ETHERST: Ethereum-Based Public Key Infrastructure Identity Management with a Reward-and-Punishment Mechanism
Abstract
:1. Introduction
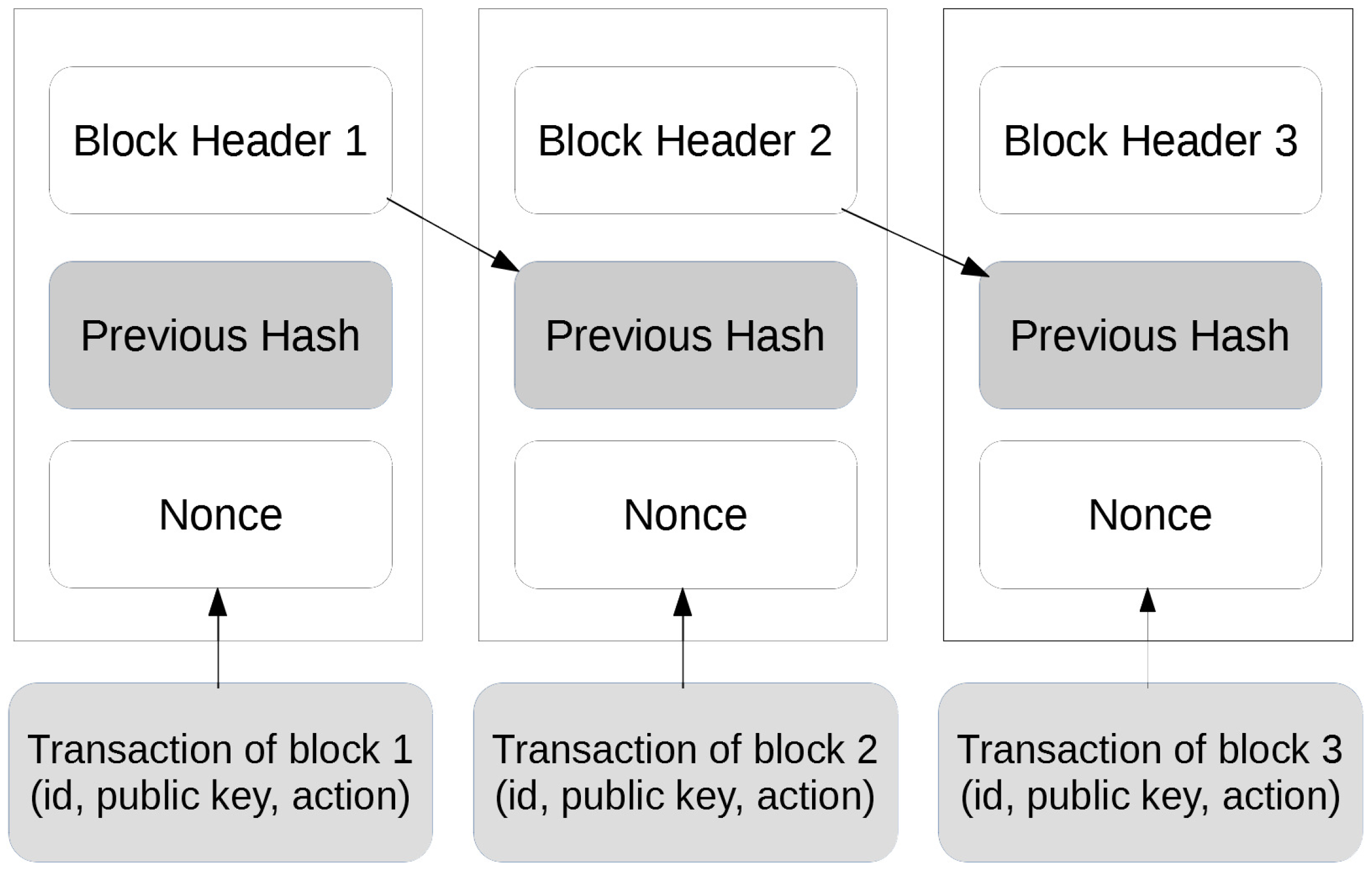
1.1. Blockchain Technology
1.2. Ethereum, Smart Contract, Ether and ERC-20
1.3. Conventional Public Key Infrastructure (PKI)
- Registration of identity with a corresponding public key.
- Updating the public key of a previously registered identity.
- Looking up a public key for an identity.
- Verification of the public key for an identity.
- Revoking the public key for an identity.
