A Comprehensive and Systematic Survey on the Internet of Things: Security and Privacy Challenges, Security Frameworks, Enabling Technologies, Threats, Vulnerabilities and Countermeasures
Abstract
1. Introduction
Contribution
- Review the latest related security and privacy similar studies in IoT;
- Discuss proposals for IoT security architectures and frameworks in recent literature;
- Provide a taxonomy of attacks on IoT;
- Present classification of attacks’ impacts according to NIST’s FIPS 199 definitions on loss of Confidentiality, Integrity and Availability (CIA) due to attacks on select smart devices;
- Discuss a multi-faceted approach to mitigation and countermeasures in IoT security;
- Allocate a section on open research area pertain to IoT ecosystem.
2. IoT Overview
2.1. Internet of Things (IoT)
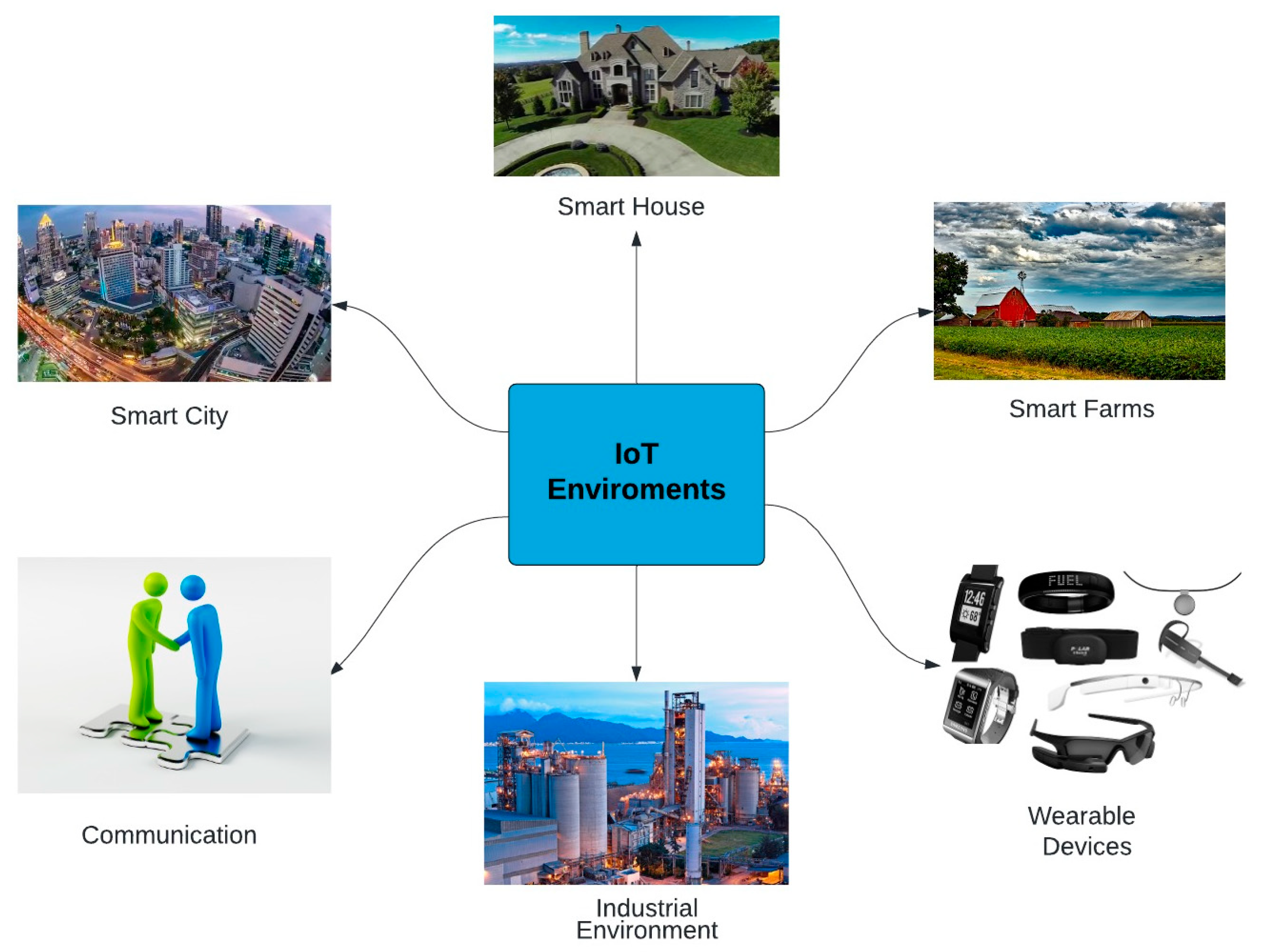
2.2. Application and Scope of Internet of Things
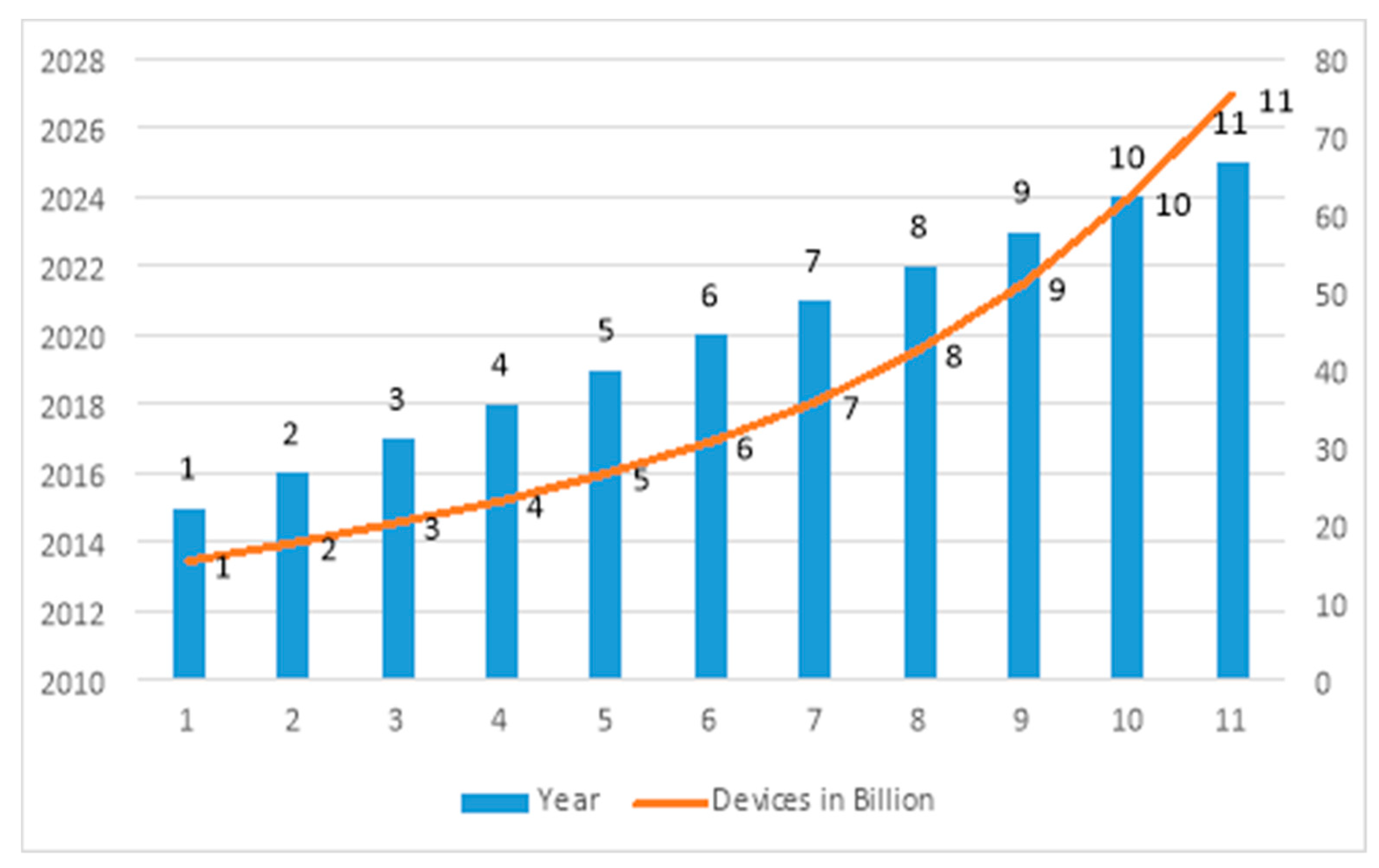
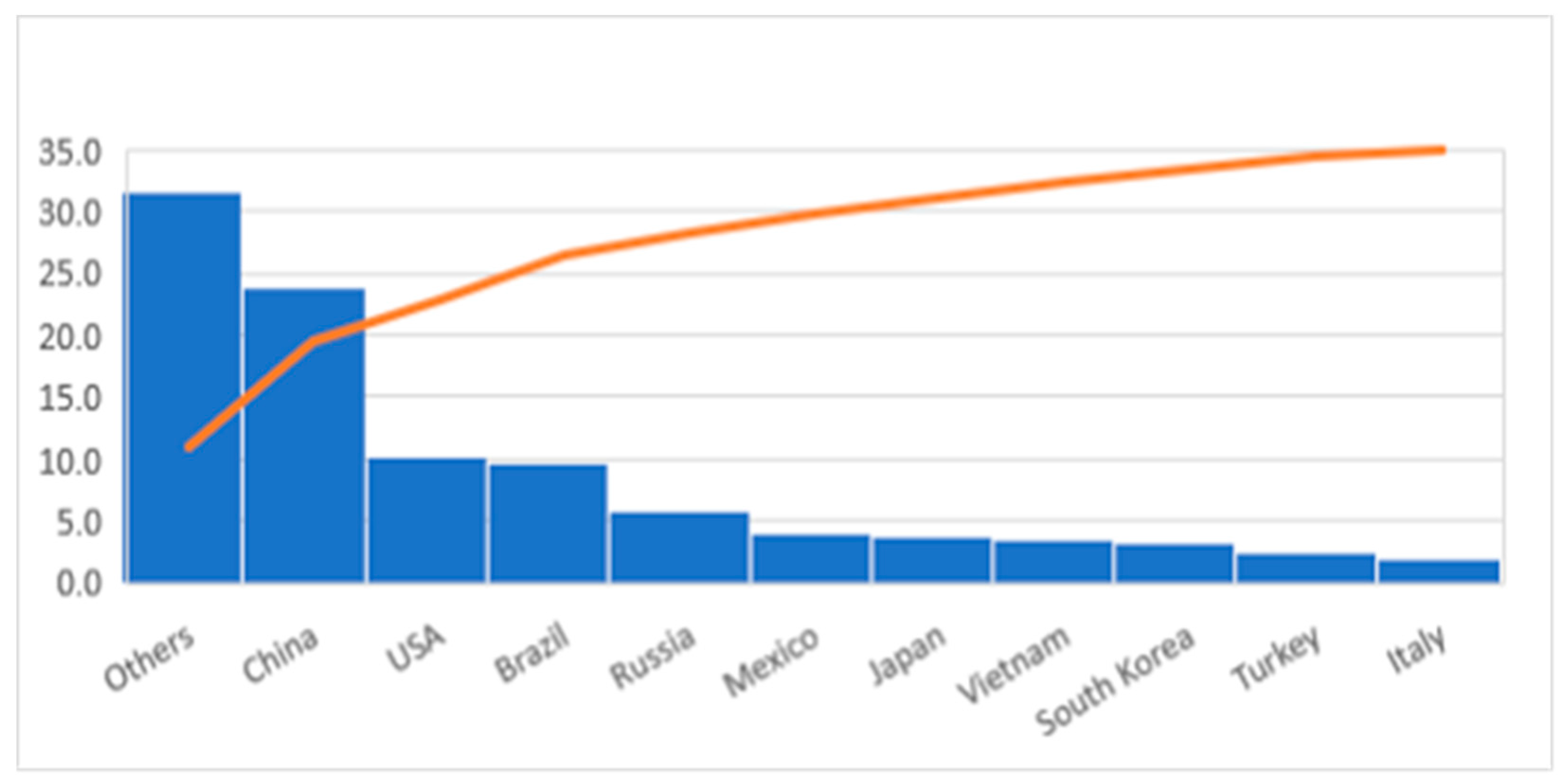
2.3. Sheer Volume of Devices Lacking Sophistication
2.4. Privacy Concerns, IoT’s
- Confidentiality-It ensures that only authorized users can access the data and information reports and only to the extent they need that access.
