Abstract
With the maturity and popularization of the Internet of Things, we saw the emergence of the Internet of Vehicles. This collects and processes real-time traffic information, alleviates traffic congestion, and realizes intelligent transportation. However, sensitive information, such as real-time driving data of vehicles, are transmitted on public channels, which are easily to steal and manipulate for attackers. In addition, vehicle communications are vulnerable to malicious attacks. Therefore, it is essential to design secure and efficient protocols. Many studies have adopted asymmetric cryptosystems and fog computing to in this environment, but most of them do not reflect the advantages of fog nodes, which share the computational burden of cloud servers. Therefore, it is challenging to design a protocol that effectively uses fog nodes. In this paper, we design an authentication protocol based on a symmetric encryption algorithm and fog computing in the Internet of Vehicles. In this protocol, we first propose a four-layer architecture that significantly reduces the computational burden of cloud servers. To resist several well-known attacks, we also apply Intel software guard extensions to our protocol. This is because it can resist privileged insider attacks. We prove the security of the proposed protocol through the Real-Or-Random model and informal analysis. We also compare the performance of the proposed protocol with recent protocols. The results show better security and a lower computational cost.
1. Introduction
With the maturity and popularization of the Internet of Things (IoT) [1,2], a special network connecting vehicles through the Internet has emerged: the Internet of Vehicles (IoV) [3,4,5]. The IoV is a subset of the IoT that realizes communication by vehicle-to-vehicle (V2V), vehicle-to-pedestrian (V2P), and vehicle-to-infrastructure (V2I) connections. The IoV collects, processes, and shares road information in real time, alleviates traffic congestion in traffic control, and reduces traffic accidents through early warnings to ensure vehicle safety. It also realizes intelligent transportation to improve its efficiency.
Previously, researchers introduced cloud computing into the IoV to efficiently process large amounts of real-time road information. With an increasing number of vehicles, the computational burden of the cloud server (CS) is also increasing. The authors of [6,7,8] proposed a definition of fog computing. Compared with cloud computing, fog computing has the characteristics of low latency, large numbers, wide distribution, and lighter computing. Fog and cloud computing are complementary but not substitutes. Cloud computing realizes the calculation or storage of a large amount of data, compensating for the lack of computing resources for fog nodes.
Recently, the literature [9,10,11,12] has involved research on authenticated key agreement (AKA) protocols for applying fog computing to the IoV. In 2019, Ma et al. [9], based on asymmetric cryptosystems and fog computing, proposed an AKA protocol. The protocol used the traditional three-layer architecture: “vehicle–fog node–CS”, where the vehicle and roadside unit (RSU) play the participant (i.e., vehicle). However, the protocol showed that the participation of a CS was required for each authentication, which did not reflect the advantages of fog nodes and did not realize the function of fog nodes sharing the computational burden of a CS. Moreover, Eftekhari et al. [10] found that the protocol [9] was insecure and vulnerable to stolen smart card attacks, known session-specific temporary information disclosure attacks, and privileged insider attacks. Based on this architecture, Eftekhari et al. [10] designed an improved protocol that did not reflect the advantages of fog nodes. In 2020, Wu et al. [11] proposed a fog-based AKA protocol based on the traditional three-layer architecture. However, the RSU was a fog node. Each communication required the participation of a CS. In 2021, following the architecture presented in [11], Wu et al. [12] proposed a lightweight AKA protocol that still did not realize the function of fog nodes sharing the computational burden of a CS.
Although the above AKA protocols [9,10,11,12] use fog computing, they fail to realize the function of fog nodes sharing the computational burden of a CS. This is because in the conventional architecture, fog nodes actually replace the RSU, and computing is still on the CS, which does not reduce the computational burden of the CS. Therefore, we first propose a four-layer architecture: “vehicle–RSU–fog node–CS”. The four-layer architecture of the IoV based on fog computing is shown in Figure 1. In this architecture, when a vehicle enters the road and wants to communicate with the RSU, the communication modes are divided into the following two cases:
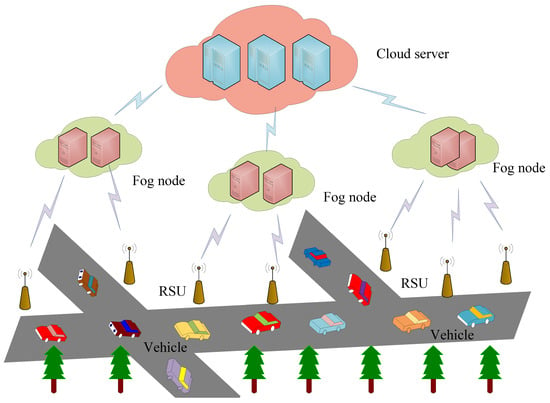
Figure 1.
The four-layer architecture of the based on fog computing.
- 1.
- Case 1: The RSU judges that the vehicle communicates with itself for the first time and then sends a data request to the CS. The CS sends a response to the RSU accordingly and simultaneously sends the data response to the fog node. Thereafter, the vehicle and RSU realize their communication with the assistance of the fog node. The four entities involved in this communication process are the vehicle, RSU, fog node, and CS.
- 2.
- Case 2: This extends from Case 1. Only the fog node (without the participation of the CS) can help the vehicle and RSU to realize communication. Here, this architecture effectively realizes the function of the fog node sharing the computational burden of the CS.
The IoV environment still has some security challenges. For example, sensitive information such as vehicle real-time driving data are transmitted on a public channel, which is easy to steal from and manipulate for an attacker, resulting in the disclosure of vehicle privacy. In addition, the process of vehicle communication is vulnerable to replay attacks [13], impersonation attacks [14,15,16], and privileged insider attacks [9], among others. Therefore, to ensure communication and protect the sensitive data of vehicles, a safe and effective protocol must be designed.
