Abstract
In the Internet of things (IoT) environment, many applications access services through remote methods. In this paper, we designed a new geometric authentication mechanism to enhance security. The solution is based on geometric characteristics to achieve rapid authentication at low computational cost. In addition, we use the user’s biometrics to improve the security level of the system. Our solution meets the following security features: anonymity, resistance to forgery attacks and replay attacks, fast error detection, resistance to offline password guessing attacks, resistance to server overload attacks, mutual authentication, session key agreement, and flexibility in users choosing and changing their passwords easily.
1. Introduction
Wireless and mobile communication systems have become increasingly popular. Many service providers are beginning to propose convenient Internet of things (IoT) services and cloud applications for users. People usually use mobile devices to access all kinds of services, e.g., web-browsing, remote monitoring, and multimedia applications anytime and anywhere. Figure 1 shows an example where the user logs in to the IoT gateway (IGW) to access or control IoT devices remotely. There is no doubt that an authentication mechanism is essential to protect valid users against different types of attacks. Remote user authentication schemes are the easiest and most practical authentication mechanisms for nonsecure networks.
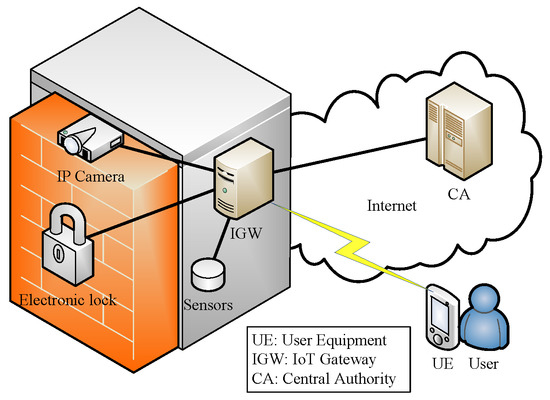
Figure 1.
Remote access via gateway in IoT environment.
However, previous authentication schemes suffer from high computational cost and insufficient security. Some schemes use asymmetric cryptography, which results in high computational cost. Most schemes use ID/password-based authentication, but the security robustness of these schemes is insufficient. Therefore, we propose a new three-factor (i.e., smart device, biometrics, and password) remote user authentication scheme for improving the performance and enhancing security in the IoT environment in this paper.
The contributions of this paper are as follows.
- Lightweight authentication: The computational performance of our scheme is better than the traditional authentication schemes (e.g., asymmetric or symmetric encryption scheme) because our scheme uses only a hash function and arithmetic.
- Three-factor authentication: A higher-entropy password increases the difficulty in brute forcing it. Many papers have proven that the three-factor authentication scheme has better security (i.e., higher password entropy) and robustness.
- Reduced IGW computing load: Many authentication methods require full participation of the IGW. However, in an IoT environment, the number of IoT devices is large. Therefore, previous schemes are not suitable for use in an IoT environment because the IGW easily suffers from the single-point failure problem due to a distributed denial-of-service (DDoS) attack. In our scheme, GAME supports the fast error detection process on the client side. If the user access is illegal, the smartphone immediately detects an error event and then rejects the login. In this way, the computational load of the IGW can be effectively reduced.
2. Related Work
This section includes three parts: user requirements, system requirements, and existing authentication schemes.
2.1. User Requirements
Since the designed authentication system must be user-friendly, the following requirements must be taken into account for users:
- Secure and simple password selection and modification: The system should enable users to select and modify their passwords easily and securely. This means that the user can change their password without the help of a trusted third party after having ensured the legality of the cardholder.
- Registration only once: The user must register only once with the Central Authority (CA) and may then access a variety of application servers. Additionally, the single registration may reduce the network load and the CA overhead.
- Anonymity: User privacy has been increasingly brought to the attention of industry and academia. Therefore, anonymous authentication implies verifying that a user is not using the real identity to perform the authentication procedure.