- Integrity-It ensures that data are secured and encrypted and only modified by authorized users during transmission, processing, and storage.
- Availability-Although it is essential to secure the data and information, we have to make sure data is available in a timely manner; otherwise, it may lose its value, e.g., in emergency and medical applications.
2.5. Phases of Data as They Pass through IoT’s Different Layers
2.6. IoT Wireless Protocols and Standards
3. Related Work
4. The Need for Security
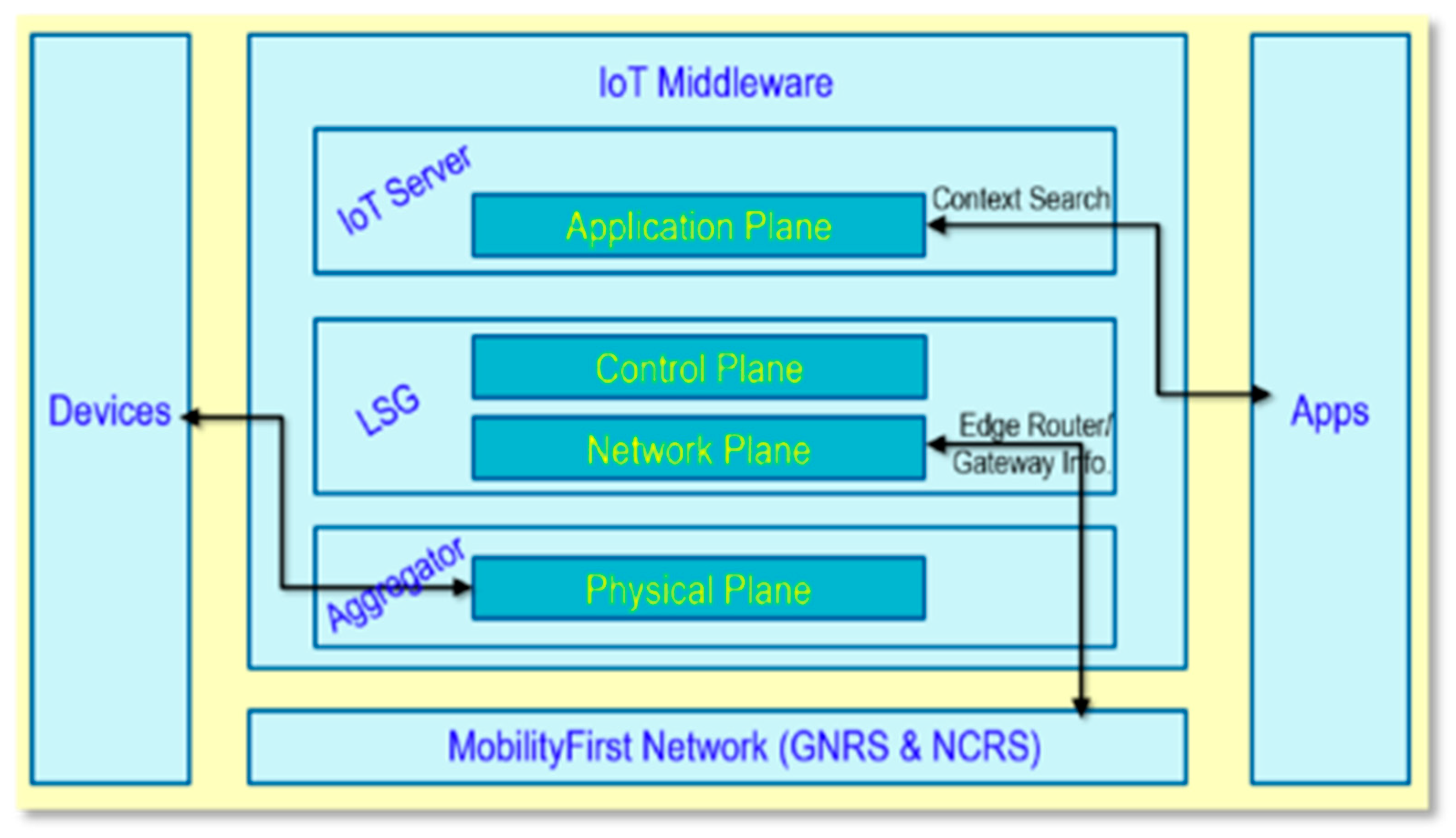
5. IoT Security Architectures and Frameworks
6. Attacks, Threats and Vulnerabilities
6.1. Perception/Physical Layer
6.2. Network Layer Attacks
6.3. Application Layer Attacks
6.4. Impact of Attacks on Security Objectives
- Low: limited effect on operations, assets, or individuals
- Moderate (Mod): serious effect on operations, assets, or individuals
- High: severe or catastrophic effect on operations, assets or individuals
- Not applicable: only applies to Confidentiality
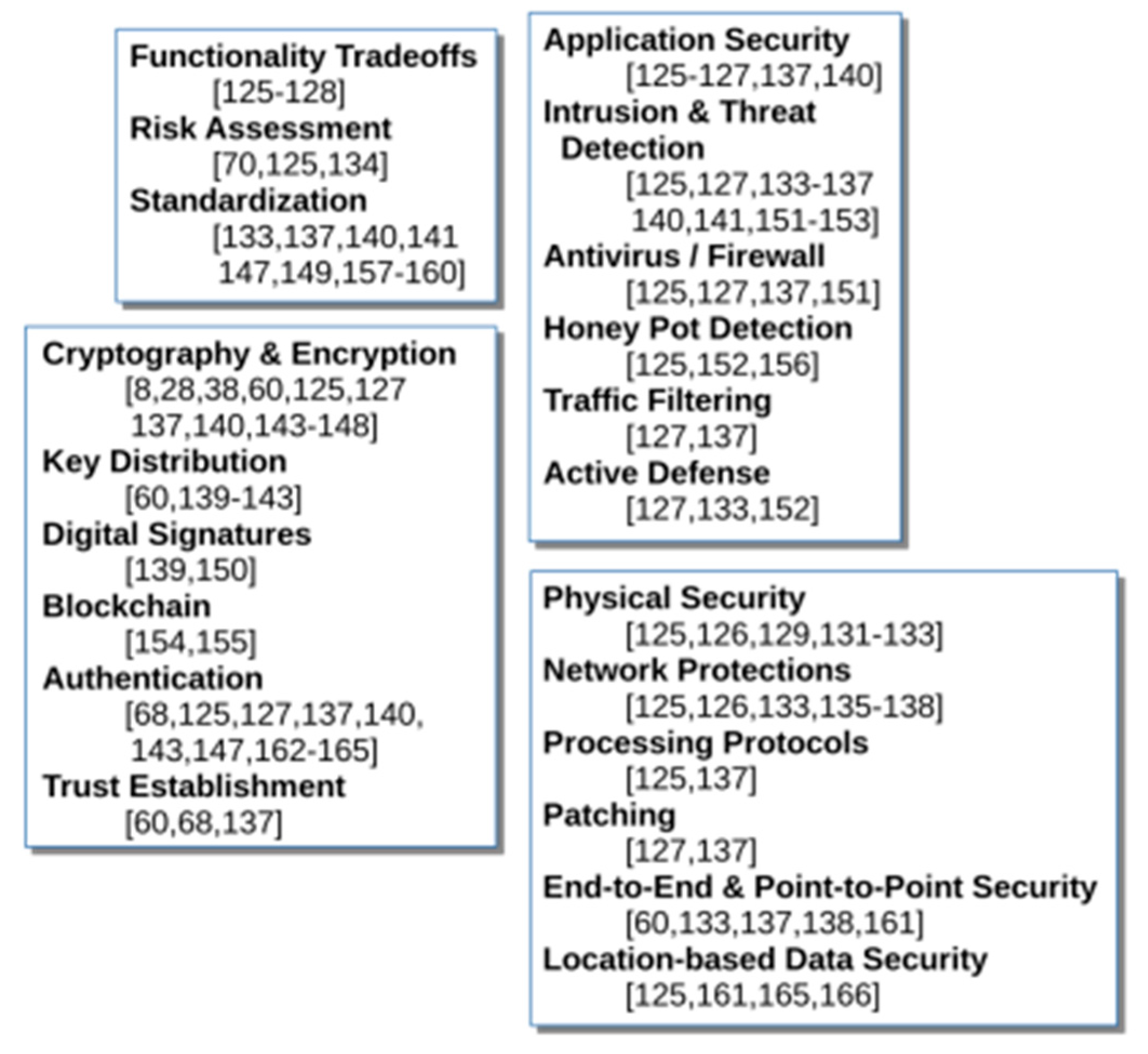
7. Mitigation and Countermeasures
7.1. Functionality Trade-Offs
7.2. Physical Security
7.3. Risk Assessment
7.4. Network Protections
