Depth-First Net Unfoldings and Equivalent Reduction
Abstract
:1. Introduction
2. Unfolding of Petri Net
- (1)
- P and T represent finite sets of places and transitions, respectively;
- (2)
- F ⊆ (P × T) ∪ (T × P) arcs set;
- (3)
- P ∪ T ≠ ∅ and P ∩ T = ∅.
- (1)
- •x = {y ∈ P ∪ T|(y, x) ∈ F};
- (2)
- x•= {y ∈ P ∪ T|(x, y) ∈ F}.
- (1)
- If there is a transition t and the markings M and M′ satisfy M[t〉M′, then the marking M′ from M is directly reachable;
- (2)
- If there is a sequence of transition occurrence σ = t1 t2 t3 … tn, M[t1〉M1[t2〉M2…Mn−1[tn〉M″, that is, M[σ〉M″, then the marking M″ from M is reachable. All sets of identifiers reachable from the marking M are denoted as R(M).
- (1)
- x and y belong to a causal relationship, denoted as x ≤ y, if and only if there is a path from x to y in N. If x ≠ y, it is recorded as x < y;
- (2)
- x and y belong to a conflicting relationship, denoted as x # y, if and only if ∃t1, t2 ∈ T: •t1 ∩ •t2 ≠ ∅ ∧ t1 ≤ x ∧ t2 ≤ y;
- (3)
- x and y belong to a concurrent relationship, denoted as x co y, if and only if they satisfy ¬(x < y ∧ y < x ∧ x # y), that is, x and y are neither causal nor conflicting.
- (1)
- ∀x, y ∈ P ∪ T: x < y ⇒ y ⊀ x;
- (2)
- ∀p ∈ P: |•P| ≤ 1;
- (3)
- There is no self-conflicting change, that is, ∀t ∈ T: ¬(t # t).
- (1)
- h(B) ⊆ P ∧ h(E) ⊆ T;
- (2)