Due to the above security challenges of the IoV environment, researchers are committed to enhancing the security of the IoV. Therefore, a hardware-based, trusted execution environment called software guard extensions (SGX) [17,18,19] has emerged. SGX is secure hardware developed by Intel. The difference between SGX and other security software is that it only includes hardware, which avoids software vulnerabilities and malicious threats in the system and largely ensures system security. In addition, SGX provides a trusted execution environment, as malicious code cannot access or tamper with any sensitive data stored in SGX, guaranteeing data confidentiality and integrity. The structure of SGX mentioned in [17]. Preserved random memory (PRM) is a reserved area for SGX in the dynamic memory, and the Enclave Page Cache (EPC) is a part of the PRM. SGX has a secure container called Enclave, which is stored in the EPC to store sensitive data and code. The user enters the value into the Enclave through the Ecall. After SGX completes the confidential computing in the Enclave, it returns the computational results through Ocall.
To ensure secure communication and reduce the computational burden of the CS, we propose an authentication protocol under a four-layer architecture. We also apply SGX and a symmetric encryption algortihm to the proposed protocol to resist several well-known attacks. Our main contributions are as follows:
- (1)
- We first propose a four-layer architecture in the IoV environment as shown in Figure 1. Adopting such an architecture reduces the computational pressure of the CS.
- (2)
- We apply SGX to store the private value of the fog node and RSU in SGX so that even if the attacker obtains the data in the authentication table, he or she cannot obtain the private values in SGX. In other words, SGX can make the proposed protocol resist privileged insider attacks and enhance the security of the protocol.
- (3)
- We prove the security of the proposed protocol through the Real-Or-Random model (ROR) and informal analysis. Furthermore, we compare the performance of the proposed protocol with recent protocols, with the results showing better security and a lower computational cost.
The rest of the paper is organized as follows. Section 2 briefly reviews the relevant research work. Section 3 describes the system model and proposed protocol in detail. In Section 4, we use the ROR model and informal analysis to prove the protocol’s security. We compare the performance of the proposed protocol with recent protocols and discuss the obtained results in Section 5. Finally, we provide a brief summary of the content of this study in Section 6.
2. Related Work
Researchers have conducted extensive research on security challenges based on the IoV [20,21]. In 2007, Raya et al. [22] determined that information transmission security should be ensured in the IoV. Therefore, cryptographic technology, namely the public key infrastructure (PKI) mechanism, was introduced into the proposed protocol. Although this technology ensured that the vehicles privacy was not leaked, the computational cost was extremely high. In 2011, Huang et al. [23] designed an AKA protocol for value-added services known as ABAKA. The protocol realized anonymity but used elliptic curve cryptography (ECC), and the overhead remained extremely high. In 2017, Ying et al. [13] designed a protocol and claimed that it realized anonymous and secure communication. The protocol had a low computational cost and was lightweight. Mohit et al. [14] proposed a secure authentication protocol that configured vehicle sensors for the IoV to monitor the vehicle and the surrounding environment. However, Yu et al. [15] found that the protocol [14] was vulnerable to user impersonation attacks and could not provide anonymity or mutual authentication. Yu et al. [15] designed an improved protocol for ensuring communication security. However, Sadri et al. [24] found that the protocol [15] was vulnerable to user impersonation and sensor capture attacks and could not provide untraceability. Sadri et al. [24] designed a secure protocol based on this. In 2021, Jiang et al. [25] designed an authentication protocol based on a physical unclonable function (PUF). This protocol effectively combined biometrics and a PUF to achieve secure identification and authentication. In the same year, Kurma et al. [26] designed a new authentication protocol for the IoV. The protocol [26] was based on radio frequency identification, which increased the protocol security and used ECC at a high computational cost.
In previous years, to achieve efficient authentication, the literature [27,28] adopted the cloud computing architecture to different environments. Later, researchers found that fog computing is more suitable for the IoV than cloud computing with a large amount of real-time data to process. Therefore, scholars have applied fog computing to the IoV to reduce the computational burden of the CS. Wazid et al. [29] proposed a protocol based on authentication key management (AKM) between two different entities, namely AKM and the IoV, to realize security authentication in the IoV. Han et al. [30] proposed a security protocol based on fog computing [30], which had two highlights. One was that the vehicle and RSU were self-authenticated without the participation of the trusted authority (TA), which improved the communication efficiency. The other was that the fog node managed the pseudonym of the vehicle to realize privacy protection. Soleymani et al. [31] designed a message authentication protocol that used bilinear pairing primitives with a high overhead. The protocol [31] also used pseudonym management for privacy protection. Ma et al. [9], based on asymmetric cryptosystems and fog computing, proposed an AKA protocol. The protocol used ECC at a high computational cost, and they claimed that the protocol was provably secure. However, Eftekhari et al. [10] found that the protocol [9] was vulnerable to known session-specific temporary information disclosure, privileged insider, and stolen smart card attacks. Eftekhari et al. [10] proposed an improved lightweight protocol. Wu et al. [11] proposed an AKA protocol. The protocol also used ECC, which had a large computational cost and computational burden from the CS under the architecture used. In 2021, Wu et al. [12] designed a lightweight AKA protocol, which was also based on the above architecture and did not realize the function of fog nodes sharing the computational burden of the CS. The main works related to this paper are summarized in Table 1.

Table 1.
Summary of authentication protocols.
