Lightweight Secure Authentication and Key Distribution Scheme for Vehicular Cloud Computing
Abstract
1. Introduction
- We propose a key distribution model that is efficient and secure. We use CP-ABE algorithm for keys encryption instead of using this algorithm for messages encryption. This way, we just need to encrypt keys during the registration step. Vehicles can then communicate with RSU using symmetrical encryption. The model securely ensures fast transmission of messages.
- GUARANTY protocol ensures vehicles’ privacy by using Pseudo-ID instead of the vehicle’s original ID.
- Our scheme ensures vehicles authentication by using IBS signature scheme to authenticate legitimate vehicles.
- V2V communication is secured in our approach by using authentication key ‘AuK’ transmitted by RSU to all authenticated vehicles.
2. Related Work
3. Background
3.1. Network Architecture
- Vehicle: In our network model, a vehicle has sensors to sense traffic congestion and status, Global Positioning System (GPS), On-Board Unit (OBU), and Event Data Recorder (EDR). The vehicle is the main component of the proposed network architecture.
- On-Board Unit (OBU): Each vehicle is equipped with an OBU to collect its information, such as the position, speed, and acceleration/deceleration, and transmits it to vehicles or RSUs within its transmission range through the wireless medium. As stated in Reference [24], “it uses the Wireless Access in Vehicular Environment (WAVE) standard, which is based on the emerging IEEE 802.11p specification”.
- Road Side Units (RSU): It is a fixed infrastructure deployed on the roadside to monitor the traffic or in the road intersections to manage the traffic lights. It acts as a gateway for the vehicles to access the Internet. The main use of RSUs in the proposed approach is to provide secret key and authentication key transmission in a secure manner.
- Vehicle-to-Vehicle (V2V) communication: Vehicles communicate with other vehicles within their transmission range through a direct wireless transmission of data without need of using fixed infrastructures. In GUARANTY algorithm, vehicles must be authenticated to establish a secure communication between them. The registration, Pseudo-ID formation, and authentication phases are used at the start of vehicles’ trip or when the vehicle’s secret key is threatened. In this case, the vehicle can re-register itself at the nearby RSU to have a new secret key.
- Vehicle-to-RSU (V2R) communication: This is the communication between vehicles and RSU, and it is usually done via wireless transmission. In our model, vehicles send a registration request for key generation and a signature request for its authentication.
- Vehicle-to-Internet (V2I) communication: It is a communication, between vehicles and the Internet, which can be established directly or indirectly using the RSU.
- Cloud Center: A virtual server, in a cloud computing platform, which offers many services, such as computing capabilities, storage, and communication resources on demand. The cloud generates the keys. All vehicles’ information is stored in the database and then used in vehicles’ private key generation.
3.2. Network Security Model
- The RSUs are connected via a wired connection, and the communication between them is carried out via a secure channel.
- Vehicles are in an area covered completely by RSUs.
- The cloud is trusted and secure.
- The communication between the cloud and the RSU is carried out via a secure channel.
- The vehicles contain OBUs that are equipped with processing and storage capabilities to carry out the encryption/decryption.
- Cloud-based Revocation Authorities (CRAs) are responsible for the revocation process.
- Attacks on confidentiality: The aim of these kind of attacks is to access confidential data illegally. Eavesdropping and Man in the Middle (MiM) are examples of these attacks.
- Attacks on authentication: The objective of this attack is to claim that it is an authorized vehicle, such as impersonate and Sybil attacks.
- Attacks on vehicles’ privacy: The objective of this attack is to expose the identity of vehicles, such as tracking attacks.
3.3. Access Structures
3.4. Access Tree
- : number of children of x.
- : threshold value, where:If = 1, the threshold gate is an ’OR’ gate.If = , the threshold gate is an ’AND’ gate.
- : represents node’s index.
- : is the attribute value associated with the leaf node x.
- : is the parent of x in the tree .
3.5. Linear Secret Sharing Schemes (LSSSs)
- The piece of each party is a vector over, in which there exists a constant for each k, and the piece of is taken from .
- We define a share generating matrix (M) for , with l rows and n columns in a similar way to Reference [25]. “For all i = 1, … l, where ‘i’ is the row of M. The function defines the party labeling row ‘i’ as . The column vector v = (s, r2, …, rn), where s ∈ F is the secret to be shared, and r2, …, rn ∈ F are randomly chosen. So, is the vector that shares the secret s according to . The share belongs to party ” [25].
3.6. Bilinear Maps
- Bilinearity: for all u, v ∈ G1 and a, b ∈ Zp, we have e(, ) = e(.
- Non-degeneracy: e (g1, g1)≠1.
3.7. Ciphertext-Policy Attribute-Based Encryption (CP-ABE)
- Setup: The algorithm takes the security parameter and the attribute of the user as input. It generates the public key (PK) and a master key (MK) as output.
- Encryption: The algorithm has as input: the PK, a message, and an access structure. It will encrypt the message and generate a ciphertext, where only the users that possess the set of attributes that satisfies the access structure will be able to decrypt the message.
- Key Generation: The values of the master key and a set of attributes (describing the key) are the input to the algorithm, which generates a private key SK.
