1. Introduction
With the rapid growth of digital communication and data exchange, there is hence an urgent need for the protection of data that is sensitive and confidential. The cryptographic encryption algorithms can be categorized as symmetric encryption algorithms and asymmetric encryption algorithms. The most well-known symmetric encryption algorithms are the Advanced Encryption Standard (AES) and Data Encryption Standard (DES) [
1]. The DES was originally developed by International Business Machines (IBM) and later on adopted as a standard by the United States in 1977. The use of DES has now been withdrawn. The use of DES is permitted only as a component function of Triple DES (TDES) [
2]. In 2001, the National Institute of Standards and Technology (NIST) announces the Rijndael cipher as a standard of AES. From 2001 until now AES has been successfully applied as a standard not only in the United States but also worldwide. The key size of any encryption algorithms is important for determining the strength of the algorithms. Thus, AES has the flexibility to have three keys that are 128 bits, 192 bits, and 256 bits.
The foundation of modern cryptography by Claude Shannon indicates that two properties that a good cryptosystem should have are confusion and diffusion [
2]. An important component in cryptographic algorithms that provide confusion by the non-linear component is the S-box. In most cryptographic algorithms such as AES and DES, S-box is the only nonlinear component providing a complex relationship between plaintext and ciphertext. In the one round of AES, there are four steps namely SubByte, ShiftRow, MixColumn, and AddRoundKey [
3,
4,
5]. The S-box transformation is in the SubByte which is the only nonlinear part out of the four steps. Many of the past studies have shown that DES is broken due to its weak S-boxes. This implies that the security of cryptosystems is also measured by the security of its S-boxes. Thus, to develop secure cryptographic algorithms, researchers have focused on the formula of constructing a secure S-box and assessing the strength of the particular S-boxes against the analysis such as nonlinearity test, algebraic degree, differential uniformity, and strict avalanche criterion.
The objective of this work is to develop a cryptographically strong 8 × 8 S-box and analyses the S-box to prove its security properties. The rest of this paper is structured as follows. In
Section 2, we listed the literature review on various techniques and improved techniques in constructing the S-box. The review of S-box properties and analysis on nonlinearity test, algebraic degree, differential uniformity, and strict avalanche criterion are presented in
Section 3.
Section 4 is a brief introduction to linear fractional transformation and permutation function. In
Section 5, an S-box is constructed using linear fractional transformation and added permutation function to the S-box. Analysis of the cryptographic characteristics of the improved produce S-box was compared before and after the permutation function in
Section 6, followed by the conclusions in
Section 7.
2. Related Work
Shannon has suggested two methods for a cryptographic algorithm to be resistant to cryptanalysis attacks. These methods are called confusion and diffusion [
6]. The method of confusion in the cryptographic algorithm is to complicate the relationship between the ciphertext and symmetric key, meanwhile, the idea of diffusion is to hide the relationship between the ciphertext and the plaintext. The simplest way to achieve both confusion and diffusion in the cryptographic algorithm is to use a substitution function and permutation function. The most difficult step in verifying the strength of a cryptographic algorithm against cryptanalysis is the selection of cryptographically secure S-box. Therefore, understanding the design and properties of an S-box for applications in the encryption algorithm is essential [
7]. Researchers have been challenged by the improved efficiency of the S-Box to develop confusion ability in the block cipher.
In literature, there are several methods and tools implemented for the construction of cryptographically powerful S-boxes. It is an extremely required property for S-box to demonstrate a good resistance towards linear and differential cryptanalysis [
8,
9]. The linear cryptanalysis is a known-plaintext attack based on finding an affine approximation to the action of a cipher which connects in one expression for some bits of the randomly chosen plaintext and fixed key [
10]. By collecting known plaintext and ciphertext pairs the attack can try to guess the value of bits key, as more plaintext and ciphertext pairs are collected the guessing will become more reliable. Differential cryptanalysis is a process that analyzes the effect of different in plaintext pairs on the resulting pairs of ciphertext. Such differences can be used to assign probabilities and to identify the most likely key. Using the resulting ciphertext pairs this approach typically works on many pairs of plaintexts that have the same particular difference.
Mohamed et al. have suggested several properties to be present in an S-box to be able to resist various cryptanalytic attacks [
11]. An S-box that has a majority of these properties offers greater security. To be considered as cryptographically strong and secure, an S-box requires high nonlinearity, low differential uniformity, high algebraic degree, balancing, low linear approximation, high algebraic complexity, and low/no fixed and opposite fixed points. An S-box has high nonlinearity will offer greater resistance to linear cryptanalysis [
12]. AES uses extremely nonlinear S-box for the encryption and decryption processes in its various rounds. S-box of the AES is operating independently on each byte of the input, this S-box is invertible and developed by assembling two transformations: multiplication inverse and affine transformation [
4]. In [
13], Jie et al. have proposed an improved of AES S-box by changing the affine transformation and adding an affine transformation. The other research that improved AES S-box is changing the complexity of the algebraic expression increases from 9 to 255 and preserve the existing irreducible polynomial, affine transformation matrix, and affine constant with the ability to resist against differential cryptanalysis invariable. Another research on constructing the S-box that caught attention is the S-box structure namely Affine-Power-Affine [
3]. The S-box structure named Affine-Power-Affine aimed to increase the algebraic expressions term of AES S-box which is simple.
In [
14], Mamadolimov et al. have proposed to develop an S-box from power and binomial functions over the finite field and the resulting S-box has Differential Uniformity (DU) 8 and Nonlinearity (NL) 102. This method has been extended and improved by expending the range of the power function into trinomial and including the addition and multiplication as the manipulation techniques [
15]. The obtain S-box has improved the analysis results to DU 4 and NL 108. Zahid and Arshad proposed the cubic polynomial mapping to produce an 8 × 8 S-box. The tested strength of the S-box shows the maximum value of NL is 108 [
16].
Construction of the S-box using linear fractional transformation has been introduced by [
17,
18,
19]. The proposed S-box has been structured by a simple and direct algorithm with a single step function. The strength analysis shows that the S-box fits the criteria for cryptographically strong and is protected against differential and linear cryptanalysis.
In this work, we have applied the method in constructing the S-box that involves the technique of linear fractional transformation. Then applied permutation function to increase the non-linear properties of this S-box. Security analysis is done to the S-box before and after the application of the permutation function to observe the effectiveness of permutation function in increasing the security of the S-box.