3. The Proposed Protocol: SGXAP
This section introduces the system model and the proposed protocol in detail. Definitions and specific descriptions of the symbols used in the protocol are listed in Table 2.

Table 2.
Notations used in the protocol.
3.1. System Model
The system includes four entities: the vehicle, RSU, fog node, and CS. In this model, the RSUs know which fog nodes they are deployed in, and the CS also knows which fog node RSU is deployed. These four entities, namely the definition, function, computing power, and storage capability of each role, are explained in detail below:
- (1)
- Vehicle: This refers to the vehicle or vehicle user who selects the appropriate speed or driving route by acquiring the relevant real-time road information collected by the RSU.
- (2)
- RSU: This is a semi-trusted device that collects real-time road condition information. It is arranged on both sides of the road and has weak computing power and storage capacity. The RSU judges whether the vehicle is communicating with itself for the first time.
- (3)
- Fog node: This is a semi-trusted entity with certain computing power. It quickly processes the road condition information collected by the RSU and can store data. As a third party, the fog node participates in communicating between the vehicle and RSU.
- (4)
- CS: This is a semi-trusted entity which can realize the calculation or storage of a large amount of data. Here, the CS is the registration center, which participates in registering vehicle, RSU, and fog node. For Case 1, it is also the data transmitter.
When the vehicle wants to communicate with the RSU, there are two communication modes:
- 1.
- Case 1 is shown in Figure 2. The RSU judges that the vehicle communicates with itself for the first time and sends a data request to the CS. Then, the CS transmits the private value of the vehicle to the fog node and RSU. Here, the RSU stores the private data of the vehicle to judge whether the communication between the vehicle and itself is happening for the first time. The fog node stores information about the vehicle to realize the authentication process. Finally, the vehicle and RSU realize communication through the fog node.
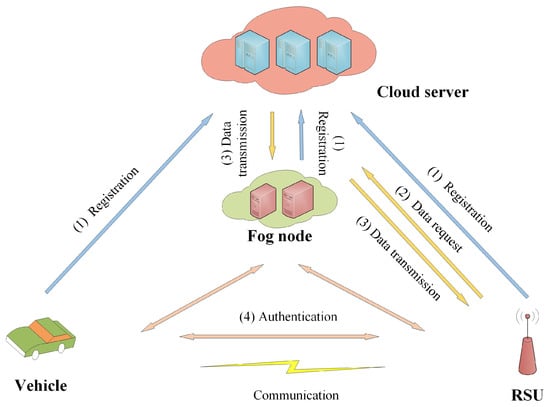 Figure 2. System model of Case 1.
Figure 2. System model of Case 1. - 2.
- Case 2 is shown in Figure 3. This case extends Case 1. Therefore, only the fog node (without the participation of the CS) can help the vehicle and RSU to realize communication. This is because in the first communication, the fog node and RSU know the private information of the vehicle. Here, this architecture dramatically reduces the computational burden of the CS.
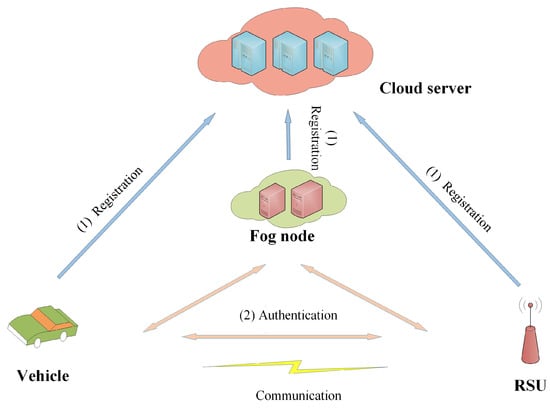 Figure 3. System model of Case 2.
Figure 3. System model of Case 2.
3.2. The Proposed SGXAP
The proposed protocol comprises three phases: registration, login authentication, and data transmission.
3.2.1. Registration Phase
The registration phase of the proposed protocol includes the , , and registration phases.
In the registration phase, registers with the , as shown in Figure 4. The detailed registration steps are as follows:
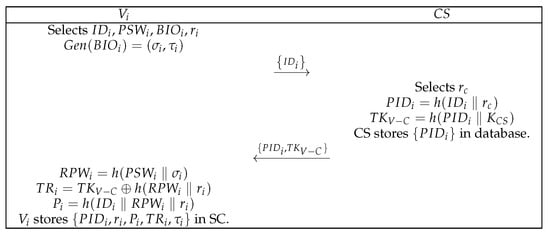
Figure 4.
registration phase.
- (1)
- First, selects the , password , biometrics , and random number , computes , and finally transmits to the .
- (2)
- After receives the message , it selects , computes and , and then saves the pseudo identity in the database before finally transmitting to .
- (3)
- After receives the message , it computes , , and . Finally, stores in the smart card (SC).
In the registration phase, registers with the , as shown in Figure 5. The detailed registration steps are as follows:
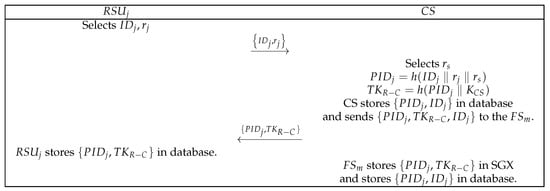
Figure 5.
registration phase.
- (1)
- First, selects the and random number and then transmits to the .
- (2)
- After the receives the message , it selects , computes and , saves in the database, transmits to , and sends to .
- (3)
- After receives the message , it stores in the database.
- (4)
- After receives the message , it stores in SGX and stores in the database.
