Abstract
Criminal activities have always been a part of human society, and even today, in a world of extremely advanced surveillance and policing capabilities, many different kinds of crimes are still committed in almost every social environment. However, since those who commit crimes are not representative of the majority of their community, members of these communities tend to wish to report crime when they see it; however, they are often reluctant to do so for fear of their own safety should the people they report identify them. Thus, a great deal of crime goes unreported, and investigations fail to gain key evidence from witnesses, which serves only to foster an environment in which criminal activity is more likely to occur. In order to address this problem, this paper proposes an online illegal event reporting scheme based on cloud technology, which combines digital certificates, symmetric keys, asymmetric keys, and digital signatures. The proposed scheme can process illegal activity reports from the reporting event to the issuing of a reward. The scheme not only ensures informers’ safety, anonymity and non-repudiation, but also prevents cases and reports being erased, and ensures data integrity. Furthermore, the proposed scheme is designed to be robust against abusive use, and is able to preclude false reports. Therefore, it provides a convenient and secure platform for reporting and fighting crime.
1. Introduction
In today’s technologically advanced society, mechanisms for fighting crime are extremely advanced, from remote, automatic surveillance to sophisticated dedicated laboratories and evidence analysis, yet crime still has a significant presence in our world, both globally and in local communities, including sexual assault, drugs and violent crimes, all of which endanger the public. While some people may be willing to actively report illegal acts, others choose not to do so, as they are worried about the fallibility of the policing, reporting and criminal justice systems, based on previous failings in all three departments [1,2,3]. People are afraid for their own safety should those they report identify them, or they are worried that law enforcement officials may simply erase any case they report. Moreover, people afraid of intimidation may choose not to offer information, or stand as a witness to criminal acts, despite a high reward being offered for such information. All of these concerns have, in the past, contributed to an environment in which crime is more difficult to address, and in which crime is more likely to be committed. However, recent years have seen rapid developments in Internet technology, in particular cloud technology, which have made possible an online crime reporting system with identity protection. In fact, the high degree of identity protection offered by these technological advances is a necessity for any such online crime reporting system [4].
User identities must be as secure as possible for any such reporting system, as informers are required to use their real names; understandably, this information must be kept secret to ensure the informer’s safety [5]. Informers are required to provide their real identities, as the use of pseudonyms would make them difficult to contact, and cases may not be accepted as a result. However, an informer’s real identity is always vulnerable to exposure through human error.
There are two primary requirements for an online crime reporting system: Informers must provide their real identities, and their identities must be well protected. With these requirements in mind, several online crime reporting systems have been proposed for different applications in recent years [1,2,6,7]. In order to ensure that the informer’s identity is protected during reporting, anonymity can effectively protect victims and witnesses; however, the security mechanisms involved in identity verification and data transmission are important issues to be addressed.
As a result, this paper presents a novel reporting system using a cryptographic mechanism for improved security and identity confidentiality. The proposed scheme also combines digital certificates, symmetric keys, asymmetric keys, digital signatures and a design verification mechanism to achieve integrity, privacy and un-falsification of transmitted data. In addition, the system not only ensures the legitimacy of a user’s identity, but also protects informers’ privacy and security [7] in an anonymous manner. Rewards can also automatically be remitted to informers. In addition, the proposed system prevents administration problems, such as cases being deleted or lost, or malicious abuse of the reporting system.
The proposed scheme uses a network online reporting mechanism to improve reporting and reduce policing costs [2], combined with digital certificates for authentication [8,9,10] to ensure that reports cannot be made anonymously. The proposed system is thus able to use an impartial third-party organization to confirm an informer’s identity, and protect the informer’s privacy and security. In addition, if cases reported are not accepted within a specified time, the system is equipped with an automatic upward reporting mechanism to prevent late investigations or the erasure of cases. If reported information leads to the successful resolution of a case, a reward will be automatically remitted to the informers via the system, so that the process is completely hidden and safe, thus offering complete informer identity protection, and preventing a variety of security threats.
Network service applications have increased rapidly with the recent rapid growth of information technology, giving rise to the development of powerful, high-capacity cloud computing systems that can satisfy various user demands and offer shared resources online [11,12]. According to the literature [13], many enterprises employ cloud services and their applications provided through a browser offering access to online programming applications, software and data. These computing services can be implemented in the cloud platform. In addition, [14] noted that the cloud services are an important future trend.
Many online reporting systems have been proposed to date, and research into such systems has provided several requirements for such systems [6,15,16,17,18]. For example: trusted third-parties are used to verify legitimate informer identities using digital certificate technology to prevent abuse of the system by impostor attacks [15,16]; authentication mechanisms are crucial to such systems [19,20,21].
Informers may wish to remain anonymous during the online reporting process [6] because they are afraid for their own safety should their identity become known to those being reported [17]. Therefore, it is important to protect informer identity. In addition, as Martín et al. [18] noted, messages must be secure against tampering during transmission. It is also important to ensure that the identity of the informer is not even known to the auditor or the system in the event of a malicious digital attack.
Another important requirement is non-repudiation. The system server saves information signed by all personnel; thus, if disputes occur, users cannot deny that the record has been signed [18].
Other concerns include:
(1) That reported cases may be erased or delayed due to external intervention. Therefore, if reported cases have not been accepted within a specified time, the proposed scheme is equipped with an automatic upward reporting mechanism to avoid reported cases being suppressed.
(2) That informers’ identities may be disclosed in the reward procedure. The system must protect the privacy of informers in any actions, so the proposed scheme includes a precautionary mechanism to ensure that managers or databases are not leaked, as there is no record to track the identity of a person making a report.
(3) That reported information may be intercepted or leaked, revealing the informer’s identity. Therefore, it is essential to ensure complete transmission confidentiality.
To sum up, an online reporting system should meet the following requirements: authentication, anonymity, integrity, and non-repudiation, preventing cases from being erased, avoiding the disclosure of informer identity in the award procedure, protecting the privacy of informers, and preventing the reported information from being intercepted.
2. Methodology
This section describes how the proposed online crime reporting system with identity protection protects informer identity and privacy during the reporting process, how the proposed system prevents cases being erased, and the automatic reward process.
