Adaptive and Blind Audio Watermarking Algorithm Based on Chaotic Encryption in Hybrid Domain
Abstract
:1. Introduction
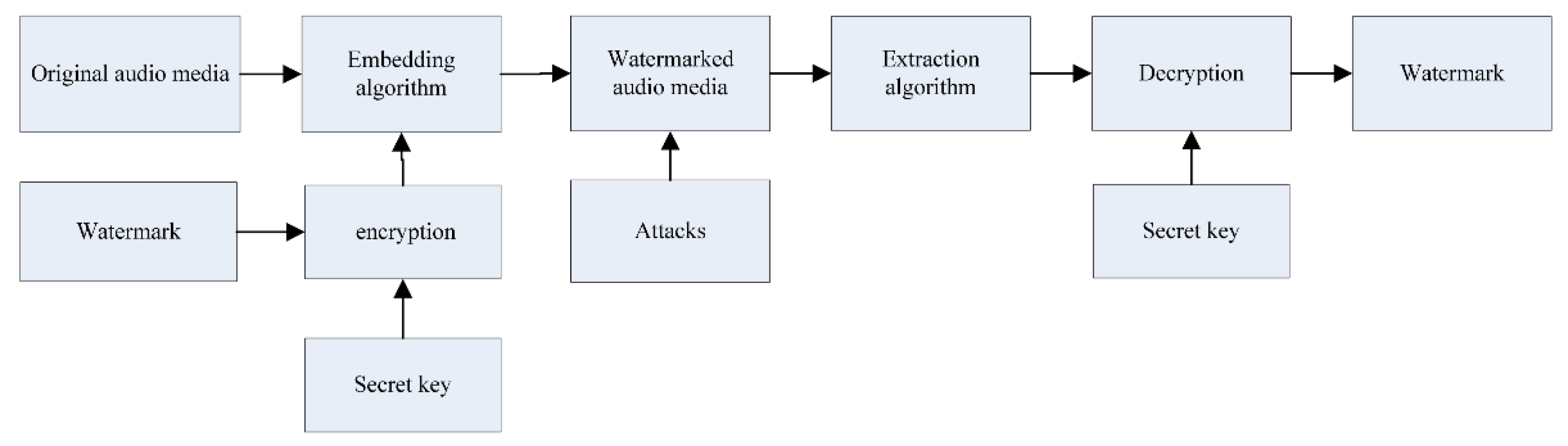
2. Watermarking Algorithm in Hybrid Domain
2.1. The Pretreatment to the Watermark Picture
2.2. Principle of Watermark Embedding
2.3. Principle of Watermark Extracting
2.4. The Design of the Adaptive Embedding Depth
3. Detailed Implementation Steps
3.1. Implementation Steps for Embedding Watermark
- Step 1:
- Convert the watermark picture into binary stream with the length of , and then generate the binary chaotic sequence according to Formulas (3) and (4), a bipolar string is generated according to Formulas (5)–(7) ultimately.
- Step 2:
- Add a group of “1111 1111” at the beginning of the bipolar string as the start sign and add a group of “-1-1-1-1-1-1-1-1” at the end of the bipolar string as the end sign.
- Step 3:
- Divide into audio segments with sample points. .
- Step 4:
- Perform the -level DWT on to get .
- Step 5:
- Separate into and , and then implemented DCT on them to obtain and .
- Step 6:
- Calculate , and according to Formulas (11)–(13).
- Step 7:
- Repeat Step 4 to Step 6. Calculate the average amplitudes of all audio segments to obtain and .
- Step 8:
- Calculate the adaptive embedding depth of each audio segment according to Formula (31). Embed a 1 bit watermark into each audio segment according to the embedding rules in Formulas (14) and (15).
- Step 9:
- Perform IDCT on and respectively to get .
- Step 10:
- Perform IDWT on to reconstruct .
- Step 11:
- Repeat Step 8 to Step 10 until the end of the embedding process.
- Step 12:
- Recombine to obtain the whole watermarked audio .
3.2. Implementation Steps for Extracting Watermark
- Step 1:
- Filter to reduce the out-of-band noise by low-pass filter.
