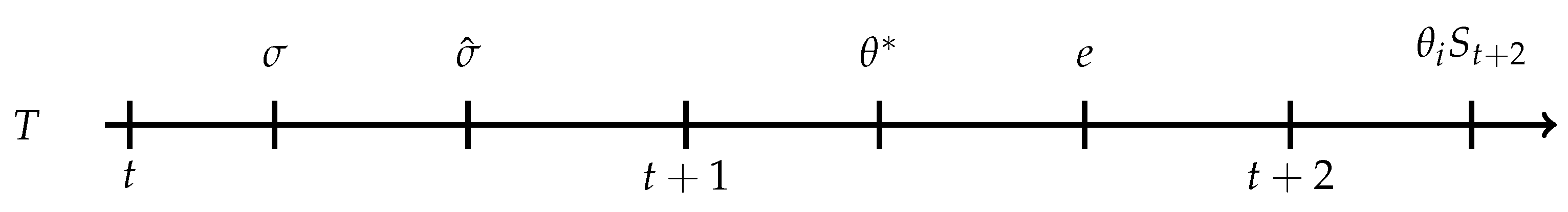1. Introduction
The standard assumption in economics is that decision makers (DMs) are endowed with perfect reflection. They are likely to embark on a process of conscious mental revision of their available alternatives in order to characterize each choice and evaluate their consequences. To sustain the perfect reflection assumption, the theory of decision making first postulates that individual preferences are exogenous, and secondly, that information is always (weakly) valuable even when it is bad news. Yet, the robustness of the assumption of perfect reflection depends on both the complexity of the decision problem and on the individual’s subjective beliefs about the value of information. Complex decision problems are those in which payoff-relevant variables are defined endogenously and are entangled as part of the choice. By the same account, standard economics assumes that the value of information is instrumental to make better decisions. However, a growing body of theoretical and experimental literature suggests that information also has an affective value that may directly enter the agent’s utility function—a phenomenon known as “belief-based utility”. This can create an incentive to avoid information, even when it is useful, free, and independent of strategic considerations. In such cases, the assumption of perfect reflection becomes difficult to justify. The difficulty stems from the relaxation of one or more conditions of exogeneity, rationality, and self-knowledge.
To cast light on the process of relaxing the assumption of perfect reflection, let us start with a simple scenario and complicate it little by little. In many situations, real life is complex because choices are accompanied by aspirations, motivations, emotions, dispositions, and beliefs that alter the characteristics of the alternatives as well as the nature of the decision problem. Imagine choosing between investing in education to get career A or B. In a simple framework, the DM chooses A over B only if the pleasure or the profit received from A is greater than that received from B. It follows that she will choose to invest in A when both the possibilities are available. In this scenario, she has a precise definition of the objects of her choice: career A over B. Suppose, now, that the availabilities of the alternatives are uncertain, as the outcomes (and the preferences over them) are endogenous—that is, explained through mental states such as motivations and beliefs. Specifically, we assume that the individual has incomplete information about the outcomes of the alternatives and decides to undertake a conscious mental revision about which is the best, also inferring which one is the most socially acceptable. The object of her choice is therefore changed. It is no longer presented to her eyes on the basis of only the intrinsic value of the alternatives, but also on the value that society attributes to the alternatives. The nature of the decision problem is now changed since the DM’s motivational structure is changed because it is informed by the heuristic “the most socially acceptable”. Heuristics represent a shortcut that the DM chooses in order to solve the uncertainty.
For the DM, her decision problem is no longer between the outcomes of each career path, but between career paths together with their degree of social acceptance. Specifically, the career path finds its value in the social recognition as an ideal career for a specific type of DM that belongs to a given community. The “socially acceptable” mental states (i.e., beliefs and motivations) are originated by the presence of norms, which ultimately define the mental representation that the DM has of herself and her identity. Consequently, the DM has to internalize the consequences of both actions and motivations. A DM with imperfect reflection will not anticipate that her conformist motivation might play a role, whereas a perfectly reflective DM will know how to handle the endogeneity. Hence, given the objections to the assumption of bounded rationality, it seems reasonable to ask ourselves the question: where do a DM’s mental states come from? Consider again the “heuristics” example. It has two features that are worthy of further analysis: the mental states and the sampling of the information.
According to Elster [
1,
2], mental states, as beliefs and motivations, define behavior. Beliefs and motivations
1 help the DM to navigate in life, to justify the undertaken action and to experience emotions. If we want to order the states in a causal relation, motivations are causal determinants of the states and, then, of the belief formation. A complete analysis of the mental states should look at both costs and constraints of the motivated mental states. The costs of mental states are the false or inaccurate beliefs that even though they are pleasant they can induce suboptimal choices or emotional drawback. In turn, constraints
2 are the information processing that can be biased and affected by overconfidence or optimism, or can be constrained by priors or social norms. While the earlier attempts of bounded rationality theory were based on the costs [
4,
5], recent theory has focused on the investigation of the constraints. When motivated mental states enter the framework, the traditional exogeneity assumption no longer holds, nor the other assumptions of accurate knowledge of the preferences and of fixed inter-temporal preferences. The “heuristic” example supports an analysis of both costs and constraints. The choice of career A over B could be explained by a motivated mental state that favors a conformist behavior. This motivated belief drives the DM to strategically sample only the information that is considered important for the conformist extent and to disregard the information that does not match it. That is, the DM organizes the information structure to favor the priors that career A is better. Hence the norms, while establishing the socially acceptable attributes of an individual identity, also drive individuals’ preferences for information acquisition or avoidance.
