Clustering-Based Data Dissemination Protocol Using the Path Similarity for Autonomous Vehicles
Abstract
:1. Introduction
1.1. Clustering Algorithms
1.2. Path Similarity
2. Related Works and Problems
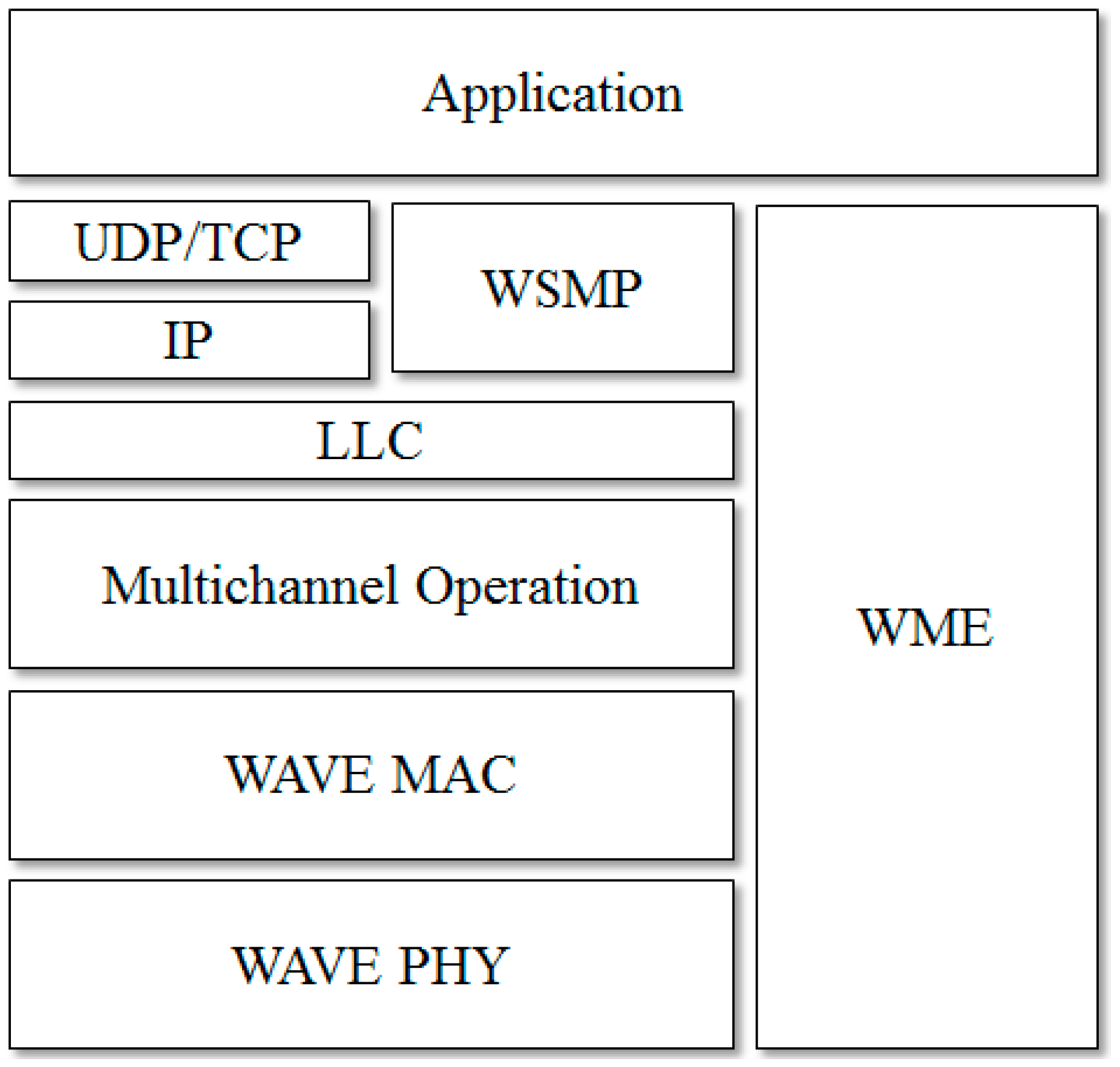
2.1. DSRC/WAVE
2.2. Data Dissemination Scheme Based on Clustering and Probabilistic Broadcasting
3. Proposed Method
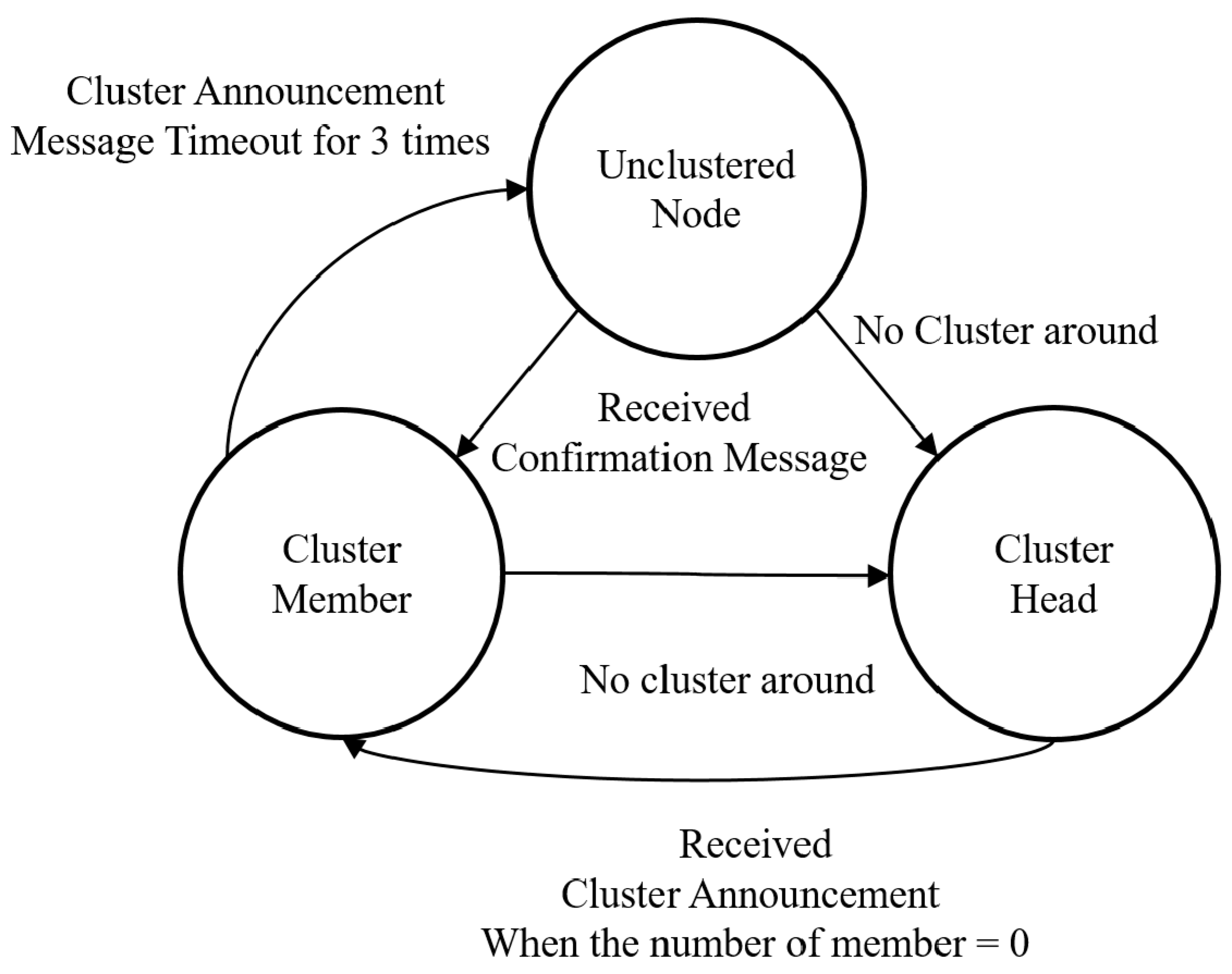
3.1. Term Definitions
3.2. Path-Based Clustering Model
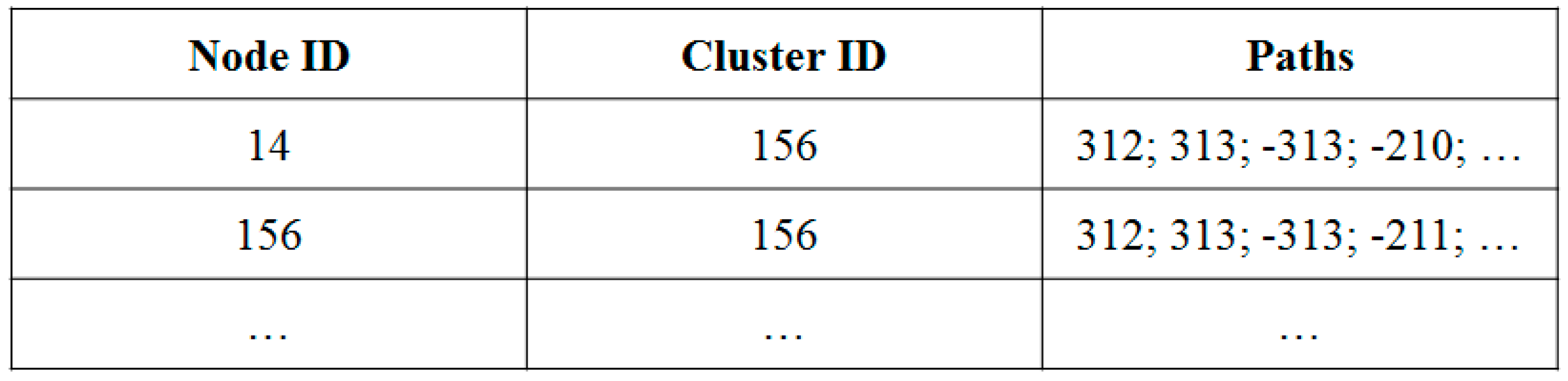
3.2.1. Concept Definitions
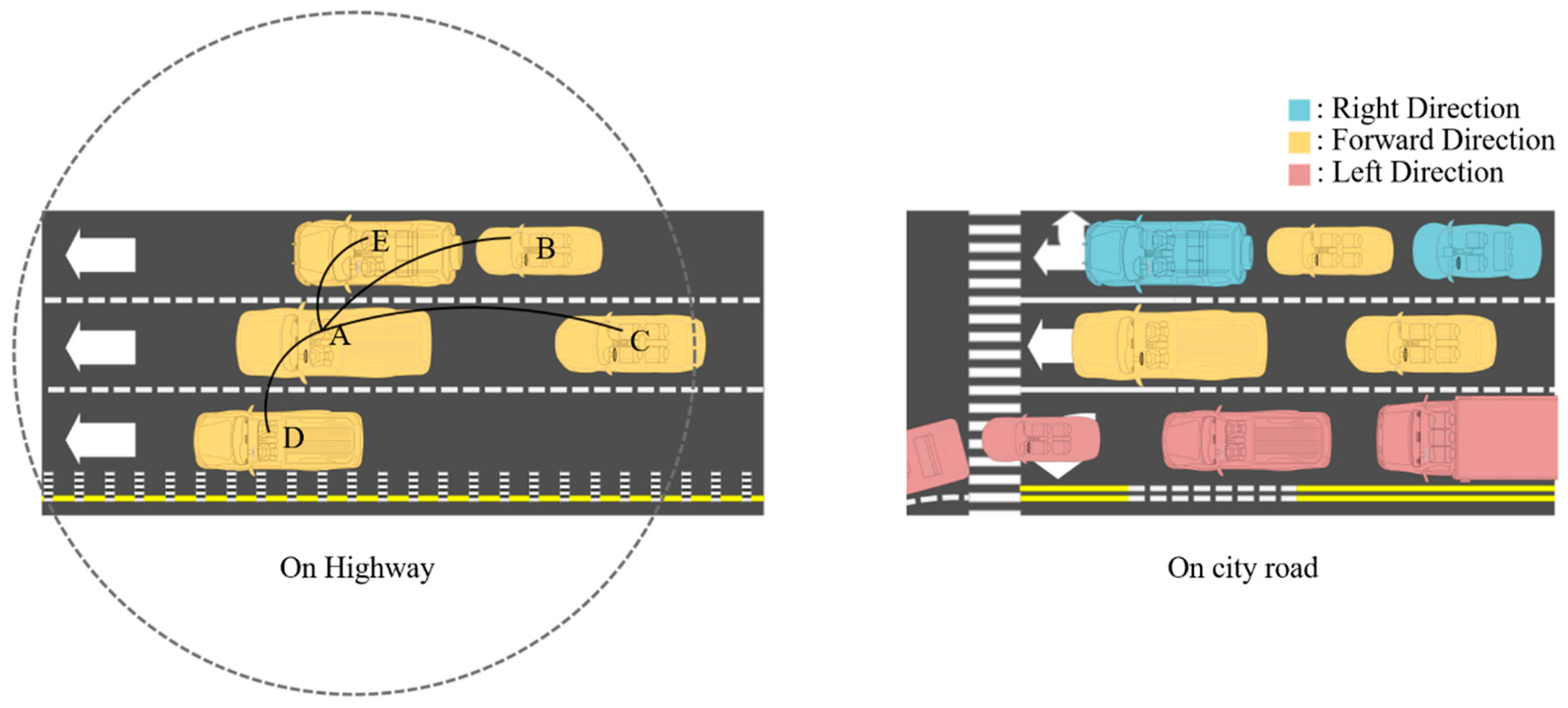
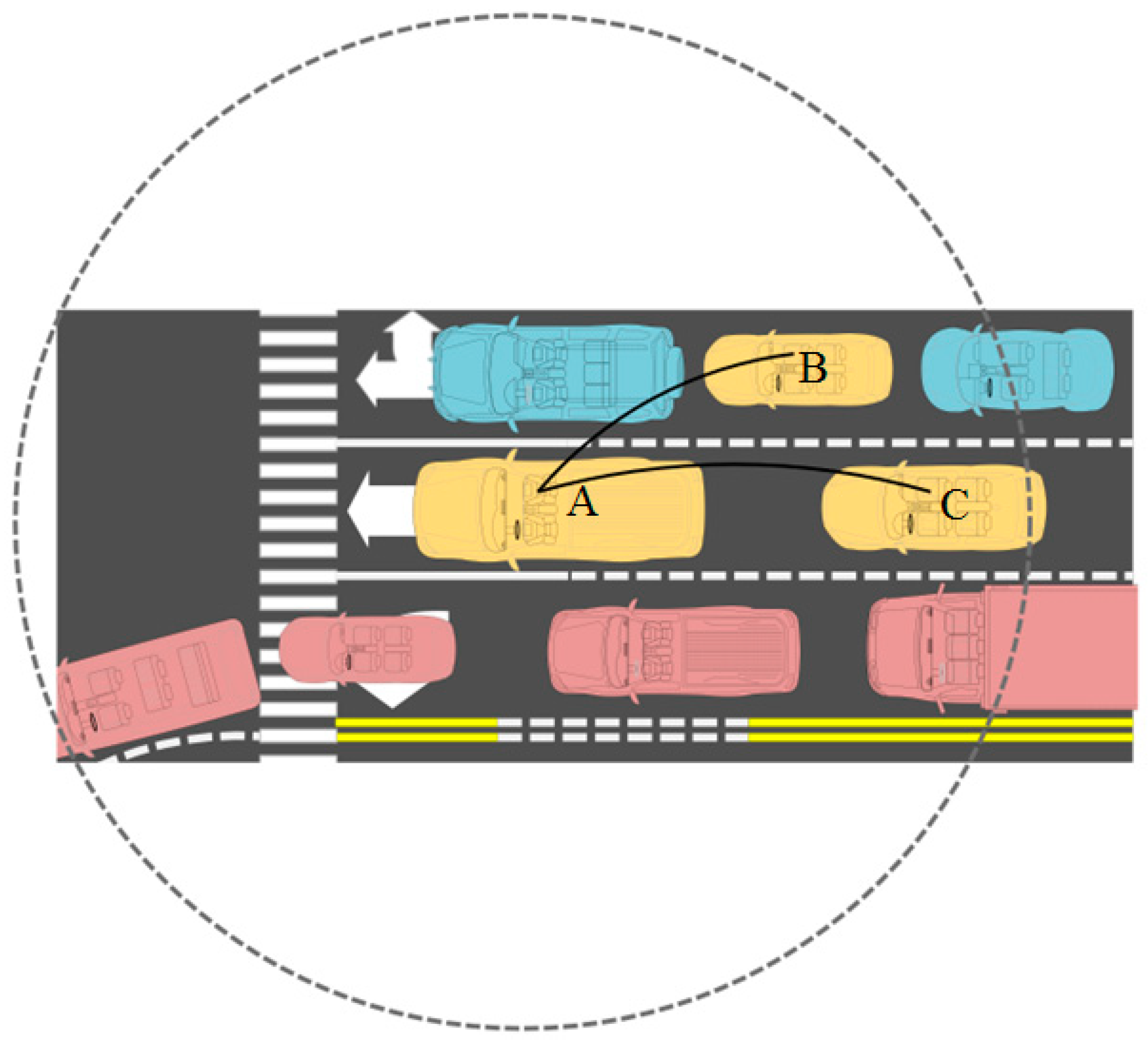
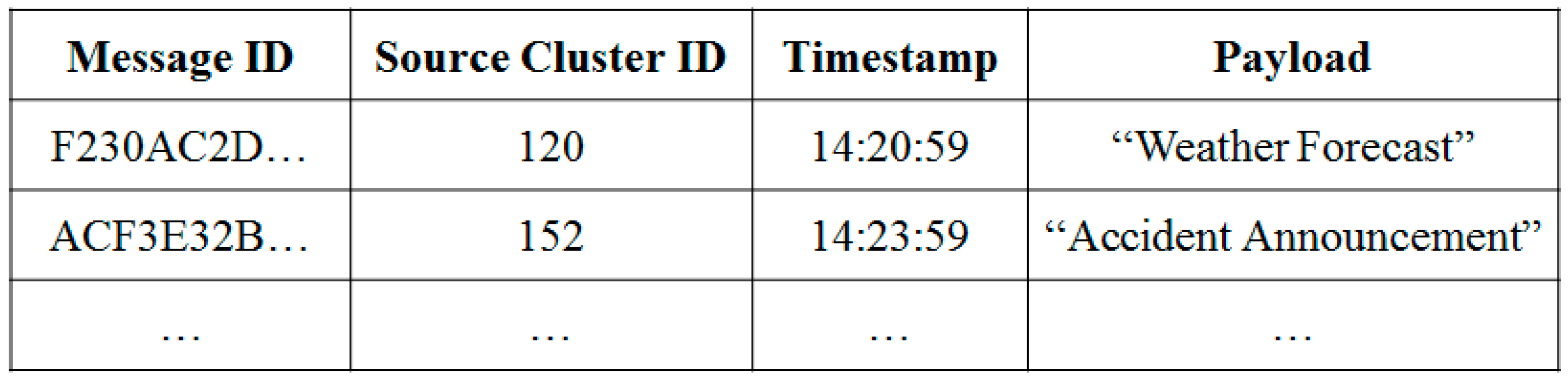
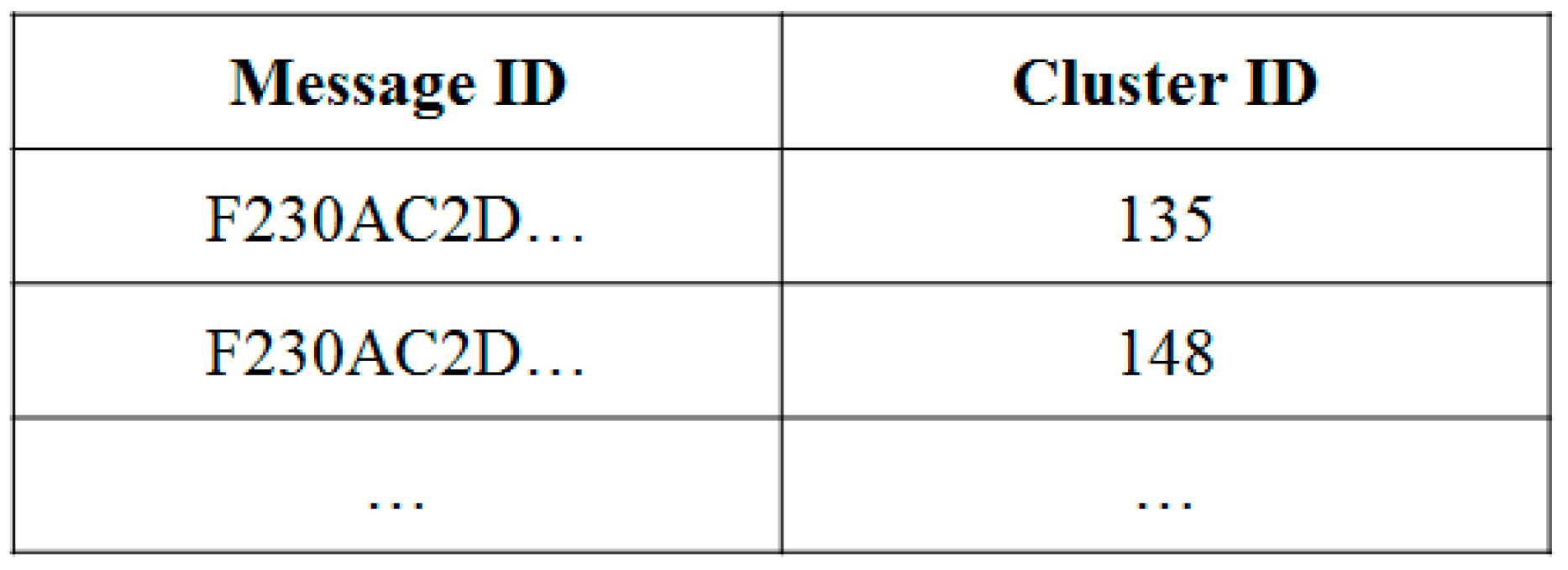
3.2.2. Use-Cases of PCDP
3.3. Clustering Algorithm for Applying the Path-based Clustering Model
3.3.1. Path Distance Algorithm
| Algorithm 1 Path distance algorithm | |
| 1. | Set i = 1, j = 1, d = 0 |
| 2. | For each rmi and rnj of pm, pn |
| 3. | If rmi is the same as rnj, then |
| 4. | Add 1 to i and j |
| 5. | Else then |
| 6. | Add 1 to i and d |
| 7. | Add (lm − j) to d |
| 8. | Set d as d over max(lm, ln) |
| Algorithm 2 Clustering algorithm with path distance | |
| 1. | Set b = 0, flg = false, parameter th, assign p |
| 2. | If there is a cluster head among neighbors, then |
| 3. | While not found proper cluster head and flg not set |
| 4. | For each |
| 5. | Calculate path distance dm |
| 6. | If dm < b, then |
| 7. | Set b = dm |
