1. Introduction
Digital forensics has emerged as a new area of study during the last two decades due to the explosive growth of the internet, usage of electronic devices, rapid innovation in technology and growing size of storage devices and high rise in digital or computer crimes. Digital forensics’ objective is to find and interpret the origin of an event or artefact found on a computer system. Moreover, digital forensics is concerned with the recovery and investigation of digital evidence; when needed, this is often because of a (cyber) crime. The most common reasons for performing digital forensics are attribution, identifying a leak within an organisation, and assessing the possible damage that occurred during a breach. The field of digital forensics is divided up into several subdivisions, depending on the type of the digital device that is the subject of the investigation. These include computer forensics, network forensics, forensic data analysis, and mobile device forensics. Digital investigators examine data and devices to find out as much as possible about a breach or crime that involved digital devices in the form of digital evidence. Carrier [
1] classifies digital forensics into three main phases, namely acquisition, analysis and presentation. The aim of the acquisition phase is to preserve the state of a digital system so that evidence can be retrieved and analysed later in controlled conditions. The next phase, i.e., analysis, is to investigate the acquired data to determine evidence of malicious activity. The presentation phase is based entirely on legal rules and regulations, which change depending on the jurisdiction of the country where the digital evidence is located, and it is thus beyond the scope of this paper. Generally, at the acquisition phase, the first step initiated by the investigator is to acquire images of the storage devices of a seized computer. The next step after the acquisition phase involves determining evidence that may involve the exploration of documents and image files of relevance to the investigation.
In a digital forensic investigation, as in a conventional crime scene reconstruction, it is important to be capable of composing a timeline of the file system activities on a computer system. The timeline is used to reconstruct the suspected crime, and it is beneficial in presenting user access to the target system, execution of certain applications, and identifying system and data files which were accessed, modified or deleted during particular periods of interest to the investigation [
2]. To show the evidence collected from a seized computer in a law court, the process by which the evidence was derived is required to be clearly shown to abide by accepted procedures and practices [
3]. In legal proceedings, this practice is known as the ‘chain of custody’. To prove the authenticity of the evidence, comprehensible chains of reasoning are required to be submitted to the court about the scientific methods adopted in the extraction of evidence. Digital investigators face various challenges, such as high speed and volumes of data, explosions of complexity [
4], development of standards, privacy-preserving investigations, and rise of anti-forensics techniques when digital or electronic devices are considered to extract evidence from them in the form of the construction of timeline, and this is the objective of our paper. This paper presents an abstraction-based approach to support digital investigators during an investigation via reconstruction of the timeline of events and artefacts which is readable and understandable for investigators and reduces the time needed to collect digital evidence from digital devices.
The remainder of this paper is structured as follows.
Section 2 provides a review of related work.
Section 3 discusses the methodology for this research.
Section 4 provides implementation, results and its discussion from the use of the developed methodology. At last, we finish with conclusions in
Section 5.
2. Literature Review
Prasad & Satish [
5] defined digital forensics as the procedure of identifying, collecting, preserving, analysing and presenting digital evidence in a way that is legally accepted by the court. To collect the digital evidence from digital devices efficiently, effectively and within a limited period of time, reconstruction of timeline required. Carvey [
6] defined timeline as “a means of identifying or linking a sequence of events in a manner that is easy for people such as incident responders to visualize and understand”. Harrell [
7] defined “timeline analysis is a great technique to determine the activity that occurred on a system at a particular period of time on a system”. So, “creating a timeline of the various events that occurred during an incident is one of the key tasks performed by the digital forensic practitioner” [
8]. Timeline analysis should be a key component to any investigation as the timing of events is nearly always relevant. The primary source of timeline information is the file system metadata. File systems’ track different time stamps and have nuances that must be considered when performing forensic analysis [
9].
