3.3. Registration Phase
In this phase, each smartphone user needs to install an application dependent on the proposed protocol. At the point when the application has been completely installed, the user needs to perform registration through a secure channel such as TLS. The object of registration is to exchange {KN-S, DKN-S, mN-S}, {KN-P, DKN-P, mN-P}, {KN-TP, DKN-TP, mN-TP}, and {KN-V, DKN-V, mN-V} between the N and S, between N and P, between N and TP, and between N and V through the secure channel such as TLS. The details of the registration phase are shown as follows:
Both N and S can create a set of session keys, SK
N-Sj, where j = 1, …, m
N-S, by using the session key creation technique described in [
13].
Both N and P can create a set of session keys, SK
N-Pj, where j = 1, …, m
N-P, by using the session key creation technique described in [
15]. Both N and TP can create a set of session keys, SK
N-TPj, where j = 1, …, m
N-TP, by using the session key creation technique described in [
13].
Both N and V can create a set of session keys, SK
N-Vj, where j = 1, …, m
N-V, by using the session key creation technique described in [
13].
3.4. Authentication Phase
In this phase, the proposed protocol provides authentication between N and P, between N and S through P, and between P and S. Note that P communicates with an NFC reader through a secure channel. From
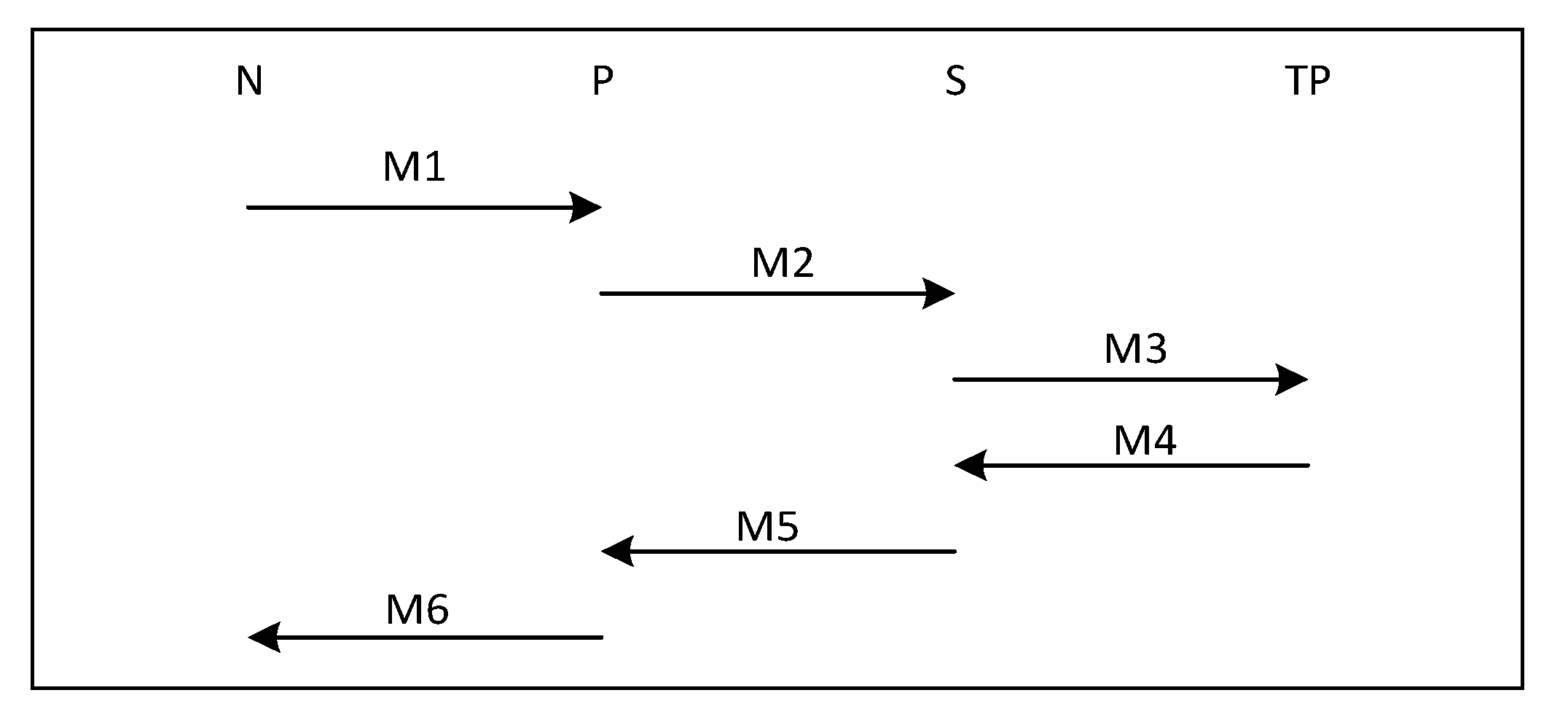
Figure 1 displays the transaction flow of authentication protocol of all parties, including N, P, S and TP.