In the registration phase, registers with the , as shown in Figure 6. The detailed registration steps are as follows:
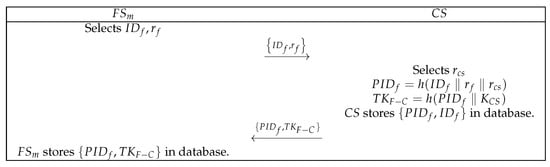
Figure 6.
registration phase.
- (1)
- First, selects the identity and random number and then transmits to the .
- (2)
- After the receives the message , it selects , computes and , saves in the database, and transmits to .
- (3)
- After receives the message , it stores in the database.
3.2.2. Login and Authentication Phase
The vehicle and RSU achieve authentication and establish a session key with the assistance of the fog node to realize secure communication. The authentication of the proposed protocol has the following two cases:
- 1.
- Case 1. communicates with under for the first time. The authentication process needs the assistance of and the participation of the . When receives the message sent by , it cannot retrieve the private value of through the pseudo-identity . Then, enters the data transmission phase and sends a data request to the . After the successfully verifies , it sends the private value of to and , and then and store the private value. Finally, , , and continue to realize relevant authentication. The entire process includes the authentication phase of Figure 7 and the data transmission phase of Figure 8.
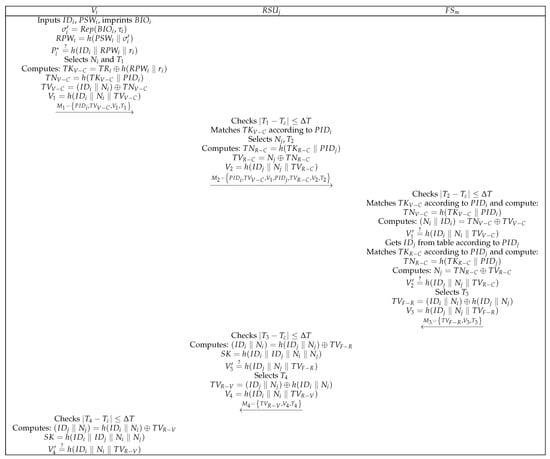 Figure 7. Login and authentication phase.
Figure 7. Login and authentication phase.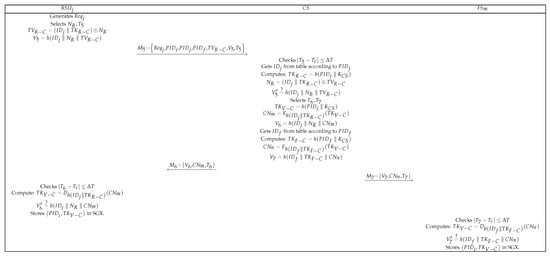 Figure 8. Data transmission phase.
Figure 8. Data transmission phase. - 2.
- Case 2. has communicated with under . Therefore, the private value of is stored in and , and the entire authentication process can be realized without the participating. The process is the login authentication phase, as shown in Figure 7.
The entities in the authentication phase include , , and without the participating. The specific authentication steps are illustrated in Figure 7.
- (1)
- first enters its own , , and , and the SC computes , , and and compares . If they are equal, then the login is successful. Otherwise, the login fails. After successfully logging in to the SC, selects a random number and timestamp and computes , , , and . Finally, sends the message to .
- (2)
- After receives from , it first checks the freshness of the timestamp . If the limit is exceeded, then the authentication is suspended. Otherwise, the authentication continues. Then, indexes stored in SGX according to . If it cannot be indexed, then it indicates that is communicating with for the first time. Here, sends a data request to the , requesting the to send the private value of to itself and , as shown in Figure 8, and then continue to realize the authentication process. If it can be indexed, is not communicating with for the first time, and the authentication process continues. Later, selects , and computes , , and . Finally, sends the message to .
- (3)
- After receives from , it checks the freshness of and then sends to the security interface of SGX. SGX matches the secret value according to , computes , and outputs the secret value from the secure interface after the computation is completed. Then, computes and and compares . If they are equal, this indicates that is legal. Otherwise, the authentication is suspended. finds the identity according to and then sends to the security interface of SGX. SGX matches the secret value according to , computes , and outputs the secret value from the secure interface. Then, computes , and compares . If they are equal, is legal. Otherwise, the authentication is suspended. After authenticating and , selects timestamp , computes , , and finally sends the message to .
- (4)
- After receives the message from , it checks the freshness of and computes , , and . Then, compares . If they are equal, is legal. Otherwise, the authentication fails. After the authentication is successful, selects the timestamp and computes and . Finally, the message is sent to .
- (5)
- After receives from , it first checks the freshness of and then computes , , and . Then, compares . If they are equal, is legal. Otherwise, the authentication fails.
3.2.3. Data Transmission Phase
When communicates with under for the first time, the private value of is not stored in or . Thus, requests private data from the . The entities in this phase include , , and the . According to Case 1, when receives the message sent by and does not retrieve the privacy value of through , requests data from the , as shown in Figure 8. The specific steps are as follows:
- (1)
- generates a data request , selects and , and computes and . Finally, the message is sent to the .
- (2)
- After the receives from , it checks the freshness of . After finding according to , the computes , , and and compares . If they are equal, is legal. Otherwise, the authentication is suspended. Then, selects and and computes , , and . The finds according to and computes , , and . Finally, the message is sent to , and is sent to .
- (3)
- After receives from the , it checks the freshness of , computes and , and compares . If they are equal, then is legal. Otherwise, the authentication is suspended. Finally, stores in SGX.
- (4)
- After receives the message from the , it checks the freshness of , computes and , and compares . If they are equal, then the is legal. Otherwise, the authentication is suspended. Finally, stores in SGX.
