Security and Accuracy of Fingerprint-Based Biometrics: A Review
Abstract
1. Introduction
- (1)
- Law enforcement: Biometric technology has been embraced with open arms by law enforcement agencies across the world for its efficiency in security-oriented scenarios. In fact, biometrics is not a new tool in law enforcement. Fingerprint biometrics have been adopted by Argentinian criminologists for more than a century. Nowadays, with rapid technological development, biometrics have launched a worldwide revolution in law enforcement. Biometric recognition systems have now been utilized by law enforcement agencies of many countries, including the United States, United Kingdom, Australia, and China. For example, in 2011, the Department of Defense and the FBI started working on the United States’ next generation biometric system, named Next Generation Identification (NGI), which is designed to include fingerprint, face, iris, and palm data, and their facial recognition program became fully operational in late 2014 [9].
- (2)
- Border control: In order to prevent identity fraud and strengthen border and national security, many countries employ biometric systems to track and manage the flow of passengers across borders. For instance, since 2008, all non-Americans who travel to the United States are requested to scan their fingerprint by US border security officials [10]. In order to eliminate the need for paper passports, Australia is planning to boost its “Seamless Traveler” program. The proposal of this program is to have 90 percent of the 35 million annual travelers to enter Australia via a paperless biometric recognition system by 2020 [11].
- (3)
- Consumer biometrics: Consumer devices equipped with biometric systems are standalone products for the consumer market, such as door locks, surveillance systems, automotive, and especially mobile devices (smartphones, tablets, etc.). In the past, passwords were the only secure way of authentication, and fingerprint scanners were most likely used by law enforcement agencies and the military. However, times have changed. In the last decade, biometric technology has developed in leaps and bounds and spread to every corner of our lives as a more secure method of authentication. With the popularity of smart phones, mobile phones utilizing biometrics is a winning combination in the consumer market, allowing biometric technology to become much more widely accepted [12].
- (4)
- Financial services: Finance is the most mature biometrics market outside the domain of law enforcement for the logic that protecting money is the first priority for most people. Financial companies have been early adopters of biometrics. For example, cash machines with fingerprint readers are currently deployed at an increasing pace [13]. Moreover, a new MasterCard, which includes an embedded fingerprint reader, attempts to introduce a biometric authentication layer for card payment [14], so as to enhance customers’ comfort level in terms of security and convenience.
- Security and recognition accuracy, despite being two most important aspects in biometric system design, have not been adequately studied simultaneously. Prior to this review paper, no research work has delivered a comprehensive review considering both of them. In this paper, up-to-date research and insights into security and recognition accuracy are thoroughly analyzed and discussed.
- Based on a thorough analysis, limitations of existing research are discussed and suggestions for future work to overcome those limitations are provided.
- The two most critical attacks to biometric systems are discussed in this paper. How to resolve the challenges, so as to defend biometric systems, is the focus of current and future biometric security research.
- Most existing methods, either with or without template protection, were set forth in ideal situations. In this paper, we emphasize the importance of considering recognition accuracy under non-ideal conditions. Our analysis is backed by solid evidence and detailed comparison.
2. Security Analysis: Attacks and Countermeasures
- (a)
- Attacks at the interface, e.g., attacks at point 1;
- (b)
- Attacks at the modules, e.g., attacks at points 3 and 5;
- (c)
- Attacks to the channels between modules, e.g., attacks at points 2, 4, 7, and 8;
- (d)
- Attacks to the template database, e.g., attacks at point 6.
2.1. Attacks to User Interface and Countermeasures
2.2. Attacks to Template Databases and Countermeasures
2.2.1. Cancelable Biometrics
2.2.2. Biometric Cryptosystems
3. Recognition Accuracy
3.1. Accuracy under Ideal vs. Non-Ideal Conditions
3.2. Accuracy Without vs. With Template Protection
4. Conclusions
- New developments in deep learning techniques have enhanced the performance of biometric systems across a wide range of biometric modalities, such as face recognition modality. We envisage that deep learning techniques [78,79,80] will also be potential tools for latent fingerprint matching. However, the use of deep learning algorithms may bring potential threats to biometric systems because of the vulnerabilities of those deep learning algorithms themselves.
- The security issues (e.g., spoofing attacks, attacks to biometric templates) analyzed for a general biometric system are also valid to any biometric system on different platforms, for example, a mobile platform. Nowadays, smartphones are becoming more and more popular, thus forming a promising platform for the use of biometrics [81]. However, mobile biometrics face more challenges, since smartphones usually have less computing capability and limited energy. Therefore, light-weight secure algorithm design for mobile biometrics is an emerging research topic [82,83,84].
- Trade-off between security and recognition accuracy in fingerprint template protection remains a challenge. As shown in Table 5, the best matching performance of fingerprint competition with template protection is the EER = 1.542%, which is much worse than that (EER = 0.022%) without template protection. Besides exploring more robust and distinctive features and designing better transformation functions, the use of multi-biometrics in template protection design is likely to be the way forward and deserves further research.