| 8. | Set p = m |
| 9. | If b < th, then |
| 10. | Send cluster assignment request to p |
| 11. | Else then |
| 12. | Set timer t |
| 13. | Else then |
| 14. | Broadcast cluster head announcement |
| 1. | Sub procedure t: |
| 2. | If there is no dm lower than th, then |
| 3. | Send cluster head announcement |
3.3.2. Clustering Process
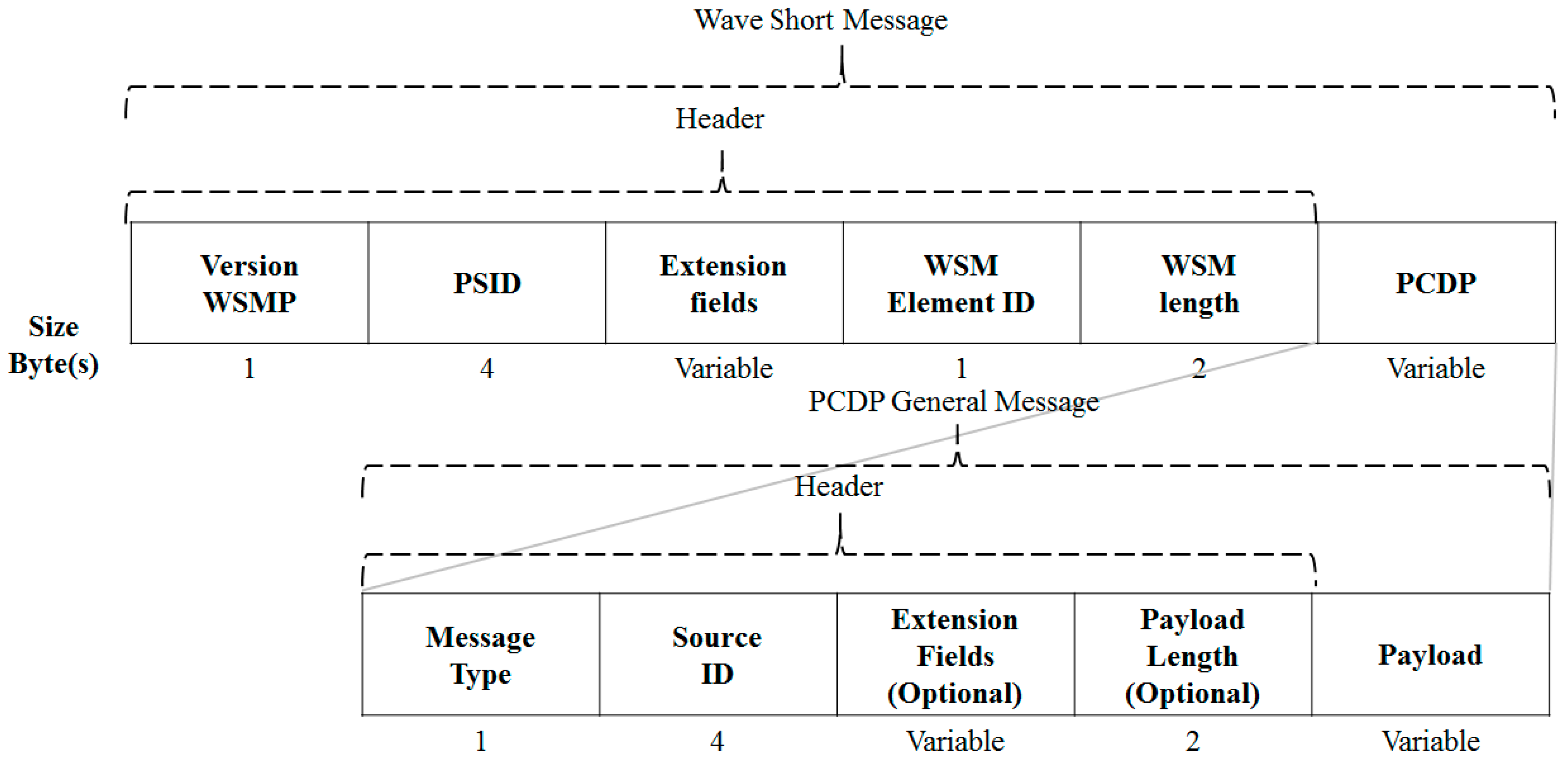
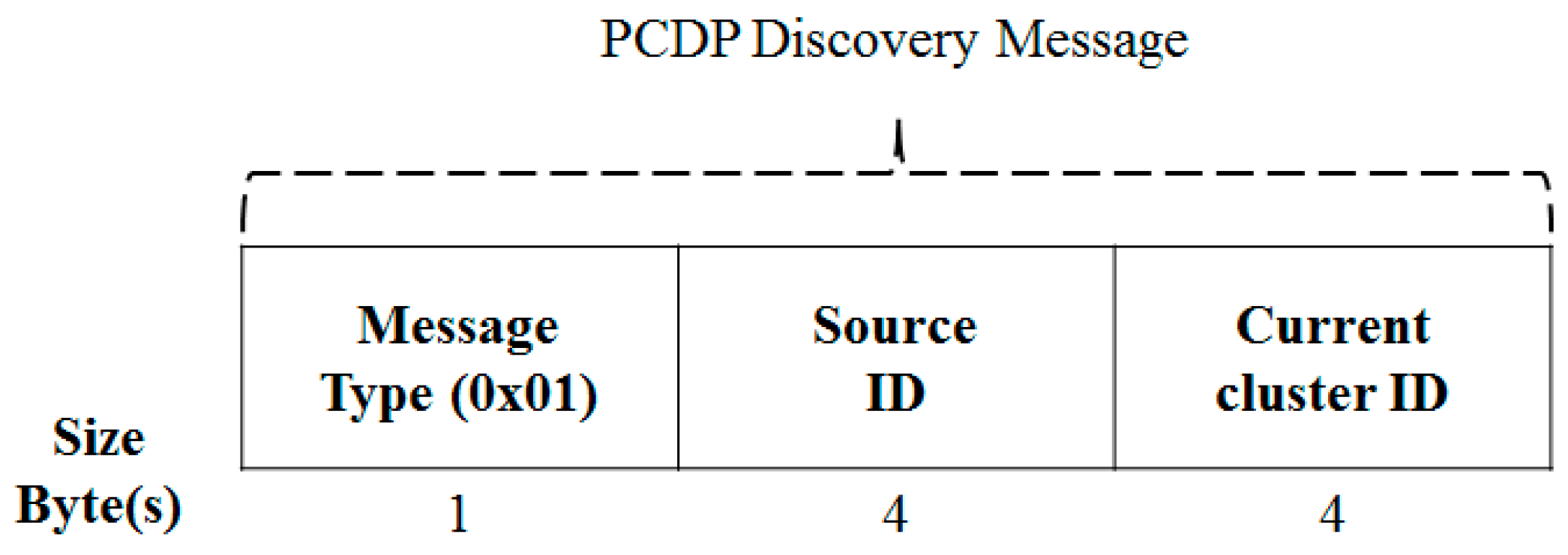
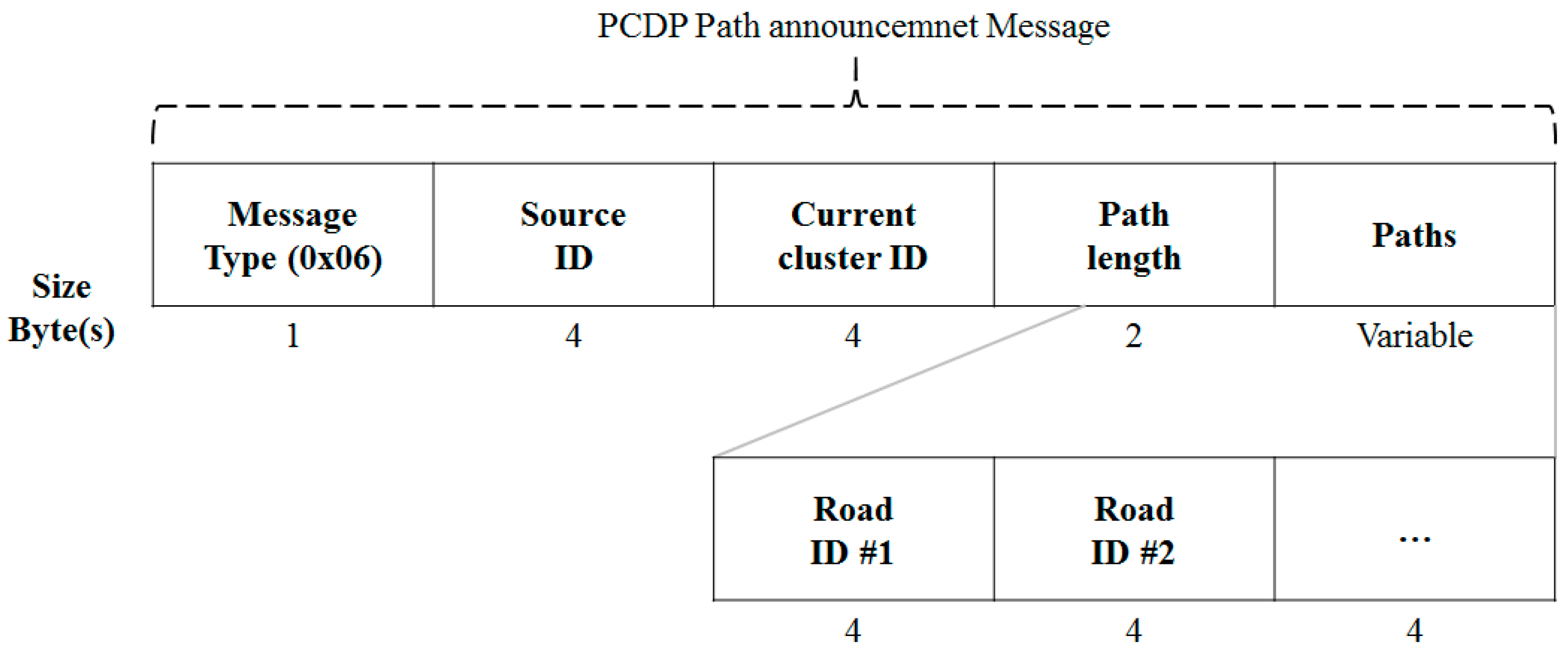
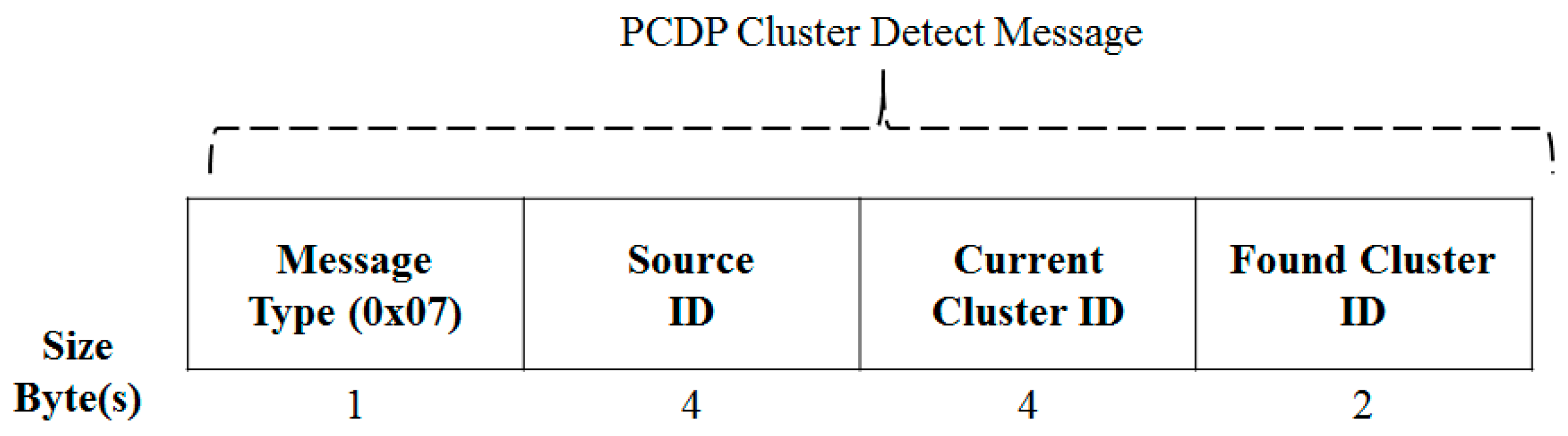
3.3.3. Message Format for a Clustering Process
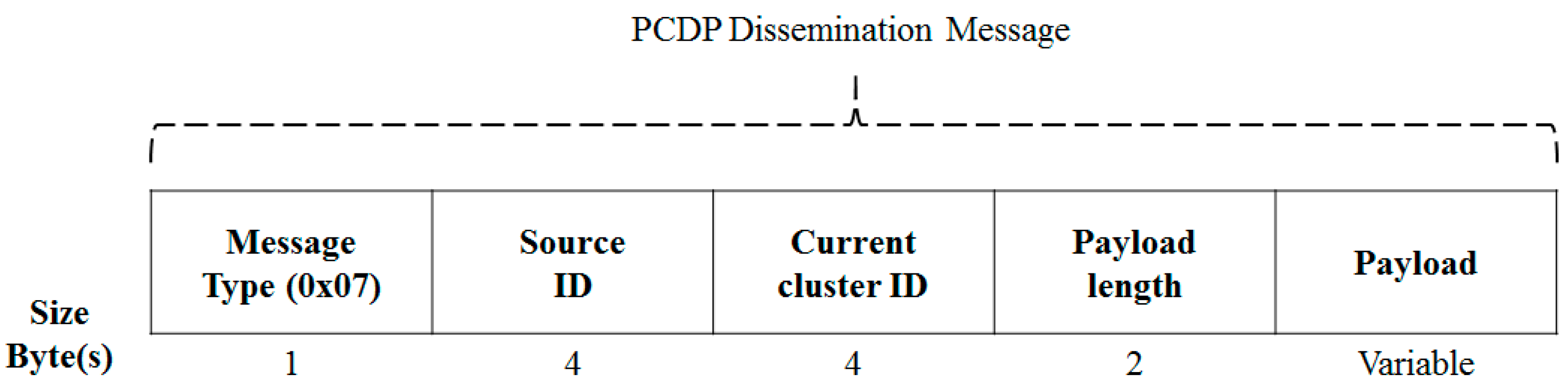
3.4. Data Dissemination Protocol
3.4.1. A Data Dissemination Algorithm
| Algorithm 3 Data dissemination algorithm | |
| Parameter m: received message, n: current node | |
| 1. | If n is in a cluster, then |
| 2. | If the source’s cluster ID n’s cluster ID, then |
| 3. | Set m’s source and cluster ID field to n’s and broadcast m |
| 4. | Else if n is the cluster head, then |
| 5. | Set m’s source to n’s and broadcast m |
| 6. | Else then |
| 7. | Drop m |
| 8. | Else then |
| 9. | Set m’s source to n’s and broadcast m |
3.4.2. Message Format for a Data Dissemination Process
4. Results
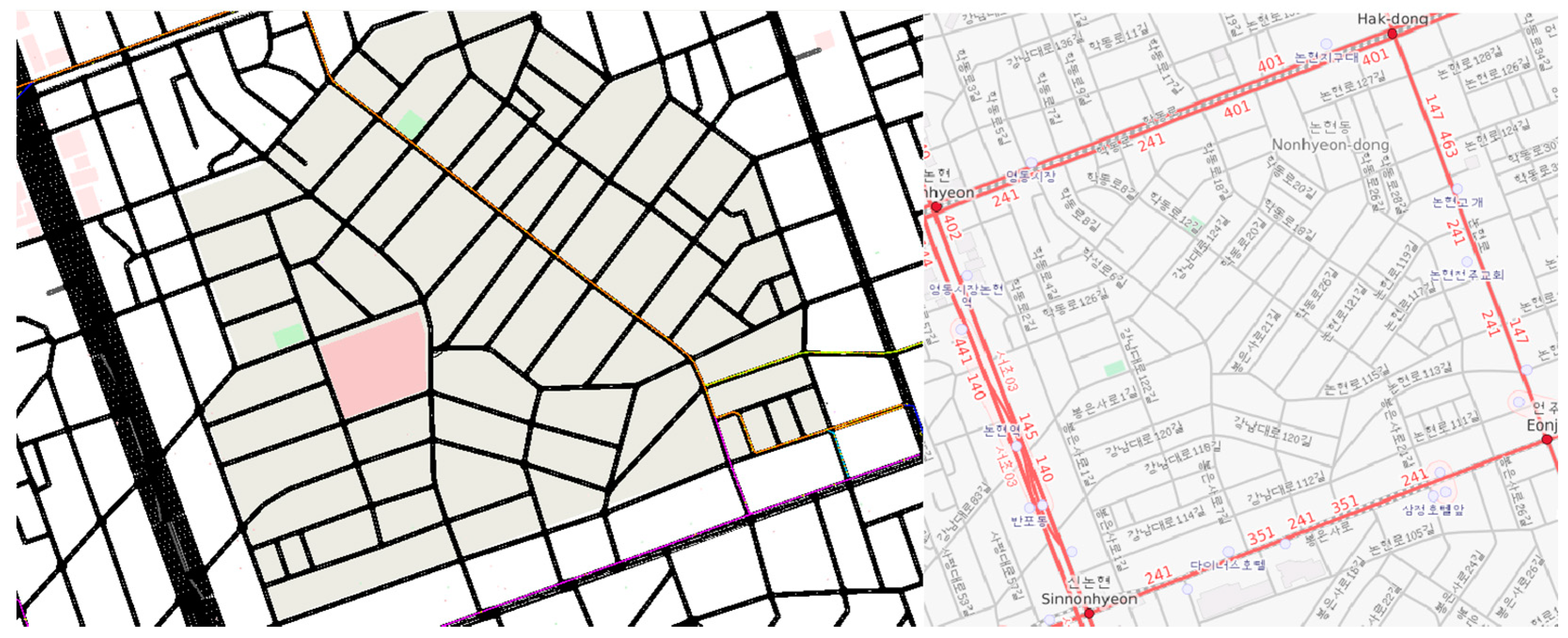
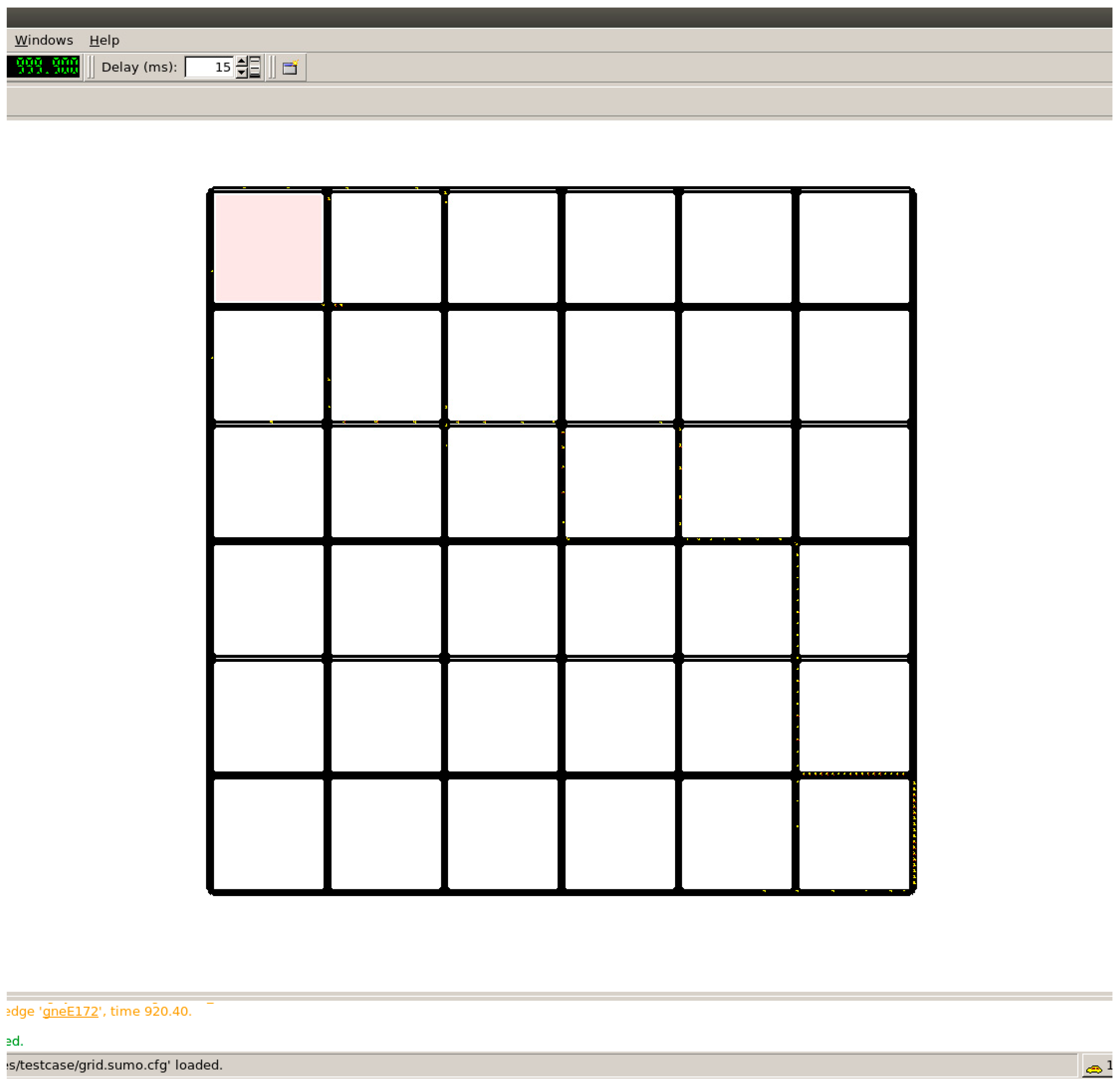
4.1. Simulation Environment
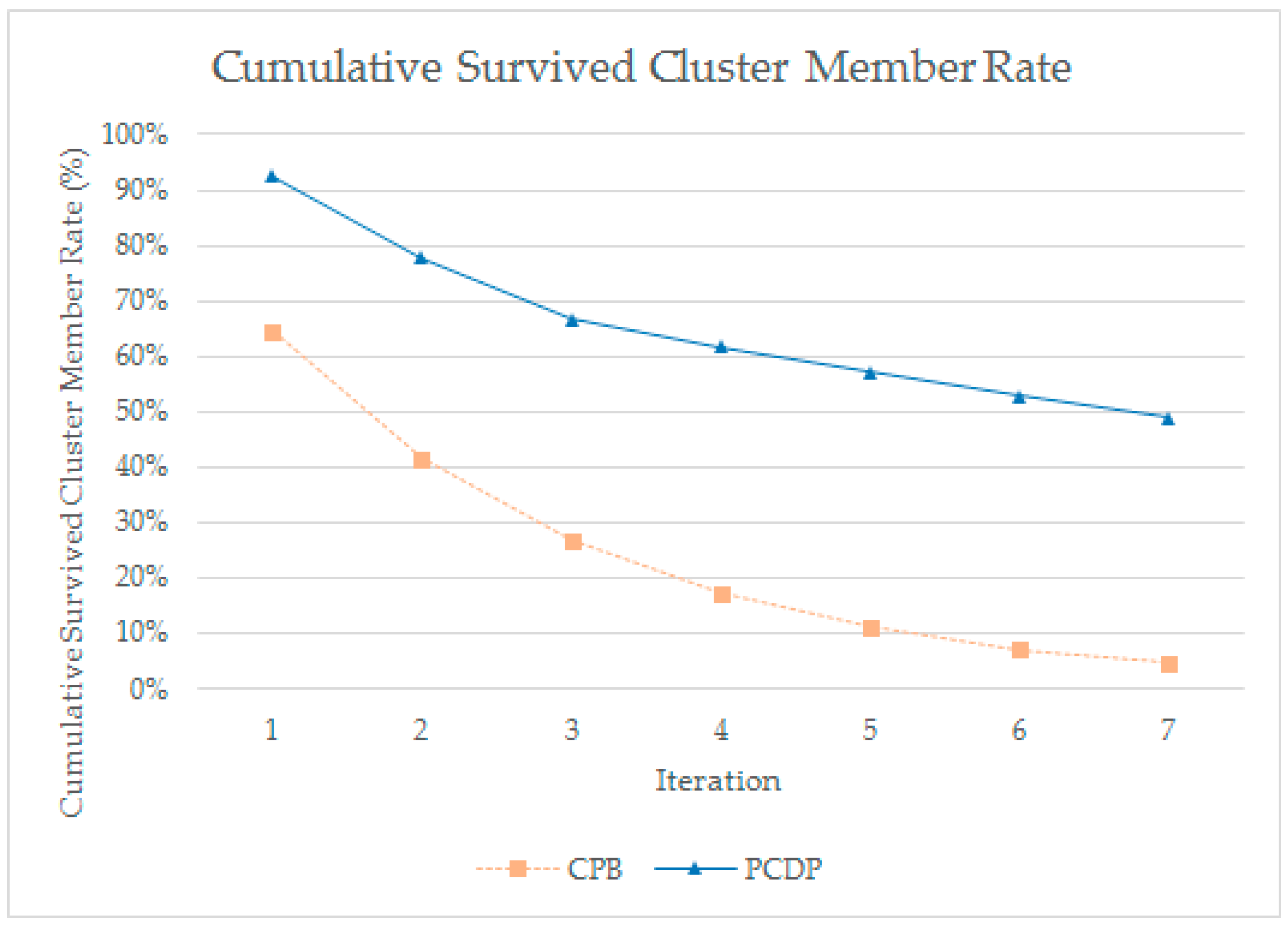
4.2. Cluster Robustness Evaluation
4.3. Overhead Evaluation
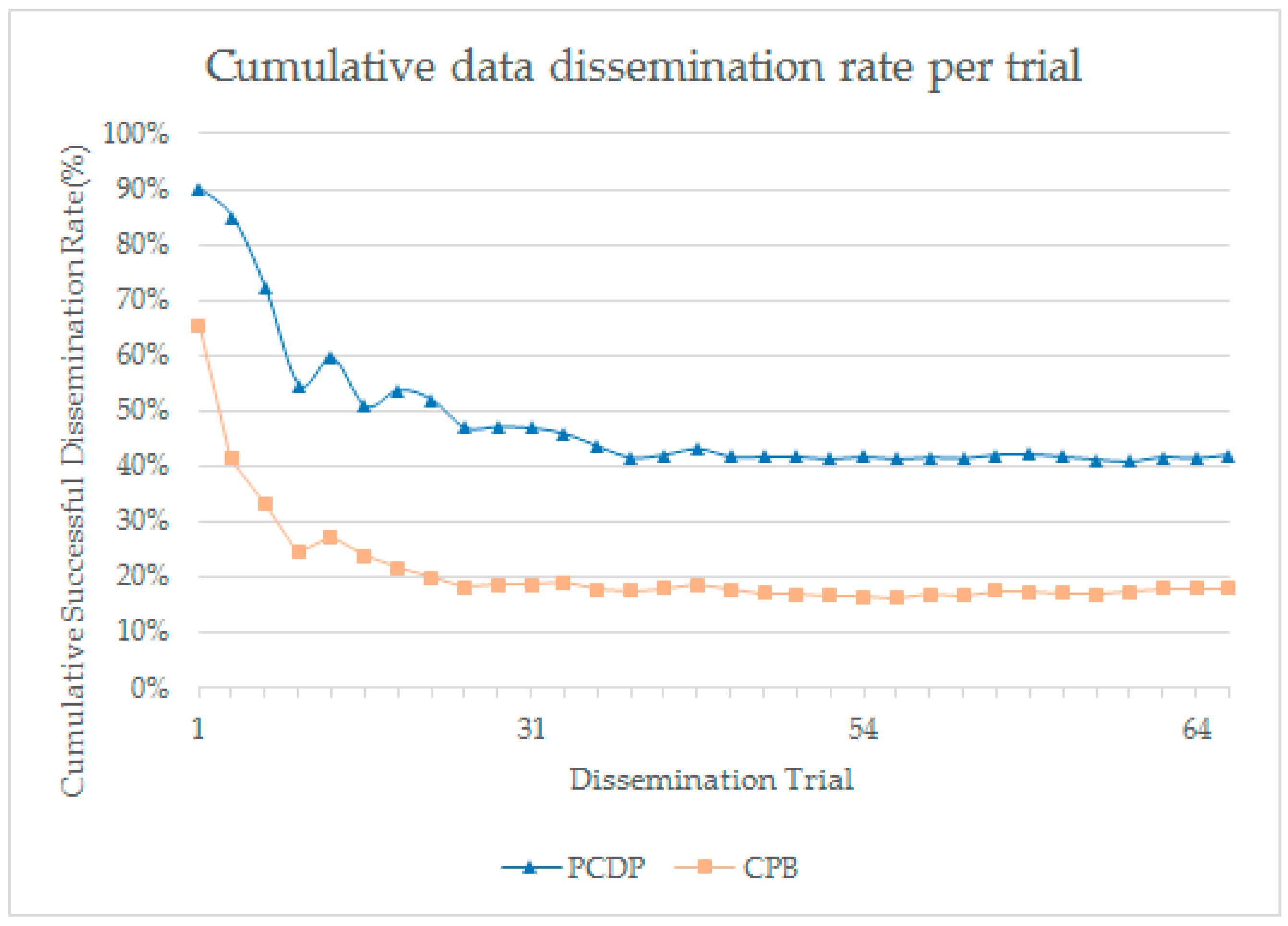
