Abstract
Recently, various types of single valued neutrosophic (SVN) rough set models were presented based on the same inclusion relation. However, there is another SVN inclusion relation in SVN sets. In this paper, we propose a new type of SVN covering rough set model based on the new inclusion relation. Furthermore, the graph and matrix representations of the new SVN covering approximation operators are presented. Firstly, the notion of SVN -covering approximation space is proposed, which is decided by the new inclusion relation. Then, a type of SVN covering rough set model under the SVN -covering approximation space is presented. Moreover, there is a corresponding SVN relation rough set model based on a SVN relation induced by the SVN -covering, and two conditions under which the SVN -covering can induce a symmetric SVN relation are presented. Thirdly, the graph and matrix representations of the new SVN covering rough set model are investigated. Finally, we propose a novel method for decision making (DM) problems in paper defect diagnosis under the new SVN covering rough set model.
1. Introduction
Rough set theory, as a tool to deal with various types of data in data mining, was proposed by Pawlak [1,2] in 1982. Then rough set theory has been extended to generalize rough sets based on other notions such as binary relations [3], neighborhood systems [4], and coverings [5].
Covering-based rough sets [6,7,8,9] were proposed to deal with the type of covering data. In application, they have been applied to knowledge reduction [10,11], decision rule synthesis [12,13], and other fields [14,15]. In theory, covering-based rough set theory has been connected with matroid theory [16,17,18], lattice theory [19,20], and fuzzy set theory [21,22,23]. Zadeh’s fuzzy set theory [24] addresses the problem of how to understand and manipulate imperfect knowledge. It has been used in various applications [25,26,27,28]. Recent investigations have attracted more attention on combining covering-based rough set and fuzzy set theories. There are many fuzzy covering rough set models proposed by researchers, such as Ma [29] and Yang et al. [30].
Smarandache [31] and Wang et al. [32] presented single valued neutrosophic (SVN) sets, which can be regarded as an extension of intuitionistic fuzzy sets [33]. Both neutrosophic sets and rough sets can deal with partial and uncertainty information [34]. Therefore, it is necessary to combine them. Recently, Mondal and Pramanik [35] presented the concept of rough neutrosophic set. Yang et al. [36] presented a SVN rough set model based on SVN relations. Wang and Zhang [37] presented two types of SVN covering rough set models. All these SVN rough set models are presented based on an inclusion relation which is named type-1 inclusion relation and denoted by . The definition of is shown as follows; for any ,
Under the type-1 inclusion relation, for two SVN numbers and , we have , and . The definition of SVN -covering approximation space is presented as follows (see the work by the authors of [37]).
Let U be a universe and be the SVN power set of U. For a SVN number , we call , with , a SVN -covering of U, if for all , exists such that . We also call a SVN -covering approximation space.
However, there exists another inclusion relation in the work by the authors of [38], which is called type-2 inclusion relation and denoted by . The definition of is introduced as follows; for any ,
Under the type-2 inclusion relation, for two SVN numbers and , we have , and .
In the definition of SVN -covering approximation space, if is replaced by , there will be a new SVN covering approximation space (we call it a SVN -covering approximation space in this paper). In Example 1 in this paper, we find the following statements.
- (1)
- Let . Then is a SVN -covering of U, but it is not a SVN -covering of U.
- (2)
- Let . Then is a SVN -covering of U, but it is not a SVN -covering of U.
That is to say, the SVN -covering approximation space is a new SVN covering approximation space, which is different from the SVN -covering approximation space. Since different inclusion relations ( and ) have different union and intersection operations, the SVN -covering approximation space has different union and intersection operations from the SVN -covering approximation space. Hence, notions and corresponding SVN covering rough set models of SVN -covering approximation space do not apply to SVN -covering approximation space, which is the justification for studying this topic. Therefore, the investigation of the SVN -covering approximation space and its corresponding SVN covering rough set model is very important. It not only can manage some issues that the SVN -covering approximation space can not deal with, but also constructs a new type of SVN covering rough set model. This is our motivation of this research.
