Implementing a Symmetric Lightweight Cryptosystem in Highly Constrained IoT Devices by Using a Chaotic S-Box
Abstract
1. Introduction
1.1. Research Background and Motivation
1.2. Related Work
1.3. Contributions of the Work
2. Preliminaries
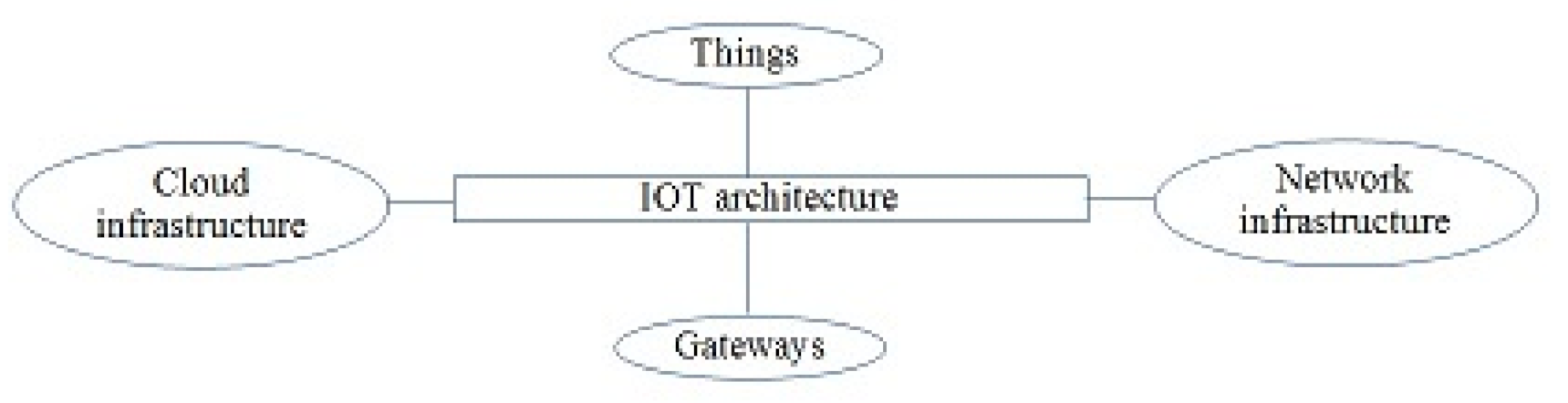
2.1. Internet of Things
2.2. Boolean Functions
2.3. NIST Statistical Test Suite
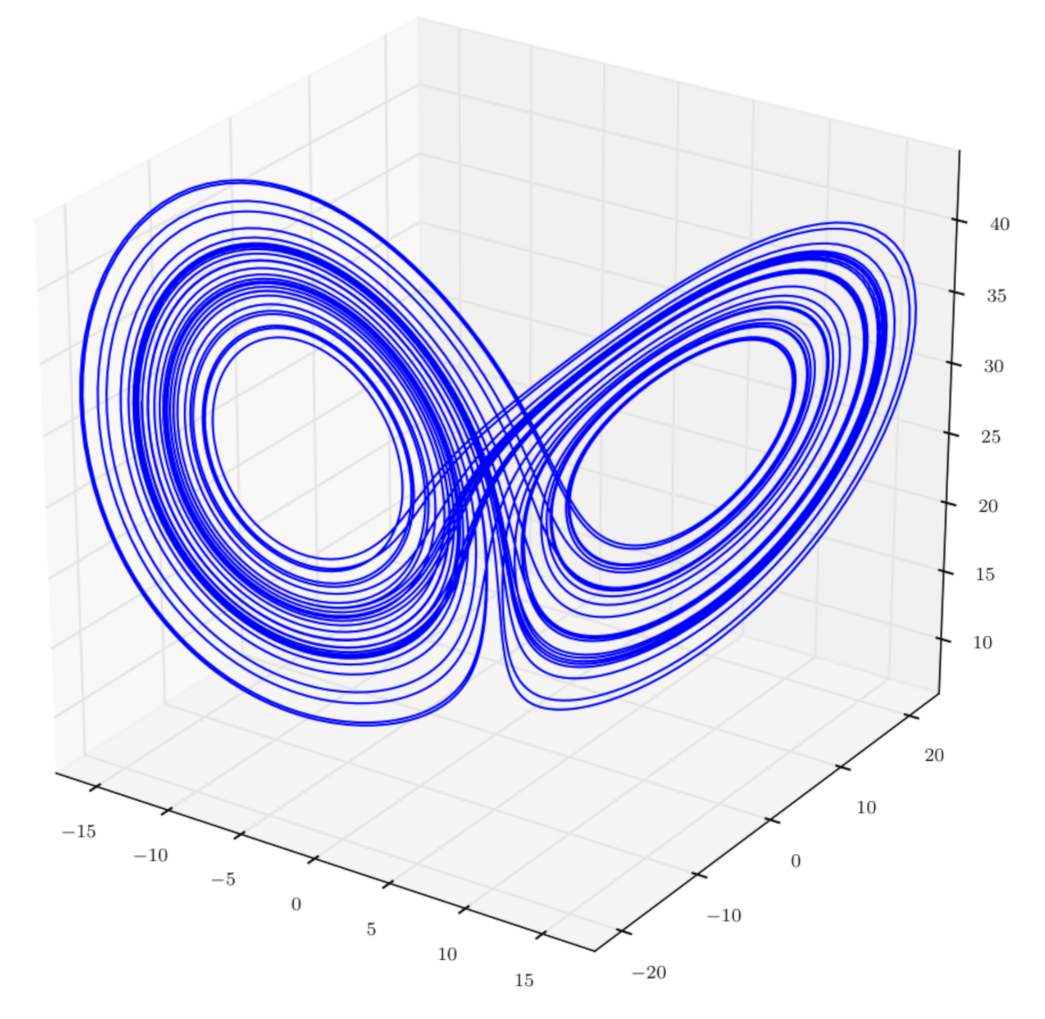
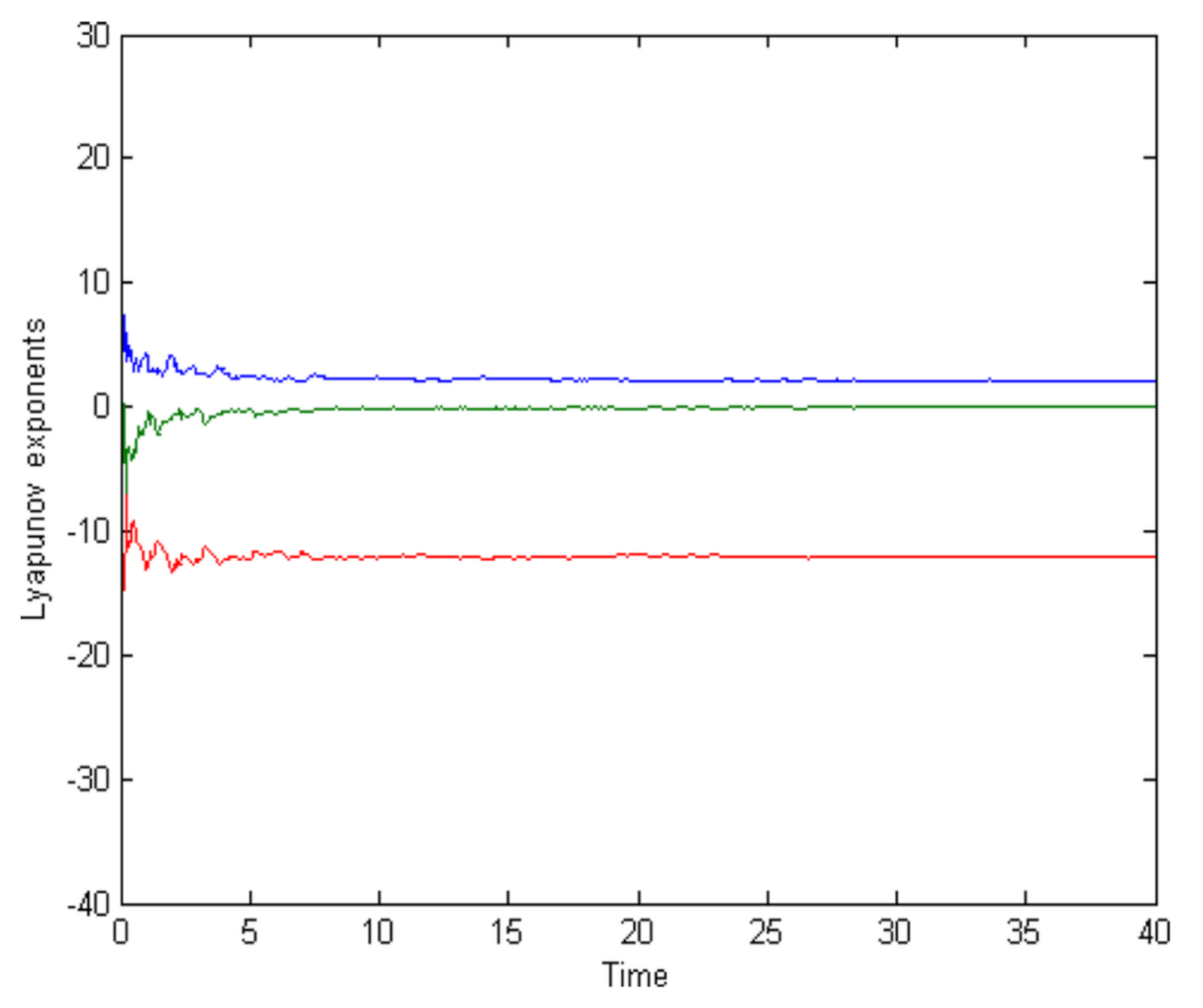
2.4. The Lorenz System
2.5. SHA-2
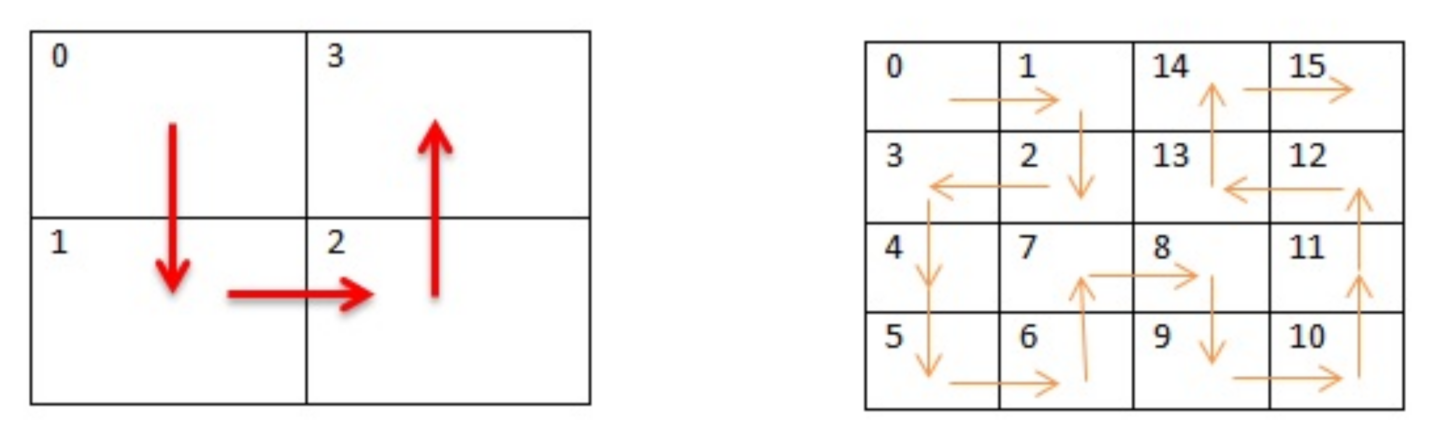
3. Scan Methodology
- → rightRot() → U →→ R → D → leftRot() →
- rightRot()
- → U → R → D → -