4.4. Data Dissemination Rate Evaluation
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Arbib, J.; Seba, T. Rethinking Transportation 2020–2030: The Disruption of Transportation and the Collapse of the Internal-Combustion Vehicle and Oil Industries; RethinkX: San Francisco, CA, USA, 2017. [Google Scholar]
- The Next Generation Mobile Networks—NGMN, NGMN V2X White Paper. Last modified 13 August 2018. Available online: https://www.ngmn.org/fileadmin/ngmn/content/downloads/Technical/2018/180813_Liaison_NGMN_C-V2X__v1.0.pdf (accessed on 10 November 2018).
- 3rd Generation Partnership Project. Study on LTE Support for Vehicle to Everything (V2X) Services (Release 14); Technical Report, 3GPP TR 22.885 V14.0.0 (2015-12); 3GPP: Valbonne, France, April 2015. [Google Scholar]
- Columbus, L. Roundup of Internet of Things Forecasts and Market Estimates. Forbes. 2016. Available online: https://www.forbes.com/sites/louiscolumbus/2016/11/27/roundup-of-internet-of-things-forecasts-and-market-estimates-2016/#5e917ed4292d (accessed on 5 December 2018).
- Allal, S.; Boudjit, S. Geocast routing protocols for VANETs: Survey and guidelines. In Proceedings of the 2012 Sixth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS), Palermo, Italy, 4–6 July 2012; pp. 323–328. [Google Scholar]
- Schwartz, R.S.; Barbosa, R.R.; Meratnia, N.; Heijenk, G.; Scholten, H. A directional data dissemination protocol for vehicular environments. Comput. Commun. 2011, 34, 2057–2071. [Google Scholar] [CrossRef]