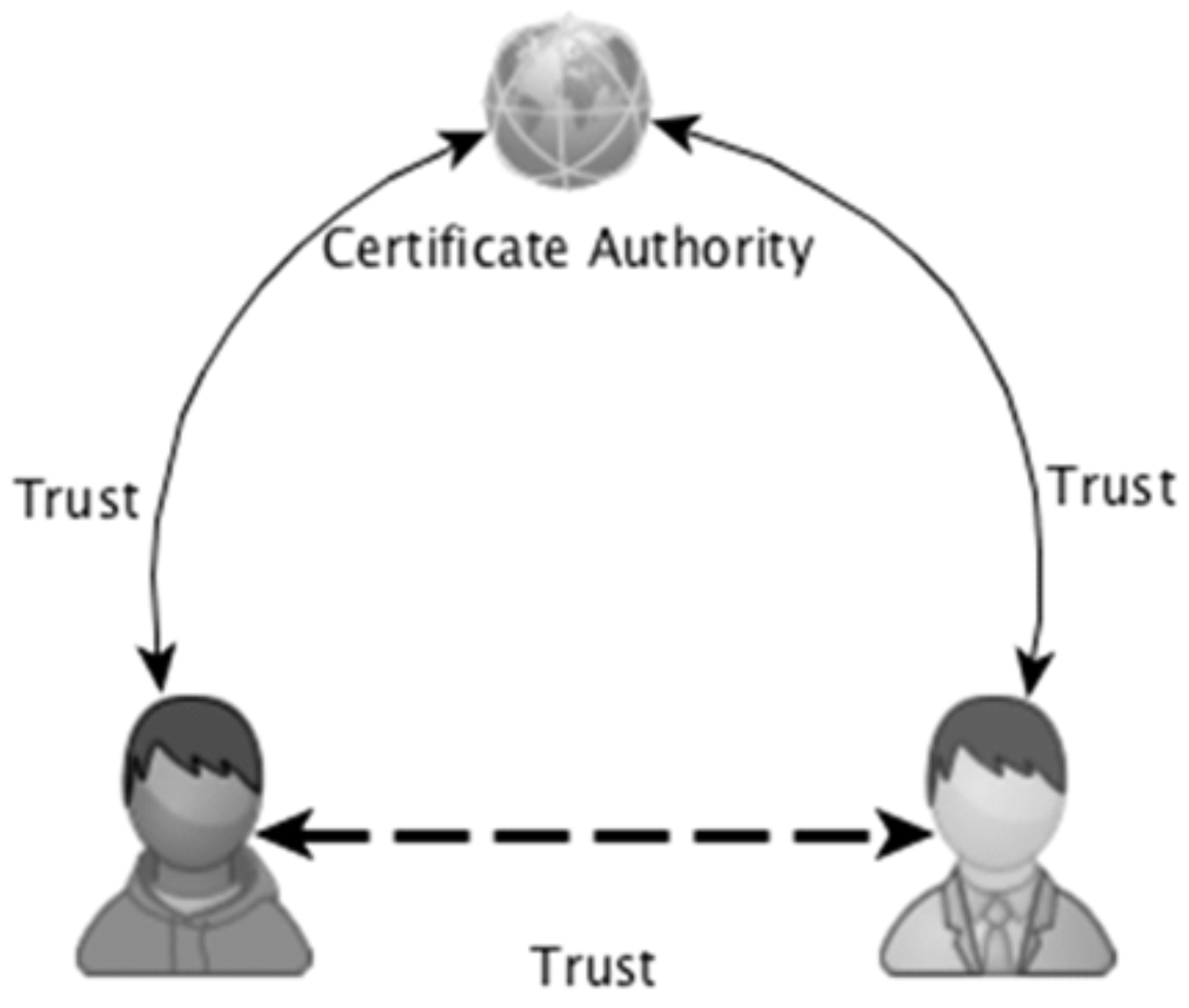
1.3.1. Certificate Authorities (CAs)
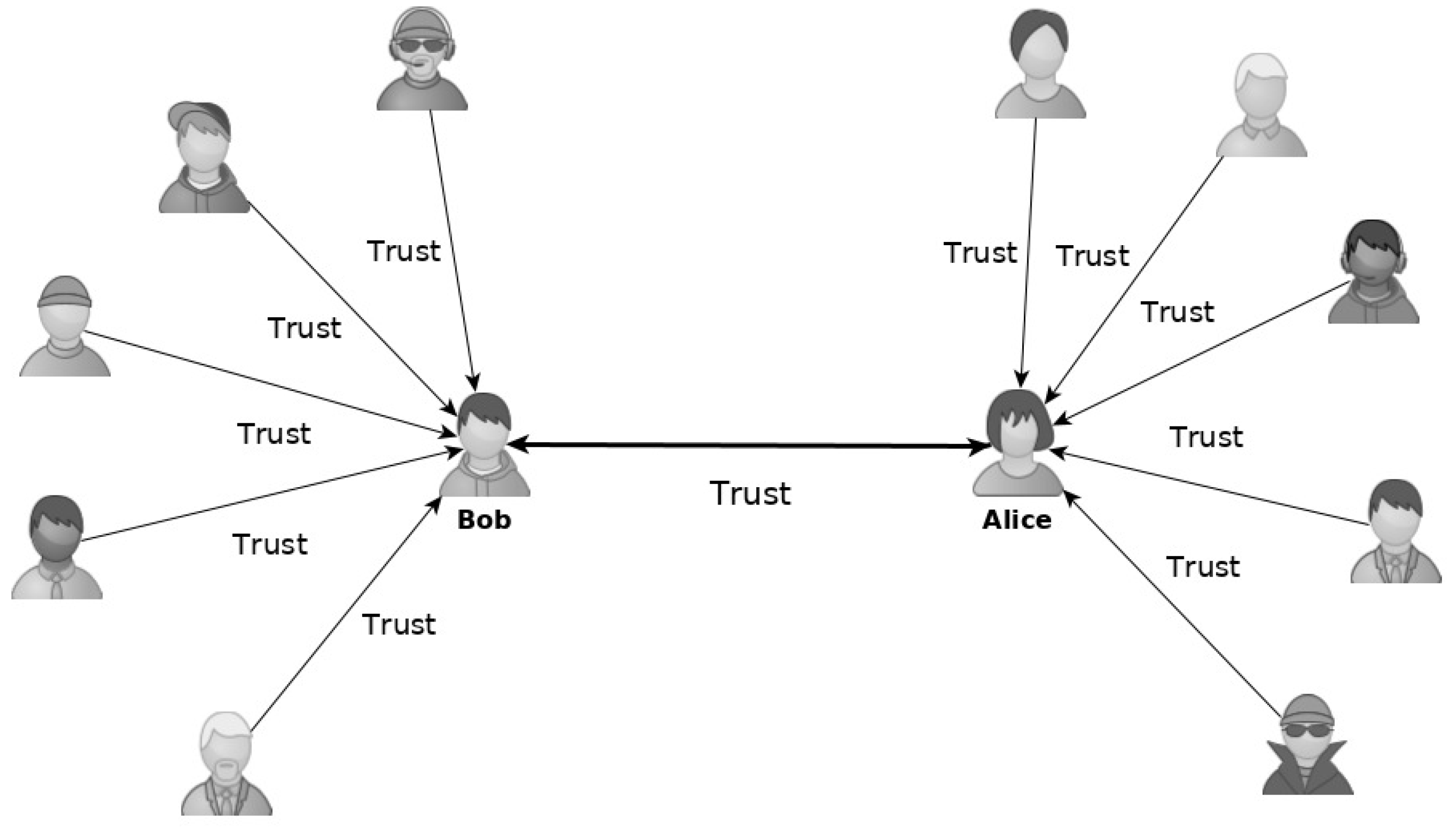
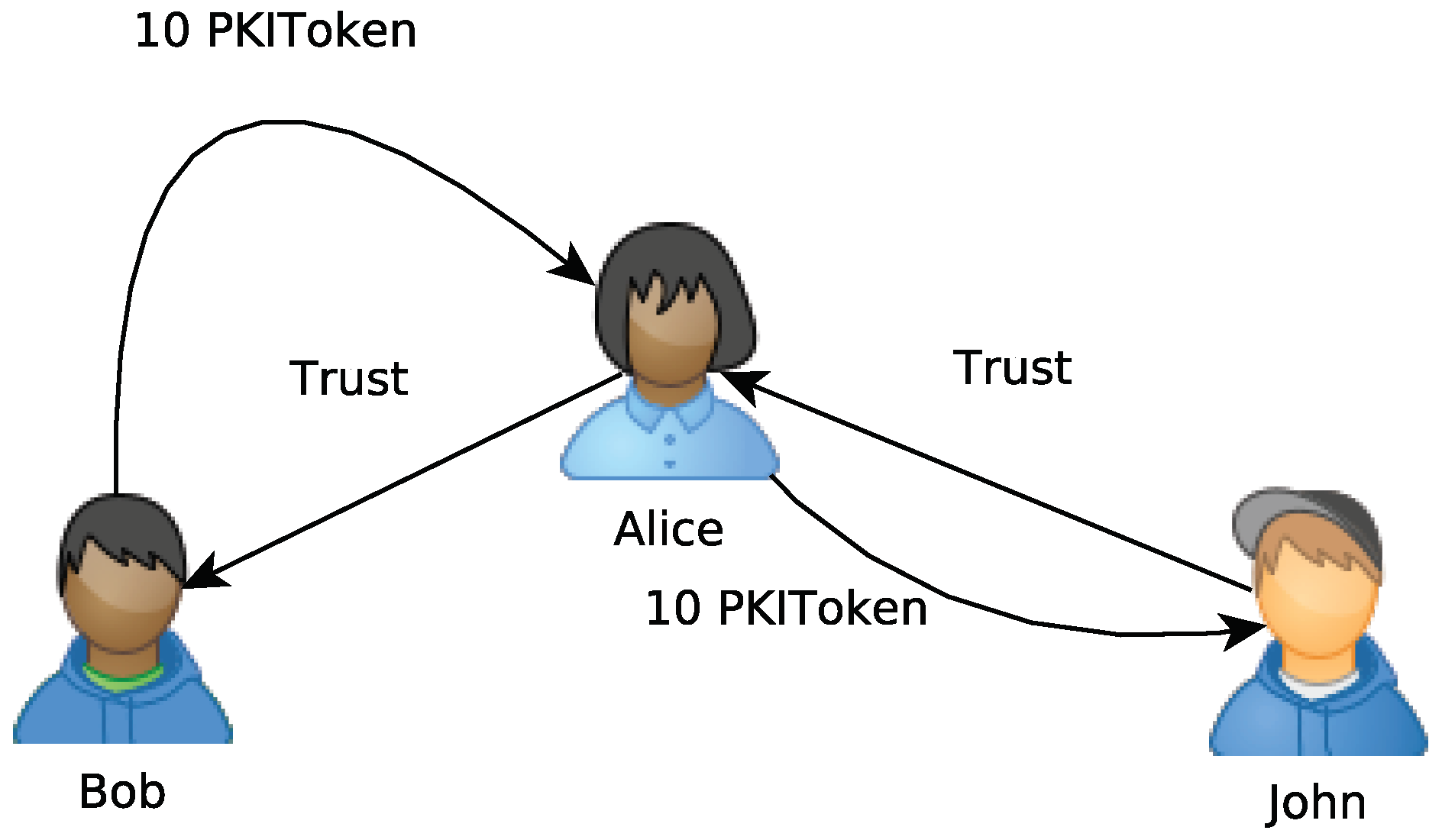
1.3.2. PGP Web of Trust (WoT)
- No trust: users are not sure whether this public key is valid or not.
- Marginal trust: this public key may be valid but users cannot be too sure.
- Complete trust: users are confident that this public key is valid.
- Legitimate: deemed legitimate by users.
1.4. Blockchain-Based PKI
- Permission Type
- Revocation
- Blockchain Type
- Certificate Format
- PKI Type
- Storage Type
- Updateable Key
- Privacy
- Incentives
- Evaluation
1.5. Our Contributions
1.6. Organization
2. The Evolution of Blockchain-Based PKI
2.1. Beginning of Blockchain-Based PKI
2.1.1. CertChain
2.1.2. Blockstack and AuthCoin
2.1.3. Pomcor
2.1.4. SCPKI
2.1.5. Instant Karma PKI (IKP)
- Public auditability
- Automation
- Incentivization
- Deterrence
2.1.6. Internet Web Trust System
- Admission mechanism for CA nodes.
- Certificate chain structure.
- Conventional certificate management function.
- Error certificate feedback mechanism.
- Automatic economic reward and punishment mechanism.
3. Incentivization and Disincentivization in Blockchain-Based PKI
- Minimize the influence of fluctuations on the market value of Ether.
- Allows the model owner to determine the value of reward/punish medium.
- Allow better control over disputes.
- Better adoption on commercial deployment.