- Decryption: The algorithm gets the public key, the ciphertext, and the private key input. The algorithm checks if the set of attributes satisfies the access structure AS (defined in the ciphertext), and then it will decrypt the ciphertext and return the original message.
3.8. Identity-Based Signature (IBS)
- Setup: The master key is generated by a certified authority and broadcasted to all vehicles via RSUs.
- Extraction: Vehicle generates its private key based on its identifier, the master key, and timestamp.
- Signing: Vehicles encrypts the message (Msg) using its private key to generate the signature (SIG).
- Verification: The validity of the signature is verified by the receiving vehicle.
4. Our Proposed GUARANTY Scheme
4.1. Registration
- Step 1: The cloud assigns an identifier , a verification number , and an authentication key ‘AuK’ to each RSU. It also registers all vehicles’ ID with their chassis numbers (CN).
- Step 2: Each vehicle must register itself at the nearby RSU, when it enters or leaves the particular region, by broadcasting a Registration Request (RR) message encrypted with the public key of RSU . The registration request contains the vehicle’s attribute values (vehicle identifier, location, current speed, and the direction value, etc.). The RSU verifies location-related attributes using location proof methodologies [29]. At the end, the vehicle’s attribute values are transmitted to the cloud with the VN, where VN ensures the legitimacy of the RSU. In the case where the RSU is malicious, it will be detected by the cloud by checking the VN, and then it will be revoked.T represents the current time, represents vehicle’s identifier, represents the speed of vehicle Z, represents the direction of vehicle Z, represents the position of vehicle Z, and represents the identifier of the nearest RSU.
- Step 3: The cloud generates two keys, after receiving the vehicle’s attribute values, and sends them to the RSU: the attribute key ‘AK’ and the secret key ‘SK’. When RSU receives the two keys, it must encrypt the secret key ’SK’ using attribute key ‘AK’ of the corresponding vehicle.For the transmission of the secret key ‘SK’, we apply the CP-ABE algorithm, which has the following five parts:
- a
- Setup: When the cloud receives the attribute values of the vehicle, it runs the setup algorithm. It takes attributes set S as input in which the set of attributes contains the vehicle’s attributes transmitted by the vehicle and the corresponding chassis number (CN) registered in the cloud. The cloud then generates the public and the master key as output. For this, it chooses two groups G1 and G2 of prime order P, and two generators and . It chooses also two random exponents b, . The public key is generated as:The master key is set as:
- b
- Key-generation: To generate the attribute key (AK), the cloud gets the master-key (MK) and a set of attributes S as input. It generates the attribute key AK corresponding to the set of attributes of the vehicle. The algorithm first generates a random number t and then creates the attribute key as:where is the attribute string of attribute x hashed to an element of G1. To generate the secret key, the cloud chooses a random number s and computes the secret key:
- c
- Encryption: The algorithm defines the access matrix (M, k) based on a given a LSSS. The matrix M is defined as (l*n ), where l is the number of rows, n is the number of columns, and k refers to the function that maps rows of M to the attributes. The algorithm selects a random vector v= (s, , …, ), where the exponent s is randomly chosen as the secret to be shared in secret key generation. The other values are used to share the encryption exponent s. It calculates , where i takes value from 1 to l. The algorithm also chooses random , …, . The ciphertext is published as:So, the cloud generates keys, sends them to the RSU, and then it encrypts the secret key using the attribute key and sends the ciphertext to the corresponding vehicle.
- d
- Decryption: In this step, the vehicle takes as input a ciphertext (CT) and the attribute key for a set of attributes S. The Lagrange basis polynomials [30] evaluated at zero, , are computed for the indices involved in access policy by:
| Algorithm 1 Registration Algorithm. |
The cloud registers all vehicles ID with their chassis number and RSUs ID with their RSU broadcasts in the network sends encrypted by . RSU verifies: is legitimate RSU transmits , , to the cloud. Cloud runs the Setup algorithm. Cloud runs the key generation algorithm. Cloud transmit ‘SK’ and ‘AK’ keys to the RSU. RSU runs encryption algorithm. runs decryption algorithm. RSU runs System Revocation. |
4.2. Pseudo-ID Formation
- Step 1: RSU will encrypt the secret key ‘SK’ using the attribute key ‘AK’ and broadcasts it on the network. Vehicles within the range of particular RSU will acquire the encrypted secret key. The vehicle that satisfies the attribute values will decrypt the message and recover the secret key for Pseudo-ID generations.
- Step 2: Pseudo-ID of the vehicle (z) is generated by encrypting the original ID of the vehicle (z) by its secret key and sends it to the RSU as:, where is the generated Pseudo-ID of vehicle Z, T is the current time, is the encrypted value of the vehicle’s ID using the secret key, and is the ID of the RSU.
| Algorithm 2 Pseudo-ID Formation Algorithm. |
|
4.3. Authentication
- A-
- V2I and I2V Authentication: Identifier-Based Signature (IBS) algorithm is used to ensure the authentication among vehicles and Infrastructures as illustrated in Algorithm 3. The V2I and I2V authentication are explained next:
- Step 1: Each RSU broadcasts its information periodically to all vehicles within its rang. This information is in this form:where is the ID of RSU, T is the current time, and is the public key of RSU.