7.5. Key Distribution
7.6. Cryptography and Encryption
7.7. Digital Signatures
7.8. Processing Protocols
7.9. Application Security
7.10. Patching
7.11. Intrusion and Threat Detection
7.12. Antivirus/Firewall
7.13. Blockchain
7.14. Honeypot Detection
7.15. Standardization
7.16. Traffic Filtering
7.17. End-to-End and Point-to-Point Security
7.18. Authentication
7.19. Trust Establishment
7.20. Active Defense
7.21. Location-based Data Security
8. Open Research Ideas
9. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Sha, K.; Wei, W.; Andrew Yang, T.; Wang, Z.; Shi, W. On security challenges and open issues in Internet of Things. Future Gener. Comput. Syst. 2018, 83, 326–337. [Google Scholar] [CrossRef]
- Samaila, M.G.; Neto, M.; Fernandes, D.A.B.; Freire, M.M.; Inácio, P.R.M. Challenges of securing Internet of Things devices: A survey. Secur. Priv. 2018, 1, e20. [Google Scholar] [CrossRef]
- El-Shweky, B.E.; El-Kholy, K.; Abdelghany, M.; Salah, M.; Wael, M.; Alsherbini, O.; Ismail, Y.; Salah, K.; AbdelSalam, M. Internet of things: A comparative study. In Proceedings of the 2018 IEEE 8th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 8–10 January 2018; pp. 622–631. [Google Scholar] [CrossRef]