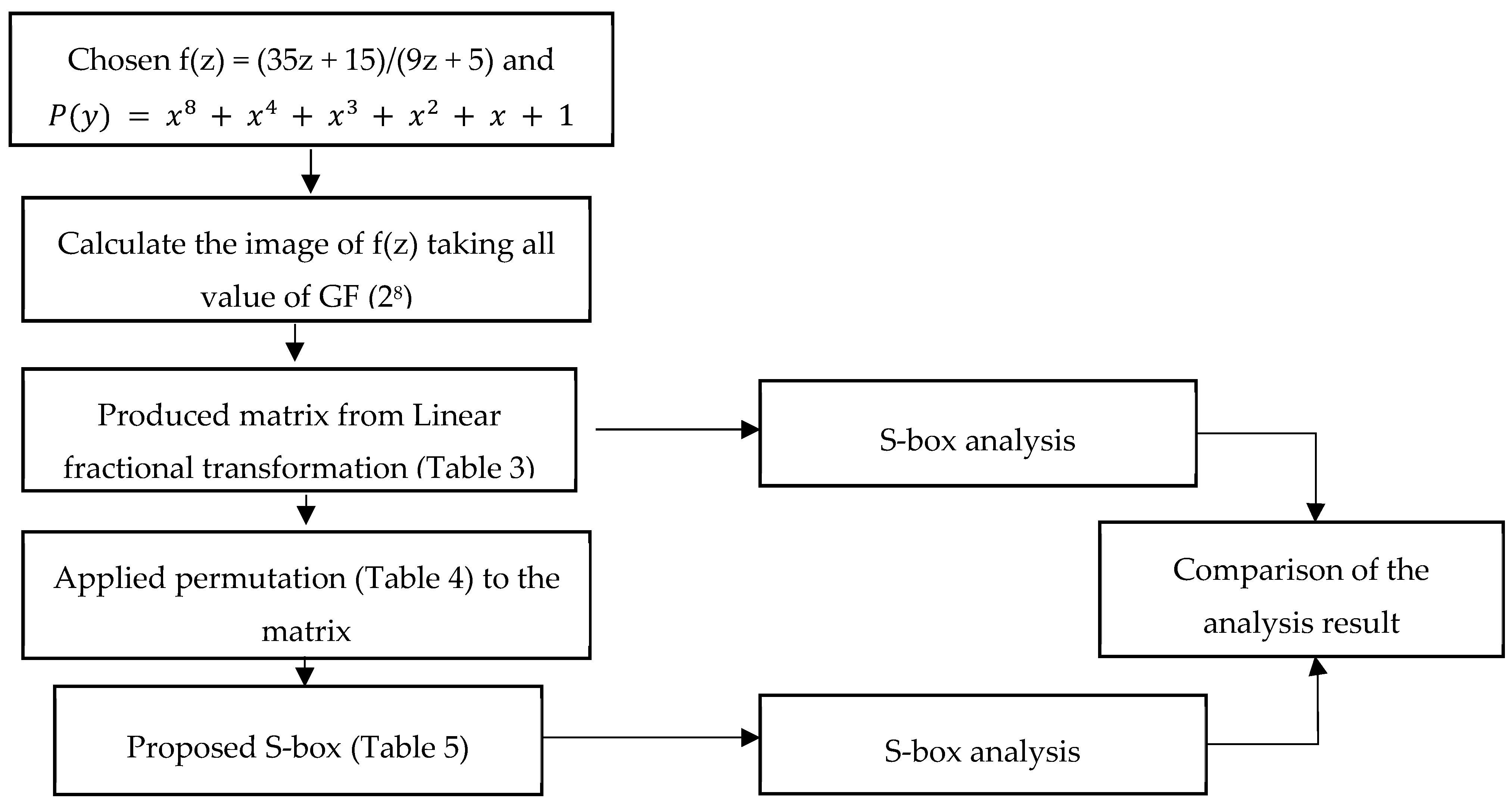
5. Constructions of S-Box
To design an S-box, we utilized an algebraic property of linear fractional transformation and its application on
where n = 8 having elements from 0 to 255. By using the properties of
, the produced S-box will be composed of 256-bit of elements. In AES, S-box is constructed based on the degree 8 irreducible polynomial
. In [
17],
is used as the generating polynomial. The chosen irreducible polynomial for construction of the S-box is
. Any degree 8 irreducible polynomial from the list given in
Table 1 can be used for constructing
S-box, however, the choice of the polynomial may get different S-boxes with different algebraic and statistical properties.
The first step of S-box construction is using an algebraic methodology for
, which is defined as
where
and
is the chosen irreducible polynomial. The second step is to apply the linear fractional transformation such that f(z) = (35z + 15)/(9z + 5), where
. Any values for parameters a, b, c, and d can be used as long it is satisfying the condition ad − bc ≠ 0. Calculation of image f(z) using the chosen form of linear fractional transformation for each of the elements is shown in
Table 2. This linear transformation will produce a 16 × 16 matrix by having elements from
which is given in
Table 3.
The last step is to apply permutation as in
Table 4 to the matrix (
Table 3). The resulting S-box is shown in
Table 5.
The proposed S-box is constructed with the technique of linear fractional transformation and permutation function. The idea of added permutation function is to increase the non-linear properties of this S-box. Therefore, the security analysis is done to the S-box before and after the application of the permutation function to observe the effectiveness of the permutation function in increasing the security of the S-box.
Figure 1 shows the block diagram of the proposed method for the construction of the new S-box.