- For any event e ∈ E, the h function acting on •e (resp., e•) satisfies the bijection of •e to •h(e) (resp., e• and h(e)•);
- (3)
- The h function acting on Min(O) is also limited to the bijection between Min(O) and M0;
- (4)
- For any event e1, e2 ∈ E, if •e1 = •e2 and h(e1) = h(e2), then e1 = e2.
- (1)
- Causal closure: e ∈ C ⇒ ∀e′ ≤ e: e′ ∈ C;
- (2)
- No conflict: ∀e, e′ ∈ C: ¬(e # e′).
- (1)
- <e satisfies the order relationship;
- (2)
- C1⊂ C2⇒ C1 <e C2;
- (3)
- If C1 <e C2 and Marking(C1) = Marking(C2), then there is an isomorphic relationship I1 and an extended event set E′ to satisfy C1 ⊕ E′ <C2 ⊕ I1(E′).
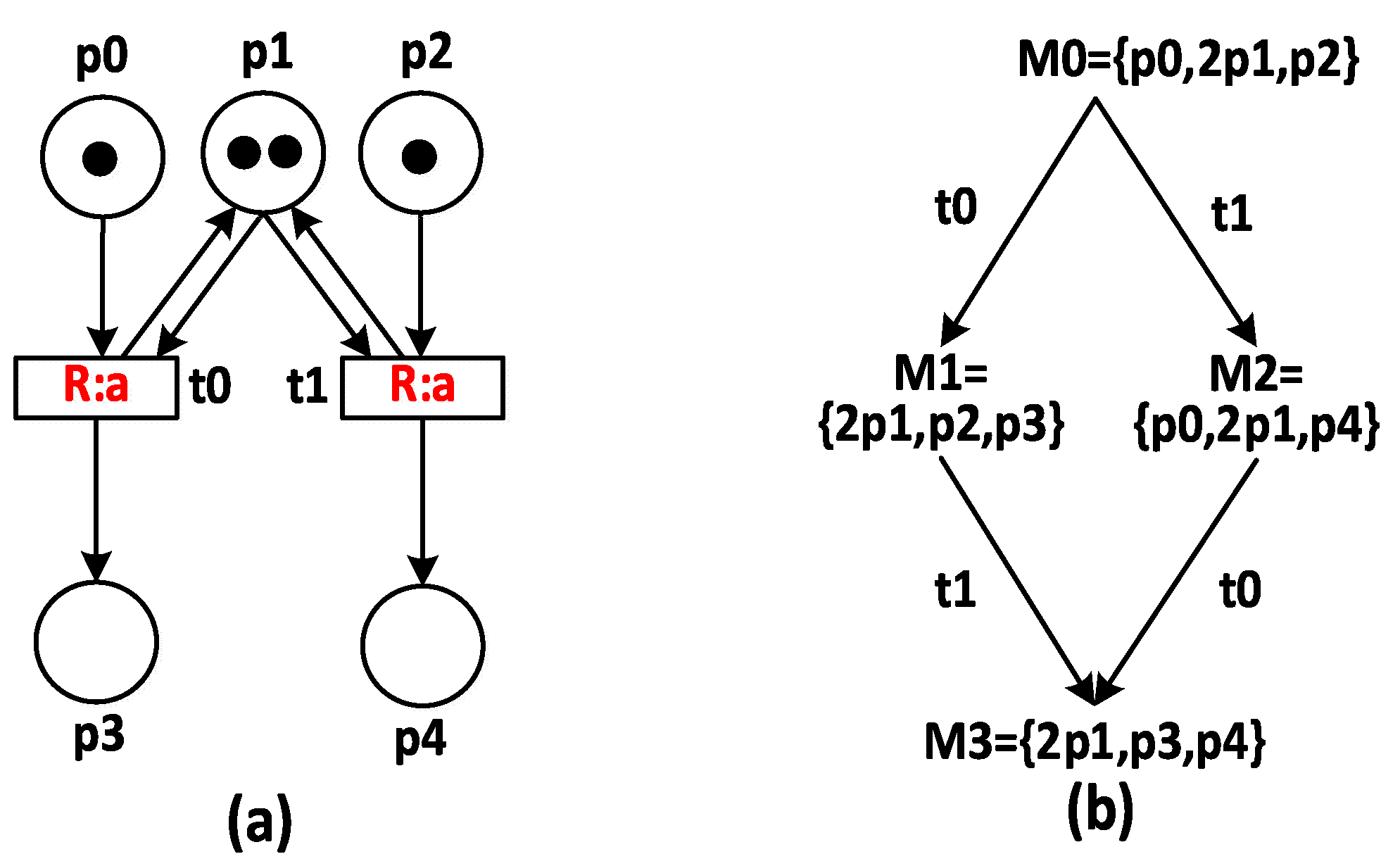
3. Net Unfolding
| Algorithm 1: ERV Net Unfolding Algorithm [12] |
| input: Petri net ∑ = (P, T, F, M0) output: Finite complete prefix Fin. 1: Fin: = Min (Unf (∑)); 4: Poe: = PE(Fin); /*Possible Extension Set*/ 2: Cutoff: = ∅; /*Cut-off Event Set*/ 5: while Poe ≠ ∅, do 6: Select the event e with the smallest <e relationship from Poe; 7: if [e] ∩ Cutoff_node = = ∅, then 8: Expanding e and e• ∪ •e into Fin; 9: Poe: = PE(Fin); 18: if e is cut-off event, then 19: Cutoff_node: = Cutoff _node ∪ {e} 20: end if 22: else Poe: = Poe \ {e}; 24: end if 25: end while |
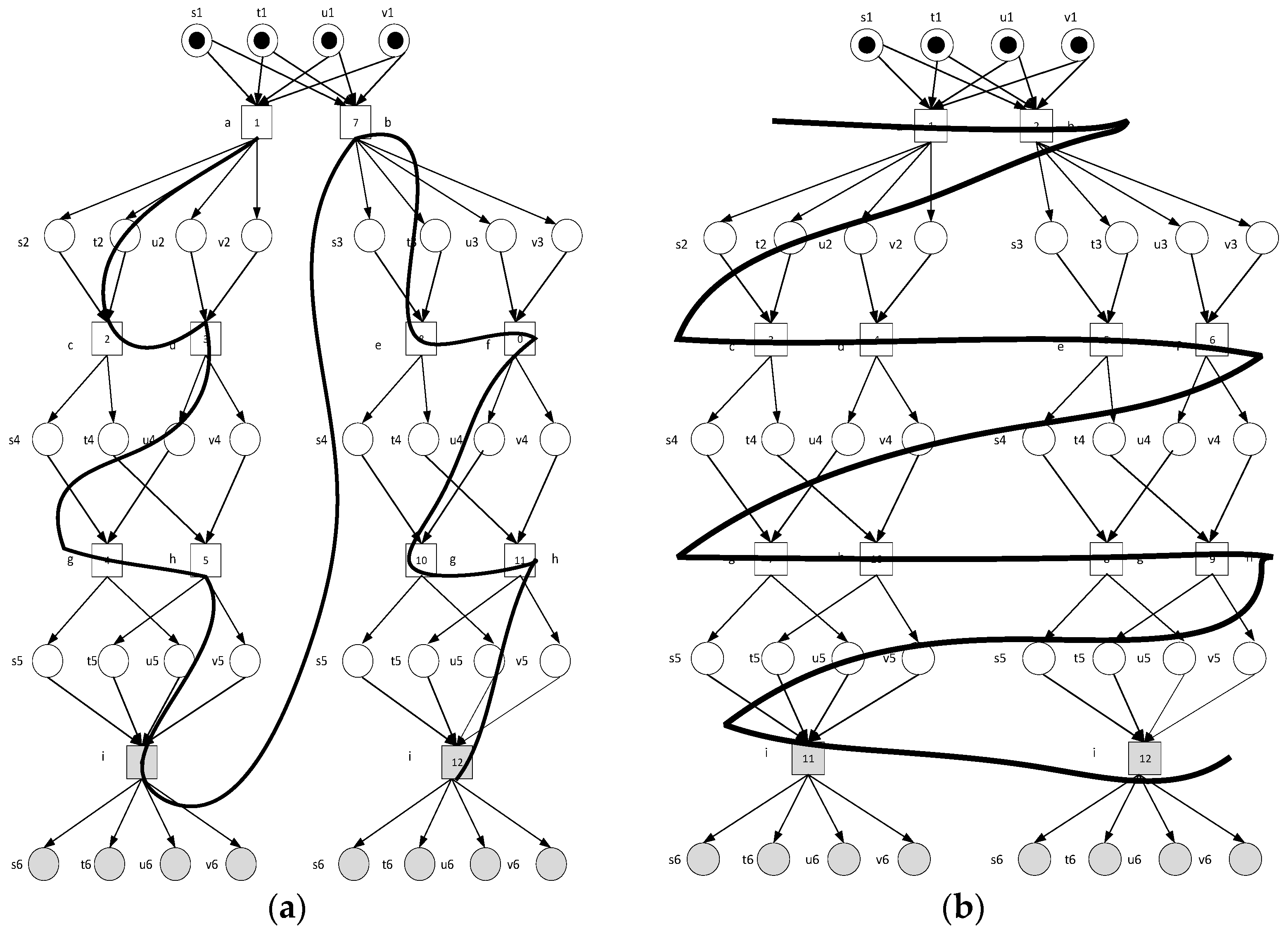
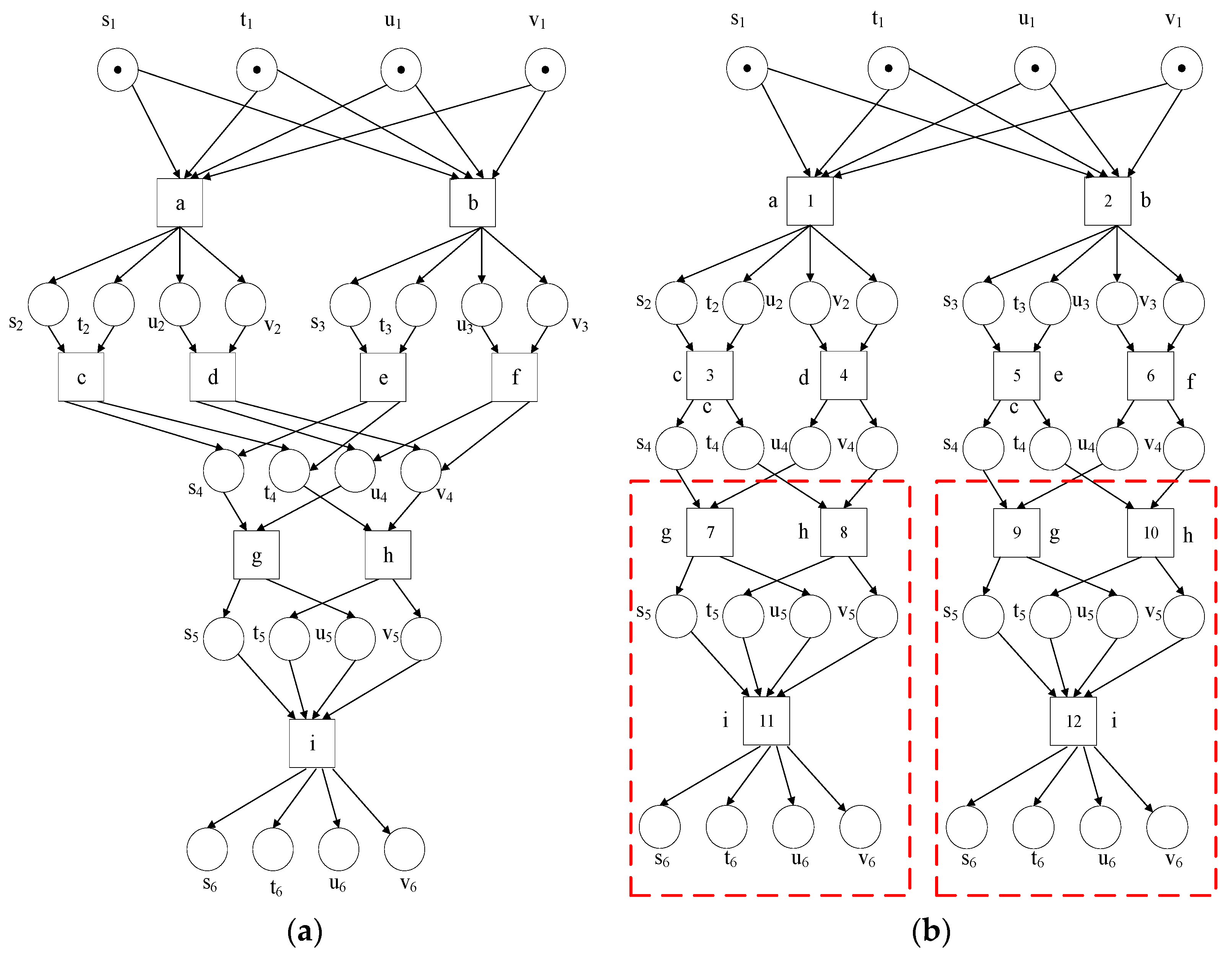
4. Depth-First Unfolding
| Algorithm 2: The Depth-First Unfolding Algorithm |
| input: a Petri net output: a complete prefix of 1. the empty branching processes 2. Push all init of the places from to 3. M0 4. I = 0; // Record the subscript of the event 5. //Enabled events 6. while Ø, do 7. pop //using stack for data structure; 8. i = i + 1; 9. fire e title with ei (Trigger transition event subscript plus 1)) 10. add new instances from to 11. {If similarity (new instances) does not exist in π, new instances of places Superscript j++; 12. else, the superscript j is 0 (0 means there is no superscript)// Counting of newly generated library superscripts starting from 0)} 13. if !C then // Become a new node and cut it the next time it appears 14. else // Become a cutting event (if it already exists, it is a cutting node); 15. End while |
- –
- Determine the set [en] comprising all predecessors of en, i.e., the set of all events em such that the unfolding includes a path from em to e. In this case, [e3] = {e1, e3};
- –
- Select any occurrence sequence σi containing each element of [e] exactly once (which is guaranteed to exist) and allow it to occur. Here, σi = e1e3;
- –
- Let m denote the marking of the unfolding reached by firing σi (which can be proven to be independent of the choice of σi) and define Me as the label of m. In this instance, m = {i, e, h} and Me3 = { i, e, h}.