2.2. System Requirements
Given that a remote authentication system is susceptible to attack by adversaries, our goal is to design a system that is robust enough to resist such attacks. From related studies [1,2], the following key requirements are identified for secure authentication:
- Efficiency: Due to the limited computing power of mobile devices, the communication and computing costs on mobile devices must be lightweight.
- Integrity: The system must ensure the integrity of the message. This means that, when the data is modified, the system will find out and authentication fails.
- Session key protocol: After the authentication process, a session key will be generated between the mobile device and the IGW to provide secure communication and achieve forward secrecy.
- Mutual authentication: The IGW must verify that the user is legitimate, and the user must also ensure that the IGW is not forged. Therefore, the authentication system needs a mutual authentication process.
- No verification table: In most applications, the CA stores the user’s password table, which can cause the verifier to be stolen. Therefore, the design solution should avoid maintaining password verification tables for users.
2.3. Existing Authentication Schemes
Wu [3] first proposed a remote login authentication scheme based on geometric methods in 1995. However, some studies [4,5] found that Wu’s scheme was vulnerable to replay attacks and offline password guessing attacks. Chien et al. [5] proposed a modified authentication scheme to solve these problems, but [6,7] showed that the modified scheme [5] was still vulnerable to offline password guessing attacks. In addition, it is easy for illegal users to forge valid login requests under the revised scheme. Later, [7] proposed an improved scheme to overcome these drawbacks. The common disadvantage of all the above schemes is that they do not consider user privacy. However, privacy issues are now receiving more and more attention from industry and academia. To this end, we propose an anonymous remote user authentication scheme based on geometric methods [8]. However, our previous work did not take into account session key agreement and mutual authentication.
Many studies [9,10,11,12,13,14,15,16,17,18] combined a user’s biometrics with a password and a smart device to design a remote user authentication scheme to improve the security level (i.e., a secret key that has a value of high entropy [14]). In 2002, Lee et al. [9] proposed a fingerprint-based remote user authentication scheme using smart cards. However, a large number of subsequent studies [10,11,12] pointed out that this scheme cannot resist server spoofing attacks and masquerading attacks. Although Lin and Lai [12] combined password and fingerprint into super passwords and provided an offline password change scheme, Mitchell and Tang [13] proposed that the password change process is fragile because the smart card does not have enough information to check the correctness of the old passwords. Then, Fan and Lin [14] proposed a three-factor authentication scheme that combines a password with smart card and biometrics to provide high-security remote authentication. Khan et al. [15] proposed an improved scheme to enhance the security. However, this scheme was proven to be vulnerable to parallel session attacks [16,17], where an attacker who does not know the password of a legitimate user can pretend to be a user by eavesdropping on the communication between the user and the server to generate a valid login message in some way. Later, Li and Hwang [18] proposed an efficient biometric-based remote user authentication scheme using smart cards. Unfortunately, these biometric-based solutions [9,10,11,12,13,14,15,16,17,18] only support a single server environment, which is a limitation because there are multiple application servers on the Internet. Recently, Chuang and Chen [1] proposed a biometrics-based multi-server authentication scheme. However, Mishra et al. [19] revealed that the scheme in [1] is prone to masquerading, smart card theft, and server spoofing attacks. Afterward, Mishra et al. designed a more secure three-factor authentication scheme. Later, Lu et al. [20,21] pointed out that the solution [19] could be attacked by server masquerading and spoofing. Recently, many studies [22,23,24,25,26,27,28] proposed a lightweight authentication scheme for the IoT environment. However, these solutions still have weaknesses, especially in terms of computing and communication costs, which are higher than the solution we proposed. Banerjee et al. [29] proposed an anonymous and robust authentication scheme for IoT-based smart homes. However, [2] pointed out that Banerjee et al.’s scheme [29] does not ensure identity protection, traceability, or session secret key negotiation. Xiang and Zheng [30] presented a situation-aware device authentication scheme in smart home environments. They claimed that their solution can withstand various security threats and ensure mutual authentication and data integrity. However, Oh et al. [31] proved that this scheme cannot guarantee secure mutual authentication and is vulnerable to smart device theft, impersonation, and session key disclosure attacks.
