Token-Based Access Control for IoT Based on Blockchain
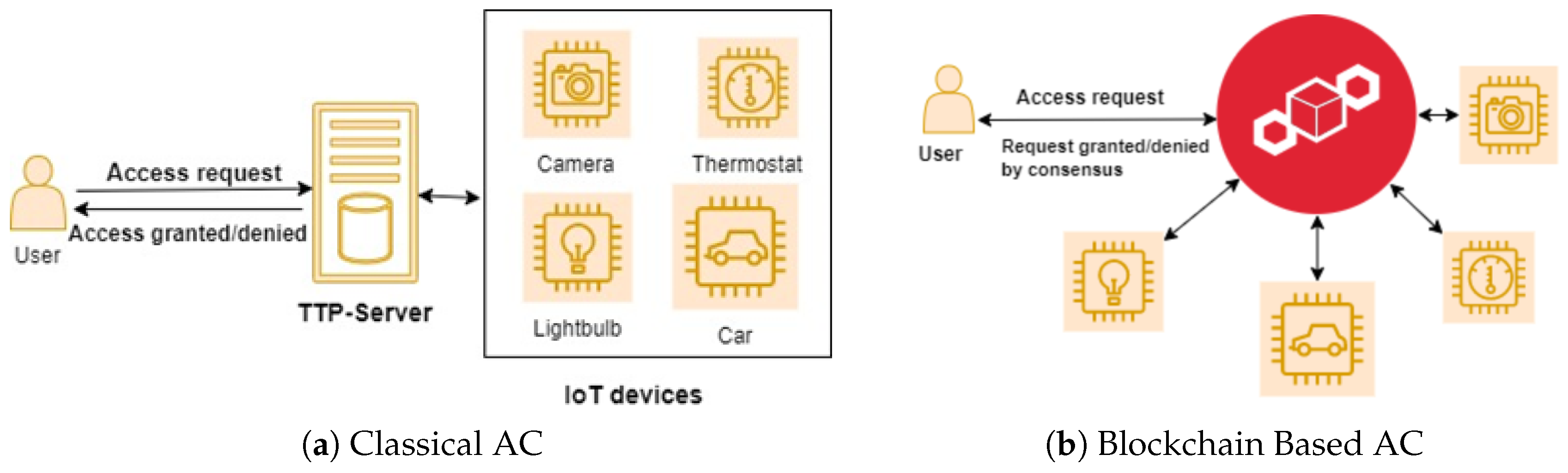
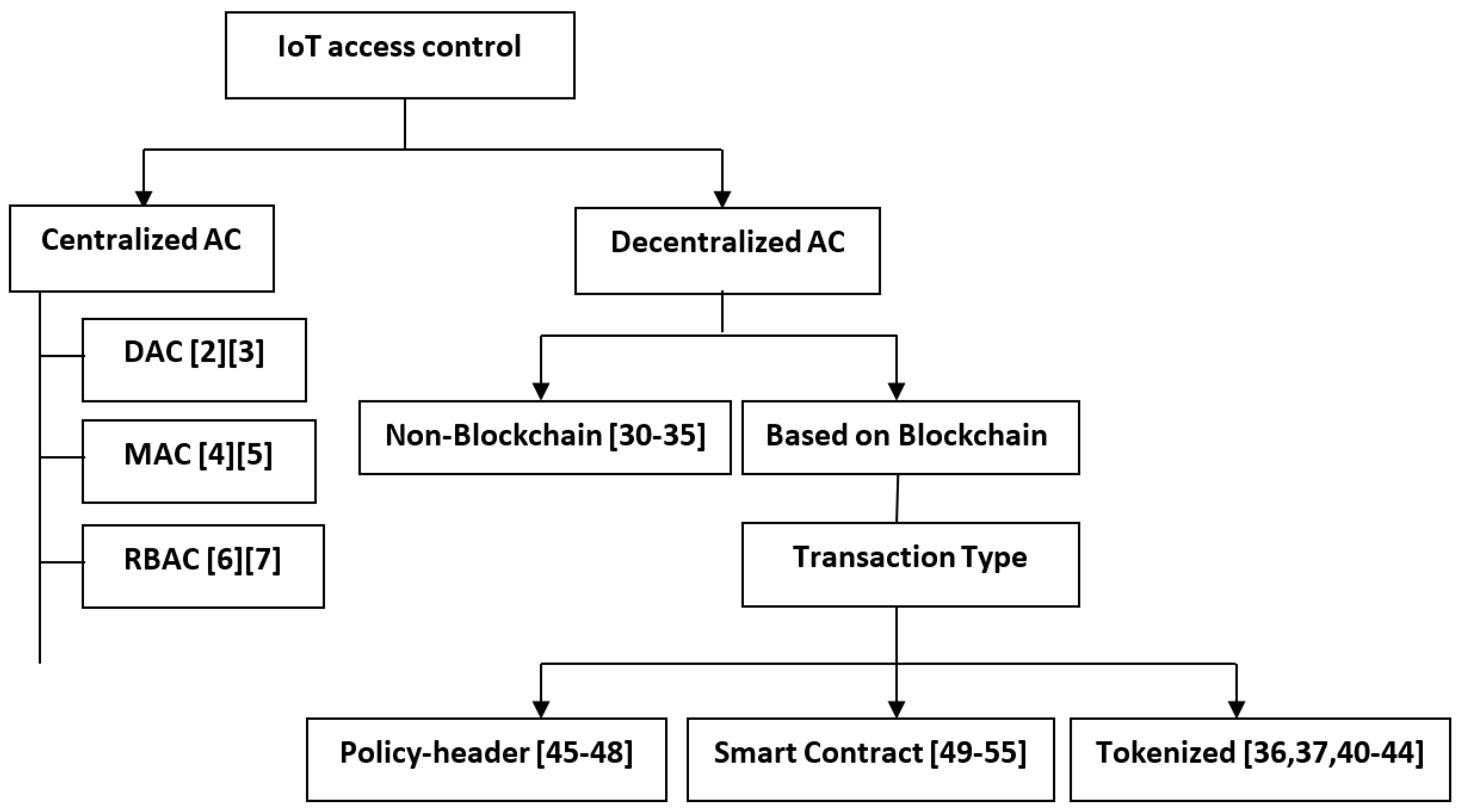
Tokenization can be defined as a digital signature that holds accessing privileges created by the owner of the object to his requestor, in order to allow access to a particular object based on his address. Therefore, a user without a token cannot access the owner’s resources. IoT access control based on tokenization with blockchain technology brings many benefits in IoT environments, such as decreasing communication costs with validating only once by utilizing a signature, and tokens can be represented in different access-control (AC) actions. In addition, blockchain technology facilitates the process of validating and verifying tokens by the IoT devices without a third party, which diminishes security issues, such as single point of failure as well as privacy preservation. Many researchers have mentioned IoT access control based on blockchain with the tokenized approach, so we illustrate and summarize with a comparison table of these approaches.
FairAccess [
36] presents a completely decentralized access control and authorization management structure for IoT devices. This proposed framework defines a token for authorization; therefore, the defined token as a digital signature serves as the authority permitting requesters to access a particular object based on their address. In fact, according to this proposed framework, the blockchain is represented as a database that keeps all access approach policies by combining pairs (target-object, requester) and forming transactions. In addition, it acts as a logging database, which guarantees auditing work. In the FairAccess system, the authorization token is used to provide access to the requester or receiver to a particular object based on its identification address. On the other hand, the smart contract is utilized by expressing the policies of access control as a scripting language. However, this framework has some drawbacks such as authorization through tokenization only and terminating a token or a new request for access must be communicated to the owner, which causes a delay. Furthermore, there is no integration between access control and legitimate relationship networks that features an enormous significance in a combinable and integrated IoT.
IoTChain [
37] is a fully decentralized access control architecture for IoT resources. The IoTChain architecture is the integration of the Object Security Architecture (OSCAR) framework [
38], which produces keys for users and sends them to owners to secure their resources. The Authentication and Authorization for Constrained Environments (ACE) structure [
39] is used to authorize requesters to access IoT resources. This proposed framework provides an end-to-end solution to authorize access to IoT resources securely. In the IoTChain approach, the owner of the resource defines access privileges in smart contracts, which self-execute to generate access tokens to the users when the required conditions are satisfied. A request is made by the client to the key server in order to join the blockchain network, and then it checks the client is authorized or not. When the client authorizes and receives group keys, then he downloads and decrypts the encrypted resources. However, the framework has some issues, such as low scalability, and assessment of its performance, as well as the fact that robustness requires implementing various applications over the IoTChain system.