Author Contributions
Funding
Conflicts of Interest
References
- Jain, A.K.; Flynn, P.; Ross, A.A. Handbook of Biometrics; Springer: New York, NY, USA, 2007. [Google Scholar]
- Riaz, N.; Riaz, N.; Riaz, A.; Riaz, A.; Khan, S.A.; Khan, S.A. Biometric template security: An overview. Sensor Rev. 2017, 38, 120–127. [Google Scholar] [CrossRef]
- Prabhakar, S.; Pankanti, S.; Jain, A.K. Biometric recognition: Security and privacy concerns. IEEE Secur. Priv. 2003, 1, 33–42. [Google Scholar] [CrossRef]
- Awad, A.I.; Hassanien, A.E. Impact of Some Biometric Modalities on Forensic Science. In Computational Intelligence in Digital Forensics: Forensic Investigation and Applications; Springer: Berlin, Germany, 2014; pp. 47–62. [Google Scholar]
- Zheng, G.; Shankaran, R.; Orgun, M.A.; Qiao, L.; Saleem, K. Ideas and challenges for securing wireless implantable medical devices: A review. IEEE Sens. J. 2016, 17, 562–576. [Google Scholar] [CrossRef]
- Zheng, G.; Fang, G.; Shankaran, R.; Orgun, M.A.; Zhou, J.; Qiao, L.; Saleem, K. Multiple ECG fiducial points-based random binary sequence generation for securing wireless body area networks. IEEE J. Biomed. Health Inf. 2017, 21, 655–663. [Google Scholar] [CrossRef]
- Zheng, G.; Fang, G.; Shankaran, R.; Orgun, M.A. Encryption for implantable medical devices using modified one-time pads. IEEE Access 2015, 3, 825–836. [Google Scholar] [CrossRef]
- Awad, A.I.; Hassanien, A.E.; Zawbaa, H.M. A Cattle Identification Approach Using Live Captured Muzzle Print Images. In Advances in Security of Information and Communication Networks; Springer: Berlin, Germany, 2013; pp. 143–152. [Google Scholar]
- The FBI Now Has the Largest Biometric Database in the World. Will It Lead to More Surveillance? Available online: http://www.ibtimes.com/fbi-now-has-largest-biometric-database-world-will-it-lead-more-surveillance-2345062 (accessed on 27 November 2018).
- U.S. Security Officials Will Begin Scanning All 10 Fingerprints of Most Non-Americans Traveling to the United States. Available online: https://travel.state.gov/content/visas/en/news/u-s--security-officials-will-begin-scanning-all-10-fingerprints-.html (accessed on 27 November 2018).
- Australia Wants to Streamline Its Border Control Using Biometrics. Available online: http://www.smithsonianmag.com/innovation/australia-wants-to-streamline-its-border-control-using-biometrics-180962052/ (accessed on 27 November 2018).
- How Biometrics on Smartphones is Changing our Lives. Available online: http://www.m2sys.com/blog/biometric-resources/biometrics-on-smartphones/ (accessed on 27 November 2018).
- Biometrics for Finance Applications. Available online: https://www.tractica.com/research/biometrics-for-finance-applications/ (accessed on 27 November 2018).
- MasterCard Trials Biometric Bankcard with Embedded Fingerprint Reader. Available online: https://techcrunch.com/2017/04/20/mastercard-trials-biometric-bankcard-with-embedded-fingerprint-reader/ (accessed on 27 November 2018).
- Maio, D.; Maltoni, D.; Capelli, R.; Franco, A.; Ferrara, M.; Turroni, F. FVC-onGoing: On-Line Evaluation of Fingerprint Recognition Algorithms. 2013. Available online: https://biolab.csr.unibo.it/fvcongoing/UI/Form/Home.aspx (accessed on 25 January 2019).
- Jain, A.K.; Ross, A.; Prabhakar, S. An introduction to biometric recognition. IEEE Trans. Circuits Syst. Video Technol. 2004, 14, 4–20. [Google Scholar] [CrossRef]
- Tipton, S.J.; White, D.J., II; Sershon, C.; Choi, Y.B. iOS security and privacy: Authentication methods, permissions, and potential pitfalls with touch id. Int. J. Comput. Inf. Technol. 2014, 3, 482–489. [Google Scholar]
- Ratha, N.K.; Connell, J.H.; Bolle, R.M. An analysis of minutiae matching strength. In Proceedings of the 3rd International Conference on Audio-and Video-Based Biometric Person Authentication, Halmstad, Sweden, 6–8 June 2001; pp. 223–228. [Google Scholar]
- Jain, A.K.; Nandakumar, K.; Nagar, A. Biometric template security. EURASIP J. Adv. Signal Process. 2008, 2008, 1–17. [Google Scholar] [CrossRef]