3. Proposed Scheme
In this section, we describe our geometric authentication mechanism for enhancing security, called GAME, in an IoT environment. GAME is a lightweight authentication scheme. Moreover, we combine biometric technology and a password to enhance the level of security. The proposed geometric authentication mechanism involves four procedures: registration, login, authentication, and changing passwords. The notation used throughout this paper is listed in Table 1.

Table 1.
Notation.
3.1. Registration Procedure
Before logging in to access the service, the user must complete the registration process, which needs to be executed through a secure channel. Figure 2 shows the user registration procedure, while the steps are outlined below.
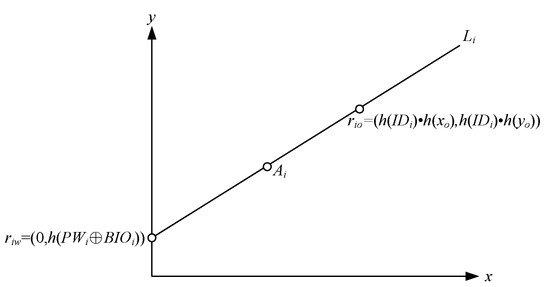
Figure 2.
Registration procedure.
Step 1: The user sends their registration information to the central authority (CA) through a secure communication channel. The registration information includes their identification IDi, password PWi, and biometric information BIOi.
Step 2: After the CA receives the user’s data, it selects a large prime number P, calculates Vi = h2(PWi⊕BIOi) and defines two points (riw and rio), which are (0, h(PWi⊕BIOi)) and (h(IDi)∙h(x0), h(IDi)∙h(y0)). Next, the CA establishes a line Li through riw and rio, and then calculates the midpoint between riw and rio, which is represented by Ai. The secret point (x0,y0) is a secret point stored in the trusted platform module (TPM) of the IGW and the CA. Note that the CA selects a different secret point for each IGW.
Step 3: The CA stores the parameters {h(IDi), h( ), P, Ai, Vi} in the NFC-SIM card of the mobile phone and provides them to the user via a secure channel.
3.2. Login Procedure
The user logs in from the mobile phone. This login process is the first checkpoint. If the user access is illegal, the mobile phone immediately detects an error event (e.g., wrong user password or failed biometric identification), and then reports the error. When the number of input errors exceeds three, the card is locked, as shown in Figure 3.
Figure 3.
(a) PIN code lock. (b) The device is locked after three incorrect inputs.
Step 1: The user enters their IDi and PWi on the mobile phone. Then, the mobile phone scans their biometric information BIOi on the sensor.
Step 2: The mobile phone checks h(IDi) and verifies whether h2(PWi⊕BIOi) is equal to Vi. If this information is verified, the phone calculates riw = (0,h(PWi⊕BIOi)) and reconstructs the line Li through riw and Ai.
Step 3: The mobile phone calculates the point between riw and Ai, represented by Bi, generates a new point riT, which is equal to (0, h(h(PWi⊕BIOi)⊕h(T))), and then uses riT and Bi to generate a new line LWT.
Step 4: The mobile phone selects a point Ci on the LWT line, which is different from riT and Bi, generates a random number ri, and then calculates the alias AIDi, AIDi = ri∙h(IDi).
Step 5: The user sends an authentication message {AIDi, Ai, Ci, T} to the IGW through a normal wireless network.
3.3. Authentication Procedure
After the IGW receives the login request message, the IGW starts the authentication process to verify the user’s request message, as shown in Figure 4 and Figure 5. The steps of the certification process are described below.
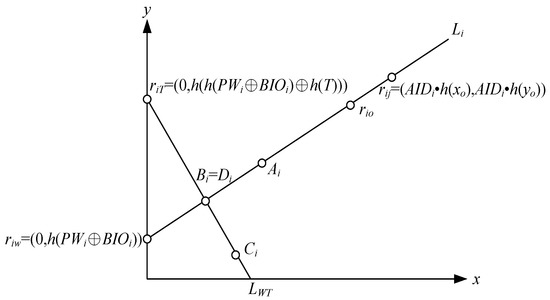
Figure 4.