On the last account, the example can be taken to a higher level of sophistication that specifies a further particular mechanism. The social norms that suggest the DM’s choice of A over B, reinforce their grip on the DM by arousing feeling linked to the anticipation of the future identity, which could mean either savoring future success or dreading future failures. In this way, “being a professional A”
3 will not only be good because it is socially accepted, but because A is highly considered, the anticipation of the future identity A has an impact on immediate well-being [
6]. This particular way of framing the effect of beliefs about future events and identity over current feelings is called anticipatory utility [
6,
7] (henceforth AU). In the framework of AU, beliefs enter the utility function directly via emotional predisposition, highlighting the importance of information gathering and avoidance. This result is more interesting in light of Simon’s perspective
4 on the role of information. In fact, in the general case of self-conflicting goals, or intra-personal conflict motives, as in Brocas and Carillo [
9] or Bénabou and Tirole [
10,
11], an individual may choose to avoid information even when it is freely available. Moreover, even if being informed will improve the DM’s current decision, the information could be completely or partially shared with her future incarnations, affecting her future optimal choice and thus creating an intra-personal conflict. Ignorance would be a rational and strategic behavior.
With the elements of sampling information and AU, this paper models how social norms and identity are linked from an intertemporal perspective that is different from Akerlof and Kranton’s [
12,
13]. The work presents a dual-self model [
14] within a monotonic decision problem [
15]. The main structure posits the decision problem as a game between a short- and a long-run self. The two selves may incur inconsistent decisions in time. Because of this, they might want to manipulate the information structure they possess.
This work is closely related to and borrows from Kószegi [
16] and Bénabou and Tirole [
10,
11]. As in the model, in Kószegi ignorance is costly in terms of inefficient actions and the DM is information-averse. Bénabou and Tirole face the two topics in different papers. In Bénabou and Tirole [
10], imperfect recall is the tool through which the DM can keep a high self-esteem, however the scenario with a second stage of the action strategy is not considered and the cases of analysis consider only the situation in which a low signal is subjected to a recall strategy. In [
11], the authors show that a DM with an anticipatory utility function and with preferences for the future outcome can be led to make inefficient decisions. The current paper merges the three works, obtaining the result that ignorance is costly in terms of inefficient actions whenever the DM is information-averse. However, the inefficiencies can be offset by the gains in the DM’s self-image (or self-esteem). The aversion for the information is analyzed in both cases of receiving good or bad signals, because both matter for the consequence of inefficient actions and self-esteem maintenance. Their existence is determined by the presence of social norms that inform the DM not only in terms of the socially accepted identity but also in how to respond to information conflicting with it. The existing literature on ignorance as a strategic action to maintain self-serving biases focuses mostly on the asymmetric recall of good signal [
10,
11,
16,
17,
18,
19,
20,
21]. Recalling a good signal is always appealing when the outcome of that signal dominates any other outcomes. For example, signaling a high IQ or scoring a high point in a student laboratory experiment is always better than signaling the opposite [
18], because the identity of “being a good student” is the dominant in such environment, hence any feedback contrasting that ideal identity would be forgotten. Another example could be the one of showing a high moral stand in a society in which morality is an important feature [
11]. A final example is served by [
11], in which recalling a good signal could be used as a strategy to maintain personal motivation for people who lack self-control in seeing their plans through. In these and other contexts, the asymmetric recall of good signal is justified by the fact that being good is the most socially acceptable identity. Yet, there are social situations in which identity and social norms identify being both good and bad as socially acceptable. Let us consider, for example, the case of the student groups “nerds”, “jocks”, “leading crowd”, and “burnouts” in Akerlof and Kranton’s [
13], and their effects on matching the image and the behavior of an ideal group member. In contrast to existing work, this study first emphasizes the important role of social norms as underlying reasons for motivated beliefs (i.e., the demand side of self-deception), and second the necessity to generalize the selective recall strategy (i.e., the supply side of self-deception). This model tries to generalize the asymmetric recall strategy by proposing a thicker strategic input to the second result of Kószegi [
16] in which he introduces the possibility of partial information acquisition. Even with the generalization of the recall strategy, the model shows the existence of the trade-off [
10,
22] between affective benefits from the biased self-image based on social conformity to a specific social norm on the one hand, and the incentive for accuracy of decision making on the other hand.
The rest of this paper is organized as follow. In
Section 2 a literature review accommodating all the above phenomena is presented. To follow,
Section 3 and
Section 4 introduce and solve the model, respectively.
Section 5 provides comments and discussions. Finally,
Section 6 offers conclusions. An Appendix section for complementary results and graphs follows.