- Step 2:
- Divide into audio segments , and .
- Step 3:
- Perform -level DWT on to get .
- Step 4:
- Separate into and , and then implement DCT on them to obtain and .
- Step 5:
- Calculate and .
- Step 6:
- If , the extracted binary is ‘1’, otherwise, it is ‘0’.
- Step 7:
- Repeat Step 3 to Step 6 until the end of the extracting process.
- Step 8:
- When a group of “11111111” start sign appears in the extracted binary information, the watermark begins to be extracted. When a group of “0000 0000” end sign is present, the extraction is finished.
- Step 9:
- Generate the binary chaotic sequence according to Formulas (3) and (4), and then obtain the extracted picture according to Formula (24).
4. Experimental Results and Analysis
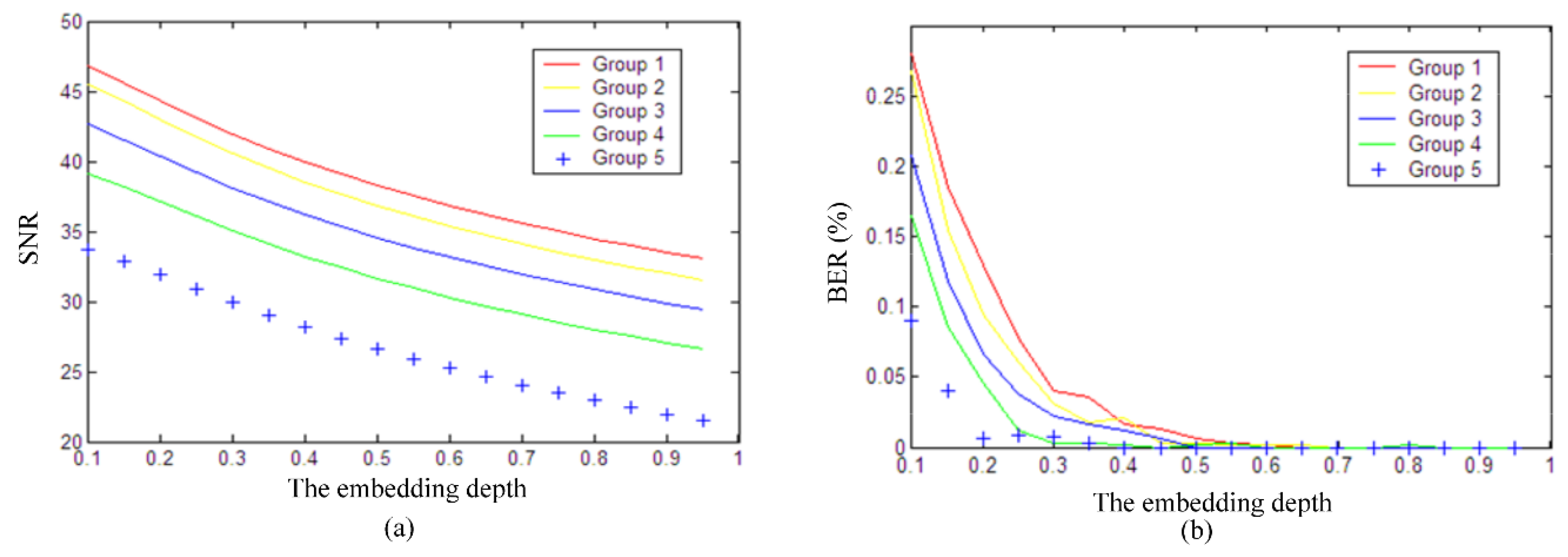
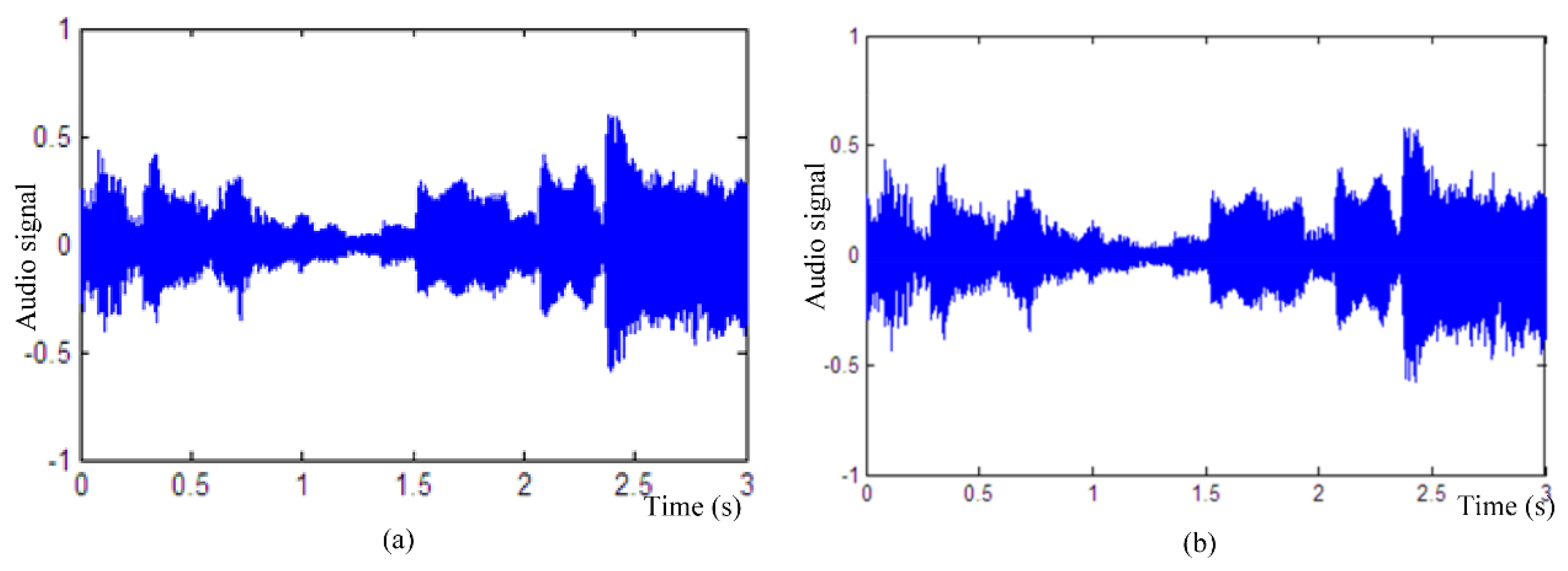
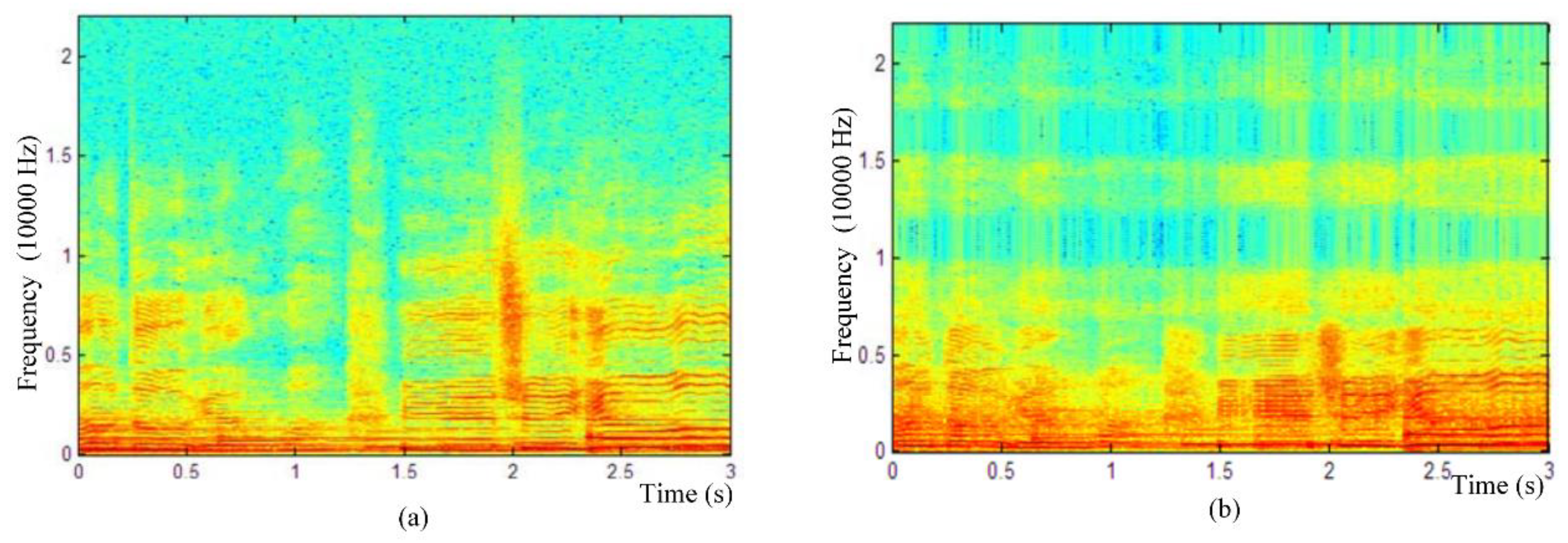
4.1. Capacity and Imperceptibility
4.2. Robustness
- (1)