- Wolny, G. Modified dmac clustering algorithm for vanets. In Proceedings of the 2008 Third International Conference on Systems and Networks Communications, Sliema, Malta, 26–31 October 2008; pp. 268–273. [Google Scholar]
- Nakagami, M. The m-distribution—A general formula of intensity distribution of rapid fading. In Statistical Methods in Radio Wave Propagation; Elsevier: Los Angeles, CA, USA, 1960; pp. 3–36. [Google Scholar]
- Whitmore, G. Estimating degradation by a Wiener diffusion process subject to measurement error. Lifetime Data Anal. 1995, 1, 307–319. [Google Scholar] [CrossRef] [PubMed]
- Ci, W.X.; Ahmed, S.K.; Zulkifli, F.; Ramasamy, A.K. Traffic flow simulation at an unsignalized T-junction using Monte Carlo Markov Chains. In Proceedings of the 2009 IEEE International Conference on Signal and Image Processing Applications, Kuala Lumpur, Malaysia, 18–19 November 2009; pp. 346–351. [Google Scholar]
- Bezdek, J.C.; Ehrlich, R.; Full, W. FCM: The fuzzy c-means clustering algorithm. Comput. Geosc. 1984, 10, 191–203. [Google Scholar] [CrossRef]
- Hartigan, J.; Wong, M. Algorithm AS 136: A k-means clustering algorithm. Appl. Stat. 1979, 28, 100–108. [Google Scholar] [CrossRef]
- Lung, C.-H. Software architecture recovery and restructuring through clustering techniques. In Proceedings of the Third International Workshop on Software Architecture, Orlando, FL, USA, 1–5 November 1998. [Google Scholar]