3. The Model
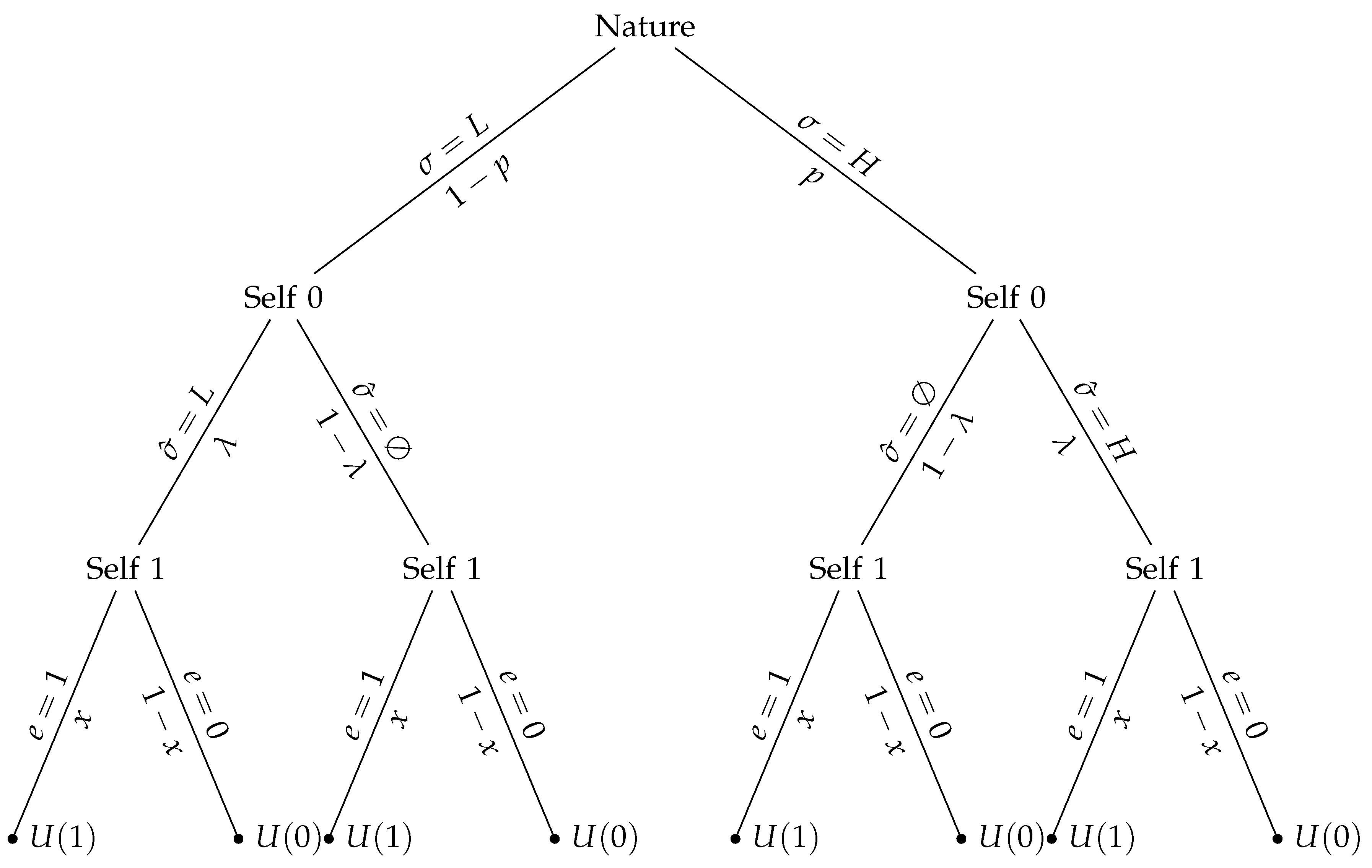
Consider a decision problem in which an intra-personal game is played by a sequence of temporal incarnations of the DM: a myopic short-run self and a long-run self. Both incarnations have preferences over their identity , where is a non-empty, compact subset of ℜ. The identity is validated according to the group’s expectations in terms of membership to one of the two social groups in which the society is divided in this current model. Each social group has its own distribution of type H or L. The DM’s utility is a function of economic outcomes and anticipatory emotions towards the outcomes, either positive or negative. The total utility is built over three periods of time, according to which at the beginning of period t the DM is endowed with an initial endowment, or amount of human capital, . At this stage the DM receives a signal, , that is informative about her identity traits, . The probability of observing an H signal is . The signal is informative in the sense that it can either broaden or restrict the set of opportunities available to the DM if it does not clash with the expectations of the group. The evaluation of available opportunities is grounded on the existence of two kinds of expectation that support the presence of social norms associated to the social group to which DM belongs or aspires to take part of.
Definition 1. Empirical expectations state what the DM “expects the other in her position will do” in a particular situation. Normative expectations define what “they think other people believe ought to be done”(Bicchieri [31]). The presence of the two kinds of expectation transform the DM’s decision into a monotone decision problem, whereby the posterior beliefs induced by the signal can be ordered so that specific actions are chosen in response to their corresponding signal realizations sustained by the norms. This is because:
Definition 2. A social norm is a code of conduct shared by society and enforced through internal sanctions like guilt, shame, and loss of self-esteem.
The presence of strong norms dictating a certain type of behavior is a possible source of cognitive dissonance for the individual whenever the realization of the signal does not accord with that norm. Accordingly, the DM who has internalized the norm needs to solve the dissonance caused by the signal,
. Since it is a nomothetic dissonance in our case, the best option is normally to avoid the source of the dissonance—that is, to choose the interpretation and recall strategy of the signal,
, with probability
. At
, the DM updates her beliefs about her identity,
, according to Bayes’ rule and chooses to invest in education,
, and experiences emotional utility from the outcome of the investment choice,
. In period
, the DM faces a choice regarding the investment that is individually deemed socially worthy: investing (or not) at time
has an impact on the identity that the DM wants to signal at
and produces at
an emotional reaction related to signaling the new identity at
. The action is the main variable that allows the DM to pursue her plan over the future identity. The plan will have as return both the material outcome and the self-esteem outcome. The latter comes from the DM’s perception of enacting her plan. The plan can go in two directions: maintaining the status quo of her neighborhood, with probability
; or changing the status and undertaking a new path with probability
. The individual has the theoretical possibility of choosing to not replicate the identity trait of her reference group and to go for her own identity according to her aspiration level and autonomy. The outcome of the action has material payoff only on the last period,
, and it is the final amount of human capital gained after the investment choice,
. The timing is pictured in
Figure A1, in
Appendix A.
An important assumption of the model is that it is a non-cooperative game between the long-run self and the short-run incarnation, namely, the individual cannot commit ex ante to her future decisions. Instead, the long-run self chooses a self-control action causing a current cost that influences the utility function of the myopic self, producing externalities on her future welfare. The magnitude of externality depends on the individual’s identity trait, whose value is subject to imperfect information.
Timet. The expected value of the identity is conditional on each possible realization of such signals, and it is given by:
with
and
.