- Gaussian noise: add 20 dB Gaussian noise.
- (2)
- Gaussian noise: add 30 dB Gaussian noise.
- (3)
- Gaussian noise: add 35 dB Gaussian noise.
- (4)
- Amplitude scaling: reduce the amplitude of the watermark audio signal to 0.8.
- (5)
- Amplitude scaling: amplify the amplitude of the watermark audio signal to 1.2.
- (6)
- Low-pass filtering: apply low-pass filter with 4 kHz.
- (7)
- MP3 compression: apply MP3 compression with 64 kbps.
- (8)
- MP3 compression: apply MP3 compression with 128 kbps.
- (9)
- echo interference: add an echo with 50 ms delay and 5% decay.
- (10)
- Resampling: change the sampling rates by 44100-22050-44100 Hz.
- (11)
- Requantization: change the quantization bits by 16-8-16 bits per sample.
- (1)
- This adaptive algorithm has an excellent robustness against Gaussian noise, resampling, requantization, echo interference, MP3 compression and amplitude scaling, so it is far superior to the algorithms proposed in [1,4,10,18]. This can be seen by comparing the results in column 2 and column 4 that the robustness of this adaptive algorithm is much better than that in [4], mainly because the embedding depth of each audio segment is adaptively controlled by the overall average amplitude.
- (2)
- The BER of this algorithm in resisting the low-pass filter is only 0.01%, which is higher than 0.39% in [1], 21.975% in [10], 28.250% in [18], and 0.12% in [25]. The average BER in case of Gaussian noise with 20dB is 1.92%, which is inferior to the algorithm in [25], so some watermark bits may be lost when resisting strong noise attacks. The 4th level wavelet coefficients will be affected by strong noise so as to reduce the robustness because this algorithm conceals the watermarks by modifying the 4th-level coefficients. As the noise becomes smaller, BER are significantly declined in 30 dB and 35 dB.