- rightRot()
- → R → U → L →
- leftRot()
- → L → D → R →
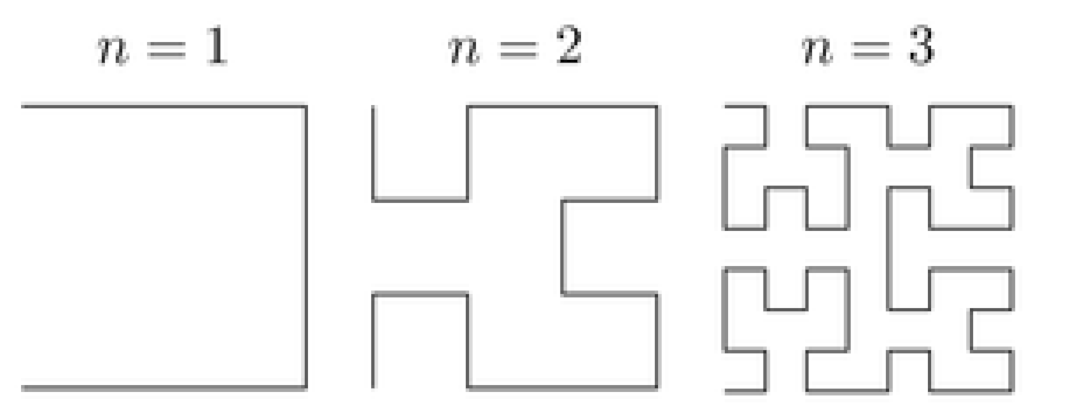
4. Hilbert Curve Scan Pattern
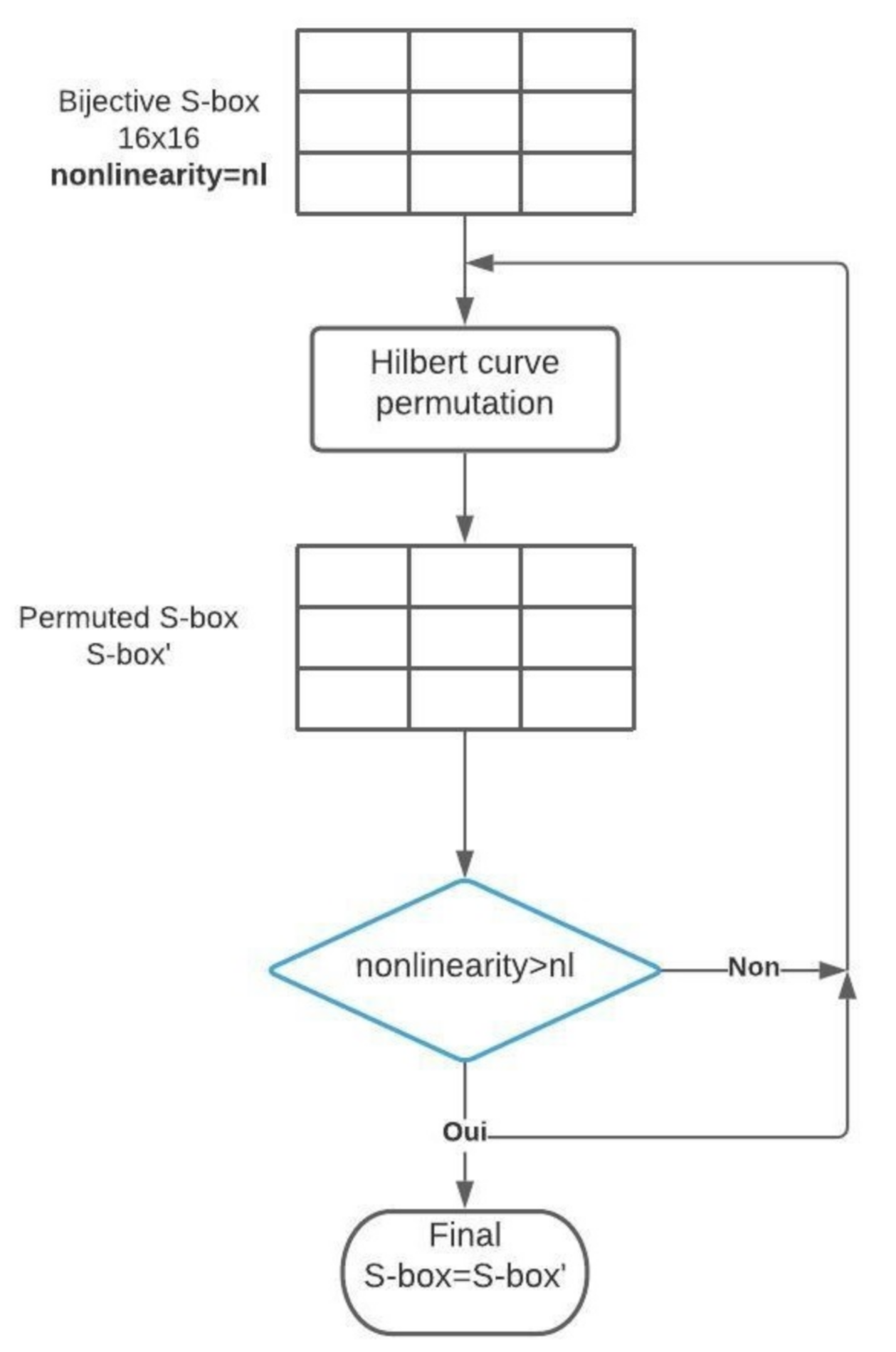
5. Modified AES S-Box Generation
5.1. The Main Idea
5.2. Generate the Chaotic Boolean Functions
- Generate a chaotic set S of 2048 bits.
- Define an empty binary set S.
- Iterate Equation (1) for 200 times to get rid of the transient effect by using .
- Get m Boolean functions by dividing the set S into 8 binary subsets of 256 bits.
- Create the initial S-box.
- Adjustment: Each element in the S-box must be unique. To guarantee this property, an adjustment of the S-box is needed.