Assupmtion 1. The DM has a prior distribution on Θ, and she observes a signal σ with likelihoods . If satisfies the Monotone Likelihood Ratio Property (MLRP), then the posterior belief follows the MLRP. Hence, the high signal first-order stochastically dominates (FOSD) the low signal:
Thus, the stochastic order of the information structure tells us that for any values of the identity parameter (
), higher values of the signal make the higher parameter value relatively more likely. In the absence of empirical expectations and social norms, better information allows for a more accurate match between beliefs and actions. If beliefs are formed through the group’s expectations, then their match with the actions could be driven by a further specification of the signal structure: there are going to be some signal realizations that are more preferred than others. For example, a group with a majority of
L type (namely, with a biased prior that shows that
L types are more frequent in that group) could tend to welcome more other
L types rather than
H types, and in terms of the stochastic orderings, the information structure considered more informative will be the one that on average will produce with higher probability an
L signal than any other informative structure. Then, in cases where the signal realization does not respect the ordering, the DM decides how to recall the signal.
Accordingly and following Bénabou and Tirole [
10,
21] and Rabin [
5], I admit that the individual can decide how to record the signal at time
t. Whether to interpret it realistically
or to rationalize it
with
. Rationalization means that the long-run self at time
t may either communicate the signal truthfully to the short-run self at stage
, or suppress it. The DM’s decision at time
t is to make a recall strategy that is the probability,
, of truthfully transmitting to self-
the signal,
:
The DM will observe the signal if the gain of making an informed decision will exceed the cost of memory manipulation. will be chosen according to how reliable or informative the signal is—namely, if it is pivotal in the decision.
The recall strategy has its own justification based on the DM’s preferences over . If the signal confirms her prior on her initial identity trait (), she will not discard the original signal (), and then she will make the investment choice correlated with her characteristics. The incentive is also justified by the fact that the DM will make another evaluation that will trigger her choice. She may envisage what the consequences of sending specific signals are, whether it comes from a recollection or an action, to her circle.
Examples. A girl in a social circle of non-educated women who decides to continue her education will signal a message diverging from the circle identity. The heir of a wealthy family that decides not to pursue the family profession may find some hurdle in gaining the acceptance of her peers. A woman facing a tradeoff between work and family, when all the people around her seem to have chosen one of the two spheres, will hinder her choice of labour supply.
Hence, at time
t the long-run self chooses the strategy to recall the signal. Endogenizing the imperfect recall allows the DM to reduce the externalities from one self to another. Following Festinger [
41], reducing dissonance is not costless, whether it is implemented via attitude change or via memory manipulation. It requires re-valuing past behavior or information and breaking cognitive habits. Because the DM has preferences over her identity, and because she may want to solve the cognitive dissonance, she has the incentive to manipulate her recollection (or ex-post denial
11) by exerting an effort. Let us consider the example of the little girl. Let us imagine that the girl has received a signal
H that goes against the empirical expectations displayed in her circle that want all the girls to be uneducated (i.e., all the girls signal to be
L). Now, she has to decide how to recall the signal, considering the trade-off between following the old path of no investment in education or to continue her education, signaling a message diverging from the circle identity. It seems necessary to stress the fact that recall strategies in an awareness-management context do not lead the individual to fool herself. Yet, she is aware that what she may have forgotten are not random events but rather the result of an incentivized inference. The memory effort is associated to a cost
12 function,
, that will impose further restriction to the choice and the agency of the individual
13.
Assupmtion 2. The cost is strictly increasing, convex, twice-continuously differentiable, and if , then and .
Timet+ 1. The short-run self updates her beliefs and chooses the action
e (i.e., investing in education) from a finite set
A, given the signal recalled. The DM is rational and then before updating she evaluates the precision of the signal received by her previous incarnation. She considers the possibility that the long-run self at time
t may have manipulated the true signal. Accordingly, she needs to estimate the probability that the signal is accurate. If
expresses the probability that Self-
t has truly transmitted the signal,
represents Self-
t + 1’s belief concerning Self-
t’s communication strategy. Yet, the accuracy of the signal is given by:
implying that if Self-
t + 1 receives
, by using Bayes’ rule, she will assign the probability
that
was observed and the probability
that
occurred. The incentive constraints for Self-
t + 1 do not change at this stage. However, the degree of self-assessment needs to take the accuracy of the recall into account. Hence, the DM’s revised beliefs are:
After the updating, the DM will choose the investment actions taking into account both the future material outcome (i.e., in the example of the girl, the future material outcome is an increase of her human capital level) and the anticipatory emotion of the outcome (i.e., feeling good/bad with that increase of human capital) realized that depends on the action taken (i.e., investing one more year in education).
The individual will implement the action strategy
, where
A is a non-empty, compact, and convex set in
ℜ. The investment in education will impact the DM’s human capital. Let us assume that each individual at time (
t) is endowed with an initial level of human capital,
.
is the initial endowment, and is interpreted in such way as to permit complementarities between the family’s human capital and the quality of community the family lives in. In this way, according to the initial level we give a representation of initial stratification that may determine the future one. In this scenario, the population is divided in two groups according to income and social status:
H-types belong to the portion of the population characterized by high income, good social connections, and communities; while
L-types represent the complement portion of the population. Human capital accumulates according to the following equation:
where
is the DM’s human capital at time
t,
is the educational investment faced at time
t, and
is the interest rate of that investment. The educational investment will determine the future group affiliation of the DM. The sense of affiliation is the motivation for the action. The DM’s probability to invest is of the form:
and it represents the conditional probability law of the action
e for each possible value of
. Since the decision of investment takes the persistence of identity into account, we need to express how the future identity enters the DM’s decision problem. The anticipatory emotion at time
t aroused by the thought of the future identity is derived rationally by calculating the posterior identity the DM gains by means of the investment choice. The posterior identity evaluated to the investment decision is
, where:
After the action, the DM experiences a shift in beliefs by assuming that she is sophisticated, in foreseeing this shift, by applying the Bayesian calculation:
and
where the prior beliefs at time
are represented by
, the probability of being
H-type given the recall. Moreover, recalling the probability of investing given the type,
, then
is defined as
and
Then, the posterior probabilities in the two scenarios will be:
and
Table A1 in
Appendix A shows the probabilities of the two signals and the posterior beliefs.