- Step 2: Vehicles acquire the information from RSU. Vehicles that need to generate their signature will send a signature request message to the RSU. The signature request has this form:where is the ID of RSU, is the Pseudo-ID of the vehicle Z, T is the current time, and is the IBS generated by vehicle using its ID and the current time. The and the current time values are concatenated, and the resulting value is encrypted using the secret key (), which results in .
- Step 3: After receiving the signature request from the vehicle, the RSU verifies whether the vehicle is legitimate(by decrypting the signature using the secret key of vehicle Z and verifying the identifier and the time). If it is a legitimate vehicle, the RSU encrypts the authentication key(AuK) using the secret key of vehicle Z and broadcasts it with an authentication message to indicate that is legitimate. The authentication signature message has this form:where is the ID of RSU, T is the current time, is Pseudo-ID of vehicle z, is the signature of vehicle Z, AuM is an authentication message to indicate that the vehicle which has the is legitimate, and is an authentication key encrypted by the secret key of vehicle Z. Only the vehicle authenticated (vehicle Z) can access to this key. All vehicles within RSU’s transmission range save the Pseudo-ID of vehicle Z in their authentication table for V2V authentication.
- B-
- V2V Authentication: To establish secure communication between vehicles, V2V authentication is carried out (Figure 3 describes the sequence diagram of the V2V authentication process). Algorithm 4 presents the V2V authentication process. When a vehicle wants to communicate with other vehicles, it will generate an authentication signature and send a communication request message:where is the Pseudo-ID of vehicle Z, T is the current time, CReq is the communication request message, is the IBS (generated by vehicle Z using its ID, and the current time), and is the authenticated signature of vehicle Z. The Pseudo-ID of vehicle Z (PIDz) and the current time value are concatenated, and the resulting value is encrypted using the secret key (AuK), which results in . is the ID of the RSU which has authenticated the vehicle. Each vehicle that receives the communication request message of vehicle Z must verify in its authentication table, and it must verify also the authentication signature (by decrypting the signature using AuK and verifying the Pseudo-ID and the time).
| Algorithm 3 V2I authentication Algorithm. |
calculates (). sends to RSU. RSU verifies: is valid Broadcast Save and in authentication table. RSU runs System Revocation. |
| Algorithm 4 V2V authentication Algorithm |
sends to and registered at the same RSU verifies in its authentication table: Valid verifies the authentication signature: correct Reply = accept Reply = Refuse Runs System revocation algorithm Reply = Refuse Runs System revocation algorithm sends to RSU2. RSU2 transmits verification request to RSU. RSU sends Reply and Auk to RSU2. RSU2 sends Reply and AuK encrypted by ’’ to . sends reply to . |
4.4. Cryptography
- A-
- V2I Communication: After the distribution of SK in a secure manner, we use symmetric cryptography for the transmission of messages. Vehicles must encrypt the message using their secret key (SK) to ensure confidentiality and the security of information. The RSU then decrypts the message and transmits it to the cloud via a secure channel. When the cloud sends the answer, the RSU must also encrypt the message using the secret key SK of the vehicle. In this way, we ensure secure communication between cloud and vehicles. V2I communication process is described in Algorithm 5.
- B-
- V2V Communication: Each vehicle in an RSU’s transmission range must authenticate itself on the RSU, and, when the authenticates the vehicle, it will send an authentication message with authentication key (). All vehicles authenticated on the same RSU will obtain the same authentication key (). So, we can provide a secure communication session with vehicles authenticated by the same RSU. Vehicles authenticated by different RSU () can obtain the () from its nearby RSU () and provide a secure communication session with other vehicles. Algorithm 6 shows the V2V communication process.Vehicles that want to communicate with other vehicles must encrypt the message using the authentication key (AuK), and only authenticated vehicles can decrypt the message.
| Algorithm 5 V2I Communication Algorithm. |
sends to RSU. RSU decrypts the message. RSU transmits the message to the cloud. Cloud sends a reply to RSU. RSU send to . |
| Algorithm 6 V2V Communication Algorithm. |
sends to . authenticated by the same RSU decrypts the message. sends to . obtains the Auk from the nearby RSU. decrypts the message. sends to . |
5. Security Analysis and Performance Evaluation
5.1. Security Analysis
- A
- Take the RSU’s information and declare itself that it is the RSU: In this case, the malicious vehicle cannot decrypt the message (vehicles’ attributes) because it does not have the private key of RSU (). The vehicle waits for its for time; then, it will define the RSU as a malicious node after this time, and it will run a System Revocation.
- B
- Take the RSU’s identifier and generate its private and public keys: In this case, the malicious vehicle can access to the vehicles’ attributes but:
- -
- It cannot access to the cloud for keys generation because it does not have the of RSU. If it tries to access the cloud, it will be detected as a malicious node, and then its access will be revoked.