In this paper, we present some new concepts in SVN -covering approximation space, as well as their properties. Then the type-2 SVN covering rough set model under the SVN -covering approximation space is proposed. On the one hand, the graph and matrix representations of the type-2 SVN covering rough set model are investigated respectively. Moreover, some relationships between the type-2 SVN covering rough set model and other SVN rough set models are presented. One the other hand, we present a method to DM problems in paper defect diagnosis, which is an important topic in paper making industries, under the type-2 SVN covering rough set model. Many researchers have studied decision making (DM) problems by rough set models [39,40,41,42]. Hence, the proposed DM method is compared with other methods which are presented by Liu [43], Ye [44], Yang et al. [36], and Wang et al. [37] respectively.
The rest of this paper is organized as follows. Section 2 reviews some fundamental definitions about covering-based rough sets and SVN sets. In Section 3, some concepts and properties in SVN -covering approximation space are studied. The relationship between the SVN -covering approximation space and the SVN -covering approximation space is presented. In Section 4, we present the type-2 SVN covering rough set model. Some relationships between the type-2 SVN covering rough set model and other SVN rough set models are presented. Moreover, a SVN relation can be induced by the SVN -covering, so a corresponding SVN relation rough set model and two conditions under which the SVN -covering can induce a symmetric SVN relation are presented. In Section 5, some new graphs and graph operations are presented. Based on this, the graph representation of the type-2 SVN covering approximation operators is shown. In Section 6, some new matrices and matrix operations are also presented, and the matrix representation of the type-2 SVN covering approximation operators is presented. In Section 7, a novel method to paper defect diagnosis is presented under the type-2 SVN covering rough set model. Moreover, the proposed method is compared with other methods. This paper is concluded and further work is indicated in Section 8.
2. Basic Definitions
Suppose U is a nonempty and finite set called universe.
Definition 1.
(Covering [45,46]) Let U be a universe and be a family of subsets of U. If none of subsets in is empty and , then is called a covering of U.
The pair is called a covering approximation space.
Definition 2.
(SVN set [32]) Let U be a nonempty fixed set. A SVN set A in U is defined as an object of the following form.
where is called the degree of truth-membership of the element to A, is called the degree of indeterminacy-membership of the element to A, is called the degree of falsity-membership. They satisfy for all . The family of all SVN sets in U is denoted by . For convenience, a SVN number is represented by , where and .
For the inclusion relation of neutrosophic sets, there are two different definitions in the literature. An original definition is proposed by Smarandache [31,47], we call it type-1 inclusion relation in this paper, denoted by . For set theory, union and intersection operations are corresponding to inclusion relation. Hence, there are corresponding union and intersection operations defined as follows; for any ,
- (1)
- iff , and for all ;
- (2)
- ;
- (3)
- .
Specially, for two SVN numbers, and , , and .
Under the type-1 inclusion relation, Wang and Zhang [37] presented the definition of SVN -covering approximation space.
Definition 3.
[37] Let U be a universe and be the SVN power set of U. For a SVN number , we call , with , a SVN β-covering of U, if for all , exists such that . We also call a SVN β-covering approximation space.
Definition 4.
[37] Let be a SVN β-covering of U and . For any , the SVN β-neighborhood of x induced by can be defined as
Another one is used in some papers [32,38], we call it type-2 inclusion relation in this paper, denote it by . Hence, the type-2 inclusion relation, corresponding union and intersection operations are shown as follows; for any ,
- (1)
- iff , and for all ;
- (2)
- ;
- (3)
- .
Specially, for two SVN numbers and , , and .
For the above inclusion relations of neutrosophic sets, the following operations use the same definition in this paper [32,36].
- (4)
- iff and , iff and ;
- (5)
- ;
- (6)
- .
3. SVN -Covering Approximation Space
In this section, the definition of SVN -covering approximation space is presented. There are two basic concepts—SVN -covering and SVN -neighborhood—in this new approximation space.
Definition 5.
Let U be a universe and be the SVN power set of U. For a SVN number , we call , with , a SVN -covering of U, if for all , exists such that . We also call a SVN -covering approximation space.
In Definition 5, if is replaced by , then is called a SVN -covering of U in [37]. By the definitions of and , we know if is a SVN -covering of U, then is not necessarily a SVN -covering. To show the difference between SVN -covering and SVN -covering, we use the work presented by the authors of [37] in the following example.
Example 1.