Preferences. The model extends for three periods, from t to .
In the last period, the DM will receive the outcomes of the action taken at time
.
The DM’s preferences at time
are represented by the anticipatory utility function: namely, at time
the DM gets an instantaneous utility of her current identity and a utility from the anticipation of time
identity outcomes. Consistent with Carrillo et al. [
3], the instantaneous utility is represented by the cost function related to the action that will produce externalities in the future stages. Hence, the instantaneous utilities at time
t and
are represented by the current effort the DM has to exercise in order to perform the action after,
. The DM has perfect foresight, namely, she is sophisticated in the sense that she applies Bayesian operators to foresee her dynamic inconsistency.
The utility at time
is represented by
, and its expression is the following:
The anticipation at time
of the utility at time
is expressed by
, the value function in which both the future outcome of the investment,
, and the aspiration level,
(i.e., the DM’s expected identity given the investment decision), are represented:
In the value function is a traditional time discount factor (), and s is the anticipatory factor. Hence, is represented by the schooling return times the identity trait. The trait identity is represented in such a way that it takes into account the anticipatory utility at time , and the discounted utility from identity at time , .
The psychological insight of
s is what Lowenstein [
6] calls
savoring of the agent’s belief about the contribution of
to her future welfare and identity.
s represents the feeling of pleasure, if
, or of fear, if
, derived by the anticipation of the contribution of the final identity. However, in this context, the feeling experienced is socially grounded in the sense that it depends upon the evaluation of the neighbors. In different but related words, this attitude can be explained by the individual’s compliance with the norm that her social background proposes to her. The agent indulges in pleasant beliefs (conversely, avoiding the disagreeable ones) about the signal she sends to her peers when considering whether to invest or not. This sentiment in the model is anticipated at time 0 and measured by
s. The anticipation of future blame or praise related to the decision taken represents a further constraint to consider during the decision making. In period
, the agent obtains the return
from investing in
. At time
, she derives feelings (pleasure or pain) from anticipating the prospect future identity,
.
Assupmtion 3. The value function is continuous and supermodular: it is strictly increasing and continuous in the aspiration level , and continuous for every , but it also has increasing differences for all pairs of aspiration level, and education choice ( satisfies Milgrom–Shannon’s single-crossing condition). Besides, the value function satisfies the following assumption: , if , and .
The requirements enlighten three aspects: the first is a condition of good expected behavior with respect to the decision of investment; the second requirement points out the beneficial effect of the investment on the utility. Finally, the third requirement shows that the action has informational content feeding conformist behavior to a norm. On this account a clarification is due. According to Caplin and Leahy [
7], anticipatory emotions affect the behavior when the total utility function is strictly concave. In this way, the DM is averse to variation to future anticipatory emotion. However, according to Bernheim and Thomadsen [
53], the assumption of non-linearity can be relaxed in the case of imperfect recall.
One important property of this set-up is that, as [
7] pointed out, anticipatory emotions can affect behavior when
is non-linear, determining the DM’s preference for information. Whenever the utility function is concave, the DM is information-averse to variation in future anticipatory emotion—she suffers from anxiety. Consequently, the individual prefers to take an ignorant action rather than receiving information prior to making the decision unless this allows her to select an action that sufficiently improves her outcome. This is true when the information is perfectly recalled. However, as [
53] showed, the non-linearity assumption can be relaxed when memory of the signal is imperfect and the anticipatory emotions still matter, because the imperfect recall breaks down the law of iterated expectations.
Moreover, considering the fact that aspiration level and education choice are complementary, and that
is a function of the unknown identity,
, and of the signal and its recall, if the value function respects specific conditions, according to [
15] we can investigate the comparative statics of the educational investment with respect to the original signal.
Assupmtion 4. If is single-crossing in e and θ holds, then is non-decreasing in if and if . Additionally, since by Assumption 1 we know that satisfies the monotone likelihood ratio property, then the expected value function is single crossing in e and σ and therefore the optimal choice, , is weakly increasing in σ.
Regarding the cost function at time , the DM needs to decide whether to invest in the old path at no cost or in the new path at a cost . Let us again consider the example of the girl. In the first case, the girl pursues the old track of being un-educated (i.e., , the one her peers and family expect from her), while in the second case she faces the cost of deviation from the marked path by investing (i.e., ) one more year in school. The cost function of the investment in education (i.e., ) is assumed to be smooth, increasing, convex, and known at time 0. The cost is given by , where .
I assume that investing in the new path supports both the participation constraint and the sorting condition, considering that .
Finally, the total utility at time
t takes into consideration the memory manipulation costs and the discounted values of the future utility. Here, the DM’s trade-off between accuracy of decision making and self-image takes place:
4. The DM’s Problem
The properties of the Perfect Bayesian Equilibria (PBE) can be studied in two parts by applying backward induction. First, we compute the optimal Investment of the short-run self at time taking the recall strategy as given. Second, we obtain the Memory Manipulation decision of the long-run self at time t, taking the optimal investment strategy into account. The existence of a PBE is established in the online appendix.
Choice of e. By the end of
, the DM updates her beliefs and chooses the action given the recall of the signal. She does this by maximizing anticipatory utility given the beliefs set she owns at that time. The optimal action is
Choice of. At the end of period
t, the DM chooses how to recall the signal received at the beginning of the stage. This occurs whenever the benefits of memory manipulation both in terms of self-esteem and efficient future actions overcome the cost of the manipulation.
