MICKEY 2.0.85: A Secure and Lighter MICKEY 2.0 Cipher Variant with Improved Power Consumption for Smaller Devices in the IoT
Abstract
1. Introduction
- We propose a new MICKEY 2.0 cipher variant, called MICKEY 2.0.85. This variant has been tested for pseudo-randomness, which, to the best of our knowledge, has never been done before.
- We presented a reduction method for MICKEY 2.0, which resulted in fewer GES for MICKEY 2.0.85.
- We propose a new variant (MICKEY 2.0.85), which is 23% faster and consumes 16% less power than MICKEY 2.0 while maintaining similar pseudo-randomness test results.
- We performed two common cryptanalysis processes, each of which shows the lighter variant to be at least as resistant to attacks as its less efficient predecessor.
2. Background
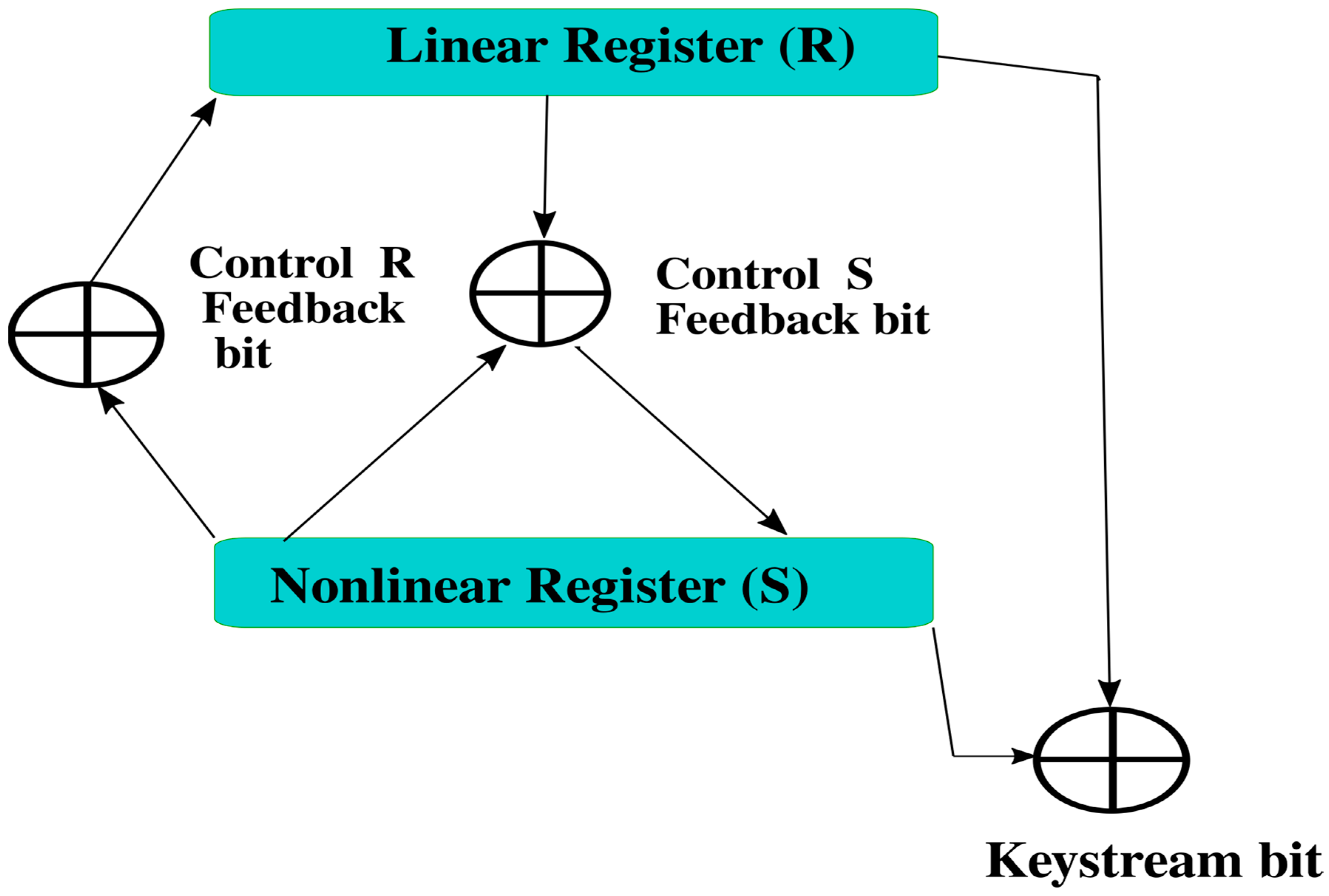
2.1. MICKEY 2.0 Family of Ciphers
2.2. MICKEY Algorithm Keystream Generation
2.3. Algorithm Overview
2.4. Internal State: Data Structure Details
3. Methods
- By reducing the number of bits for both registers, the number of gates (XOR, AND, and MUX) will be reduced given that the number of iterations within the loops will decrease. Therefore, the cipher will have less GEs.The reduction methods should be implemented carefully because they affect the security due to their effect on the pseudo-randomness for the generated keystream.The bits removed from each register were selected, and pseudo-randomness tests were performed.