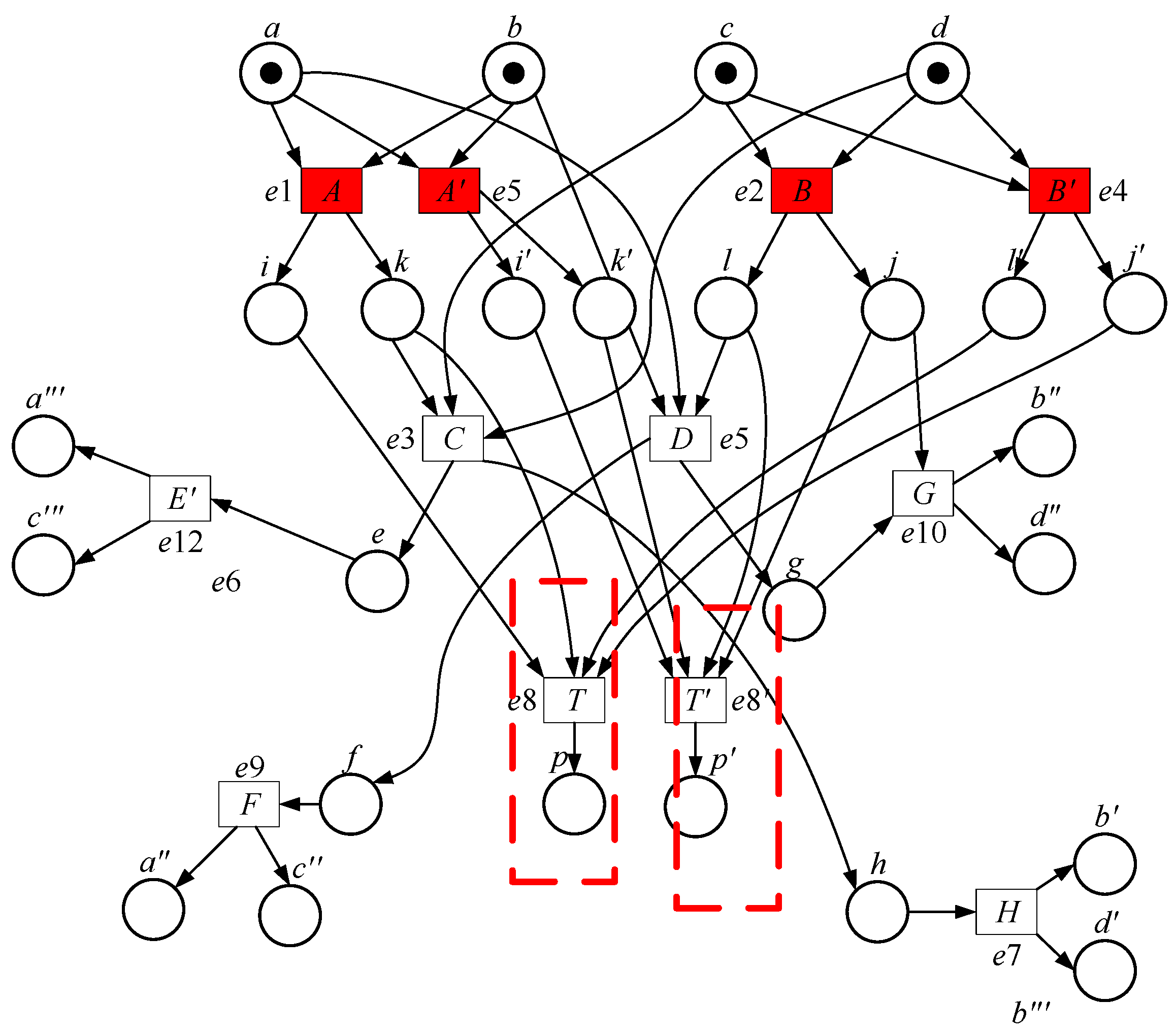
- (a)
- Me(pT) = 1; the algorithm concludes with the result ”reachable”;
- (b)
- Me′ is already known to be reachable: either Me = MI or Me′ = Me for some other event e′. In such a case, e′ is referred to as the corresponding event of e.
5. Equivalence Reduction of Unfolded Nets
6. Case Study and Experiments Result
- (i)
- Soundness: each complete path explored by the algorithm is a consistent path of the Petri net;
- (ii)
- Completeness: the algorithm explores all consistent paths of the Petri net;
- (iii)
- Optimality: each path is explored exactly once.
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Esparza, J.; Kanade, P.; Schwoon, S. A Negative Result on Depth-First Net Unfoldings. Int. J. Softw. Tools Technol. Transf. 2008, 10, 161–166. [Google Scholar] [CrossRef]
- Abdulla, P.A.; Aronis, S.; Atig, M.F.; Jonsson, B.; Leonardsson, C.; Sagonas, K. Stateless model checking for TSO and PSO. Acta Inform. 2017, 54, 789–818. [Google Scholar] [CrossRef]
- Maiya, P.; Gupta, R.; Kanade, A.; Majumdar, R. Partial Order Reduction for Event-Driven Multi-threaded Programs; Springer: Berlin/Heidelberg, Germany, 2016. [Google Scholar]
- Raad, A.; Berdine, J.; Dang, H.-H.; Dreyer, D.; O’hearn, P.; Villard, J. Local Reasoning about the Presence of Bugs: Incorrectness Separation Logic; Springer International Publishing: Cham, Switzerland, 2020. [Google Scholar]
- Chatterjee, K.; Pavlogiannis, A.; Toman, V. Value-centric dynamic partial order reduction. In Proceedings of the ACM on Programming Languages, Phoenix, AZ, USA, 22–26 June 2019. [Google Scholar]
- Kokologiannakis, M.; Marmanis, I.; Gladstein, V.; Vafeiadis, V. Truly stateless, optimal dynamic partial order reduction. In Proceedings of the ACM on Programming Languages, Philadelphia, PA, USA, 16–22 January 2022. [Google Scholar]
- Schemmel, D.; Büning, J.; Rodríguez, C.; Laprell, D.; Wehrle, K. Symbolic Partial-Order Execution for Testing Multi-Threaded Programs. Int. Conf. Comput. Aided Verif. 2020, 12224, 376–400. [Google Scholar]
- Abdulla, P.A.; Aronis, S.; Jonsson, B.; Sagonas, K. Source sets: A foundation for optimal dynamic partial order reduction. J. Assoc. Comput. Mach. 2017, 64, 25.1–25.49. [Google Scholar] [CrossRef]