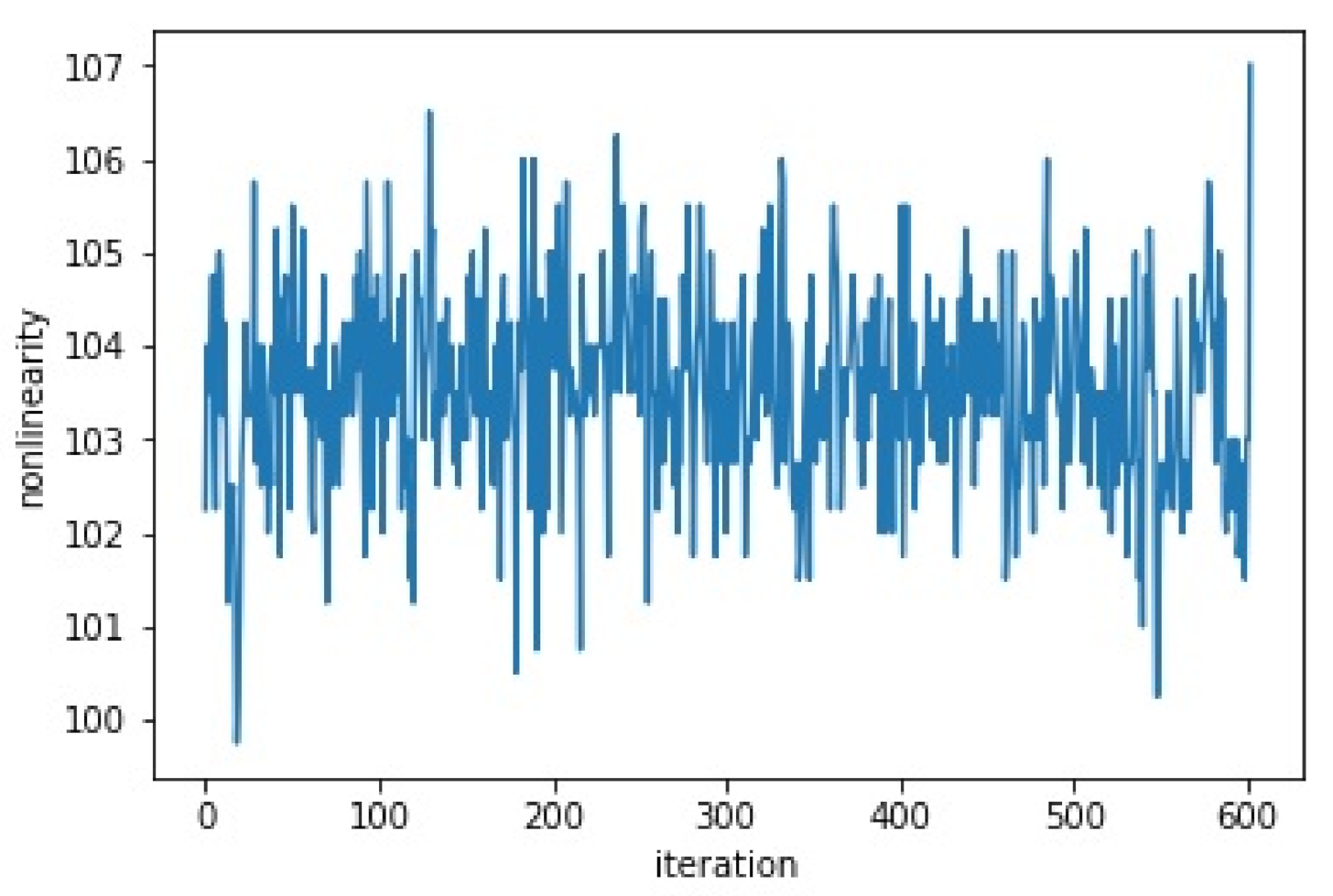
5.3. Generate a Cryptographically Strong S-box
5.4. Experimental Results and Cryptographic Properties of the Chaotic S-box
5.4.1. Bijectivity
5.4.2. Nonlinearity
5.4.3. Strict Avalanche Criterion: SAC
5.4.4. Bits Independence Criterion: BIC
5.4.5. Nist Statistical Test Suite
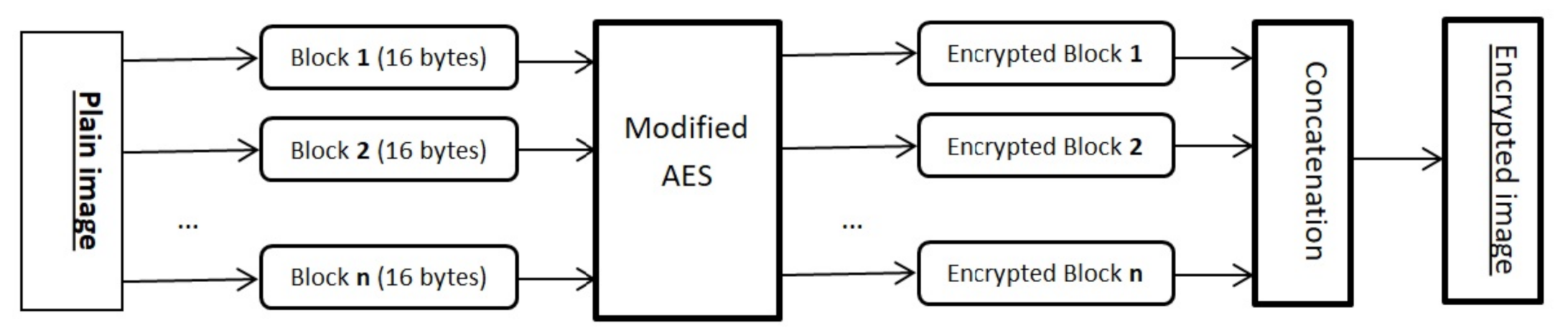
6. The Proposed Image Encryption Scheme
- store the TinyOS operating system,
- store the encryption algorithm,
- store the grayscale image to be encrypted and
- run the algorithm in order to generate the encrypted image.