Let , and . We can see that is a SVN -covering of U in Table 1, but it is not a SVN β-covering of U.

Table 1.
The tabular representation of in [37].
Conversely, if is a SVN -covering of U, then is not necessarily a SVN -covering. In Example 1, suppose . Then is a SVN -covering of U, but it is not a SVN -covering of U.
By the definition of SVN -neighborhood, the notion of SVN -neighborhood is presented in the following definition.
Definition 6.
Let be a SVN -covering of U and . For any , the SVN -neighborhood of x induced by can be defined as
Note that is a SVN number . Hence, means , and , where SVN number .
Remark 1.
Let be a SVN -covering of U, and . For any ,
Example 2.

Let be a SVN -covering approximation space in Example 1 and . Then
Hence, all SVN -neighborhoods are shown in Table 2:

Table 2.
The tabular representation of ().
According to Definitions 3–6, we know that “Let be a SVN -covering of U. If is also a SVN -covering of U, then and have no inclusion relations ( and ) for all . To explain this statement, the following example is presented.
Example 3.


Let , and , where is shown in Table 1 of Example 1. By Definitions 3 and 5, we know that is a SVN -covering and also a SVN β-covering of U. Then

Table 3.
The tabular representation of ().

Table 4.
The tabular representation of ().
- is not established, since .
- is not established, since .
- is not established, since .
- is not established, since .
Hence, and have no inclusion relations ( and ) for all .
In a SVN -covering approximation space , we present the following properties of the SVN -neighborhood.
Proposition 1.
Let be a SVN -covering of U and . Then for each .
Proof.
For any , . □
Proposition 2.
Let be a SVN -covering of U and . For all , if , , then .
Proof.
Let . Since , for any , if , then . Since , for any , when . Then, for any , implies . Therefore, . □
Proposition 3.
Let be a SVN -covering of U and . For two SVN numbers , if , then for all .
Proof.
For all , since , . Hence, for all . □
Proposition 4.
Let be a SVN -covering of U. For any , if and only if .
Proof.
and
.
Suppose the SVN number .
Then,
.
Therefore, for each ,
Hence, .
: For any , since ,
Therefore, . □
4. A Type of SVN Covering Rough Set Model Based on a New Inclusion Relation
In this section, we propose a type of SVN covering rough set model on the basis of the SVN -neighborhoods, which is decided by a type-2 inclusion relation. Then, we investigate some properties of the new lower and upper SVN covering approximation operators. Finally, some relationships between this model and some other rough set models are presented.
4.1. Characteristics of the New Type of SVN Covering Rough Set Model Based on the New Inclusion Relation
Definition 7.
Let be a SVN -covering approximation space. For each , where , we define the type-2 SVN covering upper approximation and lower approximation of A as
If , then A is called the type-2 SVN covering rough set.
Example 4.
Let be a SVN -covering approximation space in Example 1, and . Then all SVN -neighborhoods () are shown in Table 2 of Example 2. By Definition 7, we have
Let the SVN universe set be and the SVN empty set be , which are decided by the type-2 inclusion relation . Some basic properties of the type-2 SVN covering upper and lower approximation operators are presented in the following proposition.
Proposition 5.
Let be a SVN -covering of U. Then the type-2 SVN covering upper and lower approximation operators in Definition 7 satisfy the following properties for all .
- (1)
- , ;
- (2)
- , ;
- (3)
- If , then , ;
- (4)
- , ;
- (5)
- , .
Proof.
- (1)
- Since the SVN universe set is and the SVN empty set is ,and
- (2)
- If we replace A by in this proof, we can also prove .
- (3)
- Since , , and for all . ThereforeHence, . In the same way, there is ;
- (4)
- SinceSimilarly, we can obtain ;
- (5)
- Since , , and ,, , and .Hence, , . □
4.2. Relationships between the New Model and Some Other Rough Set Models
In this subsection, we investigate some relationships between the type-2 SVN covering rough set model and other two SVN rough set models respectively. Among these two SVN rough set models, one is a SVN covering rough set model and the other is a SVN relation rough set model.
Wang and Zhang [37] presented the type-1 SVN covering rough set model under a SVN -covering approximation space, which is related to the type-1 inclusion relation. We consider whether the type-1 SVN covering approximate operators and the type-2 SVN covering approximate operators presented in Section 4.1 have inclusion relations.
Definition 8.
[37] Let be a SVN β-covering approximation space. For each , where , we define the type-1 SVN covering upper approximation and lower approximation of A as
If , then A is called the type-1 SVN covering rough set.
Let be a SVN -covering of U and also be a SVN -covering of U. By Definitions 7 and 8, we know that the type-1 SVN covering approximate operators ( and ) and the type-2 SVN covering approximate operators ( and ) are related to all SVN -neighborhoods (, for any ) and SVN -neighborhoods (, for any ), respectively. By Example 3, we know that and have no inclusion relations ( and ) for all . Hence, the type-1 SVN covering approximate operators and the type-2 SVN covering approximate operators also have no inclusion relations ( and ).
In the work by the authors of [36], a SVN relation R on U is defined as }, where , and . If for any , , and , then R is called a symmetric SVN relation.
For a SVN -covering of U, one can use the SVN -covering induce a SVN relation on U as
where
The following two propositions present two conditions under which is a symmetric SVN relation.
Proposition 6.
Let be a SVN -covering of U, and be the induced SVN relation on U by . If for any , then is a symmetric SVN relation.
Proof.
Since for any , , and . Hence, , and , i.e., is a symmetric SVN relation. □
Proposition 7.
Let be a SVN -covering of U, be the induced SVN relation on U by , and . If and for any , then is a symmetric SVN relation, where denotes the cardinality of .
Proof.
Since , C is the only one element of . Since for any , . Hence, , and , i.e., is a symmetric SVN relation. □
Then, the type-2 SVN covering rough set model defined in Section 4.1 can be viewed as a SVN relation rough set model.
Definition 9.
Let be a SVN -covering of U, and be the induced SVN relation on U by . For any , the upper approximation and lower approximation of A are defined as
Remark 2.
Let be a SVN -covering of U, and be the induced SVN relation on U by . Then
5. Graph Representation of the Type-2 SVN Covering Rough Set Model
In this section, the graph representation of the type-2 SVN covering rough set model is presented. Firstly, some new graphs and graph operations are presented. Then, we show the graph representation of the type-2 SVN covering approximation operators defined in Definition 7. The order of elements in U is given.
A graph is a pair consisting of a nonempty set V of vertices and a set E of edges such that . We shall often write for V and for E, particularly when several graphs are being considered. Two vertices are adjacent if there is an edge with them as ends. A graph is called bipartite if the vertex set V can be divided into two disjoint sets and , such that every edge connects a vertex in to one in . One often writes to denote a bipartite graph whose partition has the partite sets and . A complete bipartite graph is a simple bipartite graph such that two vertices are adjacent if and only if they are in different partite sets. A weighted graph is a graph with numerical labels on the edges.
Firstly, the graph representation of the SVN -covering is defined in the following definition.
Definition 10.
Let be a SVN -covering of U with and . For any , we define a completely weighted bipartite graph , named completely weighted bipartite graph associated with A, where , the weight , and (). For the SVN β-covering , there are m completely weighted bipartite graphs (), and all are called the graph representation of the SVN -covering .
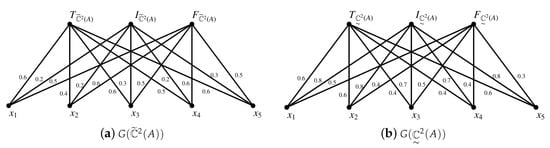
Example 5.
Let be a SVN -covering approximation space in Example 1 and . Then () are the graph representation of the SVN -covering . All () are shown in Figure 1 and Figure 2.