Diagram of user login and authentication phases.
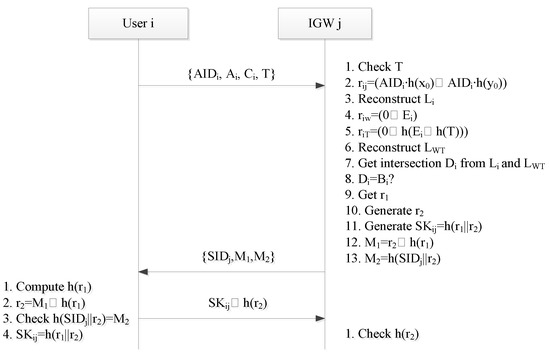
Figure 5.
Message flow of authentication phase.
Step 1: The IGW first checks the timestamp. It rejects the login message if the difference between T’ and T is larger than the threshold.
Step 2: The IGW computes point rij = (AIDi∙h(x0), AIDi∙h(y0)) and then reconstructs the line Li by rij and Ai.
Step 3: The IGW computes the intersection point riw of Li and the y-axis, defines riw = (0, Ei), and then computes riT = (0, h(Ei⊕h(T))).
Step 4: The IGW uses riT and Ci to reconstruct the line LWT and computes the intersection point Di of Li and LWT.
Step 5: The IGW accepts the login request if the value of Di is equal to the middle point Bi of Ai and riw. Otherwise, the request is rejected.
Step 6: When the authentication is successful, the IGW can deduce r1 through rio and rij on the Li line. rij = (AIDi∙h(x0),AIDi∙h(y0)) = (r1∙h(IDi)∙h(x0),r1∙h(IDi)∙h(y0)) = r1(h(IDi)∙h(x0),h(IDi)∙h(y0)) = r1∙rio.
Step 7: Then, the IGW generates the random number r2, computes the session key SKij = h(r1||r2), and generates the messages M1 and M2; M1 = r2⊕h(r1) and M2 = h(SIDj||r2).
Step 8: The IGW sends the message {SIDj, M1, M2} to the user.
Step 9: After the mobile phone receives the message, it calculates h(r1), takes out r2, and then checks whether h(SIDj||r2) is equal to M2. If it is correct, the session key SKij = h(r1||r2) is generated, and the encrypted message SKij⊕h(r2) is sent to the IGW.
Step 10: After the IGW receives the message, it uses the session key SKij to decrypt the encrypted message, obtains h(r2), and then verifies whether it is correct. If it is correct, the mutual authentication is completed. Otherwise, access is denied.
3.4. Password Change Procedure
In our method, when the user wants to change their password, they do not need the help of the CA. Figure 6 shows the lines and points used in the user password change procedure.
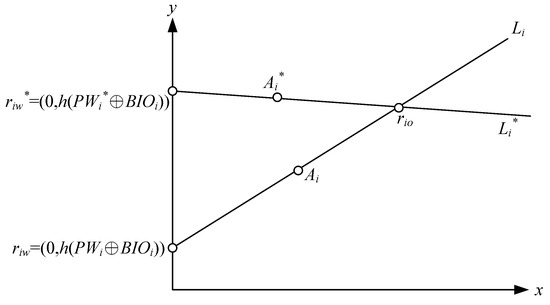
Figure 6.
User password change phase.
Step 1: The user keys in their IDi and PWi, and then the mobile phone scans their biometric feature BIOi at the sensor.
Step 2: The mobile phone checks h(IDi) and verifies whether h2(PWi⊕BIOi) is equal to Vi. If the information is verified, the user can key in their new password PWi*. The mobile phone sets the point riw = (0, h(PWi⊕BIOi)), calculates the point rio = 2Ai − riw, computes the new point riw* = (0, h(PWi*⊕BIOi)), computes the new point Ai* = (riw*+rio)/2, and calculates the new Vi* = h2(PWi*⊕BIOi). It then replaces the stored Ai and Vi with Ai* and Vi*, respectively.
