The Effects of Applying Privacy by Design to Preserve Privacy and Personal Data Protection in Mobile Cloud Computing: An Exploratory Study
Abstract
:1. Introduction
2. Background and Motivation
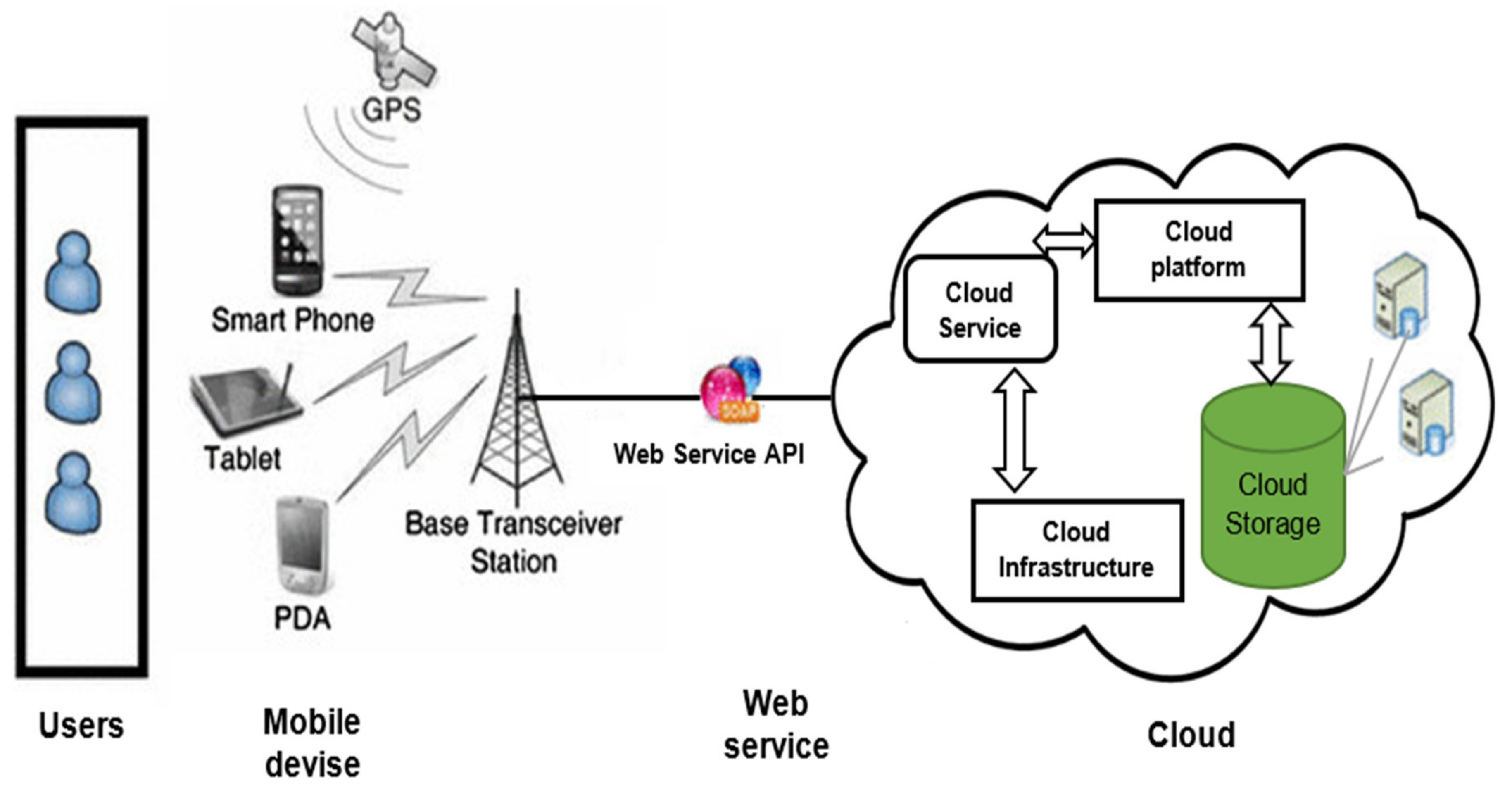
2.1. Mobile Cloud Computing
2.2. Privacy by Design
2.3. The Need for an Exploratory Study
3. Exploratory Study
3.1. Purpose of the Study
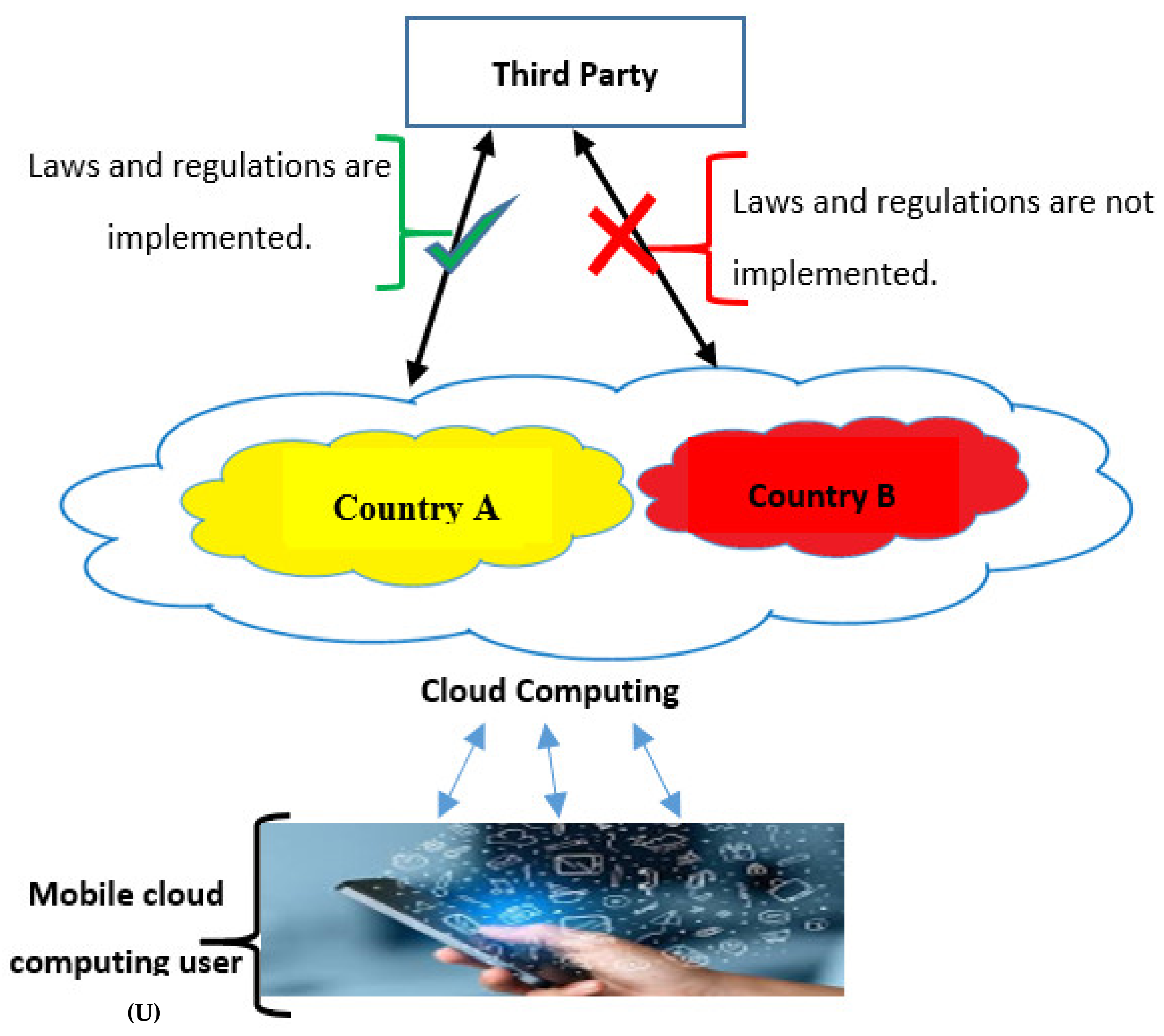
3.2. Proposed Framework
- Registration phase: In this phase, the MCC user must register for using the MCC storage service. In addition to providing the basic data, the MCC user must select the storage location classified based on applying laws and regulations in the MCC storage service locations.