- -
- When it generates false keys (, ), can detect that is wrong because the does not include the real due to cloud access failure of the malicious node to recover the (RSU does not have a verification number). So, the malicious RSU cannot generate and cannot use the vehicles’ attributes to access the (RSU does not have the ). When vehicles receive a wrong from a node, they will define it as a malicious node and run the System Revocation.
- -
- Impersonate attack: is an attack that harms the authentication of vehicles. In this kind of attack, an attacker impersonates a good vehicle to receive its messages, and get privileges not granted to it. It can also do malicious things and declare that a legitimate vehicle did them. In our proposed scheme, malicious vehicles can use the Pseudo-ID () and the signature of the legitimate vehicle to communicate with the other vehicles. So, it will send a communication request: <, T, CReq, , , to vehicle z. Vehicle z must verify the of vehicle ‘i’ to detect that its signature is not satisfied (it does not have the real AuK) and declares it as a malicious vehicle.
- -
- Man in the Middle (MiM) attack: Tt is an attack that harms the confidentiality and the integrity of vehicles. In this case, a malicious vehicle listens to the communication between two vehicles. GUARANTY algorithm ensures the confidentiality of:
- -
- Messages transmitted between vehicles, by the encryption of messages using the authentication key (AuK).
- -
- Messages transmitted between vehicles and RSU, by the encryption of messages using the vehicle’s secret key (SK).