After completing the above data request, , , and continue the authentication process.
4. Security Analysis
4.1. Formal Security Analysis
The ROR model, proposed by Canetti et al. [32], calculates the probability that the attacker (A) can break the through multiple query operations to prove the security of the protocol. Here, we compute the probability of cracking the and prove that our protocol is secure.
4.1.1. Adversary Model
We used the Dolev–Yao and Canetti–Krawczyk models to define the capabilities of A [33,34]. The specific capabilities are as follows:
- (1)
- A can intercept, interrupt, forge, and replay the information transmitted on the common channel.
- (2)
- A can act as malicious insiders of the fog nodes and CS to obtain internal information.
- (3)
- A can guess the identities or passwords of vehicles by violent cracking.
- (4)
- A can obtain the values in the vehicle’s smart card.
- (5)
- A can obtain the private key of the CS and a random number of four entities.
Here, we use , , and to represent the m-th , n-th , and z-th instances, respectively. Here, we assume that the query capabilities of A are , , and :
- (1)
- : A intercepts messages transmitted on the common channel;
- (2)
- : A sends message M to entity Y and receives a response;
- (3)
- : A enters a character string of any length and returns the corresponding hash value;
- (4)
- : A can obtain the private value of an entity;
- (5)
- : A flips a coin C. If , then A can obtain . If , A can obtain any string of the same length as the .
4.1.2. Security Requirements
The secure AKA protocol should meet the following security requirements:
- 1.
- User anonymity and untraceability: A can neither obtain the real identity of the communication entity nor trace the session key of the communication process through the data transmitted on the public channel.
- 2.
- Resistance of common attacks: The secure AKA protocol should be able to resist the following attacks:
- (1)
- Privileged insider attacks: As an A, the insiders of the communication entity spy on the private data stored in the database to disguise as a legal entity or obtain the session key;
- (2)
- Impersonation attacks: A intercepts and decrypts the data transmitted on the public channel, disguises as a legal entity, communicates with other entities, and establishes a session key;
- (3)
- Known temporary information disclosure attacks: A calculates the session key in the communication process by obtaining the random number of an entity and the data transmitted on the public channel;
- (4)
- Man-in-the-middle attacks: A intercepts the data transmitted on the public channel, tampers with the data, and establishes the session key with the legal entity without the knowledge of both parties of the communication entity;
- (5)
- Offline password guessing attacks: A intercepts the verification value containing the password stored on the public channel or in the smart device, repeatedly guesses the password, calculates the verification value in the offline state, and compares it with the intercepted verification value until the two values are equal;
- (6)
- Replay attacks: A repeatedly sends the message transmitted on the public channel to the communication entity so as to deceive the entity and interfere with normal communication;
- (7)
- Stolen smart card attacks: After A steals the smart card and obtains the parameters about the entity identity before using the parameters to launch camouflage attacks or malicious acts.
Theorem 1.
Suppose that A can execute the above queries and the probability that A can break the proposed protocol P in polynomial time is . Here, refers to the number of queries executed, refers to the number of times the hash is executed, l refers to the bit length of the biological information, and and refer to two constants.
Proof.

We define seven games – to simulate the attack process of A. In the proof, represents the probability that A can win multiple rounds of the game. The process of A simulating the query is shown in Table 3. The proof steps are as follows:

Table 3.
The process of Send, Execute, Corrupt, and Test queries.
: In the ROR model, the simulation of is consistent with a real attack. Therefore, we have
: and are different from the add Execute() operation. In , A can intercept transmitted on the common channel. When ends, A executes a Test() query to compute the , where . As is confidential to A, the probability of is equal to . The probability of is
: The difference between and is that adds the Send() operation. According to Zipf’s law [35], the probability of is expressed as
: adds the Hash() operation and reduces the Send() operation. According to the birthday paradox, the probability of is
: In , A obtains temporary information to verify that it is resistant to known temporary information disclosure attacks. A can obtain a random number for one of the two parties: and . Suppose A obtains a random number . As , , and are unknown, the cannot be computed. Similarly, if the random number is leaked, then the cannot be computed by A. Therefore, the probability of is expressed as
: In this game, A executes the Corrupt() query to obtain the parameters in the smart card. Legitimate users typically use low-entropy passwords. A may attempt to extract the password by executing an offline password guessing attack using the parameters . However, in our protocol, A cannot obtain without the biometric information and secret credential . The probability of A guessing one bit of biological information is . According to Zipf’s law [35], when , the probability that A can guess a password is greater than 0.5. These results prove that the proposed protocol is resistant to offline password guessing attacks. Therefore, we can derive
: This game verifies whether the proposed protocol is resistant to impersonation attacks. The difference between and is that A uses for the query operation, and the probability of successfully obtaining is
The probability of the success and failure of is 1/2. Therefore, the probability that A can guess is
Using these formulas, we obtain
Therefore, we can obtain
□
4.2. Informal Security Analysis
4.2.1. Mutual Authentication
The proposed protocol realizes mutual authentication using . uses to verify the legitimacy of and to verify the legitimacy of . uses to verify the legitimacy of , and uses to verify the legitimacy of . Therefore, the proposed protocol can achieve mutual authentication.
4.2.2. Replay Attacks
The timestamps are used by the protocol to resist replay attacks. Here, we consider as an example. When receives message of , it first checks the freshness of . If is valid, then the authentication continues. Otherwise, authentication is suspended. Suppose A intercepts and repeatedly sends it to . When checks the freshness of , exceeds this time, and the authentication process stops. Therefore, the proposed protocol can resist replay attacks.
