Forgery Detection and Localization of Modifications at the Pixel Level
Abstract
:1. Introduction
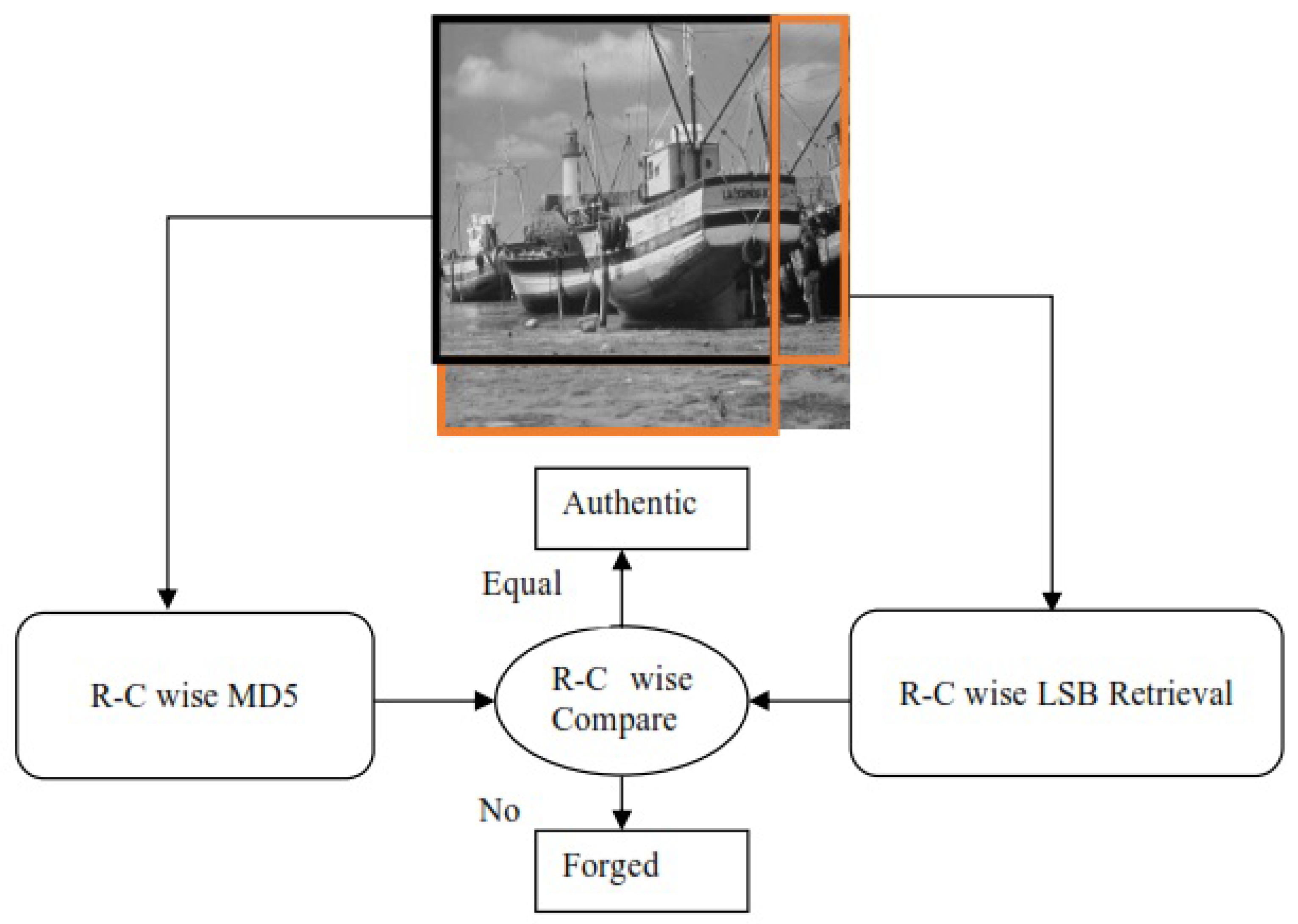
2. Proposed Forgery Detection Techniques
3. Experimental Results and Analysis
4. Comparison
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Farid, H. Image forgery detection. IEEE Signal Process. Mag. 2009, 26, 16–25. [Google Scholar] [CrossRef]
- Blythe, P.; Fridrich, J. Secure digital camera. In Proceedings of the Digital Forensic Research Workshop, Baltimore, MD, USA, 11–13 August 2004. [Google Scholar]
- Cox, I.; Miller, M.L.; Bloom, J.A. Digital Watermarking; Morgan Kaufmann: San Mateo, CA, USA, 2001. [Google Scholar]
- Redi, J.A.; Taktak, W.; Dugelay, J.L. Digital image forensics: A booklet for beginners. Multimed. Tool Appl. 2011, 51, 133–162. [Google Scholar] [CrossRef] [Green Version]
- Wang, J.; Liu, G.; Zhang, Z.; Dai, Y.; Wang, Z. Fast and robust forensics for image region-duplication forgery. Acta Autom. Sinica 2009, 35, 1488–1495. [Google Scholar] [CrossRef]
- Ansari, M.D.; Ghrera, S.P.; Tyagi, V. Pixel-based image forgery detection: A review. IETE J. Educ. 2014, 55, 40–46. [Google Scholar] [CrossRef]
- Khan, S.; Bianchi, T. Reduced Complexity Image Clustering Based on Camera Fingerprints. In Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Brighton, UK, 12–17 May 2019; pp. 2682–2688. [Google Scholar]
- Fridrich, J. Robust bit extraction from images. In Proceedings of the IEEE International Conference on Multimedia Computing and Systems, Florence, Italy, 7–11 June 1999; pp. 536–540. [Google Scholar]
- Zhao, Z.; Li, J.; Li, S.; Wang, S. Detecting digital image splicing in chroma spaces. In International Workshop on Digital Watermarking; Springer: Berlin, Germany, 2010; pp. 12–22. [Google Scholar]
- Doke, K.K.; Patil, S.M. Digital signature scheme for image. Int. J. Comput. Appl. 2012, 49, 1–6. [Google Scholar]
- Bravo-Solorio, S.; Nandi, A.K. Automated detection and localisation of duplicated regions affected by reflection, rotation and scaling in image forensics. Signal Process. 2011, 91, 1759–1770. [Google Scholar] [CrossRef]
- Pun, C.M.; Yuan, X.C.; Bi, X.L. Image forgery detection using adaptive over segmentation and feature point matching. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1705–1716. [Google Scholar]
- Moghaddasi, Z.; Jalab, H.A.; Noor, R.M. SVD-based image splicing detection. In Proceedings of the 6th International Conference on Information Technology and Multimedia, Putrajaya, Malaysia, 18–20 November 2014; pp. 27–30. [Google Scholar]
- Boato, G.; Natale, F.G.; Zontone, P. How digital forensics may help assessing the perceptual impact of image formation and manipulation. In Proceedings of the Fifth International Workshop on Video Processing and Quality Metrics for Consumer Electronics, Scottsdale, AZ, USA, 13–15 January 2010. [Google Scholar]