- -
- Attributes transmitted during the registration step, by the encryption of attributes using the public key of RSU ().
- -
- Sybil attack: this attack harms the authentication of vehicles. In this case, an attacker generates multiple fake vehicles on the road with different identities and tries to authenticate them at the same time. Our approach can detect this attack:
- -
- If the malicious vehicle communicates with RSU to register and authenticate itself. The RSU detects that it is a malicious vehicle by verifying the location-related attributes using location proof methodologies [29].
- -
- If the malicious vehicle ‘mal’ generates its Pseudo-ID and its signature and establishes a communication directly with other vehicles by sending a communication request <, T, CReq, (), (),>. They can detect that it is a malicious vehicle by verifying the and in their authentication table.
- -
- Eavesdropping attack: The proposed algorithm authenticates the vehicle properly, which does not allow the intruder to access the information circulating in the network during the transmission process. Furthermore, the symmetric session keys (Sk, AuK) is used to encrypt the collected data. This approach keeps the data confidential and stops the attacker from accessing the message.
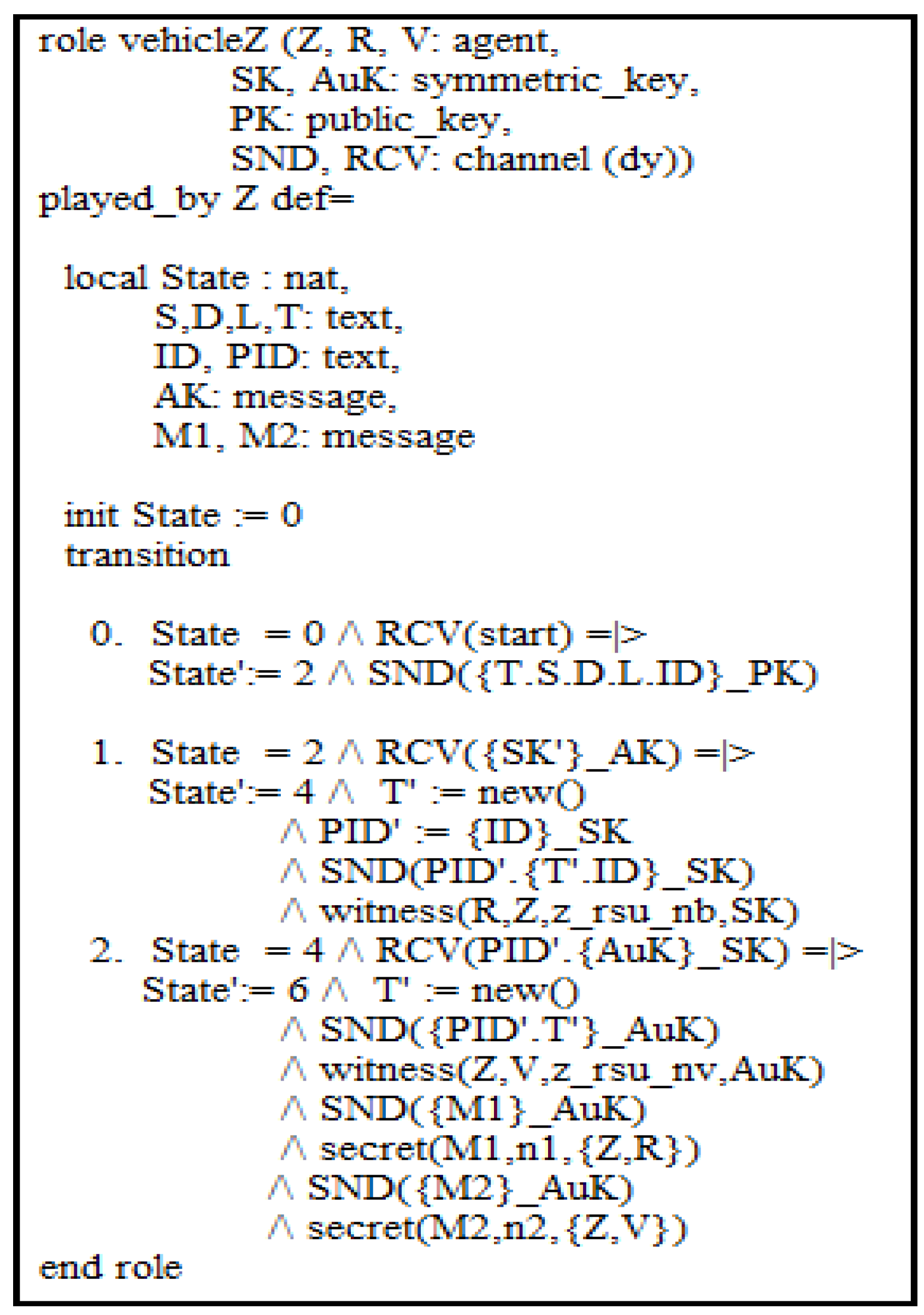
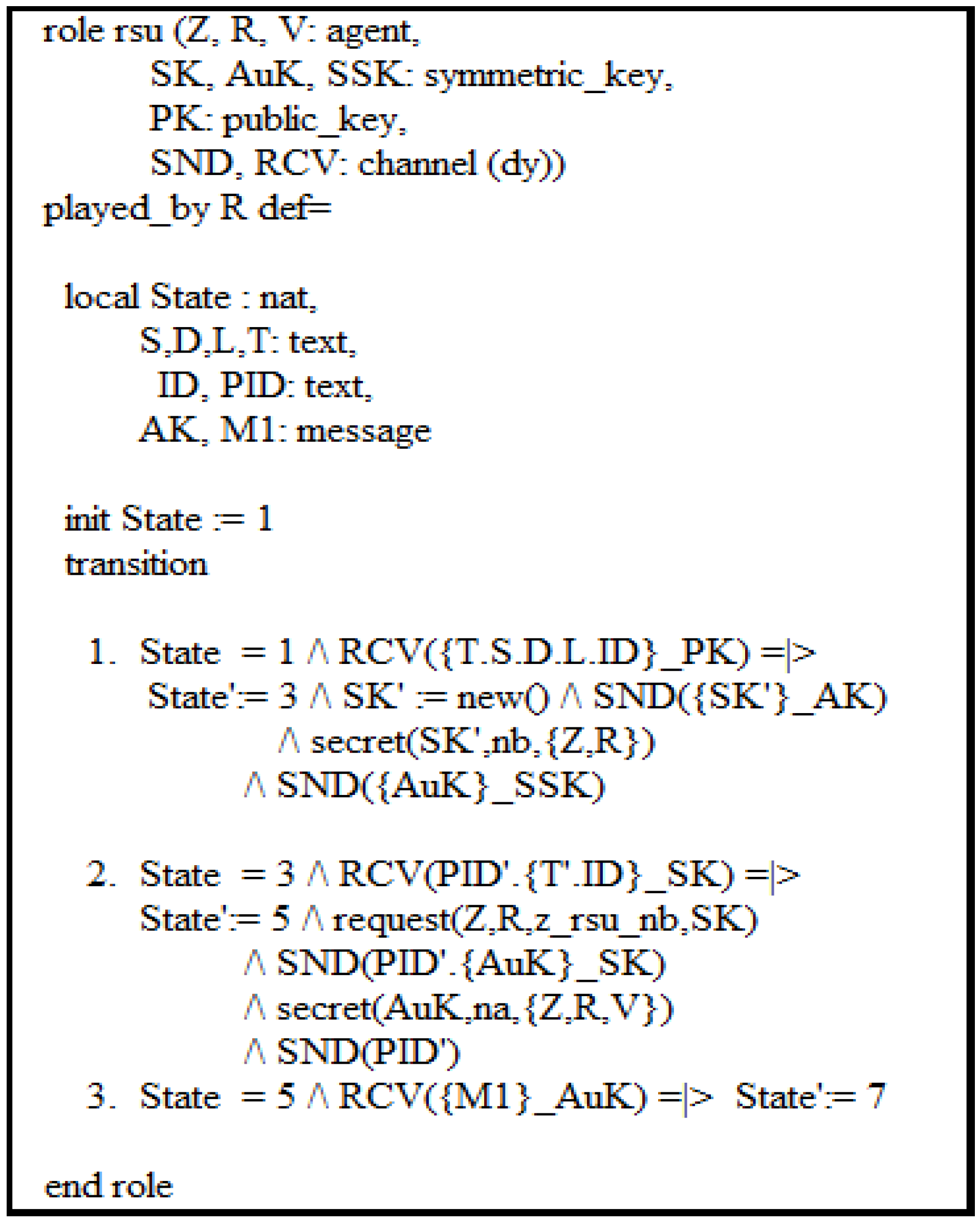
5.2. Specification of GUARANTY Scheme Using AVISPA Tool
- Secrecy_of nb indicates that SK is kept secret to vehicle Z and RSU.
- Secrecy_of na indicates that AuK is only known by RSU, vehicle Z, and vehicle V.