Figure 1.
and .

Figure 2.
and .
An intersection operation about and is presented in the following definition, for any .
Definition 11.
Let be a SVN -covering of U with and . For any , we define a completely weighted bipartite graph associated with D, where and
Based on Definition 11 and the definition of , the relationship between and can be obtained for any .
Lemma 1.
Let be a SVN -covering of U. Then for any .
Proof.
According to the definition of and Definition 11, it is immediate. □
By Definition 6, for any . Hence, any is a completely weighted bipartite graph, which can be represented in the following proposition.
Proposition 8.
Let be a SVN -covering of U with , and . Then
Proof.
By Definitions 6 and 11, and Lemma 1, it is immediate. □
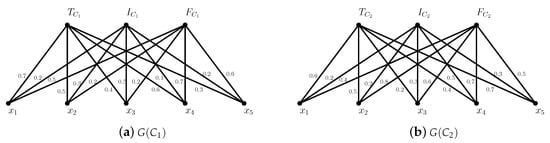
Example 6.
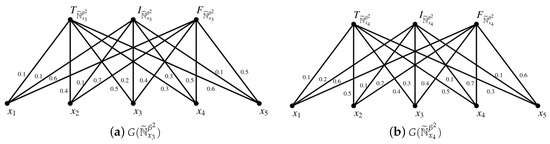
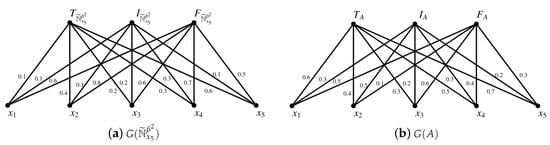
Let be a SVN -covering approximation space in Example 1 and . By Proposition 8, we have

Figure 3.
and .

Figure 4.
and .