- Avcibas, I.; Bayram, S.; Memon, N.; Ramkumar, M.; Sankur, B. A classifier design for detecting image manipulations. In Proceedings of the 2004 International Conference on Image Processing, ICIP ’04, Singapore, 24–27 October 2004; pp. 2645–2648. [Google Scholar]
- Stamm, M.C.; Liu, K.R. Blind forensics of contrast enhancement in digital images. In Proceedings of the 2008 15th IEEE International Conference on Image Processing, San Diego, CA, USA, 12–15 October 2008; pp. 3112–3115. [Google Scholar]
- Stamm, M.C.; Liu, K.R. Forensic estimation and reconstruction of a contrast enhancement mapping. In Proceedings of the 2010 IEEE International Conference on Acoustics, Speech and Signal Processing, Dallas, TX, USA, 14–19 March 2010; pp. 1698–1701. [Google Scholar]
- Stamm, M.C.; Liu, K.R. Forensic detection of image manipulation using statistical intrinsic fingerprints. IEEE Trans. Inf. Forens. Secur. 2010, 5, 492–506. [Google Scholar] [CrossRef]
- Cao, G.; Zhao, Y.; Ni, R. Forensic estimation of gamma correction in digital images. In Proceedings of the 2010 IEEE International Conference on Image Processing 2010, Hong Kong, China, 26–29 September 2010; pp. 2097–2100. [Google Scholar]
- Li, X.F.; Shen, X.J.; Chen, H.P. Blind identification algorithm for retouched images based on Bi-Laplacian. J. Comput. Appl. 2011, 31, 239–242. [Google Scholar] [CrossRef]
- Cao, G.; Zhao, Y.; Ni, R.; Li, X. Contrast enhancement-based forensics in digital images. IEEE Trans. Inf. Forensics Secur. 2014, 9, 515–525. [Google Scholar] [CrossRef]
- Chierchia, G.; Poggi, G.; Sansone, C.; Verdoliva, L. A Bayesian-MRF approach for PRNU-based image forgery detection. IEEE Trans. Inf. Forensics Secur. 2014, 9, 554–567. [Google Scholar] [CrossRef]
- Fan, Z.; de Queiroz, R. Maximum likelihood estimation of JPEG quantization table in the identification of bitmap compression history. In Proceedings of the International Conference on Image Processing Proceedings, Vancouver, BC, Canada, 10–13 September 2000; pp. 948–951. [Google Scholar]
- Fan, Z.; De Queiroz, R.L. Identification of bitmap compression history: JPEG detection and quantizer estimation. IEEE Trans. Image Process. 2003, 12, 230–235. [Google Scholar] [PubMed] [Green Version]
- Lukáš, J.; Fridrich, J. Estimation of primary quantization matrix in double compressed JPEG images. In Proceedings of the Digital Forensic Research Workshop, Cleveland, OH, USA, 6–8 August 2003; pp. 5–8. [Google Scholar]
- Popescu, A.C. Statistical Tools for Digital Image Forensics. Ph.D. Thesis, Dartmouth College, Hanover, NH, USA, 2004. [Google Scholar]
- Popescu, A.C.; Farid, H. Exposing digital forgeries in color filter array interpolated images. IEEE Trans. Signal Process. 2005, 53, 3948–3959. [Google Scholar] [CrossRef]
- Lukas, J.; Fridrich, J.; Goljan, M. Digital camera identification from sensor pattern noise. IEEE Trans. Inf. Forensics Secur. 2006, 1, 205–214. [Google Scholar] [CrossRef]