Inglot & Liu [
10] specified that there are basically two approaches for analysis of the timeline. Firstly, there are applications that have been specifically created for the analysis of the timeline, and they focus on visually presenting the timeline, such as Cyber Forensics Time Lab (CFTL), Zeitline, Encase, Sleuth kit, Forensic toolkit and many others. Secondly, there are a combination of command-line tools and spreadsheet applications which are labour intensive, such as Log2timeline and excel together. Guðjónsson [
11] designed a tool to extract timestamps from various files found on a typical computer system and aggregate them. The tool Log2timeline is a part of a Python-based backend engine plaso. The purpose of plaso was to have the timestamps in a single place for computer forensic analysis. Such a timeline sometimes is called a Super Timeline. Sitompul, Handoko, & Rahmat [
12] state that to have a clear view of events that occurred during a time period is challenging to achieve in digital investigation. Event reconstruction, which allows a digital investigator to understand the timeline of a crime, is one of the paramount steps of the digital investigation process [
13]. This complex task requires exploration of a large number of events due to the innovation in technology frequently, a heterogeneous, huge quantity of data, and manually-performed event reconstruction process, which is inefficient and expensive [
14]. Bang et al. [
15] discussed how the creation time, last written time, and last accessed time of a file or folder are important factors that can indicate events that have affected a computer system. They analysed changes in the time information of files and folders for different operations of the FAT and NTFS file systems and attempts to reconstruct the user’s actions. Further, they demonstrate the use of time information for digital evidence analysis by presenting a case study. Chabot et al. [
16] identified two major challenges (heterogeneity and volume of data) with event reconstruction. To solve these two challenges, they present an approach supported by theoretical concepts that can assist investigators through the whole process, including the construction and interpretation of the events describing the case. The proposed approach is based on a model which integrates knowledge of experts from the digital forensic fields and software development to allow a semantically rich representation of events related to incidents.
Hargreaves & Patterson [
17] considered a possible use of the tool Log2timeline for timeline reconstruction; however, they decided to build their own Python-based prototype. The other contribution of the research work was a framework that allows analyses to be written that can produce a high-level event based on the presence of one or more low-level events. The shortcoming of the approach was that the analysers, which were oriented to particular events, have to be written in advance. Brady, Overill & Keppens [
18] proposed the use of an ontology, the Digital Evidence Semantic Ontology (DESO), that allows an examiner to quickly discover what artefacts may be available on a device before time-consuming processes are commenced. The DESO is built on the ideas of the Gene Ontology (GO). The general principle behind DESO is two-fold: (1) examiners use some form of classification or tagging system that allowed examiners to readily assess what artefacts were available; (2) once artefacts have been extracted from various sources, DESO provides the means to compare them. The main idea of DESO is to enable comparison of the artefacts extracted from different sources. Brady & Overill [
19] continued the development of the ontology DESO. DESO’s primary purpose is to act as a repository and a classifier of digital evidence artefacts to allow correlation of extracted data from heterogeneous sources. Investigative objectives are set and fulfilled by asking simple questions based on who, what, when, where, why and how? (‘5WH’). Only the “What” subclass has been detailed. The classes “why” and “how” were not discussed at all. An implemented body of DESO was not revealed. It remained behind the scenes. Only the ideas were presented.
Debinski, Breitinger & Mohan [
20] state that event reconstruction is a fundamental step for investigators to understand a case where a prominent tool is Log2timeline to generates timelines. While these timelines provide great evidence and assist to understand a case, they are complex and require tools as well as training scenarios. Moreover, they also state some of the major limitations of Log2timeline, such as the fact that there is no easy-to-use tool that beginners/investigators can use to analyse a generated timeline and no free training material that also allows practitioners to learn and improve their familiarity with the Log2timeline as well as visualization tools. To support investigators, the authors developed Timeline2GUI a standalone tool written in Python that supports the analysis of the CSV timeline (output from Log2timeline). The tool is similar to the commonly-used Excel sheet to allow an easy transition for practitioners. In addition, they developed three training cases that are freely available and can be used to improve investigator’s timeline analysis skills by either using Timeline2GUI, the Excel sheet or any other tool. The performance of Timeline2GUI can be enhanced by speeding up the process, such as by removing irrelevant fields or combining fields in future work. Soltani, Seno & Yazdi [
21] proposed an event reconstruction framework which determines whether an application has been run on a compromised system. The proposed framework has constructed the signature or the TPFSM-A (temporal pattern of file system modification of the application) and the TPFSM-D (temporal pattern of file system modification of the hard disk). Moreover, the framework has presented a distance metric which is used to calculate the distance between the signature of the application and TPFSM-D of the hard disk. Finally, the decision engine of the framework has used the calculated distance to decide whether the application has been run on the compromised system.