4.2.3. Privileged Insider Attacks
Suppose that A can obtain the value from a party’s database. Here, we consider as an example. Based on this assumption, A can obtain the values stored in the database. However, because the protocol uses a secure hardware SGX, the values stored in SGX are not available. Therefore, A cannot obtain the value required to compute the , where . Therefore, the proposed protocol can resist privileged insider attacks.
4.2.4. Man-in-the-Middle Attacks
Suppose that A can intercept in the common channel. Here, we consider an intercept between and as an example. Because A does not know the values of or in the smart card, A cannot compute the values of required by , where . Thus, the legitimacy of cannot be verified in . The same applies for A attempting to intercept . Therefore, the proposed protocol can resist man-in-the-middle attacks.
4.2.5. User Anonymity and Untraceability
In our protocol, the identities of , , and are not transmitted to the common channel, but pseudo-identities are transmitted. A cannot know the identities of the three, thus realizing anonymity. Because random numbers and used in are variable in every session, A cannot track , , or . Therefore, our protocol provides anonymity and untraceability.
5. Comparisons and Discussions
In this section, we compare the proposed protocol with the AKA protocols proposed by Ma et al. [9], Wazid et al. [29], Eftekhari et al. [10], and Wu et al. [11] in terms of security and performance.
5.1. Security Comparisons
Table 4 presents the comparison results in terms of security. Here, indicates that the protocol can resist the attack, × indicates that the protocol is vulnerable to the attack, and − demonstrates that it is not mentioned whether the protocol can resist it. As shown in the table, the protocol of Ma et al. [9] is vulnerable to privileged insider attacks, known specific temporary information disclosure attacks, and stolen smart card attacks. The protocol proposed by Wazid et al. [29] is vulnerable to impersonation attacks. The other protocols and the proposed protocol are secure.

Table 4.
Comparisons of security.
5.2. Performance Comparison
In this part, we compare the proposed protocol with the current AKA protocols for computational and communication costs. Because the authentication phase of the proposed protocol has two cases, the calculations of the computational and communication costs are also divided into two cases.
To calculate the computational cost, we considered two cases of the proposed protocol as examples. In Case 1, and have no privacy value of . Therefore, the CS must transmit the privacy value to and to realize the entire authentication process. This situation requires the participation of the CS. Therefore, when calculating the computational cost, in addition to calculating the computational cost of the three parties involved in the authentication phase, we also needed to calculate the computational cost of the CS. In Case 2, and have the private value of and do not require the participation of the CS; only the computational costs of , , and need to be calculated.
When comparing the computational cost, we estimated the computational time of each entity in the protocol through a simulation experiment. We used MI 8 to simulate the vehicle, a Lenovo laptop to simulate the RSU and fog node, and a Lenovo desktop computer to simulate the cloud server. The equipment configuration of the three devices is shown in Table 5. The simulation experiment used the average execution time of the three devices 10 times as the running time, as shown in Table 6. Here, the ⊕ and ‖ operations were negligibly small, and the execution time of fuzzy extraction was similar to that of the hash function, according to [36]. It is shown in [19] that the average running time of the system with SGX only increases by 20 s, sufficiently showing the low computation cost of SGX. Hence, we ignored the computational cost of SGX in the following comparisons. The results of the comparison of the computational cost are listed in Table 7. It is evident from Table 7 that for and , excluding our protocol, the other protocols performed point multiplication, so the computational cost of our protocol was the lowest. For , only our protocol contained the RSU. For the CS, the computational cost of Wazid et al. [29] was smaller than that of our protocol, whereas the others were higher than that of our protocol. As the CS had strong computing power, it did not affect the protocol’s performance. Therefore, the computational cost of the proposed protocol was relatively small.

Table 5.
Experimental environment.

Table 6.
Experimental results.

Table 7.
Computational cost comparison1.
When comparing the communication cost, the length of the timestamp was regarded as 32 bits, the length of the identity and random number was 160 bits, that of the hash function and symmetric encryption and decryption was 256 bits, and that of the ECC point was 320 bits. The proposed protocol was considered an example to illustrate the calculation method. The communication cost was calculated based on the two cases of the protocol. For Case 1, we needed to calculate the communication cost in the authentication phase and the communication cost in the data transmission phase. In Case 1, the protocol transmitted seven messages on the common channel, including , , , , , , and . Here, are random numbers, are hash values, are timestamps, and are encrypted values. Through our calculations, the communication cost of Case 1 was 5152 bits. In Case 2, we only needed to calculate the communication cost of the four messages in the authentication phase. Through calculations, the communication cost of Case 2 was 2688 bits. From the above calculation method, the communication costs of the protocols of Ma et al. [9], Wazid et al. [29], Eftekhari et al. [10], and Wu et al. [11] were 4512, 3488, 4416, and 4448 bits, respectively. The comparison results are presented in Table 8. Therefore, evidently in Case 1, because our protocol has seven rounds of messages, the communication cost of our protocol was higher than that of the other protocols. In Case 2, the communication cost of our protocol was lower than that of the other protocols, which significantly reduced the communication cost of the protocol.

Table 8.
Communication cost comparison.
5.3. Discussions
Now, we discuss our protocol and those of Eftekhari et al. [10] and Wu et al. [11] in terms of architecture, computational cost, and communication cost.
