An Oracle-Based On-Chain Privacy
Abstract
:1. Introduction
2. Background Review and Related Work
2.1. Background Review
2.1.1. Blockchain
2.1.2. Smart Contract
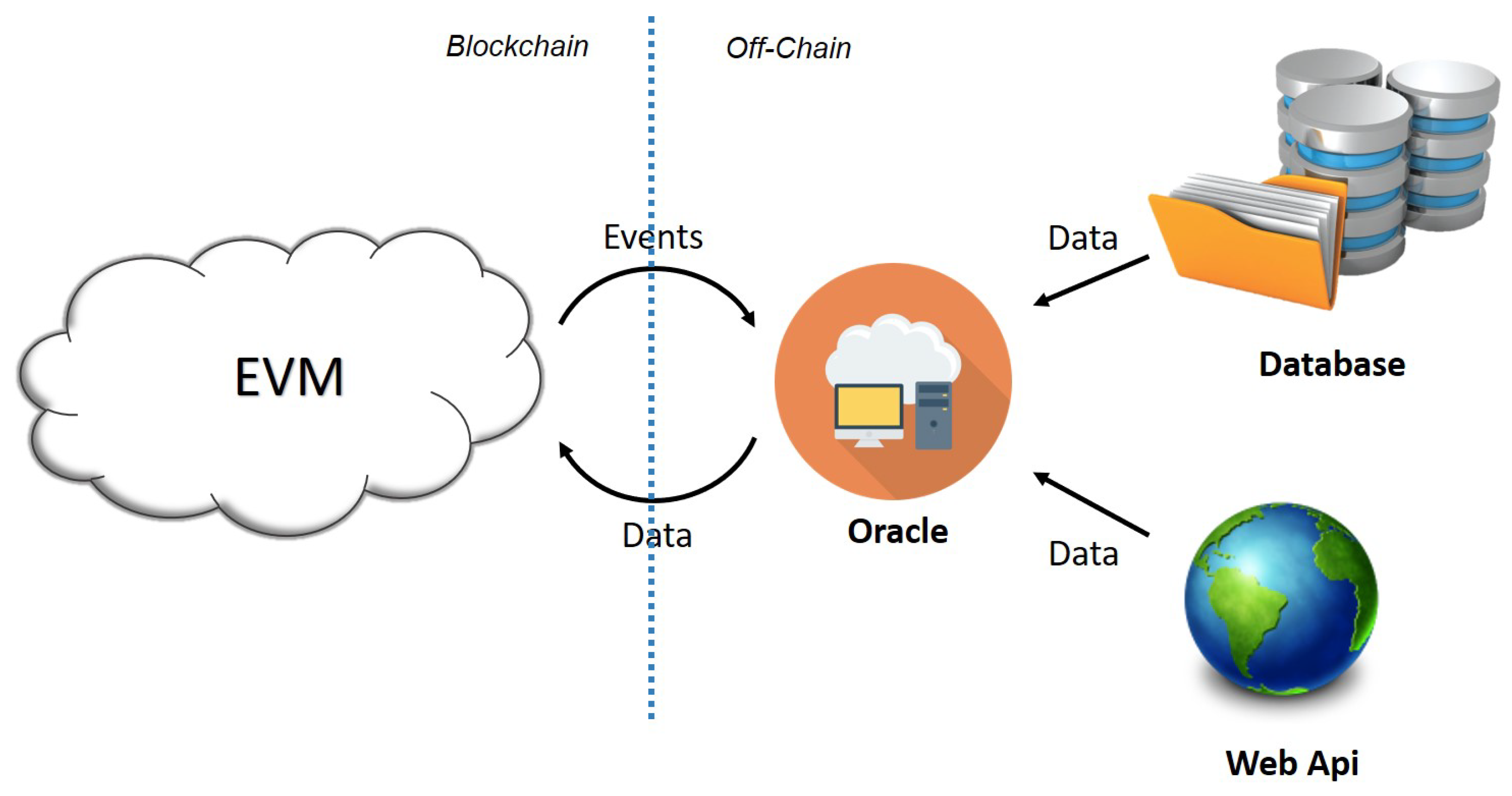
2.1.3. Oracle
2.1.4. Homomorphic Encryption Algorithms
2.2. Related Work
3. The Proposed Mechanisms
3.1. Execution Environment
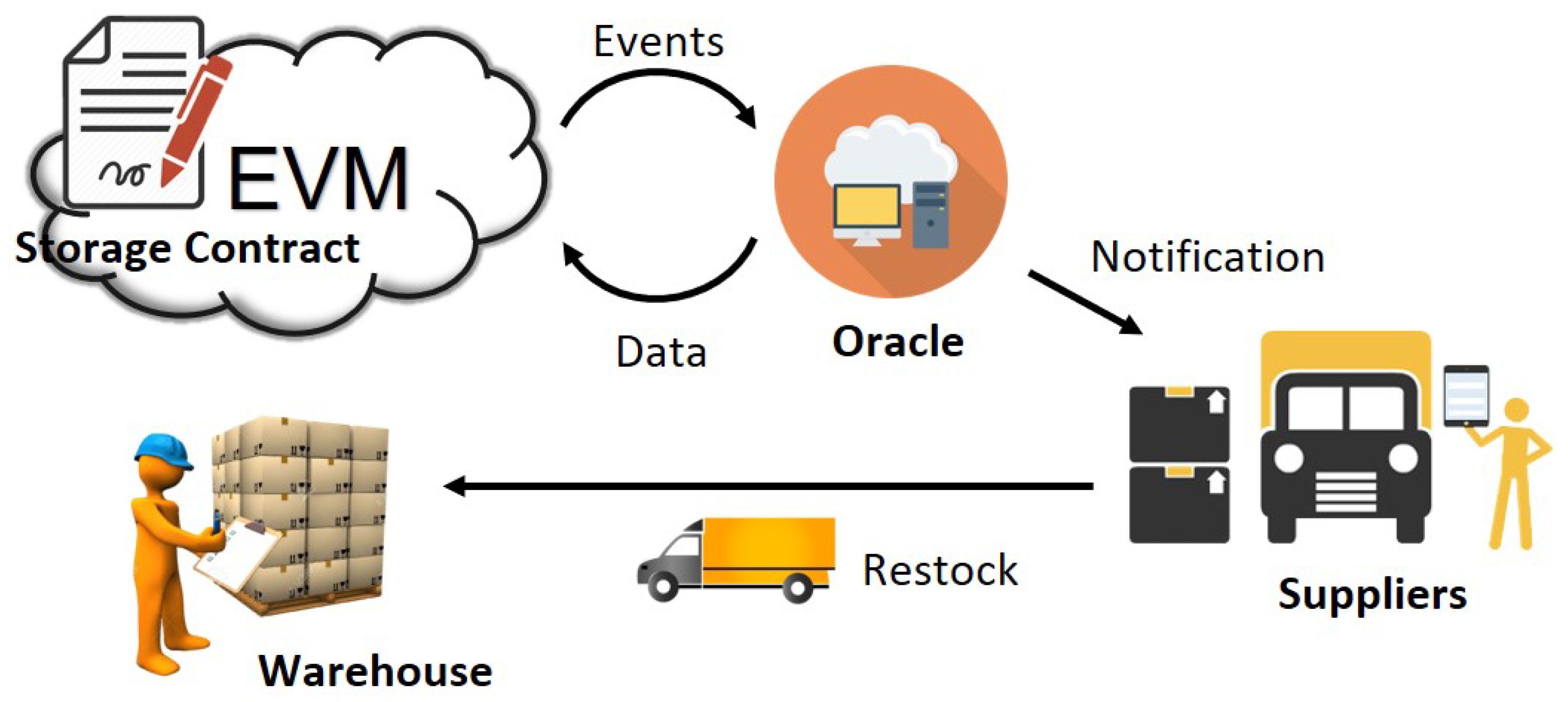
3.2. Application Scenario 1
