:To verify the security of STDSM, we employ a novel method that combines High-Level Petri Net (HLPN) modeling with the satisfiability modulo theories library (SMT-Lib) and the Z3 solver. This method implements bounded model checking [4] to validate STDSM. Our verification results show that STDSM has the capabilities of protecting data confidentiality and integrity, and it can also track data user identity. Our performance evaluation results show STDSM’s high efficiency compared with the related works.
2. Related Work
2.1. Secure Data Sharing in EEC Paradigm
2.2. Decentralized Information Flow Control
3. Preliminaries
3.1. High-Level Petri Net
3.2. SMT-Lib and Z3 Solver
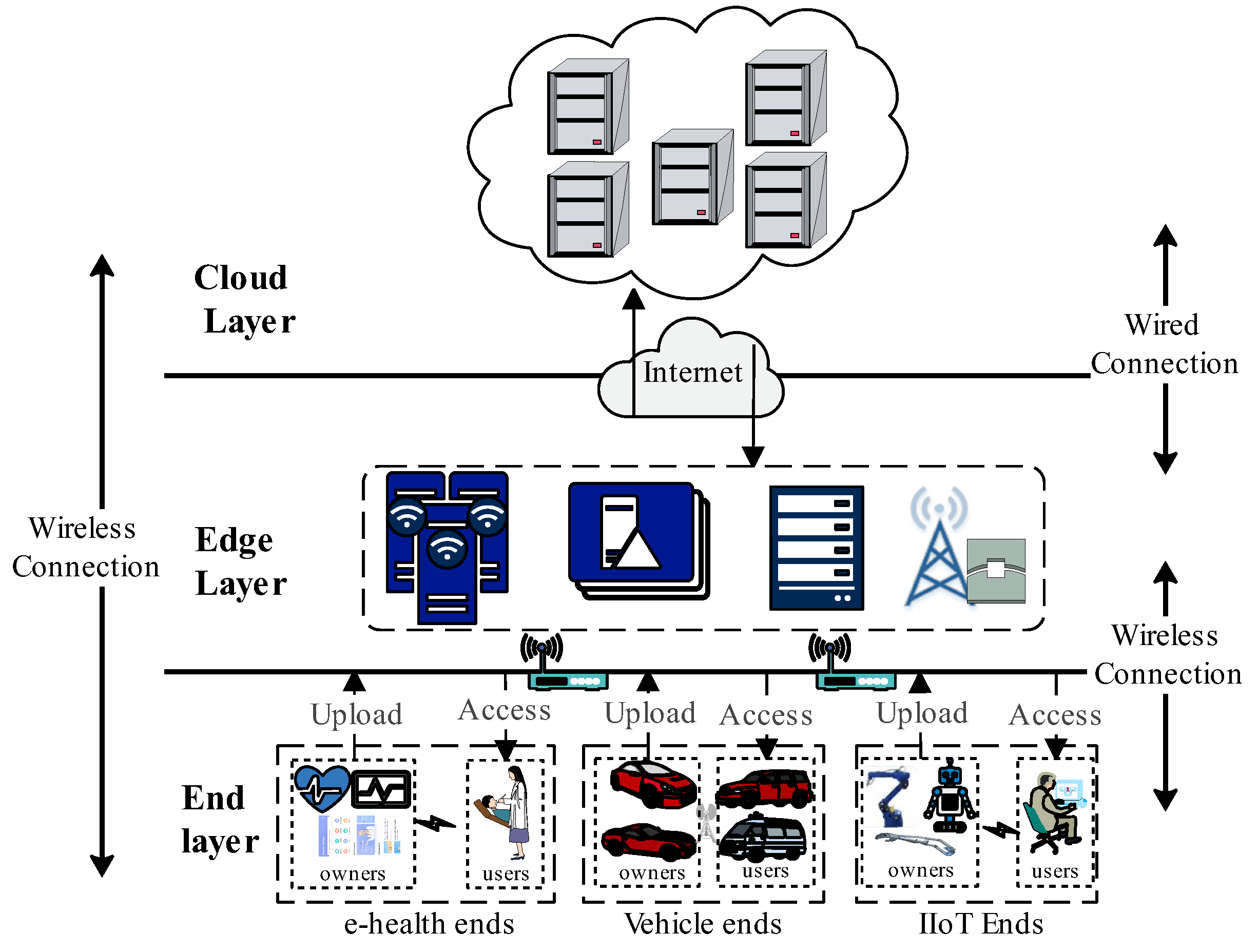
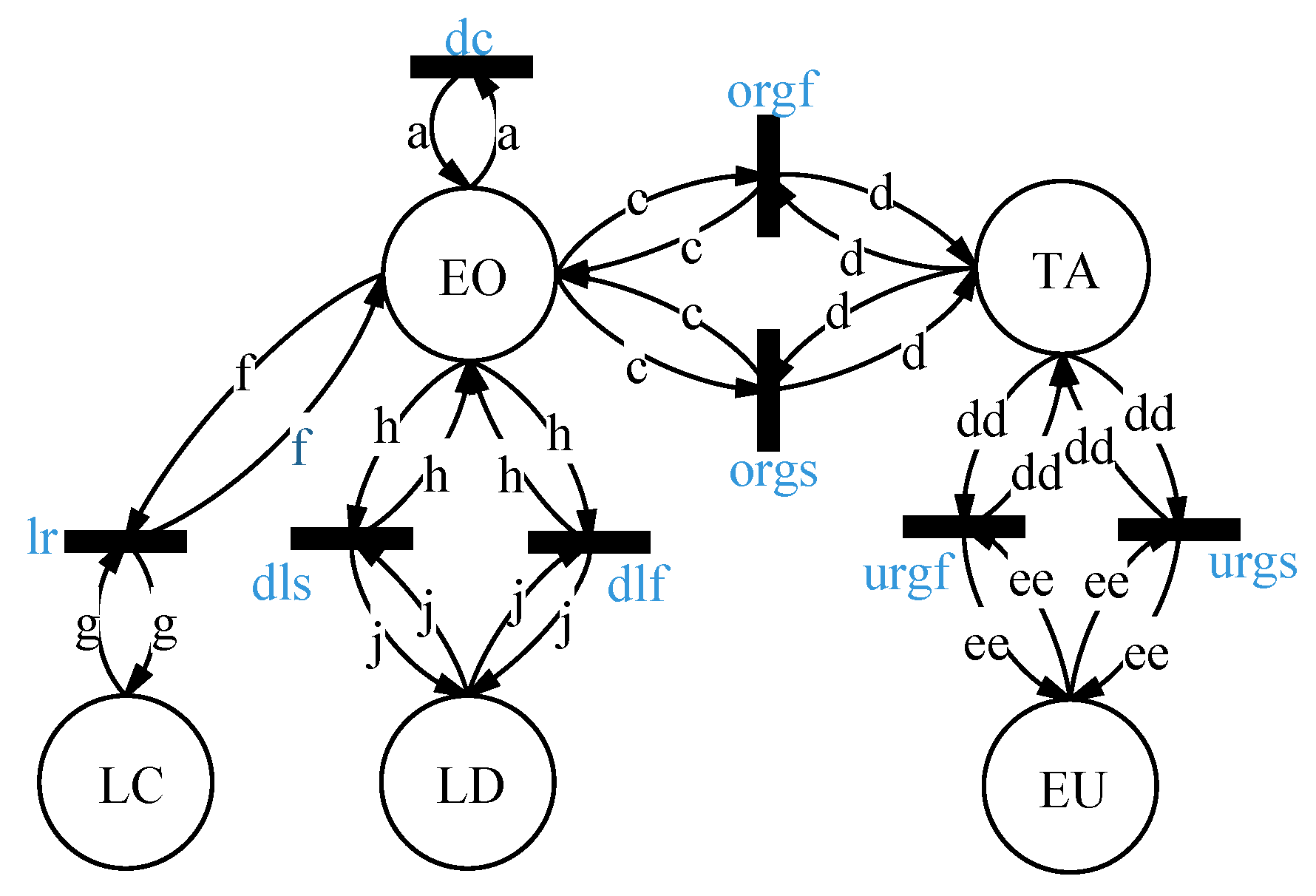
4. STDSM
4.1. Model Description
- Bob can read the data only if his secrecy label also contains both and ;
- Bon will accept the data only if his integrity label is a subset of Alice’s, e.g., , meaning he trusts data from Alice’s device;