4. Analysis
4.1. Definition
- A fragile key has a very low entropy value (e.g., only a password is used to protect access), and an attacker can guess the user’s password within polynomial time. On the contrary, a strong key usually has a high entropy value (e.g., password plus biometric information and mobile phone), such that the attacker cannot guess the user password within polynomial time [14]. Additionally, any two people cannot have the same biometric information.
- In this research, the hash function is a one-way collision-free hash function (e.g., SHA-512 [32]). When the value of x is given, this hash function can easily calculate h(x). However, if the value of h(x) is given, it is difficult to push back x without incurring a high computational cost.
- During the login process, this secure hardware has retrial restrictions to prevent attackers from using brute force cracking techniques to guess the user’s password.
4.2. Security Analysis
- Higher security level: Many papers have already proven that the security of the three-factor authentication scheme is stronger than the security of the two-factor authentication scheme.
- Anonymity and identity protection: In the login procedure, the user’s original name is converted into an alias (e.g., AIDi = ri∙h(IDi)). The generation of the alias is based on a random number (i.e., Step 4 of the login procedure). The random number generated by each login process is different. Therefore, the attacker cannot know the original identity of the user without knowing the random number ri. In addition, our anonymity mechanism is a dynamic identity process. In the registration phase, the SIM card does not store the identity of the user. Therefore, the attacker cannot retrieve the user identity, even if the attacker obtains the SIM card. In GAME, we use a hash function to protect the identity of the user (i.e., h(IDi)).
- Resistance to replay attack: In the login procedure, the login request is rejected if an attacker resends {AIDi, Ai, Ci, T′} to the IGW. Since T′ is inconsistent with the T in Ci, it is different from Ci′. Thus, our method can resist replay attacks. In the authentication procedure, GAME can still resist replay attacks since the message contains the random number. The random number generated is different each time. Therefore, the authentication process will not succeed if an attacker intercepts and replays the authentication message.
- Choose and change passwords easily: Users can select and modify passwords without participating in the CA, which is very convenient for users. Note that this procedure can still be considered a security issue. When users modify their passwords, they must succeed in verification before they execute the password change procedure.
- Fast error detection: In our method, the fast error detection process is performed only on the client side and does not require the IGW to assist in authentication. Therefore, this stage does not consume network transmission resources and IGW computing resources. In the login and password change process, if an attacker tries to guess the password or enters wrong biometric data, the mobile phone can immediately detect the input error (i.e., Step 2 in the login procedure and Step 2 in the password change procedure), and then perform error reporting and lock the card.
- Resistance to offline password guessing attacks: In previous studies, if an attacker captured consecutive login messages {AIDi1, Ai, Ci1, T1} and {AIDi2, Ai, Ci2, T2} at the time points of T1 and T2, they could try to guess the user’s PWi and use the retrieved information to verify their guess. Then, they may calculate the point riw′ = (0,h(PWi′⊕BIOi)) and calculate the intermediate point Bi′ between riw′ and Ai. In addition, the attacker can calculate this riT1′ = (0,h(h(PWi′⊕BIOi)⊕h(T1))) and construct the line LWT1′ passing through the two points of Ci1 and riT1′. Similarly, the attacker can calculate the point riT2′ and the construction line LWT2′. Next, they can compare Bi′ with the intersection of LWT1′ and LWT2′, Bi″. If the values are equal, this means that the password PWi′ guessed by the attacker is correct. However, in our method, the attacker cannot retrieve these values (i.e., riw′, riT1′, and riT2′) because the attacker does not have the user’s biometric BIOi. Thus, our method can resist offline password guessing attacks.
- Resistance to forgery attacks: Although the attacker can intercept the login message {AIDi, Ai, Ci, T}, they cannot forge a valid login message {AIDi, Ai, Ci′, T′} to pass the authentication process. This is because the attacker does not know h(PWi⊕BIOi) and, thus, cannot calculate the point Bi and the corresponding point riT′ = (0, h(h(PWi⊕BIOi)⊕h(T′))). Of course, the attacker will not be able to correctly re-establish the line LWT. Therefore, our solution can resist forgery attacks.