Zhao and Coplien [
22] stated that the success of symmetry applications in various scientific disciplines motivated them to explore the concept of symmetry in software. Further, the authors explained object-oriented language constructs use the notion of symmetry and explored symmetry in an object-oriented language and also provide some examples of symmetry outside of object-oriented programming to show that symmetry considerations broaden beyond object-orientation to other areas of software design.
Jensen [
23] stated that a class is the classification of objects. Classifications establish the class member invariance such that the description of the class is true for all the objects of the class. This view of the class can be explained as symmetry. A class enables the change of the object, but the change must respect the structure and behaviour stipulated by the class.
The literature review shows that numerous tools and techniques have been developed to support digital investigators handling timeline analysis available, but none of them are able to solve the complexity of construction of the timeline of events and artefacts effectively in digital forensics. Some of the primary reasons which are responsible for the ineffective reconstruction of timelines include the immense amount of data, heterogeneity of data, rapid innovation of technology, accelerated growth of the internet, and integrity of the timeline. The purpose of the paper is to develop and implement a methodology for the reconstruction of the timeline of events and artefacts which is able to regenerate the timeline completely and understandably based on the level of abstraction, and is also able to accomplish this even with the existence of above-mentioned issues and can follow the symmetry properties by stipulating specific conditions at each level of abstraction to compose the relevant timeline.