- Nguyen, H.T.T.; Rodríguez, C.; Sousa, M.; Coti, C.; Petrucci, L. Quasi-Optimal Partial Order Reduction; Springer: Cham, Switzerland, 2018. [Google Scholar]
- Albert, E.; de la Banda, M.G.; Gómez-Zamalloa, M.; Isabel, M.; Stuckey, P.J. Optimal context-sensitive dynamic partial order reduction with observers. In Proceedings of the 28th ACM SIGSOFT International Symposium, Beijing, China, 15–19 July 2019. [Google Scholar]
- Janicki, R.; Mikulski, Ł. Algebraic Structure of Step Traces and Interval Traces. Fundam. Inform. 2020, 175, 253–280. [Google Scholar] [CrossRef]
- Rodríguez, C. Verification Based on Unfoldings of Petri Nets with Read Arcs; Cachan Ecole Normale Supérieure: Cachan, France, 2013. [Google Scholar]
- Lutz-Ley, A.; López-Mellado, E. Stability Analysis of Discrete Event Systems Modeled by Petri Nets Using Unfoldings. IEEE Trans. Autom. Ence Eng. 2018, 4, 1–8. [Google Scholar] [CrossRef]
- Koutny, M. Petri nets and petris nets: A personal perspective. In Carl Adam Petri: Ideas, Personality, Impact; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Janicki, R.; Koutny, M. Operational Semantics, Interval Orders and Sequences of Antichains. Fundam. Inform. 2019, 169, 31–55. [Google Scholar] [CrossRef]
- Baldan, P.; Bruni, A.; Corradini, A.; König, B.; Rodríguez, C.; Schwoon, S. Efficient unfolding of contextual Petri nets. Theor. Comput. Sci. 2012, 449, 2–22. [Google Scholar] [CrossRef]
- Schwarick, M.; Rohr, C.; Liu, F.; Assaf, G.; Chodak, J.; Heiner, M. Efficient Unfolding of Coloured Petri Nets Using Interval Decision Diagrams. In Application and Theory of Petri Nets and Concurrency; Springer: Cham, Switzerland, 2020. [Google Scholar]
- Rodríguez, C.; Schwoon, S. Cunf: A Tool for Unfolding and Verifying Petri Nets with Read Arcs; Springer International Publishing: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Xiang, D.; Liu, G.; Yan, C.; Jiang, C. Checking the Inconsistent Data in Concurrent Systems by Petri Nets with Data Operations. In Proceedings of the 2016 IEEE 22nd International Conference on Parallel and Distributed Systems (ICPADS), Wuhan, China, 13–16 December 2016. [Google Scholar]