- NIST randomness consisting of a 15-test suite is a standard statistical test that can be implemented on the keystream generated by the targeted cipher to evaluate the cipher strength. The comparison of these results with existing and popular ciphers is an important measurement to provide a good indicator that the proposed ciphers are sufficient for use.
- The cipher performance in terms of encryption speed was tested by running the cipher 10 times and calculating the average speed.
4. Related Work
5. Algorithm Reduction Methodology
5.1. Reduction Optimal Setting
5.1.1. Overview
5.1.2. Internal State Drivers
6. Results and Analysis
6.1. NIST Randomness Test Suite
6.2. Algorithm Performance Testing
- Measured the start time,
- Initialized and encrypted the plaintext string,
- Measured the end time,
- Calculated the difference.
6.3. Power Consumption Comparison
7. Cryptanalysis
7.1. Repeated Key AKA Many Time Pad Attack
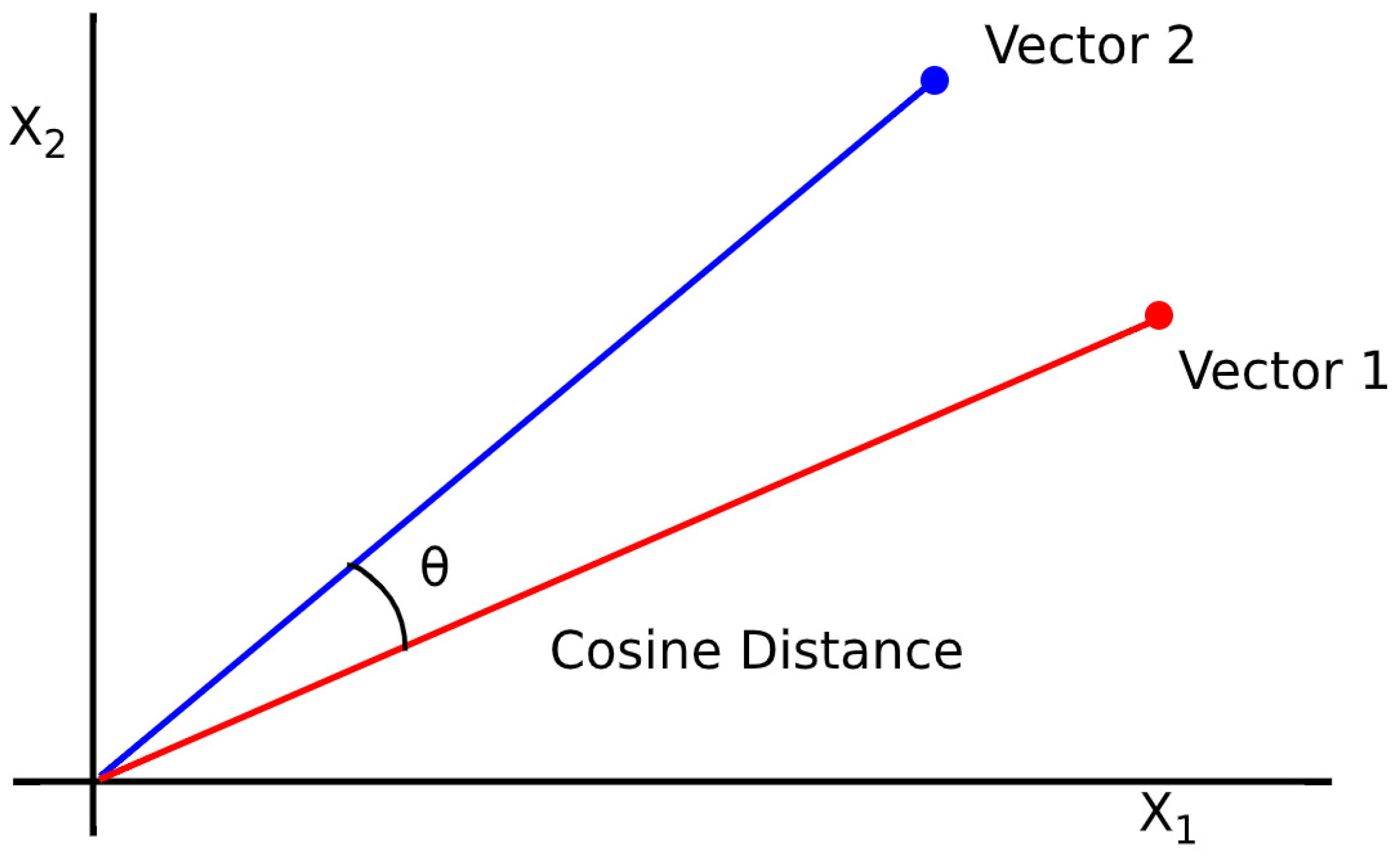
7.2. Cosine Similarity Analysis
8. Discussion
9. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
Appendix A. How GEs Are Counted
| Gate | Number of Gate Equivalents |
|---|---|
| NOT | 1 |
| AND | 2 |
| OR | 2 |
| XOR | 3 |
| NAND | 1 |
| NOR | 1 |
| XNOR | 3 |
| MUX | 3 |
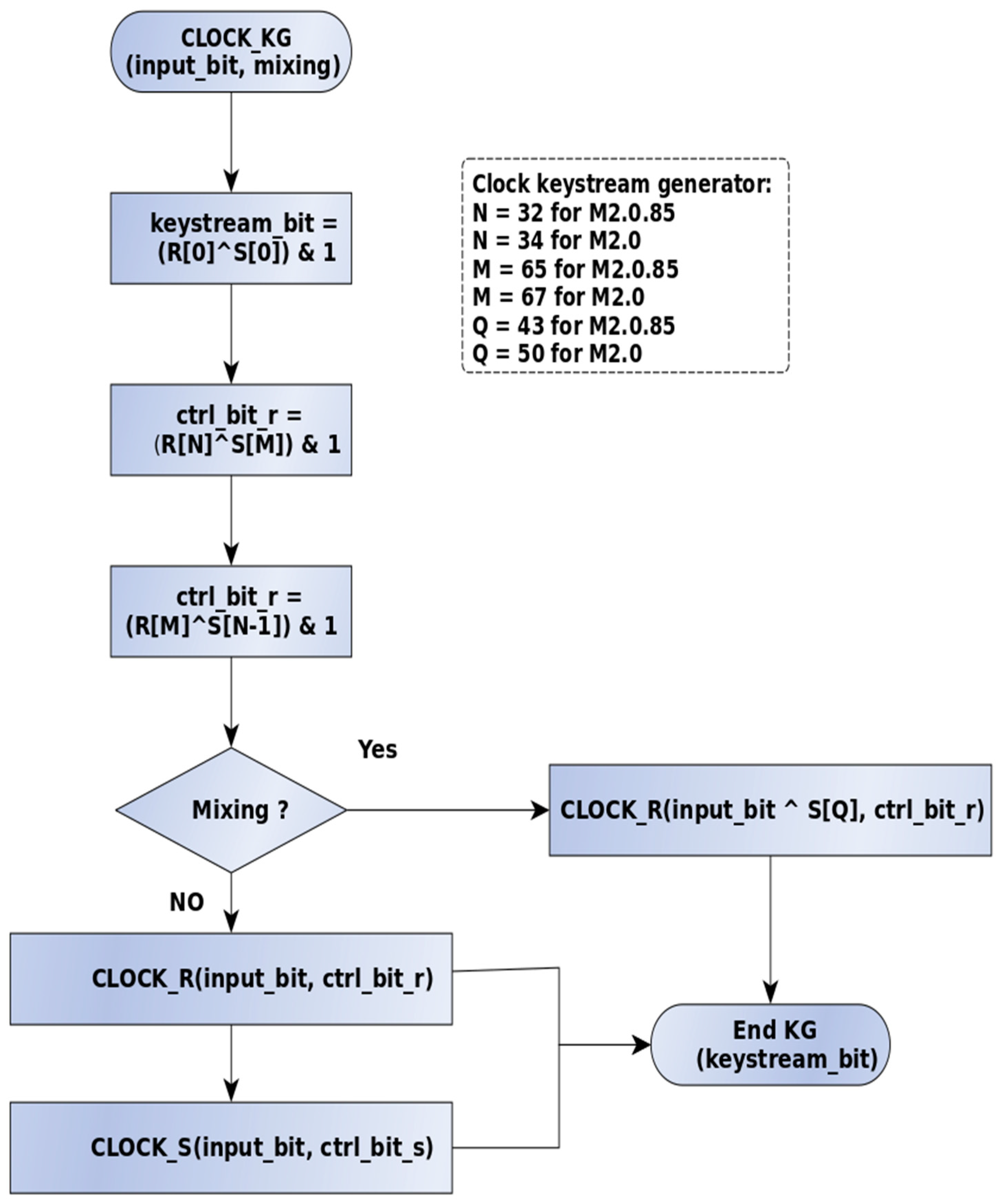
- Initialize the internal state using: IV, key, and CLOCK_KG (which uses CLOCK_R and CLOCK_S) to mix in the IV and KEY bits based on the internal driver structures(R_MASK and COMP0, COMP1, FB0, FB1)
- For each bit in the message invoke CLOCK_KG
- a
- CLOCK_KG invokes CLOCK_R, which advances the linear bit and masks it with R_MASK to determine its final value.