Outchakoucht et al. [
40] proposed a framework for IoT access control, based on blockchain and machine learning algorithms. In this system, the resource owner defines the access control policies in the smart contract to control access to his resources. When a user sends a request to access a resource, the smart contract is automatically executed if the request meets certain conditions, and then it generates a token to the requestor for authorization. In addition, this system utilizes the blockchain to guarantee decentralized access control, while the reinforcement learning algorithm dynamically optimizes access policies. However, this framework is not implemented and does not demonstrate its feasibility for privacy and security testing.
Xue et al. [
41] presented an access management for smart homes based on private blockchain. In this system, the administrator has a smart home that identifies policies of access control and manages constrained devices, as well as authenticating visitors. A visitor initializes a transaction to access smart devices, and the administrator authenticates the visitor based on its stored public key, as well as checking his access rights based on the policy header of a private blockchain; when the transaction is validated, the administrator generates a token and key to the visitor to access the IoT devices in the home. In addition, the proposed solution accesses all records kept on the blockchain to avoid alteration, due to its immutability. Although the proposed solution enhances the security of accessing the smart home devices, its policies on access control are not self-enforced, and do not mention how to secure and trace outsourced data as off-blockchain storage.
Maesa et al. [
42] presented an access control mechanism based on blockchains, that produces policies as well as control access rights to resources. In this approach, the resource owner creates two different tokens based on Bitcoin transactions; the first is used to transfer access rights between subjects, while the second is used for updating or revoking policies credited to the owner. This framework stores the actual policies and user attributes in an external system, while the blockchain contains a link from that external system. The communication between the system components, such as external system, resource owner, and subjects, is based on the policy decision, which is either accept or reject. Policy outsourcing reduces space complexity in the blockchain, but does not benefit from blockchain features such as availability, security, or immutability. In addition, policy enforcement in this model is not self-executed.
BlendCAC [
43] is a capability-based access control system for the IoT, based on blockchains. In this model, the domain coordinator is a resource owner who defines policies and controls services and devices, while the cloud has globally controlled access policies and provides services. A user is a requester who wants to access a resource. A capability token is generated by the owner when receiving the user’s request, and then is stored in the smart contract as a new token. The cloud service provider decides on the user’s service request to provide access, or not, based on the token retrieved from the blockchain. Furthermore, this model permits only managers to do capability revocation. Although this framework provides distributed capability-based access control with scalability and light weight for the IoT, it is not deployed in real-world IoT applications as well, as it has a latency in its block validation process inherited from the utilized Ethereum platform.
Fotiou et al. [
44] proposed an IoT access management solution based on blockchains. In this model, the clients cannot interact directly with IoT devices or gateways, but can interact over the blockchain. A client needs to access IoT devices must have at least one token, while the increasing number of tokens that have clients means more access rights. In addition, the smart contract checks whether ot not the clients have the required number of tokens to invoke it, while the IoT gateways check the user’s role at the time, as well as resource location based on gateway access policies. The RPC servers allow clients and IoT devices to be aware of the events generated by a smart contract. This framework is implemented based on the Ethereum blockchain.
Table 4 shows a comparison of token-based access control approaches for the IoT. The approaches are compared in terms of access control model, blockchain type, transaction model, and other main features. These approaches employ tokenization access control to grant or revoke access to IoT resources by the requesters, based on the owner’s policy. However, these tokenization approaches are not automatically executing policies of access control to enforce it. In addition, some of these frameworks can authorize through tokenization only, and terminating a token or requesting new access must communicate that to the owner, which causes latency. To overcome transaction latency for tokenization access control approaches in IoT systems, the policies of the access control may be built on a smart contract, which automatically executes the policies to control access rights and detect unwanted activities.
Table 4.
A Comparison Table of Token-Based Access Control Approaches.
Table 4.