Then, the decision made by the agent with endogenous imperfect recall is modeled as the PBE of the multi-self game. It is constituted of a strategy profile that comprises an interpretation strategy () and an action strategy (), and of a posterior belief.
Definition 3. A PBE of the game is the set of strategy profiles , where is given by the pair and , and the posterior beliefs such that
- 1.
;
- 2.
;
- 3.
is obtained by the Bayes’ rule if , .
Condition 1 states that Self-t chooses the amount of memory manipulation that maximizes the agent’s expected payoff conditional on each outcome . Condition 2 states that the short-run Self- takes an ex-post action e with positive probability if and only if this action maximizes her utility given the beliefs she holds about the manipulation employed by Self-t. She might consider the fact that she might have forgotten about previous status. At this point, the imperfect recall is not strategic. Hence, the short-run self does not have to take in consideration the possibility that her previous self might have suppressed the signal. Condition 3 is a consistency condition, requiring that the beliefs of Self- satisfy Bayes’ rule given the strategy of Self-t. This condition is stronger than Bayesian consistency because it requires beliefs to be consistent even for certain events that may not occur on the equilibrium path (namely, events associated with ex-ante actions that are not played in equilibrium). This condition ensures that the PBE satisfies subgame perfection, which would not be the case if one only restricted beliefs on the equilibrium path to be consistent with Bayes’ rule.
4.1. Self-t + 1 Investment Game
Given
, at
the individual will choose the action that maximizes her future plan
14. For the DM, the incentive criterion (IC) to invest at time
in the new path,
, requires that the gains of investment, measured in terms of utility differentials, are greater than the cost of facing the investment
The criterion to invest at time
in the old path,
:
That is to say, whenever the utility differentials are not so large for the DM to confront the cost of investing in a new path, then it is more efficient to remain in her status quo.
Given the parameters, the individual will maximize her total plan under the set of strategies and beliefs expressed above. If at any stage of the game the strategies are sequentially rational, namely, optimal given the beliefs, and the belief system is consistent given the equilibrium strategies, and considering that and A and respect the requirements for the existence of a fixed point according to Kakutani’s theorem, then:
Proposition 1. There exists a unique monotonic undominated equilibrium, characterized by thresholds and with and investment probabilities and such that: Because of Assumptions 3 and 4,
is weakly increasing in
, and then respectively in
p, imposing that a higher type cannot choose a lower investment choice.
hence, whenever
then
.
Moreover, monotone comparative statics imply that is a cutpoint decision rule. There is a parameter value , and respectively p such that the DM chooses the separating equilibria for some value moving from , and she can instead have multiple equilibria at the cutpoint.
The equilibrium is evaluated for
, for decreasing values of
. Moreover, the results above show that the probability of receiving a specific signal has a monotonic hump-shaped effect on the overall probability investment whose trend will increase in
p on the interval
15, then it will equal to 1 on
, and after that it will fall to 0.
Characterization of Equilibria. Let us discuss the incentive criteria (
15) and (
16) in order to characterize the equilibria.
Pooling toward null investment.
Both agents will choose the strategy of non-investment in the new path. From the assumption on
and the incentive criteria specific for each type, the
H types are those who might have some strategic interest in not investing in a different path, since for them the decision to invest could be less costly than for the
L type. Assume that it means that
In this equilibrium, we consider only the incentive constraint of an H-type, since for L-type it will be always costly to invest. We obtain the incentive constraint by knowing that if p is high enough (i.e., the self-image is behind the threshold ), H-type can afford not to invest. Then, and the posterior beliefs are and since and . Then, type H can afford not to invest if , but when the latter relation does not hold, then H will take some action to distinguish herself from L. In this equilibrium, H-type will not invest in education for several other motivations. The fact that in this scenario means that the agent is surrounded by people following the old path and it would be too costly for her to take action to prove being the eccentric one. If she deviates from the norm, this deviation will be self-justified, as the malleability of the beliefs will increase. In turn,
In this equilibrium, we consider both the incentive constraints of an H-type and an L-type. We get the incentive constraint by knowing that if there is the possibility of separating the types, then and and the posterior beliefs are and since and . Then, type H will invest and L will not since and the is so high that it is not worthwhile for L to invest. In this scenario, incentive constraints bind for the two types with and .
Semi-separating (hybrid) by randomising for
:
This scenario occurs when the cost of investment for L-type is small enough to imitate the H-type. However, the imitation is always constrained by the prior, and the credibility of signaling to be H-type depends on p and : the lower the former, the more credible the strategy. Then, we have and , and the posterior probabilities are while , with the posterior beliefs represented by and . Accordingly, type H will not invest and L will only depend on how credible the posterior probabilities are, .
Pooling towards total investment:
In the case of both types investing in further education, the incentive constraint that we need to consider is the one of the L-type, since by definition H-type will always have incentive to invest. In this scenario, we have that the probability to invest is and then, recalling (8), the posterior beliefs are and since and . Then, type H will invest and L will only if her binds and in that case . The incentive holds since it is worthy to pursue for costs facing even a small gain in self-image: as the cost increases, so does the threshold .
Comparative Analysis. The probability to invest (
x) is determined by both the internal (
p,
,
s) and external (
,
r,
) constraints. Moreover, both individuals invest more when
and
(weakly) increase. In all cases, type
H will go either for a separating, a full investment, or hybrid equilibrium, while type
L will invest only in hybrid or full situation. Then, to show for what values of the main parameters the probability to invest increases, we need to study how the incentive constraint varies with respect to a variation of parameters. From
if individuals invest in education, then
. We have:
is a measure of initial affiliation. Its level and quality are higher for the
H type, driving her to show more incentive in eliciting identity-affirming investment. The positive impact of the stock on the willingness to invest is a consequence of the so-called
escalating commitment, expressed by the requirement on
: individuals have a higher demand for optimistic beliefs when they have more at stake (in this case, when they have higher identity-specific capital
already invested). From here it is worth making another consideration:
The higher the initial investment, the more positive the emotion attached to future identity and the higher the incentive to invest.