Figure 5.
and .
Finally, the type-2 SVN covering upper approximation and lower approximation of A are represented by graphs.
Theorem 1.
Let be a SVN -covering of U with . For each , and are completely weighted bipartite graphs, where , and the weight of any edge is listed as follows.
Proof.
According to Definition 7, we know and for any . Hence, and are completely weighted bipartite graphs by Definition 10. According to Definitions 7 and 10, , and the weight of any edge is shown as follows.
□
6. Matrix Representation of the Type-2 SVN Covering Rough Set Model
In this section, the matrix representation of the type-2 SVN covering rough set model is investigated. Firstly, some new matrices and matrix operations are presented. Then, we show the matrix representation of the type-2 SVN approximation operators defined in Definition 7. The order of elements in U is given.
Two new matrices about a SVN -covering are presented in the following definition.
Definition 12.
Let be a SVN -covering of U with and . Then is named a matrix representation of , and is called a -matrix representation of , where
Example 8.
Let be a SVN -covering approximation space in Example 1 and . Then
In order to calculate all (for any ) by matrices, the following operation is presented.
Definition 13.
Let and be two matrices. We define , where
Based on Definitions 12 and 13, all (for any ) can be obtained by matrix operations.
Proposition 9.
Let be a SVN -covering of U with and .
Then
where is the transpose of
Proof.
Suppose , and . Since is a SVN -covering of U, for each i (), there exists k () such that .
Then
Hence, . □
Example 9.
Let be a SVN -covering approximation space in Example 1 and . According to and in Example 8, we have
There are two operations in the work by the authors of [37], which can be used to calculate and (for any ) by matrices.
Definition 14.
[37] Let and be two matrices. We define and , where
According to Proposition 9 and Definition 14, the set representations of and (for any ) can be converted to matrix representations. with is the vector representation of A. and are also vector representations.
Theorem 2.
Let be a SVN -covering of U with and . Then for any ,
Proof.
According to Proposition 9, Definitions 7 and 14, for any (),
and
Hence, . □
Example 10.
Let be a SVN -covering approximation space in Example 1, and . Then
7. An Application to DM Problems in Paper Defect Diagnosis
Under the type-2 SVN covering rough set model, we present a novel approach to DM problems in paper defect diagnosis in this section.
7.1. The Problem of DM in Paper Defect Diagnosis
Let be the set of papers and be the m main symptoms (for example, spot, steak, and so on) for a paper defect B. Assume that an inspector R evaluate every paper ().
Assume that the inspector R believes each paper () has a symptom value () denoted by , where is the degree that inspector R confirms paper has symptom , is the degree that inspector R is not sure paper has symptom , is the degree that inspector R confirms paper does not have symptom , and .
Let be the critical value. If any paper , there is at least one symptom such that the symptom value for the paper is not less than (i.e., ), respectively, then is a SVN -covering of U for some SVN number .
If d is a possible degree, e is an indeterminacy degree and f is an impossible degree of the paper defect B of every paper that is diagnosed by the inspector R, denoted by , then the decision maker (the inspector R) for the DM problem needs to know how to evaluate whether the papers have the paper defect B or not.
7.2. The DM Algorithm
In this subsection, we give an approach for the problem of DM with the above characterizations using the type-2 SVN covering rough set model. According to the characterizations of the DM problem in Section 7.1, we construct the SVN decision information system and present the Algorithm 1 of DM under the framework of the type-2 SVN covering rough set model.
| Algorithm 1 The DM algorithm under the type-2 SVN covering rough set model |
| Input: SVN decision information system (). |
Output: The score ordering for all alternatives.
|
According to the above process, we can get the DM according to the ranking. In Step 4, is the cosine similarity measure between and the ideal solution , which is proposed by Ye [44].
7.3. An Applied Example
Example 11.

Assume that is a set of papers. According to the paper defects’ symptoms, we write to be four main symptoms (spot, steak, crater, and fracture) for a paper defect B. Assume that the inspector R evaluates every paper () as shown in Table 1.
Let be the critical value. Then, is a SVN -coverings of U. Assume that the inspector R diagnosed the value of the paper defect B of every paper.
Step 1: () are shown in Table 2.
Step 2:
Step 3:
Step 4: We can obtain () in Table 5.

Table 5.
().
Step 5: According to the principle of numerical size, we have
.
Therefore, the inspector R diagnoses the paper as more likely to be sick with the paper defect B.
7.4. A Comparison Analysis
To validate the feasibility of the proposed DM method, a comparative study is conducted with other methods. These methods which were introduced in Liu [43], Ye [44], Yang et al. [36], and Wang et al. [37] are compared with the proposed approach using SVN information system.
Because Table 1 is the same as in the work by the authors of [37] and the counting processes of the methods presented by Liu [43], Ye [44], Yang et al. [36], and Wang et al. [37], are shown in the work by the authors of [37], so we do not show these counting processes in this paper. For Example 11, the results of them are calculated as follows.
- In Liu’s method, we suppose the weight vector of the criteria is and . Hence, we getAccording to the cosine similarity degrees (), we obtain
- In Ye’s method, we suppose the weight vector of the criteria is . ThenAccording to all (), we obtain
- In Yang’s method, we suppose paper defect and . Let . We getThen,According to all (), we obtain
- In Wang’s method, we do not use in Example 11, and the reason is explained later. We suppose in Wang’s method. ThenHence,According to all (), we obtain