2.1. Notations
- Ux—user x is categorized as: informer Ui, investigator Ut, superior Us
- Ui—informer
- Ut—investigator
- Us—superior
- ServerPLA—reporting server
- ServerCA—certificate authority server
- TFGateway—cooperating payment server
- IDx—the reporting system account of Ux
- PWx—the reporting system password of Ux
- PWHASH—the hash value of a password
- SNevent—the serial number of a case
- ACCi—the bank account of Ui
- Cash—the reward amount
- SN—the serial number of an IC (Integrated Circuit) card
- IDNO—the ID number of an IC card (last four digits)
- PUKUx—the public key of Ux
- PRKUx—the private key of Ux
- Msgevent—attached data for reporting (e.g., photos and related documents)
- Msgsuc—success response from reporting server
- Msgunsuc—unsuccessful response from reporting server
- MsgCA—the result of verification from the CA (Certificate Authority) server
- Msgver—the audit result of reporting case form Ut or Us
- MsgBANKsuc—notification of remit
- Sigx—the signature of x
- VPUKUx(Sigx)—use the public key PUKUx to verify signature Sigx
- SPRKUx(M)—use the private key PRKUx to sign message M
- EKEY(M)—encrypt message M by symmetric key KEY
- DKEY(C)—decrypt ciphertext C by symmetric key KEY
- EPUKSERVERPLA(M)—encrypt message M by public key PUKSERVERPLA
- DPRKSERVERPLA(C)—decrypt ciphertext C by server’s private key PRKSERVERPLA
- H(. )—one way hash function
- X→Y—send a message from X to Y
- A ≟ B—determine if A is equal to B
 —insecure channel
—insecure channel —secure channel
—secure channel
2.2. System Structure
The system structure and operation processes of the proposed system are shown in Figure 1. The main interactive roles are informers, investigators and superiors. The servers include the reporting server, the cooperating payment server, and the certificate authority server. The platform uses digital certificates on personal identification IC (Integrated Circuit) cards, which verify the identity of the user, thus preventing reports by impostors. The user (e.g., informer, investigator and superior) must apply for a personal identification IC card in person at the digital certificate management center. In all operations, the verification of a personal IC card is issued by the reporting platform to the digital certificate management center. In the following descriptions, it is assumed that the user has registered successfully and has logged in to the reporting platform.
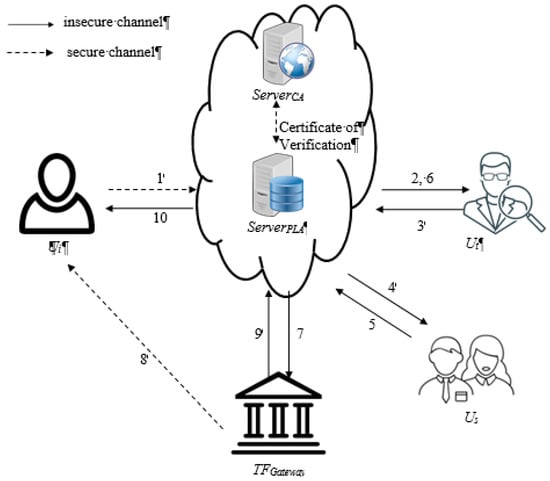
Figure 1.
System structure and operations of reporting cloud.
- (1)
- Informer logs in to the system to make a report, or to process other related operations.
- (2)
- The reporting server assigns an investigator to conduct an investigation, and the investigator receives the report of a crime, and determines whether the preliminary evidence is sufficient to open a case.
- (3)
- The investigator transmits the result of the audited case to the reporting server.
- (4)
- The reporting server transmits the reports audited by the investigator to a superior. In addition, if the investigator does not receive or audit reports within a specified period, the system will automatically notify the superior of the reports. If the upward notification confirms the reports are sufficient to open cases, with a reward to be issued, the reports will be sent to the upper superiors for confirmation. When all the superiors confirm that the details of the report are sufficient for the reward, the financial system will automatically remit the reward to the informer’s account. On the other hand, if the investigator determines that a report is abusing the system, then the superior will re-confirm whether the case is rejected or must be re-investigated to avoid a wrong judgment.
- (5)
- Each superior sends the results of the case to the reporting server.
- (6)
- When the reporting server receives a superior’s determination that the case needs re-investigating, the case will be reassigned to a new superior.
- (7)
- When the reporting server receives the confirmation and agrees to issue the reward, the server will notify the financial institution.
- (8)
- The cooperating payment server of the financial institution will automatically remit the reward to the informer’s account.
- (9)
- When the cooperating payment server has remitted the reward, it will notify the reporting server.
- (10)
- The reporting server notifies the informer that the remittance has been completed.
2.2.1. Registration Phase
Before a user is granted access to the platform for the first time, they must go to the digital certificate management center to get a personal identification IC card, which they will then use to register and access the platform. Figure 2 is the flow chart of the registration verification phase. The steps of the registration phase are as follows:
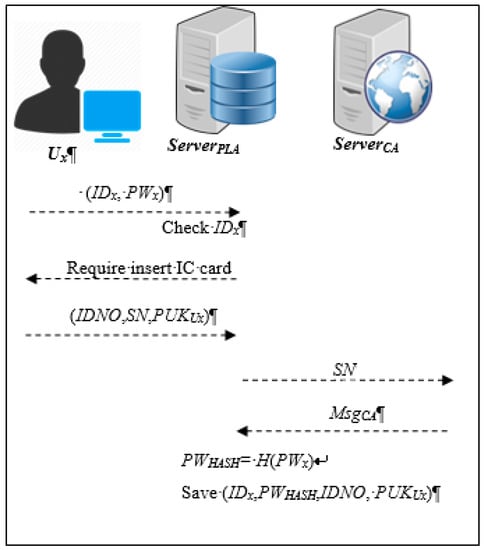
Figure 2.
The flow chart of the registration phase.
Step 1: Ux→ServerPLA
User Ux must first register and provide basic information, such as account IDx and password PWx. The user Ux will transmit IDx and PWx to the reporting server ServerPLA.
Step 2: ServerPLA→Ux
After receiving the IDx and PWx, the reporting server verifies the account IDx of the user Ux. If the user account IDx is approved by the server, then user Ux will be asked to insert his/her personal identification IC card to determine whether the IC card is valid.
Step 3: Ux→ServerPLA
User Ux must insert the personal identification IC card and enter the PIN code. If the PIN code is correct, then user Ux will receive the SN number of the IC card, the public key PUKUx and his/her personal data (for example, the last four digits of the ID card number IDNO) and the system will send IDNO, SN, and PUKUx to the reporting server.
Step 1: ServerPLA→ServerCA
After receiving the the user’s IDNO, SN and public key PUKUx, the reporting server will transmit the SN and authentication data to the OCSP (Online Certificate Status Protocol) service of the certificate authority server ServerCA to check the validity of SN.
Step 2: ServerCA→ServerPLA
The certificate authority server ServerCA will verify the SN sent by the reporting server ServerPLA, and send the result MsgCA back to the reporting server.
Step 3: ServerPLA
After receiving the MsgCA that ServerCA has already sent back, the ServerPLA can determine whether MsgCA is valid. If it is valid, then user Ux is a legal user. The reporting server will then convert the user’s password PWx into PWHASH with SHA-256:
PWHASH = H(PWx)
Finally, the registration information IDx, encrypted PWHASH, IDNO and public key PUKUx of the user Ux are stored in the database, completing the registration process.
2.2.2. Login Verification Phase
Once a user passes the verification phase, s/he will be allowed to log into the system. The following Steps (1) and (2) describe the login processes and verification steps. Figure 3 shows the flow chart of the login verification phase.
