New Constructions of Quantum Stabilizer Codes Based on Difference Sets
Abstract
1. Introduction
2. Quantum Stabilizer Code
2.1. Quantum Information Theory
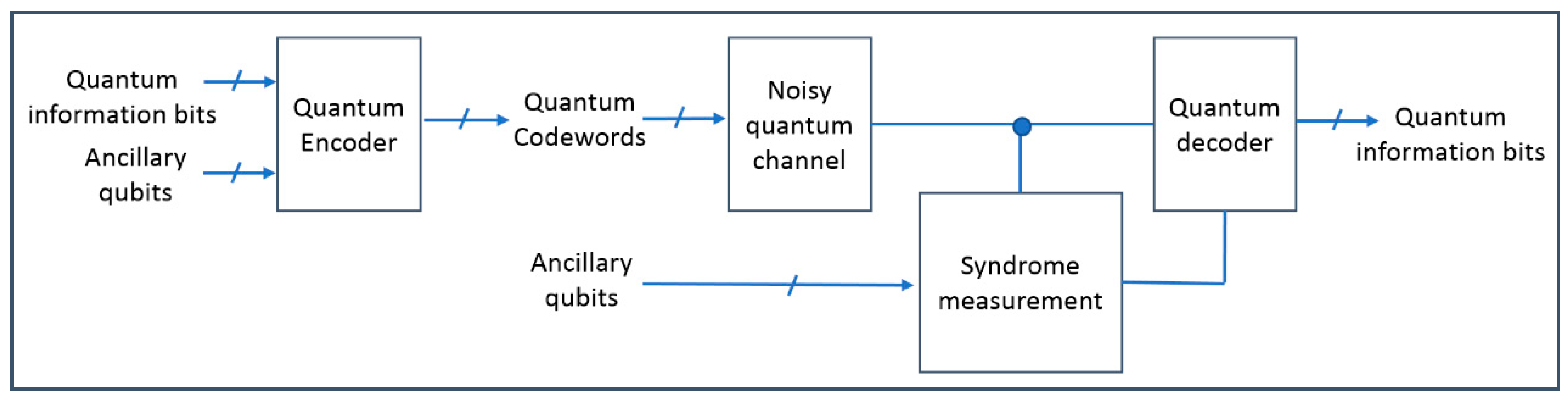
2.2. Quantum Error Correction Code
2.3. Binary Formalism of Quantum Stabilizer Codes
3. Circulant Matrices Based on DS and QECC Construction
3.1. Difference Sets and Shifted Difference Sets
3.2. Circulant Permutation Matrices
3.3. Construction of Quantum Stabilizer Code Based on DS
4. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Goyal, P.; Knuth, K.H. Quantum Theory and Probability Theory: Their Relationship and Origin in Symmetry. Symmetry 2011, 3, 171–206. [Google Scholar] [CrossRef]
- Shor, P.W. Algorithms for quantum computation discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar]
- Nguyen, D.M.; Kim, S. Quantum Key Distribution Protocol Based on Modified Generalization of Deutsch-Jozsa Algorithm in d-level Quantum System. Int. J. Theor. Phys. 2018. [Google Scholar] [CrossRef]
- Shor, P.W. Scheme for reducing decoherence in quantum memory. Phys. Rev. A 1995, 52, 2493–2496. [Google Scholar] [CrossRef]
- Steane, A.M. Error correcting codes in quantum theory. Phys. Rev. Lett. 1996, 77, 793–797. [Google Scholar] [CrossRef] [PubMed]
- Calderbank, A.R.; Shor, P.W. Good quantum error-correcting codes exist. Phys. Rev. A 1996, 54, 1098–1105. [Google Scholar] [CrossRef] [PubMed]
- Gottesman, D. Stabilizer Codes and Quantum Error Correction. Ph.D. Thesis, California Institute of Technology, Pasadena, CA, USA, 1997. [Google Scholar]
- Nguyen, D.M.; Kim, S. Minimal-Entanglement Entanglement-Assisted Quantum Error Correction Codes from Modified Circulant Matrices. Symmetry 2017, 9, 122. [Google Scholar] [CrossRef]
- Nguyen, D.M.; Kim, S. Construction and complement circuit of a quantum stabilizer code with length 7. In Proceedings of the Eighth International Conference on Ubiquitous and Future Networks, Vienna, Austria, 5–8 July 2016. [Google Scholar] [CrossRef]
- Gallager, R.G. Low density parity check codes. IRE Trans. Inf. Theory 1962, 8, 21–28. [Google Scholar] [CrossRef]
- Chung, S.Y.; Forney, G.D.; Richardson, T.J.; Urbanke, R. On the design of low-density parity check codes within 0.045 db of the shannon limit. IEEE Comm. Lett. 2001, 45, 58–60. [Google Scholar] [CrossRef]
- Kim, S.; No, J.S.; Chung, H.; Shin, D.J. Quasi-cyclic low-density parity-check codes with girth larger than 12. IEEE Trans. Inf. Theory 2007, 53, 2885–2891. [Google Scholar]
- Kim, S. Adaptive FEC codes suitable for variable dimming values in visible light communication. IEEE Photonics Technol. Lett. 2015, 27, 967–969. [Google Scholar]
- Postol, M.S. A proposed quantum low density parity check code. arXiv, 2001; arXiv:quant-ph/010813. [Google Scholar]
- Hagiwara, M.; Imai, H. Quantum quasi-cyclic LDPC codes. In Proceedings of the IEEE International Symposium on Information Theory (ISIT), Nice, France, 24–29 June 2007. [Google Scholar]
- Hwang, Y.; Chung, Y.; Jeon, M. A class of quantum low-density parity check codes by combining seed graphs. Quantum Inf. Process. 2013, 12, 2219–2239. [Google Scholar] [CrossRef]
- Tan, P.; Li, J. Efficient quantum stabilizer codes: LDPC and LDPC convolutional constructions. IEEE Trans. Inf. Theory 2010, 56, 476–491. [Google Scholar] [CrossRef]