Table 6.
The results utilizing the different methods of Example 11.
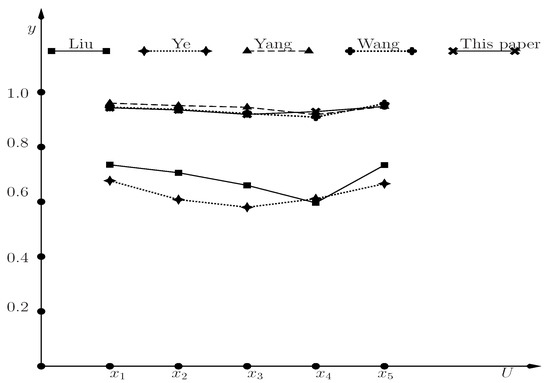
Figure 7.
The chat of different values of patient in utilizing different methods in Example 11.
Liu [43] and Ye [44] presented the methods by SVN theory. The method developed by Liu [43] is based on the Hammer SVN number aggregation (HSVNNWA) operator, the ranking order willed be changed by different and . The parameter can be regarded as an attitude of the decision maker’s preferences. For Example 11, we set the weight vector of the criteria is and , then we obtain . The method developed by Ye [44] is based on the weighted correlation coefficient or the weighted cosine similarity measure , where is the ideal alternative. We can get two ranking orders of by the values of and , respectively. Then, we find that these two kinds of ranking orders are the same. Hence, we only show in this paper. In Table 6 and Figure 7, there are the same ranking results of their methods.
Yang et al. [36] and Wang et al. [37] used different SVN rough set models to make a decision. The method presented by Yang et al. [36] is based on a SVN relation rough set model on two-universes. That is to say, the DM problems with SVN information can be dealt with by Yang’s method when it induces a SVN relation on two-universes. In Example 11, we obtain a SVN relation on two universes from Table 1. The method presented by Wang et al. [37] based on the type-1 SVN covering rough set model. That is to say, the DM problems with SVN information can be dealt with by Wang’s method when it can induce a SVN -covering. In Example 11, we suppose . However, is not a SVN -covering of U when . Hence, the method presented by Wang et al. can not be used in Example 11 when . Let’s re-assume . Then is a SVN -covering of U. Hence, the method presented by Wang et al. can be used in Example 11 when .
In this paper, we present the type-2 SVN covering rough set model based on SVN -coverings. Under the type-2 SVN covering rough set model, a novel method for DM problems with SVN information is presented. The contributions of our proposed method are summarized as follows.
- (1)
- The DM problems with SVN information can be dealt with by our proposed method when it can induce a SVN -covering. The method presented by Wang et al. [37] can not be used in Example 11 when . But our proposed method can deal with Example 11 when . Hence, our proposed method complements Wang’s.
- (2)
- It is a new viewpoint to use SVN sets and rough sets in paper defect diagnosis.
Using different methods, the obtained results may be different. To achieve the most accurate results, further diagnosis is necessary for combination with other hybrid methods.
8. Conclusions
This paper investigates a new type of SVN covering rough set model, which can be seen as a new bridge linking SVN sets and covering-based rough sets. Comparing the existing literatures [36,37,48,49], the main contributions of this paper are concluded as follows.
- (1)
- By introducing some definitions and properties in SVN -covering approximation spaces, we present the type-2 SVN covering rough set model based on the type-2 inclusion relation. The existing literatures [36,37,48,49] used the type-1 inclusion relation to study the combination of SVN sets and rough sets. Hence, this paper presents a new and interesting viewpoint to study the combination of SVN sets and rough sets.
- (2)
- It would be tedious and complicated to use set representation to calculate the new SVN covering approximation operators. Therefore, the graph and matrix representations of these new SVN covering approximation operators make it possible to calculate them. We are the first to study the equivalent representation of the SVN rough set model by graph theory. By these graph and matrix representations, calculations will become algorithmic and can be easily implemented by computers.
- (3)
- Paper defect diagnosis is important in paper making industries. We propose a method to paper defect diagnosis under the type-2 SVN covering rough set model. The proposed DM method is compared with other methods which are presented by Liu [43], Ye [44], Yang et al. [36], and Wang et al. [37], respectively.
Further study will be deserved by the following research topics. On the one hand, the type-2 inclusion relation or graph theory can be considered into other SVN rough set models [34,36,48,49] in future research. On the other hand, neutrosophic sets and related algebraic structures [50,51,52,53,54,55] will be connected with the research content of this paper in further research.
Author Contributions
All authors have contributed equally to this paper. The idea of this whole thesis was put forward by X.Z., he also completed the preparatory work of the paper. J.W. analyzed the existing work of the rough sets and SVN sets and wrote the paper.