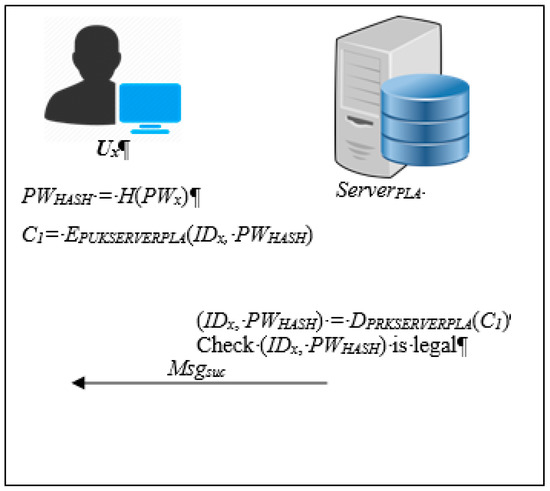
Figure 3.
The flow chart of the login verification phase.
Step 1: Ux→ServerPLA
The user Ux logs into the reporting platform and enters the account IDx and password PWx, and then sends this information. This will convert the password PWx into PWHASH:
PWHASH = H(PWx)
Then the ServerPLA uses the public key PUKSERVERPLA to encrypt IDx and PWHASH. After this, the encrypted message C1 is transmitted to the reporting server:
C1 = EPUKSERVERPLA(IDx, PWHASH)
Step 2: ServerPLA→Ux
When the reporting server receives the encrypted message C1, the server ServerPLA will use its own private key PRKSERVERPLA to decrypt C3:
(IDx, PWHASH) = DPRKSERVERPLA(C1)
The user Ux, account IDx and password PWHASH will be obtained, and then compared with the data stored in the database. If IDx and PWHASH match the database, ServerPLA will respond with a success message Msgsuc that the login is successful.
2.2.3. Reporting Phase
In the reporting phase, the informer can log into the system and fill in a crime report by entering the identity of the offender, the related documents and the details of the violation. The informer’s identity is not required. The informer simply needs to insert his/her IC card and verify his/her identity. If the informer’s identity is correct, the system will allow him/her to submit a report. The flow chart of the reporting phase is shown in Figure 4.
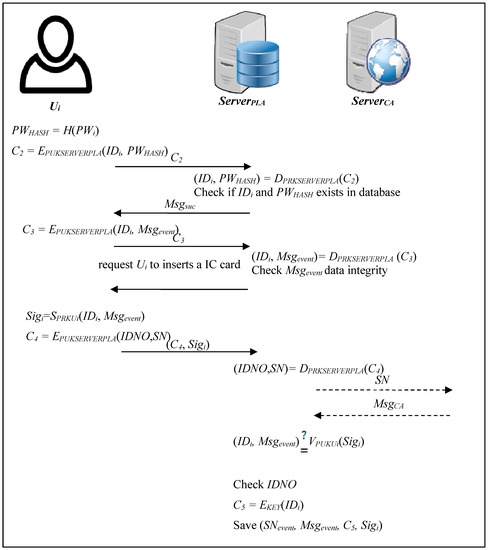
Figure 4.
The flow chart of the reporting phase.
Step 1: Ui→ServerPLA
The informer Ui logs into the reporting platform, enters his/her account IDi and password PWi, and then submits them. This will convert the PWi into PWHASH:
PWHASH = H(PWi)
After this, PUKSERVERPLA uses the public key to encrypt IDi and PWHASH and then send the encrypted message C4 to the reporting server:
C2 = EPUKSERVERPLA(IDi, PWHASH)
Step 2: ServerPLA→Ui
When the reporting server receives the encrypted message C2 from the informer Ui, the server will use the private key PRKSERVERPLA to decrypt message C2:
(IDi, PWHASH) = DPRKSERVERPLA(C2)
The informer Ui account IDi and password PWHASH will be obtained and then compared with the data stored in the database. If IDi and PWHASH match the related data in the database, ServerPLA will reply Msgsuc to inform Ui that they have successfully logged in.
Step 3: Ui→ServerPLA
Then, the informer Ui enters the report event Msgevent and encrypts IDi and Msgevent by public key PUKSERVERPLA. The encrypted message C3 will be sent to the reporting server:
C3 = EPUKSERVERPLA(IDi, Msgevent)
Step 4: ServerPLA→Ui
The reporting server ServerPLA uses its own private key PRKSERVERPLA to decrypt C3, and then gets the informer’s IDi and report event Msgevent:
(IDi, Msgevent) = DPRKSERVERPLA(C3)
It then checks that the form is completed. If the information is completed, the ServerPLA will request the informer Ui to insert his/her IC card.
Step 5: Ui→ServerPLA
After this, Ui inserts his/her IC card and enters his/her PIN code. If the PIN code is correct, it will use the informer’s private key PRKUi to sign the reported event Msgevent:
Sigi = SPRKUi(IDi, Msgevent)
Next, SN and IDNO are obtained from the informer Ui’s IC card, and the public key PUKSERVERPLA is used to encrypt the SN and IDNO:
C4 = EPUKSERVERPLA(IDNO, SN)
Finally, ServerPLA sends the encrypted message C4 and the informer’s signature Sigi to the reporting server.
Step 6: ServerPLA→ServerCA
The reporting server receives C4 and Sigi of Ui, and then uses the server’s private key PRKSERVERPLA to decrypt C4, and obtains the IDNO and SN of Ui..
(IDNO, SN) = DPRKSERVERPLA(C4)
The reporting server will transmit the SN to the OCSP service of the certificate authority server through a secure channel to check the validity of SN.
Step 7: ServerCA→ServerPLA
The certificate authority server ServerCA will verify the SN from the reporting ServerPLA and send the result MsgCA back to ServerPLA.
Step 8: ServerPLA
When the reporting server receives the result of the certificate authority server ServerCA and it is effective, it will then compare the information in signature Sigi and messages (IDi, Msgevent):
(IDi, Msgevent) ≟ VPUKUi(Sigi)
If the signature is correct, the server will compare the IDNO of the IC card with the IDNO stored in the database. If the comparison is successful, the system will generate an event number SNevent. This event number SNevent will be associated with the identity of the informer. Therefore, the system will encrypt the IDi of the Ui with symmetric key from ServerPLA:
C5 = EKEY (IDi)
Finally, the SNevent, Msgevent, C5 and Sigi are saved in the database.
2.2.4. The Superior Verification Phase
Upon logging into the system, the investigator will conduct an investigation of reported crimes randomly assigned by the system. If the reported case is illegal and has a reward, it will be forwarded to the superior to issue the reward. On the other hand, if it is a non-reward case, the investigator will indicate the case processing status as “closed”. This phase verifies individual identification of the IC card as in the case reporting phase steps (6)–(7). The case before the superior will only receive and display relevant documents and content, and does not contain the identity of the informer because the identity of the informer was confirmed at the beginning of the reporting phase, which means the informer is a legal user, and the whole process of the report is guaranteed to be anonymous. The following steps (1)–(4) describe the auditing process and give an overview of verification, as shown in Figure 5.
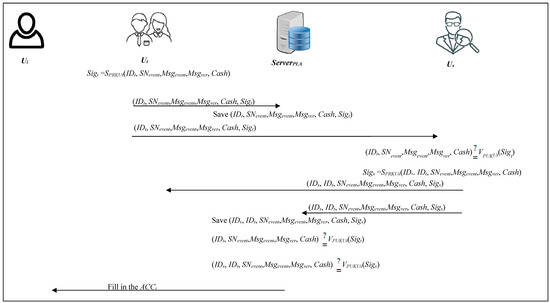
Figure 5.