- Regardless of the decision, the trace data records that Alice and Bob attempted this data transfer.
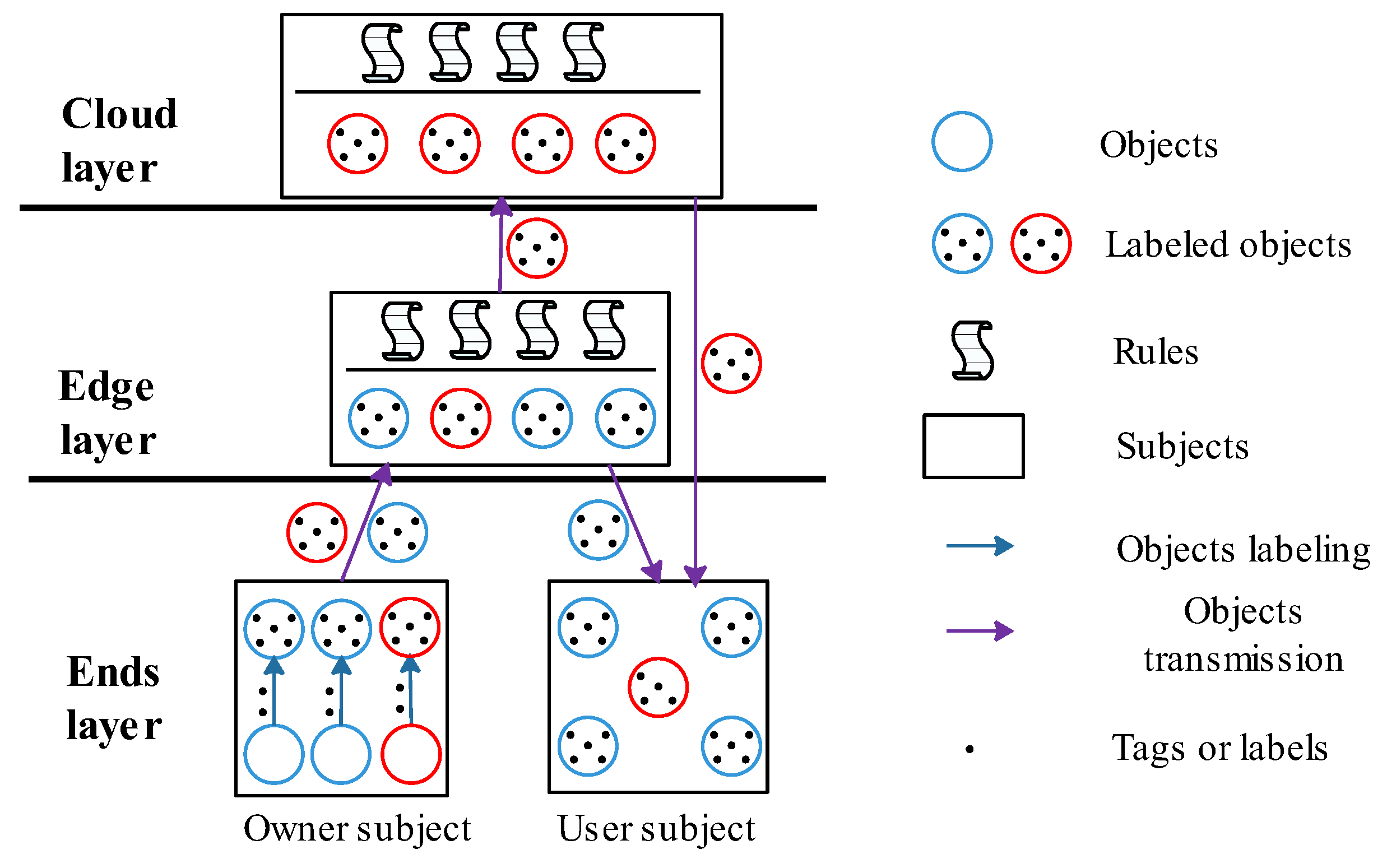
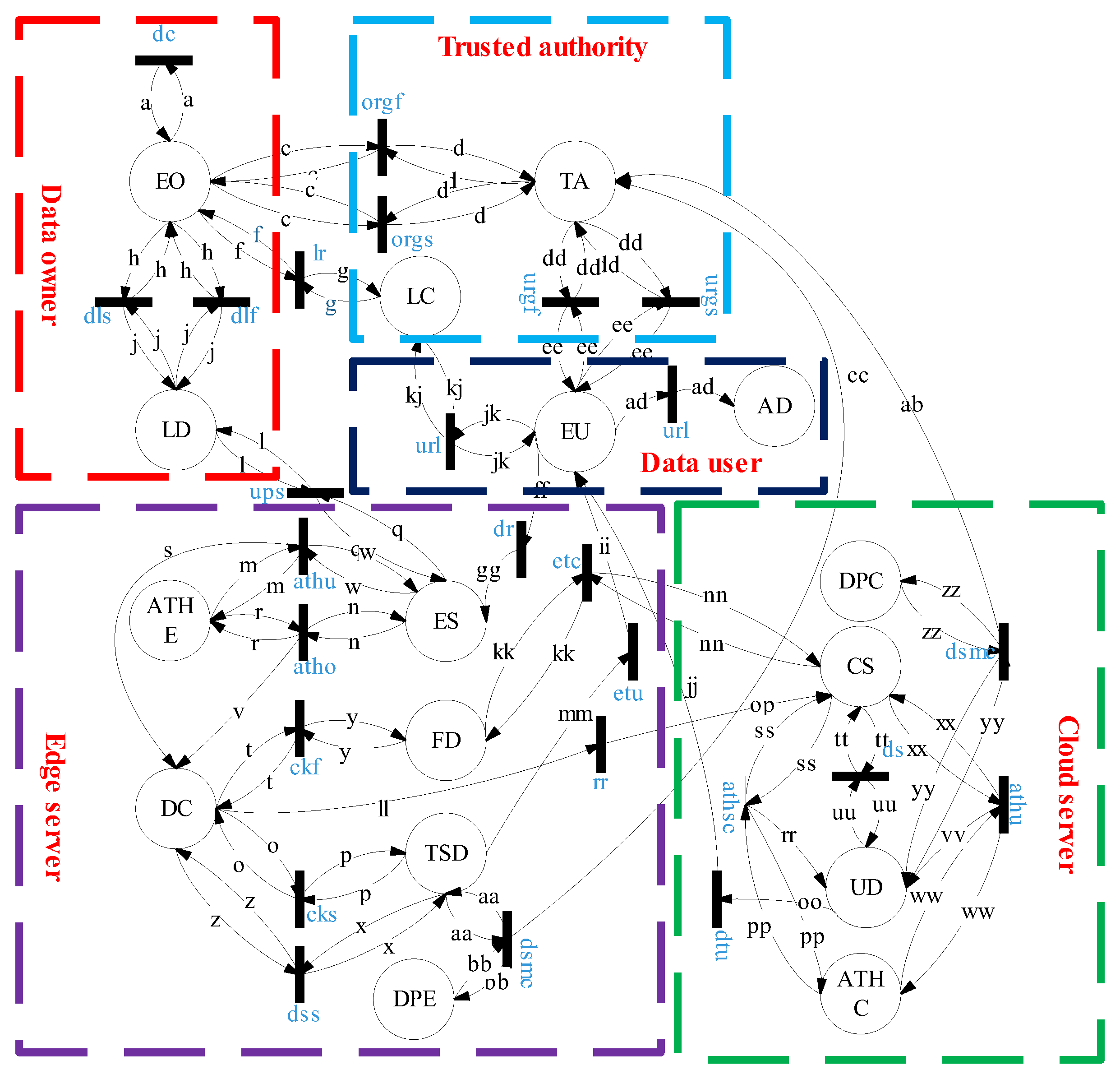
4.2. Modeling
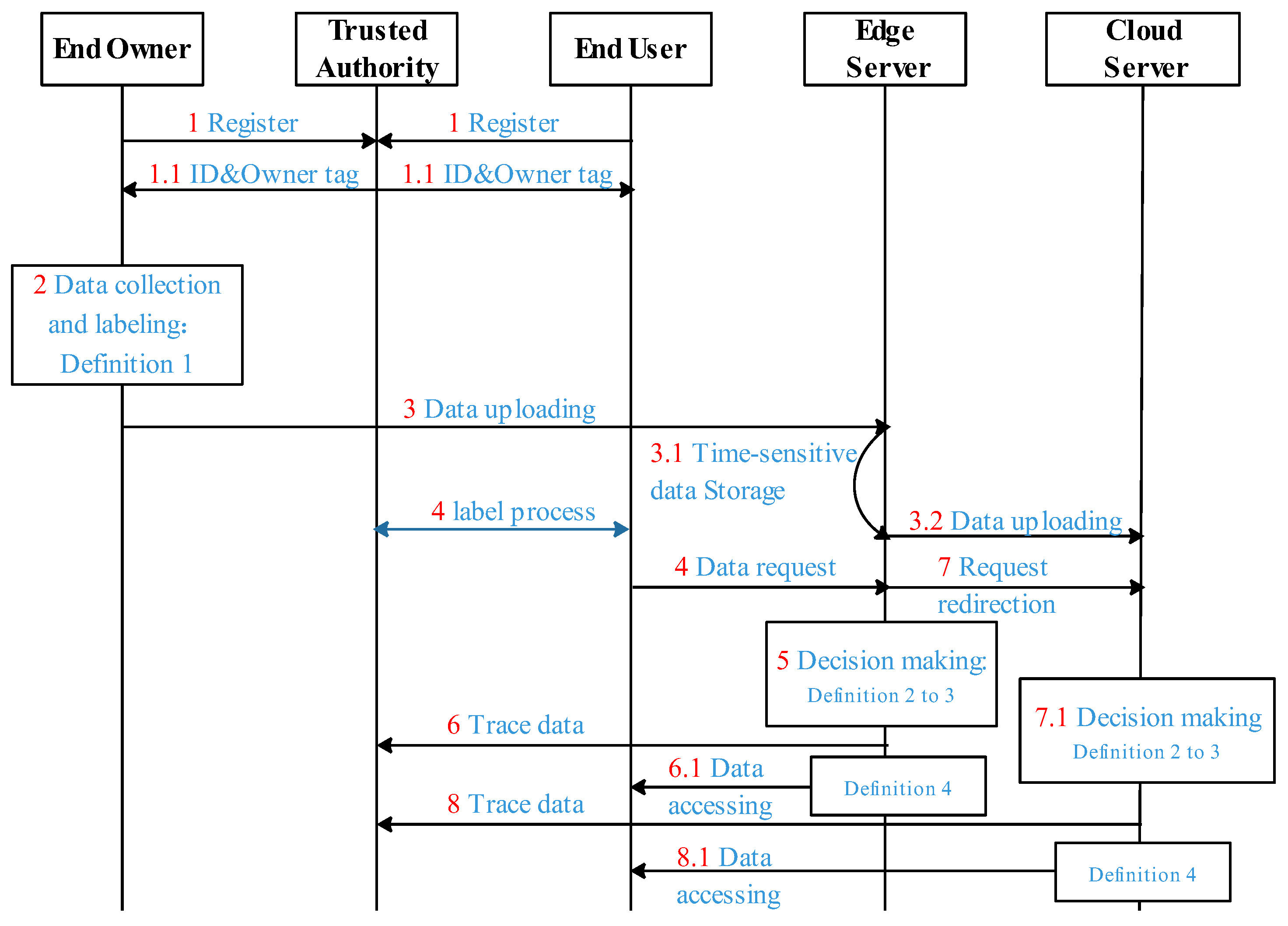
4.3. Workflows
- (1)
- EO and EU are registered at the TA using their attributes, and then TA generates and distributes the unique ID to them. Furthermore, TA also simultaneously computes and distributes the owner tag and to them, respectively.