- Secrecy_of n1 signifies that the message M1 is kept secret between vehicle Z and RSU.
- Secrecy_of n2 signifies that the message M2 is only known by vehicle Z and vehicle V.
- Authentication_on z_rsu_nb signifies that RSU creates a secure key SK, and vehicle Z obtains it securely via message; if RSU receives the same value of SK from vehicle Z, RSU then authenticates vehicle Z.
- Authentication_on z_rsu_nv signifies that RSU creates an authentication key AuK and sends it securely to an authenticated vehicle V. Vehicle Z receives the authentication key securely via message; if vehicle V receives the same value of AuK from vehicle V, vehicle V then authenticates vehicle Z.
5.3. Computational Complexity Analysis
5.4. Performance Evaluation
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| Speed of vehicle Z | |
| Direction of vehicle Z | |
| Localization of vehicle Z | |
| Identifier of RSU | |
| Verification Number of RSU | |
| Secret key of vehicle Z | |
| Attribute key of vehicle Z | |
| Identifier of vehicle Z | |
| Pseudo-ID of vehicle Z | |
| Signature of vehicle Z | |
| Authentication Signature of vehicle Z | |
| CReq | Communication request |
| AuK | Authentication Key |
| Msg | Message |
| AuM | Authentication Message |
| VER | Verification Message |
| RR | Registration Request |
| Public Key of RSU | |
| MK | Master Key |
| CT | Ciphertext |
| Chassis Number of vehicle Z |
Appendix A


References
- De Souza, P.R.R.; Matteussi, K.J.; Veith, A.D.S.; Zanchetta, B.F.; Leithardt, V.R.; Murciego, Á.L.; De Freitas, E.P.; Dos Anjos, J.C.; Geyer, C.F. Boosting Big Data Streaming Applications in Clouds With BurstFlow. IEEE Access 2020, 8, 219124–219136. [Google Scholar] [CrossRef]
- Trubia, S.; Severino, A.; Curto, S.; Arena, F.; Pau, G. Smart Roads: An Overview of What Future Mobility Will Look Like. Infrastructures 2020, 5, 107. [Google Scholar] [CrossRef]
- Zhu, J.; Xu, W. Real-Time Data Filling and Automatic Retrieval Algorithm of Road Traffic Based on Deep-Learning Method. Symmetry 2021, 13, 1. [Google Scholar] [CrossRef]
- Goumidi, H.; Aliouat, Z.; Harous, S. Vehicular cloud computing security: A survey. Arab. J. Sci. Eng. 2020, 45, 2473–2499. [Google Scholar] [CrossRef]
- Hasrouny, H.; Samhat, A.E.; Bassil, C.; Laouiti, A. VANet security challenges and solutions: A survey. Veh. Commun. 2017, 7, 7–20. [Google Scholar] [CrossRef]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the IEEE Symposium on Security and Privacy, Oakland, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar] [CrossRef]
- Nkenyereye, L.; Park, Y.; Rhee, K.H. Secure vehicle traffic data dissemination and analysis protocol in vehicular cloud computing. J. Supercomput. 2018, 74, 1024–1044. [Google Scholar] [CrossRef]
- Wan, C.; Zhang, J. Efficient identity-based data transmission for VANET. J. Ambient Intell. Humaniz. Comput. 2018, 9, 1861–1871. [Google Scholar] [CrossRef]
- Lu, Z.; Liu, W.; Wang, Q.; Qu, G.; Liu, Z. A privacy-preserving trust model based on blockchain for vanets. IEEE Access 2018, 6, 45655–45664. [Google Scholar] [CrossRef]
- Arora, A.; Yadav, S.K. Block chain based security mechanism for internet of vehicles (iov). In Proceedings of the 3rd International Conference on Internet of Things and Connected Technologies, (ICIoTCT), Jaipur, India, 26–27 March 2018; pp. 267–272. [Google Scholar] [CrossRef]
- Feng, X.; Wang, L. PAU: Privacy Assessment method with Uncertainty consideration for cloud-based vehicular networks. Future Gener. Comput. Syst. 2019, 96, 368–375. [Google Scholar] [CrossRef]
- SathyaNarayanan, P. A sensor enabled secure vehicular communication for emergency message dissemination using cloud services. Digit. Signal Process. 2019, 85, 10–16. [Google Scholar] [CrossRef]
- Hussain, R.; Rezaeifar, Z.; Lee, Y.H.; Oh, H. Secure and privacy-aware traffic information as a service in VANET-based clouds. Pervasive Mob. Comput. 2015, 24, 194–209. [Google Scholar] [CrossRef]
- Jenefa, J.; Anita, E.M. Secure Vehicular Communication Using ID Based Signature Scheme. Wirel. Pers. Commun. 2018, 98, 1383–1411. [Google Scholar] [CrossRef]
- Huang, D.; Verma, M. ASPE: Attribute-based secure policy enforcement in vehicular ad hoc networks. Ad Hoc Netw. 2009, 7, 1526–1535. [Google Scholar] [CrossRef]
- Liu, X.; Xia, Y.; Chen, W.; Xiang, Y.; Hassan, M.M.; Alelaiwi, A. SEMD: Secure and efficient message dissemination with policy enforcement in VANET. J. Comput. Syst. Sci. 2016, 82, 1316–1328. [Google Scholar] [CrossRef]