- Baumert, L.D. Cyclic Difference Sets; Springer: New York, NY, USA, 1971. [Google Scholar]
- Anderson, I. Combinatorial Designs: Construction Methods; Ellis Horwood Limited: New York, NY, USA, 1990. [Google Scholar]
- Beth, T.; Jungnickel, D.; Lenz, H. Design Theory; Cambridge University Press: New York, NY, USA, 1986. [Google Scholar]
- MacKay, D.; Mitchison, G.; McFadden, P. Sparse-graph codes for quantum error correction. IEEE Trans. Inf. Theory 2004, 50, 2315–2330. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, Y.; Zhao, S.; Zheng, B. A construction of entanglement-assisted quantum LDPC codes from the cyclic difference set. In Proceedings of the IEEE 11th International Conference on Signal Processing (ICSP), Beijing, China, 21–25 October 2012. [Google Scholar]
- Xie, Y.; Yuan, J.; Malaney, R. Quantum stabilizer codes from difference sets. In Proceedings of the IEEE International Symposium on Information Theory (ISIT), Istanbul, Turkey, 7–12 July 2013. [Google Scholar]
- Vos, A.D.; Baerdemacker, S.D. Symmetry Groups for the Decomposition of Reversible Computers, Quantum Computers, and Computers in between. Symmetry 2011, 3, 305–324. [Google Scholar] [CrossRef]
- Nguyen, D.M.; Kim, S. Quantum Stabilizer Codes Construction from Hermitian Self-Orthogonal Codes over GF (4). J. Commun. Netw. 2018, 20, 209–315. [Google Scholar] [CrossRef]
- Xie, Y.; Yuan, J.; Sun, T.Q. On design of quantum stabilizer codes from quadratic residues sets. IEEE Trans. Inf. Theory 2014, 66, 3721–3735. [Google Scholar]
- Grassl, M. Bounds on the Minimum Distance of Linear Codes and Quantum Codes. Available online: http://codetables.de/ (accessed on 7 November 2018).
| Generators | Operators |
|---|---|
| g1 | XZZXI |
| g2 | IXZZX |
| g3 | XIXZZ |
| g4 | ZXIXZ |
| No | Difference Set | |
|---|---|---|
| 1 | 7, 3, 1 | 1 2 4. |
| 2 | 7, 4, 2 | 0 3 5 6. |
| 3 | 15, 7, 3 | 0 1 2 4 5 8 10. |
| 4 | 21, 5, 1 | 3 6 7 12 14. |
| 5 | 23, 11, 5 | 1 2 3 4 6 8 9 12 13 16 18. |
| 6 | 31, 15, 7 | 1 2 3 4 6 8 12 15 16 17 23 24 27 29 30. |
| 7 | 47, 23, 11 | 1 2 3 4 6 7 8 9 12 14 16 17 18 21 24 25 27. 28 32 34 36 37 42. |
| 8 | 199, 99, 49 | 1 2 4 5 7 8 9 10 13 14 16 18 20 23 25 26 28 29 31 32 33 35 36 40 43 45 46 47 49 50 51 52 53 56 57 58 61 62 63 64 65 66 70 72 79 80 81 86 89 90 91 92 94 98 100 102 103 104 106 111 112 114 115 116 117 121 122 123 124 125 126 128 130 131 132 139 140 144 145 151 155 157 158 160 161 162 165 169 172 175 177 178 180 182 184 187 188 193 196. |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nguyen, D.M.; Kim, S. New Constructions of Quantum Stabilizer Codes Based on Difference Sets. Symmetry 2018, 10, 655. https://doi.org/10.3390/sym10110655
Nguyen DM, Kim S. New Constructions of Quantum Stabilizer Codes Based on Difference Sets. Symmetry. 2018; 10(11):655. https://doi.org/10.3390/sym10110655
Chicago/Turabian StyleNguyen, Duc Manh, and Sunghwan Kim. 2018. "New Constructions of Quantum Stabilizer Codes Based on Difference Sets" Symmetry 10, no. 11: 655. https://doi.org/10.3390/sym10110655
APA StyleNguyen, D. M., & Kim, S. (2018). New Constructions of Quantum Stabilizer Codes Based on Difference Sets. Symmetry, 10(11), 655. https://doi.org/10.3390/sym10110655