- (2)
- On the EO side, it first aggregates raw data, then requests secrecy and integrity labels from TA and, finally, labels raw data using , , and owner tag based on the rule of Definition 1. After that, EO uploads the labeled data to ES. In addition, the labels and owner tag are also propagated along with the data.
- (3)
- Once the labeled data are received, ES first checks the data and determines whether it is delay-sensitive, and if so then ES locally stores the data. Otherwise, ES uploads the received data to the cloud.
- (4)
- EU first requests secrecy, , and integrity labels, , from TA, then requests data by sending a request message to ES, in which the EU secrecy label , the integrity label , and the owner tag are contained in the message.
- (5)
- Once ES has determined that the requested data are delay-sensitive, it then makes a sharing decision by enforcing the secure rules of Definition 2 to 3.
- (6)
- Subsequently, the trace data are also generated according to and , and it is stored in TA regardless of the sharing decision. Meanwhile, upon verification of a positive data sharing decision, the requested data are transmitted to the end user. Finally, EU accesses the shared data based on the rule of Definition 4.
- (7)
- Alternatively, once the requested data are delay-insensitive, ES redirects the data request to the cloud. Then, CS makes a sharing decision by enforcing the secure rules of Definition 2 to 3 to decide whether to share data.
- (8)
- The trace data are also generated according to and and are stored in TA regardless of the sharing decision. Meanwhile, upon verification of a positive data sharing decision, the requested data are transmitted to the end user. Finally, EU accesses the shared data based on the rule of Definition 4.
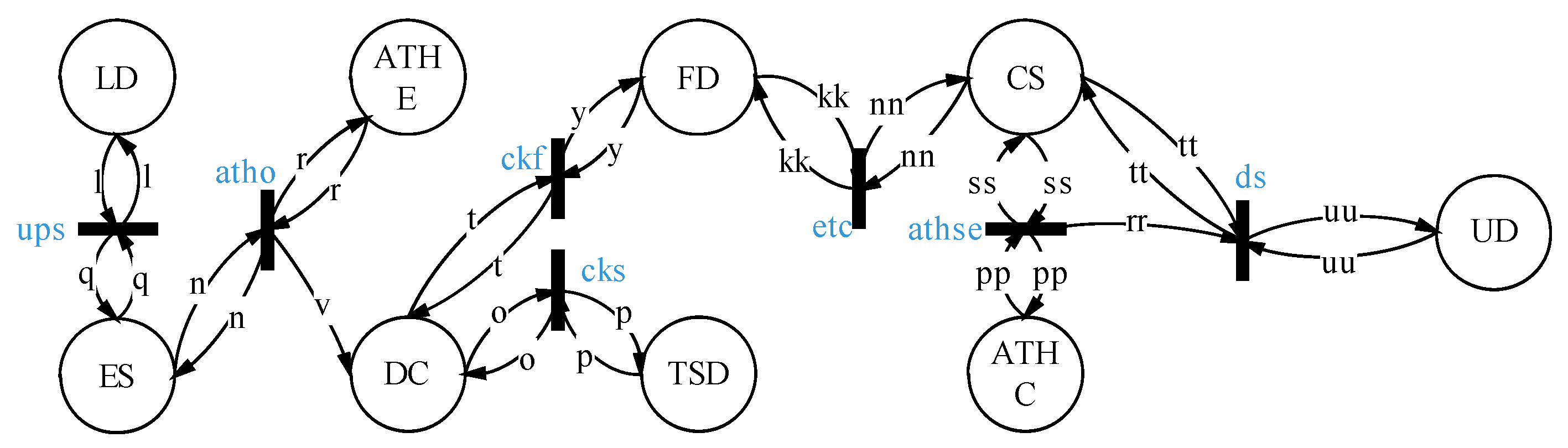
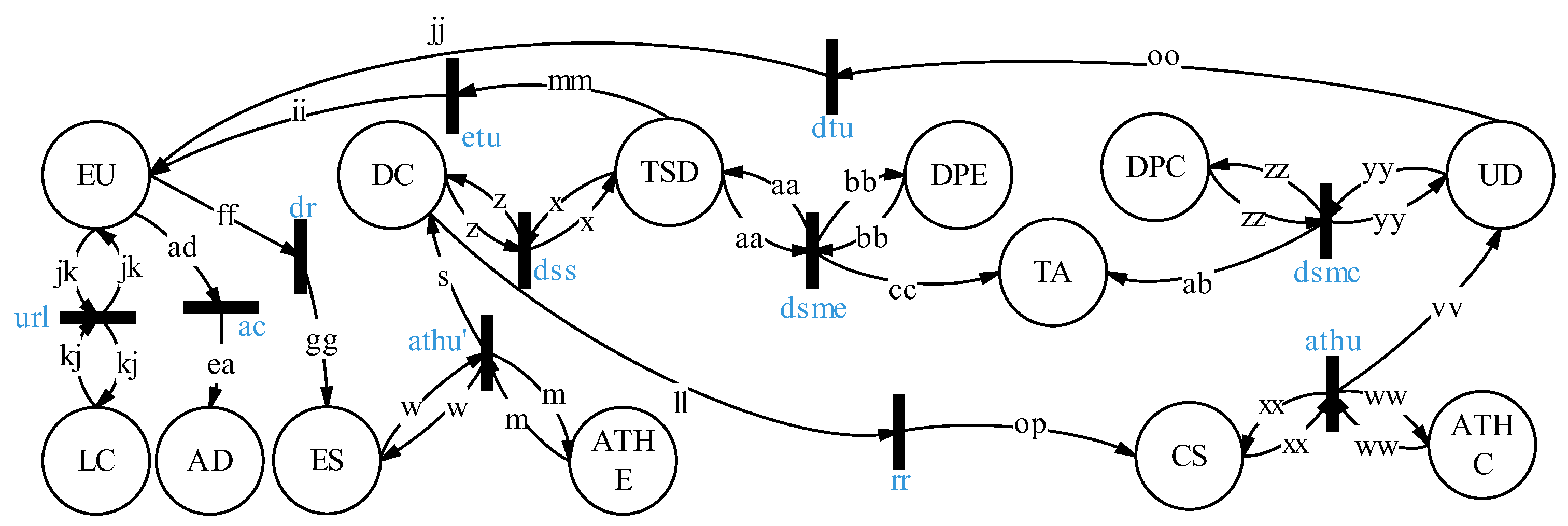
5. Formal Analysis and Verification of STDSM
5.1. Formal Analysis
5.1.1. Register and Data Labeling
5.1.2. Data Outsource
5.1.3. Data Request and Delivery
5.2. Formal Verification
5.2.1. Assertions for Security Properties
- Assertion for data confidentiality. Let be the secrecy label attached to data d in EEC system S. Data confidentiality is preserved ifwhere d is the shared data, S means the data set within system, T is the system lifetime, and is the labeling time. Accordingly, our formal verification adopts this foundational assertion:
- Assertion for data integrity. Similarly, let be the secrecy label attached to data d in EEC system S. Data integrity is preserved ifAccordingly, our formal verification utilizes this foundational assertion:
- Assertion for identity traceability. Similarly to the confidentiality and integrity assertions, let be the owner tag attached to data d in EEC system S. Identity traceability is preserved ifwhere and represent the owner tag of data owner and data user. In STDSM, the shared data are also labeled using the owner tag. Accordingly, our formal verification utilizes this foundational assertion:
5.2.2. Result
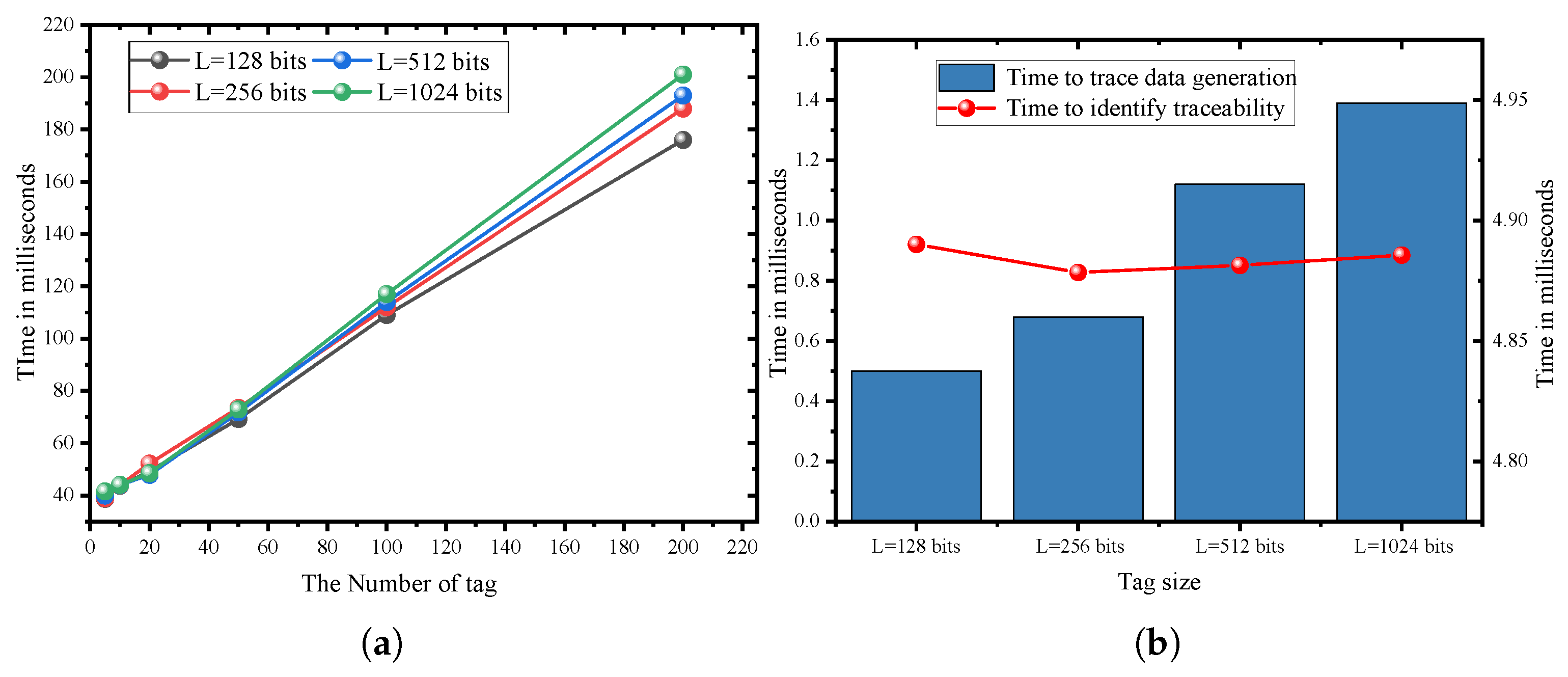
6. Performance Evaluation
6.1. Experimental Setup
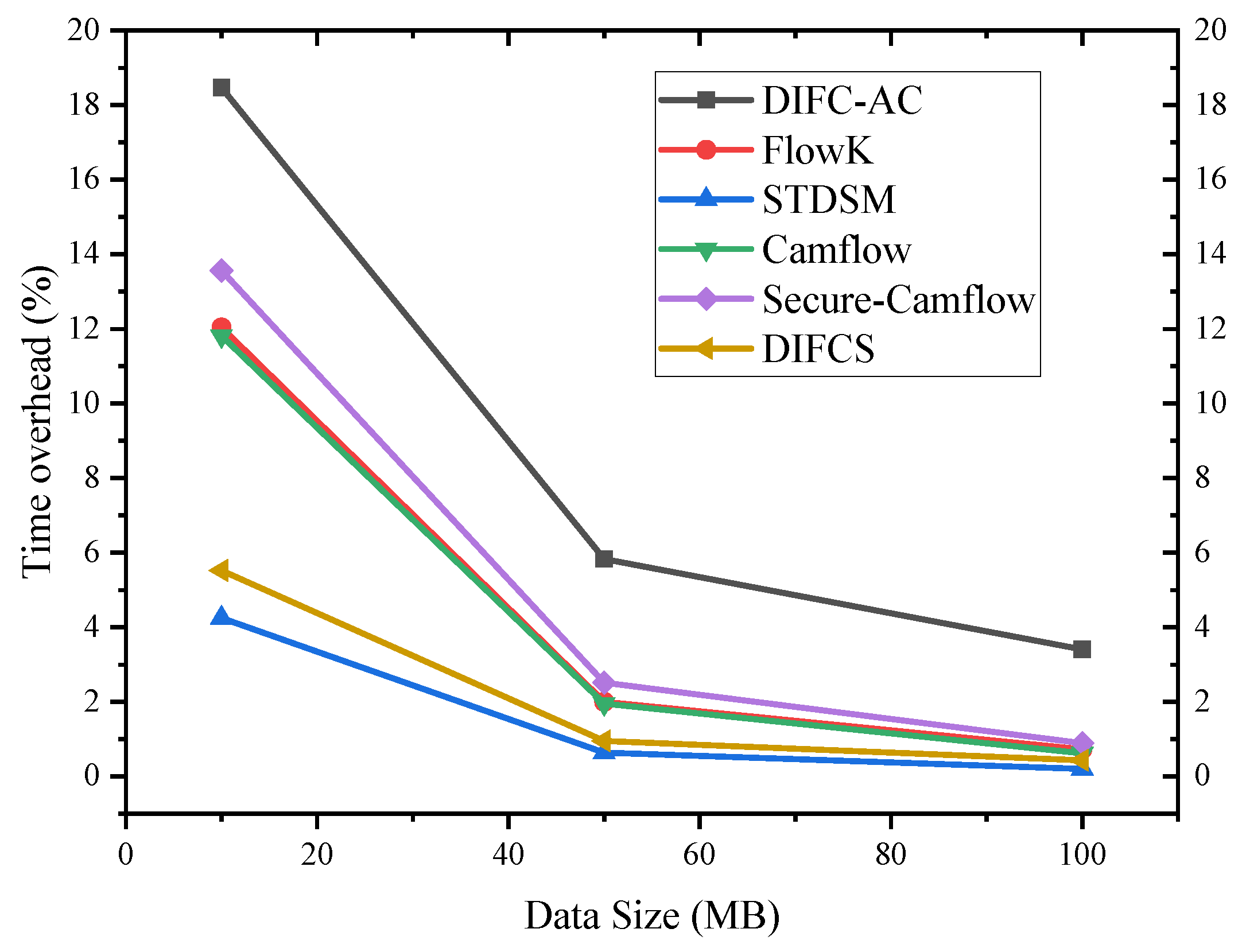
6.2. Numerical Result
6.3. Storage Overhead Analysis
6.4. Functional Comparison
7. Conclusions and Discussions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Aouedi, O.; Vu, T.H.; Sacco, A.; Nguyen, D.C.; Piamrat, K.; Marchetto, G.; Pham, Q.V. A survey on intelligent Internet of Things: Applications, security, privacy, and future directions. IEEE Commun. Surv. Tutor. 2024, 27, 1238–1292. [Google Scholar] [CrossRef]
- Huang, Z.; Zhang, Z.; Hua, C.; Liao, B.; Li, S. Leveraging enhanced egret swarm optimization algorithm and artificial intelligence-driven prompt strategies for portfolio selection. Sci. Rep. 2024, 14, 26681. [Google Scholar] [CrossRef]
- Liao, B.; Han, L.; Cao, X.; Li, S.; Li, J. Double integral-enhanced Zeroing neural network with linear noise rejection for time-varying matrix inverse. CAAI Trans. Intell. Technol. 2024, 9, 197–210. [Google Scholar] [CrossRef]
- Lu, J.; Li, W.; Sun, J.; Xiao, R.; Liao, B. Secure and real-time traceable data sharing in cloud-assisted IoT. IEEE Internet Things J. 2024, 11, 6521–6536. [Google Scholar] [CrossRef]
- Wang, C.; Wang, Y.; Yuan, Y.; Peng, S.; Li, G.; Yin, P. Joint computation offloading and resource allocation for end-edge collaboration in internet of vehicles via multi-agent reinforcement learning. Neural Netw. 2024, 179, 106621. [Google Scholar] [CrossRef]
- Duan, S.; Wang, D.; Ren, J.; Lyu, F.; Zhang, Y.; Wu, H.; Shen, X. Distributed Artificial Intelligence Empowered by End-Edge-Cloud Computing: A Survey. IEEE Commun. Surv. Tutor. 2022, 25, 591–624. [Google Scholar] [CrossRef]
- Pasquier, T.F.M.; Singh, J.; Eyers, D.; Bacon, J. CamFlow: Managed data-sharing for cloud services. IEEE Trans. Cloud Comput. 2015, 5, 472–484. [Google Scholar] [CrossRef]
- Zhang, T.; Jiang, M.; Luo, F.; Guo, Y. A lattice-based puncturable CP-ABE scheme with forward security for cloud-assisted IoT. IEEE Internet Things J. 2025, 12, 26538–26554. [Google Scholar] [CrossRef]
- Weng, J.; Lai, J. Proxy re-encryption. In Encyclopedia of Cryptography, Security and Privacy; Springer: Cham, Switzerland, 2025; pp. 1992–1997. [Google Scholar] [CrossRef]
- Elhabob, R.; Eltayieb, N.; Xiong, H.; Kumari, S. Equality test on identity-based encryption with cryptographic reverse firewalls for telemedicine systems. IEEE Internet Things J. 2024, 12, 2106–2121. [Google Scholar] [CrossRef]