- El-Abed, M.; Lacharme, P.; Rosenberger, C. Privacy and Security Assessment of Biometric Systems; Cambridge Scholar Publishing: Cambridge, UK, 2015. [Google Scholar]
- Kang, H.; Lee, B.; Kim, H.; Shin, D.; Kim, J. A study on performance evaluation of the liveness detection for various fingerprint sensor modules. In Proceedings of the International Conference on Knowledge-Based and Intelligent Information and Engineering Systems, Oxford, UK, 3–5 September 2003; pp. 1245–1253. [Google Scholar]
- Schuckers, S.A. Spoofing and anti-spoofing measures. Inf. Secur. Tech. Rep. 2002, 7, 56–62. [Google Scholar] [CrossRef]
- Yang, W.; Hu, J.; Fernandes, C.; Sivaraman, V.; Wu, Q. Vulnerability analysis of iPhone 6. In Proceedings of the 14th Annual Conference on Privacy, Security and Trust (PST), Auckland, New Zealand, 12–14 December 2016; pp. 457–463. [Google Scholar]
- Tan, B.; Schuckers, S. Liveness detection for fingerprint scanners based on the statistics of wavelet signal processing. In Proceedings of the Conference on Computer Vision and Pattern Recognition Workshop (CVPRW’06), New York, NY, USA, 17–22 June 2006; p. 26. [Google Scholar]
- Coli, P.; Marcialis, G.L.; Roli, F. Fingerprint silicon replicas: Static and dynamic features for vitality detection using an optical capture device. Int. J. Image Graphics 2008, 8, 495–512. [Google Scholar] [CrossRef]
- Galbally, J.; Alonso-Fernandez, F.; Fierrez, J.; Ortega-Garcia, J. A high performance fingerprint liveness detection method based on quality related features. Future Gener. Comput. Syst. 2012, 28, 311–321. [Google Scholar] [CrossRef]
- Kim, W. Fingerprint liveness detection using local coherence patterns. IEEE Signal Process. Lett. 2017, 24, 51–55. [Google Scholar] [CrossRef]
- Jung, H.; Heo, Y. Fingerprint liveness map construction using convolutional neural network. Electron. Lett. 2018, 54, 564–566. [Google Scholar] [CrossRef]
- Kundargi, J.; Karandikar, R. Fingerprint liveness detection using wavelet-based completed LBP descriptor. In Proceedings of the 2nd International Conference on Computer Vision and Image Processing, Roorkee, India, 9–12 September 2017; Springer: Berlin, Germany, 2018; pp. 187–202. [Google Scholar]
- Xia, Z.; Yuan, C.; Lv, R.; Sun, X.; Xiong, N.N.; Shi, Y.-Q. A novel weber local binary descriptor for fingerprint liveness detection. IEEE Trans. Syst. Man Cybern. Syst. 2018. [Google Scholar] [CrossRef]
- Yuan, C.; Sun, X.; Wu, Q.J. Difference co-occurrence matrix using BP neural network for fingerprint liveness detection. Soft Comput. 2018, 1–13. [Google Scholar] [CrossRef]
- Ratha, N.K.; Connell, J.H.; Bolle, R.M. Enhancing security and privacy in biometrics-based authentication systems. IBM Syst. J. 2001, 40, 614–634. [Google Scholar] [CrossRef]
- Ratha, N.K.; Chikkerur, S.; Connell, J.H.; Bolle, R.M. Generating cancelable fingerprint templates. IEEE Trans. Pattern Anal. Mach. Intell. 2007, 29, 561–572. [Google Scholar] [CrossRef]
- Jin, A.T.B.; Ling, D.N.C.; Goh, A. Biohashing: Two factor authentication featuring fingerprint data and tokenised random number. Pattern Recogn. 2004, 37, 2245–2255. [Google Scholar] [CrossRef]
- Lee, C.; Choi, J.-Y.; Toh, K.-A.; Lee, S. Alignment-free cancelable fingerprint templates based on local minutiae information. IEEE Trans. Syst. Man Cybern. Part B Cybern. 2007, 37, 980–992. [Google Scholar]
- Ahn, D.; Kong, S.G.; Chung, Y.-S.; Moon, K.Y. Matching with secure fingerprint templates using non-invertible transform. In Proceedings of the Congress on Image and Signal Processing (CISP’08), Sanya, China, 27–30 May 2008; pp. 29–33. [Google Scholar]
- Yang, H.; Jiang, X.; Kot, A.C. Generating secure cancelable fingerprint templates using local and global features. In Proceedings of the 2nd IEEE International Conference on Computer Science and Information Technology (ICCSIT 2009), Beijing, China, 8–11 August 2009; pp. 645–649. [Google Scholar]
