1. Introduction
The security of multimedia information communication has become the focus of attention due to the openness and sharing of network transmission, especially for digital images related to military, medical, and other fields that contain sensitive information. Therefore, developing a secure digital image encryption algorithm has become a vital research direction. However, for the inherent characteristics of digital images like the enormous data capacity, strong correlation among adjacent pixels, and high redundancy, the mainstream textual cryptography systems such as the Data Encryption Standard (DES), the Advanced Encryption Standard (AES), etc., are poorly suited to image encryption [
1].
Chaotic systems possessing several salient features like extreme sensitivity to initial conditions and control parameters, ergodicity, aperiodicity, and randomicity have been used to generate pseudo-random sequences that are very complex and difficult to analyze and predict. In 1977, Fridrich firstly used the pseudo-random sequences generated by chaotic systems in image cryptosystems [
2]. Subsequently, many chaos-based image encryption systems [
1,
3,
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15,
16,
17,
18] have been constantly developed by researchers. For example, in [
8], a new chaotic map was created based on a Beta function and used to develop a novel image encryption system with excellent resistance to various attacks. In 2019, Alawida et al. [
14] proposed a hybrid digital chaotic system-based image cryptosystem, which has higher complexity, higher sensitivity, and a larger key space compared to other chaotic-based methods proposed previously. Some algorithms have been proven to be insecure due to the following drawbacks: (1) smaller key space; (2) lower plaintext sensitivity; (3) the chaotic sequence generated by the low-dimensional chaotic map is more likely to degenerate into a short-period sequence because of the finite precision of the computer; (4) the same key streams are used in the scrambling and diffusion operation when encrypting different original images. For example, A. Jain et al. presented a robust image encryption scheme [
17] by using a one-dimensional logistic map and claimed that the cryptosystem could resist traditional attacks like statistical attack, exhaustive attack, and differential attack. In 2017, Dou et al. [
19] analyzed and broke the encryption process by the chosen plaintext attack. More recently, Wang et al. [
20] found an image encryption scheme using a 1D chaotic map [
18] to be insecure and to be able to be completely cracked by the chosen plaintext.
In the last few years, the properties of DNA computing like enormous parallelism, higher information density, and ultra-low power consumption have been discovered, and many image encryption algorithms [
10,
16,
17,
21,
22,
23,
24,
25,
26,
27,
28,
29,
30,
31,
32] have been designed by combining DNA computing and chaos. For example, in [
17], the DNA operation combined with chaotic systems was used to develop a robust image encryption system. Firstly, the pixels in the original image are encoded into the DNA sequence, and a mask is generated by a chaotic map. Secondly, the diffusion process is implemented through the DNA addition and the complementary operation between the mask and the DNA encoded image. Finally, the diffused image is permuted using chaotic sequences generated by 2D chaos and decoded to obtain the cipher image. However, for some image encryption algorithms [
10,
16,
17,
21], all pixels of the original image are encoded/decoded by fixed DNA encoding/decoding rules, which lead to less randomness of the encryption schemes. For example, in [
21], the original image was divided into four equal sub-images, which were encoded into DNA matrices according to a specific DNA encoding/decoding rule. The index of the employed DNA encoding/decoding rules, ranging from one to eight, is stationary and used for secret keys. However, it is insecure against exhaustive attack because it can be broken by a maximum of eight tests. Furthermore, including the algorithm in [
21], most DNA operation-based schemes suffer similar drawbacks in the pure chaos-based image encryption algorithms mentioned above, which may lead to the encryption system being vulnerable to chosen plaintext attacks. To overcome the security flaws, many plaintext-related mechanisms and random DNA encoding/decoding technology have been proposed and used in image encryption recently. In [
28], 2D-HSMwas used to control the DNA encoding/decoding rules randomly. Specifically, the parameter of
calculated from the pixel value of the original image was used to manage the encryption process. However, the image cryptosystems developed in [
28] have been broken with the chosen plaintext attack because of the insufficient plaintext association in 2019 [
33]. In [
22], the initial values and parameters of the chaotic system were calculated by the SHA 256 hash of the original image and modified by the plain image’s Hamming distance, leading to the high plaintext sensitivity of the encryption algorithm to resist the chosen plaintext attacks effectively. However, for algorithms like those in [
22,
31], due to encrypting different images with distinct keys, one must transfer the keys through a secret channel every time, which increases the implementation complexity and limits the application of this algorithm to real-time encryption.