- Safi, Q.G.K.; Luo, S.; Wei, C.; Pan, L.; Yan, G. Cloud-based security and privacy-aware information dissemination over ubiquitous VANETs. Comput. Stand. Interfaces 2018, 56, 107–115. [Google Scholar] [CrossRef]
- Kudva, S.; Badsha, S.; Sengupta, S.; Khalil, I.; Zomaya, A. Towards secure and practical consensus for blockchain based VANET. Inf. Sci. 2021, 545, 170–187. [Google Scholar] [CrossRef]
- Sestrem Ochôa, I.; Reis Quietinho Leithardt, V.; Calbusch, L.; De Paz Santana, J.F.; Delcio Parreira, W.; Oriel Seman, L.; Albenes Zeferino, C. Performance and Security Evaluation on a Blockchain Architecture for License Plate Recognition Systems. Appl. Sci. 2021, 11, 1255. [Google Scholar] [CrossRef]
- Yan, X.; Gu, X.; Wang, J.; Wan, J.; Chen, L. A kind of event trust model for VANET based on statistical method. Wirel. Pers. Commun. 2021, 1–15. [Google Scholar] [CrossRef]
- Green, M.; Hohenberger, S.; Waters, B. Outsourcing the decryption of abe ciphertexts. In Proceedings of the USENIX Security Symposium, Washington, DC, USA, 11–13 August 2011. [Google Scholar]
- Parno, B.; Perrig, A. Challenges in securing vehicular networks. In Proceedings of the Workshop on hot topics in networks (HotNets-IV), New York, NY, USA, 14–15 November 2005; pp. 1–6. [Google Scholar]
- Schneier, B. The Blowfish Encryption Algorithm. 2008. Available online: https://doi.org/http://www.schneier.journal.com/blowfish.html (accessed on 8 May 2012).
- Liang, W.; Li, Z.; Zhang, H.; Wang, S.; Bie, R. Vehicular ad hoc networks: Architectures, research issues, methodologies, challenges, and trends. Int. J. Distrib. Sens. Netw. 2015, 11, 1–11. [Google Scholar] [CrossRef]
- Beimel, A. Secret-sharing schemes: A survey. In International Conference on Coding and Cyptology, Oxford, UK, 12–15 December 2011; Springer: Berlin, Germany, 2011; pp. 11–46. [Google Scholar] [CrossRef]
- Ostrovsky, R.; Sahai, A.; Waters, B. Attribute-based encryption with non-monotonic access structures. In Proceedings of the 14th ACM conference on Computer and communications security, Alexandria, VR, USA, 28–31 October 2007; pp. 195–203. [Google Scholar] [CrossRef]
- Waters, B. Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization. In International Workshop on Public Key Cryptography; Springer: Berlin, Germany, 2011; pp. 53–70. [Google Scholar] [CrossRef]
- Shamir, A. Identity-based cryptosystems and signature schemes. In Workshop on the Theory and Application of Cryptographic Techniques; Springer: Berlin, Germany, 1984; pp. 47–53. [Google Scholar] [CrossRef]
- Saroiu, S.; Wolman, A. Enabling new mobile applications with location proofs. In Proceedings of the 10th workshop on Mobile Computing Systems and Applications, Santa Cruz, CA, USA, 23–24 February; pp. 1–3. [CrossRef]
- Corless, R.M. On a generalized companion matrix pencil for matrix polynomials expressed in the Lagrange basis. In Symbolic-Numeric Computation; Springer: Berlin, Germany, 2007; pp. 1–15. [Google Scholar] [CrossRef]
- Armando, A.; Basin, D.; Boichut, Y.; Chevalier, Y.; Compagna, L.; Cuéllar, J.; Drielsma, P.H.; Héam, P.C.; Kouchnarenko, O.; Mantovani, J.; et al. The AVISPA tool for the automated validation of internet security protocols and applications. In International Conference on Computer Aided Verification; Springer: Berlin, Germany, 2005; pp. 281–285. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theor. 1983, 29, 198–208. [Google Scholar] [CrossRef]








| Ref | Advantages | Techniques Used | Limitations |
|---|---|---|---|
| [7] | Preserves vehicles’ privacy and authentication, short signature verification time | IBS signature; batch verification | Vulnerable because it does not support a proper encryption scheme |
| [8] | Ensures messages confidentiality and integrity; preserves vehicles’ privacy | Lagrange interpolation; algebraic signature | Vulnerable against Sybil and impersonate attacks |
| [9] | provides vehicles’ privacy and trustworthiness | Public keys as identity; reputation management | Certificate update; reputation score update; high computation time and storage capacity |
| [10] | Preserves privacy, authentication, confidentiality using Blockchain technology | Pseudo-ID; key of group; blockchain for authentication | High computation time; high storage capacity |
| [11] | Evaluating privacy protection | Analyzing users’ historical bihaviour | Vulnerable against eavesdropping and spoofing attacks |
| [12] | Secure communication with low delay; avoids information tracking | WAVE protocol; Blowfish protocol | Vulnerable against impersonate and Sybil attacks |