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Kaur, A.; Dutta, M.K. An optimized high payload audio watermarking algorithm based on LU-factorization. Multimedia Syst. 2018, 24, 341–353. [Google Scholar] [CrossRef]
- Hemis, M.; Boudraa, B.; Megias, D.; Merazi-Meksen, T. Adjustable audio watermarking algorithm based on DWPT and psychoacoustic modeling. Multimedia Tools Appl. 2018, 77, 11693–11725. [Google Scholar] [CrossRef]
- Liu, Z.; Huang, J.; Sun, X.; Qi, C. A security watermark scheme used for digital speech forensics. Multimedia Tools Appl. 2017, 76, 9297–9317. [Google Scholar] [CrossRef]
- Wu, Q.L.; Wu, M. A Novel Robust Audio Watermarking Algorithm by Modifying the Average Amplitude in Transform Domain. Appl. Sci. 2018, 8, 723. [Google Scholar] [CrossRef]
- Liu, S.; Pan, Z.; Song, H. Digital image watermarking method based on DCT and fractal encoding. IET Image Process. 2017, 11, 815–821. [Google Scholar] [CrossRef]
- Han, S.C.; Yang, J.F.; Wang, R.; Jia, G.M. A robust color picture watermarking algorithm against rotation attacks. Optoelectron. Lett. 2018, 14, 61–66. [Google Scholar] [CrossRef]
- Wang, C.Y.; Zhang, Y.P.; Zhou, X. Robust image watermarking algorithm based on ASIFT against geometric attacks. Appl. Sci. 2018, 8, 410. [Google Scholar] [CrossRef]
- Kazemivash, B.; Moghaddam, M.E. A robust digital image watermarking technique using lifting wavelet transform and firefly algorithm. Multimedia Tools Appl. 2017, 76, 20499–20524. [Google Scholar] [CrossRef]
- Khelifi, F.; Brahimi, T.; Han, J.G.; Li, X.L. Secure and privacy-preserving data sharing in the cloud based on lossless image coding. Signal Process. 2018, 148, 91–101. [Google Scholar] [CrossRef]