- Zhang, L.; Peng, M.; Wang, W.; Jin, Z.; Su, Y.; Chen, H. Secure and efficient data storage and sharing scheme for blockchain-based mobile-edge computing. Trans. Emerg. Telecommun. Technol. 2021, 32, e4315. [Google Scholar] [CrossRef]
- Vacca, A.; Di Sorbo, A.; Visaggio, C.A.; Canfora, G. A systematic literature review of blockchain and smart contract development: Techniques, tools, and open challenges. J. Syst. Softw. 2021, 174, 110891. [Google Scholar] [CrossRef]
- Hu, T.; Liu, X.; Chen, T.; Zhang, X.; Huang, X.; Niu, W.; Lu, J.; Zhou, K.; Liu, Y. Transaction-based classification and detection approach for Ethereum smart contract. Inf. Process. Manag. 2021, 58, 102462. [Google Scholar] [CrossRef]
- Fan, K.; Pan, Q.; Wang, J.; Liu, T.; Li, H.; Yang, Y. Cross-domain based data sharing scheme in cooperative edge computing. In Proceedings of the 2018 IEEE International Conference on Edge Computing (EDGE), San Francisco, CA, USA, 2–7 July 2018; pp. 87–92. [Google Scholar] [CrossRef]
- Lin, Y.; Xiong, H.; Su, H.; Yeh, K.H. Multi-Authority CP-ABE Scheme With Cryptographic Reverse Firewalls for Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2015, 26, 5348–5359. [Google Scholar] [CrossRef]
- Ding, R.; Zhong, H.; Ma, J.; Liu, X.; Ning, J. Lightweight privacy-preserving identity-based verifiable IoT-based health storage system. IEEE Internet Things J. 2019, 6, 8393–8405. [Google Scholar] [CrossRef]
- Liu, W.; You, L.; Shao, Y.; Shen, X.; Hu, G.; Shi, J.; Gao, S. From accuracy to approximation: A survey on approximate homomorphic encryption and its applications. Comput. Sci. Rev. 2025, 55, 100689. [Google Scholar] [CrossRef]
- Xie, J.; Guo, D.; Shi, X.; Cai, H.; Qian, C.; Chen, H. A fast hybrid data sharing framework for hierarchical mobile edge computing. In Proceedings of the IEEE INFOCOM 2020-IEEE Conference on Computer Communications, Toronto, ON, Canada, 6–9 July 2020; pp. 2609–2618. [Google Scholar] [CrossRef]
- Xie, M.; An, B.; Jia, X.; Zhou, M.; Lu, J. Simultaneous update of sensing and control data using free-ride codes in vehicular networks: An age and energy perspective. Comput. Netw. 2024, 252, 110667. [Google Scholar] [CrossRef]
- Zuo, Y.; Dai, C.; Guo, J.; Guo, Z.; Xiao, F.; Jin, S. Secure data sharing for autonomous vehicles in mobile blockchain networks. IEEE Netw. 2025, 39, 166–175. [Google Scholar] [CrossRef]
- Liu, H.; Zhang, P.; Pu, G.; Yang, T.; Maharjan, S.; Zhang, Y. Blockchain empowered cooperative authentication with data traceability in vehicular edge computing. IEEE Trans. Veh. Technol. 2020, 69, 4221–4232. [Google Scholar] [CrossRef]
- Myers, A.C.; Liskov, B. A decentralized model for information flow control. ACM SIGOPS Oper. Syst. Rev. 1997, 31, 129–142. [Google Scholar] [CrossRef]