- Synchronization phase: In this phase, the MCC storage service provides synchronization in the existing storage services [44]. In synchronization, personal data on a mobile device are synced to a server that leads to an MCC storage service location. The added, modified, or deleted data will automatically reflect in the selected storage location using upload and download processes [45]. The proposed framework utilizes the existing synchronization process, adding the location, including the ability to know the location of the storage that the user is synchronized with.
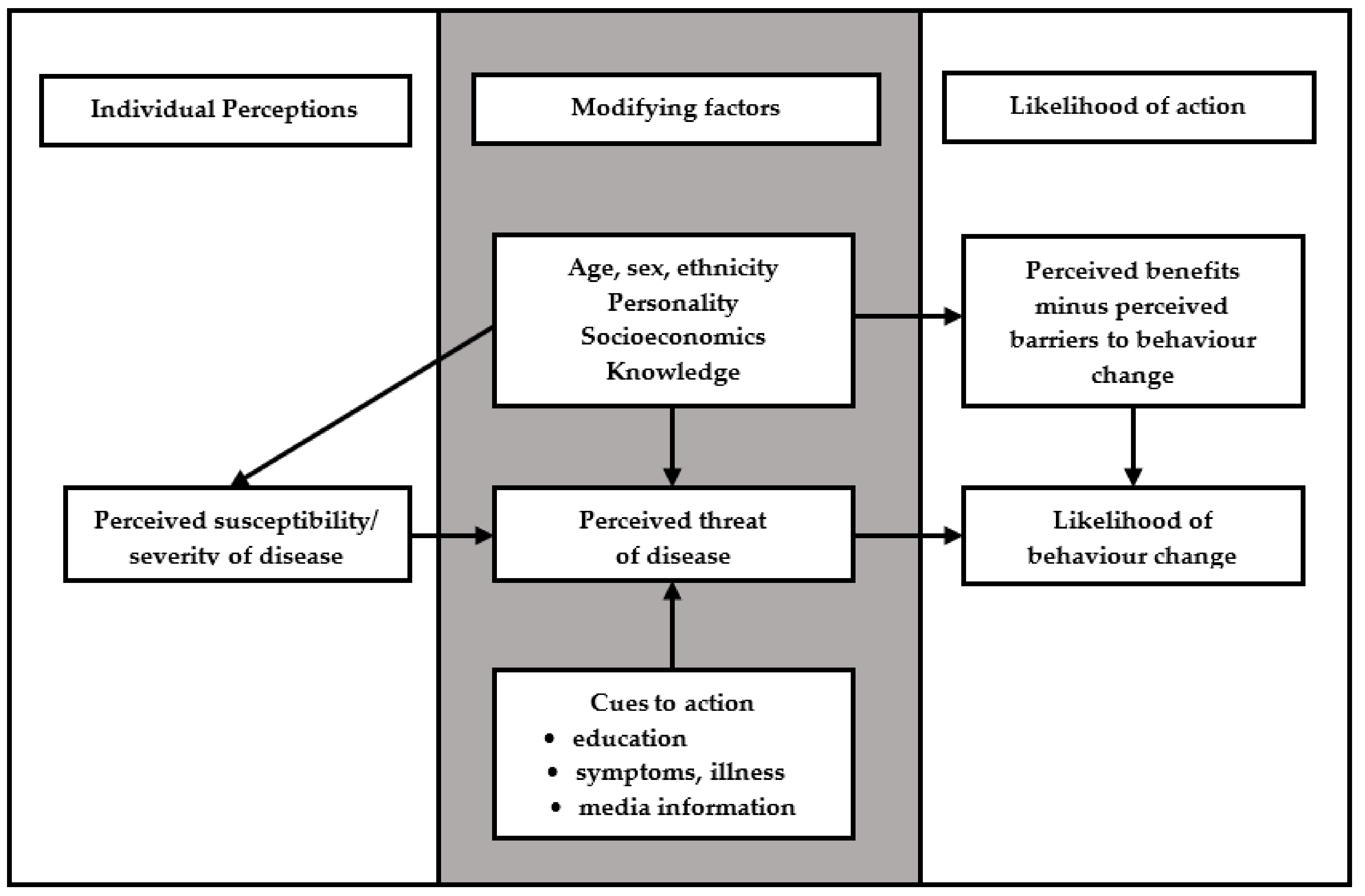
3.3. Research Model
- The HBM tackles personal human issues towards assessing and modeling the impacts of the diseases [15,19,20,49,50,51]. Information systems security experts have adopted the HBM for modeling and assessing personal issues, such as personal data protection and privacy. Obviously, there are many privacy and personal data protection factors that have causes and impacts, which can be assessed by the HBM.
- The HBM can enrich the PbD in MCC through providing cues to action (refers to experiences and applying location transparency for MCC storage location), where cues to action is distinguishing the HBM from other theories, such as Technology Acceptance Model (TAM) [52], Theory of Reasoned Action (TRA) [53], and Theory of Planned Behavior (TPB) [54].
- The HBM can be used to measure the effects of applying PbD to preserve privacy and personal data protection in MCC, since the perceived threat and its underlying relationship to privacy and personal data protection behavior for MCC can be investigated by the HBM.