- Khomenko, V.; Koutny, M.; Vogler, W. Canonical Prefixes of Petri Net Unfoldings. In Proceedings of the 14th International Conference on Computer Aided Verification, Boulder, CO, USA, 8–12 July 2003. [Google Scholar]
- Pham, T.A.; Jéron, T.; Quinson, M. Unfolding-Based Dynamic Partial Order Reduction of Asynchronous Distributed Programs. Int. Conf. Form. Tech. Distrib. Objects Compon. Syst. 2019, 11535, 224–241. [Google Scholar]
- Kolčák, J.; Šafránek, D.; Haar, S.; Paulevé, L. Unfolding of Parametric Boolean Networks. Electronic Notes in Theoretical Computer Science. Electron. Notes Theor. Comput. Sci. 2018, 335, 67–90. [Google Scholar] [CrossRef]
- Vogler, W.; Semenov, A.; Yakovlev, A. Unfolding and Finite Prefix for Nets with Read Arcs; Springer: Berlin/Heidelberg, Germany, 1998. [Google Scholar]
- Kahkonen, K.; Heljanko, K. Testing Multithreaded Programs with Contextual Unfoldings and Dynamic Symbolic Execution. In Proceedings of the International Conference on Application of Concurrency to System Design, Tunis La Marsa, Tunisia, 23–27 June 2014. [Google Scholar]
- Bonet, B.; Haslum, P.; Khomenko, V.; Thiébaux, S.; Vogler, W. Recent advances in unfolding technique. Theor. Comput. Sci. 2014, 551, 84–101. [Google Scholar] [CrossRef]
- Leon, H.P.D.; Haar, S.; Longuet, D. Model-based Testing for Concurrent Systems: Unfolding-based Test Selection. Int. J. Softw. Tools Technol. Transf. 2016, 18, 305–318. [Google Scholar] [CrossRef]
- Saarikivi, O.; Ponce-De-León, H.; Kähkönen, K.; Heljanko, K.; Esparza, J. Minimizing Test Suites with Unfoldings of Multithreaded Programs. ACM Trans. Embed. Comput. Syst. 2017, 16, 45. [Google Scholar] [CrossRef]
- Fei, L.; Heiner, M.; Ming, Y. An efficient method for unfolding colored Petri nets. In Proceedings of the 2012 Winter Simulation Conference (WSC), Berlin, Germany, 9–12 December 2012. [Google Scholar]
- Visme, M.; Winskel, G. Causal Unfoldings and Disjunctive Causes. arXiv 2020, arXiv:1607.03747. [Google Scholar] [CrossRef] [PubMed]
- Sousa, M.; Rodríguez, C.; D’Silva, V.; Kroening, D. Abstract Interpretation with Unfoldings. In Proceedings of the International Conference on Computer Aided Verification, Heidelberg, Germany, 24–28 July 2017. [Google Scholar]