Funding
This work is supported by the National Natural Science Foundation of China under Grant Nos. 61976130 and 61573240, and the Natural Science Foundation of Education Department of Shaanxi Province, China, under Grant No. 19JK0506.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Pawlak, Z. Rough sets. Int. J. Comput. Inf. Sci. 1982, 11, 341–356. [Google Scholar] [CrossRef]
- Pawlak, Z. Rough Sets: Theoretical Aspects of Reasoning About Data; Kluwer Academic Publishers: Boston, MA, USA, 1991. [Google Scholar]
- Kondo, M. On the structure of generalized rough sets. Inf. Sci. 2006, 176, 589–600. [Google Scholar] [CrossRef]
- Wang, C.; Chen, D.; Wu, C.; Hu, Q. Data compression with homomorphism in covering information systems. Int. J. Approx. Reason. 2011, 52, 519–525. [Google Scholar] [CrossRef]
- Wang, S.; Zhu, W.; Zhu, Q.; Min, F. Characteristic matrix of covering and its application to Boolean matrix decomposition. Inf. Sci. 2014, 263, 186–197. [Google Scholar] [CrossRef]
- Bartol, W.; Miro, J.; Pioro, K.; Rossello, F. On the coverings by tolerance classes. Inf. Sci. 2004, 166, 193–211. [Google Scholar] [CrossRef]
- Bianucci, D.; Cattaneo, G.; Ciucci, D. Entropies and co-entropies of coverings with application to incomplete information systems. Fundam. Inf. 2007, 75, 77–105. [Google Scholar]
- Zhu, W. Relationship among basic concepts in covering-based rough sets. Inf. Sci. 2009, 179, 2478–2486. [Google Scholar] [CrossRef]
- Zhu, W. Topological approaches to covering rough sets. Inf. Sci. 2007, 177, 1499–1508. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, X. Matrix approaches for some issues about minimal and maximal descriptions in covering-based rough sets. Int. J. Approx. Reason. 2019, 104, 126–143. [Google Scholar] [CrossRef]
- Yao, Y.; Zhao, Y. Attribute reduction in decision-theoretic rough set models. Inf. Sci. 2008, 178, 3356–3373. [Google Scholar] [CrossRef]
- Li, F.; Yin, Y. Approaches to knowledge reduction of covering decision systems based on information theory. Inf. Sci. 2009, 179, 1694–1704. [Google Scholar] [CrossRef]
- Wu, W. Attribute reduction based on evidence theory in incomplete decision systems. Inf. Sci. 2008, 178, 1355–1371. [Google Scholar] [CrossRef]
- Lang, G.; Li, Q.; Cai, M.; Fujita, H.; Zhang, H. Related families-based methods for updating reducts under dynamic object sets. Knowl. Inf. Syst. 2019, 60, 1081–1104. [Google Scholar] [CrossRef]
- Wang, J.; Zhu, W. Applications of bipartite graphs and their adjacency matrices to covering-based rough sets. Fundam. Inf. 2017, 156, 237–254. [Google Scholar] [CrossRef]
- Li, X.; Yi, H.; Liu, S. Rough sets and matroids from a lattice-theoretic viewpoint. Inf. Sci. 2016, 342, 37–52. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, X. Four operators of rough sets generalized to matroids and a matroidal method for attribute reduction. Symmetry 2018, 10, 418. [Google Scholar] [CrossRef]
- Wang, J.; Zhu, W.; Wang, F.; Liu, G. Conditions for coverings to induce matroids. Int. J. Mach. Learn. Cybern. 2014, 5, 947–954. [Google Scholar] [CrossRef]
- Chen, J.; Li, J.; Lin, Y.; Lin, G.; Ma, Z. Relations of reduction between covering generalized rough sets and concept lattices. Inf. Sci. 2015, 304, 16–27. [Google Scholar] [CrossRef]
- Zhang, X.; Dai, J.; Yu, Y. On the union and intersection operations of rough sets based on various approximation spaces. Inf. Sci. 2015, 292, 214–229. [Google Scholar] [CrossRef]
- D’eer, L.; Cornelis, C. A comprehensive study of fuzzy covering-based rough set models: Definitions, properties and interrelationships. Fuzzy Sets Syst. 2018, 336, 1–26. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, X. Two types of intuitionistic fuzzy covering rough sets and an application to multiple criteria group decision making. Symmetry 2018, 10, 462. [Google Scholar] [CrossRef]
- Zhang, X.; Miao, D.; Liu, C.; Le, M. Constructive methods of rough approximation operators and multigranulation rough sets. Knowl.-Based Syst. 2016, 91, 114–125. [Google Scholar] [CrossRef]
- Zadeh, L.A. Fuzzy sets. Inf. Control 1965, 8, 338–353. [Google Scholar] [CrossRef]
- Jankowski, J.; Kazienko, P.; Watróbski, J.; Lewandowska, A.; Ziemba, P.; Zioło, M. Fuzzy multi-objective modeling of effectiveness and user experience in online advertising. Expert Syst. Appl. 2016, 65, 315–331. [Google Scholar] [CrossRef]
- Boloş, M.I.; Bradea, I.A.; Delcea, C. A fuzzy logic algorithm for optimizing the investment decisions within companies. Symmetry 2019, 11, 186. [Google Scholar] [CrossRef]
- Pozna, C.; Minculete, N.; Precup, R.E.; Kóczy, L.T.; Ballagi, Á. Signatures: Definitions, operators and applications to fuzzy modeling. Fuzzy Sets Syst. 2012, 201, 86–104. [Google Scholar] [CrossRef]