3. Methodology
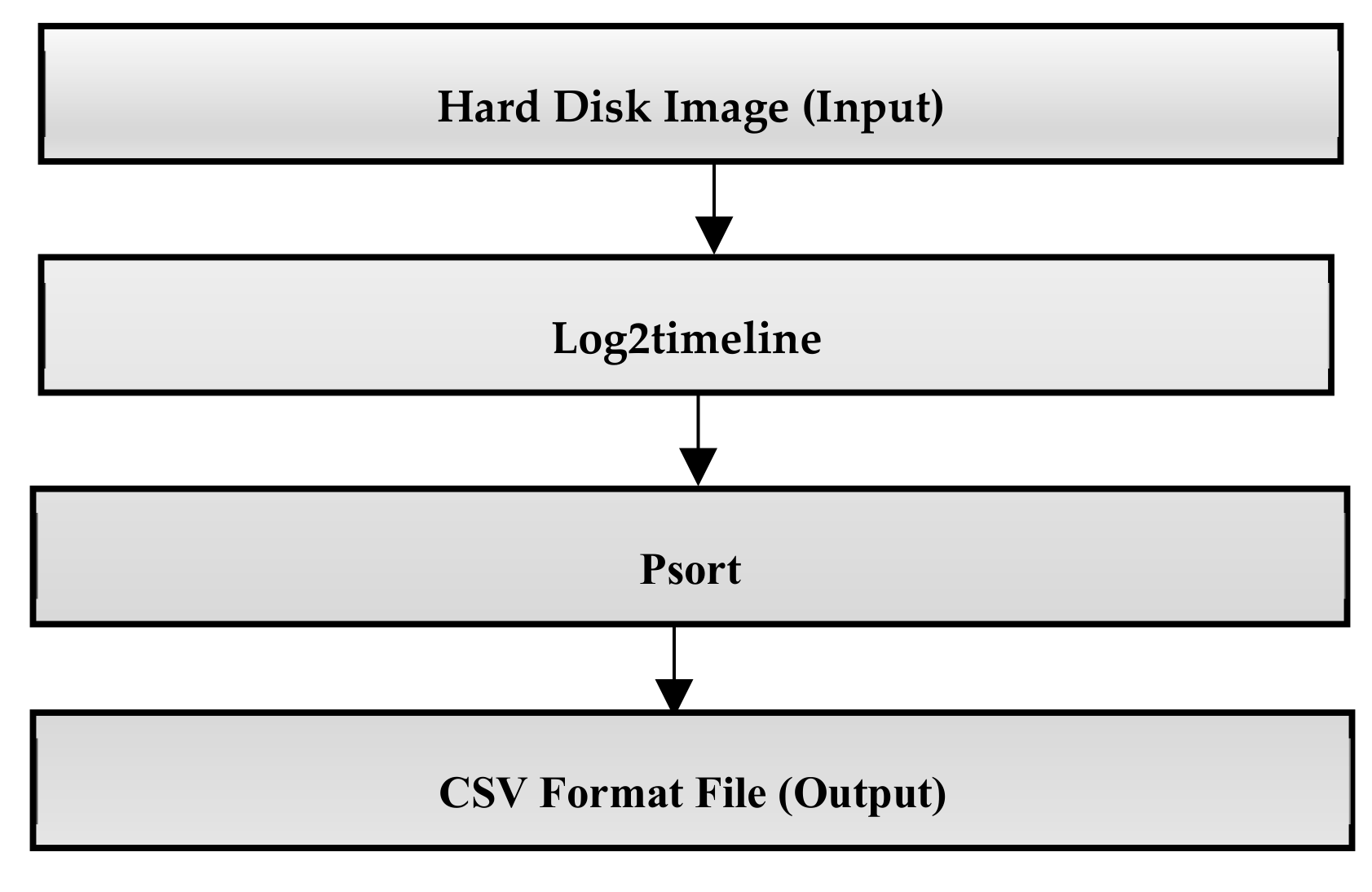
Various problems are highlighted in the literature review section stem from a huge volume of data when the timeline is extracted from a disk image, particularly with the ‘Super Timeline’ approach. Our research work is based on the data provided by Log2timeline in the form of plaso file, which is sorted out with the Psort tool as shown in
Figure 1.
Additionally, Psort allows converting the plaso file into common file formats such as CSV. The CSV timeline contains 17 fixed fields as listed in
Table 1 (SANS, 2011); then, data from the CSV file is imported into an Excel sheet. One of the most common problems in the timeline extracted by Log2timeline is a repetition of the same time unit for numerous times. For instance, time unit “11:49:53” in the field “time” repeated multiple times correspond to various sources of data such as “WEBHIST” and “LNK” in the field “source”, which shows that the occurrence of the same event has raised the reflection in different logs and different artefacts, as shown in
Table 2. Such scenarios formulate timeline large, complex and difficult to analyse for digital forensic practitioners. So, we extract such scenarios from the timeline and replace using appropriate methods (such as one event per time unit to eliminate duplication) to reconstruct a simple, compact, recognisable and structured timeline for digital forensics practitioners.
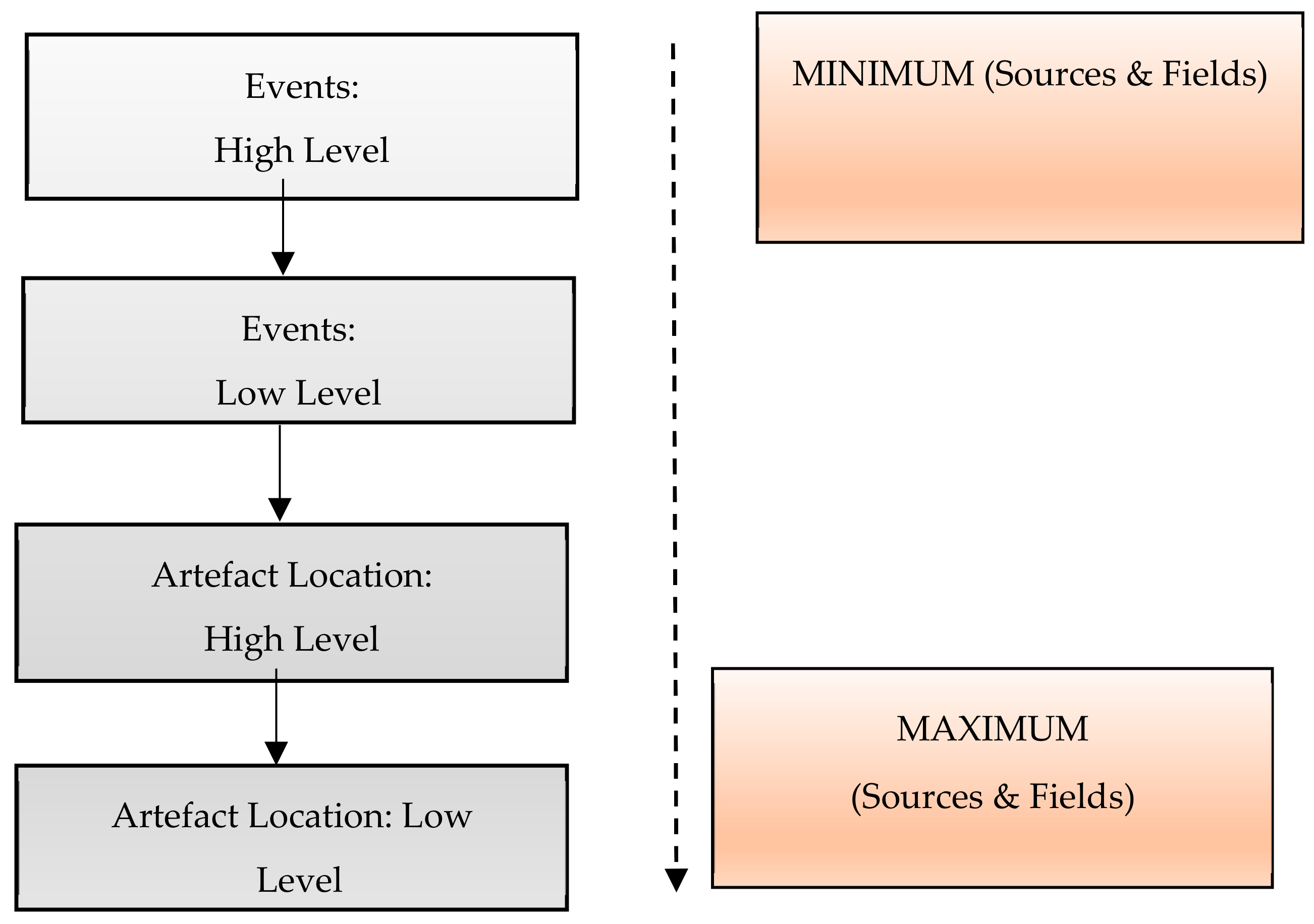
We present a methodology by which it is viable to present the timeline of events and artefacts relevant by using the concept of abstraction to extend the timeline of events and artefacts at four different abstraction levels, i.e., events: High level; events: Low level; artefact location: High level; and artefact location: Low level, as shown in
Figure 2 to generate timeline readable and understandable for digital investigators. The ideas behind the breakdown of the timeline provided by Log2timeline into four levels of abstraction is given to present the different kinds of information, and a different structure should be specified for each level along with distinctive levels of details of information in order to reduce complexity of timeline, omitting unwanted details, enforcing the correctness of timeline and presenting only information that will be helpful to recognise and understand particular actions executed by users by analysing different sources and fields.
In digital forensics, an event can be characterised as an activity performed by users utilising digital devices. On the other side, “artefact” currently does not have a formal definition within the domain of cyber/digital forensics, resulting in a lack of standardised reporting and linguistic understanding between professionals. Generally, the artefact can be defined as a piece of data that may or may not be relevant to the investigation/response. Examples include registry keys, files, timestamps, and event logs. In other words, artefacts can be defined as something observed in a scientific investigation or experiment that is not naturally present but occurs as a result of the preparative or investigative procedure.