- Resistance to stolen smart device: When the attacker steals the smart device of a user, the attacker still cannot be authenticated successfully. This is because the attacker cannot provide valid biometric identification in login phase. Moreover, the biometric information of the user is not directly stored on the smart device.
- Resistance to server overloading attacks: In previous methods, the entire authentication procedure was executed on the server, making the server vulnerable to overload attacks. Assuming that the user’s mobile phone is stolen by an attacker, in the previous method, the attacker could deduce the user’s identity through intercepted messages. Even if the attacker types in the wrong password, a large number of malicious authentication request messages can be generated on the server. These malicious authentication request messages will cause server computing overload. However, this situation cannot happen with our method, because (i) our method supports the authentication of biometric information, and (ii) our method supports fast error detection. Therefore, when the user enters the wrong ID, password, or biometric message, the mobile phone will not generate a malicious authentication request message to the server.
- Mutual authentication: A mutual authentication procedure is supported by our authentication method. The server needs to verify that the user is legitimate, and the user also needs to ensure that the server is not forged. When mutual authentication is successful, the security of the overall system can be ensured.
- Session key generation: After the authentication process, a session key is generated between the user and the IGW to provide secure communication. The IGW responds with a message {SIDj, M1, M2} to the mobile phone. After the mobile phone receives the message, it calculates h(r1), takes out r2, and then checks whether h(SIDj||r2) is equal to M2. If it is correct, the session key SKij = (r1||r2) is generated, and the encrypted message SKij⊕h(r2) is sent to the IGW. The session key is generated from two random numbers through a hash function; thus, each session key is different and cannot be pushed back.
4.3. Comparison with Other Schemes
We compared our scheme with related existing schemes [28,29,30]. Table 2 shows the comparisons of security features. Obviously, the proposed scheme provides the most security properties.

Table 2.
Comparisons of security features.
4.4. Computation Analysis
We measured the computation time required for various operations. As hardware, we use the UP Board IoT gateway (Raspberry Pi compatible) developed by AAEON as the test platform [33], as shown in Figure 7. The operating system was a 64 bit Windows 10, the memory was 4 GB, and the CPU was an Intel Atom 1.44 GHz. Table 3 shows the measured calculation time of each operation. Since the proposed method only uses arithmetic operations, XOR operations, and hash functions, the calculation time is much shorter than the RSA authentication method. Table 4 compares the computational costs of the proposed scheme and those of other schemes. Tm, TR, Th, Ta, and Ts denote the execution times of an ECC point multiplication, fuzzy extractor function, hash function, and an arithmetic and symmetric key encryption/decryption, respectively. The scheme in [30] featured the lowest computational cost, but it suffered from many attacks.

Figure 7.
AAEON UP Board (IoT gateway).

Table 3.
Computational time.

Table 4.
Comparison of computational cost with other schemes.
5. Conclusions
Since most of the authentication schemes are based on ID/password, security is obviously insufficient. In this paper, we proposed an anonymous remote user authentication mechanism based on geometric methods, whereby we used a combination of password and user’s biometric information to provide a more secure authentication mechanism. Moreover, GAME only uses arithmetic operations and hash functions; thus, the computational complexity of the method is extremely low, and the calculation time is much shorter than that of traditional asymmetric encryption authentication methods. Therefore, our method is very suitable for application services on mobile devices in an IoT environment. Lastly, the proposed method satisfies the following security properties: it is anonymous, can resist forgery attacks, can resist repeated attacks, can quickly detect errors, can resist offline password guessing attacks, can resist server overload attacks, and can enable easy selection and modification of the password.