- Abo-Zahhad, M.; Ahmed, S.M.; Sabor, N.; Sasaki, S. Mobile sink-based adaptive immune energy-efficient clustering protocol for improving the lifetime and stability period of wireless sensor networks. IEEE Sens. J. 2015, 15, 4576–4586. [Google Scholar] [CrossRef]
- Arain, Q.A.; Uqaili, M.A.; Deng, Z.; Memon, I.; Jiao, J.; Shaikh, M.A.; Zubedi, A.; Ashraf, A.; Arain, U.A. Clustering based energy efficient and communication protocol for multiple mix-zones over road networks. Wirel. Pers. Commun. 2017, 95, 411–428. [Google Scholar] [CrossRef]
- Lin, H.; Wang, L.; Kong, R. Energy efficient clustering protocol for large-scale sensor networks. IEEE Sens. J. 2015, 15, 7150–7160. [Google Scholar] [CrossRef]
- Vodopivec, S.; Bešter, J.; Kos, A. A survey on clustering algorithms for vehicular ad-hoc networks. In Proceedings of the 2012 35th International Conference on Telecommunications and Signal Processing (TSP), Prague, Czech Republic, 3–4 July 2012; pp. 52–56. [Google Scholar]
- Zanjireh, M.M.; Larijani, H. A survey on centralised and distributed clustering routing algorithms for WSNs. In Proceedings of the 2015 IEEE 81st Vehicular Technology Conference (VTC Spring), Glasgow, UK, 11–14 May 2015; pp. 1–6. [Google Scholar]