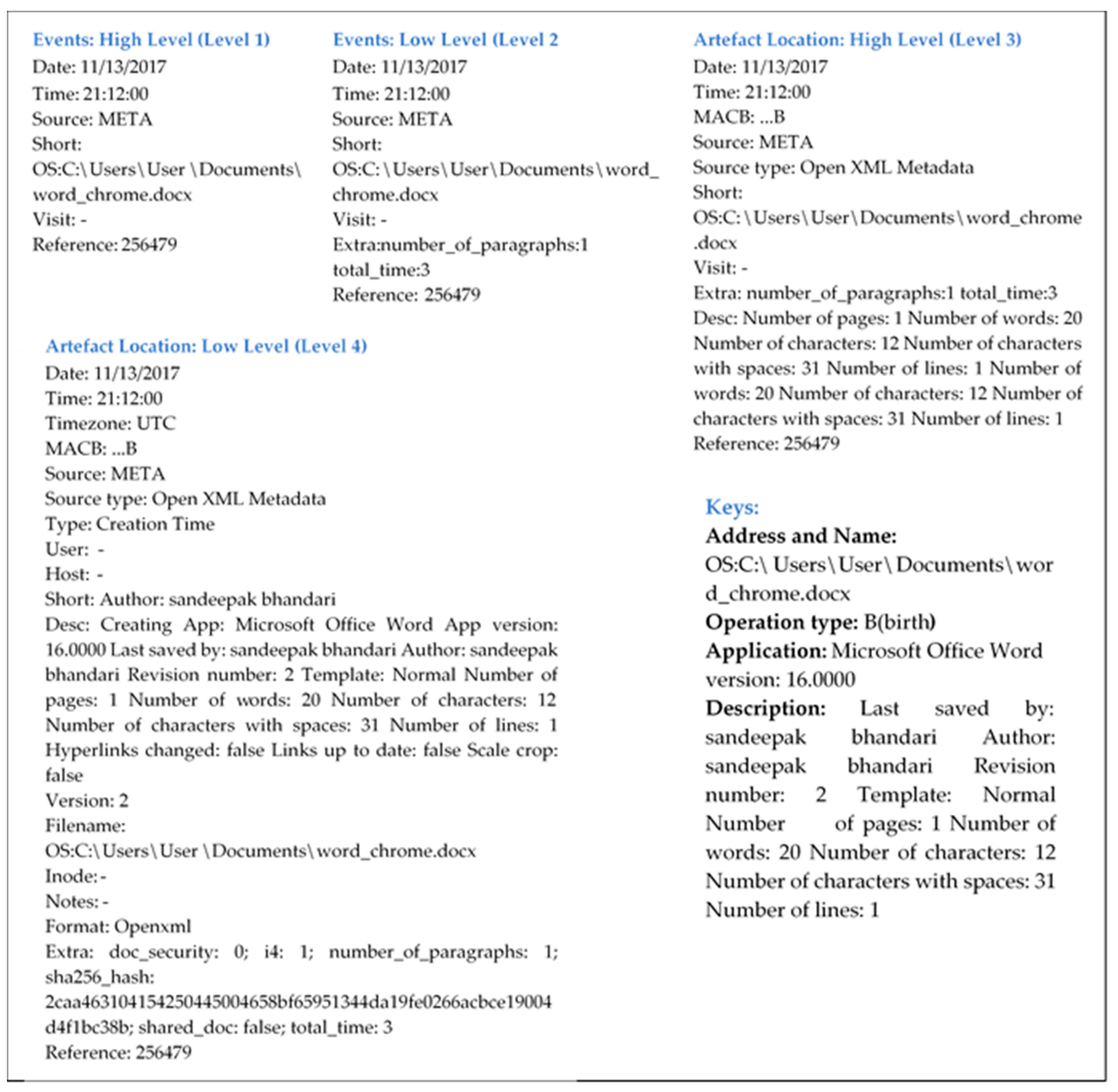
The selected methodology in the research involves the development of four different modules, with each module corresponding to one of the levels of abstraction of the timeline of events and artefacts. At each level of the methodology, different types of sources, parameters and fields are considered to compose improved structure and representation of the timeline. At events: High level information related to activities carried out by users such as the creation of files, access of web pages and downloads of information in the form of files of various formats (jpeg, pdf and docx) is provided. Such information with higher levels of abstraction is extracted by analysing six different sources, “LNK”, “LOG”, “META”, “OLECF”, “PE” and “WEBHIST”, and six distinct fields, namely “date”, “time”, “source”, “short”, “visit” and “reference”, providing required information to recognise particular activities. Moreover, the number of sources and fields considered for analysing depends upon what kind of information it is and its level of detail required at the particular level of the timeline.