- b
- CLOCK_KG also invokes CLOCK_S, which may or may not advance the nonlinear bit depending on the linear position and the values of (COMP0, COMP1, FB0, and FB1)
- c
- CLOCK_KG determines the keystream bit by XORing the current linear and nonlinear registers and ANDs them with 1.
- d
- Ciphertext Generation: The current plaintext message bit is XORed with the current Keystream bit, which becomes the ciphertext output.
Appendix B. GE Comparison between MICKEY Family Algorithms
| Function | Operation | GE Multiplier | MICKEY 2.0 Count | MICKEY 2.0.85 Count | ||
|---|---|---|---|---|---|---|
| Number | GE | Number | GE | |||
| CLOCK_R | XOR | 3 | 401 | 1203 | 341 | 1023 |
| MUX | 3 | 2 | 6 | 2 | 6 | |
| CLOCK_S | XOR | 3 | 400 | 1200 | 340 | 1020 |
| AND | 2 | 100 | 200 | 85 | 170 | |
| MUX | 3 | 2 | 6 | 2 | 6 | |
| CLOCK_KG | XOR | 3 | 4 | 12 | 4 | 12 |
| ECRYPT_IVs setup | MUX | 3 | 160 | 480 | 160 | 480 |
| Encrypt_process | MUX | 3 | 8 | 24 | 8 | 24 |
| Total GE | 3131 | 2741 | ||||
References
- Babbage, S.; Dodd, M. The stream cipher MICKEY 2.0, ECRYPTStream Cipher, EU ECRYPT Netw., Denmark, U.K., Tech. Rep., 2006. Available online: https://www.ecrypt.eu.org/stream/index.html (accessed on 10 October 2019).
- Rukhin, A.; Soto, J.; Nechvatal, J.; Smid, M.; Barker, E. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; Booz-Allen and Hamilton Inc.: Mclean, VA, USA; Tysons Corner, VA, USA, 2001. [Google Scholar]
- NIST. Announcing the Advanced Encryption Standard (AES); Federal Information Processing Standards Publication: Gaithersburg, MA, USA, 2001; Volume 197, p. 33.
- Biryukov, A. The Design of a Stream Cipher LEX. In Proceedings of the International Workshop on Selected Areas in Cryptography, Montreal, QC, Canada, 17–18 August 2006; Springer: Berlin/Heidelberg, Germany, 2006; pp. 67–75. [Google Scholar]
- Maitra, S.; Yelamarthi, K. Rapidly Deployable IoT Architecture with Data Security: Implementation and Experimental Evaluation. Sensors 2019, 19, 2484. [Google Scholar] [CrossRef] [PubMed]
- Rangra, A.; Sehgal, V.K.; Shukla, S. A Novel Approach of Cloud Based Scheduling Using Deep-Learning Approach in E-Commerce Domain. Int. J. Inf. Syst. Model. Des. (IJISMD) 2019, 10, 59–75. [Google Scholar] [CrossRef]
- Chakraborty, R.S.; Mathew, J.; Vasilakos, A.V. Security and Fault Tolerance in Internet of Things; Springer International Publishing: Berlin/Heidelberg, Germany, 2019. [Google Scholar]
- Randhawa, R.H.; Hameed, A.; Mian, A.N. Energy efficient cross-layer approach for object security of CoAP for IoT devices. Ad Hoc Netw. 2019, 92, 101761. [Google Scholar] [CrossRef]
- Zhang, S.; Chen, G. Micro-Trivium: A lightweight algorithm designed for radio frequency identification systems. Int. J. Distrib. Sens. Netw. 2017, 13. [Google Scholar] [CrossRef]
- Rezvani, B.; Diehl, W. Hardware Implementations of NIST Lightweight Cryptographic Candidates: A First Look; Report 2019/824; Cryptology ePrint Archive: Blacksburg, VA, USA, 2019. [Google Scholar]
- Aagaard, M.D.; Sattarov, M.; Zidaric, N. Hardware design and analysis of the ACE and WAGE ciphers. arXiv 2019, arXiv:1909.12338. [Google Scholar]
- Babbage, S.; Dodd, M. The Stream Cipher MICKEY (Version 1); ECRYPT Stream Cipher Project Report, 2006. Available online: https://www.ecrypt.eu.org/stream/ciphers/mickey/mickey.pdf (accessed on 10 October 2019).