- Ahmad, T.; Hu, J. Generating cancelable biometrie templates using a projection line. In Proceedings of the 11th International Conference on Control Automation Robotics and Vision (ICARCV), Singapore, 7–10 December 2010; pp. 7–12. [Google Scholar]
- Wang, S.; Deng, G.; Hu, J. A partial Hadamard transform approach to the design of cancelable fingerprint templates containing binary biometric representations. Pattern Recogn. 2017, 61, 447–458. [Google Scholar] [CrossRef]
- Wang, S.; Hu, J. Alignment-free cancellable fingerprint template design: A densely infinite-to-one mapping (DITOM) approach. Pattern Recogn. 2012, 45, 4129–4137. [Google Scholar] [CrossRef]
- Wang, S.; Hu, J. Design of alignment-free cancelable fingerprint templates via curtailed circular convolution. Pattern Recogn. 2014, 47, 1321–1329. [Google Scholar] [CrossRef]
- Wang, S.; Hu, J. A blind system identification approach to cancelable fingerprint templates. Pattern Recogn. 2016, 54, 14–22. [Google Scholar] [CrossRef]
- Zhang, N.; Yang, X.; Zang, Y.; Jia, X.; Tian, J. Generating registration-free cancelable fingerprint templates based on Minutia Cylinder-Code representation. In Proceedings of the IEEE Sixth International Conference on Biometrics: Theory, Applications and Systems (BTAS), Arlington, VA, USA, 29 September–2 October 2013; pp. 1–6. [Google Scholar]
- Cappelli, R.; Ferrara, M.; Maltoni, D. Minutia cylinder-code: A new representation and matching technique for fingerprint recognition. IEEE Trans. Pattern Anal. Mach. Intell. 2010, 32, 2128–2141. [Google Scholar] [CrossRef]
- Ferrara, M.; Maltoni, D.; Cappelli, R. Non-invertible minutia cylinder-code representation. IEEE Trans. Inf. Foren. Sec. 2012, 7, 1727–1737. [Google Scholar] [CrossRef]
- Ferrara, M.; Maltoni, D.; Cappelli, R. A two-factor protection scheme for MCC fingerprint templates. In Proceedings of the 2014 International Conference of the Biometrics Special Interest Group (BIOSIG), Darmstadt, Germany, 10–12 September 2014; pp. 1–8. [Google Scholar]
- Arjona, R.; Prada-Delgado, M.A.; Baturone, I.; Ross, A. Securing minutia cylinder codes for fingerprints through physically unclonable functions: An exploratory study. In Proceedings of the 2018 International Conference on Biometrics (ICB), Gold Coast, Australia, 20–23 February 2018; pp. 54–60. [Google Scholar]
- Yang, W.; Hu, J.; Wang, S.; Wu, Q. Biometrics based Privacy-Preserving Authentication and Mobile Template Protection. Wirel. Commun. Mobile Comput. 2018, 2018, 17. [Google Scholar] [CrossRef]
- Sandhya, M.; Prasad, M.V. Securing fingerprint templates using fused structures. IET Biom. 2017, 6, 173–182. [Google Scholar] [CrossRef]
- Yang, W.; Wang, S.; Hu, J.; Zheng, G.; Valli, C. A fingerprint and finger-vein based cancelable multi-biometric system. Pattern Recogn. 2018, 78, 242–251. [Google Scholar] [CrossRef]
- Dwivedi, R.; Dey, S. A novel hybrid score level and decision level fusion scheme for cancelable multi-biometric verification. arXiv, 2018; arXiv:1805.10433. [Google Scholar]
- Juels, A.; Wattenberg, M. A fuzzy commitment scheme. In Proceedings of the 6th ACM Conference on Computer and Communications Security, Singapore, 1–4 November 1999; pp. 28–36. [Google Scholar]
- Uludag, U.; Jain, A.K. Fuzzy fingerprint vault. In Proceedings of the Workshop Proceedings—Biometrics: Challenges Arising from Theory to Practice, Cambridge, UK, 22–27 August 2004; pp. 13–16. [Google Scholar]
- Juels, A.; Sudan, M. A fuzzy vault scheme. Des. Codes Cryptogr. 2006, 38, 237–257. [Google Scholar] [CrossRef]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In Proceedings of the Advances in Cryptology-Eurocrypt 2004, Interlaken, Switzerland, 2–6 May 2004; pp. 523–540. [Google Scholar]
- Teoh, A.B.J.; Kim, J. Secure biometric template protection in fuzzy commitment scheme. IEICE Electron. Exp. 2007, 4, 724–730. [Google Scholar] [CrossRef]
- Uludag, U.; Pankanti, S.; Jain, A.K. Fuzzy vault for fingerprints. In Proceedings of the 5th International Conference on Audio-and Video-Based Biometric Person Authentication, Hilton Rye Town, NY, USA, 20–22 July 2005; pp. 310–319. [Google Scholar]