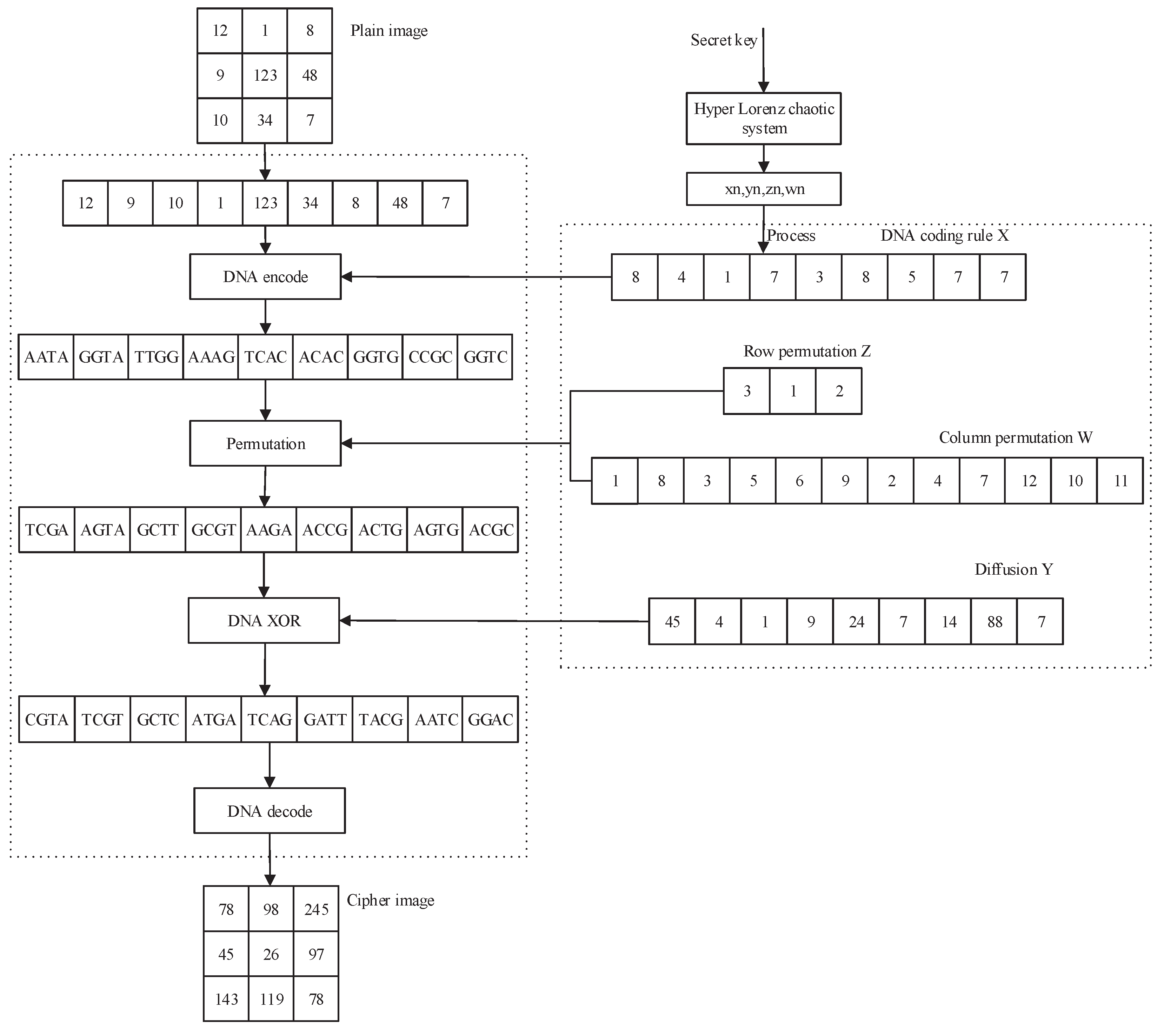
The discussions above show that existing algorithms have one or more of the following defects: (1) the potential insecurity of low-dimensional chaotic systems; (2) the shortcomings of fixed DNA coding rules; (3) the security flaws of low sensitivity to the plain images; (4) the implementation complexity of the one-time-pad mechanism. To overcome these flaws, we propose a novel plaintext-related mechanism based on the peculiarity of plaintext DNA coding (PPDC), which is used to control the encryption process. The value of PPDC is determined by all pixel values of the original image and the chaotic sequence generated by a four-wing hyper-chaotic system, which can significantly increase plaintext sensitivity to strengthen the ability to resist powerful chosen plaintext attacks.