An increase in the evaluation of the interest rate means an enlargement of the perception and awareness of the opportunity available. The interest rate of education is important information for the decision mechanism, and its lack depends on how connected the society is vertically and horizontally. Whenever the society is highly stratified, this piece of information is lost.
The more pleasant the sentiment related to the future identity conveyed by the investment possibility, the higher the incentive to invest. The positive feelings depend on how much the DM feels her current self connected with her future self, so that she can engage in forward-looking choices.
Finally, the impact of the cost on the probability of investment is inversely related regarding the type: for H-type, a decrease of the initial cost increases (it gets closer to 1), decreasing her willingness to invest. For type, a decrease of cost means a decrease of (it gets closer to 0) reducing the mixing region, then it increases her willingness to invest ().
4.2. Self-t Memory Manipulation Game
Once the signal has been received, how will the DM interpret the new information in order to safeguard her beliefs? Here, the Self-
t implements the recall strategy by using memory manipulation (or ex-post denial) to safeguard her beliefs. She has incentives to process the
H and
L signals asymmetrically. In order to do so, let us define what the expected utilities are given the signals and recollections
16.
When the signal is recall and interpreted realistically, the expected utilities given either the signal and the recollection are the same, then:
If the DM instead decides to rationalize the signal (i.e., if she recollects
), the expected utilities will be:
as illustrated in
Figure A217. The rationalization of the signal represents an incentive for the DM, who has preferences over her identity. Since the manipulation of her beliefs is defined according to Bayes’ rule, the DM will eventually make correct inferences and learn her identity. However, the updating process is slower than what would normally be implied by Bayes’ rule. This situation is described as
conservatism bias, according to which all new information is insufficiently weighted in the updating process.
Memory Manipulation. Individuals maximize utility not only through behavior but by adopting a view of reality that is consistent with their well-being. These views have direct effects on behavior. The adoption passes by the imperfect recall of information and manipulation of the beliefs. The main consequence is that the long-run self will recall the information received in such a way as to manipulate the information set
18 that the short-run self will inherit. Hence, after observing a signal
, the long-run self chooses
to maximize the following function:
By adding Equation (
26), we get
Definition 4. represents the decision-making factor.
Given the recall strategy, will the DM make a suboptimal decision?
Definition 5. represents the self-image differential in utility, considering .
Given the recall strategy, how much utility does the DM gain through a more favorable inference of her identity? Let us consider the two cases.
The expected utility of Self-
t conditional on receiving a signal
is:
Because of the assumption on revealed preferences , hence the decision-making factor is negative for the L type. That is to say, forgetting L’s signal might lead to a suboptimal choice of the future action. However, the self-esteem will boost, because of the stochastic ordering of the signal, .
Upon receiving a signal
, and after a few manipulations, the expected utility will be:
In this case, forgetting the H signal has a negative effect on both decision-making and self-esteem. Because of both the revealed preferences and the stochastic ordering, receiving H signal is a situation in which memory manipulation should not be implemented.
Memory Manipulation in Hedonic Case. If we consider the decision of recalling the signal as in pure hedonic value
19, then the DM will choose to consider only the self-image differential. The recall strategy will be dependent on it, on the cost function of memory, and on the content of the initial signal. In
Appendix C it is possible to find the full characterization of the equilibria coming from the manipulation when both types of agent choose the amount of information to recall. Let us consider case-by-case. When
Self-
t maximizes the following:
thus, Self-
t will choose the amount of manipulation, then
, so as to maximize the previous formula. Then, for
L-type we may observe that
then by Kuhn–Tucker Theorem,
The recollection strategy would be different for H and L types.
Let us start by studying the
L type. Her inference about the accuracy
20 of the signal, with some manipulation, is
whose values depend on whether
, then
, or
, then
. Hence,
. By applying Kuhn–Tucker’s theorem, the FOC (
30) becomes:
By the implicit function theorem, exists.
Proposition 2. The PBEs for belief manipulation are defined by The amount of belief manipulation will be:
Increasing in ;
Decreasing in ;
Increasing in p.
Analogously, the expected utility of Self-
t after observing an
H signal is:
and
Type
H’s inference about the accuracy
21 of the signal, with some manipulation is
whose values depend on whether
, then
, or
, then
. Hence,
. By applying Kuhn–Tucker’s theorem, the FOC (
35) becomes:
By the implicit function theorem exists.
Proposition 3. The PBEs for belief manipulation follow: The amount of belief manipulation will be:
In both cases, for any increase of
both sides of (
31) and (
36) are increasing in the belief strategy, then there may be multiple interior equilibria.
5. Discussion
Like in the investment decision, the possibility of different equilibria depends on the probability of investing that, in turn, rely on the decision of how to recollect the signal, , in accordance with the prevailing empirical expectations on the identity types . Moreover, the incentives to engage in manipulation are higher as the self-image payoff gain, , increases. The assumption of the manipulation cost function allows us to have equilibria with both manipulation and no manipulation according to the magnitude of . In a pure strategy with accurate recall, the initial division of the population will be reflected in the following periods, then no undermining of the self-esteem in terms of peer recognition.