- Gerla, M.; Lee, E.-K.; Pau, G.; Lee, U. Internet of vehicles: From intelligent grid to autonomous cars and vehicular clouds. In Proceedings of the 2014 IEEE World Forum on Internet of Things (WF-IoT), Seoul, South Korea, 6–8 March 2014; pp. 241–246. [Google Scholar]
- Bai, X.; Latecki, L.J. Path similarity skeleton graph matching. IEEE Trans. Pattern Anal. Mach. Intell. 2008, 30, 1282–1292. [Google Scholar] [PubMed]
- Xu, Y.; Wang, B.; Liu, W.; Bai, X. Skeleton graph matching based on critical points using path similarity. In Asian Conference on Computer Vision; Springer: Berlin, Germany, 2009; pp. 456–465. [Google Scholar]
- Jin, T.; Jiang, B.; Luo, B. Graph Matching Based on Graph Histogram and Path Similarity. J. Comput.-Aided Des. Comput. Graphics 2011, 9, 3. [Google Scholar]
- Leontiadis, I.; Mascolo, C. GeOpps: Geographical Opportunistic Routing for Vehicular Networks. In Proceedings of the 2007 IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks, Espoo, Finland, 18–21 June 2007; pp. 1–6. [Google Scholar]
- Chen, M.; Leung, V.C.M.; Mao, S.; Yuan, Y. Directional geographical routing for real-time video communications in wireless sensor networks. Comput. Commun. 2007, 30, 3368–3383. [Google Scholar] [CrossRef]
- Intelligent Transportation System Applications Using Dedicated Short-Range Communications, Federal Communications Commission Document. Last modified 16 May 2001. Available online: https://www.fcc.gov/document/intelligent-transportation-system-applications-using-dedicated-short-range (accessed on 10 November 2018).