The flow chart of the superior verifying phase.
Step 1: Ut→ServerPLA;Ut→Us
When the investigator Ut receives the report event Msgevent assigned by the system, the investigator investigates that event. If the investigation shows that it is an illegal event with reward, the investigator Ut will be requested to insert his/her IC card and enter his/her PIN code. If the PIN code is correct, the server will use the investigator Ut’s private key PRKUt to sign the case. The signature of the investigator Sigt includes the identity of the investigator IDt, event number SNevent, reporting event Msgevent, event verification result Msgver and the reward amount Cash:
Sigt = SPRKUt(IDt, SNevent, Msgevent, Msgver, Cash)
The investigator will close it, and the IDt, SNevent, Msgevent, Msgver, Cash and Sigt are stored directly in the database.
Step 2: ServerPLA
When the reporting server receives the signature of the undertaker, the IDt, SNevent, Msgevent, Msgver, Cash and Sigt will be stored in the database.
Step 3: Us→ServerPLA;Us→Ut
When the superior receives the signature of the investigator, the superior Us will use the public key PUKUt of the undertaker Ut to check whether the signature is correct. If it is correct, then the illegal event has passed the undertaker’s audit:
(IDt, SNevent, Msgevent, Msgver, Cash) ≟ VPUKUt(Sigt)
At this point, the superior Us audits the case checked by the investigator Ut again. If the superior agrees to issue the reward, then the case will be decided by signature. The reporting server will then request that the superior Us insert the IC card and enter the PIN code. If the PIN code is correct, the superior will use the IC card private key PRKUs to sign the case:
Sigs = SPRKUs(IDs, IDt, SNevent, Msgevent, Msgver, Cash)
The superior then sends IDs, IDt, SNevent, Msgevent, Msgver, Cash and Sigs to the reporting server and the investigator.
However, reward amounts differ from case to case. When the superior thinks the case requires further evaluation, this means the reward amount is higher than the superior thought. The superior thus sends IDs, IDt, SNevent, Msgevent, Msgver, Cash and Sigs to the upper superior to audit. The upper superior will follow the above steps to audit the case.
Step 4: ServerPLA→Ui
When the reporting server receives the signature of the superior, it will store IDs, IDt, SNevent, Msgevent, Msgver, Cash and Sigs in the database, and then check whether the audited case has been signed one by one. The reporting server uses the investigator’s public key PUKUt to verify the signature Sigt. If it is correct, then the investigator has already audited the case:
(IDt, SNevent, Msgevent, Msgver, Cash) ≟ VPUKUt(Sigt)
The reporting server then verifies the signature of the superior Us using the superior’s public key PUKUs to verify signature Sigs. If it is correct, then the reward has already been issued by the superior. In addition, if the reporting server receives all superiors’ signatures Sigs, it will verify all signatures Sigs by the following equation:
(IDs, IDt, SNevent, Msgevent, Msgver, Cash) ≟ VPUKUs(Sigs)
When the reporting server verifies the signature of the superior, it will automatically transmit a notification to the informer. Therefore, when the informer Ui logs into the platform, s/he will receive a notification to enter his/her the banking details ACCi.
2.2.5. Reward Issuing Phase
When the informer logs into the system and receives a remittance notification from the reporting server, the informer must fill in the remittance account within the effective period, beyond which the reward will not be issued. The reporting server will remit the reward through the designated payment server according to the existing remittance mechanism of the cooperating financial institution. Steps (1)–(4) describe the reward issuing process. The flow chart of reward issuing is shown in Figure 6.
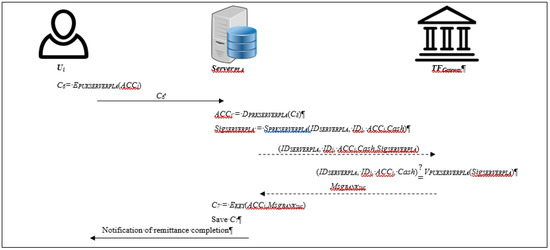
Figure 6.
The flow chart of the reward issuing phase.
Step 1: Ui→ServerPLA
The informer Ui logs into the system and receives a remittance notification, and then enters the bank account ACCi. ServerPLA uses the public key PUKSERVERPLA to encrypt the bank account ACCi and sends the encrypted message C8 to the reporting server:
C6 = EPUKSERVERPLA(ACCi)
Step 2: ServerPLA→TFGateway
The reporting server receives C8 from the informer Ui, then ServerPLA uses the private key PRKSERVERPLA to decrypt C8, and obtain the bank account ACCi of Ui:
ACCi = DPRKSERVERPLA(C6)
The ServerPLA then uses its private key PRKSERVERPLA to sign the remittance information:
and sends the remittance information and signature to the designated cooperating payment server TFGateway, and starts the payment.
SigSERVERPLA = SPRKSERVERPLA(IDSERVERPLA, IDi, ACCi, Cash),
Step 3: TFGateway→ServerPLA
When the payment server TFGateway receives the remittance information and signature SigSERVERPLA, it uses the server’s public key PUKSERVERPLA to verify the signature:
(IDSERVERPLA, IDi, ACCi, Cash) ≟ VPUKSERVERPLA(SigSERVERPLA)
If the verification is successful, the server will issue the reward to the informer Ui, and send a message MsgBANKsuc to the reporting server.
Step 4: ServerPLA→Ui
When the reporting server receives the reply message MsgBANKsuc of remittance from the cooperating payment server TFGateway, the server will verify the remittance information. If it is correct, then the remittance has been successful. After this, the server will send a message to inform the informer Ui that the reward has been remitted to the designated account. Finally, the reporting server uses the symmetric key KEY of ServerPLA to encrypt ACCi and MsgBANKsuc, and then stores the encrypted message C9 in the database:
C7 = EKEY(ACCi, MsgBANKsuc)
2.2.6. The Judgment of and Punishment for Abusing the System
If a report is judged by the investigator Ut to be abuse of the system, the report will be sent upward to the superior Us for further evaluation. When the reporting server receives confirmation from all the superiors that the report is abuse, it will suspend the informer, denying them access to the system for a period of time. If the user repeatedly abuses the system, and reaches the maximum threshold of abuse instances, the informer will be permanently banned from the system. On the other hand, as long as one superior Us confirms that the requires further evaluation, the reporting server will assign it to another investigator to re-check. This not only prevents bad judgments, but also prevents cases being erased.
3. System Implementation
3.1. Hardware and Software Environment
- IC Reader, personal identity IC card
- Apache
- PHP (Personal Home Page)
- Mysql
- Microsoft Windows Server
3.2. Implementation
3.2.1. Registration Phase
In the registration phase, the user can click the register button and enter the registration page, as shown in Figure 7. On this page the user must enter his/her account and password for registration. The system will then ask the user to insert his/her personal identity IC card and enter his/her PIN code, as shown in Figure 8. If the PIN code is correct, the system will send the SN to the certificate authority center via SSL (Secure Socket Layer) secure channel, and verify the user’s identity. If the verification result is correct, then the registration is complete.