| [13] | Provides the confidentiality of conductor’s location which preserves vehicles’ privacy | Location-based encryption | Messages can be decrypted in the case where malicious vehicle exists at the region Z and at the confident time |
| [14] | Provides V2R authentication and V2V authentication with and without RSU; preserves vehicles’ privacy | IBS signature; IBOOS signature | Vulnerable against eavesdropping, spamming and malware attacks |
| [15] | Provides access control and confidentiality | CP-ABE | Significant decryption time |
| [16] | Preserves access control, confidentiality, and low decryption time | CP-ABE where the decryption task is carried out by RSU | Lacks of vehicles’ privacy and authentication |
| [17] | Ensures vehicles’ privacy, authentication, access control, and confidentiality | CP-ABE to encrypt messages; IBS signature | Lacks of V2V authentication; privacy can be affected when transmitting ID in the registration; high computation time |
| [18] | Provides an efficient and an effective miner node selection strategy in the application of vehicular blockchain | Blockchain technology; service score-based protocol; PBFT consensus algorithm | Lacks of authentication, confidentiality, and access control; high storage capacity |
| [19] | Provides privacy in LPR systems using blockchain | Ethereum private blockchain; Smart contract | Lacks of authentication and confidentiality |
| [20] | Ensures vehicles’ safety using a trust model | Mathematical statistical methods; computation of vehicles’ trust value | Lacks of authentication, confidentiality and integrity |
| GUAR-ANTY | Low computation time; preserves vehicles’ privacy; provides V2R and V2V authentication; secure keys distribution; access control | CP-ABE for key exchange; symmetric cryptography for messages exchange; IBS signature and key group for authentication; Pseudo-ID for privacy | Lacks of messages integrity |
| , | Generators of a group of prime order. |
| Master secret key component. | |
| Exponential function. | |
| The attribute string of attribute x hashed to an element of G1. | |
| M | The access matrix. |
| s | The secret to be shared. |
| k | Function that maps rows of M to the attributes. |
| Valid shares of the secrets. | |
| The Lagrange basis polynomials function. |
| Features | [7] | [8] | [9] | [10] | [11] | [12] | [13] | [14] | [16] | [17] | [18] | [19] | [20] | GUARANTY |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Authentication | √ | × | √ | √ | × | × | × | √ | × | √ | × | × | × | √ |
| Confidentiality | × | √ | × | × | × | √ | × | × | √ | × | × | × | × | √ |
| Privacy | √ | √ | √ | √ | √ | √ | √ | √ | × | √ | √ | √ | √ | √ |
| Secure key distribution | × | × | × | × | × | × | × | × | × | × | × | √ | × | √ |
| Access control | × | × | × | × | × | × | × | × | √ | √ | × | × | × | √ |
| Impersonation attack resistance | √ | × | √ | √ | × | × | × | √ | × | × | × | × | × | √ |
| MIM attack resistance | × | × | × | × | × | × | × | × | × | × | × | × | × | √ |
| Sybil attack resistance | √ | × | √ | √ | × | × | × | √ | × | × | √ | × | √ | √ |
| Eavesdropping attack resistance | × | √ | × | × | × | √ | × | × | √ | × | × | √ | × | √ |
| Tracking attack resistance | √ | √ | √ | √ | √ | √ | √ | √ | × | √ | √ | √ | √ | √ |
| Operation | Complexity |
|---|---|
| Setup | |
| Key Generation | |
| Encryption | |
| Decryption |
| Topology (m) | 5000 × 5000 |
| Number of nodes | 100 |
| Number of RSUs | 4 |
| Communication range of nodes (m) | 300 |
| Speed (m/s) | 30 |
| MAC layer | MAC 802_ 11p |
| Time(s) | 300 s |
| Mobility model | Random Following IDM_ LC |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Goumidi, H.; Harous, S.; Aliouat, Z.; Gueroui, A.M. Lightweight Secure Authentication and Key Distribution Scheme for Vehicular Cloud Computing. Symmetry 2021, 13, 484. https://doi.org/10.3390/sym13030484
Goumidi H, Harous S, Aliouat Z, Gueroui AM. Lightweight Secure Authentication and Key Distribution Scheme for Vehicular Cloud Computing. Symmetry. 2021; 13(3):484. https://doi.org/10.3390/sym13030484
Chicago/Turabian StyleGoumidi, Hadjer, Saad Harous, Zibouda Aliouat, and Abdelhak Mourad Gueroui. 2021. "Lightweight Secure Authentication and Key Distribution Scheme for Vehicular Cloud Computing" Symmetry 13, no. 3: 484. https://doi.org/10.3390/sym13030484
APA StyleGoumidi, H., Harous, S., Aliouat, Z., & Gueroui, A. M. (2021). Lightweight Secure Authentication and Key Distribution Scheme for Vehicular Cloud Computing. Symmetry, 13(3), 484. https://doi.org/10.3390/sym13030484