3.4. Development of Survey Instrument, and Data Collection and Analyses
3.4.1. Instruments
- The first part consists of the demographical data of the respondents, such as Age, Gender, Marital status, Level of education, and Cloud storage.
- The second part contains the constructs, which were ordered as follows:
- ⮚
- Perceived threat: It contains two sub-dimensions, including the perceived susceptibility to violation and threat and perceived severity of risks associated with some given cloud storage locations that do not apply laws and regulations for privacy and personal data protection in MCC. In summary, perceived susceptibility and perceived severity were measured by 4 and 5 items, respectively, adopted from the Al Khater study and self-developed [59].
- ⮚
- Perceived benefits were assessed by the six items developed by Al Khater study and self-developed [59].
- ⮚
- Perceived barriers were assessed by the four items developed by Al Khater study and self-developed [59].
- ⮚
- Cues to Action of PbD were assessed by the six items developed by Al Khater study and self-developed [59].
- ⮚
- Privacy and data protection behavior in MCC are assessed by the five items developed by Al Khater study and self-developed [59].
3.4.2. Validity and Reliability
3.4.3. Data Collection and Analysis
- A.
- Measurement model:
- B.
- Structural model:
4. Results and Discussion
4.1. Results
4.1.1. Results of Measurement Model
- A.
- Convergent validity and reliability
- B.
- Discriminant validity
- C.
- Second-order
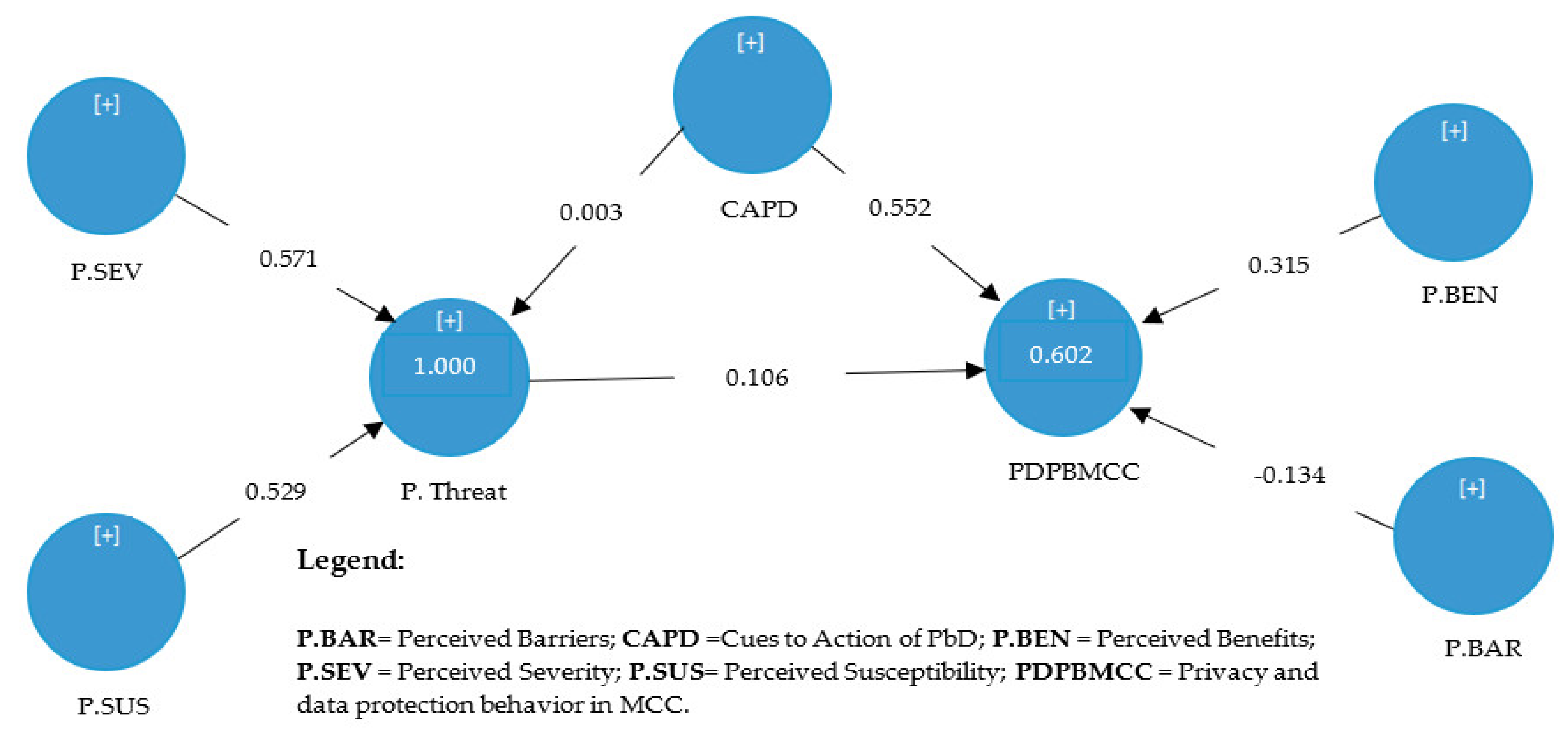
4.1.2. Results of Structural Model
4.2. Discussion
5. Threat to Validity
5.1. Internal Validity
5.2. External Validity
5.3. Construct Validity
6. Comparison with Related Work
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A
Appendix B
| # | Threat | Explanation |
| 1 | Phishing Attacks | “is a type of fraudulent attack in which the intruder acquires the user’s personal information by masquerading as a trustworthy third party through either a fake or stolen identity.” [97]. |
| 2 | Spam Attacks | Spam messages are unwanted messages. |
| 3 | Information Leakage | “Social media are all about openly sharing and exchanging information with friends. Some users willingly share their personal information such as health-related data.” [97]. |
| 4 | Location Leakage threat | is a type of data leakage [97]. |
| 5 | Cyberstalking | “is to harass an individual or group through the Internet or social networking.” [97]. |
| 6 | User Profiling | “is one of the common activities in almost all online services, where OSN servers analyze routine user activities in their space through various machine-learning techniques.” [97]. |
| 7 | Surveillance | “is a new type of monitoring that is different from the sociability and social roles of a person in politics, the economy, and civil society.” [97]. |
| 8 | User identification | “is defined as a feature that helps individuals recognize each other.” [98]. |
| 9 | Privacy of user’s personal space | “The visibility of a social profile has a different type of presence on different social networks.” [98]. |
| 10 | Users’ communication | The information that a user shares with other online social network users, for example, there is some default information that a user shares with the online social network provider such as visited profiles, IP address, the time of connection, and the messages sent. [98]. |
References
- Asrani, P. Mobile cloud computing. Int. J. Eng. Adv. Technol. 2013, 2, 606–609. [Google Scholar]
- Alnajrani, H.M.; Norman, A.A.; Ahmed, B.H. Privacy and data protection in mobile cloud computing: A systematic mapping study. PLoS ONE 2020, 15. [Google Scholar] [CrossRef] [PubMed]
- Sandle, P. Reuters. British Airways Faces Record $230 Million Fine Over Data Theft. 2019. Available online: https://www.reuters.com/article/us-iag-cybercrime-ico/british-airwaysfaces-record-230-million-fine-over-data-theft-idUSKCN1U30KD (accessed on 12 November 2020).