6. Results and Discussion
To obtain the S-box with proper confusion creating potency, we use a few commonly used analyses such as nonlinearity test, algebraic degree, differential uniformity, and strict avalanche
6.1. Nonlinearity Test
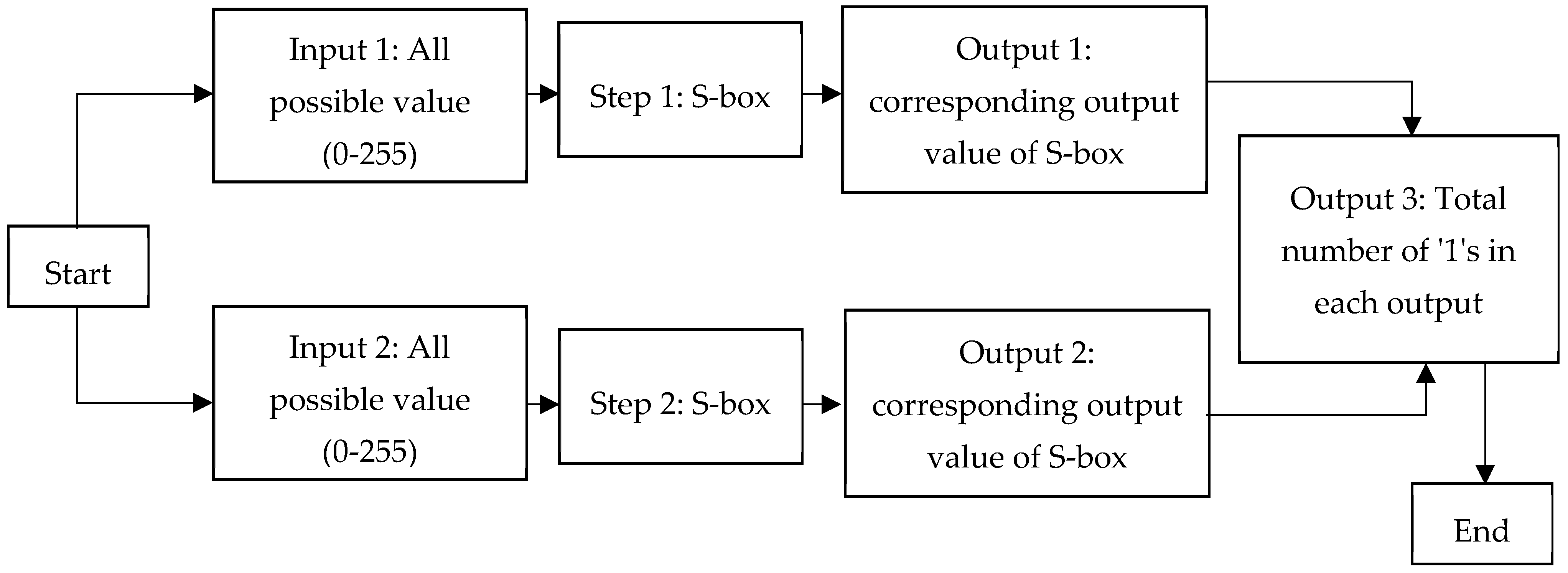
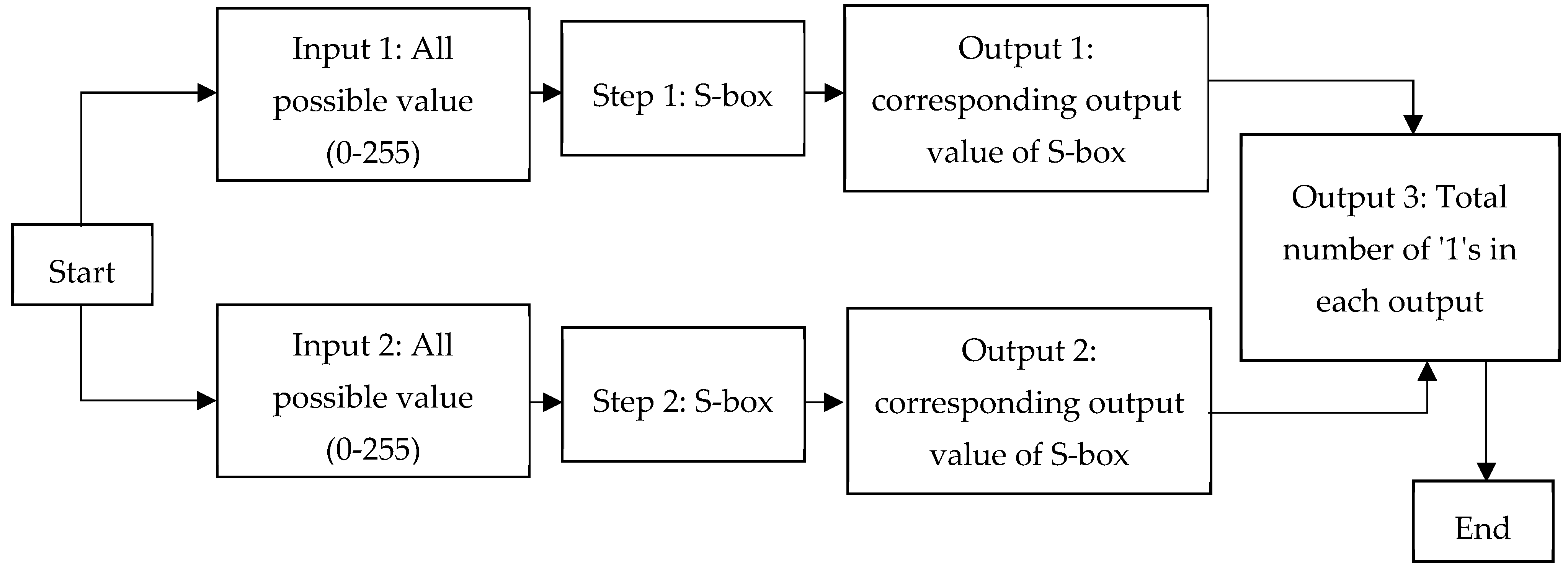
Figure 2 shows the process that has been carried out to find the nonlinearity of S-box which is referred to linear cryptanalysis technique. Input all possible S-box values and evaluate the corresponding output values, the number of cases which hold true is finally observed.
The nonlinearity test is done to the S-box before and after the application of the permutation function. The result shows that the NL value of the S-box before the permutation function is 95, which is vulnerable to linear cryptanalysis. The NL value of the S-box after permutation function is 112, thus it is not susceptible to a linear cryptanalysis attack. The results of this NL value show that the added permutation function has contributed to increasing the nonlinear properties to the S-box.
Figure 3 shows the NL analysis result for S-box after the permutation function. These bar charts represent the number of vectors (axis-y) corresponding to a specific value of the NL parameter (axis-x).
Table 6 shows the results of the S-boxes nonlinearity test before the permutation function and with added permutation function.
6.2. Algebraic Degree
Table 6 shows the results of the S-boxes algebraic degree analysis. The result indicates that the algebraic degrees of output-bit functions for S-box before permutation function and S-box after permutation function are all equal to 7. The algebraic degree of the S-box
has reached the maximum:
. The result of this algebraic degree shows that both S-box with or without permutation function has reached the optimum and maximum value which is 7, therefore the permutation function has not effected in the algebraic degree test.