- Nandakumar, K.; Jain, A.K.; Pankanti, S. Fingerprint-based fuzzy vault: Implementation and performance. IEEE Trans. Inf. Forensics Secur. 2007, 2, 744–757. [Google Scholar] [CrossRef]
- Zhang, P.; Hu, J.; Li, C.; Bennamoun, M.; Bhagavatula, V. A pitfall in fingerprint bio-cryptographic key generation. Comput. Secur. 2011, 30, 311–319. [Google Scholar] [CrossRef]
- Li, P.; Yang, X.; Cao, K.; Tao, X.; Wang, R.; Tian, J. An alignment-free fingerprint cryptosystem based on fuzzy vault scheme. J. Netw. Comput. Appl. 2010, 33, 207–220. [Google Scholar] [CrossRef]
- Arakala, A.; Jeffers, J.; Horadam, K. Fuzzy extractors for minutiae-based fingerprint authentication. In Proceedings of the 2007 International Conference on Advances in Biometrics, Seoul, Korea, 27–29 August 2007; pp. 760–769. [Google Scholar]
- Xi, K.; Hu, J.; Han, F. An alignment free fingerprint fuzzy extractor using near-equivalent Dual Layer Structure Check (NeDLSC) algorithm. In Proceedings of the 6th IEEE Conference on Industrial Electronics and Applications (ICIEA), Beijing, China, 21–23 June 2011; pp. 1040–1045. [Google Scholar]
- Karthi, G.; Azhilarasan, M. Hybrid multimodal template protection technique using fuzzy extractor and random projection. IJRCCT 2013, 2, 381–386. [Google Scholar]
- Yang, W.; Hu, J.; Wang, S. A Delaunay Triangle-Based Fuzzy Extractor for Fingerprint Authentication. In Proceedings of the 2012 IEEE 11th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Liverpool, UK, 25–27 June 2012; pp. 66–70. [Google Scholar]
- Liu, E.; Zhao, Q. Encrypted domain matching of fingerprint minutia cylinder-code (MCC) with I1 minimization. Neurocomputing 2017, 259, 3–13. [Google Scholar] [CrossRef]
- Yang, W.; Hu, J.; Wang, S. A Delaunay triangle group based fuzzy vault with cancellability. In Proceedings of the 2013 6th International Congress on Image and Signal Processing (CISP), Hangzhou, China, 16–18 December 2013; pp. 1676–1681. [Google Scholar]
- Alam, B.; Jin, Z.; Yap, W.-S.; Goi, B.-M. An alignment-free cancelable fingerprint template for bio-cryptosystems. J. Netw. Comput. Appl. 2018, 115, 20–32. [Google Scholar] [CrossRef]
- Sarkar, A.; Singh, B.K. Cryptographic key generation from cancelable fingerprint templates. In Proceedings of the 2018 4th International Conference on Recent Advances in Information Technology (RAIT), Dhanbad, India, 15–17 March 2018; pp. 1–6. [Google Scholar]
- LeCun, Y.; Bengio, Y.; Hinton, G. Deep learning. Nature 2015, 521, 436. [Google Scholar] [CrossRef]
- Cappelli, R.; Maio, D.; Maltoni, D.; Wayman, J.L.; Jain, A.K. Performance evaluation of fingerprint verification systems. IEEE Trans. Pattern Anal. Mach. Intel. 2006, 28, 3–18. [Google Scholar] [CrossRef]
- Yoon, S.; Cao, K.; Liu, E.; Jain, A.K. LFIQ: Latent fingerprint image quality. In Proceedings of the 2013 IEEE Sixth International Conference on Biometrics: Theory, Applications and Systems (BTAS), Arlington, VA, USA, 29 September–2 October 2013; pp. 1–8. [Google Scholar]
- Cao, K.; Liu, E.; Jain, A.K. Segmentation and enhancement of latent fingerprints: A coarse to fine ridgestructure dictionary. IEEE Trans. Pattern Anal. Mach. Intell. 2014, 36, 1847–1859. [Google Scholar] [CrossRef]
- Arora, S.S.; Liu, E.; Cao, K.; Jain, A.K. Latent fingerprint matching: Performance gain via feedback from exemplar prints. IEEE Trans. Pattern Anal. Mach. Intell. 2014, 36, 2452–2465. [Google Scholar] [CrossRef]
- Nandakumar, K.; Jain, A.K. Biometric template protection: Bridging the performance gap between theory and practice. IEEE Signal Process. Mag. 2015, 32, 88–100. [Google Scholar] [CrossRef]
- Yang, W.; Wang, S.; Zheng, G.; Chaudhry, J.; Valli, C. ECB4CI: An enhanced cancelable biometric system for securing critical infrastructures. J. Supercomput. 2018, 74, 4893–4909. [Google Scholar] [CrossRef]
- Liu, E.; Zhao, H.; Liang, J.; Pang, L.; Xie, M.; Chen, H.; Li, Y.; Li, P.; Tian, J. A key binding system based on n-nearest minutiae structure of fingerprint. Pattern Recogn. Lett. 2011, 32, 666–675. [Google Scholar] [CrossRef]