- Kaeslin, H. Digital Integrated Circuit Design: From VLSI Architectures to CMOS Fabrication; Cambridge University Press, University Printing House: Cambridge, UK, 2008. [Google Scholar]
- Xilinx. Xilinx Power Estimator (XPE). Available online: https://www.xilinx.com/products/technology/power/xpe.html (accessed on 12 October 2019).
- Verma, G.; Khare, V.; Kumar, M. More precise FPGA power estimation and validation tool (FPEV_tool) for low power applications. Wirel. Pers. Commun. 2019, 106, 2237–2246. [Google Scholar] [CrossRef]
- Katagi, M.; Moriai, S. Lightweight Cryptography for the Internet of Things; Sony Corporation: Tokyo, Japan, 2008; pp. 7–10. Available online: http://dx.doi.org/10.1016/j.istr.2012.10.005 (accessed on 12 October 2019).
- Preneel, B. Stream Ciphers: Past, Present and Future; ISCISC, 2010. Available online: https://securewww.esat.kuleuven.be/cosic/publications (accessed on 12 October 2019).
- Dunkelman, O.; Keller, N. A New Attack on the LEX Stream Cipher. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Melbourne, Australia, 7–11 December 2008; Springer: Berlin/Heidelberg, Germany, 2008; pp. 539–556. [Google Scholar]
- ECRYPT II. The eSTREAM Portfolio. Available online: http://www.ecrypt.eu.org/stream (accessed on 6 August 2019).
- Liu, Y.; Shi, Y.; Gu, D.; Dai, B.; Zhao, F.; Li, W.; Liu, Z.; Zeng, Z. Improved impossible differential cryptanalysis of large-block Rijndael. Sci. China Inf. Sci. 2019, 62, 32101. [Google Scholar] [CrossRef]
- Leander, G.; Paar, C.; Poschmann, A.; Schramm, K. New Lightweight DES Variants. In Proceedings of the Fast Software Encryption, Luxembourg, 26–28 March 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 196–210. [Google Scholar]
- Hong, J.; Kim, W. TMD-Tradeoff and State Entropy Loss Considerations of Stream Cipher MICKEY. Available online: http://eprint.iacr.org/2005/257 (accessed on 20 October 2019).
- Kitsos, P.; Sklavos, N.; Provelengios, G.; Skodras, A.N. FPGA-based performance analysis of stream ciphers ZUC, snow3g, grain V1, MICKEY V2, Trivium and E0. Microprocess. Microsyst. 2013, 37, 235–245. [Google Scholar] [CrossRef]
- Manifavas, C.; Hatzivasilis, G.; Fysarakis, K.; Papaefstathiou, Y. A survey of lightweight stream ciphers for embedded systems. Secur. Commun. Netw. 2016, 9, 1226–1246. [Google Scholar] [CrossRef]