4. Design of ETHERST
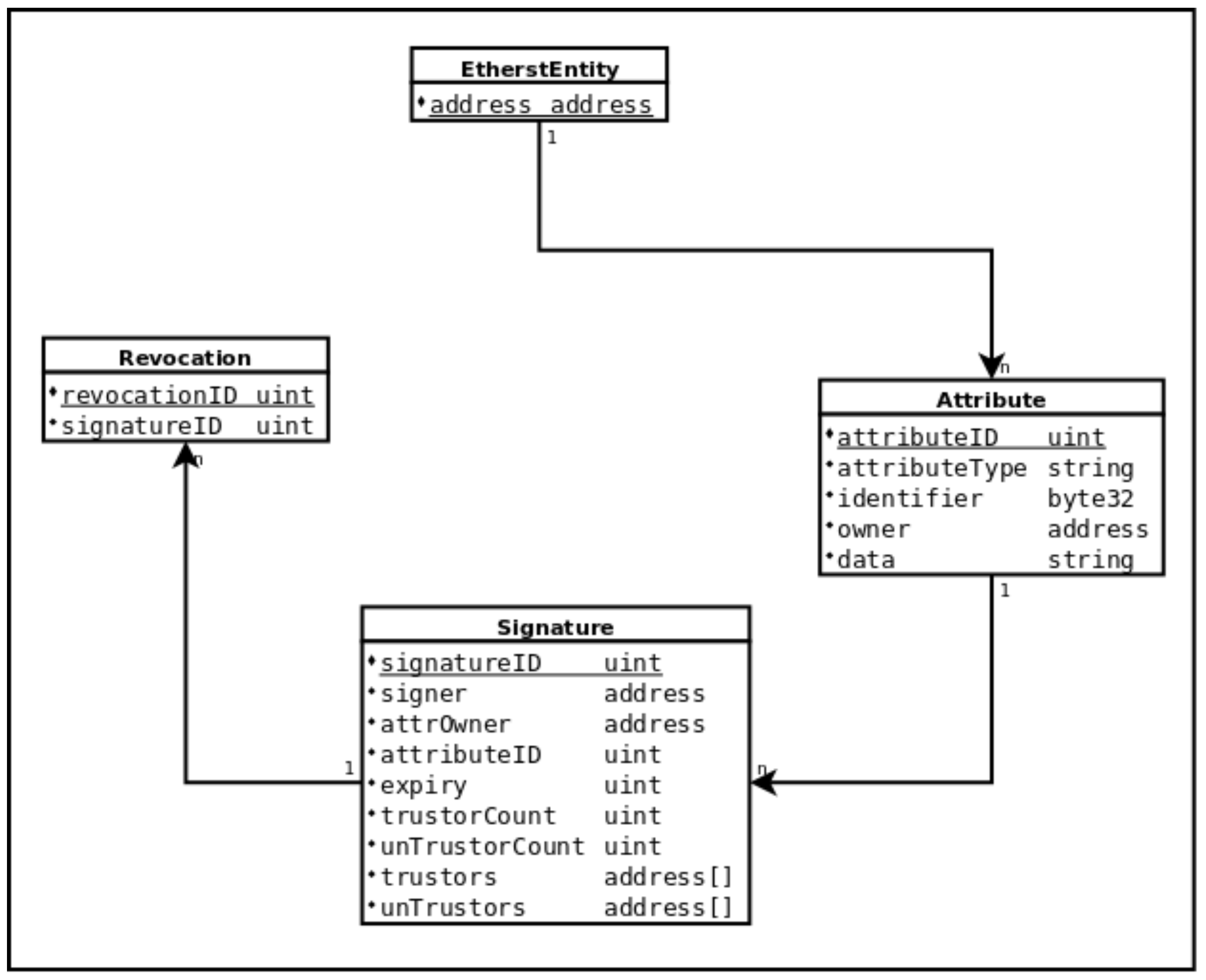
4.1. ETHERST Version 1.0
- ETHERST entity
- Attribute
- Signature
- Revocation
- Create attribute.
- Sign attribute.
- Revoke signature.
- Trust signature.
- Untrust signature.
4.1.1. Create Attribute
- Type of Attribute—the type of attribute that is represented, for instance, “key” or “name”.
- Identifier—a unique identifier for the attribute if there is any.
- Data—the attribute data which includes the proof of binding for the attribute.
4.1.2. Sign Attribute
- Attribute ID—a unique identifier for the attribute.
- Expiry—the expiry timestamp for the signature. It represents the time at which the signature is considered invalid.
4.1.3. Revoke Signature
- Signature ID—unique identifier for the signature.
4.1.4. Trust Signature
| Algorithm 1:Trust Signature. |
| Result: Status of trusting Input: SignatureID Output: status of trusting Initialization Deny if mapLastTrustAction[msg.sender] less than 1 day  return status |
4.1.5. Untrust Signature
- Fluctuation of the market value of Ether affects the reward-and-punishment mechanism feasibility and increases uncertainty.
- Requirement of deposit before attribute creation discourages involvement of nodes.
4.2. ETHERST Version 2.0
| Algorithm 2:Untrust Signature. |
| Result: Status of untrusting Input: SignatureID Output: status of untrusting Initialization Deny if mapLastUnTrustAction[msg.sender] less than 1 day  return status |
- PKIToken smart contract.
- ETHERST version 2.0 smart contract.
4.2.1. Sign Attribute
4.2.2. Trust Signature
| Algorithm 3:Trust Signature. |
| Result: Status of trusting Input: SignatureID Output: status of trusting Initialization  returnstatus |
4.2.3. Untrust Signature
| Algorithm 4:Untrust Signature. |
| Result: Status of untrusting Input: SignatureID Output: status of untrusting Initialization  returnstatus |
5. Implementation and Evaluation
- Size of attribute data is 500 bytes each.