- Cappa, F.; Oriani, R.; Peruffo, E.; McCarthy, I. Big Data for Creating and Capturing Value in the Digitalized Environment: Unpacking the Effects of Volume, Variety, and Veracity on Firm Performance. J. Prod. Innov. Manag. 2020. [Google Scholar] [CrossRef]
- Arthur, C. The Guardian. DigiNotar SSL Certificate Hack Amounts to Cyberwar, Says Expert. 2011. Available online: http://www.theguardian.com/technology/2011/sep/05/diginotar-certificate-hack-cyberwar (accessed on 15 November 2020).
- Ryan, M.D. Cloud computing privacy concerns on our doorstep. Commun. ACM 2011, 54, 36–38. [Google Scholar] [CrossRef]
- Hsu, H.M. Does Privacy Threat Matter in Mobile Health Service? From Health Belief Model Perspective. In PACIS 2016 Proceedings; Pacific Asia Conference on Information Systems (PACIS): Atlanta, GA, USA, 2016; p. 65. [Google Scholar]
- Del Vecchio, P.; Mele, G.; Passiante, G.; Vrontis, D.; Fanuli, C. Detecting customers knowledge from social media big data: Toward an integrated methodological framework based on netnography and business analytics. J. Knowl. Manag. 2020, 24, 799–821. [Google Scholar] [CrossRef]
- Finn, R.L.; Wright, D.; Friedewald, M. Seven types of privacy. In European Data Protection: Coming of Age; Springer: Dordrecht, The Netherlands, 2013; pp. 3–32. [Google Scholar]
- Hayes, D.R.; Cappa, F. Open-source intelligence for risk assessment. Bus. Horiz. 2018, 61, 689–697. [Google Scholar] [CrossRef]
- Pearson, S.; Yee, G. Privacy and Security for Cloud Computing: Computer Communications and Networks; Springer: London, UK, 2013. [Google Scholar]
- Alnemr, R.; Cayirci, E.; Dalla Corte, L.; Garaga, A.; Leenes, R.; Mhungu, R.; Pearson, S.; Reed, C.; de Oliveira, A.S.; Stefanatou, D.; et al. A data protection impact assessment methodology for cloud. In Annual Privacy Forum; Springer: Cham, Switzerland, 2015; pp. 60–92. [Google Scholar]
- Dove, E.S. The EU General Data Protection Regulation: Implications for international scientific research in the digital era. J. Law Med. Eth. 2018, 46, 1013–1030. [Google Scholar] [CrossRef] [Green Version]
- Kroener, I.; Wright, D. A strategy for operationalizing privacy by design. Inf. Soc. 2014, 30, 355–365. [Google Scholar] [CrossRef]
- Ng, B.Y.; Kankanhalli, A.; Xu, Y.C. Studying users’ computer security behavior: A health belief perspective. Decis. Support Syst. 2009, 46, 815–825. [Google Scholar] [CrossRef]
- Edwards, K. Examining the Security Awareness, Information Privacy, and the Security Behaviors of Home Computer Users. Ph.D. Thesis, Nova Southeastern University, Fort Lauderdale, FL, USA, 2015. [Google Scholar]
- Orji, R.; Vassileva, J.; Mandryk, R. Towards an effective health interventions design: An extension of the health belief model. Online J. Public Health Inform. 2012, 4. [Google Scholar] [CrossRef] [Green Version]
- Rosenstock, I.M. Historical origins of the health belief model. Health Educ. Monogr. 1974, 2, 328–335. [Google Scholar] [CrossRef]
- Humaidi, N.; Balakrishnan, V. The moderating effect of working experience on health information system security policies compliance behaviour. Malays. J. Comput. Sci. 2015, 28, 70–92. [Google Scholar]
- Williams, C.K.; Wynn, D.; Madupalli, R.; Karahanna, E.; Duncan, B.K. Explaining users’ security behaviors with the security belief model. J. Organ. End User Comput. 2014, 26, 23–46. [Google Scholar] [CrossRef]
- Ringle, C.M.; Wende, S.; Will, A. SmartPLS; Version 2.0 M3; University of Hamburg: Hamburg, Germany, 2005. [Google Scholar]
- Ferreira, J.A.L.; da Silva, A.R. Mobile cloud computing. Open J. Mob. Comput. Cloud Comput. 2014, 1, 59–77. [Google Scholar]
- Al-Ruithe, M.; Benkhelifa, E.; Hameed, K. Current state of cloud computing adoption–an empirical study in major public sector organizations of saudi arabia (ksa). Procedia Comput. Sci. 2017, 110, 378–385. [Google Scholar] [CrossRef]
- Fernando, N.; Loke, S.W.; Rahayu, W. Mobile cloud computing: A survey. Future Gener. Comput. Syst. 2013, 29, 84–106. [Google Scholar] [CrossRef]
- Bellman, S.; Johnson, E.J.; Kobrin, S.J.; Lohse, G.L. International differences in information privacy concerns: A global survey of consumers. Inf. Soc. 2004, 20, 313–324. [Google Scholar] [CrossRef]
- Tikkinen-Piri, C.; Rohunen, A.; Markkula, J. EU General Data Protection Regulation: Changes and implications for personal data collecting companies. Comput. Law Secur. Rev. 2018, 34, 134–153. [Google Scholar] [CrossRef] [Green Version]
- Fromholz, J.M. The European Union data privacy directive. Berk. Tech. LJ 2000, 15, 461. [Google Scholar]
- Harfoushi, O. Trust model for effective cloud computing usage: A quantitative study. J. Theor. Appl. Inf. Technol. 2017, 95, 1116–1123. [Google Scholar]
- Ruiter, J.; Warnier, M. Privacy regulations for cloud computing: Compliance and implementation in theory and practice. In Computers, Privacy and Data Protection: An Element of Choice; Springer: Dordrecht, The Netherlands, 2011; pp. 361–376. [Google Scholar]
- Hanen, J.; Kechaou, Z.; Ayed, M.B. An enhanced healthcare system in mobile cloud computing environment. Vietnam J. Comput. Sci. 2016, 3, 267–277. [Google Scholar] [CrossRef] [Green Version]
- Chen, D.; Zhao, H. Data security and privacy protection issues in cloud computing. In Proceedings of the 2012 International Conference on Computer Science and Electronics Engineering, Hangzhou, China, 23–25 March 2012; IEEE: New York, NY, USA, 2012; Volume 1, pp. 647–651. [Google Scholar]
- Guilloteau, S.; Venkatesen, M. Privacy in Cloud Computing-ITU-T Technology Watch Report March 2012; International Telecommunication Union: Geneva, Switzerland, 2013. [Google Scholar]
- Langheinrich, M. Privacy by design—Principles of privacy-aware ubiquitous systems. In Proceedings of the International Conference on Ubiquitous Computing, Atlanta, GA, USA, 30 September–2 October 2001; Springer: Berlin/Heidelberg, Germany, 2001; pp. 73–291. [Google Scholar]