- Johnson, M.K.; Farid, H. Exposing digital forgeries by detecting inconsistencies in lighting. In Proceedings of the 7th Workshop on Multimedia and Security, New York, NY, USA, 1–2 August 2005; pp. 1–10. [Google Scholar]
- Johnson, M.K.; Farid, H. Exposing digital forgeries in complex lighting environments. IEEE Trans. Inf. Forensics Secur. 2007, 2, 450–461. [Google Scholar] [CrossRef]
- Chen, H.; Shen, X.; Lv, Y. Blind identification method for authenticity of infinite light source images. In Proceedings of the 2010 Fifth International Conference on Frontier of Computer Science and Technology, Changchun, China, 18–22 August 2010; pp. 131–135. [Google Scholar]
- Kee, E.; Farid, H. Exposing digital forgeries from 3-D lighting environments. In Proceedings of the 2010 IEEE International Workshop on Information Forensics and Security, Seattle, WA, USA, 12–15 December 2010; pp. 1–6. [Google Scholar]
- Lv, Y.; Shen, X.; Chen, H. An improved image blind identification based on inconsistency in light source direction. J. Supercomput. 2011, 58, 50–67. [Google Scholar] [CrossRef]
- Fan, W.; Wang, K.; Cayre, F.; Xiong, Z. 3D lighting-based image forgery detection using shape-from-shading. In Proceedings of the European Signal Processing Conference, Bucharest, Romania, 27–31 August 2012; pp. 1777–1781. [Google Scholar]
- De Carvalho, T.J.; Riess, C.; Angelopoulou, E.; Pedrini, H.; de Rezende Rocha, A. Exposing digital image forgeries by illumination color classification. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1182–1194. [Google Scholar] [CrossRef] [Green Version]
- Johnson, M.K.; Farid, H. Detecting Photographic Composites of People. In International Workshop on Digital Watermarking; Springer: Berlin, Germany, 2007; pp. 19–33. [Google Scholar]
- Ng, T.T.; Chang, S.F.; Hsu, J.; Xie, L.; Tsui, M.P. Physics-motivated features for distinguishing photographic images and computer graphics. In Proceedings of the ACM International Conference on Multimedia, Singapore, 6–12 November 2005; pp. 239–248. [Google Scholar]
- Wahid, M.; Ahmad, N.; Zafar, M.H.; Khan, S. On combining MD5 for image authentication using LSB substitution in selected pixels. In Proceedings of the 2018 International Conference on Engineering and Emerging Technologies (ICEET), Lahore, Pakistan, 22–23 February 2018; pp. 1–6. [Google Scholar]
- Khan, S.; Yousaf, M.H.; Akram, J. Implementation of Variable Least Significant Bits Stegnography using DDDB Algorithm. Int. J. Comput. Sci. Issues (IJCSI) 2011, 8, 101–109. [Google Scholar]
- Khan, S.; Ahmad, N.; Ismail, M.; Minallah, N.; Khan, T. A secure true edge based 4 least significant bits steganography. In Proceedings of the 2015 International Conference on Emerging Technologies (ICET), Peshawar, Pakistan, 19–20 December 2015; pp. 1–4. [Google Scholar]
- Khan, S.; Wahid, M.; Irfan, M.A.; Naeem, M.; Gul, A.; Zafar, M.H. Row Level Image Forgery Detection Technique using Embedded Digital Signature. J. Eng. Appl. Sci. 2018, 37, 1–6. [Google Scholar]