Author Contributions
Conceptualization, M.-C.C.; methodology, M.-C.C. and C.-C.Y.; software, C.-C.Y.; investigation, M.-C.C.; resources, M.-C.C.; data curation, C.-C.Y.; writing—original draft preparation, M.-C.C.; writing—review and editing, M.-C.C. and C.-C.Y.; supervision, M.-C.C. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Ministry of Science and Technology, R.O.C., under grants MOST 107-2221-E-163-001-MY3.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Chuang, M.-C.; Chen, M.C. An anonymous multi-server authenticated key agreement scheme based on trust computing using smart cards and biometrics. Expert Syst. Appl. 2014, 41, 1411–1418. [Google Scholar] [CrossRef]
- AL-Turjman, F.; Deebak, D.B. Seamless authentication: For IoT-big data technologies in smart industrial application systems. IEEE Trans. Ind. Inform. 2021, 17, 2919–2927. [Google Scholar]
- Wu, T.-C. Remote login authentication scheme based on a geometric approach. Comput. Commun. 1995, 18, 959–963. [Google Scholar] [CrossRef]
- Hwang, M.-S. Cryptanalysis of a remote login authentication scheme. Comput. Commun. 1999, 22, 742–744. [Google Scholar] [CrossRef]
- Chien, H.-Y.; Jan, J.-K.; Tseng, Y.-M. A modified remote login authentication scheme based on geometric approach. J. Syst. Softw. 2001, 55, 287–290. [Google Scholar] [CrossRef]
- Chang, C.-C.; Lin, I.-C. Cryptanalysis of the modified remote login authentication scheme based on a geometric approach. Informatica 2005, 16, 37–44. [Google Scholar] [CrossRef]
- Ku, W.-C.; Chang, S.-T.; Chen, H.-H.; Tsaur, M.-J. Weakness and simple improvement of a password authentication scheme based on geometric approach. In Proceedings of the IEEE Conference on Local Computer Networks (LCN), Sydney, Australia, 17 November 2005; pp. 472–473. [Google Scholar]
- Chuang, M.-C.; Lee, J.-F. An anonymous remote user authentication scheme based on a geometric approach for wireless networks. In Proceedings of the IEEE International Conference on Consumer Electronics, Communications and Networks (CECNet), Xianning, China, 16–18 April 2011; pp. 1015–1018. [Google Scholar]
- Lee, J.K.; Ryu, S.R.; Yoo, K.Y. Fingerprint-based remote user authentication scheme using smart cards. Electron. Lett. 2002, 38, 554–555. [Google Scholar] [CrossRef]
- Ku, W.; Chang, S.; Chiang, M. Further cryptanalysis of fingerprint-based remote user authentication scheme using smartcards. Electron. Lett. 2005, 41, 240–241. [Google Scholar] [CrossRef]
- Chang, C.-C.; Lin, I.-C. Remarks on fingerprint-based remote user authentication scheme using smart cards. ACM SIGOPS Oper. Syst. Rev. 2004, 38, 91–96. [Google Scholar] [CrossRef]
- Lin, C.-H.; Lai, Y.-Y. A flexible biometrics remote user authentication scheme. Comput. Stand. Interfaces 2004, 27, 19–23. [Google Scholar] [CrossRef]
- Mitchell, C.J.; Tang, Q. Security of the Lin-Lai Smart Card Based User Authentication Scheme, Technical Report. 2005. Available online: http://www.rhul.ac.uk/mathematics/techreports (accessed on 1 May 2021).