- Baharon, M.R.; Shi, Q.; Llewellyn-Jones, D. A new lightweight homomorphic encryption scheme for mobile cloud computing. In Proceedings of the 2015 IEEE International Conference on Computer and Information Technology; Ubiquitous Computing and Communications; Dependable, Autonomic and Secure Computing; Pervasive Intelligence and Computing, Liverpool, UK, 26–28 October 2015; IEEE: New York, NY, USA, 2015; pp. 618–625. [Google Scholar]
- Angin, P.; Bhargava, B.; Ranchal, R.; Singh, N.; Linderman, M.; Othmane, L.B.; Lilien, L. An entity-centric approach for privacy and identity management in cloud computing. In Proceedings of the 2010 29th IEEE Symposium on Reliable Distributed Systems, New Delhi, India, 31 October–3 November 2010; IEEE: New York, NY, USA, 2010; pp. 177–183. [Google Scholar]
- Huang, D.; Zhou, Z.; Xu, L.; Xing, T.; Zhong, Y. Secure data processing framework for mobile cloud computing. In Proceedings of the 2011 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Shanghai, China, 10–15 April 2011; IEEE: New York, NY, USA, 2011; pp. 614–618. [Google Scholar]
- Li, F.; Rahulamathavan, Y.; Conti, M.; Rajarajan, M. Robust access control framework for mobile cloud computing network. Comput. Commun. 2015, 68, 61–72. [Google Scholar] [CrossRef] [Green Version]
- Douglas, J.E.; Burgess, A.W.; Burgess, A.G.; Ressler, R.K. Crime Classification Manual: A Standard System for Investigating and Classifying Violent Crime; John Wiley & Sons: New York, NY, USA, 2013. [Google Scholar]
- Maurushat, A. Ethical Hacking; University of Ottawa Press: Ottawa, ON, Canada, 2019. [Google Scholar]
- Ehécatl Morales-Trujillo, M.; García-Mireles, G.A.; Matla-Cruz, E.O.; Piattini, M. A Systematic Mapping Study on Privacy by Design in Software Engineering. CLEI Electron. J. 2019, 22. [Google Scholar] [CrossRef]
- Le Métayer, D. Privacy by design: A matter of choice. In Data Protection in a Profiled World; Springer: Dordrecht, The Netherlands, 2010; pp. 323–334. [Google Scholar]
- Sanaei, Z.; Abolfazli, S.; Gani, A.; Buyya, R. Heterogeneity in mobile cloud computing: Taxonomy and open challenges. IEEE Commun. Surv. Tutor. 2013, 16, 369–392. [Google Scholar] [CrossRef]
- Abolfazli, S.; Sanaei, Z.; Gani, A.; Xia, F.; Yang, L.T. Rich mobile applications: Genesis, taxonomy, and open issues. J. Netw. Comput. Appl. 2014, 40, 345–362. [Google Scholar] [CrossRef]
- Flores, H.; Srirama, S.N.; Paniagua, C. A Generic Middleware Framework for Handling Process Intensive Hybrid Cloud Services from Mobiles. Available online: http://doi.acm.org/10.1145/2095697.2095715 (accessed on 11 November 2020).
- Cui, Y.; Lai, Z.; Wang, X.; Dai, N. Quicksync: Improving synchronization efficiency for mobile cloud storage services. IEEE Trans. Mob. Comput. 2017, 16, 3513–3526. [Google Scholar] [CrossRef]
- Jayanti, R.K.; Burns, A.C. The antecedents of preventive health care behavior: An empirical study. J. Acad. Mark. Sci. 1998, 26, 6–15. [Google Scholar] [CrossRef]
- Ng, B.Y.; Xu, Y. Studying users’ computer security behavior using the Health Belief Model. In Proceedings of the Conference: Pacific Asia Conference on Information Systems, PACIS 2007, Auckland, New Zealand, 4–6 July 2007. [Google Scholar]
- Humaidi, N. An Investigation of Health Information System Security Policies Compliance Behaviour. Ph.D. Dissertation, University of Malaya, Kuala Lumpur, Malaysia, 2016. [Google Scholar]
- Claar, C.L.; Johnson, J. Analyzing the adoption of computer security utilizing the Health Belief Model. Issues Inf. Syst. 2010, 11, 286–291. [Google Scholar]
- Humaidi, N.; Balakrishnan, V. The influence of security awareness and security technology on users’ behavior towards the implementation of health information system: A conceptual framework. In 2nd International Conference on Management and Artificial Intelligence IPEDR; IACSIT Press: Singapore, 2012; Volume 35, pp. 1–6. [Google Scholar]
- Koloseni, D.N.; Lee, C.Y.; Gan, M.L. Understanding Information Security Behaviours of Tanzanian Government Employees: A Health Belief Model Perspective. Int. J. Technol. Hum. Interact. 2019, 15, 15–32. [Google Scholar] [CrossRef] [Green Version]
- Davis, F.D. A Technology Acceptance Model for Empirically Testing New End-User Information Systems: Theory and Results. Ph.D. Dissertation, Massachusetts Institute of Technology, Cambridge, MA, USA, 1985. [Google Scholar]
- Goldenhar, L.M.; Connell, C.M. Understanding and predicting recycling behavior: An application of the theory of reasoned action. J. Environ. Syst. 1992, 22, 91–103. [Google Scholar] [CrossRef]
- Lee, J.; Cerreto, F.A.; Lee, J. Theory of planned behavior and teachers’ decisions regarding use of educational technology. J. Educ. Technol. Soc. 2010, 13, 152–164. [Google Scholar]
- Vatka, M. Information Behaviour and Data Security: Health Belief Model Perspective; Åbo Akademi: Turku, Finland, 2019. [Google Scholar]
- Dodel, M.; Mesch, G. Cyber-victimization preventive behavior: A health belief model approach. Comput. Hum. Behav. 2017, 68, 359–367. [Google Scholar] [CrossRef]
- Glanz, K.; Rimer, B.K.; Viswanath, K. Health Behavior and Health Education: Theory, Research, and Practice; John Wiley & Son: New York, NY, USA, 2008. [Google Scholar]
- Wetzels, M.; Odekerken-Schröder, G.; Van Oppen, C. Using PLS path modeling for assessing hierarchical construct models: Guidelines and empirical illustration. MIS Q. 2009, 177–195. [Google Scholar] [CrossRef]
- Al Khater, N.R. A Model of a Private Sector Organisation’s Intention to Adopt Cloud Computing in the Kingdom of Saudi Arabia. Ph.D. Dissertation, University of Southampton, Southampton, UK, 2017. [Google Scholar]
- Brown, S. Likert Scale Examples for Surveys. ANR Program Evaluation; Iowa State University: Ames, IA, USA, 2010. [Google Scholar]
- Vasantha, R.N.; Harinarayana, N.S. Online survey tools: A case study of Google Forms. In National Conference on Scientific, Computational & Information Research Trends in Engineering, GSSS-IETW, Mysore; University in Mysore: Mysore, India, 2016. [Google Scholar]