7. Experimental Results
7.1. The Setup
7.2. Security Analysis and Experimental Results
7.2.1. Memory Consumption and Execution Times
7.2.2. Information Entropy
7.2.3. The Histogram Analysis
7.2.4. Correlation Coefficient Analysis
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Lee, J.; Kapitanova, K.; Son, S.H. The price of security in wireless sensor networks. Comput. Netw. 2010, 54, 2967–2978. [Google Scholar] [CrossRef]
- Fernandez-Anez, V. Stakeholders approach to smart cities: A survey on smart city definitions. In International Conference on Smart Cities; Springer: Berlin/Heidelberg, Germany, 2016; pp. 157–167. [Google Scholar]
- Martínez-Ballesté, A.; Pérez-Martínez, P.A.; Solanas, A. The pursuit of citizens’ privacy: A privacy-aware smart city is possible. IEEE Commun. Mag. 2013, 51, 136–141. [Google Scholar] [CrossRef]
- Abomhara, M.; Køien, G.M. Cyber security and the internet of things: Vulnerabilities, threats, intruders and attacks. J. Cyber Secur. Mobil. 2015, 4, 65–88. [Google Scholar] [CrossRef]
- McKay, K.; Bassham, L.; Sönmez Turan, M.; Mouha, N. Report on Lightweight Cryptography; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2016. [Google Scholar] [CrossRef]
- Bogdanov, A.; Knudsen, L.R.; Leander, G.; Paar, C.; Poschmann, A.; Robshaw, M.J.; Seurin, Y.; Vikkelsoe, C. PRESENT: An ultra-lightweight block cipher. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin/Heidelberg, Germany, 2007; pp. 450–466. [Google Scholar]
- Pieprzyk, J. Topics in Cryptology-CT-RSA 2010: The 10th Cryptographers’ Track at the RSA Conference 2010, San Francisco, CA, USA, March 1–5, 2010. Proceedings; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2010; Volume 5985. [Google Scholar]
- Blondeau, C.; Nyberg, K. Links between truncated differential and multidimensional linear properties of block ciphers and underlying attack complexities. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2014; pp. 165–182. [Google Scholar]
- Shirai, T.; Shibutani, K.; Akishita, T.; Moriai, S.; Iwata, T. The 128-bit blockcipher CLEFIA. In International Workshop on Fast Software Encryption; Springer: Berlin/Heidelberg, Germany, 2007; pp. 181–195. [Google Scholar]
- Tsunoo, Y.; Tsujihara, E.; Shigeri, M.; Saito, T.; Suzaki, T.; Kubo, H. Impossible differential cryptanalysis of CLEFIA. In International Workshop on Fast Software Encryption; Springer: Berlin/Heidelberg, Germany, 2008; pp. 398–411. [Google Scholar]
- Guo, J.; Peyrin, T.; Poschmann, A.; Robshaw, M. The LED block cipher. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin/Heidelberg, Germany, 2011; pp. 326–341. [Google Scholar]
- Dinur, I.; Dunkelman, O.; Keller, N.; Shamir, A. Key recovery attacks on 3-round Even-Mansour, 8-step LED-128, and full AES 2. In International Conference on the Theory and Application of Cryptology and Information Security; Springer: Berlin/Heidelberg, Germany, 2013; pp. 337–356. [Google Scholar]
- Shibutani, K.; Isobe, T.; Hiwatari, H.; Mitsuda, A.; Akishita, T.; Shirai, T. Piccolo: An ultra-lightweight blockcipher. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin/Heidelberg, Germany, 2011; pp. 342–357. [Google Scholar]
- Minier, M. On the security of Piccolo lightweight block cipher against related-key impossible differentials. In International Conference on Cryptology in India; Springer: Berlin/Heidelberg, Germany, 2013; pp. 308–318. [Google Scholar]
- Borghoff, J.; Canteaut, A.; Güneysu, T.; Kavun, E.B.; Knezevic, M.; Knudsen, L.R.; Leander, G.; Nikov, V.; Paar, C.; Rechberger, C.; et al. PRINCE–a low-latency block cipher for pervasive computing applications. In International Conference on the Theory and Application of Cryptology and Information Security; Springer: Berlin/Heidelberg, Germany, 2012; pp. 208–225. [Google Scholar]
- Banik, S.; Bogdanov, A.; Isobe, T.; Shibutani, K.; Hiwatari, H.; Akishita, T.; Regazzoni, F. Midori: A block cipher for low energy. In International Conference on the Theory and Application of Cryptology and Information Security; Springer: Berlin/Heidelberg, Germany, 2015; pp. 411–436. [Google Scholar]
- Guo, J.; Jean, J.; Nikolic, I.; Qiao, K.; Sasaki, Y.; Sim, S.M. Invariant Subspace Attack Against Full Midori64. IACR Cryptol. EPrint Arch. 2015, 2015, 1189. [Google Scholar]
- Lin, L.; Wu, W. Meet-in-the-middle attacks on reduced-round Midori64. IACR Trans. Symmetric Cryptol. 2017, 215–239. [Google Scholar] [CrossRef]
- Kim, S.; Verbauwhede, I. AES Implementation on 8-bit Microcontroller; Department of Electrical Engineering, University of California: Los Angeles, CA, USA, 2002. [Google Scholar]
- Law, Y.W.; Doumen, J.; Hartel, P. Survey and benchmark of block ciphers for wireless sensor networks. ACM Trans. Sens. Netw. (TOSN) 2006, 2, 65–93. [Google Scholar] [CrossRef]
- Vitaletti, A.; Palombizio, G. Rijndael for sensor networks: Is speed the main issue? Electron. Notes Theor. Comput. Sci. 2007, 171, 71–81. [Google Scholar] [CrossRef]