In the first item (architecture), both protocols [10,11] used the traditional three-layer architecture (i.e., vehicle–fog node–CS). As mentioned in the Introduction, this architecture fails to realize the function of fog nodes sharing the computational burden of the CS, because the fog nodes actually replace the RSUs, and computation is still performed on the CS. To reduce the computational burden of the CS, we extended the traditional architecture to propose the first four-layer architecture, namely vehicle–RSU–fog node–CS. In this architecture, when a vehicle enters the road and wants to communicate with the RSU, the communication modes are divided into the two cases. Case 1 requires the participation of each entity, while Case 2 only requires the participation of the vehicle, RSU and fog node without the CS. Therefore, this architecture effectively realizes the function of the fog node sharing the computational burden of the CS.
In the second item (computational cost), both protocols [10,11] performed ECC operations. Our protocol performs hash, fuzzy extraction, and symmetric encryption and decryption operations in Case 1, and it only performs hash and fuzzy extraction operations in Case 2. Though the three protocols are secure, our protocol has a lower computational cost.
In the final item (communication cost), the communication cost of the proposed protocol (Case 1) was slightly higher than that of both protocols [10,11] because it requires an additional three rounds to judge whether the vehicle communicates with the RSU for the first time. However, Case 1 only occurred once for the same vehicle and RSU. In Case 2, our protocol had a lower communication cost than Eftekhari et al. [10] and Wu et al.’s [11] protocols.
6. Conclusions
In this paper, we first introduced the IoV and fog computing and reviewed the related research results. After that, we proposed an authentication protocol based on SGX and fog computing in the IoV. In this protocol, we first proposed a four-layer architecture that significantly reduced the computational burden of the CS. To resist several well-known attacks, we applied SGX to our protocol. Finally, we proved the security of the proposed protocol through the ROR model and informal analysis. We also compared its performance with those of recent protocols. The results show that the proposed protocol had better security and a lower computational cost. Future studies will continue to conduct further research based on the architecture used. We hope that this research will provide ideas and help researchers.
Author Contributions
Conceptualization, T.-Y.W.; innovation, X.G.; methodology, T.-Y.W. and X.G.; software, Y.-C.C.; formal analysis, S.K.; investigation, C.-M.C.; writing—original draft preparation, T.-Y.W., X.G., Y.-C.C., S.K. and C.-M.C. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
This study did not involve humans.
Data Availability Statement
The data are contained within the article.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| IoT | Internet of Things |
| IoV | Internet of Vehicles |
| SGX | Software guard extensions |
| PRM | Preserved random memory |
| EPC | Enclave page cache |
| ROR | Real-or-Random |
| V2V | Vehicle-to-vehicle |
| V2P | Vehicles-to-pedestrians |
| V2I | Vehicle-to-infrastructure |
| AKA | Authenticated key agreement |
| RSU | Roadside unit |
| PKI | Public key infrastructure |
| ECC | Elliptic curve cryptography |
| AKM | Authentication key management |
| PUF | Physical unclonable function |
References
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Chegini, H.; Naha, R.K.; Mahanti, A.; Thulasiraman, P. Process automation in an IoT–fog–cloud ecosystem: A survey and taxonomy. IoT 2021, 2, 92–118. [Google Scholar] [CrossRef]
- Yang, F.; Wang, S.; Li, J.; Liu, Z.; Sun, Q. An overview of internet of vehicles. China Commun. 2014, 11, 1–15. [Google Scholar] [CrossRef]
- Contreras-Castillo, J.; Zeadally, S.; Guerrero-Ibañez, J.A. Internet of vehicles: Architecture, protocols, and security. IEEE Internet Things J. 2017, 5, 3701–3709. [Google Scholar] [CrossRef]
- Zhou, H.; Xu, W.; Chen, J.; Wang, W. Evolutionary V2X technologies toward the Internet of vehicles: Challenges and opportunities. Proc. IEEE 2020, 108, 308–323. [Google Scholar] [CrossRef]
- Stojmenovic, I.; Wen, S.; Huang, X.; Luan, H. An overview of fog computing and its security issues. Concurr. Comput. Pract. Exp. 2016, 28, 2991–3005. [Google Scholar] [CrossRef]
- Chen, S.; Zhang, T.; Shi, W. Fog computing. IEEE Internet Comput. 2017, 21, 4–6. [Google Scholar] [CrossRef]
- Dastjerdi, A.V.; Gupta, H.; Calheiros, R.N.; Ghosh, S.K.; Buyya, R. Fog computing: Principles, architectures, and applications. In Internet of things; Elsevier: Amsterdam, The Netherlands, 2016; pp. 61–75. [Google Scholar] [CrossRef] [Green Version]
- Ma, M.; He, D.; Wang, H.; Kumar, N.; Choo, K.K.R. An efficient and provably secure authenticated key agreement protocol for fog-based vehicular ad-hoc networks. IEEE Internet Things J. 2019, 6, 8065–8075. [Google Scholar] [CrossRef]
- Eftekhari, S.A.; Nikooghadam, M.; Rafighi, M. Security-enhanced three-party pairwise secret key agreement protocol for fog-based vehicular ad-hoc communications. Veh. Commun. 2021, 28, 100306. [Google Scholar] [CrossRef]