- Yerukala, N.; Padmavathi, G.; Nalla, V.; Prasad, V.K. LFL-A New Stream Cipher for Secure Communications. In Proceedings of the 2018 IEEE International Conference on Computational Intelligence and Computing Research (ICCIC), Madurai, India, 13–15 December 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–5. [Google Scholar]
- Polak, I.; Boryczka, M. Tabu Search in revealing the internal state of RC4+ cipher. Appl. Soft Comput. 2019, 77, 509–519. [Google Scholar] [CrossRef]
- Kara, O.; Esgin, M.F. On analysis of lightweight stream ciphers with keyed update. IEEE Trans. Comput. 2018, 68, 99–110. [Google Scholar] [CrossRef]
- Qasaimeh, M.; Al-Qassas, R.S.; Tedmori, S. Software randomness analysis and evaluation of lightweight ciphers: The prospective for IoT security. Multimed. Tools Appl. 2018, 77, 18415–18449. [Google Scholar] [CrossRef]
- Parikh, N.; Singh, G.; Sundaresan, N. Query suggestion with large scale data. In Handbook of Statistics; Elsevier: Amsterdam, The Netherlands, 2013; Volume 31, pp. 493–518. [Google Scholar]
- Liu, D.; Chen, X.; Peng, D. Some cosine similarity measures and distance measures between q-rung orthopair fuzzy sets. Int. J. Intell. Syst. 2019, 34, 1572–1587. [Google Scholar] [CrossRef]
- Gorbenko, I.; Kuznetsov, A.; Gorbenko, Y.; Vdovenko, S.; Tymchenko, V.; Lutsenko, M. Studies on statistical analysis and performance evaluation for some stream ciphers. Int. J. Comput. 2019, 18, 82–88. [Google Scholar]
- Rifki, R.; Septiarini, A.; Hatta, H.R. Cryptography using random Rc4 stream cipher on SMS for android-based smartphones. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 89–93. [Google Scholar] [CrossRef]
- Hussein, D.M.; Taha, M.H.N.; Khalifa, N.E.M. A blockchain technology evolution between business process management (BPM) and internet-of-things (IoT). Int. J. Adv. Comput. Sci. Appl. 2018, 9, 442–450. [Google Scholar] [CrossRef]
- Abidin, Z.Z.; Zakaria, N.; Harum, N.; Baharon, M.; Hong, E.-S.; Abas, Z.A.; Ayop, Z.; Ariff, N.M. Crypt-tag authentication in NFC implementation for medicine data management. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 93–100. [Google Scholar] [CrossRef]
- Yeh, K.H.; Lo, N.W.; Wang, C.K. A robust NFC-based personalized IPTV service system. Multimed. Tools Appl. 2018, 77, 5129–5148. [Google Scholar] [CrossRef]
- Wan, X.F.; Zheng, T.; Cui, J.; Zhang, F.; Ma, Z.Q.; Yang, Y. Near Field Communication-based Agricultural Management Service Systems for Family Farms. Sensors 2019, 19, 4406. [Google Scholar] [CrossRef] [PubMed]