6.3. Differential Uniformity
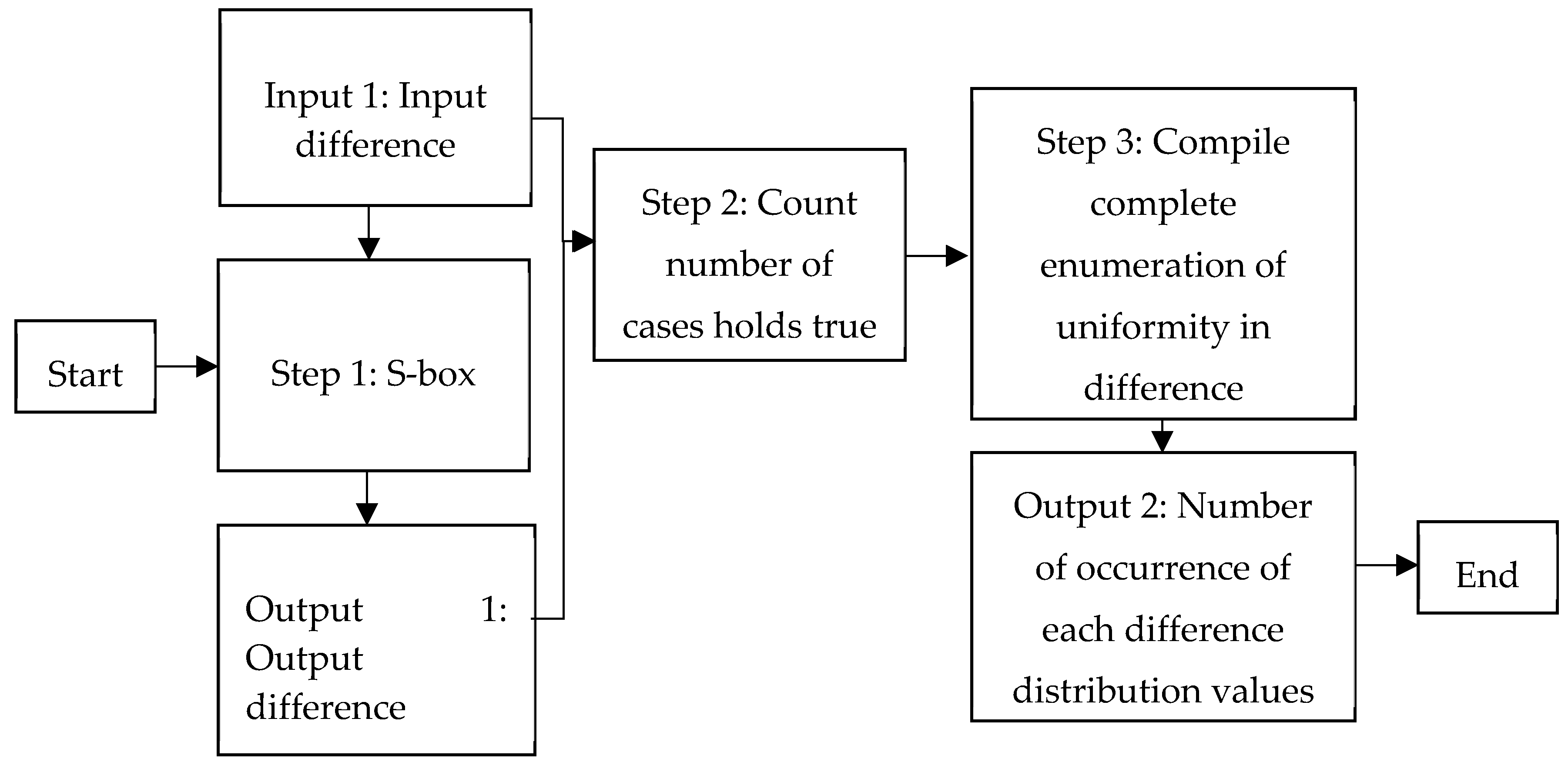
The process of this analysis is similar to the differential cryptanalysis method as depicted in
Figure 4. The result shows that the DU value of the S-box before permutation function is 8 (as shown in
Table 7), which is vulnerable to cryptanalysis. The DU value of the S-box after permutation function is 4 (as shown in
Table 7) thus it is not susceptible to attack.
Table 6 shows the results of the S-boxes differential uniformity test before and after the added permutation function. The results have shown that the added permutation function has contributed to improving the DU value to the S-box.
6.4. Strict Avalanche Criterion
Strict avalanche criterion test uses Hamming Weight for Frequency Analysis to evaluate if the S-box satisfies the property of Avalanche, completeness, and strong S-box.
6.4.1. Avalanche Effect
A function demonstrates the effect of an avalanche if an average of one-half of the output bits shift each time a one input bit is added. Various Hamming Weight Frequency Analysis is used to decide whether it matches Avalanche’s properties. This method aims to track the total number of changes in a bit at each output. Output values were chosen to which two inputs correspond. Use the XOR function to measure the differential value of these two outputs and obtain the differential value for the hamming. Repeat the above steps for the appropriate test count. The frequency of different differential values at each output was evaluated by counting 1s. The process of the avalanche effect test is shown in
Figure 5.
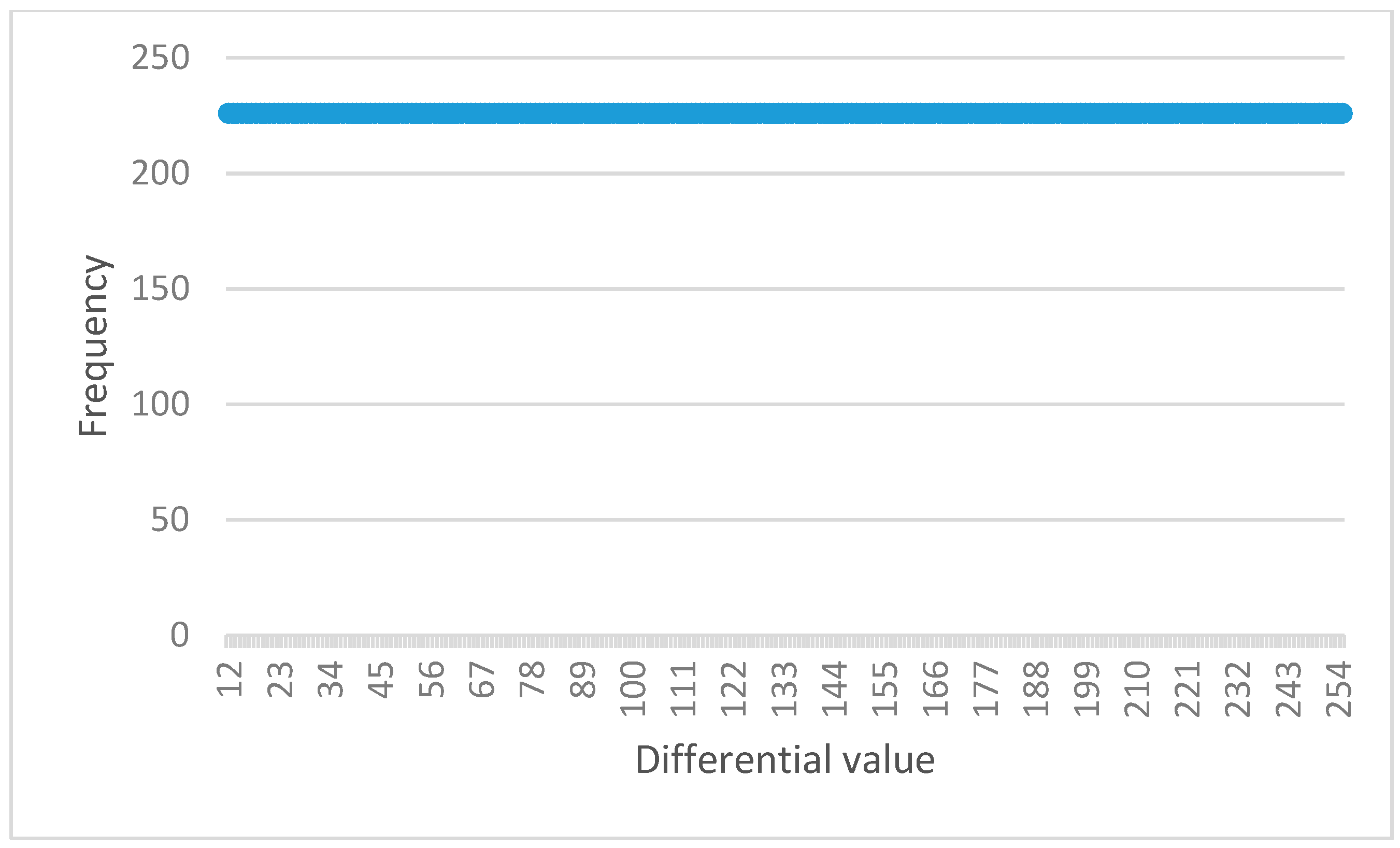
If the frequency of testing result graph shows normal distribution shape (bell shape), the S-box satisfies the avalanche effect property.