- M1:
N → P: IDN, T1, request, h(IDN, T1, Request, SKN-Sj), h(IDN, T1, request, h(IDN, T1, request, SKN-Sj), {hN-TP}SKN-TPj, SKN-Pj), {hN-TP}SKN-TPj
- M2:
P → S: IDN, IDP, T1, request, h(IDN, T1, request, SKN-Sj), h(IDP, h(IDN, T1, request, SKN-Sj), SKP-Sj), {hN-TP}SKN-TPj, {hP-TP}SKP-TPj
- M3:
S → TP: {hN-TP}SKN-TPj, {hP-TP}SKP-TPj, {hS-TP}SKS-TPj
- M4:
TP → S: {h(hN-TP, hP-TP, hS-TP)}SKN-TPj+1, {h(hN-TP, hP-TP, hS-TP)}SKP-TPj+1, {h(hN-TP, hP-TP, hS-TP)}SKS-TPj+1
- M5:
S → P: T2, response, h(T1, T2, response, SKN-Sj+1), h(h(T1, T2, response, SKN-Sj+1), SKP-Sj+1), {h(hN-TP, hP-TP, hS-TP)}SKN-TPj+1, {h(hN-TP, hP-TP, hS-TP)}SKP-TPj+1
- M6:
P → N: T2, response, h(T1, T2, response, SKN-Sj+1), h(h(T1, T2, response, SKN-Sj+1), {h(hN-TP, hP-TP, hS-TP)}SKN-TPj+1, SKN-Pj+1), {h(hN-TP, hP-TP, hS-TP)}SKN-TPj+1
N sends an authentication request message M1 to P which contains the following: h(IDN, T1, Request, SKN-Sj): the hash value is considered as a message authentication code (MAC), which is an authentication token between N and S, which will be transmitted to S through P, and ensures the integrity of the message. This message P cannot generate since P does not know the session key SKN-Sj. Hence, only N constructs this message. h(IDN, T1, Request, h(IDN, T1, Request, SKN-Sj), {hN-TP}SKN-TPj, SKN-Pj): the hash value is considered as a MAC, which is an authentication token between N and P, and ensures the integrity of the message. Moreover, this message P uses to verify the authenticity of N. N cannot deny that it did not originate this message as the possession of both SKN-Sj and SKN-Pj. {hN-TP}SKN-TPj: the message encrypted with the session key SKN-TPj shared between N and TP, which will be transmitted to TP through S. This message P cannot generate because P does not know the session key SKN-TPj. Therefore, N is original of this message. Note that T1 is generated by N to prevent replay attack.
On receiving message M1 from N, P will verify the authentication request message h(IDN, T1, request, h(IDN, T1, request, SKN-Sj), {hN-TP}SKN-TPj, SKN-Pj) of N, if the message is invalid, P rejects N’s request. If not, P forwards N’s authentication request to S in the message M2. P sends message M2 to S. It contains the following: h(IDP, h(IDN, T1, request, SKN-Sj), SKP-Sj): the hash value is considered as a MAC, which is an authentication token between P and S, and ensures the integrity of the message. Besides, this message S uses to verify the authenticity of P. {hP-TP}SKP-TPj: the message encrypted with the session key SKP-TPj shared between P and TP which will be transmitted to TP through S. This message S cannot generate because S does not know the session key SKP-TPj. Therefore, P is original of this message.
On receiving the message M2 from P, S will check the correctness of the authentication request message h(IDP, h(IDN, T1, request, SKN-Sj), SKP-Sj) of P, if the message is invalid, S rejects P’s request. If not, S will check the correctness of authentication request message h(IDN, T1, request, SKN-Sj) of N. If the message is successful, S sends response message back to N and P. Otherwise, S rejects P’s request. Then, S sends the message M3 to TP.