- Khan, S.; Wahid, M.; Khan, T.; Ahmad, N.; Zafar, M.H. Column Level Image Authentication Technique using Hidden Digital Signatures. In Proceedings of the 2018 24th International Conference on Automation and Computing (ICAC), Newcastle upon Tyne, UK, 6–7 September 2018; pp. 1–6. [Google Scholar]
- Lyu, S.; Farid, H. Detecting hidden messages using higher-order statistics and support vector machines. In Information Hiding; Springer: Berlin/Heidelberg, Germany, 2002; pp. 340–354. [Google Scholar]
- Shi, Y.Q.; Xuan, G.; Zou, D.; Gao, J.; Yang, C. Steganalysis based on moments of characteristic functions using wavelet decomposition, prediction-error image, and neural network. In Proceedings of the International Conference on Multimedia and Expo, Amsterdam, The Netherlands, 6 July 2005; pp. 269–272. [Google Scholar]
- Zou, D.; Shi, Y.Q.; Su, W.; Xuan, G. Steganalysis based on Markov model of thresholded prediction-error image. In Proceedings of the 2006 IEEE International Conference on Multimedia and Expo, Toronto, ON, Canada, 9–12 July 2006; pp. 1365–1368. [Google Scholar]
- Rad, R.M.; Wong, K. Digital image forgery detection by edge analysis. In Proceedings of the 2015 IEEE International Conference on Consumer Electronics-Taiwan, Taipei, Taiwan, 6–8 June 2015; pp. 19–20. [Google Scholar]
- Kashyap, A.; Parmar, R.S.; Suresh, B.; Agarwal, M.; Gupta, H. Detection of digital image forgery using wavelet decomposition and outline analysis. In Proceedings of the 2016 International Conference on Signal Processing and Communication (ICSC), Noida, India, 26–28 December 2016; pp. 187–190. [Google Scholar]




| Evaluation Metrics | |||
|---|---|---|---|
| Technique | TP (%) | TN (%) | Accuracy (%) |
| Lyu and Farids | 78.20 | 69.39 | 73.75 |
| Shi et al. | 75.55 | 76.02 | 75.78 |
| Zou et al. | 77.40 | 75.07 | 76.21 |
| Rad et al. | 80.11 | 77.61 | 78.80 |
| Kashyaop et al. | 83.33 | 76.0 | 81.50 |
| Khan et al. [41] | 96.51 | 95.78 | 95.01 |
| Khan et al. [42] | 96.51 | 95.78 | 95.01 |
| Proposed technique | 97.1 | 96.93 | 97.02 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khan, S.; Khan, K.; Ali, F.; Kwak, K.-S. Forgery Detection and Localization of Modifications at the Pixel Level. Symmetry 2020, 12, 137. https://doi.org/10.3390/sym12010137
Khan S, Khan K, Ali F, Kwak K-S. Forgery Detection and Localization of Modifications at the Pixel Level. Symmetry. 2020; 12(1):137. https://doi.org/10.3390/sym12010137
Chicago/Turabian StyleKhan, Sahib, Khalil Khan, Farman Ali, and Kyung-Sup Kwak. 2020. "Forgery Detection and Localization of Modifications at the Pixel Level" Symmetry 12, no. 1: 137. https://doi.org/10.3390/sym12010137
APA StyleKhan, S., Khan, K., Ali, F., & Kwak, K.-S. (2020). Forgery Detection and Localization of Modifications at the Pixel Level. Symmetry, 12(1), 137. https://doi.org/10.3390/sym12010137