The paper is organized as follows: In
Section 2, the related technologies are introduced.
Section 3 provides the detailed encryption process. The simulation and security analysis results are described in
Section 4.
Section 5 gives a brief conclusion.
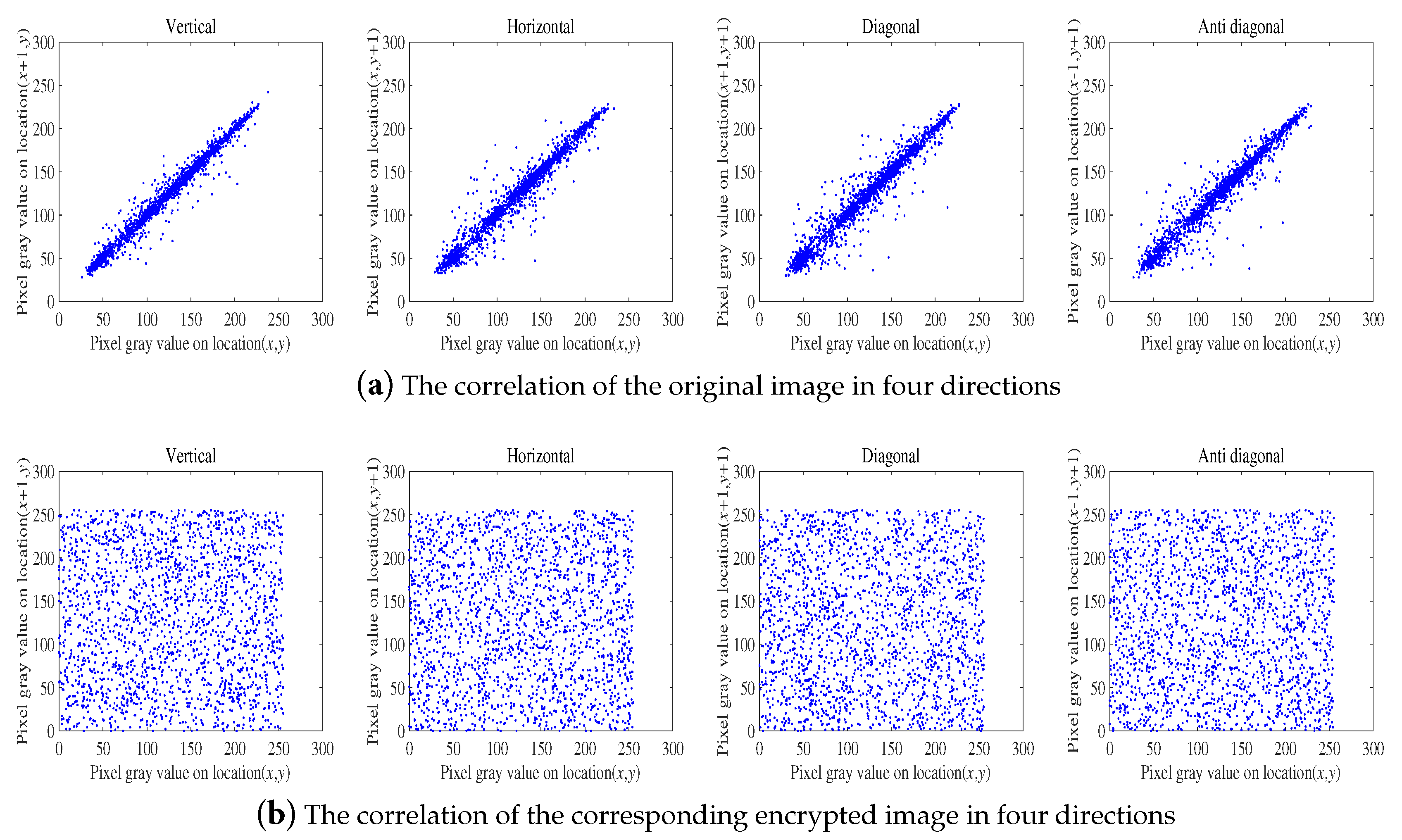
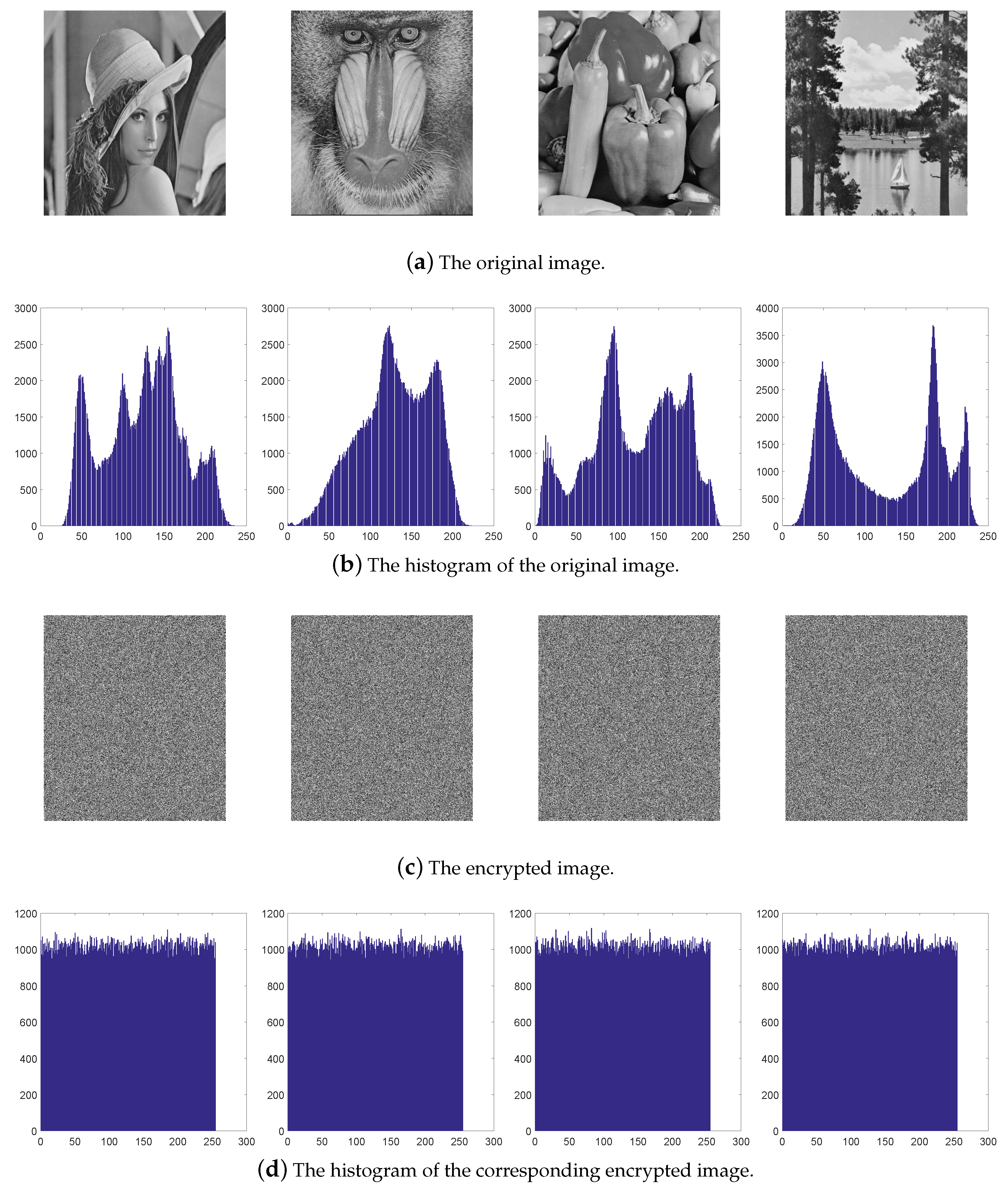
5. Conclusions
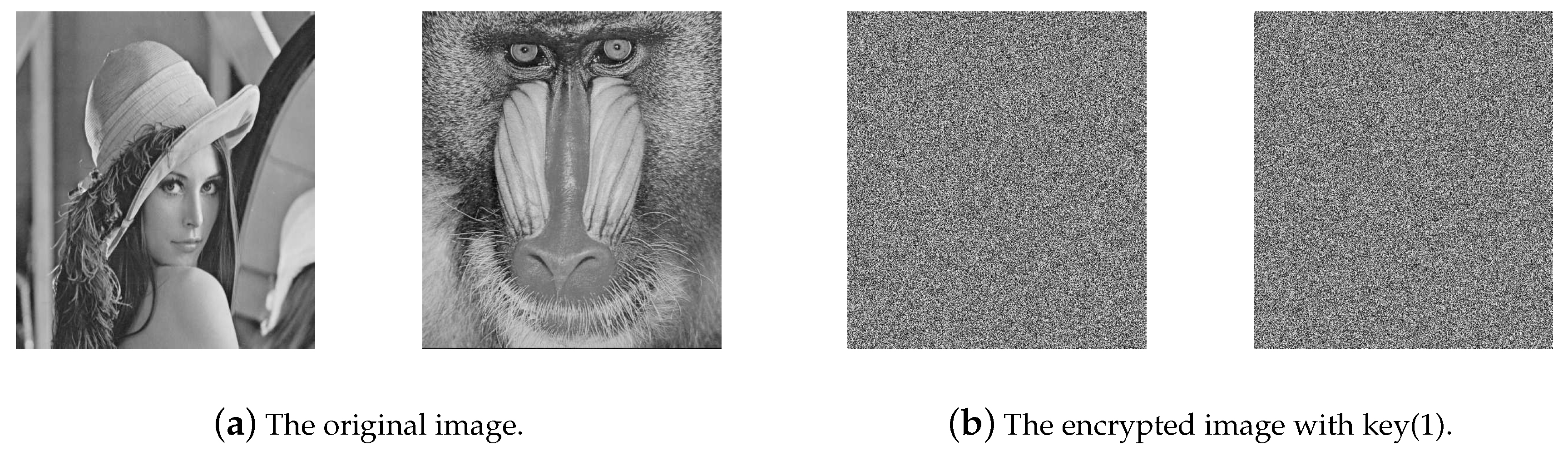
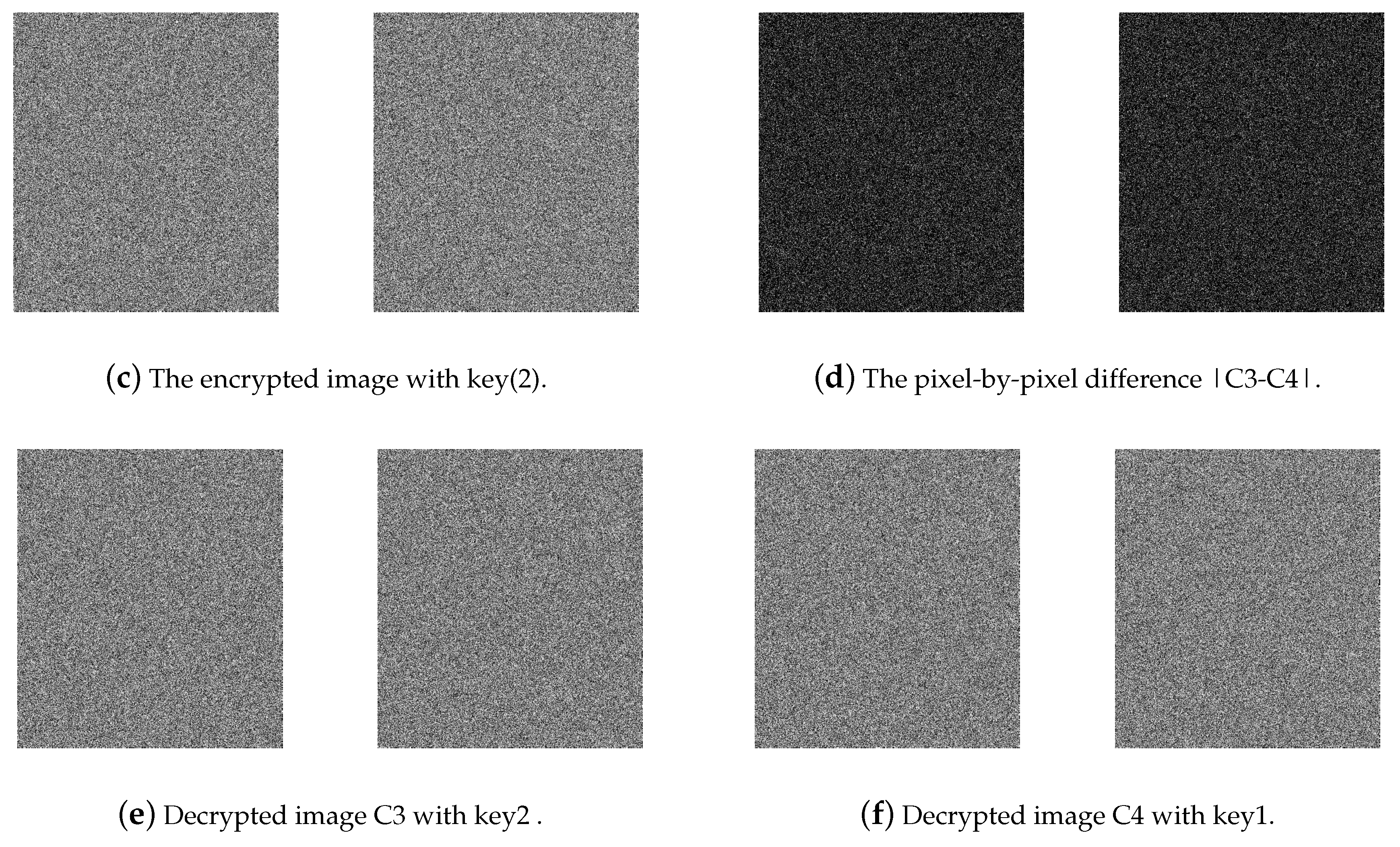
In this paper, a novel plaintext-related mechanism based on the peculiarity of plaintext DNA coding (PPDC) is proposed. The original image is firstly encoded to obtain the DNA encoding and the value of PPDC. Then, PPDC is used to process the chaotic sequences to obtain the key streams used in the permutation stage. Such key stream generation method is different from the one used in the previous DNA-based chaotic image encryption algorithms. Because the key streams are related to both the random sequences generated by the Lorenz hyper-chaotic system and plaintext image, our scheme can realize higher key sensitivity and plaintext sensitivity to resist chosen plaintext attacks or differential attacks effectively. Furthermore, the DNA level permutation operation not only disorganizes the position of the plain image pixels, but also changes the value of the pixel, which improve the efficiency and security. Especially, the encryption algorithm only needs to carry out one round of the permutation-diffusion operation to get a better ability of resisting various attacks. Secret key space analysis, histogram analysis, correlation analysis, sensitivity analysis, and information entropy analysis are given. The analysis results prove that the proposed algorithm is secure to resist all kinds of attacks, including the powerful chosen plaintext attack.