- Petrić, B.; Czárl, B. Validating a writing strategy questionnaire. System 2003, 31, 187–215. [Google Scholar] [CrossRef]
- Wallace, L.S.; Blake, G.H.; Parham, J.S.; Baldridge, R.E. Development and content validation of family practice residency recruitment questionnaires. Fam. Med. Kans. City 2003, 35, 496–498. [Google Scholar]
- Esmaeili, M. Assessment of Users’ Information Security Behavior in Smartphone Networks. Ph.D. Thesis, Eastern Michigan University, Ypsilanti, MI, USA, 2014. [Google Scholar]
- Hassan, Z.A.; Schattner, P.; Mazza, D. Doing a pilot study: Why is it essential? Malays. Fam. Physician 2006, 1, 70–73. [Google Scholar]
- Tumusiime, D.K. Perceived Benefits of, Barriers and Helpful Cues to Physical Activity among Tertiary Institution Students in Rwanda. Ph.D. Dissertation, University of the Western Cape, Cape Town, South Africa, 2004. [Google Scholar]
- Tongco, M.D.C. Purposive sampling as a tool for informant selection. Ethnobot. Res. Appl. 2007, 5, 147–158. [Google Scholar] [CrossRef] [Green Version]
- Hair, J.F.; Black, W.C.; Babin, B.J.; Anderson, R.E.; Tatham, R. Multivariate Data Analysis; Prentice hall Upper Saddle River: Bergen, NJ, USA, 1998. [Google Scholar]
- Hair, J.F.; Ringle, C.M.; Sarstedt, M. PLS-SEM: Indeed a silver bullet. J. Mark. Theory Pract. 2011, 19, 139–152. [Google Scholar] [CrossRef]
- Creswell, J.W. Educational Research: Planning, Conducting, and Evaluating Quantitative and Qualitative Research; Pearson: London, UK, 2012. [Google Scholar]
- Nulty, D.D. The adequacy of response rates to online and paper surveys: What can be done? Assess. Eval. Higher Educ. 2008, 33, 301–314. [Google Scholar] [CrossRef] [Green Version]
- Saldivar, M.G. A Primer on Survey Response Rate. Ph.D. Thesis, Learning Systems Institute Florida State University, Tallahassee, FL, USA, 2012. [Google Scholar]
- Fornell, C.; Larcker, D.F. Evaluating structural equation models with unobservable variables and measurement error. J. Mark. Res. 1981, 18, 39–50. [Google Scholar] [CrossRef]
- Chin, W.W. The partial least squares approach to structural equation modeling. Modern Methods Bus. Res. 1998, 295, 295–336. [Google Scholar]
- Ab Hamid, M.R.; Sami, W.; Sidek, M.M. Discriminant validity assessment: Use of Fornell & Larcker criterion versus HTMT criterion. In Journal of Physics: Conference Series; IOP Science: Bristol, UK, 2017; Volume 890. [Google Scholar]
- Janadari, M.P.N.; Sri Ramalu, S.; Wei, C. Evaluation of measurment and structural model of the reflective model constructs in PLS–SEM. In Proceedings of the 6th International Symposium—2016 South Eastern University of Sri Lanka (SEUSL), Oluvil, Sri Lanka, 20–21 December 2016. [Google Scholar]
- Chin, W.W. How to write up and report PLS analyses. In Handbook of Partial Least Squares Concepts, Methods and Applications; Esposito Vinzi, V., Chin, W., Henseler, J., Wang, H., Eds.; Springer: Berlin/Heidelberg, Germany, 2010; pp. 655–690. [Google Scholar]
- Nunnally, J.C. Psychometric Theory, 2nd ed.; McGraw-Hill: Singapore, 1978. [Google Scholar]
- Hair, J.F.; Babin, B.J.; Black, W.C. Multivariate Data Analysis: A Global Perspective, 7th ed.; Pearson Education: London, UK, 2010. [Google Scholar]
- Petter, S.; Straub, D.; Rai, A. Specifying formative constructs in information systems research. MIS Q. 2007, 623–656. [Google Scholar] [CrossRef] [Green Version]
- Bagozzi, R.P.; Yi, Y. On the evaluation of structural equation models. J. Acad. Mark. Sci. 1988, 16, 74–94. [Google Scholar] [CrossRef]
- Gefen, D.; Straub, D. A practical guide to factorial validity using PLS-Graph: Tutorial and annotated example. Commun. Assoc. Inf. Syst. 2005, 16. [Google Scholar] [CrossRef] [Green Version]
- Gefen, D.; Straub, D.; Boudreau, M.C. Structural equation modeling and regression: Guidelines for research practice. Commun. Assoc. Inf. Syst. 2000, 4. [Google Scholar] [CrossRef] [Green Version]
- Falk, R.F.; Miller, N.B. A Primer for Soft Modeling; University of Akron Press: Akron, OH, USA, 1992. [Google Scholar]
- Puspita, R.C.; Tamtomo, D.; Indarto, D. Health belief model for the analysis of factors affecting hypertension preventive behavior among adolescents in Surakarta. J. Health Promot. Behav. 2017, 2, 183–196. [Google Scholar] [CrossRef] [Green Version]
- Ahmed, B.H.; Lee, S.P.; Su, M.T. The Effects of Static Analysis for Dynamic Software Updating: An Exploratory Study. IEEE Access 2020, 8, 35161–35171. [Google Scholar] [CrossRef]
- Khorsan, R.; Crawford, C. External validity and model validity: A conceptual approach for systematic review methodology. Evid. Based Complement. Altern. Med. 2014, 2014. [Google Scholar] [CrossRef] [Green Version]
- Cavoukian, A.; Fisher, A.; Killen, S.; Hoffman, D.A. Remote home health care technologies: How to ensure privacy? Build it in: Privacy by design. Identity Inf. Soc. 2010, 3, 363–378. [Google Scholar] [CrossRef] [Green Version]
- Cavoukian, A. Global Privacy and Security, by Design: Turning the “Privacy vs. Security” Paradigm on its Head; Springer: Cham, Switzerland, 2017. [Google Scholar]
- Cavoukian, A.; Spencer, P.C. The Ontario Health Study’s Assessment Centres: A Case Study for “Privacy by Design”; Information and Privacy Commissioner of Ontario: Toronto, ON, Canada, 2010. [Google Scholar]
- Wohlin, C.; Runeson, P.; Höst, M.; Ohlsson, M.C.; Regnell, B.; Wesslén, A. Experimentation in Software Engineering; Springer Science & Business Media: Berlin, Germany, 2012. [Google Scholar]
- Schymik, G.; Du, J. Student Intentions and Behaviors Related to Email Security: An Application of the Health Belief Model. In Proceedings of the Conference on Information Systems Applied Research ISSN; ISCAP: São Mamede de Infesta, Portugal, 2017; Volume 2167, p. 1508. [Google Scholar]
- Ameme, B.K.; Yeboah-Boateng, E.O. Internet Banking Security Concerns: An Exploratory Study of Customer Behaviors Based on Health Belief Model. Available online: https://www.researchgate.net/publication/298794389 (accessed on 20 November 2020).