Figure 7.
Resistration.

Figure 8.
Integrated Circuit card verification.
3.2.2. Login Phase
After the user (informer, investigator, superior) completes the registration, s/he can log into the reporting system by entering his/her account and password, as shown in Figure 9.
Figure 9.
Login page.
3.2.3. Reporting Phase
The informer can fill in the crime report form, inquire about the progress of cases, or modify personal data when logged into in the system. Figure 10 shows the flowchart of the reporting process. To report a crime, the informer selects the “Report” option, as shown in Figure 11 and fills out the form, as shown in Figure 12. When the informer submits the report form, the system asks the informer to insert his/her identity IC card (as shown in Figure 13) to verify his/her identity. If his/her identity is verified, the reporting procedure is completed.
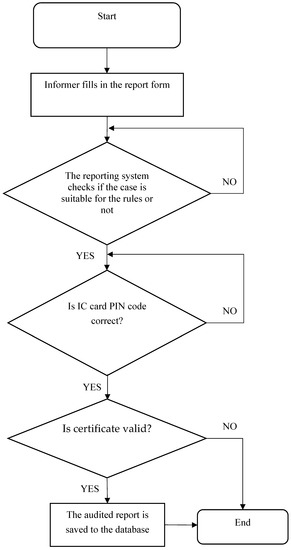
Figure 10.
Flowchart of informer’s reporting Figure 7 Registration process form.
Figure 11.
Informer menu page.
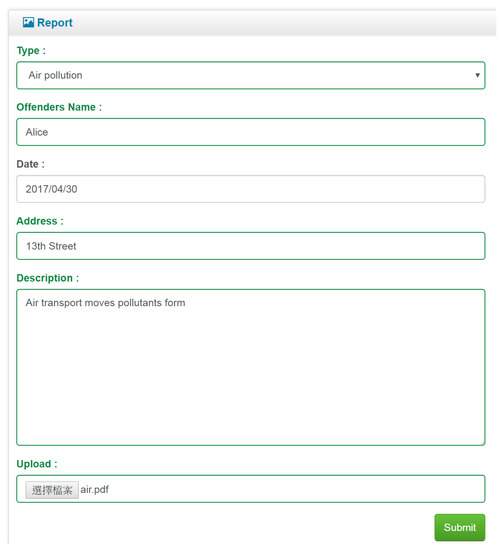
Figure 12.
Report form.

Figure 13.
Informer IC card verification page.
3.2.4. Contracting the Events
The flowchart of the investigator’s auditing process is shown in Figure 14. Figure 15 shows the main investigator page. The investigator can click the “pending” button in the menu of Figure 16 to check all cases pending investigation. All the pending cases are randomly assigned by the system to investigators. Figure 17 shows the list of pending cases. Clicking the last column of each case will open the auditing page, which shows the details for each case (see Figure 18). There are three notification choices in Figure 18 to indicate the auditing result. The meanings of these three choices are detailed as follows:
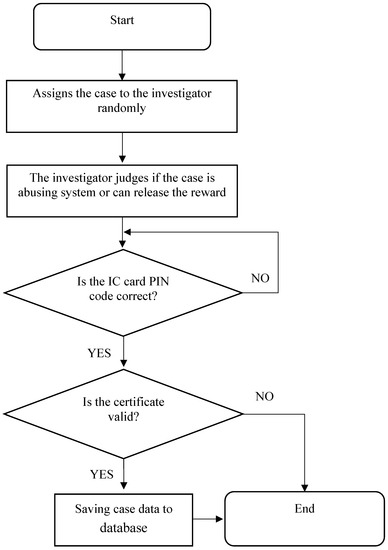
Figure 14.
Flowchart of investigator’s auditing process.
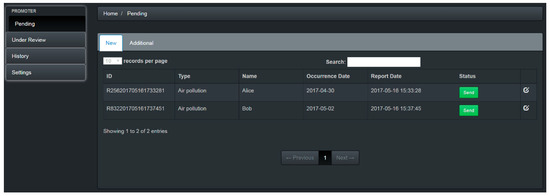
Figure 15.
The main investigator page.
Figure 16.
Investigator menu page.
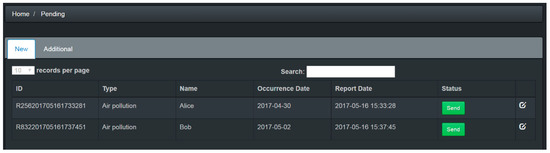
Figure 17.
List of the pending cases for investigators.
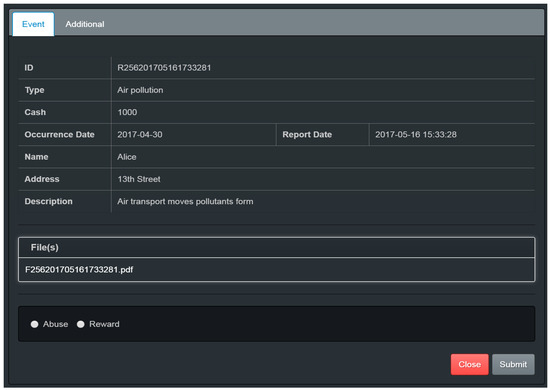
Figure 18.
Auditing page of pending case for investigator.
- (1)
- 【Abuse】button: If the reported case is not within the scope of contracting, or the reported content is not real, this choice will be used to report it to the system.
- (2)
- 【Reward】button: If the reported case is verified as real and must be rewarded, clicking the button will authorize the reward being issued.
- (3)
- 【Closed】button: If the reported case is verified as real and without reward, then clicking this button closes the case.
When the auditing result is submitted, the system will verify the IC card of the investigator, as shown in Figure 19.
Figure 19.
Investigator IC card verification page.
3.2.5. Upper Superior
Figure 20 shows the flowchart of the superior’s auditing process. The flowchart of the reward issuing process is shown in Figure 21. Figure 22 shows the main page when the superior logs into the system. On this page, the superior can check audited cases, and whether the cases are over time. If a case has not been audited by an investigator within the specified time, the system will automatically report it to the upper superior. The superior can select the “Expired” item in Figure 23 to recheck or reassign the expired case. In addition, the superior can click the “Pending” button to review audited abuse or reward cases, as shown in Figure 24.
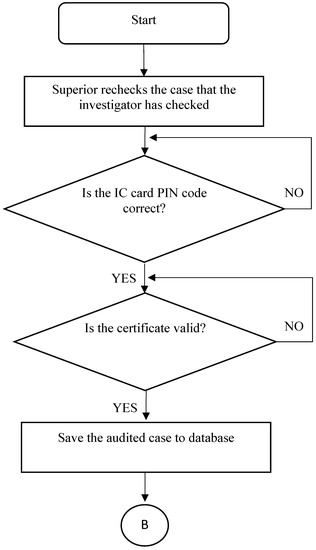
Figure 20.