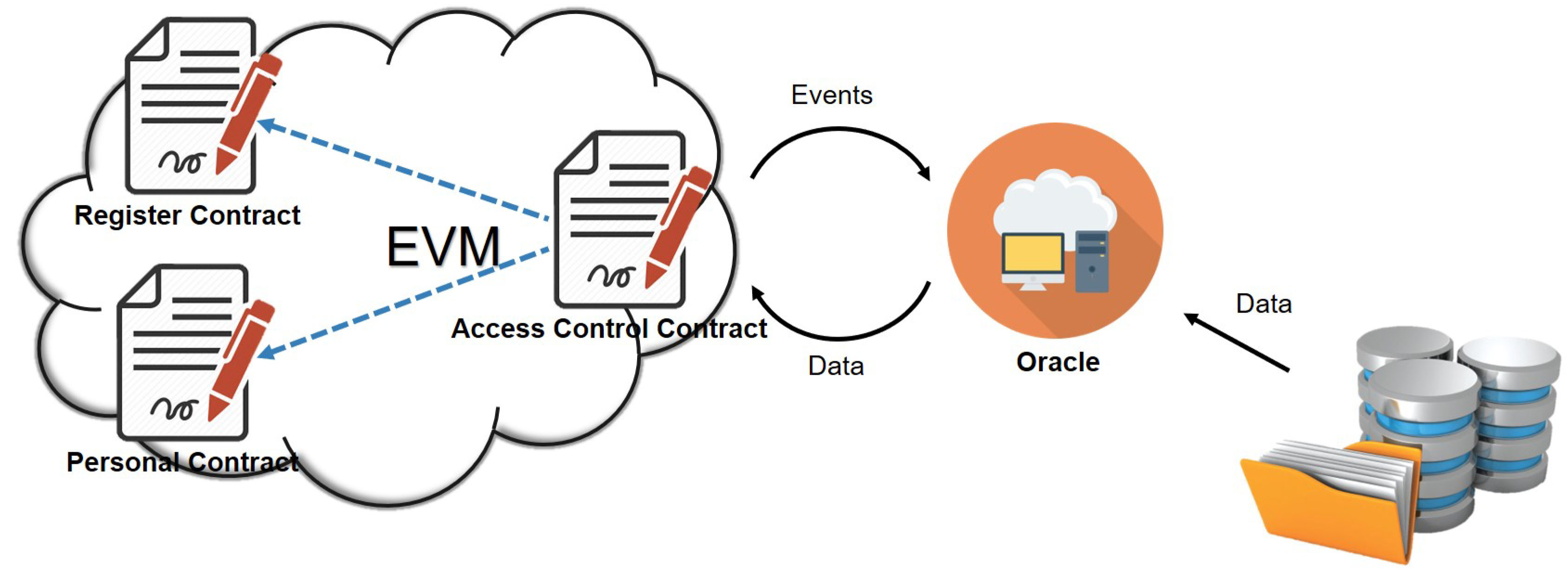
3.3. Application Scenario 2
3.3.1. Register Contract (RC)
3.3.2. Personal Contract (PC)
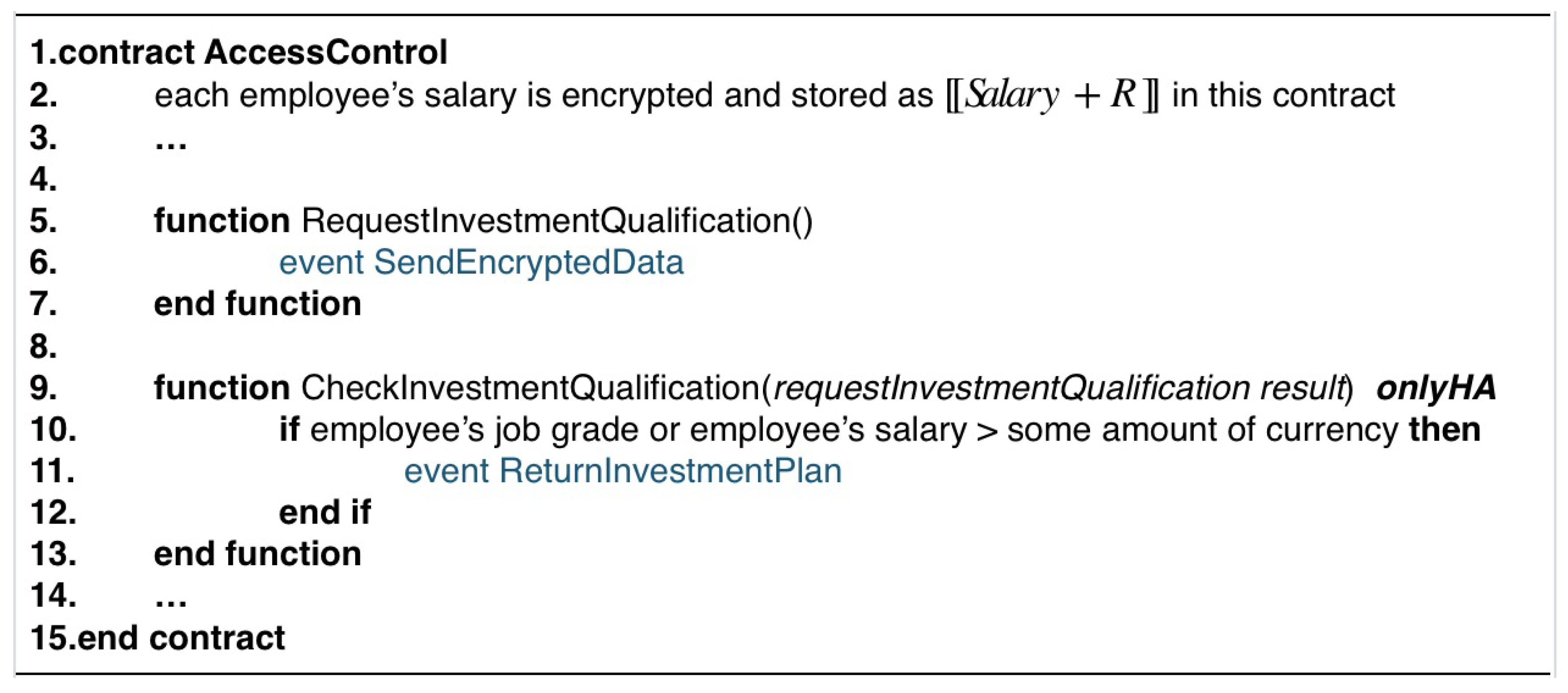
3.3.3. Access Control Contract (ACC)
3.4. On-Chain Privacy
3.5. The Applicability of the Proposed Scheme
4. Security Analysis
4.1. What If Some Adversaries Send Fake Transactions and Try to Tamper with the System?
4.2. What If an Adversary Can Read the Variable of the Contract Code?
4.3. Is an Adversary Still Be Able to Tamper with Our System without Going through the Register Account?
4.4. What If the Oracle Is Not Trustworthy?
5. Discussion
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Kar, I. Estonian Citizens Will Soon Have the World’s Most Hack-Proof Health-Care Records. 2016. Available online: http://qz.com/628889/this-eastern-european-country-is-moving-its-health-recordsto-the-blockchain/ (accessed on 27 August 2020).
- Kelly, J.; Williams, A. Forty Big Banks Test Blockchain-Based Bond Trading System. 2016. Available online: https://www.reuters.com/article/banking-blockchain-bonds/forty-big-banks-test-blockchain-based-bond-trading-system-idUSL8N16A30H (accessed on 27 August 2020).