- Duh, D.R.; Lin, T.C.; Tung, C.H.; Chan, S.J. An implementation of AES algorithm with the multiple spaces random key pre-distribution scheme on MOTE-KIT 5040. In Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing (SUTC’06), Taichung, Taiwan, 5–7 June 2006; Volume 2, pp. 64–71. [Google Scholar]
- Khambre, P.; Sambhare, S.; Chavan, P. Secure data in wireless sensor network via AES (Advanced encryption standard). IJCSIT 2012, 3, 3588–3592. [Google Scholar]
- Hussain, I.; Shah, T.; Gondal, M.A. Image encryption algorithm based on PGL (2, GF (2 8)) S-boxes and TD-ERCS chaotic sequence. Nonlinear Dyn. 2012, 70, 181–187. [Google Scholar] [CrossRef]
- Wang, X.; Teng, L. An image blocks encryption algorithm based on spatiotemporal chaos. Nonlinear Dyn. 2012, 67, 365–371. [Google Scholar] [CrossRef]
- Ye, G.; Wong, K.W. An image encryption scheme based on time-delay and hyperchaotic system. Nonlinear Dyn. 2013, 71, 259–267. [Google Scholar] [CrossRef]
- Zhang, X.; Zhao, Z. Chaos-based image encryption with total shuffling and bidirectional diffusion. Nonlinear Dyn. 2014, 75, 319–330. [Google Scholar] [CrossRef]
- Wang, X.; Wang, Q. A novel image encryption algorithm based on dynamic S-boxes constructed by chaos. Nonlinear Dyn. 2014, 75, 567–576. [Google Scholar] [CrossRef]
- Lambić, D. A new discrete-space chaotic map based on the multiplication of integer numbers and its application in S-box design. Nonlinear Dyn. 2020, 100, 699–711. [Google Scholar] [CrossRef]
- Farah, M.B.; Farah, A.; Farah, T. An image encryption scheme based on a new hybrid chaotic map and optimized substitution box. Nonlinear Dyn. 2019, 99, 3041–3064. [Google Scholar] [CrossRef]
- Ye, T.; Zhimao, L. Chaotic S-box: Six-dimensional fractional Lorenz–Duffing chaotic system and O-shaped path scrambling. Nonlinear Dyn. 2018, 94, 2115–2126. [Google Scholar] [CrossRef]
- Aboytes-González, J.; Murguía, J.; Mejía-Carlos, M.; González-Aguilar, H.; Ramírez-Torres, M. Design of a strong S-box based on a matrix approach. Nonlinear Dyn. 2018, 94, 2003–2012. [Google Scholar] [CrossRef]
- Crossbow, T. Telosb Data Sheet. 2010. Available online: https://scholar.google.com.hk/scholar?hl=zh-CN&as_sdt=0%2C5&q=Crossbow%2C+T.+Telosb+data+sheet%2C+2010.&btnG= (accessed on 12 January 2021).
- IEEE Computer Society LAN/MAN Standards Committee. IEEE Standard for Information Technology Telecommunications and Information Exchange between Systems Local and Metropolitan Area Networks Specific Requirements. Part 15.4: Wireless Medium Access Control (MAC) and Physical Layer (PHY) Specifications for Low-Rate Wireless Personal Area Networks (LR-WPANs). 2006. Available online: https://ci.nii.ac.jp/naid/10030068811/ (accessed on 12 January 2021).
- Garcia-Morchon, O.; Kumar, S.; Keoh, S.; Hummen, R.; Struik, R. Security Considerations in the IP-based Internet of Things draft-garciacore-security-06. Internet Eng. Task Force 2013. Available online: https://tools.ietf.org/html/draft-garcia-core-security-06 (accessed on 12 January 2021).
- Evans, D. The internet of things: How the next evolution of the internet is changing everything. CISCO White Pap. 2011, 1, 1–11. [Google Scholar]
- Clearfield, C. Why the FTC Can’t Regulate the Internet Of Things. Forbes Magazine, 18 September 2013. Available online: http://www.forbes.com/sites/chrisclearfield/2013/09/18/whythe-ftc-cant-regulate-the-internet-of-things/ (accessed on 12 January 2021).
- Banafa, A. IoT and Blockchain Convergence: Benefits and Challenges. IEEE Internet Things Newsl. 2017. Available online: https://iot.ieee.org/newsletter/january-2017/iot-and-blockchain-convergence-benefits-and-challenges.html (accessed on 12 January 2021).
- Jamal, S.S.; Anees, A.; Ahmad, M.; Khan, M.F.; Hussain, I. Construction of cryptographic S-Boxes based on mobius transformation and chaotic tent-sine system. IEEE Access 2019, 7, 173273–173285. [Google Scholar] [CrossRef]
- Wang, Q.; Nie, C.; Xu, Y. Constructing Boolean Functions Using Blended Representations. IEEE Access 2019, 7, 107025–107031. [Google Scholar] [CrossRef]
- Bassham, L.; Rukhin, A.; Soto, J.; Nechvatal, J.; Smid, M.; Barker, E.; Leigh, S.; Levenson, M.; Vangel, M.; Banks, D.; et al. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2010. [Google Scholar] [CrossRef]
- Zhang, G.; Ding, W.; Li, L. Image encryption algorithm based on tent delay-sine cascade with logistic map. Symmetry 2020, 12, 355. [Google Scholar] [CrossRef]
- Guesmi, R.; Farah, M.A.B.; Kachouri, A.; Samet, M. A novel chaos-based image encryption using DNA sequence operation and Secure Hash Algorithm SHA-2. Nonlinear Dyn. 2016, 83, 1123–1136. [Google Scholar] [CrossRef]
- Guesmi, R.; Farah, M.A.B.; Kachouri, A.; Samet, M. Hash key-based image encryption using crossover operator and chaos. Multimed. Tools Appl. 2016, 75, 4753–4769. [Google Scholar] [CrossRef]
- Li, T.; Du, B.; Liang, X. Image Encryption Algorithm Based on Logistic and Two-Dimensional Lorenz. IEEE Access 2020, 8, 13792–13805. [Google Scholar] [CrossRef]