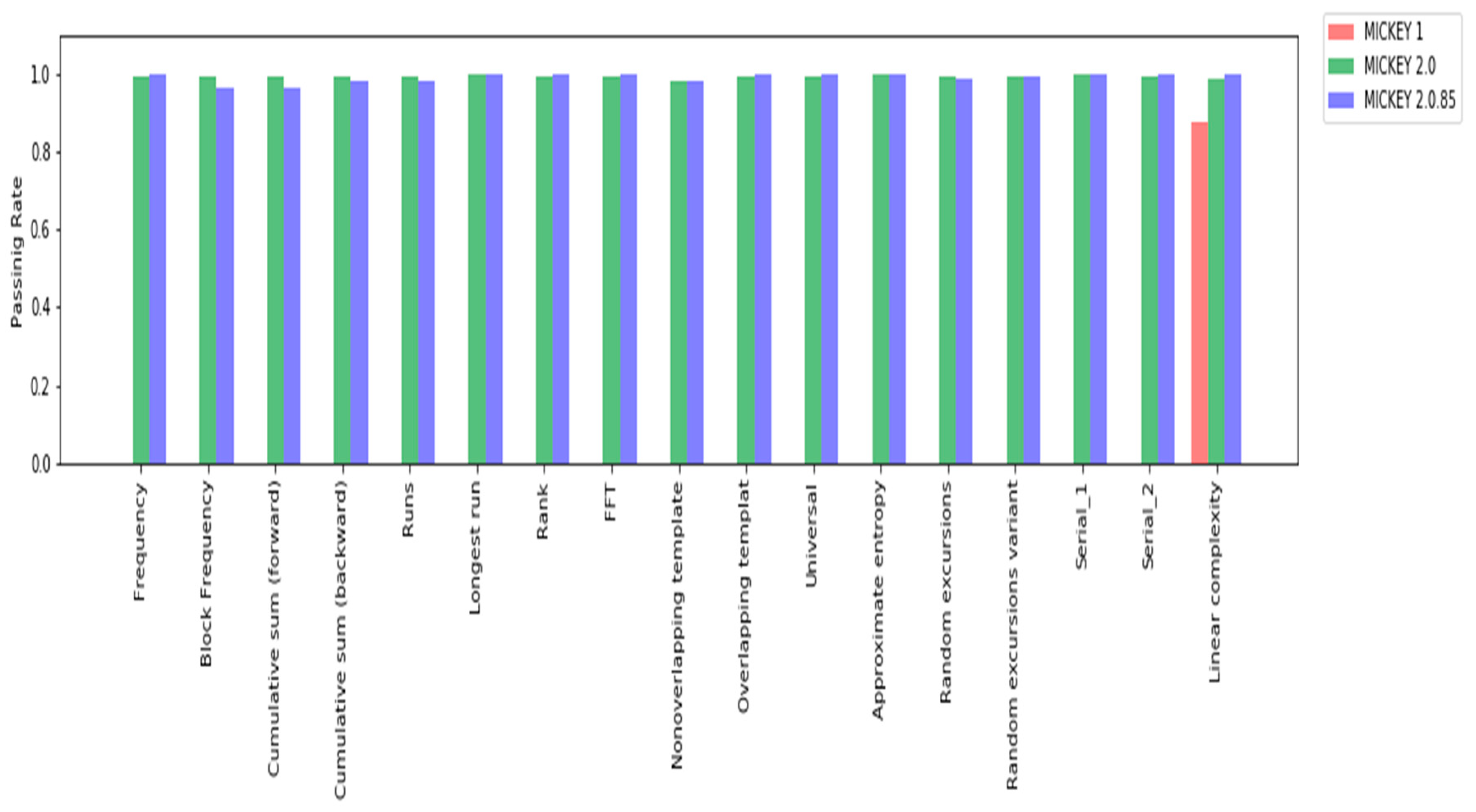

| Tests | Min p-Value | Max p-Value | Average | Proportion |
|---|---|---|---|---|
| Frequency | 0.1223 | 0.7399 | 0.3773 | 1 |
| Block frequency | 0.3504 | 0.5341 | 0.3810 | 0.9666 |
| Cumulative sum (forward) | 0.1223 | 0.9114 | 0.6635 | 0.9666 |
| Cumulative sum (backward) | 0.7399 | 0.7399 | 0.7399 | 0.9833 |
| Runs | 0.3504 | 0.5341 | 0.3810 | 0.9833 |
| Longest run | 0.3504 | 0.3504 | 0.3504 | 1 |
| Rank | 0.1223 | 0.5341 | 0.2289 | 1 |
| FFT | 0.2133 | 0.5341 | 0.2896 | 1 |
| Nonoverlapping template | 0.4588 | 0.5005 | 0.4667 | 0.9870 |
| Overlapping template | 0.0668 | 0.7399 | 0.6277 | 1 |
| Universal | 0.1223 | 0.5341 | 0.2595 | 1 |
| Approximate entropy | 0.5341 | 0.9114 | 0.7856 | 1 |
| Random excursions | 0.5745 | 1 | 0.7265 | 0.9888 |
| Random excursions variant | 0.4995 | 0.9297 | 0.7001 | 0.9960 |
| Serial_1 | 0.1223 | 0.2133 | 0.1374 | 1 |
| Serial_2 | 0.3504 | 0.7399 | 0.4460 | 1 |
| Linear complexity | 0.1223 | 0.9114 | 0.2690 | 1 |
| Tests | Min p-Value | Max p-Value | Average | Proportion |
|---|---|---|---|---|
| Frequency | 0.0351 | 0.9114 | 0.3975 | 0.9975 |
| Block frequency | 0.1223 | 0.9114 | 0.4284 | 0.9975 |
| Cumulative sum (forward) | 0.0668 | 0.9114 | 0.7886 | 0.9975 |
| Cumulative sum (backward) | 0.0179 | 0.9114 | 0.689 | 0.9975 |
| Runs | 0.0668 | 0.9114 | 0.4006 | 0.9951 |
| Longest run | 0.1223 | 0.7399 | 0.3734 | 1 |
| Rank | 0.1223 | 0.9114 | 0.2737 | 0.9975 |
| FFT | 0.1223 | 0.9114 | 0.3230 | 0.9951 |
| Nonoverlapping template | 0.4518 | 0.5289 | 0.4732 | 0.9864 |
| Overlapping template | 0.0668 | 0.9114 | 0.6395 | 0.9951 |
| Universal | 0.0668 | 0.9114 | 0.2931 | 0.9951 |
| Approximate entropy | 0.2133 | 0.9914 | 0.8154 | 1 |
| Random excursions | 0.6793 | 1 | 0.8998 | 0.9954 |
| Random excursions variant | 0.5984 | 1 | 0.8677 | 0.9962 |
| Serial_1 | 0.0668 | 0.9114 | 0.2716 | 1 |
| Serial_2 | 0.1223 | 0.9114 | 0.3974 | 0.9951 |
| Linear complexity | 0.0088 | 0.9114 | 0.2476 | 0.9926 |
| Tests | Min p-Value | Max p-Value | Average | Proportion |
|---|---|---|---|---|
| Frequency | 0.0043 | 0.9114 | 0.2475 | 0.9325 |
| Block frequency | 0.0351 | 0.9914 | 0.4088 | 0.9992 |
| Cumulative sum (forward) | 0.0088 | 0.9114 | 0.4754 | 0.9318 |
| Cumulative sum (backward) | 0.0668 | 0.9914 | 0.4386 | 0.9318 |
| Runs | 0.0179 | 0.9114 | 0.3509 | 1 |