- Ahmed, B.H.; Lee, S.P.; Su, M.T.; Zakari, A. Dynamic software updating: A systematic mapping study. IET Softw. 2020, 14, 468–481. [Google Scholar] [CrossRef]
- Dey, S.; Sampalli, S.; Ye, Q. Security and privacy issues in mobile cloud computing. Int. J. Bus. Cyber Secur. 2016, 1, 31–43. [Google Scholar]
- Hayes, D.; Cappa, F.; Le-Khac, N.A. An effective approach to mobile device management: Security and privacy issues associated with mobile applications. Dig. Bus. 2020, 1. [Google Scholar] [CrossRef]
- Ali, S.; Islam, N.; Rauf, A.; Din, I.U.; Guizani, M.; Rodrigues, J.J. Privacy and security issues in online social networks. Future Internet 2018, 10, 114. [Google Scholar] [CrossRef] [Green Version]
- Al-Muhtadi, J.; Shahzad, B.; Saleem, K.; Jameel, W.; Orgun, M.A. Cybersecurity and privacy issues for socially integrated mobile healthcare applications operating in a multi-cloud environment. Health Inform. J. 2019, 25, 315–329. [Google Scholar] [CrossRef]



| # | Research Question | Research Objective |
|---|---|---|
| 1 | How to preserve privacy and personal data protection in mobile cloud computing using privacy by design framework? | To illustrate applying privacy by design framework to preserve privacy and personal data protection in MCC. |
| 2 | How does the privacy by design framework effects preserving privacy and personal data protection in MCC? | To evaluate the privacy by design framework in preserving privacy and personal data protection in MCC. |
| Demographic | Category | Percentage | Number of Participate |
|---|---|---|---|
| Age | 19 or younger | 0.78% | 3 |
| 20 to 29 | 29.53% | 114 | |
| 30 to 39 | 50.52% | 195 | |
| 40 or older | 19.17% | 74 | |
| Gender | Male | 79.27% | 306 |
| Female | 20.73% | 80 | |
| Marital status | Single | 34.97% | 135 |
| Married | 60.62% | 234 | |
| Divorced | 4.40% | 17 | |
| Education level | Elementary/Primary education | 0.52% | 2 |
| High school diploma | 3.63% | 14 | |
| Bachelor’s degree | 49.74% | 192 | |
| Master’s degree | 39.38% | 152 | |
| Ph.D./Doctorate | 6.74% | 26 | |
| Cloud storage | Google Drive | 45.85% | 177 |
| Dropbox | 16.32% | 63 | |
| One Drive (formerly Sky Drive) | 8.03% | 31 | |
| iCloud | 21.24% | 82 | |
| Others | 8.55% | 33 |
| Constructs | Items | Loading | VIF | AVE | CR | CA |
|---|---|---|---|---|---|---|
| Perceived Severity | P.SEV1 | 0.805 | 1.696 | 0.504 | 0.835 | 0.752 |
| P.SEV2 | 0.753 | 1.514 | ||||
| P.SEV3 | 0.653 | 1.297 | ||||
| P.SEV4 | 0.666 | 1.309 | ||||
| P.SEV5 | 0.661 | 1.293 | ||||
| Perceived Susceptibility | P.SUS1 | 0.787 | 1.631 | 0.586 | 0.849 | 0.762 |
| P.SUS2 | 0.844 | 1.877 | ||||
| P.SUS3 | 0.711 | 1.351 | ||||
| P.SUS4 | 0.711 | 1.359 | ||||
| Perceived Benefits | P.BEN1 | 0.716 | 1.913 | 0.608 | 0.903 | 0.871 |
| P.BEN2 | 0.742 | 1.977 | ||||
| P.BEN3 | 0.822 | 2.314 | ||||
| P.BEN4 | 0.834 | 2.466 | ||||
| P.BEN5 | 0.740 | 1.711 | ||||
| P.BEN6 | 0.817 | 2.024 | ||||
| Perceived Barriers | P. BAR1 | 0.721 | 1.304 | 0.582 | 0.847 | 0.764 |
| P. BAR2 | 0.817 | 1.516 | ||||
| P. BAR3 | 0.792 | 1.696 | ||||
| P. BAR4 | 0.716 | 1.584 | ||||
| Cues to Action of Privacy by design | CAPD1 | 0.699 | 1.561 | 0.597 | 0.898 | 0.864 |
| CAPD2 | 0.787 | 2.033 | ||||
| CAPD3 | 0.804 | 2.065 | ||||
| CAPD4 | 0.706 | 1.500 | ||||
| CAPD5 | 0.826 | 2.494 | ||||
| CAPD6 | 0.804 | 2.298 | ||||
| Privacy and personal data protection behavior in MCC | PDBPMCC1 | 0.728 | 1.610 | 0.671 | 0.910 | 0.876 |
| PDBPMCC2 | 0.819 | 2.048 | ||||
| PDBPMCC3 | 0.868 | 2.557 | ||||
| PDBPMCC4 | 0.830 | 2.626 | ||||
| PDBPMCC5 | 0.844 | 2.741 |
| CAPD | P. BAR | P. BEN | P.SEV | P.SUS | PDPBMCC | |
|---|---|---|---|---|---|---|
| CAPD1 | 0.699 | 0.369 | 0.414 | 0.223 | 0.242 | 0.440 |
| CAPD2 | 0.787 | 0.348 | 0.570 | 0.183 | 0.203 | 0.598 |
| CAPD3 | 0.804 | 0.420 | 0.602 | 0.295 | 0.279 | 0.626 |
| CAPD4 | 0.706 | 0.378 | 0.444 | 0.311 | 0.267 | 0.524 |
| CAPD5 | 0.826 | 0.378 | 0.558 | 0.239 | 0.225 | 0.596 |
| CAPD6 | 0.804 | 0.464 | 0.519 | 0.288 | 0.299 | 0.598 |
| P.BAR1 | 0.357 | 0.721 | 0.255 | 0.359 | 0.390 | 0.255 |
| P.BAR2 | 0.458 | 0.817 | 0.342 | 0.439 | 0.428 | 0.304 |
| P.BAR3 | 0.391 | 0.792 | 0.258 | 0.562 | 0.567 | 0.249 |