Flowchart of superior’s auditing process.
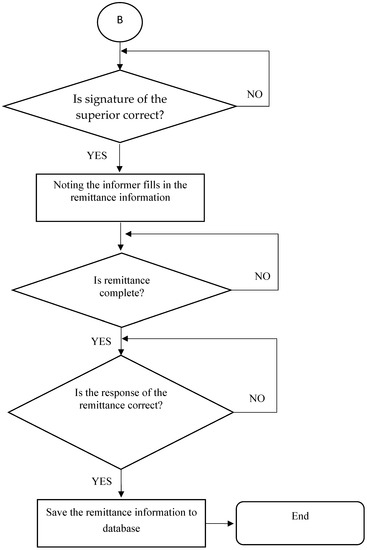
Figure 21.
Flowchart of reward issuing process.
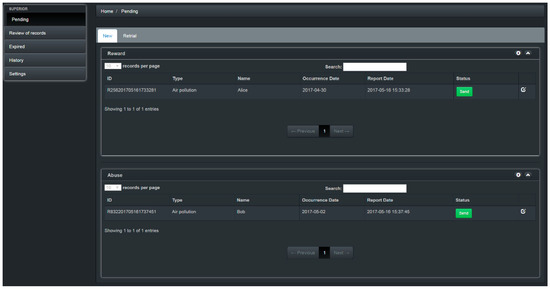
Figure 22.
The main page of the superior.
Figure 23.
Menu of the superior page.
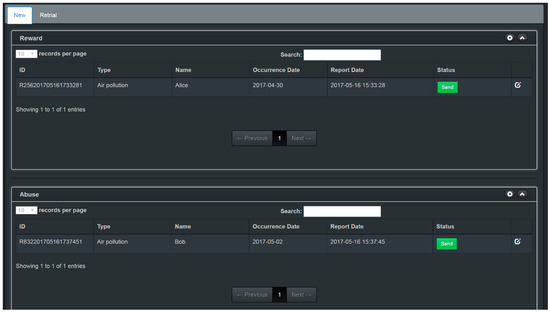
Figure 24.
List of pending cases for superior.
The Reward button is on the reward page, and the Abuse and Retrial buttons are on the abuse page. The functions of the three items are as follows:
- 【Reward】: When the reward has been confirmed for issue, the superior clicks the 【Reward】button, as shown in Figure 25.
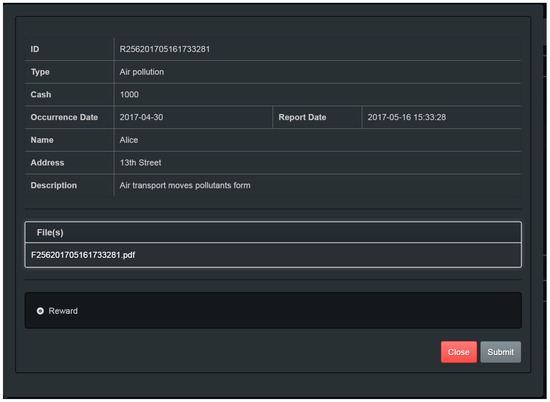 Figure 25. Reward audit page of superior.
Figure 25. Reward audit page of superior. - 【Abuse】: When the superior clicks the 【Abuse】 button in Figure 26, this means the case is an abusive reporting case.
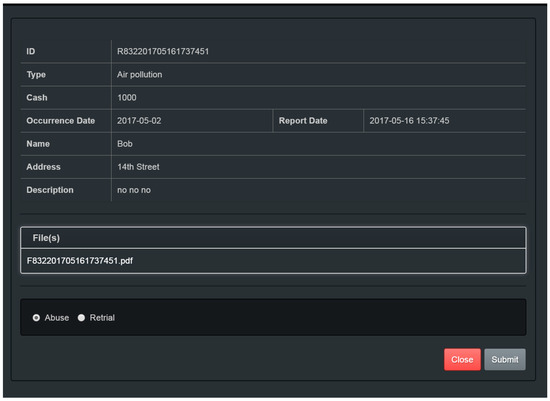 Figure 26. Abuse and retrial audit page of superior.
Figure 26. Abuse and retrial audit page of superior. - 【Retrial】: When a case is in doubt, it must be re-investigated. Such cases are called “retrial cases” and will be randomly assigned to a new investigator. The upper superior can designate a case in which there is cause for doubt as a retrial case by pressing the 【Retrial】 button, shown in Figure 26. The system will automatically reassign the retrial case to another investigator.
4. Discussion
4.1. The Identity of the Informer
To ensure the legality of the user’ identity, the system will verify the informer’s account IDi and password PWHASH when the informer logs into the system:
C2 = EPUKSERVERPLA(IDi, PWHASH)
(IDi, PWHASH) = DPRKSERVERPLA(C2)
Moreover, when the informer reports a crime, the informer must have an IC card. The system will obtain the SN and the last four digits of IDNO from the informer’s IC card. The SN will then be sent to ServerCA via SSL secure channel for verification:
C4 = EPUKSERVERPLA(IDNO, SN)
(IDNO, SN) = DPRKSERVERPLA(C4)
Scenario: Malicious users may continue to make false reports in an attempt to crash the reporting system’s server.
Analysis: The attack will fail because when an informer reports a crime; s/he must use their physical ID card, which includes the serial number SN and the ID number IDNO of the IC card. When the number of malicious reports exceeds the system threshold, the user’s reporting permission will be suspended. The proposed scheme can thus protect legal users’ identities from being abused, and can also prevent malicious reporting behavior.
4.2. Anonymous Reporting
In the reporting procedure, the system verifies the informer’s identity by certificate authority center so that the informer does not have to fill in personal information. When the center has checked the identity, it generates a case number. The content and IDi will be encrypted and stored in the database:
C5 = EKEY(IDi)
Therefore, the crime reports are stored in the database in such a way that the identity of informers is protected.
Scenario: If an informer’s true identity is leaked during the reporting process, his/her safety may be at risk as a result.
Analysis: Any attempt to obtain an informer’s the true identity will fail, as in the proposed scheme, the key message is encrypted with the asymmetric key of the reporting server. Only the legal reporting server can know the true identity of the informer. Therefore, malicious users will not be able to obtain the true identity of the informer and threaten their safety.
4.3. The Integrity of the Data
1. The reporting server uses the following formula to confirm whether the case has been reported by the informer him/herself:
(IDi, Msgevent) ≟ VPUKUi(Sigi)
Scenario: Malicious users may try to intercept the report in order to modify its content.
Analysis: The attack will fail because the message is encrypted with the public key of the reporting server C3 = EPUKSERVERPLA(IDi, Msgevent), and signed with the private key of the informer Sigi = SPRKUi(IDi, Msgevent). Thus, malicious users cannot modify report content.
2. An investigator attaches their signature when a case has been audited. The following formula can then be used to verify the signature to ensure the case is signed by the investigator correctly:
(IDt, SNevent, Msgevent, Msgver) ≟ VPUKUt(Sigt)
Scenario: Malicious users may try to intercept the investigator’s audit results in order to modify them.