- Yang, W.; Hu, J.; Wang, S.; Stojmenovic, M. An Alignment-free fingerprint bio-cryptosystem based on modified voronoi neighbor structures. Pattern Recogn. 2014, 47, 1309–1320. [Google Scholar] [CrossRef]
- Menotti, D.; Chiachia, G.; Pinto, A.; Schwartz, W.R.; Pedrini, H.; Falcao, A.X.; Rocha, A. Deep representations for iris, face, and fingerprint spoofing detection. IEEE Trans. Inf. Foren. Sec. 2015, 10, 864–879. [Google Scholar] [CrossRef]
- Goodfellow, I.; Bengio, Y.; Courville, A. Deep Learning; MIT press: Cambridge, MA, USA, 2016; Volume 1, 800p. [Google Scholar]
- Pandya, B.; Cosma, G.; Alani, A.A.; Taherkhani, A.; Bharadi, V.; McGinnity, T.M. Fingerprint classification using a deep convolutional neural network. In Proceedings of the 2018 4th International Conference on Information Management (ICIM), Oxford, UK, 25–27 May 2018; pp. 86–91. [Google Scholar]
- Yang, W.; Hu, J.; Yang, J.; Wang, S.; Lu, L. Biometrics for securing mobile payments: Benefits, challenges and solutions. In Proceedings of the 2013 6th International Congress on Image and Signal Processing (CISP), Hangzhou, China, 16–18 December 2013; pp. 1699–1704. [Google Scholar]
- Spolaor, R.; Li, Q.; Monaro, M.; Conti, M.; Gamberini, L.; Sartori, G. Biometric authentication methods on smartphones: A survey. PsychNology J. 2016, 14, 87–98. [Google Scholar]
- Wojciechowska, A.; Choraś, M.; Kozik, R. The overview of trends and challenges in mobile biometrics. J. Appl. Mathem. Comput. Mech. 2017, 16, 173–185. [Google Scholar] [CrossRef][Green Version]
- Rattani, A.; Reddy, N.; Derakhshani, R. Convolutional neural networks for gender prediction from smartphone-based ocular images. IET Biom. 2018, 7, 423–430. [Google Scholar] [CrossRef]
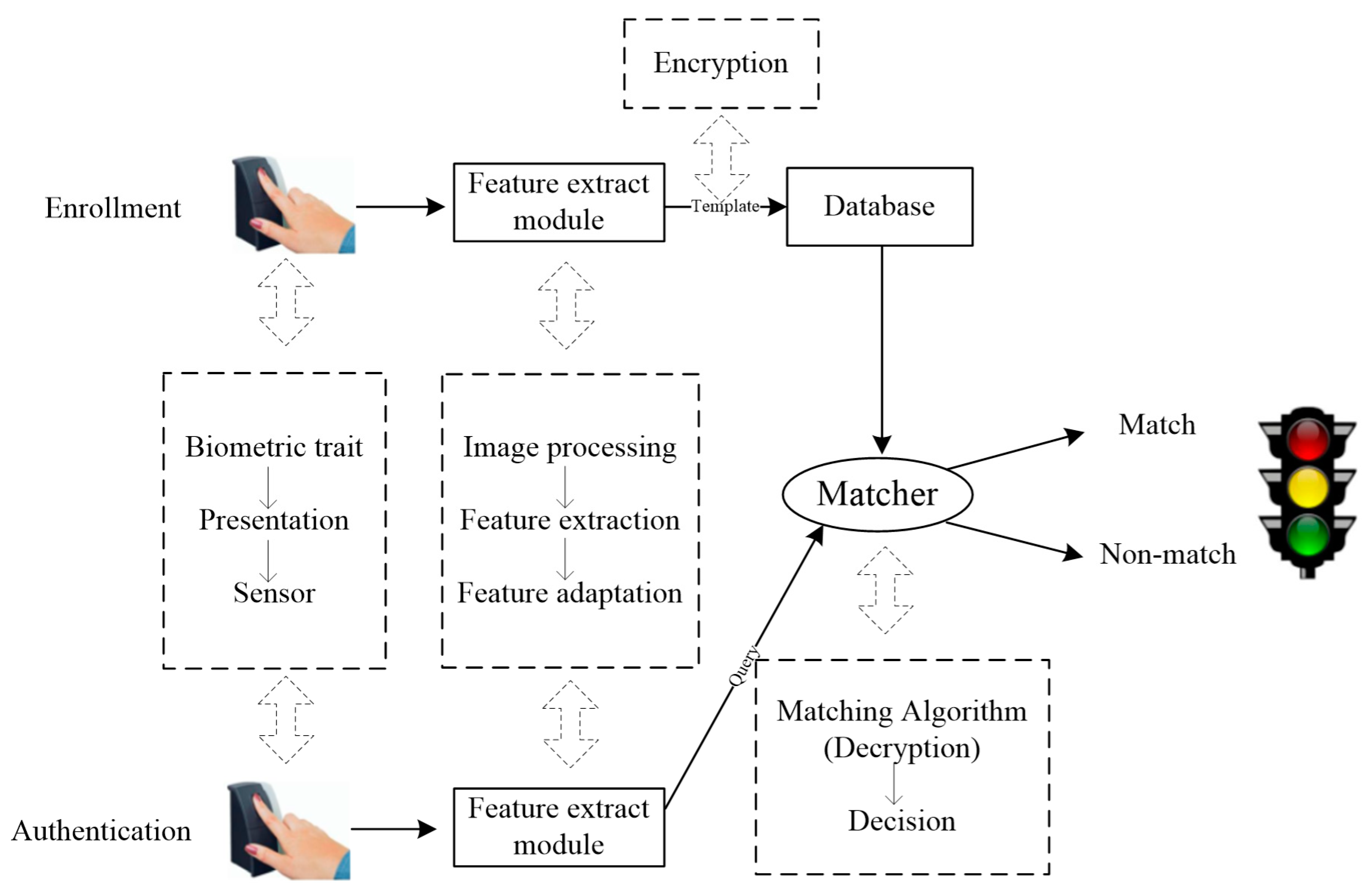
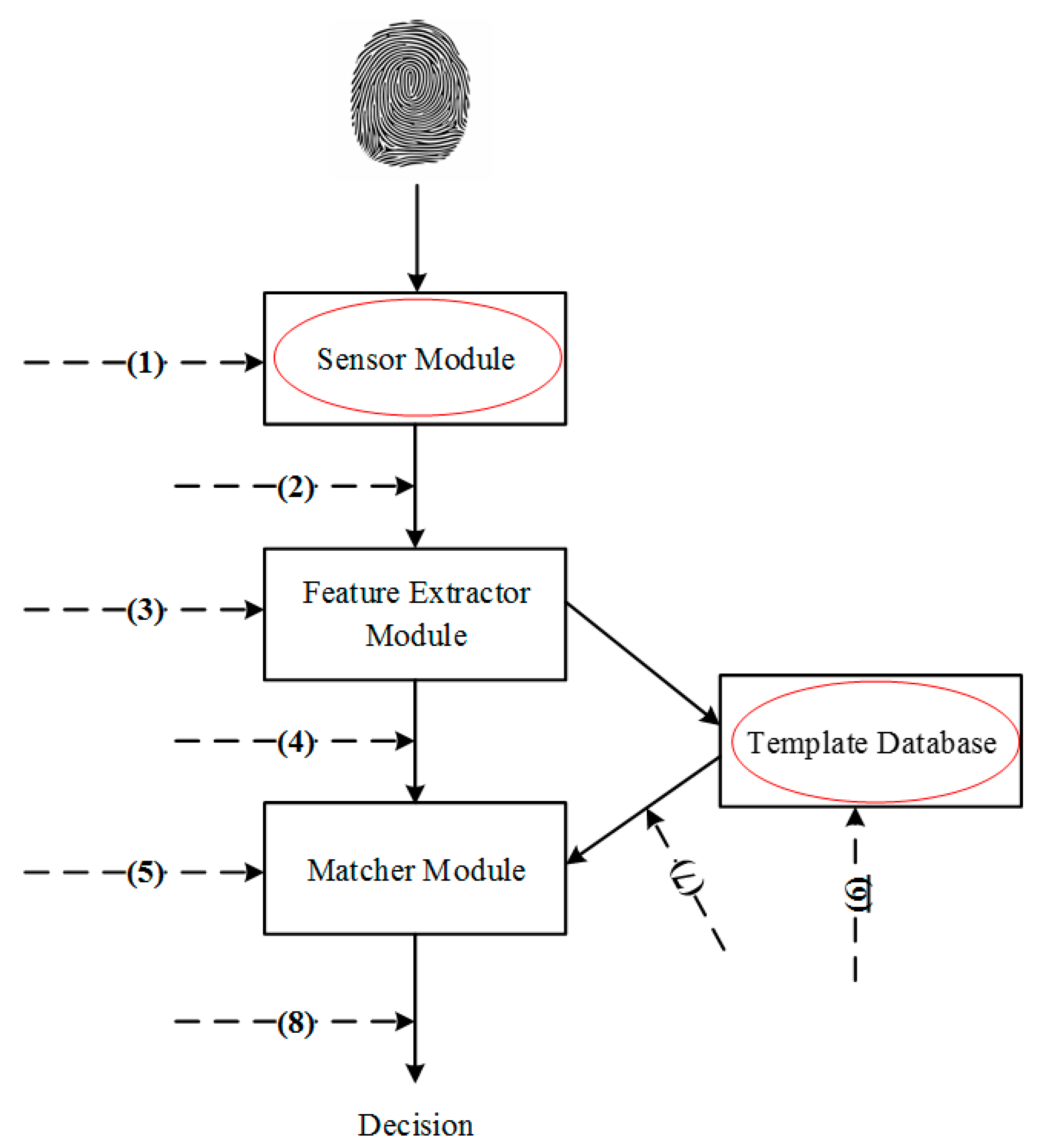

| Number | Attacks | Attack Points |
|---|---|---|
| 1 | Spoofing—present fake biometric data to sensor | 1 |
| 2 | Exploit similarity, e.g., using face from identical twins | 1 |
| 3 | Zero-effort attempt—attacker uses own biometric sample to impersonate an authorized user | 1 |
| 4 | Physically destroy the biometric sensor so as to make it out of service | 1 |
| 5 | Replay attack—the attacker intercepts a biometric signal and replay it into the system | 2 and 4 |
| 6 | Cut the communication channel to make the system unavailable | 2 and 4 |
| 7 | Denial of Service attack—alters the information from the channel in order to deny a genuine user from being authenticated | 2 and 4 |
| 8 | Hill-climbing attack—conveniently modify the query image until a desired matching score is obtained. | 2 and 4 |
| 9 | Continuously inject samples in order to deny genuine users to access the system | 2 and 4 |
| 10 | Inject Trojan horse programs | 3 and 5 |
| 11 | Attacker illegally obtains original biometric templates | 6 |
| 12 | Attacker modifies the template such as adding or replacing info | 6 |
| 13 | Read biometric templates from a communication channel and replay | 7 |
| 14 | Alter the information transmitted through a communication channel in order to deny genuine users to access the system | 7 |
| 15 | Cut the communication channel in order to make the system unavailable | 7 |
| 16 | Alter the transported matching or non-matching information in order to deny access of a genuine user or allow an impostor access. | 8 |
| 17 | Cut the communication channel in order to make the system unavailable | 8 |
| Approaches | Year of Publication | Category or Technique | Databases | Sensors | Best Performance (Correct Classification Rate) |
|---|---|---|---|---|---|
| Tan and Schuckers [24] | 2006 | Wavelet transform | Michigan State University (MSU) gummy finger database | Capacitive DC, optical, and electro-optical | 80%–100% |
| Coli et al. [25] | 2008 | Both static and dynamic features | Private database | Optical | 75.35% |
| Galbally et al. [26] | 2012 | Fingerprint parameterization based on 1uality related features | ATVS | Optical | 90% |