- TRUST-LEVEL is set as 5.
- UNTRUST-LEVEL is set as 5.
5.1. ETHERST Version 1.0
- ETHERST version 1.0 smart contract
- Simulation script
5.2. ETHERST Version 2.0
- PKIToken smart contract
- ETHERST version 2.0 smart contract
- Simulation script
- Minimize the impact of fluctuation of market value of Ether on the ecosystem of ETHERST in a commercial implementation.
- Lower the entry cost that will encourage participation of each node.
5.3. Simulation and Evaluation
5.3.1. Analysis of Cost
- Publish contracts
- Sign attribute
- Revoke signature
- Trust signature
- Untrust signature
| Algorithm 5:Algorithm to obtain gas usage of ETHERST version 1.0 operations. |
| Result: Gas usage of each operations Input: Output: Gas usage of each operations Initialize nodes with random data Choose a dedicated node A, deposit 0.0002 ETH to ETHERST contract node A create an attribute of 200 bytes data node A sign attribute Get the total gas used for signing attribute Choose a dedicated node B, trust Signature signatureId Get the total gas used for trusting signature Choose a dedicated node C, untrust Signature signatureId Get the total gas used for untrust signature from event node A revoke signature signatureId Get the total gas used for untrust signature from event Print usage of gas for all the operations. return status |
| Algorithm 6:Algoritm to obtain gas usage of ETHERST version 2.0 operations. |
| Result: Gas usage of each operations Input: Output: Gas usage of each operations Initialize nodes with random data Choose a dedicated node A node A create an attribute of 200 bytes data node A sign attribute Get the total gas used for signing attribute Choose a dedicated node B, trust Signature signatureId Get the total gas used for trusting signature Choose a dedicated node C, untrust Signature signatureId Get the total gas used for untrust signature from event node A revoke signature signatureId Get the total gas used for untrust signature from event Print usage of gas for all the operations. return status |
5.3.2. Random Activities Simulation and Analysis
| Algorithm 7:Simulation. |
| Result: Status of simulation Input: Output: status of simulation  returnstatus |
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Yakubov, A.; Shbair, W.; Wallbom, A.; Sanda, D.; State, R. R: A blockchain-based PKI management framework. In Proceedings of the 2018 IEEE/IFIP Network Operations and Management Symposium, Taipei, Taiwan, 23–27 April 2018. [Google Scholar]
- Koa, C.G.; Heng, S.H.; Tan, S.Y.; Chin, J.J. Review of Blockchain-Based Public Key Infrastructure. In Proceedings of the 7th International Cryptology and Information Security Conference 2020 (CRYPTOLOGY2020), Online, 9–10 June 2020; pp. 20–31. [Google Scholar]
- Prins, J.; Cybercrime, B. Technical Report; Diginotar Certificate Authority Breach Operation Black Tulip. 2012. Available online: https://cryptome.wikileaks.org/0005/diginotar-insec.pdf (accessed on 31 March 2019).
- Bano, S. Consensus in the Age of Blockchains. arXiv 2017, arXiv:1711.03936. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 28 February 2019).
- Chen, G.; Xu, B.; Lu, M.; Chen, N.-S. Exploring blockchain technology and its potential applications for education. Smart Learn. Environ. 2018, 5. [Google Scholar] [CrossRef] [Green Version]
- Castro, M.; Liskov, B. Practical Byzantine Fault Tolerance. OSDI 1999, 99, 173–186. [Google Scholar]
- Bentov, I.; Gabizon, A.; Mizrahi, A. Cryptocurrencies Without Proof of Work. In Financial Cryptography and Data Security; Clark, J., Meiklejohn, S., Ryan, P.Y., Wallach, D., Brenner, M., Rohloff, K., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; pp. 142–157. [Google Scholar]
- Kiayias, A.; Russell, A.; David, B.; Oliynykov, R. Ouroboros: A provably secure proof-of-stake blockchain protocol. In Proceedings of the 37th Annual International Cryptology Conference (CRYPTO), Santa Barbara, CA, USA, 20–24 August 2017; Springer: Berlin/Heidelberg, Germany, 2017. [Google Scholar]
- Dhillon, V.; Metcalf, D.; Hooper, M. The Hyperledger Project. In Blockchain Enabled Applications: Understand the Blockchain Ecosystem and How to Make It Work for You; Apress: Berkeley, CA, USA, 2017; pp. 139–149. [Google Scholar] [CrossRef]
- Brandenburger, M.; Cachin, C.; Kapitza, R.; Sorniotti, A. Blockchain and Trusted Computing: Problems, Pitfalls, and a Solution for Hyperledger Fabric. arXiv 2018, arXiv:1805.08541. [Google Scholar]
- Underwood, S. Blockchain beyond Bitcoin. Commun. ACM 2016, 59, 15–17. [Google Scholar] [CrossRef]
- Wiki, B. Script: Simple, Stack-Based. Available online: https://en.bitcoin.it/wiki/Script (accessed on 31 October 2020).