On receiving message M3 from S, TP will process three things: TP decrypts the message {hN-TP}SKN-TPj using SKN-TPj keeps the hash value, decrypts the message {hP-TP}SKP-Sj using SKP-TPj, keeps the hash value, decrypts the message {hS-TP}SKS-TPj using SKS-TPj keeps the hash value. Next, TP encrypts three hash values, encrypts the hash value of hN-TP, hP-TP, hS-TP using SKN-TPj+1. Encrypts the hash value of hN-TP, hP-TP, hS-TP using SKP-TPj+1. Encrypts the hash value of hN-TP, hP-TP, hS-TP using SKS-TPj+1. Then, TP sends messages M4 to S.
On receiving the message M4 from TP, S decrypts the message {h(hN-TP, hP-TP, hS-TP)}SKS-TPj+1 with SKS-TPj+1 and keeps the hash value as proof if a dispute arises. Then, S sends messages M5 to P. The message M5 contains the following: h(T1, T2, response, SKN-Sj+1): the hash value is considered as a message as MAC, which is an authentication token between N and S which will be transmitted to N through P, and ensures the integrity of the message. This message P will not generate since P does not know the session key SKN-Sj+1. Hence, only S constructs this message. h(h(T1, T2, response, SKN-Sj+1), SKP-Sj+1): the hash value is considered as MAC, which is an authentication token between P and S, and ensures the integrity of the message. Moreover, the message P uses to verify the authenticity of S. S cannot deny that it did not originate this message as the possession of both SKN-Sj+1 and SKP-Sj+1. {h(hN-TP, hP-TP, hS-TP)}SKN-TPj+1: this message will forward to N via P. {h(hN-TP, hP-TP, hS-TP)}SKP-TPj+1: this message will send to P.
On receiving the message M5 from S, P will verify the authentication response message h(h(T1, T2, response, SKN-Sj+1), SKP-Sj+1) of S, if the message is invalid, P rejects S’s response. Unless, P decrypts the message {h(hN-TP, hP-TP, hS-TP)}SKP-TPj+1 and keeps the hash value as proof if a dispute arises. Then, P sends the message M6 to N.
On receiving the message M6 from P, N will verify the authentication result message h(h(T1, T2, response, SKN-Sj+1), {h(hN-TP, hP-TP, hS-TP)}SKN-TPj+1, SKN-Pj+1) of P, if the message is invalid, N rejects P’s response. Unless, N will verify the authentication result message h(T1, T2, Yes/No, SKN-Sj+1) of S, if the message is invalid, N rejects P’s response. If not, N decrypts the message {h(hN-TP, hP-TP, hS-TP)}SKN-TPj+1 with SKN-TPj+1 and keeps the hash as proof if a dispute arises. Note that T2 is generated by S to prevent a replay attack.
It can be seen that N with S via P can provide mutual authentication for all engaged parties. Each message in this protocol can be used to identify the sender and the recipient of the message. Thus, our protocol ensures mutual authentication for N, P, and S. This protocol contains only symmetric cryptographic operations, MAC and a hash function, which leads to lightweight operations. Therefore, it is appropriate for NFC communications. Additionally, using a secure offline session key generation technique will enhance the security of the protocol.