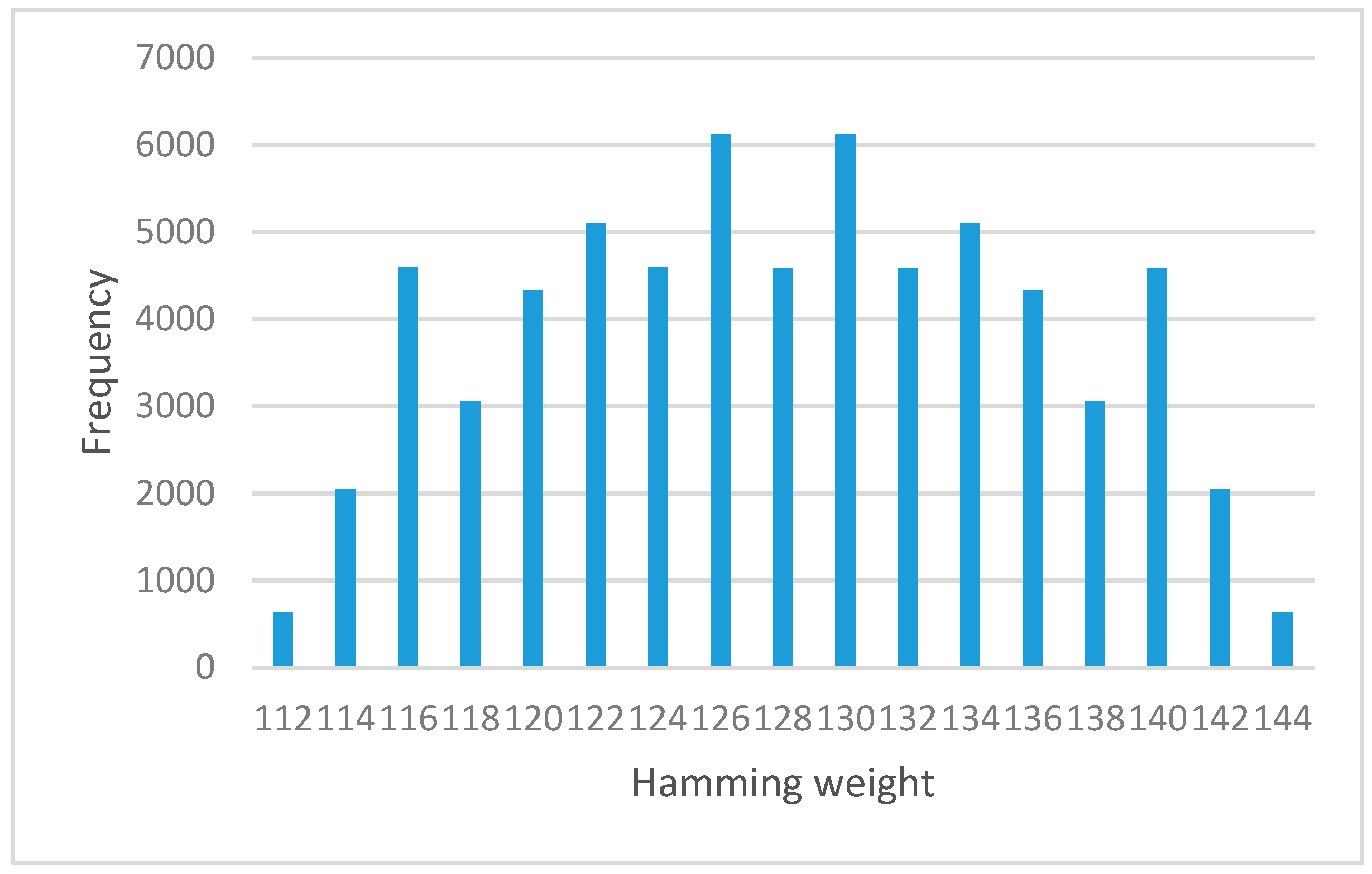
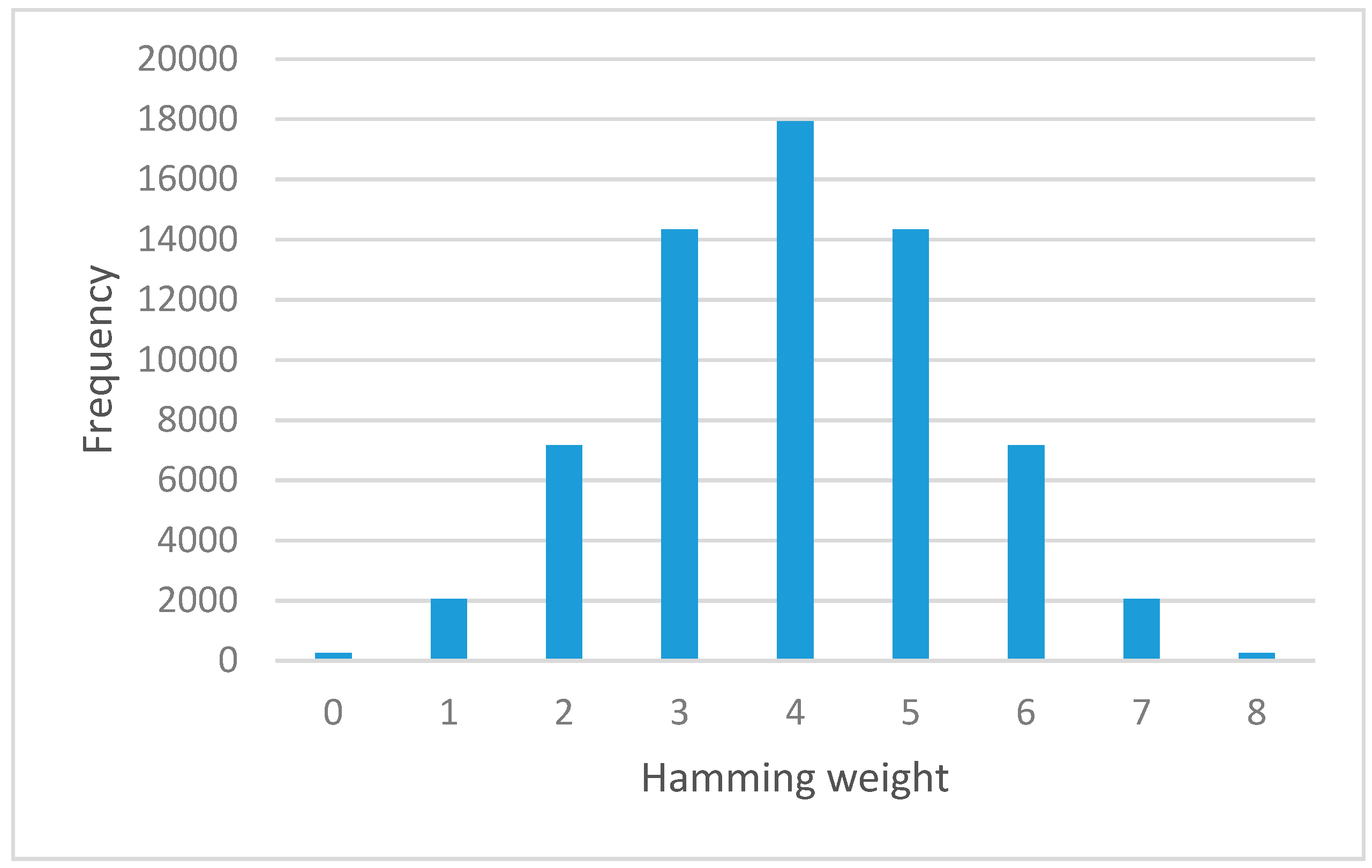
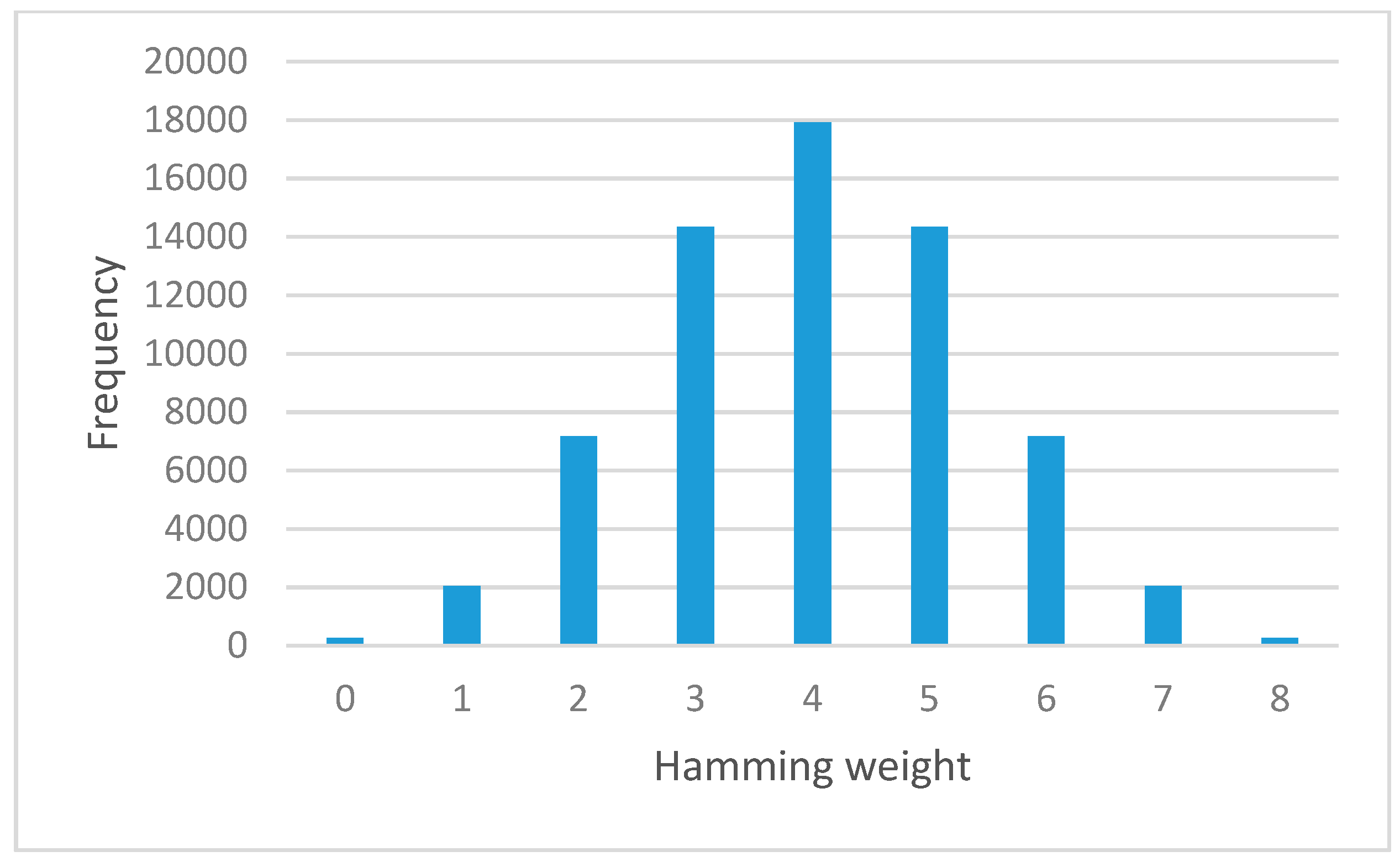
Figure 6 and
Figure 7 show the result of hamming weights and frequency for S-box before and after the permutation function, respectively. From this result, the graph shows a normal distribution shape. It is verified that both S-box appeared to satisfy the avalanche effect property.