- Group, I.W. IEEE Standard for Information Technology–Telecommunications and information exchange between systems–Local and metropolitan area networks–Specific requirements–Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) specifications Amendment 6: Wireless Access in Vehicular Environments. IEEE Std. 2010. [Google Scholar] [CrossRef]
- Uzcátegui, R.A.; De Sucre, A.J.; Acosta-Marum, G. Wave: A tutorial. IEEE Commun. Mag. 2009, 47, 126–133. [Google Scholar] [CrossRef]
- Campolo, C.; Vinel, A.; Molinaro, A.; Koucheryavy, Y. Modeling broadcasting in IEEE 802.11 p/WAVE vehicular networks. IEEE Commun. Lett. 2011, 15, 199–201. [Google Scholar] [CrossRef]
- Biddlestone, S.; Redmill, K.; Miucic, R.; Ozguner, Ü. An integrated 802.11 p wave dsrc and vehicle traffic simulator with experimentally validated urban (los and nlos) propagation models. IEEE Trans. Intell. Transp. Syst. 2012, 13, 1792–1802. [Google Scholar] [CrossRef]
- Gräfling, S.; Mähönen, P.; Riihijärvi, J. Performance evaluation of IEEE 1609 WAVE and IEEE 802.11p for vehicular communications. In Proceedings of the 2010 Second International Conference on Ubiquitous and Future Networks (ICUFN), Jeju, Korea, 16–18 June 2010; pp. 344–348. [Google Scholar]
- Momeni, S.; Fathy, M. Clustering In VANETs. In Intelligence for Nonlinear Dynamics and Synchronisation; Springer: Berlin, Germany, 2010; pp. 271–301. [Google Scholar]
- Cai, X.; He, Y.; Zhao, C.; Zhu, L.; Li, C. LSGO: link state aware geographic opportunistic routing protocol for VANETs. EURASIP J. Wirel. Commun. Netw. 2014, 2014, 96. [Google Scholar] [CrossRef]
- Nzouonta, J.; Rajgure, N.; Wang, G.; Borcea, C. VANET routing on city roads using real-time vehicular traffic information. IEEE Trans. Veh. Technol. 2009, 58, 3609–3626. [Google Scholar] [CrossRef]
- Liu, L.; Chen, C.; Qiu, T.; Zhang, M.; Li, S.; Zhou, B. A Data Dissemination Scheme based on Clustering and Probabilistic Broadcasting in VANETs. Veh. Commun. 2018, 13, 78–88. [Google Scholar] [CrossRef]
- Zhang, X.; Cao, X.; Yan, L.; Sung, D. A street-centric opportunistic routing protocol based on link correlation for urban vanets. IEEE Trans. Mob. Comput. 2016, 15, 1586–1599. [Google Scholar] [CrossRef]
- Artimy, M.M.; Robertson, W.; Phillips, W.J. Assignment of dynamic transmission range based on estimation of vehicle density. In Proceedings of the 2nd ACM International Workshop on Vehicular Ad Hoc Networks, New York, NY, USA, 2 September 2005; pp. 40–48. [Google Scholar]