- Hamza, R.; Muhammad, K.; Arunkumar, N.; Ramírez-González, G. Hash based encryption for keyframes of diagnostic hysteroscopy. IEEE Access 2017, 6, 60160–60170. [Google Scholar] [CrossRef]
- Zhou, S.; He, P.; Kasabov, N. A Dynamic DNA Color Image Encryption Method Based on SHA-512. Entropy 2020, 22, 1091. [Google Scholar] [CrossRef]
- Peano, G. Sur une courbe, qui remplit toute une aire plane. Math. Ann. 1890, 36, 157–160. [Google Scholar] [CrossRef]
- Hilbert, D. Über die stetige Abbildung einer Linie auf ein Flächenstück. In Dritter Band: Analysis· Grundlagen der Mathematik· Physik Verschiedenes; Springer: Berlin/Heidelberg, Germany, 1935; pp. 1–2. [Google Scholar]
- Maniccam, S.S.; Bourbakis, N.G. Image and video encryption using SCAN patterns. Pattern Recognit. 2004, 37, 725–737. [Google Scholar] [CrossRef]
- Suresh, V.; Madhavan, V.C. Image encryption with space-filling curves. Def. Sci. J. 2012, 62, 46–50. [Google Scholar] [CrossRef]
- Sivakumar, T.; Venkatesan, R. Image encryption based on pixel shuffling and random key stream. Int. J. Comput. Inf. Technol. 2014, 3, 1468–1476. [Google Scholar]
- Shahna, K.; Mohamed, A. A novel image encryption scheme using both pixel level and bit level permutation with chaotic map. Appl. Soft Comput. 2020, 90, 106162. [Google Scholar]
- Lambić, D. A novel method of S-box design based on chaotic map and composition method. Chaos Solitons Fractals 2014, 58, 16–21. [Google Scholar] [CrossRef]
- Guesmi, R.; Farah, M.A.B.; Kachouri, A.; Samet, M. Chaos-based designing of a highly nonlinear S-box using Boolean functions. In Proceedings of the 2015 IEEE 12th International Multi-Conference on Systems, Signals & Devices (SSD15), Mahdia, Tunisia, 16–19 March 2015; pp. 1–5. [Google Scholar]
- Guesmi, R.; Farah, M.A.B.; Kachouri, A.; Samet, M. A novel design of Chaos based S-Boxes using genetic algorithm techniques. In Proceedings of the 2014 IEEE/ACS 11th International Conference on Computer Systems and Applications (AICCSA), Doha, Qatar, 10–13 November 2014; IEEE Computer Society: Piscataway Township, NJ, USA, 2014; pp. 678–684. [Google Scholar]
- Lambić, D. A novel method of S-box design based on discrete chaotic map. Nonlinear Dyn. 2017, 87, 2407–2413. [Google Scholar] [CrossRef]
- Lambić, D. S-box design method based on improved one-dimensional discrete chaotic map. J. Inf. Telecommun. 2018, 2, 181–191. [Google Scholar] [CrossRef]
- Çavuşoğlu, Ü.; Zengin, A.; Pehlivan, I.; Kaçar, S. A novel approach for strong S-Box generation algorithm design based on chaotic scaled Zhongtang system. Nonlinear Dyn. 2017, 87, 1081–1094. [Google Scholar] [CrossRef]
- Tang, G.; Liao, X.; Chen, Y. A novel method for designing S-boxes based on chaotic maps. Chaos Solitons Fractals 2005, 23, 413–419. [Google Scholar] [CrossRef]
- Asim, M.; Jeoti, V. Efficient and Simple Method for Designing Chaotic S-Boxes. ETRI J. 2008, 30, 170–172. [Google Scholar] [CrossRef]
- Özkaynak, F.; Özer, A.B. A method for designing strong S-Boxes based on chaotic Lorenz system. Phys. Lett. A 2010, 374, 3733–3738. [Google Scholar] [CrossRef]
- Jakimoski, G.; Kocarev, L. Chaos and cryptography: Block encryption ciphers based on chaotic maps. IEEE Trans. Circuits Syst. I Fundam. Theory Appl. 2001, 48, 163–169. [Google Scholar] [CrossRef]
- Zhang, F.; Dojen, R.; Coffey, T. Comparative performance and energy consumption analysis of different AES implementations on a wireless sensor network node. Int. J. Sens. Netw. 2011, 10, 192–201. [Google Scholar] [CrossRef]
- Levis, P.; Madden, S.; Polastre, J.; Szewczyk, R.; Whitehouse, K.; Woo, A.; Gay, D.; Hill, J.; Welsh, M.; Brewer, E.; et al. TinyOS: An operating system for sensor networks. In Ambient intelligence; Springer: Berlin/Heidelberg, Germany, 2005; pp. 115–148. [Google Scholar]
- Yasser, I.; Mohamed, M.A.; Samra, A.S.; Khalifa, F. A Chaotic-Based Encryption/Decryption Framework for Secure Multimedia Communications. Entropy 2020, 22, 1253. [Google Scholar] [CrossRef]
- Zhu, S.; Zhu, C. Secure Image Encryption Algorithm Based on Hyperchaos and Dynamic DNA Coding. Entropy 2020, 22, 772. [Google Scholar] [CrossRef] [PubMed]
- Li, Z.; Peng, C.; Tan, W.; Li, L. A Novel Chaos-Based Color Image Encryption Scheme Using Bit-Level Permutation. Symmetry 2020, 12, 1497. [Google Scholar] [CrossRef]
- Wang, B.; Xie, Y.; Zhou, S.; Zheng, X.; Zhou, C. Correcting errors in image encryption based on DNA coding. Molecules 2018, 23, 1878. [Google Scholar] [CrossRef]
- Yasser, I.; Khalifa, F.; Mohamed, M.A.; Samrah, A.S. A new image encryption scheme based on hybrid chaotic maps. Complexity 2020, 2020, 9597619. [Google Scholar] [CrossRef]

| 49 | 170 | 30 | 184 | 28 | 232 | 128 | 51 | 80 | 99 | 130 | 154 | 0 | 191 | 94 | 233 |
| 223 | 106 | 255 | 120 | 7 | 162 | 254 | 68 | 81 | 16 | 131 | 72 | 123 | 192 | 204 | 234 |
| 27 | 66 | 227 | 10 | 216 | 41 | 196 | 89 | 116 | 102 | 133 | 75 | 164 | 197 | 206 | 235 |
| 18 | 5 | 190 | 12 | 19 | 150 | 43 | 45 | 60 | 246 | 173 | 119 | 113 | 112 | 225 | 238 |