6.4.2. Completeness
A function is considered complete only if all bit of output depends on every bit of the input. Thus, if the simplest Boolean expression for output bit in terms of the input bits is possible to be found, all of these Boolean expressions would have to include all the input bits when the function is completed. Process of the completeness test as shown in
Figure 8.
If the frequencies of the hamming weight of differential output are uniformly distributed, the result shows the completeness property.
Figure 9 is the result of the S-box before the permutation function, the graph is not uniformly distributed. Therefore, it is shown that the frequencies of differential output are random.
Figure 10 is the result of the S-box after the permutation function, the graph is uniformly distributed. Therefore, it is verified that the S-box after permutation function appeared to satisfy the completeness property.
6.4.3. Strong S-Box
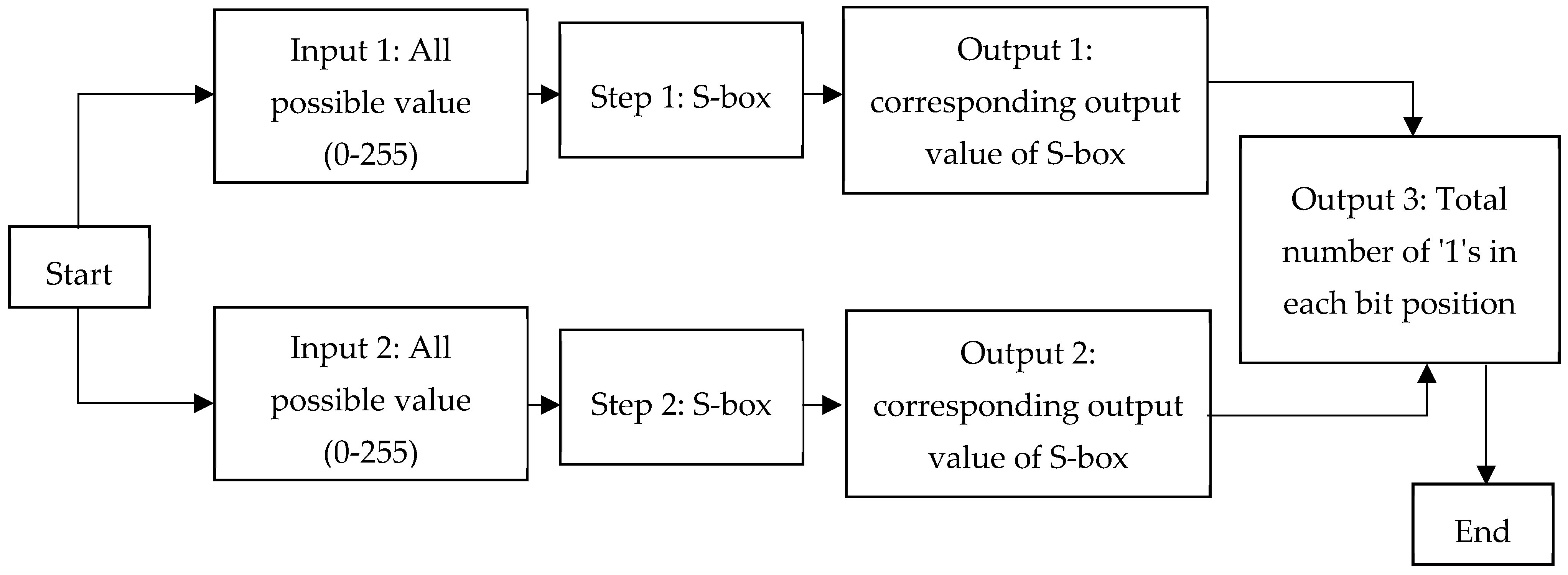
An S-box is deemed strong only if each of its output bits changes with a probability of one-half when complemented by a single one. Process of the strong S-box test as shown in
Figure 11.
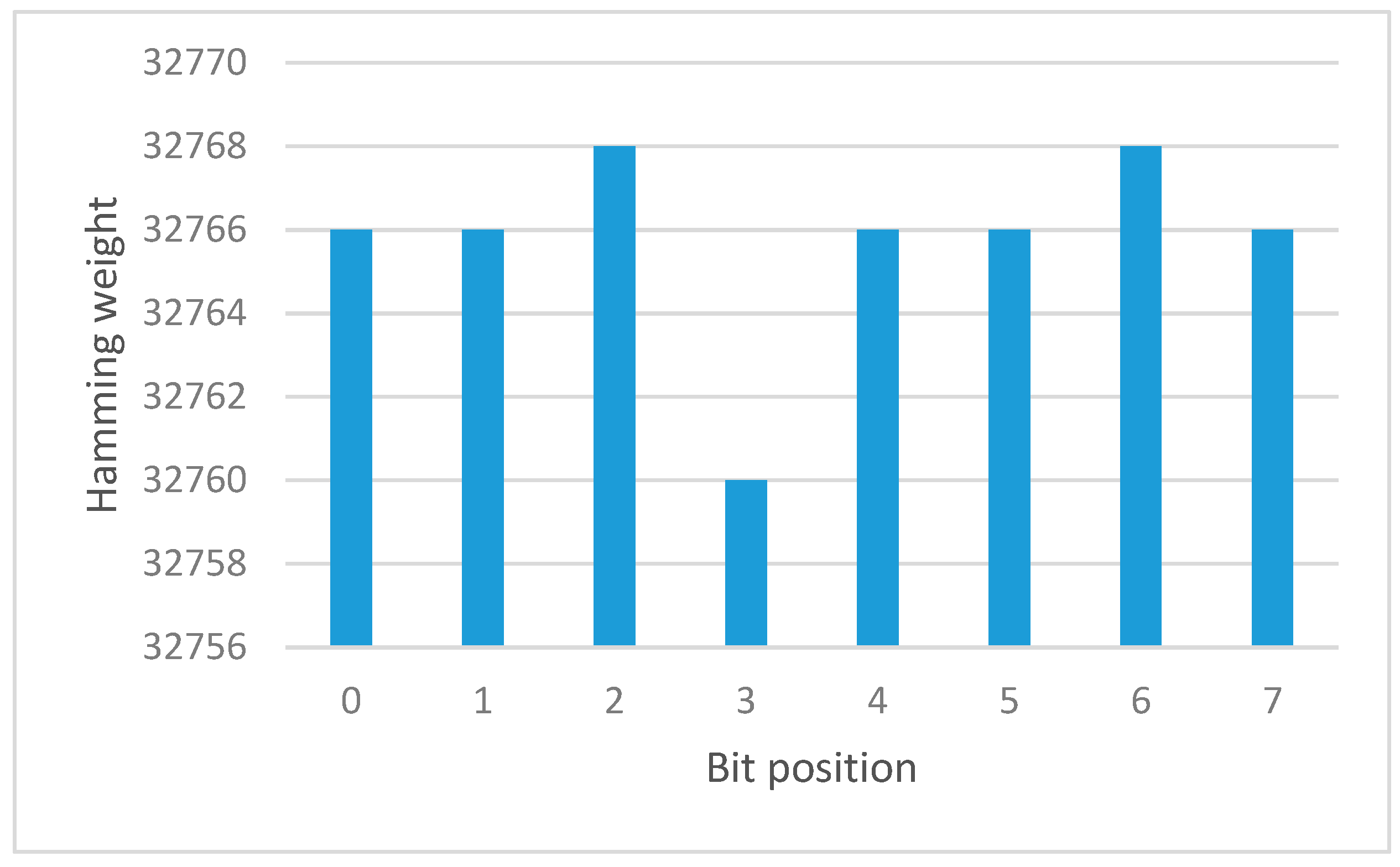
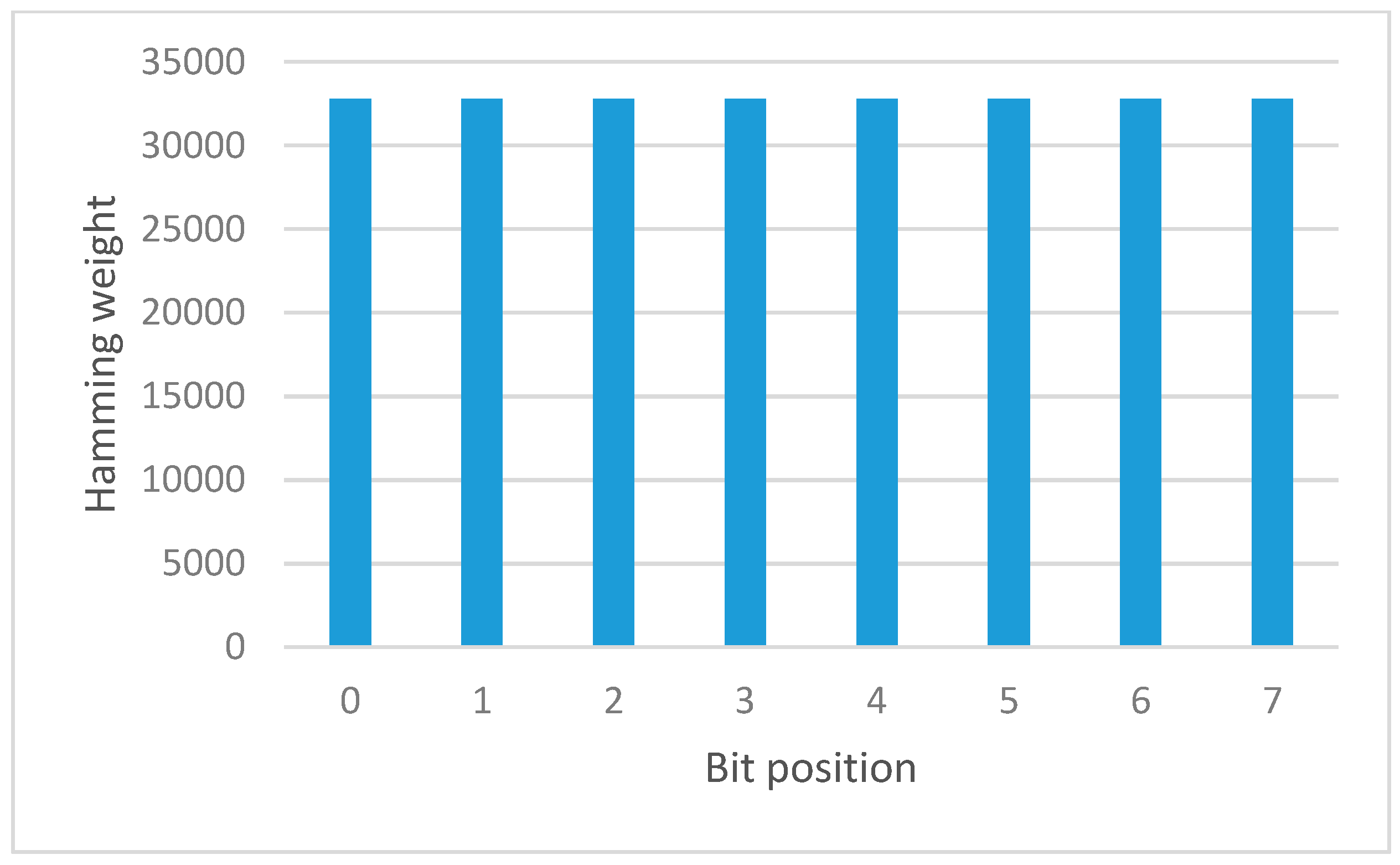
If the frequencies of the hamming weight of differential output according to the bit position are uniformly distributed, the result shows the strong S-box property. If the frequency is random, the tested S-box is considered poor.
Figure 12 shows the result of the S-box before the permutation function is not uniformly distributed.
Figure 13 shows the graph is a uniform distribution shape. Therefore, it is verified that the S-box after the permutation function appeared to satisfy the strong S-box property.
The result of the strict avalanche criterion analysis is shown in
Table 8.
After tested with all the selected S-box tests, the S-box with added permutation function has shown the optimum result as a strong and secure S-box. The S-box is compared with the other 18 S-box from various construction techniques.
Table 9 is the summary and comparison of the obtained S-box with the existing S-boxes in literature. A comparison of the S-box analysis was on the NL, AD, and DU. To considered as cryptographically strong, the following properties for the S-boxes must be satisfied: 100 < NL ≤ 120, AD ≥ 4, and 2 ≤ DU ≤ 6.
7. Conclusions
In this paper, we approach the problem of designing the S-box using linear fractional transformation and next trying to add the permutation function. we compare the result of the S-box that is constructed using linear fractional transformation and S-box with permutation function. The analysis of the S-boxes is based on algebraic attacks. The result shows that the S-box constructed by linear fractional transformation with the addition of permutation function produces a better S-box analysis result. The proposed S-box has satisfied the security properties of cryptographically strong S-box.
However, this S-box has not been implemented in any block cipher to analyses the security of the whole cipher. A block cipher will be chosen to be modified to use the proposed S-box and given a comparison between the original algorithm and the proposed algorithm for future studies. The comparison shall also include the implementation computational for performance analysis.