In a pure strategy with suppression of the signal, the updated beliefs at time converge to the average level of , showing that DM has either overconfident or underconfident beliefs in absolute terms. Moreover, if we consider the initial proportion of H-type and L-type individuals in the population, then the sense of overconfidence or underconfidence will be held in relative terms: for example, in a population where , the median identity will be the one of . The norm is to be L-type. Accordingly, if we assume that the entire population is motivated to endorse the socially accepted type, then we may have L-type DM exercising , and H-type choosing , reinforcing the identity with trait L. Let us see how it works. As already stated at the beginning of the model, in the population a proportion of DMs are identified by having received the signal . The proportion of having received is p. The average identity is given by , which can be written as a function of the proportion of H-type individuals: . Now let us assume that the the median identity is given by . What would be the distribution of the self-evaluation? Let us assume that is a signal reducing the self-image of the DM and that everyone will use the choose the same probability of recalling the signal, , and accordingly they will impute the reliability of the memory by . Now, the self-assessment considering the accuracy of the recall will be , no longer . Then, the fraction of agents who will manipulate the recall is represented by and they are those who overestimate their identity by . To those individuals, we have to add the fraction of people who did receive a good signal, and they are p: the latter and the former will enlarge the proportion of people considering beyond the average, . While the fraction of those underestimating their ability by is represented by the minority p, who will see confirmed their self-assessment as an agent below-average. Moreover, the less the manipulation cost, the higher the number of H-types repressing the good signal. Another perspective from which to look at the problem can be expressed in terms of the homogeneity of the social context in which the DM lives. Whenever , the social system enforces the highest level of entropy and diversity and then the individual should not incur any dissonance problem. That is, in a society in which you have an equal chance of moving in one direction or another, then the self-esteem problem related to the quest of belonging can be downsized. Instead, whenever the context is highly homogeneous, then the choices of either the action and of the signal rationalization are driven by the sense of belonging to a precise social group.
Yet, the manipulation costs can be very high leaving individuals in self-trap situations caused by their beliefs. Then, as already proved, the initial proportion of identity has an effect on both recalling and action strategy. One question that arises is the following: if every strategy can be brought back primitively to p, would the DM be able to identify a signal as informative for her identity and aspirations and then make a decision accordingly? Additionally, why is this question so important? It is important because the initial beliefs work as a mental insurance tool affecting the propensity towards a new piece of information. Indeed, the cognitive neighborhood, or the the information about p through the experience of a “similar” other, matters. It also matters what fraction of information on p the DM draws from whom.
5.1. Characterizing Beliefs Updating Heuristics
The work on how the DM’s information processing can be restrained is very extensive. In the studies of belief updating (Tversky and Kahneman [
54]; Cameron [
55]; Eil and Rao [
56]; Mobius et al. [
57]), agents are provided with signals about the same quantity over which belief revisions are being analyzed. For example, in Eil and Rao [
56], Mobius et al. [
57], and Grossman and Owens [
58], respondents revise their beliefs about either their own intelligence or beauty, and receive feedback about the same underlying entity for which beliefs are being reported. In Nguyen [
59] and Zafar [
37,
38], information on future earnings has been provided to students in other contexts, and it has been shown to have an impact on actual schooling choices but not without a certain delay in updating. Recalling a good signal is appealing every time the outcome of that signal dominates any other outcomes. For example, signaling a high IQ or scoring a high point in a student laboratory experiment is always better than signaling the opposite [
18,
19], because the identity of “being a good student” is the dominant in such environment, hence any feedback contrasting that ideal identity would be forgotten.
In these and other contexts, the asymmetric recall of good signal is justified by the fact that being good is the most socially acceptable identity. Yet, there are social situations in which identity and social norms establish that being both good and bad are socially acceptable, in which the history of what is socially accepted matters in the way the DM will choose how to recollect information and on how fast she will update her beliefs. So far, the “bad norm” and the “persistence in time” of the norm have not been investigated throughly in the empirical literature of motivated beliefs. This model tries to approach the time variable showing how the presence of social norms can impose preferences over information structures that, in turn, make the DM execute a rational decision process in imperfectly recalling the signal received, regardless of its good or bad sign. Yet, empirical analysis is required.
Moreover, this literature classifies agents’ updating according to the heuristic used, which ranges from conservative to representative, taking distance from a Bayesian updating depending on the weight assigned to the recent information or on the adjustment mechanism.
The conservative heuristic is the one that better applies to the context of the model. Individuals are subjected to conservatism bias if they fail to sufficiently adjust their beliefs in light of new information. In other words, they update in the right direction but less than a Bayesian updater. In this regard, people suffering from conservatism bias are those sensitive to new information, and they prefer to infer their identity from their recollection rather than from the actual signal. If we consider as the expected value of given the information structure based on the recalled signal , while is the expected value of the identity parameter given the information structure produced by the observed signal (i.e., the Bayesian estimate of given the original signal), then dominates in the sense of second-order stochastic dominance.
Let us consider as the cumulative distribution of the expected value of conditional on the actual signal .
Proposition 4. Whenever the DM is uncertainty-averse and her decision-making is justified by the presence of social norms, and whenever she is exposed to two information structures (one of which is in conflict with the information released by the norm), she will order the two structures according to the Second order Stochastic Dominance (SOSD). Namely, she will choose the information structure that is less-variable with respect to the social norm. In our model, is less variable than . Additionally, the updating process of the information produced by σ, used by the DM, is conservative in the sense that it is less than what Bayes’ rule implies.
5.2. Welfare Analysis of Awareness
In order to further assess the analysis, the perspective to consider is an ex ante one that will try to answer the following question: if the DM could choose whether to engage in a manipulation strategy before receiving the initial signal, what would she do? Ex ante it would be optimal to commit not to engage in a rationalization strategy because the expected cost related to the strategy would outweigh the expected gain. Moreover, the DM would be willing to observe the signal if the expected costs of making an uninformative decision are greater than the premium of engagement. Otherwise, she would prefer to gain a lower expected payoff but also avoid the self-deception costs. If this did not happen, then the DM would follow one of the four methods
22 that in psychology are used as resolution of the dissonance: the selective exposure to information (i.e., the tendency people have to avoid information that would create cognitive dissonance because it is incompatible with their current beliefs).