- Wright, C.S. Turing Complete Bitcoin Script White Paper. SSRN 2016. [Google Scholar] [CrossRef] [Green Version]
- Buterin, V. Ethereum: A Next-Generation Smart Contract and Decentralized Application Platform, Whitepaper. Available online: https://ethereum.org/en/whitepaper/ (accessed on 31 May 2020).
- Chen, J.; Yao, S.; Yuan, Q.; He, K.; Ji, S.; Du, R. CertChain: Public and efficient certificate audit based on blockchain for TLS connections. In Proceedings of the IEEE International Conference on Computer Communications (INFOCOM), Toronto, ON, Canada, 27 April 2018; pp. 2060–2068. [Google Scholar]
- ERC-20. EIP-20: ERC-20 Token Standard. Available online: https://eips.ethereum.org/EIPS/eip-20 (accessed on 28 February 2020).
- Fromknecht, C.; Velicanu, D.; Yakoubuv, S. A decentralized public key infrastructure with identity retention. Cryptol. ePrint Arch. 2014, 2014, 803. [Google Scholar]
- Ryabitsev, K. PGP Web of Trust: Core Concepts behind Trusted Communication. Available online: https://www.linux.com/training-tutorials/pgp-web-trust-core-concepts-behind-trusted-communication/ (accessed on 31 December 2020).
- Ulrich, A.; Holz, R.; Hauck, P.; Carle, G. Investigating the OpenPGP web of trust. Esorics Lncs 2011, 6879, 489–507. [Google Scholar] [CrossRef]
- Brunner, C.; Knirsch, F.; Unterweger, A.; Engel, D. A Comparison of Blockchain-based PKI Implementations. In Proceedings of the 6th International Conference on Information Systems Security and Privacy, ICISSP 2020, Valletta, Malta, 25–27 February 2020; pp. 333–340. [Google Scholar]
- Matsumoto, S.; Reischuk, R. IKP: Turning a PKI around with decentralized automated incentives. In Proceedings of the IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–24 May 2017; pp. 410–426. [Google Scholar]
- Li, S.; Wang, N.; Du, X.; Liu, A. Internet Web Trust System Based on Smart Contract. Commun. Comput. Inf. Sci. 2019, 1058, 295–311. [Google Scholar]
- Namecoin. Namecoin: Decentralized Secure Names. February 2019.
- Benaloh, J.; Mare, M.D. One-Way Accumulators: A Decentralized Alternative to Digital Signatures; Advances in Cryptology—EUROCRYPT ’93; Springer: Berlin/Heidelberg, Germany, 1994; pp. 274–285. [Google Scholar]
- Camacho, P.; Hevia, A.; Kiwi, M.; Opazo, R. Strong accumulators from collision-resistant hashing. Lect. Notes Comput. Sci. 2008, 5222, 471–486. [Google Scholar]
- Camenisch, J.; Kohlweiss, M.; Soriente, C. An accumulator based on bilinear maps and efficient revocation for anonymous credentials. Lect. Notes Comput. Sci. 2009, 5443, 481–500. [Google Scholar]
- Bloom, B.H. Space/timetrade-offs in hash coding with allowable errors. Commun. ACM 1970, 13, 422–426. [Google Scholar] [CrossRef]
- Ali, J.; Nelson, R.; Shea, M.; Freedman, M.J. Blockstack: A Global naming and storage system secured by blockchains. In Proceedings of the 2016 USENIX Conference on Usenix Annual Technical Conference, Denver, CO, USA, 22–24 June 2016. [Google Scholar]
- Leiding, B.; Cap, C.; Mundt, T.; Rashidibajgan, S. Authcoin: Validation and Authentication in Decentralized Networks. arXiv 2016, arXiv:1609.04955. [Google Scholar]
- Lewison, K.; Corella, F. Backing Rich Credentials with a Blockchain PKI. Technical Report. 2016. Available online: https://pomcor.com/techreports/BlockchainPKI.pdf (accessed on 30 June 2020).
- Cooper, D.; Santesson, S.; Farrell, S.; Boeyen, S.; Housley, R.; Polk, W. Internet X.509 Public Key Infrastructure Certificate and CRL Profile, RFC 5280, May 2008, doi:10.17487/RFC5280. Available online: https://www.rfc-editor.org/info/rfc5280 (accessed on 27 June 2021).