- Lei, W.N.; Chang, L.C. Robust and high-quality time-domain audio watermarking based on low-frequency amplitude modification. IEEE Trans. Multimedia 2006, 8, 46–59. [Google Scholar]
- Shahriar, M.R.; Cho, S.; Cho, S.; Chong, U. A high-capacity audio watermarking scheme in the time domain based on multiple embedding. IETE Tech. Rev. 2013, 30, 286–294. [Google Scholar] [CrossRef]
- Yang, X.M.; Li, B. A new digital audio watermarking algorithm of non-uniform Discrete Fourier Transform domain based on data mining principals. Agro Food Ind. 2017, 28, 3074–3079. [Google Scholar]
- Natgunanathan, I.; Xiang, Y.; Rong, Y.; Peng, D. Robust patchwork-based watermarking method for stereo audio signals. Multimedia Tools Appl. 2014, 72, 1387–1410. [Google Scholar] [CrossRef]
- Pal, D.; Ghoshal, N. Secured and imperceptible data transmission through digital audio signal with reduced internal noise. Wirel. Pers. Commun. 2017, 3, 1–14. [Google Scholar] [CrossRef]
- Hu, H.T.; Hsu, L.Y. Robust transparent and high capacity audio watermarking in DCT domain. Signal Process. 2015, 109, 226–235. [Google Scholar] [CrossRef]
- Natgunanathan, I.; Xiang, Y.; Hua, G.; Beliakov, G.; Yearwood, J. Patchwork-Based multi-layer audio watermarking. IEEE Trans. Audio Speech Lang. Process. 2017, 25, 2176–2187. [Google Scholar] [CrossRef]
- Qian, Q.; Wang, H.X.; Sun, X.M.; Cui, Y.H.; Wang, H.; Shi, C.H. Speech authentication and content recovery scheme for security communication and storage. Telecommun. Syst. 2018, 67, 635–649. [Google Scholar] [CrossRef]
- Chen, S.T.; Huang, H.N.; Chen, C.J.; Tseng, K.K.; Tu, S.Y. Adaptive audio watermarking via the optimization point of view on the wavelet-based entropy. Digit. Signal Process. 2013, 23, 971–980. [Google Scholar] [CrossRef]