- Azaria, A.; Ekblaw, A.; Vieira, T.; Lippman, A. MedRec: Using blockchain for medical data access and permission management. In Proceedings of the 2016 2nd International Conference on Open and Big Data (OBD). Institute of Electrical and Electronics Engineers (IEEE), Vienna, Austria, 22–24 August 2016. [Google Scholar]
- Lacey, S. The Energy Blockchain: How Bitcoin Could be a Catalyst for the Distributed Grid. 2016. Available online: http://www.greentechmedia.com/articles/read/the-energy-blockchain-could-bitcoin-be-a-catalyst-for-the-distributed-grid (accessed on 27 August 2020).
- Christidis, K.; Devetsikiotis, M. Blockchains and smart contracts for the internet of things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Yao, A.C. Protocols for secure computations. In Proceedings of the IEEE 23rd Annual Symposium on Foundations of Computer Science (sfcs 1982), Chicago, IL, USA, 3–5 November 1982. [Google Scholar]
- Rackoff, C.; Simon, D.R. Non-interactive zero-knowledge proof of knowledge and chosen ciphertext attack. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 1991. [Google Scholar]
- Armknecht, F.; Boyd, C.; Carr, C.; Gjosteen, K.; Jaschke, A.; Reuter, C.A.; Strand, M. A Guide to Fully Homomorphic Encryption. IACR Cryptol. ePrint Arch. 2015, 2015, 1192. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-peer Electronic Cash System; White Paper; 2008. Available online: https://git.dhimmel.com/bitcoin-whitepaper/ (accessed on 27 August 2020).
- Double-Spending—Bitcoin WiKi, Mar. 2016. Available online: https://en.bitcoin.it/wiki/Double-spending (accessed on 27 August 2020).
- Szabo, N. Smart Contracts. 1994. Available online: http://szabo.best.vwh.net/smart.contracts.html (accessed on 27 August 2020).
- Andrychowicz, M.; Dziembowski, S.; Malinowski, D.; Mazurek, L. Secure Multiparty Computations on Bitcoin. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 18–21 May 2014. [Google Scholar]
- Pass, R.; Shelat, A. Micropayments for decentralized currencies. In Proceedings of the ACM 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015. [Google Scholar]
- Kumaresan, R.; Bentov, I. How to Use Bitcoin to Incentivize Correct Computations. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014. [Google Scholar]
- Paillier, P. Public-key crypto systems based on composite degree residuosity classes. Eurocrypt 1999, 99, 223–238. [Google Scholar]
- Pieter, W. Hierarchical Deterministic Wallets (BIP:32). Available online: https://github.com/bitcoin/bips/blob/master/bip-0032.mediawiki (accessed on 27 August 2020).
- Maxwell, G. Confidential Transactions. Available online: https://elementsproject.org/features/confidential-transactions (accessed on 27 August 2020).
- Maxwell, G. CoinJoin. Bitcoin Forum. Available online: https://bitcointalk.org/index.php?topic=279249 (accessed on 27 August 2020).
- Heilman, E.; Alshenibr, L.; Baldimtsi, F.; Scafuro, A.; Goldberg, S. Tumblebit: An Untrusted Bitcoin-Compatible Anonymous Payment Hub; Network and Distributed System Security Symposium: San Diego, CA, USA, 2017. [Google Scholar]
- Poelstra, A. Mimblewimble: Non-Interactive CoinJoin and Better Scaling Properties Using Confidential Transactions. 2016. Available online: https://www.reddit.com/r/Bitcoin/comments/4vub3y/\mimblewimble_noninteractive_coinjoin_and_better/d61n7yd/ (accessed on 27 August 2020).
- Van Saberhagen, N. CrytoNote. 2013. Available online: https://cryptonote.org/whitepaper.pdf (accessed on 27 August 2020).