3.5. Dispute Resolution Phase
There are two sub-phases: N requests dispute, and P requests dispute. After the transaction is complete, if N or P is not satisfied with the transaction, N or P can request a dispute resolution to V, the dispute resolution protocol. Consider the protocols below:
3.5.1. N Requests Dispute
N sends the hash value h(h
N-TP, h
P-TP, h
S-TP) of the transaction to V. Upon receiving the hash value of N, V sends the requested hash value of the TP. After receiving the hash value from the TP, V compares the hash value of N with the hash value from the TP. If the hash values do not match, V rejects N’s request; if not, V sends a notification of dispute resolution to P and S. From
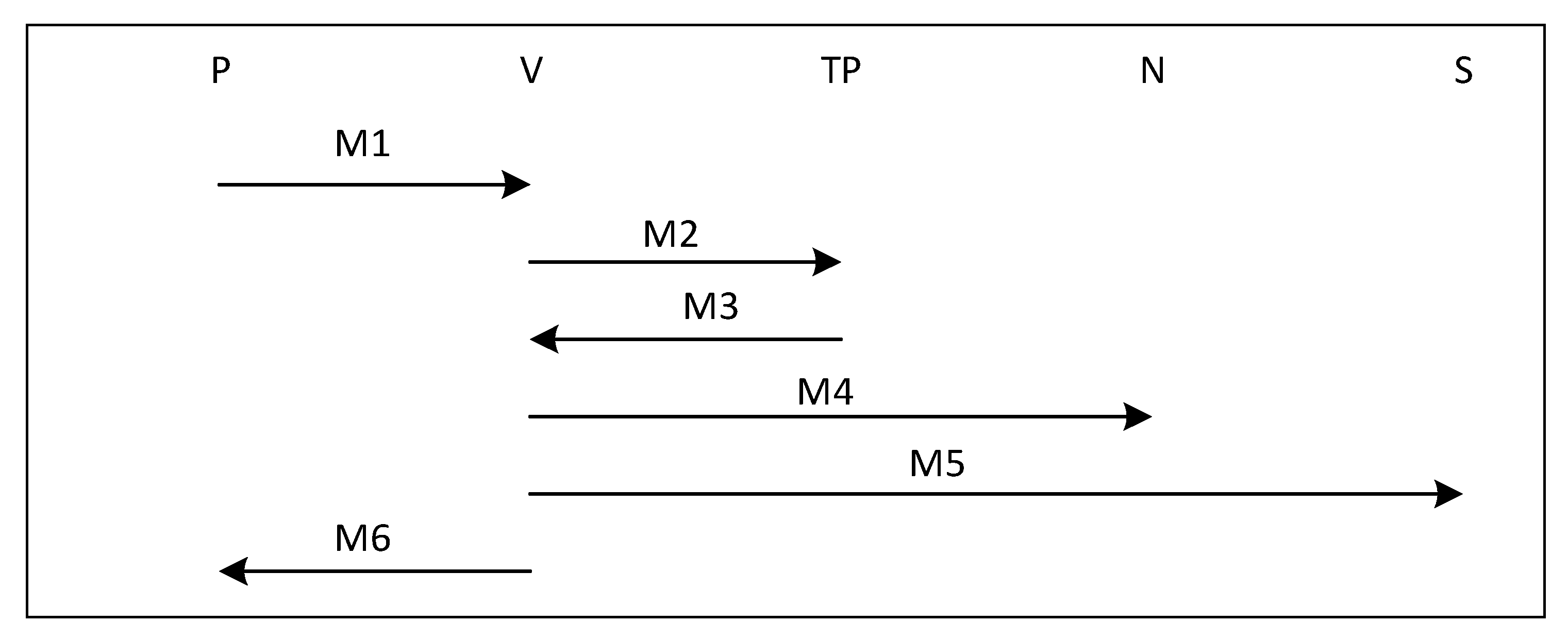
Figure 2 shows transaction flow of N request dispute protocol of all parties including N, P, S, V and TP. The details of this protocol are outlined below.
M1: N → V: {h(hN-TP, hP-TP, hS-TP)}SKN-Vj
M2: V → TP: {h(hN-TP, hP-TP, hS-TP)}SKV-TPj
M3: TP → V: {h(hN-TP, hP-TP, hS-TP)}SKV-TPj+1
M4: V → P: {h(hN-TP, hP-TP, hS-TP)}SKP-Vj
M5: V → S: {h(hN-TP, hP-TP, hS-TP)}SKS-Vj
M6: V → N: {h(hN-TP, hP-TP, hS-TP)}SKN-Vj+1
3.5.2. P Requests Dispute
P sends the hash value h(h
N-TP, h
P-TP, h
S-TP) of the transaction to V. Upon receiving the hash value of P, V sends the requested hash value of the TP. After receiving the hash value from the TP, V compares the hash value of N with the hash value from the TP. If the hash values do not match, V rejects P’s request; if not, V sends a notification of dispute resolution to N and S.
Figure 3 shows the transaction flow of P request dispute protocol of all parties including N, P, S, V and TP. The details of this protocol are outlined below.
M1: P → V: {h(hN-TP, hP-TP, hS-TP)}SKP-Vj
M2: V → TP: {h(hN-TP, hP-TP, hS-TP)}SKV-TPj
M3: TP → V: {h(hN-TP, hP-TP, hS-TP)}SKV-TPj+1
M4: V → N: {h(hN-TP, hP-TP, hS-TP)}SKN-Vj
M5: V → S: {h(hN-TP, hP-TP, hS-TP)}SKS-Vj
M6: V → P: {h(hN-TP, hP-TP, hS-TP)}SKP-Vj+1