- Wu, Q.L.; Wu, M. Novel Audio information hiding algorithm based on Wavelet Transform. J. Electron. Inf. Technol. 2016, 38, 834–840. [Google Scholar]
- Hu, H.T.; Chang, J.R.; Lin, S.J. Synchronous blind audio watermarking via shape configuration of sorted LWT coefficient magnitudes. Signal Process. 2018, 147, 190–202. [Google Scholar] [CrossRef]
- Li, J.F.; Wang, H.X.; Wu, T.; Sun, X.M.; Qian, Q. Norm ratio-based audio watermarking scheme in DWT domain. Multimedia Tools Appl. 2018, 77, 14481–14497. [Google Scholar] [CrossRef]
- Dhar, P.K.; Shimamure, T. Blind audio watermarking in transform domain based on singular value decomposition and exponential-log operations. Radioengineering 2017, 26, 552–561. [Google Scholar] [CrossRef]
- Hwang, M.J.; Lee, J.; Lee, M.; Kang, H.G. SVD-Based Adaptive QIM Watermarking on Stereo Audio Signals. IEEE Trans. Multimedia 2018, 20, 45–54. [Google Scholar] [CrossRef]
- Liu, Z.H.; Luo, D.; Huang, J.W.; Wang, J.; Qi, C.D. Tamper recovery algorithm for digital speech signal based on DWT and DCT. Multimedia Tools Appl. 2017, 76, 12481–12504. [Google Scholar] [CrossRef]
- Hu, H.T.; Chou, H.H.; Yu, C.; Hsu, L.Y. Incorporation of perceptually adaptive QIM with singular value decomposition for blind audio watermarking. EURASIP J. Adv. Signal Process. 2014, 12, 1–12. [Google Scholar] [CrossRef]


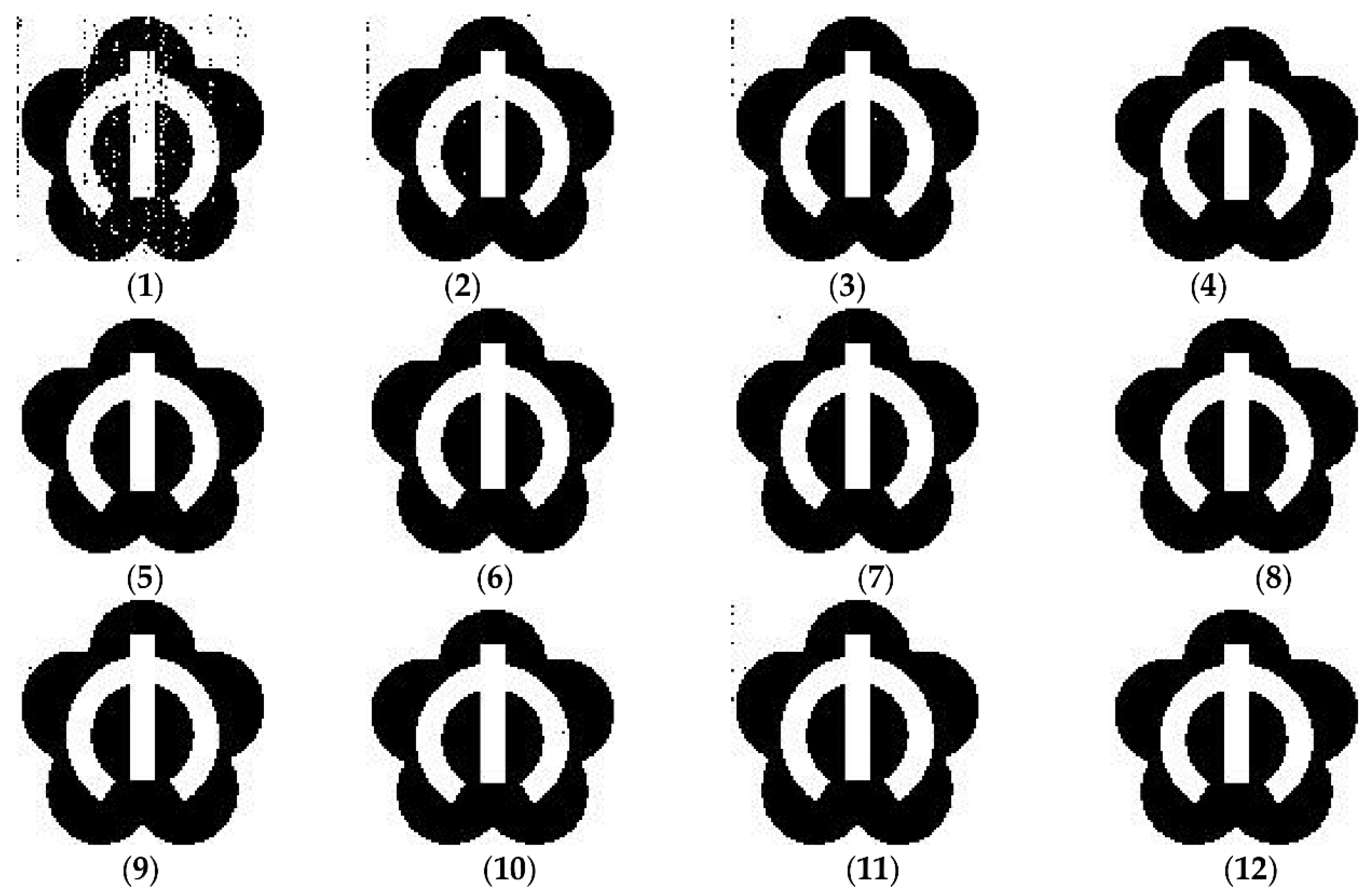
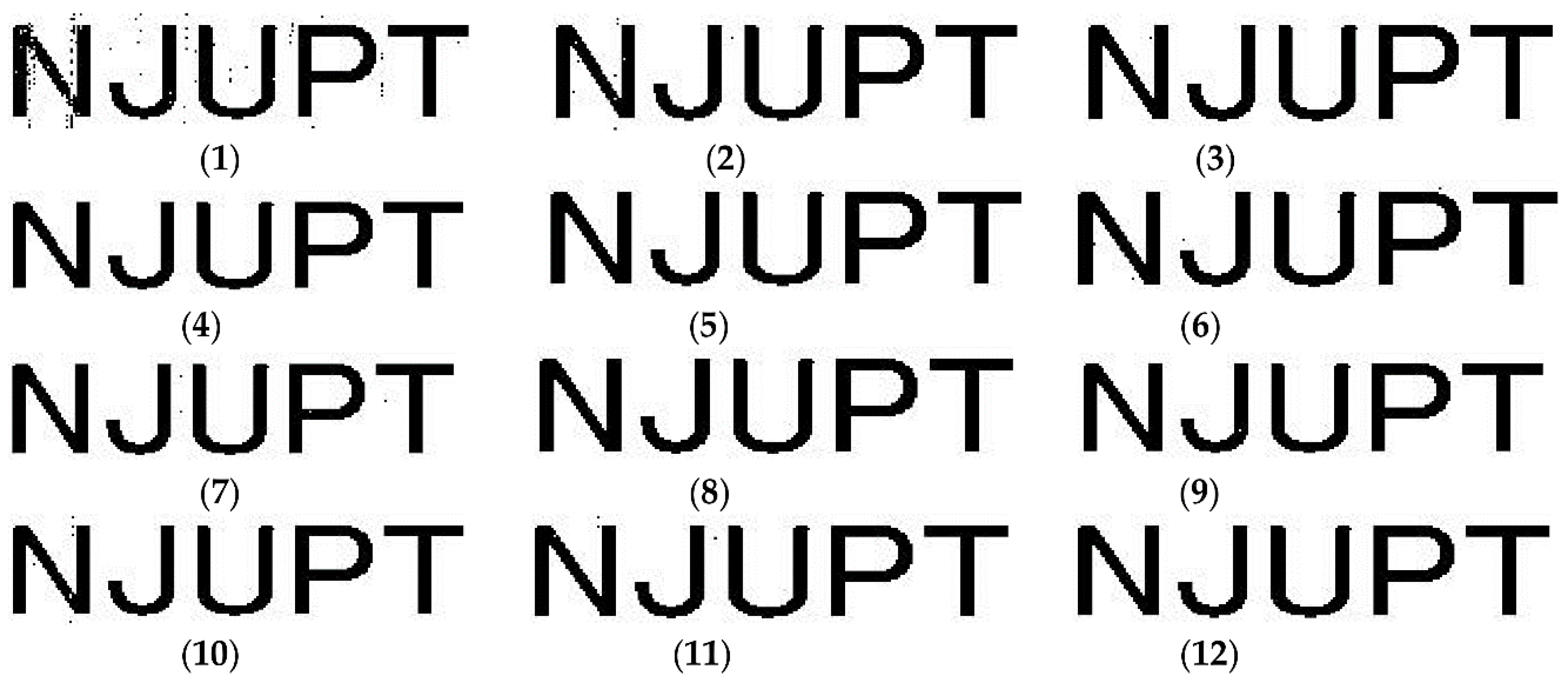

| Indexes | Proposed | [1] | [4] | [10] | [18] | [25] |
|---|---|---|---|---|---|---|
| SNR (dB) | 24.58 | N/A | 23.49 | 21.37 | 18.42 | 20.32 |
| Capacity(bps) | 172.27 | 125 | 172.27 | 43.07 | 172.27 | 139.97 |
| NC | 1 | / | 1 | / | / | / |
| BER (%) | 0.00 | 0.00 | 0.00 | / | / | 0.12 |
| Attack | The First Picture | The Second Picture | The Third Picture | Average Values |