- Wu, T.Y.; Lee, Z.; Yang, L.; Luo, J.N.; Tso, R. Provably secure authentication key exchange scheme using fog nodes in vehicular ad hoc networks. J. Supercomput. 2021, 77, 6992–7020. [Google Scholar] [CrossRef]
- Wu, T.Y.; Guo, X.; Yang, L.; Meng, Q.; Chen, C.M. A Lightweight Authenticated Key Agreement Protocol Using Fog Nodes in Social Internet of Vehicles. Mob. Inf. Syst. 2021, 2021, 3277113. [Google Scholar] [CrossRef]
- Ying, B.; Nayak, A. Anonymous and lightweight authentication for secure vehicular networks. IEEE Trans. Veh. Technol. 2017, 66, 10626–10636. [Google Scholar] [CrossRef]
- Mohit, P.; Amin, R.; Biswas, G. Design of authentication protocol for wireless sensor network-based smart vehicular system. Veh. Commun. 2017, 9, 64–71. [Google Scholar] [CrossRef]
- Yu, S.; Lee, J.; Lee, K.; Park, K.; Park, Y. Secure authentication protocol for wireless sensor networks in vehicular communications. Sensors 2018, 18, 3191. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Li, J.; Lu, H.; Guizani, M. ACPN: A novel authentication framework with conditional privacy-preservation and non-repudiation for VANETs. IEEE Trans. Parallel Distrib. Syst. 2014, 26, 938–948. [Google Scholar] [CrossRef]
- Liu, X.; Guo, Z.; Ma, J.; Song, Y. A Secure Authentication Scheme for Wireless Sensor Networks Based on DAC and Intel SGX. IEEE Internet Things J. 2021, 9, 3533–3547. [Google Scholar] [CrossRef]
- Condé, R.C.; Maziero, C.A.; Will, N.C. Using Intel SGX to protect authentication credentials in an untrusted operating system. In Proceedings of the 2018 IEEE Symposium on Computers and Communications (ISCC), Natal, Brazil, 25–28 June 2018; pp. 158–163. [Google Scholar]
- Wang, J.; Hao, S.; Li, Y.; Fan, C.; Wang, J.; Han, L.; Hong, Z.; Hu, H. Challenges towards protecting vnf with sgx. In Proceedings of the 2018 ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization, Tempe, AZ, USA, 21 March 2018; pp. 39–42. [Google Scholar] [CrossRef]
- Chaudhry, S.A. Combating identity de-synchronization: An improved lightweight symmetric key based authentication scheme for IoV. J. Netw. Intell. 2021, 6, 12. [Google Scholar]
- Xiong, H.; Chen, J.; Mei, Q.; Zhao, Y. Conditional privacy-preserving authentication protocol with dynamic membership updating for VANETs. IEEE Trans. Dependable Secur. Comput. 2022, 19, 2089–2104. [Google Scholar] [CrossRef]
- Raya, M.; Hubaux, J.P. Securing vehicular ad hoc networks. J. Comput. Secur. 2007, 15, 39–68. [Google Scholar] [CrossRef] [Green Version]
- Huang, J.L.; Yeh, L.Y.; Chien, H.Y. ABAKA: An anonymous batch authenticated and key agreement scheme for value-added services in vehicular ad hoc networks. IEEE Trans. Veh. Technol. 2010, 60, 248–262. [Google Scholar] [CrossRef]
- Sadri, M.J.; Rajabzadeh Asaar, M. A lightweight anonymous two-factor authentication protocol for wireless sensor networks in Internet of Vehicles. Int. J. Commun. Syst. 2020, 33, e4511. [Google Scholar] [CrossRef]
- Jiang, Q.; Zhang, X.; Zhang, N.; Tian, Y.; Ma, X.; Ma, J. Three-factor authentication protocol using physical unclonable function for IoV. Comput. Commun. 2021, 173, 45–55. [Google Scholar] [CrossRef]
- Kumar, S.; Banka, H.; Kaushik, B.; Sharma, S. A review and analysis of secure and lightweight ECC-based RFID authentication protocol for Internet of Vehicles. Trans. Emerg. Telecommun. Technol. 2021, 32, e4354. [Google Scholar] [CrossRef]
- Wu, T.Y.; Meng, Q.; Yang, L.; Guo, X.; Kumari, S. A provably secure lightweight authentication protocol in mobile edge computing environments. J. Supercomput. 2022, 1–22. [Google Scholar] [CrossRef]
- Huang, X.; Xiong, H.; Chen, J.; Yang, M. Efficient Revocable Storage Attribute-based Encryption with Arithmetic Span Programs in Cloud-assisted Internet of Things. IEEE Trans. Cloud Comput. 2021. [Google Scholar] [CrossRef]
- Wazid, M.; Bagga, P.; Das, A.K.; Shetty, S.; Rodrigues, J.J.; Park, Y. AKM-IoV: Authenticated key management protocol in fog computing-based Internet of vehicles deployment. IEEE Internet Things J. 2019, 6, 8804–8817. [Google Scholar] [CrossRef]
- Han, M.; Liu, S.; Ma, S.; Wan, A. Anonymous-authentication scheme based on fog computing for VANET. PLoS ONE 2020, 15, e0228319. [Google Scholar] [CrossRef]
- Soleymani, S.A.; Goudarzi, S.; Anisi, M.H.; Zareei, M.; Abdullah, A.H.; Kama, N. A security and privacy scheme based on node and message authentication and trust in fog-enabled VANET. Veh. Commun. 2021, 29, 100335. [Google Scholar] [CrossRef]
- Canetti, R.; Goldreich, O.; Halevi, S. The random oracle methodology, revisited. J. ACM (JACM) 2004, 51, 557–594. [Google Scholar] [CrossRef] [Green Version]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Analysis of key-exchange protocols and their use for building secure channels. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Innsbruck, Austria, 6–10 May 2001; Springer: Berlin/Heidelberg, Germany, 2001; pp. 453–474. [Google Scholar]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s law in passwords. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Lee, J.H.; Sherratt, R.S. Enhanced three-factor security protocol for consumer USB mass storage devices. IEEE Trans. Consum. Electron. 2014, 60, 30–37. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).