| 211 | 193 | 24 | 253 | 181 | 46 | 229 | 146 | 127 | 108 | 134 | 23 | 176 | 198 | 74 | 239 |
| 185 | 100 | 8 | 105 | 212 | 17 | 58 | 15 | 243 | 111 | 97 | 156 | 250 | 110 | 207 | 33 |
| 35 | 132 | 169 | 1 | 63 | 83 | 136 | 54 | 165 | 114 | 138 | 85 | 167 | 199 | 209 | 25 |
| 70 | 221 | 21 | 44 | 59 | 163 | 142 | 36 | 82 | 115 | 139 | 157 | 178 | 200 | 168 | 240 |
| 2 | 61 | 26 | 140 | 194 | 47 | 137 | 152 | 84 | 64 | 143 | 158 | 174 | 62 | 215 | 241 |
| 188 | 87 | 96 | 210 | 29 | 208 | 69 | 76 | 86 | 141 | 145 | 236 | 175 | 201 | 14 | 242 |
| 159 | 101 | 166 | 155 | 109 | 48 | 144 | 73 | 90 | 248 | 147 | 220 | 179 | 226 | 171 | 245 |
| 224 | 22 | 92 | 13 | 237 | 53 | 42 | 122 | 91 | 117 | 149 | 31 | 182 | 203 | 218 | 129 |
| 20 | 6 | 93 | 230 | 189 | 57 | 65 | 180 | 98 | 247 | 153 | 148 | 214 | 9 | 219 | 249 |
| 4 | 55 | 11 | 222 | 37 | 244 | 205 | 77 | 104 | 121 | 88 | 217 | 183 | 202 | 3 | 251 |
| 39 | 52 | 50 | 118 | 34 | 213 | 32 | 78 | 151 | 125 | 135 | 160 | 186 | 95 | 228 | 252 |
| 195 | 172 | 71 | 103 | 38 | 126 | 67 | 79 | 177 | 124 | 107 | 161 | 187 | 40 | 231 | 56 |
| 31 | DF | 77 | 67 | 9D | D8 | B6 | 11 | 94 | 32 | E2 | E0 | 16 | AB | 6D | F5 |
| 33 | A0 | 02 | 01 | 7C | E3 | 84 | DD | FE | 69 | 71 | 44 | 52 | 6A | 5A | 3E |
| 58 | E9 | 97 | BE | 1F | C1 | FA | 13 | 8C | A7 | 34 | A1 | 48 | 7D | F4 | 4B |
| 10 | 39 | E5 | C2 | D0 | F8 | 8B | 43 | D6 | F0 | AA | B9 | 4E | 57 | E6 | 1C |
| D3 | 0B | 03 | 81 | 5F | D4 | 68 | 23 | 5E | 61 | FD | CD | DA | 29 | 9F | EA |
| B8 | 41 | B2 | EB | 14 | 8F | 51 | 26 | 8A | 27 | 00 | C3 | 5B | 5D | 5C | 3D |
| 73 | 15 | 4A | 85 | C5 | B3 | A2 | 22 | 8E | 6C | 17 | A4 | C6 | A8 | 86 | A3 |
| 50 | 80 | 70 | AF | 87 | 6B | B1 | 18 | 07 | 30 | 62 | 08 | 6E | 1A | 45 | 55 |
| 1E | 47 | 35 | 3C | EC | 3B | 98 | 99 | B5 | 56 | F7 | 66 | 2F | 1D | 72 | 64 |
| 3A | 65 | 78 | 91 | EE | 63 | 88 | 19 | 92 | E1 | 28 | 6F | A6 | FF | A5 | 7A |
| 0C | C0 | 0D | F9 | 9E | 3F | 49 | B0 | F2 | AD | 74 | 95 | 83 | 93 | 89 | 0A |
| 04 | BC | C7 | 96 | BB | BA | 25 | 54 | 46 | CE | C9 | CB | 4D | B4 | BF | 42 |
| 2D | C8 | 36 | A9 | 0E | 53 | DB | CC | EF | 2C | 75 | F3 | 2B | 2A | D1 | C4 |
| 37 | D5 | 0F | DC | CA | D2 | 60 | 4C | FC | 59 | 2E | 24 | AC | E8 | 38 | B7 |
| 05 | 9A | FB | 12 | 90 | 82 | CF | 20 | 06 | DE | 9C | F1 | 79 | 7E | 76 | E7 |
| E4 | 40 | 1B | 4F | BD | 7B | D7 | D9 | AE | 21 | 9B | ED | F6 | 7F | 09 | 8D |
| 49 | 51 | 88 | 16 | 211 | 184 | 115 | 80 | 30 | 58 | 12 | 4 | 45 | 55 | 5 | 228 |
| 223 | 160 | 233 | 57 | 11 | 65 | 21 | 128 | 71 | 101 | 192 | 188 | 200 | 213 | 154 | 64 |
| 119 | 2 | 151 | 229 | 3 | 178 | 74 | 112 | 53 | 120 | 13 | 199 | 54 | 15 | 251 | 27 |
| 103 | 1 | 190 | 194 | 129 | 235 | 133 | 175 | 60 | 145 | 249 | 150 | 169 | 220 | 18 | 79 |
| 157 | 124 | 31 | 208 | 95 | 20 | 197 | 135 | 236 | 238 | 158 | 187 | 14 | 202 | 144 | 189 |
| 216 | 227 | 193 | 248 | 212 | 143 | 179 | 107 | 59 | 99 | 63 | 186 | 83 | 210 | 130 | 123 |
| 182 | 132 | 250 | 139 | 104 | 81 | 162 | 177 | 152 | 136 | 73 | 37 | 219 | 96 | 207 | 215 |
| 17 | 221 | 19 | 67 | 35 | 38 | 34 | 24 | 153 | 25 | 176 | 84 | 204 | 76 | 32 | 217 |
| 148 | 254 | 140 | 214 | 94 | 138 | 142 | 7 | 181 | 146 | 242 | 70 | 239 | 252 | 6 | 174 |
| 50 | 105 | 167 | 240 | 97 | 39 | 108 | 48 | 86 | 225 | 173 | 206 | 44 | 89 | 222 | 33 |
| 226 | 113 | 52 | 170 | 253 | 0 | 23 | 98 | 247 | 40 | 116 | 201 | 117 | 46 | 156 | 155 |
| 224 | 68 | 161 | 185 | 205 | 195 | 164 | 8 | 102 | 111 | 149 | 203 | 243 | 36 | 241 | 237 |
| 22 | 82 | 72 | 78 | 218 | 91 | 198 | 110 | 47 | 166 | 131 | 77 | 43 | 172 | 121 | 246 |
| 171 | 106 | 125 | 87 | 41 | 93 | 168 | 26 | 29 | 255 | 147 | 180 | 42 | 232 | 126 | 127 |
| 109 | 90 | 244 | 230 | 159 | 92 | 134 | 69 | 114 | 165 | 137 | 191 | 209 | 56 | 118 | 9 |
| 245 | 62 | 75 | 28 | 234 | 61 | 163 | 85 | 100 | 122 | 10 | 66 | 196 | 183 | 231 | 141 |
| S-Box | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | Avg. Nonlinearity | Avg. SAC |
|---|---|---|---|---|---|---|---|---|---|---|
| 108 | 108 | 106 | 108 | 106 | 106 | 108 | 106 | 107 | 0.4932 |
| S-Box | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | Nonlinearity |
|---|---|---|---|---|---|---|---|---|---|
| AES S-box | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112 |
| APA S-box | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112 |
| Gray S-box | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112 |
| [54] | 110 | 108 | 108 | 110 | 108 | 108 | 110 | 112 | 109.25 |
| [28] | 108 | 108 | 108 | 108 | 108 | 108 | 108 | 108 | 108 |
| [55] | 108 | 110 | 110 | 108 | 106 | 106 | 106 | 110 | 108 |
| [56] | 106 | 108 | 110 | 106 | 110 | 106 | 106 | 108 | 107.5 |
| Our S-box | 108 | 108 | 106 | 108 | 106 | 106 | 108 | 106 | 107 |
| [57] | 108 | 106 | 106 | 106 | 106 | 106 | 108 | 108 | 106.5 |
| [29] | 108 | 108 | 106 | 106 | 106 | 106 | 106 | 106 | 106.5 |
| [58] | 106 | 108 | 108 | 106 | 106 | 106 | 106 | 106 | 106.5 |
| [59] | 108 | 106 | 104 | 108 | 106 | 110 | 104 | 104 | 106 |