- Fan, C.-I.; Lin, Y.-H. Provably secure remote truly three-factor authentication scheme with privacy protection on biometrics. IEEE Trans. Inform. Forensics Secur. 2009, 4, 933–945. [Google Scholar] [CrossRef]
- Khan, M.K.; Zhang, J. An efficient and practical fingerprint-based remote user authentication scheme with smart cards. In Springer Lecture Notes in Computer Science, Proceedings of the International Conference on Information Security Practice and Experience, Hangzhou, China, 11–14 April 2006; Springer: Berlin, Germany, 2006; pp. 260–268. [Google Scholar]
- Khan, M.K.; Zhang, J.; Wang, X. Chaotic hash-based fingerprint biometric remote user authentication scheme on mobile devices. Chaos Solitons Fractals 2008, 35, 519–524. [Google Scholar] [CrossRef]
- Xu, J.; Zhu, W.; Feng, D. Improvement of a fingerprint-based remote user authentication scheme. In Proceedings of the IEEE International Conference on Information Security and Assurance (ISA), Busan, Korea, 24–26 April 2008; pp. 87–92. [Google Scholar]
- Li, C.-T.; Hwang, M.-S. An efficient biometrics-based remote user authentication scheme using smart cards. J. Netw. Comput. Appl. 2010, 33, 1–5. [Google Scholar] [CrossRef]
- Mishra, D.; Das, A.K.; Mukhopadhyay, S. A secure user anonymity-preserving biometric-based multi-server authenticated key agreement scheme using smart cards. Expert Syst. Appl. 2014, 41, 8129–8143. [Google Scholar] [CrossRef]
- Lu, Y.; Li, L.; Yang, X.; Yang, Y. Robust biometrics based authentication and key agreement scheme for multi-server environments using smart cards. PLoS ONE 2015, 10, e0126323. [Google Scholar] [CrossRef]
- Lu, Y.; Li, L.; Peng, H.; Yang, Y. A biometrics and smart cards-based authentication scheme for multi-server environments. Secur. Commun. Netw. 2015, 8, 3219–3228. [Google Scholar] [CrossRef]
- Dammak, M.; Boudia, O.R.M.; Messous, M.A.; Senouci, S.M.; Gransart, C. Token-based lightweight authentication to secure IoT networks. In Proceedings of the IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 11–14 January 2019; pp. 1–4. [Google Scholar]
- Gupta, A.; Tripathi, M.; Shaikh, T.J.; Sharma, A. A lightweight anonymous user authentication and key establishment scheme for wearable devices. Comput. Netw. 2019, 149, 29–42. [Google Scholar] [CrossRef]
- Lyu, Q.; Zheng, N.; Liu, H.; Gao, C.; Chen, S.; Liu, J.J.I.A. Remotely access “My” smart home in private: An antitracking authentication and key agreement scheme. IEEE Access 2019, 7, 41835–41851. [Google Scholar]
- Ma, M.; He, D.; Wang, H.; Kumar, N.; Choo, K.-K.R. An efficient and provably secure authenticated key agreement protocol for fog-based vehicular ad-hoc networks. IEEE Internet Things J. 2019, 6, 8065–8075. [Google Scholar] [CrossRef]
- Renuka, K.M.; Kumari, S.; Zhao, D.; Li, L. Design of a secure password-based authentication scheme for M2M networks in IoT enabled cyber-physical systems. IEEE Access 2019, 7, 51014–51027. [Google Scholar] [CrossRef]
- Li, X.; Peng, J.; Obaidat, M.S.; Wu, F.; Khan, M.K.; Chen, C. A secure three-factor user authentication protocol with forward secrecy for wireless medical sensor network systems. IEEE Syst. J. 2019, 14, 39–50. [Google Scholar] [CrossRef]
- Shuai, M.; Yu, N.; Wang, H.; Xiong, L. Anonymous authentication scheme for smart home environment with provable security. Comput. Secur. 2019, 86, 132–146. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Park, Y. An efficient, anonymous and robust authentication scheme for smart home environments. Sensors 2020, 20, 1215. [Google Scholar] [CrossRef] [Green Version]
- Xiang, A.; Zheng, J. A situation-aware scheme for efficient device authentication in smart grid-enabled home area networks. Electronics 2020, 9, 989. [Google Scholar] [CrossRef]
- Oh, J.; Yu, S.; Lee, J.; Son, S.; Kim, M.; Park, Y. A secure and lightweight authentication protocol for IoT-based smart homes. Sensors 2021, 21, 1–24. [Google Scholar]
- NIST, U.S. Department of Commerce. Secure Hash Standard, U.S. Federal Information Processing Standard (FIPS); NIST, U.S. Department of Commerce: Gaithersburg, MD, USA, 2002. [Google Scholar]
- AAEON. Available online: http://www.aaeon.com/tw/ (accessed on 1 March 2021).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).