- Pei, J.; Wen, L.; Ye, X.; Kumar, A. Efficient Transition Adjacency Relation Computation for Process Model Similarity. IEEE Trans. Serv. Comput. 2020, 15, 1295–1308. [Google Scholar] [CrossRef]
- Roman, N.; Irina, L. Asynchronous Interaction Patterns for Mining Multi-Agent System Models from Event Logs. In Proceedings of the Modeling and Analysis of Complex Systems and Processes 2019, Vienna, Austria, 21–23 March 2019. [Google Scholar]
- Bernardinello, L.; Lomazova, I.; Nesterov, R.; Pomello, L. Property-Preserving Transformations of Elementary Net Systems Based on Morphisms; Koutny, M., Kordon, F., Moldt, D., Eds.; Transactions on Petri Nets and Other Models of Concurrency XVI; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2022; Volume 13220. [Google Scholar] [CrossRef]

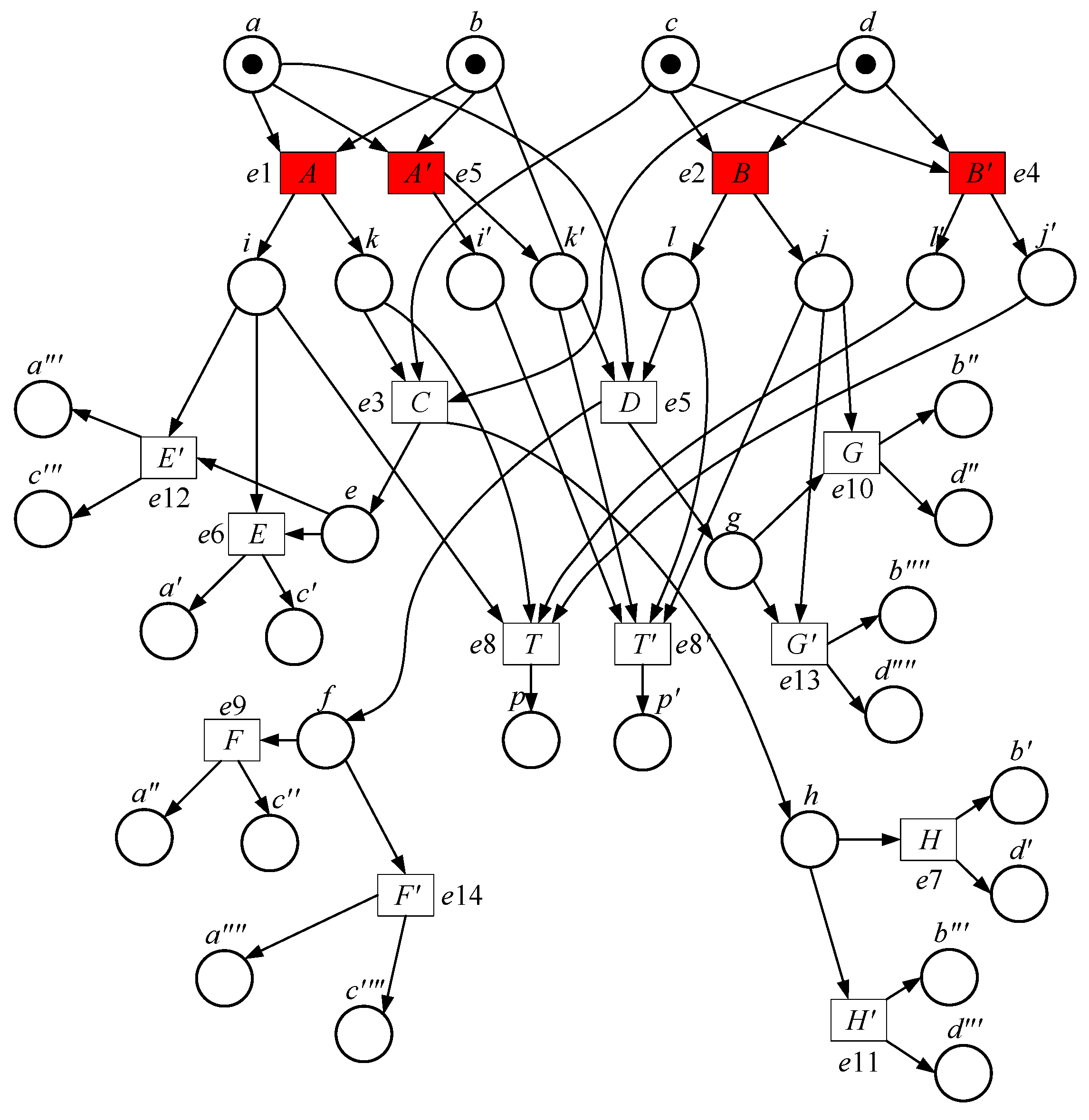

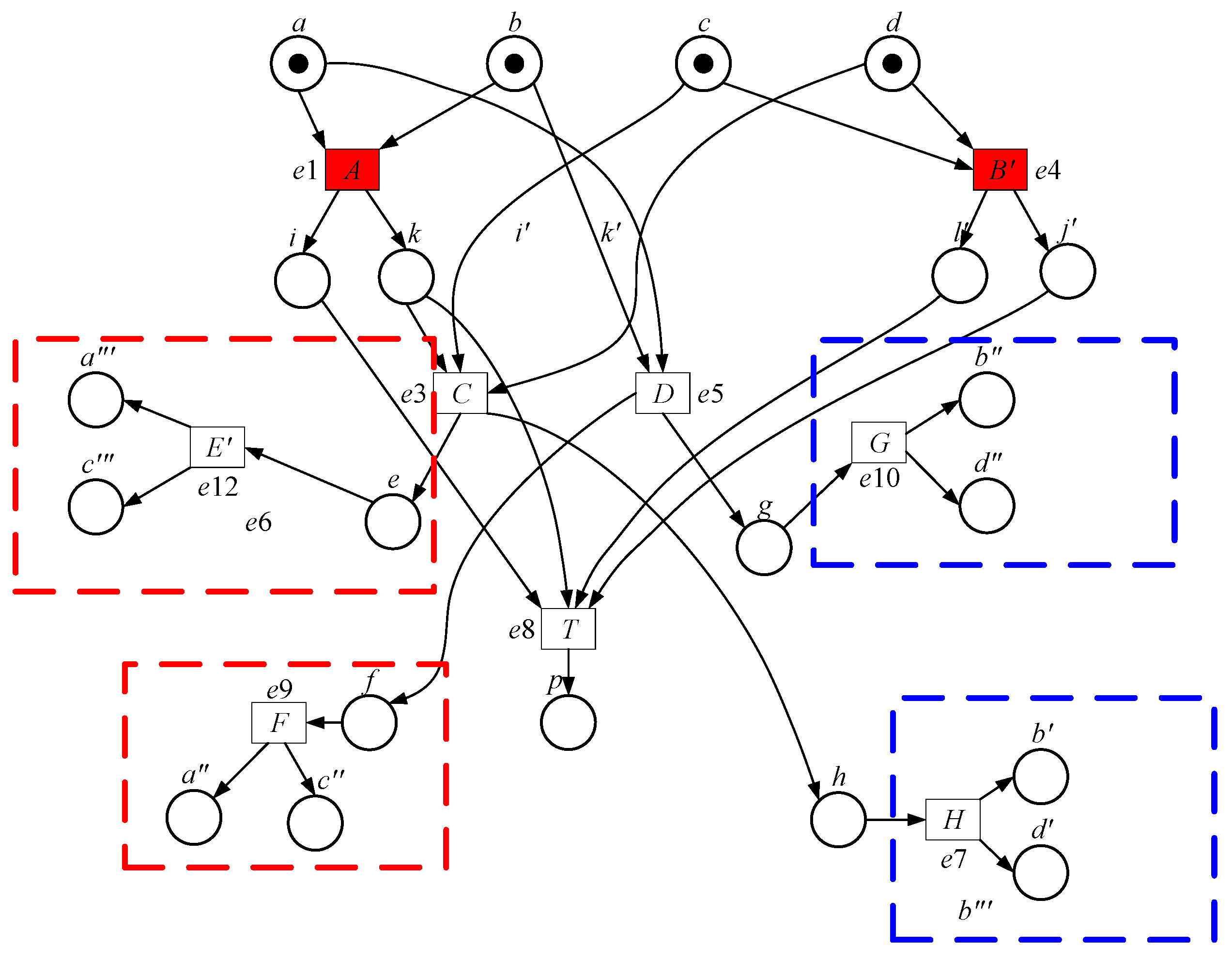
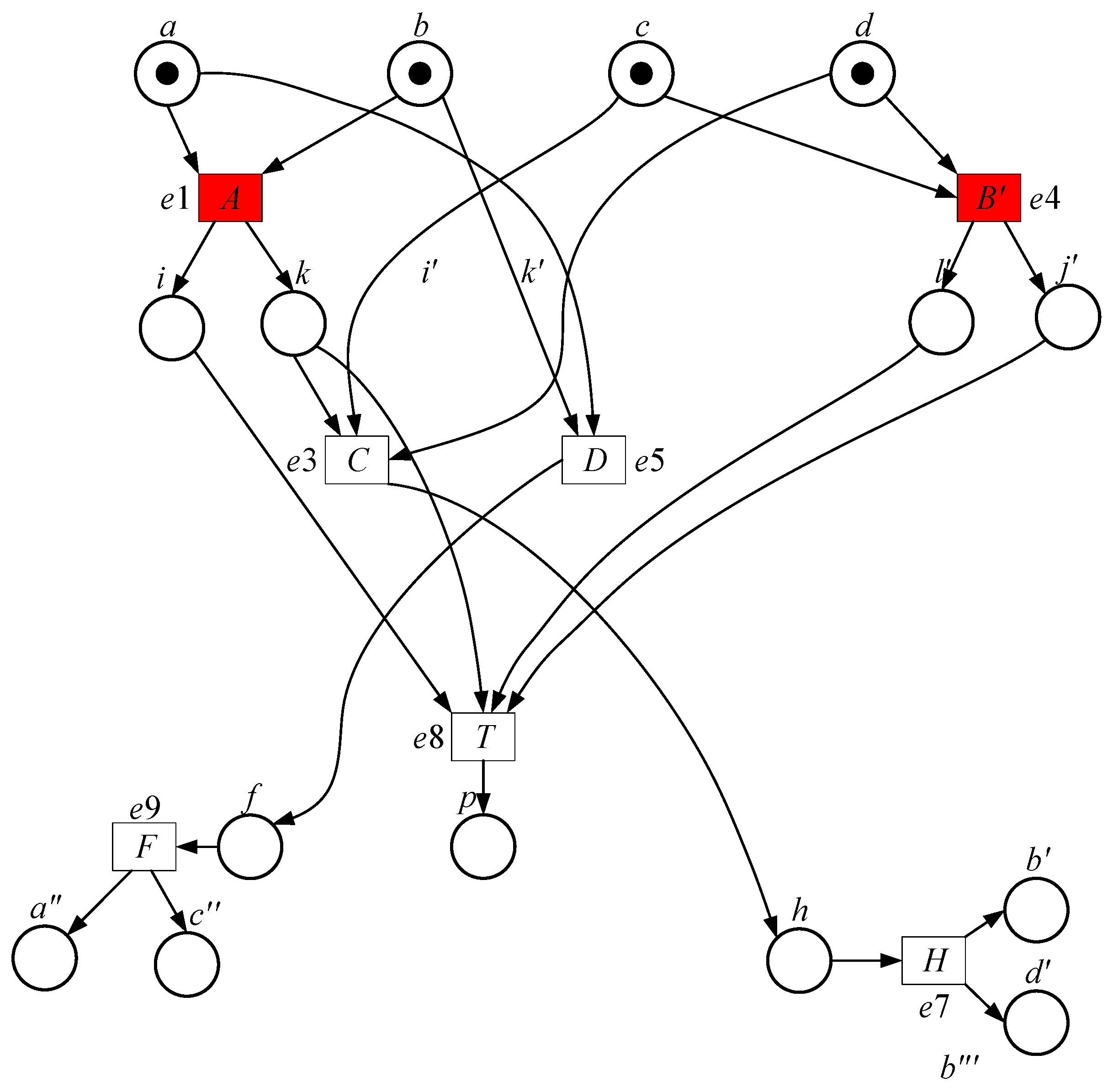


| Marking | Enabled | Select | New Marking | Type |
|---|---|---|---|---|
| a, b, c, d | A, B | A/e1(a, b->i, k) | c, d, i, k | new |
| a, b, c, d | B | B/e2(c, d->l, j) | a, b, l, j | new |
| c, d, i, k | C, B | C/e3(k, c, d->e, h) | i, e, h | new |
| c, d, i, k | B | B′/e4(c, d->l, j) | i, k, l′, j′ | new |
| a, b, l, j | A, D | A′/e5(a, b->i, k) | i′, k′, l, j | new |
| a, b, l, j | D | D/e6(a, b, l->f, g) | f, g, j | new |
| i, e, h | E, H | E/e7(e, i->a, c) | h, a′, c′ | new |
| i, e, h | H | H/e8(h->b, d) | i, e, b′, d′ | new |
| l, k, l′, j′ | T | T/e9(i, k, l, j->p) | P | end |
| i′, k′, l, j | T | T′/e10(i, k, l, j->p) | P | end |
| f, g, j | F, G | F/e11(j->a, c) | a″, c″, g, j | new |
| f, g, j | G | G/e12(g->b, d) | f, b″, d″ | new |
| h, a′, c′ | H | H′/e13(h->b, d) | a, b‴, c, d‴ | Cut-off |
| i, e, b′, d′ | E | E′/e14(e, i->a, c) | a‴, b′, c‴, d′ | Cut-off |
| a″, c″, g, j | G | G′/e15(g->b, d) | a″, b⁗, c″, d⁗ | Cut-off |
| f, b″, d″ | F | F′/e16(j->a, c) | a⁗, b″, c⁗, d″ | Cut-off |
| No | Marking | Enabled Transfer | Selected | New Marking | Type |
|---|---|---|---|---|---|
| 1 | a, b, c, d | A, B | A/e1(a, b->i, k) | c, d, i, k | new |
| 2 | a, b, c, d | B | B/e2(c, d->l, j) | a, b, l, j | new |
| 3 | c, d, i, k | C, B | C/e3(k, c, d->e, h) | i, e, h | new |
| 4 | c, d, i, k | B | B′/e4(c, d->l, j) | i, k, l′, j′ | new |
| 5 | a, b, l, j | A, D | A′/e5(a, b->i, k) | i′, k′, l, j | new |