| P.BAR4 | 0.324 | 0.716 | 0.198 | 0.500 | 0.561 | 0.167 |
| P.BEN1 | 0.558 | 0.350 | 0.716 | 0.227 | 0.209 | 0.454 |
| P.BEN2 | 0.525 | 0.292 | 0.742 | 0.192 | 0.181 | 0.431 |
| P.BEN3 | 0.547 | 0.291 | 0.822 | 0.173 | 0.178 | 0.536 |
| P.BEN4 | 0.539 | 0.259 | 0.834 | 0.120 | 0.122 | 0.552 |
| P.BEN5 | 0.497 | 0.185 | 0.740 | 0.106 | 0.070 | 0.524 |
| P.BEN6 | 0.511 | 0.301 | 0.817 | 0.272 | 0.212 | 0.594 |
| P.SEV1 | 0.257 | 0.452 | 0.200 | 0.805 | 0.511 | 0.220 |
| P.SEV2 | 0.199 | 0.443 | 0.100 | 0.753 | 0.494 | 0.149 |
| P.SEV3 | 0.167 | 0.348 | 0.129 | 0.653 | 0.375 | 0.138 |
| P.SEV4 | 0.351 | 0.532 | 0.264 | 0.666 | 0.486 | 0.295 |
| P.SEV5 | 0.203 | 0.337 | 0.128 | 0.661 | 0.418 | 0.180 |
| P.SUS1 | 0.349 | 0.499 | 0.227 | 0.530 | 0.787 | 0.248 |
| P.SUS2 | 0.220 | 0.493 | 0.127 | 0.538 | 0.844 | 0.167 |
| P.SUS3 | 0.274 | 0.436 | 0.128 | 0.422 | 0.711 | 0.255 |
| P.SUS4 | 0.157 | 0.469 | 0.146 | 0.483 | 0.711 | 0.104 |
| PDPBMCC1 | 0.575 | 0.334 | 0.456 | 0.326 | 0.293 | 0.728 |
| PDPBMCC2 | 0.637 | 0.297 | 0.526 | 0.251 | 0.188 | 0.819 |
| PDPBMCC3 | 0.644 | 0.268 | 0.545 | 0.203 | 0.211 | 0.868 |
| PDPBMCC4 | 0.563 | 0.226 | 0.558 | 0.192 | 0.168 | 0.830 |
| PDPBMCC5 | 0.584 | 0.225 | 0.637 | 0.167 | 0.174 | 0.844 |
| CAPD | P.BAR | P.BEN | P.SEV | P.SUS | PDPBMCC | |
|---|---|---|---|---|---|---|
| CAPD | 0.772 | |||||
| P.BAR | 0.510 | 0.763 | ||||
| P.BEN | 0.676 | 0.355 | 0.780 | |||
| P.SEV | 0.333 | 0.598 | 0.232 | 0.710 | ||
| P.SUS | 0.328 | 0.620 | 0.206 | 0.647 | 0.765 | |
| PDPBMCC | 0.735 | 0.330 | 0.666 | 0.278 | 0.252 | 0.819 |
| Hypo | Relationship | Std. Beta | Std. Error | T-value | p-Value | R2 | Decision |
|---|---|---|---|---|---|---|---|
| H1 | P. BEN  PDPBMCC PDPBMCC | 0.315 | 0.056 | 5.660 | 0.000 | 0.602 | Supported ** |
| H2 | P. BAR  PDPBMCC PDPBMCC | −0.134 | 0.052 | 2.581 | 0.005 | Supported ** | |
| H3 | CAPD  P. Threats P. Threats | 0.003 | 0.001 | 2.158 | 0.015 | Supported * | |
| H4 | CAPD  PDPBMCC PDPBMCC | 0.552 | 0.056 | 9.884 | 0.000 | Supported ** | |
| H5 | P.Threats  PDPBMCC PDPBMCC | 0.106 | 0.043 | 2.438 | 0.007 | Supported * | |
| Indirect Influence | |||||||
| H6 | P. SEV  PDPBMCC PDPBMCC | 0.060 | 0.025 | 2.435 | 0.007 | Supported * | |
| H7 | P. SUS  PDPBMCC PDPBMCC | 0.056 | 0.023 | 2.438 | 0.007 | Supported * | |
| Reference Number | Year | Main Issue | Contribution Type Facet | HBM Used. | PbD Used |
|---|---|---|---|---|---|
| [15] | 2009 | User’s computer security behaviors. | Model | Yes | No |
| [49] | 2010 | Computer security software. | Model | Yes | No |
| [50] | 2012 | Health information systems’ security. | Framework | Yes | No |
| [20] | 2014 | Information security behavior intentions. | Model | Yes | No |
| [19] | 2015 | Health Information System Security. | Model | Yes | No |
| [93] | 2016 | The reasons behind security breaches. | Model | Yes | No |
| [56] | 2017 | Cyber-safety activities. | Model | Yes | No |
| [92] | 2017 | Email security behaviors. | Model | Yes | No |
| [51] | 2019 | Security behaviors of employees. | Model | Yes | No |
| This study | 2020 | Privacy and Personal Data Protection in MCC | Framework | Yes | Yes |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alnajrani, H.M.; Norman, A.A. The Effects of Applying Privacy by Design to Preserve Privacy and Personal Data Protection in Mobile Cloud Computing: An Exploratory Study. Symmetry 2020, 12, 2039. https://doi.org/10.3390/sym12122039
Alnajrani HM, Norman AA. The Effects of Applying Privacy by Design to Preserve Privacy and Personal Data Protection in Mobile Cloud Computing: An Exploratory Study. Symmetry. 2020; 12(12):2039. https://doi.org/10.3390/sym12122039
Chicago/Turabian StyleAlnajrani, Hussain Mutlaq, and Azah Anir Norman. 2020. "The Effects of Applying Privacy by Design to Preserve Privacy and Personal Data Protection in Mobile Cloud Computing: An Exploratory Study" Symmetry 12, no. 12: 2039. https://doi.org/10.3390/sym12122039
APA StyleAlnajrani, H. M., & Norman, A. A. (2020). The Effects of Applying Privacy by Design to Preserve Privacy and Personal Data Protection in Mobile Cloud Computing: An Exploratory Study. Symmetry, 12(12), 2039. https://doi.org/10.3390/sym12122039