|---|---|---|---|---|
| (1) | 0.9852 | 0.9881 | 0.9672 | 0.9802 |
| (2) | 0.9985 | 0.9989 | 0.9971 | 0.9981 |
| (3) | 0.9996 | 0.9998 | 0.9991 | 0.9995 |
| (4) | 1 | 1 | 1 | 1 |
| (5) | 1 | 1 | 1 | 1 |
| (6) | 1 | 1 | 1 | 1 |
| (7) | 0.9998 | 0.9997 | 0.9996 | 0.9997 |
| (8) | 1 | 1 | 1 | 1 |
| (9) | 1 | 1 | 1 | 1 |
| (10) | 1 | 1 | 1 | 1 |
| (11) | 0.9986 | 0.9992 | 0.9993 | 0.9990 |
| Attack | Proposed | [1] | [4] | [10] | [18] | [25] |
|---|---|---|---|---|---|---|
| (1) | 1.92 | / | 2.27 | / | / | 1.29 |
| (2) | 0.18 | / | 0.22 | / | / | 0.31 |
| (3) | 0.06 | 0.78 | 0.07 | / | / | / |
| (4) | 0.01 | 2.87 | 0.01 | 0.50 | 0.30 | 0.12 |
| (5) | 0.01 | 17.92 | 0.01 | 0.47 | 0.35 | / |
| (6) | 0.01 | 0.39 | 0.01 | 21.97 | 28.25 | 0.12 |
| (7) | 0.06 | 1.95 | 0.08 | 6.85 | 0.12 | 0.00 |
| (8) | 0.01 | / | 0.01 | 4.97 | 1.61 | 0.00 |
| (9) | 0.01 | / | 0.01 | / | 0.84 | / |
| (10) | 0.01 | 0.00 | 0.01 | 6.45 | 0.12 | 0.00 |
| (11) | 0.12 | 0.78 | 0.14 | / | 0.12 | 0.00 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, Q.; Wu, M. Adaptive and Blind Audio Watermarking Algorithm Based on Chaotic Encryption in Hybrid Domain. Symmetry 2018, 10, 284. https://doi.org/10.3390/sym10070284
Wu Q, Wu M. Adaptive and Blind Audio Watermarking Algorithm Based on Chaotic Encryption in Hybrid Domain. Symmetry. 2018; 10(7):284. https://doi.org/10.3390/sym10070284
Chicago/Turabian StyleWu, Qiuling, and Meng Wu. 2018. "Adaptive and Blind Audio Watermarking Algorithm Based on Chaotic Encryption in Hybrid Domain" Symmetry 10, no. 7: 284. https://doi.org/10.3390/sym10070284
APA StyleWu, Q., & Wu, M. (2018). Adaptive and Blind Audio Watermarking Algorithm Based on Chaotic Encryption in Hybrid Domain. Symmetry, 10(7), 284. https://doi.org/10.3390/sym10070284