Analysis: The attack will fail because the message is signed with the private key of the investigator Sigt = SPRKUt(IDt, SNevent, Msgevent, Msgver, Cash). Thus, malicious users cannot modify audit results.
3. The reporting server can ensure that the reward is issued by the superior using the following equation:
(IDs, IDt, SNevent, Msgevent, Msgver) ≟ VPUKUs(Sigs)
Scenario: Malicious users may try to intercept the reward information from the superior in order to modify it.
Analysis: The attack will fail because the message is signed with the private key of the superior Sigs = SPRKUs(IDs, IDt, SNevent, Msgevent, Msgver, Cash). Thus, malicious users cannot modify the reward information.
4.4. Non-Repudiation
In order to ensure non-repudiation, the proposed system has a completion verification mechanism, as shown in Table 1, which achieves non-repudiation as follows:

Table 1.
The verifiable proofs of non-repudiation.
- The reporting server will verify the informer’s signature Sigi; therefore, the informer cannot deny the signature.
- The reporting server will verify the investigator’s signature Sigt; therefore, the investigator cannot deny the signature.
- The superior receives the Sigt of a reward case form an investigator, and the superior will verify the Sigt; therefore, the investigator cannot deny the signature.
- The reporting server receives the Sigs, which means the superior agrees to issue the reward; therefore, the superior cannot deny that they confirmed the reward.
- The cooperating payment server will receive the SigSERVERPLA issued by the reporting server; therefore, the reporting server cannot deny that it confirmed the reward.
4.5. Preventing the Case Being Erased
The proposed system is equipped with an automatic notification mechanism to prevent investigators ignoring cases. If an investigator does not audit a case within a default period of time, the reporting server will automatically send the case to an upper superior.
4.6. Secure Reward Issuing
The secure issuing of the reward is shown in Figure 27, and the processes are as follows:
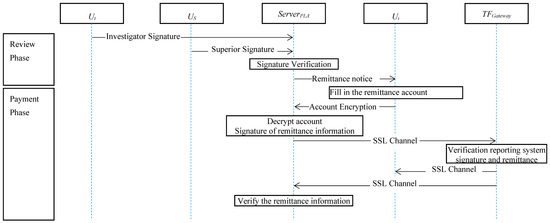
Figure 27.
The flowchart of the reward payment phase.
(1) Auditing phase:
The Ut and US send Sigt and Sigs to ServerPLA, respectively:
Sigt = SPRKUt(IDt, SNevent, Msgevent, Msgver, Cash)
Sigs = SPRKUs(IDs, IDt, SNevent, Msgevent, Msgver, Cash)
ServerPLA can verify each signature of the superior by the following equations:
(IDt, SNevent, Msgevent, Msgver, Cash) ≟ VPUKUt(Sigt)
(IDs, IDt, SNevent, Msgevent, Msgver, Cash) ≟ VPUKUs(Sigs)
According to Formulae (39) and (40), only if the signature verification is successful will the ServerPLA instruct the Ui to enter the remittance account.
Scenario: The informer attempts to modify the survey results, change the survey failure to success, or change the reward amount.
Analysis: The attack will fail to modify the survey results or reward information because the message is signed with the private key of the investigator Sigt = SPRKUt(IDt, SNevent, Msgevent, Msgver, Cash) and superior Sigs = SPRKUs(IDs, IDt, SNevent, Msgevent, Msgver, Cash). The reporting server will verify (IDt, SNevent, Msgevent, Msgver, Cash) ≟ VKUt(Sigt) and (IDs, IDt, SNevent, Msgevent, Msgver, Cash) ≟ VKUs(Sigs). Thus, the informer cannot modify the survey results or reward information.
(2) Remitting phase:
When Ui receives the notice from ServerPLA, Ui provides the remittance account ACCi. Then, the account ACCi is encrypted by Formula (41) and the encryption C8 is sent to ServerPLA. When the reporting server ServerPLA receives C8, it decrypts C8 by Formula (42) to obtain the ACCi of the Ui:
C6 = EPUKSERVERPLA(ACCi)
ACCi = DPRKSERVERPLA(C6)
Then, ServerPLA signs the remittance information by Formula (43) and sends it to the TFGateway via SSL, and begins the payment:
SigSERVERPLA = SPRKSERVERPLA(IDSERVERPLA, IDi, ACCi, Cash)
(IDSERVERPLA, IDi, ACCi, Cash) ≟ VPUKSERVERPLA(SigSERVERPLA)
The server uses Formula (44) to verify the signature. If the signature is correct, the cooperating payment server will remit to the Ui, and then send the completed message to the ServerPLA, thus preventing an incorrect amount being paid, or payment being made to the wrong person.
From the above analysis, the reward mechanism cannot be corrupted or altered. Therefore, it ensures the security of the identity of the informer. In addition, the system uses an automatic remittance mechanism. The signature mechanism ensures the identity of the superior, and this mechanism therefore not only ensures the identity, but also the confirmation of the reward. This shows that the system uses digital signatures, asymmetric key, and SSL to achieve the remittance operations.
Scenario: Malicious users attempt to modify the bank account information, and try to get the rewards of the informer.
Analysis: The attack will fail because the message is signed with the private key of the reporting server SigSERVERPLA = SPRKSERVERPLA(IDSERVERPLA, IDi, ACCi, Cash). After the designated cooperating payment server TFGateway receives the message via secure channel, it will verify (IDSERVERPLA, IDi, ACCi, Cash) ≟ VPUKSERVERPLA(SigSERVERPLA). Thus, the attacker cannot modify the bank account information to get the rewards.
4.7. Untraceability
In order to protect the privacy of informers in any actions, the proposed system uses a symmetric key algorithm to encrypt its database, further protecting the identity of the informer:
C5 = EKEY(IDi)
4.8. Confidentiality
- (1)
- The reporting server uses the SSL security protocol to ensure secure data transmission. In the registration phase, a one-way hash function is used to convert PWx into PWHASH, which prevent user passwords being leaked:PWHASH = H(PWx)
- (2)
- The system encrypts the IDi of the Ui with the symmetric key of ServerPLA to protect the identity of the informer in the event of a database security breach:C5 = EKEY(IDi)
- (3)
- In the auditing and reward phases, the server uses the asymmetric key of ServerPLA to encrypt ACCi, and MsgBANKsuc to protect sensitive informer information:C7 = EKEY(ACCi, MsgBANKsuc)
4.9. Comparison
The following compares the work in this study with the literature relating to online crime reporting systems with identity protection, as shown in Table 2.

Table 2.
The comparison of related works.
Table 2 shows that [1,2,6,7] respectively proposed an anonymous on-line crime reporting system. However, these systems mostly do not support authentication, data integrity, non-repudiation, prevention of case deletion, untraceability, the reward mechanism, confidentiality, preclusion of false reports and theoretical analysis etc. Thus, the proposed scheme is a more secure and practical reporting system based on cryptography.