| Kim [27] | 2017 | Difference of the dispersion in the image gradient field | LivDet 2009 and ATVS | Optical | 95.63% (ATVS) 86.83% (LivDet 2009) |
| Jung and Heo [28] | 2018 | Convolutional neural network (CNN) | 2015 competition set | Optical | 98.60% |
| Kundargi and Karandikar [29] | 2018 | Completed local binary pattern (CLBP) and wavelet transform (WT) | LivDet 2011 | Optical | 91.7% |
| Xia et al. [30] | 2018 | Weber local binary and Support Vector Machine (SVM) | LivDet 2011, 2013, 2015 | Optical | 94.04% |
| Yuan et al. [31] | 2018 | BP neural network | LivDet 2013 | Optical | 93.22% |
| Cancelable Biometrics | ||||
|---|---|---|---|---|
| Approaches | Year of Publication | Category or Technique | Databases | Best Performance |
| Ratha et al. [32] | 2001 | Introduction of the “cancelable biometrics” concept | - | - |
| Jin et al. [34] | 2004 | Bio-hashing | FVC2002 DB1-DB4 | EER = 0 |
| Ratha et al. [33] | 2007 | Cartesian, polar, and surface folding transformations | - | - |
| Lee et al. [35] | 2007 | The first alignment-free cancelable fingerprint system | FVC2002 DB1 | EER = 3.4% |
| Ahn et al. [36] | 2008 | Using triplets of minutia points | FVC2002 DB2 | EER = 3.61% |
| Yang et al. [37] | 2009 | Using local and global features | FVC2002 DB2 | EER = 13% |
| Ahmad and Hu [38] | 2010 | Using a projection line | FVC2002 DB2 | EER ≈ 20% |
| Wang and Hu [40] | 2012 | A densely infinite-to-one mapping (DITOM) approach | FVC2002 DB1 FVC2002 DB2 FVC2002 DB3 | EER = 3.5% EER = 5% EER = 7.5% |
| Zhang et al. [43] | 2013 | A registration-free cancelable fingerprint template based on Minutia Cylinder Code (MCC) | - | - |
| Wang and Hu [41] | 2014 | Curtailed circular convolution | FVC2002 DB1 FVC2002 DB2 FVC2002 DB3 | EER = 2% EER = 3% EER = 6.12% |
| Ferrara et al. [46] | 2014 | A two-factor protection scheme using non-invertible transformation and user-specific key | FVC2002 DB1 FVC2002 DB2 FVC2002 DB3 FVC2002 DB4 FVC2004 DB1 FVC2006 DB2 | EER = 2% EER = 1.1% EER = 4.4% EER = 3.1% EER = 3.0% EER = 0.1% |
| Wang and Hu [42] | 2016 | A blind system identification approach | FVC2002 DB1 FVC2002 DB2 FVC2002 DB3 | EER=4% EER=3% EER=8.5% |
| Wang et al. [39] | 2017 | A partial Hadamard transform approach | FVC2002 DB1 FVC2002 DB2 FVC2002 DB3 FVC2004 DB2 | EER = 1% EER = 2% EER = 5.2% EER = 13.3% |
| Sandhya and Prasad [49] | 2017 | Using fused structures (both local and distant structures) at the feature level | FVC2004 DB1 FVC2004 DB2 FVC2004 DB3 | EER = 11.89% EER = 12.71% EER = 17.60% |
| Arjona et al. [47] | 2018 | Physically Unclonable Functions based on minutia cylinder codes | FVC2002 DB2 FVC2002 DB3 | EER = 0.39% EER = 0.81% |
| Yang et al. [48] | 2018 | Defeat the attacks via record multiplicity (ARM) through the feature decorrelation algorithm | FVC2002 DB1 FVC2002 DB2 FVC2002 DB3 FVC2004 DB2 | EER = 5.75% EER = 4.71% EER = 10.22% EER = 12% |
| Yang et al. [50] | 2018 | Cancelable multi-biometric system based on fingerprint and finger-vein | MD-A MD-B | EER = 0.55% EER = 0.69% |
| Dwivedi and Dey [51] | 2018 | Fusion at the score level and the decision level | Virtual_A Virtual_B Virtual_C | EER = 0.55% EER = 0.13% EER = 0.5% |
| Biometric Cryptosystems | ||||
|---|---|---|---|---|
| Approaches | Year of Publication | Category or Technique | Databases | Best Performance |
| Juels and Watternberg [52] | 1999 | Introduction of the cryptographic primitive, fuzzy commitment scheme | - | - |
| Uludag and Jain [53] | 2004 | Utilization of a fingerprint minutiae line based representation scheme in fuzzy vault | - | - |
| Dodis et al. [55] | 2004 | Proposes two primitives: fuzzy extractor and secure sketch | - | - |
| Uludag et al. [57] | 2005 | Realization of fuzzy vault with the fingerprint minutiae data | IBM-GTDB | FAR = 0 |
| Arakala et al. [61] | 2007 | The first fingerprint biometric application—protected Fuzzy Extractor | FVC2000 | EER ≈ 10% |