A Comparison Table of Token-Based Access Control Approaches.
| Reference | Access Model | Blockchain Type | Transaction-Model | Main Features Utilized |
|---|
| FairAccess [36] | Attribute-based AC | Public | Token/Smart contract | - -
It uses Wallets to broadcast a user’s transaction in the P2P network. - -
Pseudonymous technique is used to ensure the privacy of the users.
|
| IoTChain [37] | ACE Authorization model | Private | Token/Smart contract | - -
It uses the ACE model for authentication. - -
It utilizes the OSCAR model for end-to-end security.
|
| Outchakoucht et al. [40] | General-AC | Public | Token/Smart contract | - -
Reinforcement learning algorithm gives dynamic and auto-re-adjust policies for access control.
|
| Xue et al. [41] | General-AC | Private | Token | - -
Access policies stores in the blockchain header as policy file that allows the owner to check access privileges of the visitors.
|
| Maesa et al. [42] | Attribute-based AC | Public | Token | - -
It is used for the implementation by XACML policy model. - -
It utilizes Policy Administration Point (PAP) and Policy Enforcement Point (PEP) to enforce AC policies with blockchain.
|
| BlendCAC [43] | Capability-based AC | Private | Token/Smart contract | - -
It used a JSON model for implementing tokens and certificates.
|
| Fotiou et al. [44] | Role-based AC | Public | Token/Smart contract | - -
It used ERC20 standard based on Ethereum to implement token-based access control.
|
Smart Contract-Based Access Control for IoT Based on Blockchain
A smart contract is a set of executable codes that automatically enforces agreements or terms and conditions between parties. The main benefit of utilizing a smart contract to access management in IoT systems is that the policies of AC are enforced automatically by the smart contract, as well as offering high computing capability to reach numerous access management methods.
Novo [
49] is a fully decentralized access management program in IoT-based blockchain technology. This solution excludes IoT devices from the blockchain to overcome network overheads. In addition, this framework has managers, management hubs, and agent node entities, while the managers are responsible for defining new policies in the architecture, as well as interacting with the smart contract to decide to register or de-register. Moreover, the management hubs can request permission on behalf of the IoT devices from the blockchain, by utilizing the call method. The agent node is responsible for deploying smart contracts in the framework. This framework utilized a single smart contract to cover all processes. When a request is received from IoT devices, the gateway nodes or management hubs send an access request to the blockchain network on behalf of the constrained devices and then, the smart contract checks and broadcasts it on the blockchain network for approval. Lastly, IoT devices receive permission or rejection to access the resource. Although this proposed architecture gains scalability due to distributing query permissions through management hubs, the proposed architecture will face security issues if the manager is malicious.
In terms of using various smart contracts to create an IoT access control, Zhang et al. [
50] introduced an IoT access control solution based on the smart contract. The framework contains three different contracts. In multiple access control contract (ACC), every point of this ACC can give a single function of access control to the subject-object pair. Judge contract (JC) is a detector and judge of misbehavior of ACC subjects. Register contract (RC) is responsible for maintaining ACC, as well as functions of misbehavior penalties. Furthermore, IoT gateways represent its IoT devices to request a resource, as well as enforcing AC policies that are well-defined in the smart contract. The access request will be granted if required conditions are met and there is no detected misbehavior. Nonetheless, as it is not deployed in the real world, IoT systems were not stress-tested to evaluate their feasibility.
Huang et al. [
51] presented a secure IoT data transferring approach based on the blockchain. The framework has a management layer that consists of three different contracts. Access contract is responsible for providing trusted access control to the data based on capability access control. Communication contracts are responsible for traceability and storing all transactions for data transfers in the IoT. Auto exchange contracts are responsible for sending permission rights to the requester after authorization. In this platform, the requester or data demander sends an access request to the smart contract. If the requester meets the required conditions, the smart contract automatically executes and grants access; otherwise, the request will be denied. However, this framework has latency because of the use of the Ethereum platform.
Huh et al. [
52] proposed an IoT device management solution utilizing the Ethereum platform. They used a smart contract to control the constrained devices, while using a public key system on the smart contract for authentication. In this system, they used a meter contract for storing electricity, while the policy contract defines the policies of IoT devices. Moreover, the IoT devices are responsible for changing their normal mode to an energy-saving mode if they meet a predefined specified policy. Authenticating the user requires matching with his public key, while all users’ public keys are stored on the smart contract. So, if an unauthenticated user tries to access data, it would be detected and rejected easily. However, there are some issues, such as the used platform not supporting light clients and suffering transaction latency.