| 6 | a, b, l, j | D | D/e6(a, b, l->f, g) | f, g, j | new |
| 7 | i, e, h | E, H | E/e7(e, i->a, c) | h, a′, c′ | new |
| 8 | i, e, h | H | H/e8(h->b, d) | i, e, b′, d′ | new |
| 9 | l, k, l′, j′ | T | T/e9(i, k, l, j->p) | P | end |
| 10 | i′, k′, l, j | T′ | T′/e10(i, k, l, j->p) | P | end |
| 11 | f, g, j | F, G | F/e11(j->a, c) | a″, c″, g, j | new |
| 12 | f, g, j | G | G/e12(g->b, d) | f, b″, d″ | new |
| No | Init | Enabled | Select | New | Type |
|---|---|---|---|---|---|
| 1 | a, b, c, d | A, B | A/e1(a, b->i, k) | c, d, i, k | New |
| 2 | a, b, c, d | B | B/e2(c, d->l, j) | a, b, l, j | New |
| 3 | c, d, i, k | C, B | C/e3(k, c, d->e, h) | i, e, h | New |
| 6 | a, b, l, j | D | D/e6(a, b, l->f, g) | f, g, j | New |
| 8 | i, e, h | H | H/e8(h->b, d) | i, e, b′, d′ | New |
| 9 | l, k, l′, j′ | T | T/e9(i, k, l, j->p) | P | end |
| 11 | f, g, j | F, G | F/e11(j->a, c) | a″, c″, g, j | Init |
| ERV Unfolding | Similarity Unfolding | Accuracy | |||||
|---|---|---|---|---|---|---|---|
| Exe | M | Time | Exe | M | Time | ||
| SecN (10) | 3328 | 46 | 0 | 1228 | 22 | 0 | 55% |
| SecN (15) | 147,456 | 46 | 9 | 20,456 | 47 | 11 | 65% |
| SecN (20) | 6,029,312 | 46 | 455 | 6,029,312 | 23 | 127 | 60% |
| PeN (8) | 10,080 | 182 | 1 | 10,080 | 46 | 1 | |
| PeN (16) | oom | oom | oom | 80,640 | 46 | 10 | |
| exp-p (9) | oom | oom | oom | 725,760 | 46 | 103 | |
| exp-p (4) | 20,736 | 55 | 1 | 12,736 | 26 | 1 | 57% |
| exp-p (5) | 705,600 | 326 | 58 | 705,600 | 26 | 32 | 59% |
| exp-p (6) | oom | 33 | 177 | 600 | 26 | 1757 | 62% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yang, X.; Ye, C.; Chen, Y. Depth-First Net Unfoldings and Equivalent Reduction. Symmetry 2023, 15, 1775. https://doi.org/10.3390/sym15091775
Yang X, Ye C, Chen Y. Depth-First Net Unfoldings and Equivalent Reduction. Symmetry. 2023; 15(9):1775. https://doi.org/10.3390/sym15091775
Chicago/Turabian StyleYang, Xu, Chen Ye, and Yijun Chen. 2023. "Depth-First Net Unfoldings and Equivalent Reduction" Symmetry 15, no. 9: 1775. https://doi.org/10.3390/sym15091775
APA StyleYang, X., Ye, C., & Chen, Y. (2023). Depth-First Net Unfoldings and Equivalent Reduction. Symmetry, 15(9), 1775. https://doi.org/10.3390/sym15091775