- Al-Bassam, M. SCPKI: A smart contract-based PKI and identity system. In Proceedings of the ACM Workshop on Blockchain, Cryptocurrencies and Contracts, Association for Computing Machinery, Abu Dhabi, UAE, 2–6 April 2017; pp. 35–40. [Google Scholar]
- Kim, Y.; Kim, J.; Kim, W.; Im, J.; Kim, T.; Kang, S. Predicting Fluctuations in Cryptocurrency Transactions Based on User Comments and Replies. PLoS ONE 2016, 11, e0161197. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- TruffleSuite. TruffleSuite: Sweet Tools for Smart Contracts. Available online: https://www.trufflesuite.com/ (accessed on 31 October 2020).
- OpenZepplin. OpenZepplin: The Standard for Secure Blockchain Applications. Available online: https://openzeppelin.com/ (accessed on 31 October 2020).

| Data (Byte) | Gas Used | Gas Fee in ETH | Gas Fee in USD |
|---|---|---|---|
| 100 | 238,936 | 0.00358404 | 9.3299 |
| 200 | 306,951 | 0.00460427 | 11.9857 |
| 300 | 375,030 | 0.00562545 | 14.6440 |
| 400 | 443,044 | 0.00664566 | 17.2998 |
| 500 | 511,059 | 0.00766589 | 19.9556 |
| Data (Byte) | Gas Used | Gas Fee in ETH | Gas Fee in USD |
|---|---|---|---|
| 100 | 280,329 | 0.00420494 | 10.9462 |
| 200 | 348,344 | 0.00522516 | 13.6020 |
| 300 | 416,423 | 0.00624635 | 16.2603 |
| 400 | 484,437 | 0.00726656 | 18.9161 |
| 500 | 552,452 | 0.00828678 | 21.5719 |
| Operation | Gas Used | Gas Fee in ETH | Gas Fee in USD | |||
|---|---|---|---|---|---|---|
| Ver 1 | Ver 2 | Ver 1 | Ver 2 | Ver 1 | Ver 2 | |
| Publish contracts | 2,084,797 | 3,954,127 | 0.03127196 | 0.0531191 | 81.4062 | 154.3990 |
| Sign Attribute | 101,127 | 100,631 | 0.00151691 | 0.00150947 | 3.9488 | 3.9294 |
| Revoke Signature | 22,263 | 22,263 | 0.00033395 | 0.00033395 | 0.8693 | 0.8693 |
| Trust Signature | 101,047 | 147,072 | 0.00151571 | 0.00220608 | 3.9457 | 5.7428 |
| Untrust Signature | 97,189 | 97,189 | 0.00145784 | 0.00145784 | 3.7950 | 3.7950 |
| N | Average | Minimum | Maximum | Time Used (Seconds) |
|---|---|---|---|---|
| 10 | 38.89 | 30 | 50 | 6.02 |
| 20 | 42.11 | 30 | 60 | 17.58 |
| 30 | 45.17 | 30 | 60 | 19.58 |
| 40 | 44.87 | 10 | 90 | 21.87 |
| 50 | 44.69 | 10 | 70 | 28.44 |
| 60 | 44.41 | 10 | 80 | 44.17 |
| 70 | 46.81 | 10 | 90 | 47.23 |
| 80 | 47.72 | 10 | 120 | 48.54 |
| 90 | 48.88 | 10 | 90 | 61.85 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Koa, C.-G.; Heng, S.-H.; Chin, J.-J. ETHERST: Ethereum-Based Public Key Infrastructure Identity Management with a Reward-and-Punishment Mechanism. Symmetry 2021, 13, 1640. https://doi.org/10.3390/sym13091640
Koa C-G, Heng S-H, Chin J-J. ETHERST: Ethereum-Based Public Key Infrastructure Identity Management with a Reward-and-Punishment Mechanism. Symmetry. 2021; 13(9):1640. https://doi.org/10.3390/sym13091640
Chicago/Turabian StyleKoa, Chong-Gee, Swee-Huay Heng, and Ji-Jian Chin. 2021. "ETHERST: Ethereum-Based Public Key Infrastructure Identity Management with a Reward-and-Punishment Mechanism" Symmetry 13, no. 9: 1640. https://doi.org/10.3390/sym13091640
APA StyleKoa, C.-G., Heng, S.-H., & Chin, J.-J. (2021). ETHERST: Ethereum-Based Public Key Infrastructure Identity Management with a Reward-and-Punishment Mechanism. Symmetry, 13(9), 1640. https://doi.org/10.3390/sym13091640