Using the smart contracts with multi-layered blockchains for IoT access management has the benefit of separating the responsibilities of constrained devices to overcome the public visibility of the blockchain.
Ali et al. [
53] developed a decentralized access control mechanism for IoT-based blockchains. This solution is a multi-layered blockchain architecture. In order to access resources, a requester must authenticate by consortium blockchain to allow or deny accessing the sidechain’s resources. On the other hand, the sidechain is responsible for keeping track of the data events created by IoT devices. In this framework, they used the smart contract concept to self-enforce policies of access control on consortium layer as well as the sidechain, and it also utilized peer-to-peer IPFS storage to overcome the issue of centralized authority over IoT data handling. However, it did not stress-test various cases to evaluate feasibility, and it has a transaction latency due to the platform used.
Jiang et al. [
54] proposed a cross-chain architecture based on multilayer blockchains for decentralized access IoT management. The framework utilized a consortium blockchain to secure access to the whole system, while sidechains (Tangle) record IoT data creation events. In order to access the resource of IoT clusters, the user’s public key must first be stored in the smart contract of the consortium network, then signing its private key to be verified. The requester can get an encrypted file if authenticated successfully; otherwise, the request will be denied. The authors implemented access management policies on smart contract of the consortium blockchain, while smart contracts of the sub-tangles grantees to store IoT data creation events securely, as well as allowing communication only with authenticated devices. However, the use of the Byzantine fault tolerance (BFT) consensus mechanism causes some issues like network overhead. In addition, this solution does not address privacy protection for the users.
Jo et al. [
55] presented a structural health monitoring system for IoT, based on a hybrid blockchain. This framework consists of two networks; the core network is responsible for mining nodes as well as utilizing a PoW consensus algorithm for verification, while the nodes of the edge network are responsible for access management and identification of the participants. In this solution, any participants with a key and signature can join the network. In addition, the terms and policies are implemented in the smart contract to self-execute in order to make decisions based on a predefined specific value that enables managing reactions or creating alerts. However, there is latency in the block mining process, due to the used consensus mechanism.
Smart contract-based access control in IoT would provide security and reliability in terms of accessing resources, as well as controlling and storing all transactions in the IoT systems, and it provides self-enforcing policies in the access control system.
Table 5 summarizes a comparison of the smart contract-based access controls approaches to IoT. The approaches are compared in terms of access control model, consensus mechanism, blockchain platform, and other main features. In addition, using a blockchain platform and consensus mechanisms can affect the IoT system performance. For example, PoW is not suitable for the limited resources of IoT devices, due to its low transaction and high computation cost. The smart contract-based AC approaches mostly achieve their aim of protecting IoT data and devices, but still may have some drawbacks, such as transaction latency, scalability, and privacy issues.
Table 5.
A Comparison Table of Smart Contract-Based Access Control Approaches.
Table 5.
A Comparison Table of Smart Contract-Based Access Control Approaches.
| Reference | Access Model | Consensus Mechanism | Blockchain Platform | Main Features Utilized |
|---|
| Novo [49] | General AC | PoW | Ethereum | - -
Excluded IoT devices from blockchain network. - -
Manager enables to register IoT devices and verify it.
|
| Zhang et al. [50] | Attribute-based AC | PoW | Ethereum | - -
Used three different smart contracts: ACCs, JC and RC. - -
Access-control method based on a pair (subject, object).
|
| Jo et al. [55] | General-AC | PoW | Ethereum | - -
Used two-tiered blockchain architecture. - -
Used two types of smart contracts main-contract and sub-contract.
|
| Jiang et al. [54] | General-AC | BFT | Hyperledger fabric and IOTA Tangle | - -
Used consortium blockchains as main controller part and Multiple blockchain for IoT clusters. - -
Off-chain IPFS for P2P storage.
|
| Ali et al. [53] | General-AC | PoW and Tendermint | Ethereum and Monax | - -
Multi-tiered blockchain architecture. - -
Distributed IPFS storage.
|
| Huh et al. [52] | General-AC | PoW | Ethereum | - -
RSA cryptographic system for generating keys. - -
Used Ethereum account as constrained devices.
|
| Huang et al. [51] | Capability-based AC | PoW | Ethereum | - -
Data Access Ticket (DAT) allows user to access data.
|