| Teoh and Kim [56] | 2007 | Randomized dynamic quantization, transformation to binarized biometric data, and protection by using fuzzy commitment | FVC2002 DB1 | FAR = 0, FRR = 0.9% |
| Nandakumar et al. [58] | 2007 | An automatic implementation of the fuzzy vault scheme based on fingerprint minutiae. High curvature points are derived from the fingerprint orientation field as helper data to align the template and query minutiae | FVC2002 DB2 | FAR = 0, FRR = 10% |
| Li et al. [60] | 2010 | An alignment-free fingerprint cryptosystem based on the fuzzy vault scheme, fusing the local features, known minutia descriptor, and minutia local structure | FVC2002 DB1, DB2 | FAR = 0.35, FRR = 17.5% FAR = 0, FRR = 10% |
| Xi et al. [62] | 2011 | Use the minutia local structure called Dual Layer Structure Check (DLSC) to eliminate the alignment process | FVC2002 DB2 | EER = 4.5% |
| Yang et al. [64] | 2012 | A registration-free Delaunay triangle-based fuzzy extractor. | FVC2002 DB2 | EER = 13% |
| Karthi and Azhilarasan [63] | 2013 | Use both the key generating cryptosystem and feature transformation method | FVC2004 | FAR = 1%, FRR = 1% |
| Yang et al. [66] | 2013 | A minutiae-based fuzzy vault with cancellability by applying a polar transformation to each Delaunay triangle group | FVC2002 DB1, DB2 | FAR = 0.38%, FRR = 19% FAR = 2.25%, FRR = 8% |
| Liu and Zhao [65] | 2017 | A secured fingerprint MCC matching scheme utilizing l1-minimization | FVC2002 DB1, DB2 FVC2004 DB1 | FAR = 0, FRR = 8.6% FAR = 0, FRR = 16% FAR = 0, FRR = 34.4% |
| Alam et al. [67] | 2018 | Bit-toggling strategy to inject noise into the proposed fingerprint template | FVC2002 DB1, DB2, DB3 FVC2004 DB1, DB2, DB3 | EER = 1% EER = 2.07% EER = 6.11% EER = 15.44% EER = 9.15% EER = 9.28% |
| Sarkar and Singh [68] | 2018 | A symmetric cryptographic key is spawned using cancelable fingerprint template | FVC2002 DB1 | - |
| Published on | Benchmark | Participant | Type | Algorithm | EER | |
|---|---|---|---|---|---|---|
| Without template protection | 27/07/2017 | FV-STD-1.0 | Beijing Hisign Bio-info Institute | Company | HXKJ | 0.022% |
| 09/02/2016 | FV-STD-1.0 | Neurotechnology Company | Company | MM_FV | 0.042% | |
| 29/08/2011 | FV-STD-1.0 | Tiger IT Bangladesh | Company | TigerAFIS | 0.108% | |
| With template protection | 28/12/2013 | STFV-STD-1.0 | Securics, Inc | Company | Biotope | 1.541% |
| 25/03/2013 | STFV-STD-1.0 | Biometric System Laboratory | Academic Research Group | P-MCC64 | 2.207% | |
| 25/02/2013 | STFV-STD-1.0 | Institute of Automation, Chinese Academy of Sciences | Academic Research Group | SCT | 4.082% |
| Approaches | Low/No Security | High Security | Databases |
|---|---|---|---|
| Li et al. [60] | (17.5/0.35) | (35.8/0) | FVC2002 DB1 |
| Liu et al. [76] | (14.33/0) | (20.40/0) | FVC2002 DB1 |
| Ferrara et al. [45] | (3.18/0) | (51.29/0) | FVC2002 DB1 |
| Yang et al. [77] | - | (3.38/3.38) | FVC2002 DB1 |
| Sandhya and Prasad [49] | - | 2.19/2.19 | FVC2002 DB1 |
| Wang et al. [39] | - | (1.0/1.0) | FVC2002 DB1 |
| Liu and Zhao [65] | - | (8.6/0) | FVC2002 DB1 |
| Arjona et al. [47] | - | (15.14/0) | FVC2002 DB3 |
| Yang et al. [48] | (4/4) | (4.57/4.57) | FVC2002 DB3 |
| Alam et al. [67] | - | (5.95/5.95) | FVC2002 DB1 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yang, W.; Wang, S.; Hu, J.; Zheng, G.; Valli, C. Security and Accuracy of Fingerprint-Based Biometrics: A Review. Symmetry 2019, 11, 141. https://doi.org/10.3390/sym11020141
Yang W, Wang S, Hu J, Zheng G, Valli C. Security and Accuracy of Fingerprint-Based Biometrics: A Review. Symmetry. 2019; 11(2):141. https://doi.org/10.3390/sym11020141
Chicago/Turabian StyleYang, Wencheng, Song Wang, Jiankun Hu, Guanglou Zheng, and Craig Valli. 2019. "Security and Accuracy of Fingerprint-Based Biometrics: A Review" Symmetry 11, no. 2: 141. https://doi.org/10.3390/sym11020141
APA StyleYang, W., Wang, S., Hu, J., Zheng, G., & Valli, C. (2019). Security and Accuracy of Fingerprint-Based Biometrics: A Review. Symmetry, 11(2), 141. https://doi.org/10.3390/sym11020141