- Vrkalovic, S.; Lunca, E.C.; Borlea, I.D. Model-free sliding mode and fuzzy controllers for reverse osmosis desalination plants. Int. J. Artif. Intell. 2018, 16, 208–222. [Google Scholar]
- Ma, L. Two fuzzy covering rough set models and their generalizations over fuzzy lattices. Fuzzy Sets Syst. 2016, 294, 1–17. [Google Scholar] [CrossRef]
- Yang, B.; Hu, B. On some types of fuzzy covering-based rough sets. Fuzzy Sets Syst. 2017, 312, 36–65. [Google Scholar] [CrossRef]
- Smarandache, F. Neutrosophy, Neutrosophic Probability, Set, and Logic; American Research Press: Rehoboth, DE, USA, 1998. [Google Scholar]
- Wang, H.; Smarandache, F.; Zhang, Y.; Sunderraman, R. Single valued neutrosophic sets. Multispace Multistruct. 2010, 4, 410–413. [Google Scholar]
- Atanassov, K. Intuitionistic fuzzy sets. Fuzzy Sets Syst. 1986, 20, 87–96. [Google Scholar] [CrossRef]
- Al-Quran, A.; Hassan, N.; Marei, E. A novel approach to neutrosophic soft rough set under uncertainty. Symmetry 2019, 11, 384. [Google Scholar] [CrossRef]
- Mondal, K.; Pramanik, S. Rough neutrosophic multi-attribute decision-making based on grey relational analysis. Neutrosophic Sets Syst. 2015, 7, 8–17. [Google Scholar]
- Yang, H.; Zhang, C.; Guo, Z.; Liu, Y.; Liao, X. A hybrid model of single valued neutrosophic sets and rough sets: Single valued neutrosophic rough set model. Soft Comput. 2017, 21, 6253–6267. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, X. Two types of single valued neutrosophic covering rough sets and an application to decision making. Symmetry 2018, 10, 710. [Google Scholar] [CrossRef]
- Borzooei, R.A.; Farahani, H.; Moniri, M. Neutrosophic deductive filters on BL-algebras. J. Intell. Fuzzy Syst. 2014, 26, 2993–3004. [Google Scholar]
- Akram, M.; Ali, G.; Alshehri, N.O. A new multi-attribute decision-making method based on m-polar fuzzy soft rough sets. Symmetry 2017, 9, 271. [Google Scholar] [CrossRef]
- Zhan, J.; Ali, M.I.; Mehmood, N. On a novel uncertain soft set model: Z-soft fuzzy rough set model and corresponding decision making methods. Appl. Soft Comput. 2017, 56, 446–457. [Google Scholar] [CrossRef]
- Zhan, J.; Alcantud, J.C.R. A novel type of soft rough covering and its application to multicriteria group decision making. Artif. Intell. Rev. 2018, 4, 1–30. [Google Scholar] [CrossRef]
- Zhang, Z. An approach to decision making based on intuitionistic fuzzy rough sets over two universes. J. Oper. Res. Soc. 2013, 64, 1079–1089. [Google Scholar]
- Liu, P. The aggregation operators based on archimedean t-conorm and t-norm for single-valued neutrosophic numbers and their application to decision making. Int. J. Fuzzy Syst. 2016, 18, 849–863. [Google Scholar] [CrossRef]
- Ye, J. Multicriteria decision-making method using the correlation coefficient under single-valued neutrosophic environment. Int. J. Gen. Syst. 2013, 42, 386–394. [Google Scholar] [CrossRef]
- Pomykala, J.A. Approximation operations in approximation space. Bull. Pol. Acad. Sci. 1987, 35, 653–662. [Google Scholar]
- Bonikowski, Z.; Bryniarski, E.; Wybraniec-Skardowska, U. Extensions and intentions in the rough set theory. Inf. Sci. 1998, 107, 149–167. [Google Scholar] [CrossRef]
- Smarandache, F. Neutrosophic set—A generalization of the intuitionistic fuzzy set. J. Def. Resour. Manag. 2010, 1, 38–42. [Google Scholar]
- Bao, Y.; Yang, H. On single valued neutrosophic refined rough set model and its application. J. Intell. Fuzzy Syst. 2018, 33, 1235–1248. [Google Scholar] [CrossRef]
- Guo, Z.; Liu, Y.; Yang, H. A novel rough set model in generalized single valued neutrosophic approximation spaces and its application. Symmetry 2017, 9, 119. [Google Scholar] [CrossRef]
- Wu, X.; Zhang, X. The decomposition theorems of AG-neutrosophic extended triplet loops and strong AG-(l, l)-loops. Mathematics 2019, 7, 268. [Google Scholar] [CrossRef]
- Zhang, X.; Borzooei, R.A.; Jun, Y. Q-filters of quantum B-algebras and basic implication algebras. Symmetry 2018, 10, 573. [Google Scholar] [CrossRef]
- Zhang, X.; Mao, X.; Wu, Y.; Zhai, X. Neutrosophic filters in pseudo-BCI algebras. Int. J. Uncertain. Quantif. 2018, 8, 511–526. [Google Scholar] [CrossRef]
- Zhang, X.; Hu, Q.; Smarandache, F.; An, X. On neutrosophic triplet groups: basic properties, NT-subgroups, and some notes. Symmetry 2018, 10, 289. [Google Scholar] [CrossRef]
- Ma, Y.; Zhang, X.; Yang, X.; Zhou, X. Generalized neutrosophic extended triplet group. Symmetry 2019, 11, 327. [Google Scholar] [CrossRef]
- Zhang, X.; Wang, X.; Smarandache, F.; Jaíyéolá, T.G.; Lian, T. Singular neutrosophic extended triplet groups and generalized groups. Cognit. Syst. Res. 2019, 57, 32–40. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).