- Yu, G.; Hu, J.; Zhang, C.; Zhuang, L.; Song, J. Short-term traffic flow forecasting based on Markov chain model. In Proceedings of the IEEE IV2003 Intelligent Vehicles Symposium. Proceedings (Cat. No.03TH8683), Columbus, OH, USA, 9–11 June 2003; pp. 208–212. [Google Scholar]
- Sommer, C. Veins The Open Source Vehicular Network Simulation Framework. Available online: https://veins.car2x.org/ (accessed on 10 November 2018).
- SUMO—Simulation of Urban Mobility, SUMO Official Web Site. Last modified 25 November 2018. Available online: http://sumo.dlr.de/index.html (accessed on 27 November 2018).
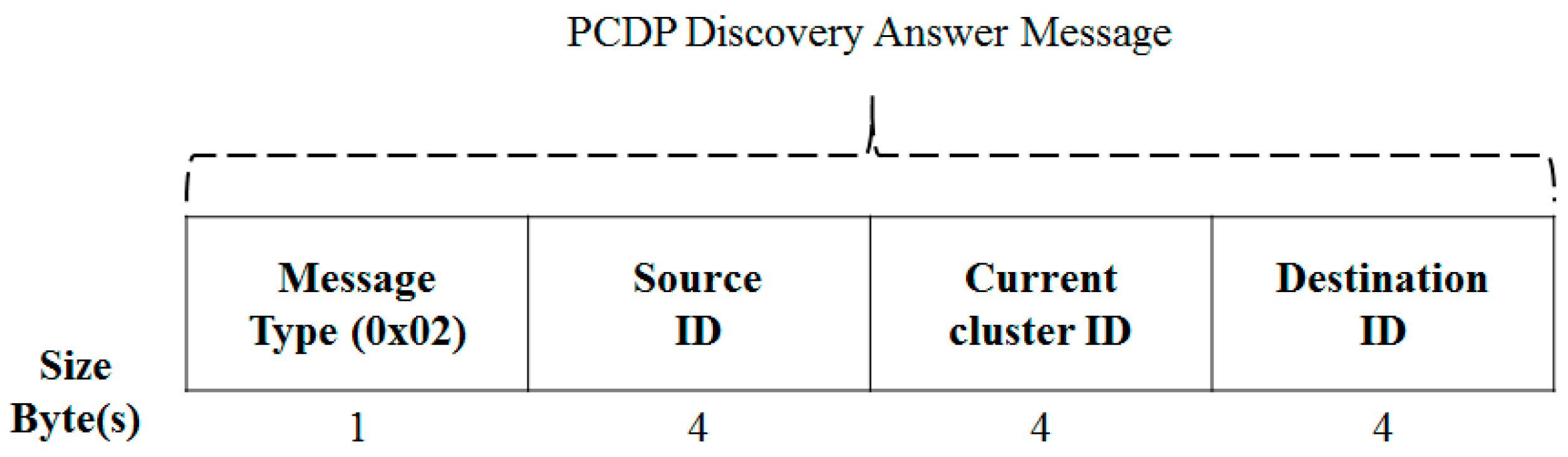
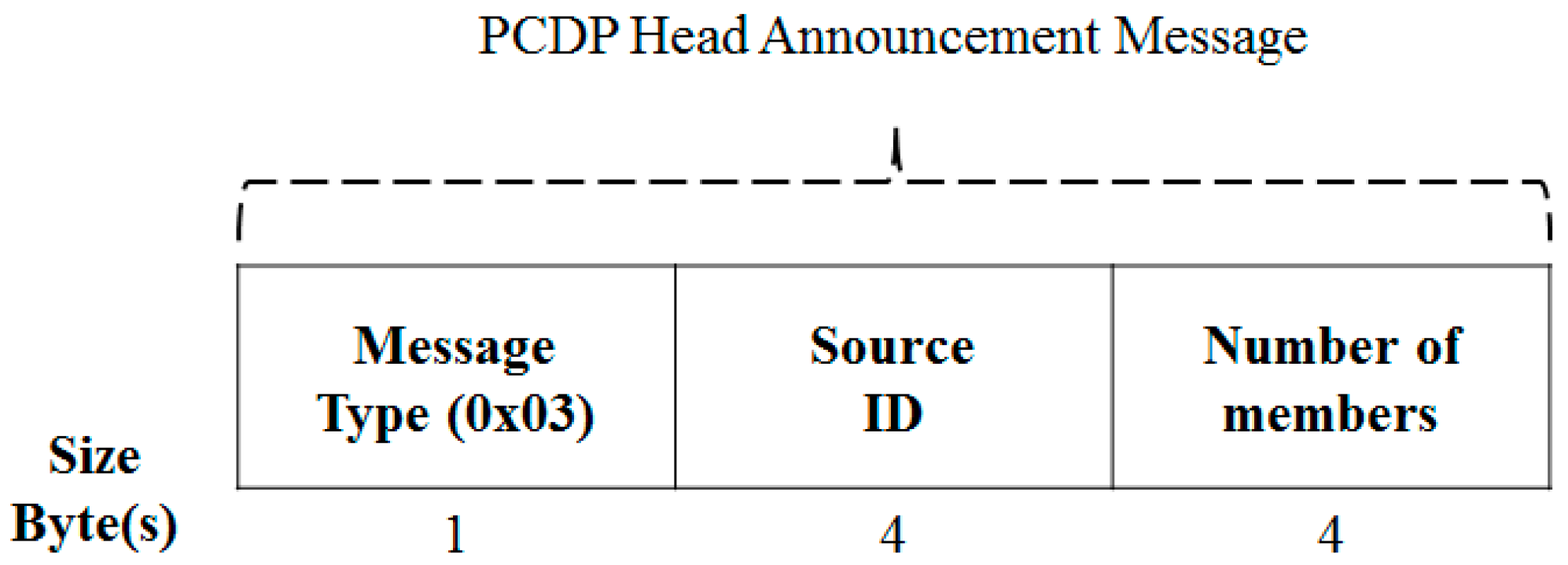
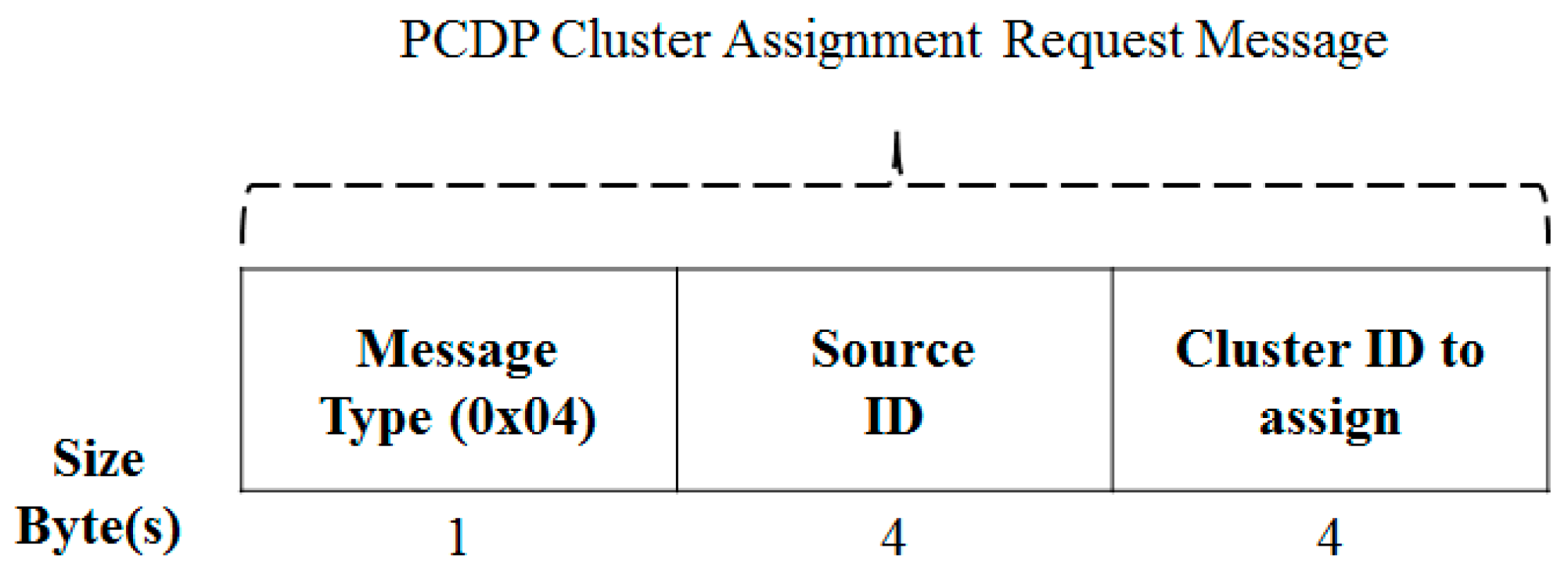
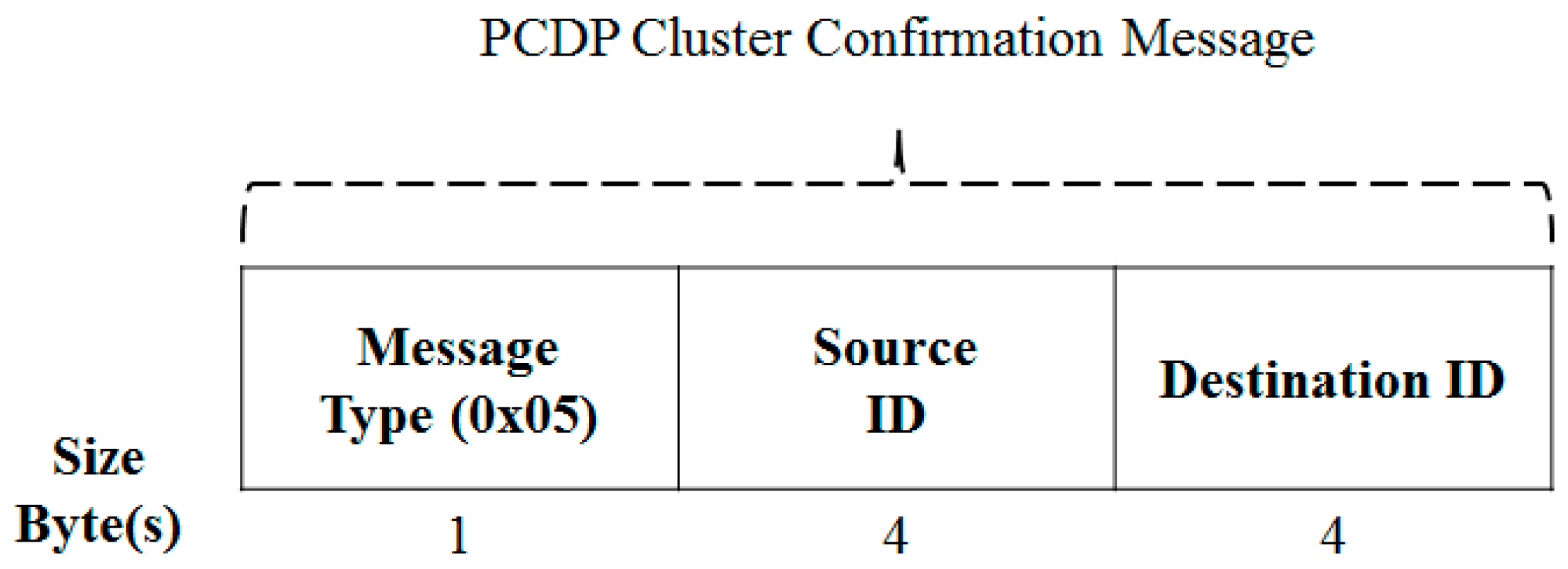

| Term | Definition |
|---|---|
| Unclustered node | Node not joined to any cluster |
| Cluster head | A node that manages the cluster in a cluster |
| Cluster member | A node belonging to a cluster but not a cluster head |
| Path distance | Similarity distance between path information of each node |
| Data dissemination rate | The percentage of messages disseminated across the network |
| Survivability | The degree to which a cluster member can be maintained as a member of a cluster for a unit of time |
| Data Dissemination | Delivering messages to the entire network so that as many nodes as possible receive |
| Variable | Value | Unit |
|---|---|---|
| Area Size | 36,000 | m2 |
| Grid Size | 1000 | m2 |
| Size of Grid | 6 × 6 | |
| Maximum Speed | 80 | km/h |
| Number of Nodes Per Route | 5 | |
| Number of Routes | 924 | |
| Simulation Time | 18,000 | S |
| Bitrate | 6 | Mbps |
| Signal Strength | −20 | dBm |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Seo, M.; Lee, S.; Lee, S. Clustering-Based Data Dissemination Protocol Using the Path Similarity for Autonomous Vehicles. Symmetry 2019, 11, 260. https://doi.org/10.3390/sym11020260
Seo M, Lee S, Lee S. Clustering-Based Data Dissemination Protocol Using the Path Similarity for Autonomous Vehicles. Symmetry. 2019; 11(2):260. https://doi.org/10.3390/sym11020260
Chicago/Turabian StyleSeo, MinSeok, SeungGwan Lee, and Sungwon Lee. 2019. "Clustering-Based Data Dissemination Protocol Using the Path Similarity for Autonomous Vehicles" Symmetry 11, no. 2: 260. https://doi.org/10.3390/sym11020260
APA StyleSeo, M., Lee, S., & Lee, S. (2019). Clustering-Based Data Dissemination Protocol Using the Path Similarity for Autonomous Vehicles. Symmetry, 11(2), 260. https://doi.org/10.3390/sym11020260