| Skipjack | 104 | 104 | 108 | 108 | 108 | 104 | 104 | 106 | 105.75 |
| Xyi S-box | 106 | 104 | 104 | 106 | 104 | 106 | 104 | 106 | 105 |
| [60] | 103 | 109 | 104 | 105 | 105 | 106 | 104 | 103 | 104.88 |
| [61] | 107 | 103 | 100 | 102 | 96 | 108 | 104 | 108 | 103.5 |
| [62] | 104 | 100 | 106 | 102 | 104 | 102 | 104 | 104 | 103.25 |
| [63] | 104 | 106 | 104 | 108 | 98 | 100 | 100 | 106 | 103.25 |
| Residue Prime | 94 | 100 | 104 | 104 | 102 | 100 | 98 | 94 | 99.5 |
| 0.5000 | 0.4531 | 0.4375 | 0.50000 | 0.4609 | 0.5000 | 0.5234 | 0.5078 |
| 0.5000 | 0.5000 | 0.5000 | 0.50000 | 0.5000 | 0.5000 | 0.5000 | 0.5000 |
| 0.5000 | 0.5000 | 0.5000 | 0.50000 | 0.4609 | 0.4687 | 0.4765 | 0.5000 |
| 0.4375 | 0.5000 | 0.4375 | 0.50000 | 0.5000 | 0.5000 | 0.4765 | 0.5000 |
| 0.5000 | 0.5000 | 0.5625 | 0.50000 | 0.4609 | 0.5000 | 0.4765 | 0.4921 |
| 0.4375 | 0.5468 | 0.5625 | 0.50000 | 0.5000 | 0.4687 | 0.5234 | 0.4921 |
| 0.5625 | 0.5000 | 0.5000 | 0.50000 | 0.4609 | 0.5000 | 0.5000 | 0.5078 |
| 0.4375 | 0.4531 | 0.5000 | 0.50000 | 0.5000 | 0.5000 | 0.4765 | 0.5000 |
| S-Box | Minimum Value | Maximum Value | Average Value |
|---|---|---|---|
| AES S-box | 0.480 | 0.528 | 0.504 |
| APA S-box | 0.472 | 0.526 | 0.499 |
| Gray S-box | 0.478 | 0.526 | 0.502 |
| Our S-box | 0.4375 | 0.5625 | 0.4932 |
| [28] | 0.406 | 0.578 | 0.492 |
| Skipjack | 0.464 | 0.534 | 0.499 |
| Xyi S-box | 0.470 | 0.536 | 0.503 |
| [60] | 0.398 | 0.570 | 0.506 |
| [61] | 0.390 | 0.585 | - |
| [62] | 0.421 | 0.593 | - |
| [63] | 0.375 | 0.593 | - |
| Residue Prime S-box | 0.470 | - | 0.502 |
| - | 108 | 104 | 104 | 100 | 100 | 102 | 100 |
| 108 | - | 98 | 104 | 106 | 98 | 104 | 104 |
| 104 | 98 | - | 106 | 92 | 102 | 102 | 100 |
| 104 | 104 | 106 | - | 104 | 104 | 100 | 106 |
| 100 | 106 | 92 | 104 | - | 104 | 104 | 102 |
| 100 | 98 | 102 | 104 | 104 | - | 98 | 108 |
| 102 | 104 | 102 | 100 | 104 | 98 | - | 100 |
| 100 | 104 | 100 | 106 | 102 | 108 | 100 | - |
| Statistic Tests | p-Value for Cipher-Images |
|---|---|
| Frequency (Monobits) test | 0.99258 |
| Frequency test within a block | 0.543019 |
| Runs test | 0.859684 |
| Test for the longest run of ones in a block | 0.99889 |
| Binary matrix rank test | 0.481248 |
| Discrete Fourier transform (Spectral) test | 0.167931 |
| Non-overlapping template matching test | Success |
| Overlapping template matching test | 0.886589 |
| Maurer’s “universal statistical” test | 0.895623 |
| Linear complexity test | 0.919679 |
| Serial test (1) | 0.773031 |
| Serial test (2) | 0.079182 |
| Approximate entropy test | 0.0920 |
| Cumulative sums | 0.675322 |
| Random excursions test | Success |
| Random excursions variant test | Success |
| Results | Pass |
| Images | Plain Image | Ciphered Image |
|---|---|---|
| Lena | 7.8055 | 7.9401 |
| Baboon | 7.6015 | 7.9290 |
| Boat | 7.2189 | 7.9433 |
| Clock | 7.0087 | 7.9366 |
| Peppers | 7.7645 | 7.9351 |
| Jelly-Beans | 7.1872 | 7.9331 |
| Splash | 7.5045 | 7.9460 |
| Plain Images | Histograms | Ciphered Images | Histograms |
|---|---|---|---|
 |  |  |  |
 |  |  |  |
 |  |  |  |
 |  |  |  |
 |  |  |  |
 |  |  |  |
 |  |  |  |
| Diagonally | Horizontally | Vertically | ||||
|---|---|---|---|---|---|---|
| Plain | Ciphered | Plain | Ciphered | Plain | Ciphered | |
| Lena | 0.8290 | 0.0669 | 0.4454 | −0.0636 | 0.9445 | 0.0465 |
| Baboon | 0.8748 | −0.1941 | 0.8834 | −0.1099 | 0.1059 | 0.0487 |
| Boat | −0.1561 | 0,2022 | 0.3059 | 0.0149 | 0.1709 | 0.0430 |
| Clock | 0.7870 | −0.0919 | 0.887 | −0.1719 | 0.9437 | −0.0314 |
| Peppers | 0.6498 | −0.2289 | 0.9315 | 0.2409 | 0.6104 | 0.1633 |
| Jelly-Beans | 0.9180 | −0.1200 | 0.9589 | −0.1413 | 0.9726 | 0.0291 |
| Splash | 0.8892 | 0.1754 | 0.0108 | 0.0059 | 0.9460 | −0.0499 |
| Images | Horizontally | Vertically | Diagonally |
|---|---|---|---|
 |  |  |  |
 |  |  |  |
 |  |  |  |
 |  |  |  |
 |  |  |  |
 |  |  |  |
 |  |  |  |
 |  |  |  |
 |  |  |  |
 |  |  |  |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alshammari, B.M.; Guesmi, R.; Guesmi, T.; Alsaif, H.; Alzamil, A. Implementing a Symmetric Lightweight Cryptosystem in Highly Constrained IoT Devices by Using a Chaotic S-Box. Symmetry 2021, 13, 129. https://doi.org/10.3390/sym13010129
Alshammari BM, Guesmi R, Guesmi T, Alsaif H, Alzamil A. Implementing a Symmetric Lightweight Cryptosystem in Highly Constrained IoT Devices by Using a Chaotic S-Box. Symmetry. 2021; 13(1):129. https://doi.org/10.3390/sym13010129
Chicago/Turabian StyleAlshammari, Badr M., Ramzi Guesmi, Tawfik Guesmi, Haitham Alsaif, and Ahmed Alzamil. 2021. "Implementing a Symmetric Lightweight Cryptosystem in Highly Constrained IoT Devices by Using a Chaotic S-Box" Symmetry 13, no. 1: 129. https://doi.org/10.3390/sym13010129
APA StyleAlshammari, B. M., Guesmi, R., Guesmi, T., Alsaif, H., & Alzamil, A. (2021). Implementing a Symmetric Lightweight Cryptosystem in Highly Constrained IoT Devices by Using a Chaotic S-Box. Symmetry, 13(1), 129. https://doi.org/10.3390/sym13010129