| Longest run | 0.0351 | 0.9914 | 0.5699 | 0.9977 |
| Rank | 0.0088 | 0.9914 | 0.5624 | 1 |
| FFT | 0.0179 | 0.9114 | 0.3348 | 0.9977 |
| Nonoverlapping template | 0.4567 | 0.5441 | 0.5066 | 0.990 |
| Overlapping template | 0.0668 | 0.9914 | 0.6846 | 0.9962 |
| Universal | 0.0351 | 0.9114 | 0.4449 | 0.9970 |
| Approximate entropy | 0.0351 | 0.9114 | 0.5135 | 0.9985 |
| Random excursions | 0.5452 | 1 | 0.7243 | 0.9943 |
| Random excursions variant | 0.4387 | 1 | 0.7171 | 0.9720 |
| Serial_1 | 0.0179 | 0.9914 | 0.5386 | 0.9992 |
| Serial_2 | 0.0351 | 0.9914 | 0.3136 | 0.9955 |
| Linear complexity | 0.0088 | 0.9114 | 0.6148 | 0.9992 |
| Bytes Encrypted | MICKEY 2.0 Encryption Time Microseconds | MICKEY 2.0.85 Encryption Time Microseconds |
|---|---|---|
| 39,900 | 719,041 | 496,029 |
| 39,900 | 640,037 | 514,030 |
| 39,900 | 670,038 | 499,028 |
| 39,900 | 670,038 | 528,030 |
| 39,900 | 648,037 | 485,028 |
| 39,900 | 646,037 | 512,030 |
| 39,900 | 661,037 | 510,029 |
| 39,900 | 649,037 | 520,030 |
| Average | 662,912.75 | 508,029.25 |
| % Improvement over MICKEY 2.0 | 0 | 23.36% |
| Cipher. | Number of GEs | Power Consumption (µA @ 100 KHz) |
|---|---|---|
| MICKEY 2.0 | 3131 | 0.574 |
| MICKEY 2.0.85 | 2741 | 0.481 |
| Trivium | 3091 | 0.681 |
| Micro-Trivium | 2696 | 0.517 |
| Mechanism | Mean Cosine Similarity | STD Cosine Similarity |
|---|---|---|
| MICKEY 2.0 | 0.8472 | 0.0225 |
| MICKEY 2.0.85 | 0.8418 | 0.0298 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alamer, A.; Soh, B.; Brumbaugh, D.E. MICKEY 2.0.85: A Secure and Lighter MICKEY 2.0 Cipher Variant with Improved Power Consumption for Smaller Devices in the IoT. Symmetry 2020, 12, 32. https://doi.org/10.3390/sym12010032
Alamer A, Soh B, Brumbaugh DE. MICKEY 2.0.85: A Secure and Lighter MICKEY 2.0 Cipher Variant with Improved Power Consumption for Smaller Devices in the IoT. Symmetry. 2020; 12(1):32. https://doi.org/10.3390/sym12010032
Chicago/Turabian StyleAlamer, Ahmed, Ben Soh, and David E. Brumbaugh. 2020. "MICKEY 2.0.85: A Secure and Lighter MICKEY 2.0 Cipher Variant with Improved Power Consumption for Smaller Devices in the IoT" Symmetry 12, no. 1: 32. https://doi.org/10.3390/sym12010032
APA StyleAlamer, A., Soh, B., & Brumbaugh, D. E. (2020). MICKEY 2.0.85: A Secure and Lighter MICKEY 2.0 Cipher Variant with Improved Power Consumption for Smaller Devices in the IoT. Symmetry, 12(1), 32. https://doi.org/10.3390/sym12010032