- Myers, A.C.; Liskov, B. Complete, safe information flow with decentralized labels. In Proceedings of the Proceedings. 1998 IEEE Symposium on Security and Privacy (Cat. No. 98CB36186), Oakland, CA, USA, 6 May 1998; pp. 186–197. [Google Scholar] [CrossRef]
- Ye, Z.; Ye, J. DIFC-AC: Information pravicy protection for colud computing system. Comput. Appl. Softw. 2013, 30, 30–34. [Google Scholar] [CrossRef]
- Pasquier, T.F.; Bacon, J.; Eyers, D. Flowk: Information flow control for the cloud. In Proceedings of the 2014 IEEE 6th International Conference on Cloud Computing Technology and Science, Singapore, 15–18 December 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 70–77. [Google Scholar] [CrossRef]
- Khurshid, A.; Khan, A.N.; Khan, F.G.; Ali, M.; Shuja, J.; Khan, A.u.R. Secure-CamFlow: A device-oriented security model to assist information flow control systems in cloud environments for IoTs. Concurr. Comput. Pract. Exp. 2019, 31, e4729. [Google Scholar] [CrossRef]
- Lu, J.; Sun, J.; Xiao, R.; Jin, S. DIFCS: A Secure Cloud Data Sharing Approach Based on Decentralized Information Flow Control. Comput. Secur. 2022, 117, 102678. [Google Scholar] [CrossRef]
- Alam, Q.; Tabbasum, S.; Malik, S.U.; Alam, M.; Ali, T.; Akhunzada, A.; Khan, S.U.; Vasilakos, A.V.; Buyya, R. Formal verification of the xDAuth protocol. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1956–1969. [Google Scholar] [CrossRef]
- Alam, Q.; Malik, S.U.; Akhunzada, A.; Choo, K.K.R.; Tabbasum, S.; Alam, M. A cross tenant access control (CTAC) model for cloud computing: Formal specification and verification. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1259–1268. [Google Scholar] [CrossRef]
- Peterson, J.L. Petri Nets. ACM Comput. Surv. 1977, 9, 223–252. [Google Scholar] [CrossRef]
- Murata, T. Petri nets: Properties, analysis and applications. Proc. IEEE 1989, 77, 541–580. [Google Scholar] [CrossRef]
- Anjum, A.; Malik, S.u.R.; Choo, K.K.R.; Khan, A.; Haroon, A.; Khan, S.; Khan, S.U.; Ahmad, N.; Raza, B. An efficient privacy mechanism for electronic health records. Comput. Secur. 2018, 72, 196–211. [Google Scholar] [CrossRef]
- Kanwal, T.; Anjum, A.; Malik, S.U.; Sajjad, H.; Khan, A.; Manzoor, U.; Asheralieva, A. A robust privacy preserving approach for electronic health records using multiple dataset with multiple sensitive attributes. Comput. Secur. 2021, 105, 102224. [Google Scholar] [CrossRef]
- Barrett, C.; Stump, A.; Tinelli, C. The smt-lib standard: Version 2.0. In Proceedings of the 8th International Workshop on Satisfiability Modulo Theories, Edinburgh, UK, 14–15 July 2010; Volume 13, p. 14. Available online: https://smtlib.cs.uiowa.edu/papers/smt-lib-reference-v2.6-r2021-05-12.pdf (accessed on 10 July 2025).