To achieve detailed information, various types of operations are performed related to the files, namely modification, access, changes and birth, and web surfing activities that address of specific web pages accessed and the download of files by user. The second level of abstraction events: Low level is reconstructed with additional details as compared to previous events: High level so an additional number of sources and fields are required for analysis. At this level, nine different sources and seven fields with the extension of three new sources, including “FILE”, “REG” and “RECBIN”, and a new field, “extra”, respectively are examined to reconstruct the timeline. The first two levels of abstraction of the methodology can provide the least information related to what type of actions are performed by users, but it is not adequate to reconstruct the complete timeline. To gain a clear view of the timeline, additional information is required. This includes a list of all .exe files run by the user, applications and files that are frequently accessed, authors of files, list of files. Namely, .automaticDestinations-ms provides information about the application used that is pinned on a user’s taskbar, timestamps, and the paths to items (documents, webpages, images, etc.) recently accessed by a program pinned on a user’s taskbar, while .msp provides updating information related to Windows operating system and other Microsoft programs, and the .msi file contains installation information for a particular installer, such as files pending to be installed and installation locations.
Moreover, detailed information is provided related to various activities performed on the internet. For instance, which application program (web browser) is used to and how (LINK–user clicked a link, GENERATED–selected an entry from the list, RELOAD–user reloaded the page and TYPED–user typed the URL in the URL bar) each specific web page is accessed. This detailed information is provided at artefact: High level, and is reconstructed by examining the nine different sources and ten fields with the addition of three new fields “MACB”, “sourcetype” and “desc “(description) with a lower level of abstraction. At different levels of abstraction, we include relevant information and removing unwanted details to reconstruct the relevant timeline by considering a different number of sources and fields. At the end, we reconstruct a timeline with the lowest abstraction level among all levels of abstraction of artefact: Low level by analysing all available nine sources and seventeen fields with the addition of 9 fields, namely “timezone”, “type”, “user”, “host”, “version” “filename”, “inode”, “notes” and “format” to provide complete detailed information related to all activities performed by user.
The proposed methodology is composed of four different abstraction levels of events and artefacts. Each level provides different information related to various activities executed by the user, with different levels of abstraction of information, beginning from minimum to maximum details, to reconstruct the relevant and recognisable timeline for the better understandability of the digital practitioner.
5. Conclusions
In digital forensics, one of the primary challenges is the reconstruction and analysis of the timeline of events and artefacts to interpret digital evidence due to the immense quantity and diversity of data. Scientific and technical literature studies show that various approaches have been developed to figure it out, but most of them are not capable of handling this issue precisely.
In this paper, we present a flexible and novel approach based on four different levels of abstraction of timeline of events and artefacts such as events: High level (new entries and web surfing), events: Low level (web surfing, actions of modifying), artefact location: High level (include all .exe files) and artefact location: Low level. The contributions of the proposed methodology are at each level of timeline; a unique structure is followed which gives information related to a particular action performed by the user. Different parameters, fields, and criteria are considered for a noise-free timeline (such as one event per time unit), and distinct relevant patterns of data are considered to exclude the irrelevant data to reconstruct the compact and efficient timeline with a distinct level of abstraction of detail in order to show the structured timeline, which assists the investigator in understanding and analysing the timeline conveniently and rapidly.
Various experiments are executed to implement the proposed approach and test the outcome. The results show that the abstraction-based approach is capable of the reconstruction of the timeline of events and artefacts efficiently, regardless of quantity and heterogeneity of data, as compared existing techniques. Moreover, in this article, only windows-based operating system operations and results are discussed. However, this methodology can be implemented to other operating systems as the Lo2timeline command based tool has the capability to compile other operating systems and generate output in the form of the L2TCSV format, which is used as an input to the methodology. In the future, we will implement a proposed methodology for the android operating system, and based on the results, an abstraction-based ontology will be developed for digital forensics’ future work.