5. Conclusions
Despite its continued presence in many (if not all) communities, some people are still afraid to report crimes, as they fear for their own safety should their identities become known to those they report. This results in an environment in which it is difficult to combat crime, and in which crime is even more likely to occur. In order to address this problem, this study proposes a cloud-based online crime reporting system with identity protection. The system not only addresses the concern that an informer’s identity may be revealed, but in doing so unites communities in combating crime. The proposed system combines digital certificates, encryption and decryption technology, and the credibility of a third party with the necessary certification. Thus it is able to verify informer identities, prevent the exposure of those identities, as well as preventing reports being erased. Using this simple and safe online reporting system, people can safely report criminal activity, thus improving and protecting the quality of life in their communities. The proposed scheme addresses all the security requirements to allow the reporting of crimes, while ensuring informers’ safety, security, anonymity and convenience. Furthermore, the proposed scheme is designed to be robust against abusive use, and is able to preclude false reports. Table 2 shows that the proposed method outperforms other related schemes. This study developed the reporting system for testing, and future work will collect data and evaluate its performance for system improvement. Finally, the authors hope that the proposed reporting system will be an effective and widely used tool in the ongoing fight against crime.
Author Contributions
Conceptualization, T.-F.S. and B.-Y.S.; validation, C.-L.C. and Y.-Y.D.; writing—original draft preparation, B.-Y.S.; writing—review and editing, T.-F.S., C.-L.C.; supervision, T.-F.S., C.-L.C.
Acknowledgments
This research was supported by the Ministry of Science and Technology, Taiwan, R.O.C., under contract numbers MOST 106-2221-E-324-013, MOST 106-2622-E-305-001-CC2 and MOST 103-2632-E-324-001-MY3.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Ku, C.H.; Iriberri, A.; Leroy, G. Crime Information Extraction from Police and Witness Narrative Reports. In Proceedings of the 2008 IEEE International Conference on Technologies for Homeland Security, Westin Hotel, Waltham, MA, USA, 12–13 May 2008; pp. 12–13. [Google Scholar]
- Iriberri, A.; Leroy, G. Natural Language Processing and e-Government: Extracting Reusable Crime Report Information. In Proceedings of the IEEE International Conference on Information Reuse and Integration, Las Vegas, NV, USA, 13–15 August 2007; pp. 221–226. [Google Scholar]
- Simon, I.S. The Fear of Reprisal and the Failure of Victims to Report a Personal Crime. J. Quant. Criminol. 1988, 4, 289–302. [Google Scholar]
- Iriberri, A.; Leroy, G.; Garrett, N. Reporting On-Campus Crime Online: User Intention to Use. In Proceedings of the 39th Hawaii International Conference on System Sciences, Kauia, HI, USA, 4–7 January 2006; pp. 1–10. [Google Scholar]
- USA.gov-Home. Available online: https://www.usa.gov/ (accessed on 15 May 2018).
- Sakpere, B.A.; Kayem, A.V.D.M.; Ndlovu, T. A Usable and Secure Crime Reporting System for Technology Resource Constrained Context. In Proceedings of the 2015 IEEE 29th International Conference on Advanced Information Networking and Applications Workshops (WAINA), Gwangiu, Korea, 24–27 March 2015; pp. 424–429. [Google Scholar]
- Eugene, F.F. Anonymous Reporting System. U.S. Patent 9135598 B2, 15 September 2015. Available online: https://www.google.com/patents/US9135598 (accessed on 15 February 2019).
- Sánchez-García, J.; García-Campos, J.M.; Reina, D.G.; Toral, S.L.; & Barrero, F. On-site DriverID: A Secure Authentication Scheme Based on Spanish eID Cards for Vehicular Ad Hoc Networks. Future Gener. Comput. Syst. 2016, 64, 50–60. [Google Scholar] [CrossRef]
- Zwattendorfer, B.; Slamanig, D. The Austrian eID Ecosystem in the Public Cloud: How to Obtain Privacy While Preserving Practicality. J. Inf. Secur. Appl. 2016, 27–28, 35–53. [Google Scholar] [CrossRef][Green Version]
- Cernian, A.; Olteanu, A.; Mateescu, G.; Vladescu, M.; Stamatescu, G.; Ropot, A.; Plesca, C.; Togan, M.; Sgarciu, V.; Carstoiu, D.; et al. The Design and Implementation of An Experimental Model for Secure Management of Personal Data Based on Electronic Identity Card and PKI Infrastructure. IFAC Proc. Vol. 2016, 45, 1697–1701. [Google Scholar] [CrossRef]
- Bajpai, D.; Vardhan, M.; Gupta, S.; Kumar, R.; Kushwaha, D.S. Security Service Level Agreements Based Authentication and Authorization Model for Accessing Cloud Services. Adv. Comput. Inf. Technol. 2012, 176, 719–728. [Google Scholar] [CrossRef]
- Hwang, J.J.; Chuang, H.K.; Hsu, Y.C.; Wu, C.H. A Business Model for Cloud Computing Based on A Separate Encryption and Decryption Service. In Proceedings of the 2011 International Conference on Information Science and Applications, Jeju Island, Korea, 26–29 April 2011; pp. 26–29. [Google Scholar]
- Wang, H.; He, W.; Wang, F.K. Enterprise Cloud Service Architectures. Inf. Technol. Manag. 2012, 13, 445–454. [Google Scholar] [CrossRef]
- Tsai, Y.L. Cloud Computing Security. Commun. CCISA 2012, 18, 62–68. [Google Scholar]
- Karuppiah, M.; Saravanan, R. A Secure Remote User Mutual Authentication Scheme Using Smart Cards. J. Inf. Secur. Appl. 2014, 19, 282–294. [Google Scholar] [CrossRef]
- Maliki, T.E.; Seigneur, J.M. Chapter 4–Online Identity and User Management Services. In Managing Information Security, 2nd ed.; Syngress: Rockland, MA, USA, 2014; pp. 75–118. [Google Scholar]
- Zhu, B.; Setia, S.; Jajodia, S.; Wang, L. Providing Witness Anonymity Under Peer-to-Peer Settings. IEEE Trans. Inf. Forens. Secur. 2010, 5, 324–336. [Google Scholar] [CrossRef]
- Vigil, M.; Buchmann, J.; Cabarcas, D.; Weinert, C.; Wiesmaier, A. Integrity, Authenticity, Non-repudiation, and Proof of Existence for Long-term Archiving: A Survey. Comput. Secur. 2015, 50, 16–32. [Google Scholar] [CrossRef]
- Sergio, M.; Esther, L.M.; Africa, L.R.; Joaquin, C.; Alexis, M.P.; Manuel, C. Analysis of New Technology Trends in Education: 2010–2015. IEEE Access 2018, 6, 36840–36848. [Google Scholar] [CrossRef]
- Tan, H.; Chung, I. A Secure and Efficient Group Key Management Protocol with Cooperative Sensor Association in WBANs. Sensors 2018, 18, 3930. [Google Scholar] [CrossRef] [PubMed]
- Tan, H.; Choi, D.; Kim, P.; Pan, S.; Chung, I. Secure Certificateless Authentication and Road Message Dissemination Protocol in VANETs. Wirel. Commun. Mob. Comput. 2018, 7978027. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).