- Moura, L.d.; Bjørner, N. Z3: An efficient SMT solver. In Proceedings of the International conference on Tools and Algorithms for the Construction and Analysis of Systems, Budapest, Hungary, 29 March–6 April 2008; pp. 337–340. [Google Scholar] [CrossRef]
- Tu, H.; Xiang, D.; Ding, Z.; Liu, G. Detecting Information Leakage Against Chinese Wall Policy Based on the Unfolding Technique of Colored Petri Nets. IEEE Trans. Comput. Soc. Syst. 2025, 12, 2108–2119. [Google Scholar] [CrossRef]
| Model/Scheme | Core Enforcement Mechanism | Application Scenario |
|---|---|---|
| DIFC-AC [24] | security labels + authorization conditions | PaaS cloud |
| FlowK [25] | security Labels + OS-level enforcement | PaaS cloud |
| Camflow [7] | security labels + OS-level enforcement | PaaS cloud |
| Secure-Camflow [26] | security labels + cryptography | Cloud-assisted IoT |
| DIFCS [27] | security labels + privilege delegation | Multi-clouds |
| STDSM (Ours) | symmetrical labels + owner tags | EEC Paradigm |
| Places | Description | Explanation |
|---|---|---|
| End data owner’s attributes | ||
| Attributes of TA | ||
| End data user’s attributes | ||
| Attributes of the shared data | ||
| Attributes of TA’s label center | ||
| Attributes of the labeled data | ||
| Attributes of the edge server | ||
| Holds attributes of authentication center on edge | ||
| Attributes of edge server’s data center | ||
| Attributes of the time-sensitive data | ||
| Attributes of the forwarded data | ||
| Attributes of the cloud | ||
| Attributes of authentication center on edge | ||
| Attributes of received data | ||
| Attributes of the decision point on edge | ||
| Attributes of the decision point on cloud | ||
| Attributes of shared data |
| Items | Types |
|---|---|
| attribute(s) | A string type for attributes |
| info. | A string type for information |
| id | An integrity number type for identity |
| tag | A string type for tags |
| label | A string type for security labels |
| result | A Boolean type for authentication result, tag generation result, etc. |
| data | A data type for IoT data |
| time | A date type for time |
| description | A string type for the description of IoT data |
| name | A string type for the name of IoT data |
| privileges | An enumeration type for security privileges |
| mapping | A string type for the places mappings |
| Devices | CPU | Memory | System |
|---|---|---|---|
| Mobile phones | Kirin 710 | 4 GB | Android 8 |
| Snapdragon 750 | 6 GB | Android 10 | |
| Desktop | Intel i7-8809 | 32 GB | Windows 11 |
| Laptop | Intel i7-7560U | 16 GB | Windows 11 |
| Server | Gold-6330 | 256 GB | Ubuntu 18.04 |
| Models | Comparison Items | |||||
|---|---|---|---|---|---|---|
| C | I | T | Auth. | Sca. | Trade-Offs/Limitations | |
| DIFC-AC [24] | ✓ | ✓ | × | Limited | Limited | OS kernel and highest overhead. |
| Flowk [25] | ✓ | ✓ | × | Supported | High | OS kernel and mod. overhead. |
| Camflow [7] | ✓ | ✓ | × | Supported | High | OS kernel and mod. overhead. |
| Secure- | ||||||
| Camflow [26] | ✓ | ✓ | × | Supported | High | Cry. with higher overhead. |
| DIFCS [27] | ✓ | ✓ | × | Supported | High | Multi-clouds and less overhead. |
| STDSM | ✓ | ✓ | ✓ | Supported | High | CTA and lowest overhead. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lu, J.; Yu, C.; Qi, M.; Luo, H.; Tian, J.; Li, J. A Symmetry-Enhanced Secure and Traceable Data Sharing Model Based on Decentralized Information Flow Control for the End–Edge–Cloud Paradigm. Symmetry 2025, 17, 1771. https://doi.org/10.3390/sym17101771
Lu J, Yu C, Qi M, Luo H, Tian J, Li J. A Symmetry-Enhanced Secure and Traceable Data Sharing Model Based on Decentralized Information Flow Control for the End–Edge–Cloud Paradigm. Symmetry. 2025; 17(10):1771. https://doi.org/10.3390/sym17101771
Chicago/Turabian StyleLu, Jintian, Chengzhi Yu, Menglong Qi, Han Luo, Jie Tian, and Jianfeng Li. 2025. "A Symmetry-Enhanced Secure and Traceable Data Sharing Model Based on Decentralized Information Flow Control for the End–Edge–Cloud Paradigm" Symmetry 17, no. 10: 1771. https://doi.org/10.3390/sym17101771
APA StyleLu, J., Yu, C., Qi, M., Luo, H., Tian, J., & Li, J. (2025). A Symmetry-Enhanced Secure and Traceable Data Sharing Model Based on Decentralized Information Flow Control for the End–Edge–Cloud Paradigm. Symmetry, 17(10), 1771. https://doi.org/10.3390/sym17101771