- Sasson, E.B.; Chiesa, A.; Garman, C.; Green, M.; Miers, I.; Tromer, E.; Virza, M. Zerocash: Decentralized anonymous payments from bitcoin. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 18–21 May 2014. [Google Scholar]
- Zyskindetal, G. Decentralizing privacy: Using blockchain to protect personal data. In Proceedings of the IEEE Security and Privacy Workshops (SPW), San Jose, CA, USA, 21–22 May 2015; pp. 180–184. [Google Scholar]
- Delgado-Mohatar, O.; Fierrez, J.; Tolosana, R.; Vera-Rodriguez, R. Biometric Template Storage with Blockchain: A First Look into Cost and Performance Tradeoffs. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition Workshops, Long Beach, CA, USA, 16–17 June 2019. [Google Scholar]
- White Paper—Ethereum/WiKi, Mar. 2016. Available online: https://github.com/ethereum/wiki/wiki/White-Paper (accessed on 27 August 2020).
- LevelDB, Google Inc. 2011. Available online: https://github.com/google/leveldb (accessed on 27 August 2020).
- Kosba, A.; Miller, A.; Shi, E.; Wen, Z.; Papamanthou, C. Hawk: The blockchain model of cryptography and privacy preserving smart contracts. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016. [Google Scholar]
- Goldwasser, S.; Micali, S. Probabilistic encryption & how to play mental poker keeping secret all partial information. In Proceedings of the ACM Fourteenth Annual ACM Symposium on Theory of Computing, San Francisco, CA, USA, 5–7 May 1982. [Google Scholar]
- Bost, R.; Popa, R.A.; Tu, S.; Goldwasser, S. Machine Learning Classification over Encrypted Data; NDSS: New York, NY, USA, 2015. [Google Scholar]

| Node A | Node B | |
| (holding decryption key sk2) | (holding decryption key sk1) | |
| 1: receive | ||
| 2: get from data owner | ||
| 3: | ||
| 4: Set , with | ||
| same bit length l, execute | ||
| secure comparison protocol | ||
| 5:Secure Comparison Protocol [29] Input: and Result: Node A gets a bit (where if ) | ||
| 6: mod () | ||
| 7: mod () | ||
| 8: | ||
| 9: | ||
| 10: mod | mod | |
| 11: Note A and Note B privately compute the encrypted bit [t] such that { } | ||
| 12: | ||
| 13: | ||
| 14: | () | |
| 15: | ||
| 16: | ||
| Adversary Tamper | Sensitive Data | Access Control | Distributed System | |
|---|---|---|---|---|
| Resistance | Protection | Mechanism | Consensus | |
| our system | ✓ | ✓ | ✓ | ✓ |
| Model | Off-Chain | Data Sharing | On-Chain | |
|---|---|---|---|---|
| Storage | Feature | Privacy | ||
| [23] | UTXO-based | ✓ | x | x |
| MedRec | Account-based | ✓ | ✓ | x |
| Proposed | Account-based | ✓ | ✓ | ✓ |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, Y.-J.; Wu, J.-L.; Hsieh, Y.-C.; Hsueh, C.-W. An Oracle-Based On-Chain Privacy. Computers 2020, 9, 69. https://doi.org/10.3390/computers9030069
Chen Y-J, Wu J-L, Hsieh Y-C, Hsueh C-W. An Oracle-Based On-Chain Privacy. Computers. 2020; 9(3):69. https://doi.org/10.3390/computers9030069
Chicago/Turabian StyleChen, Yu-Jen, Ja-Ling Wu, Yung-Chen Hsieh, and Chih-Wen Hsueh. 2020. "An Oracle-Based On-Chain Privacy" Computers 9, no. 3: 69. https://doi.org/10.3390/computers9030069
APA StyleChen, Y.-J., Wu, J.-L., Hsieh, Y.-C., & Hsueh, C.-W. (2020). An Oracle-Based On-Chain Privacy. Computers, 9(3), 69. https://doi.org/10.3390/computers9030069