- Hassan, A.M.; Awad, A.I. Urban Transition in the Era of the Internet of Things: Social Implications and Privacy Challenges. IEEE Access 2018, 6, 36428–36440. [Google Scholar] [CrossRef]
- Dhanvijay, M.M.; Patil, S.C. Internet of Things: A survey of enabling technologies in healthcare and its applications. Comput. Netw. 2019, 153, 113–131. [Google Scholar] [CrossRef]
- Ojo, M.O.; Giordano, S.; Procissi, G.; Seitanidis, I.N. A Review of Low-End, Middle-End, and High-End Iot Devices. IEEE Access 2018, 6, 70528–70554. [Google Scholar] [CrossRef]
- Frustaci, M.; Pace, P.; Aloi, G.; Fortino, G. Evaluating Critical Security Issues of the IoT World: Present and Future Challenges. IEEE Internet Things J. 2018, 5, 2483–2495. [Google Scholar] [CrossRef]
- Yu, S.; Wang, G.; Liu, X.; Niu, J. Security and Privacy in the Age of the Smart Internet of Things: An Overview from a Networking Perspective. IEEE Commun. Mag. 2018, 56, 14–18. [Google Scholar] [CrossRef]
- Liu, S.; Yue, K.; Zhang, Y.; Yang, H.; Liu, L.; Duan, X. The Research on IOT Security Architecture and Its Key Technologies. In Proceedings of the 2018 IEEE 3rd Advanced Information Technology, Electronic and Automation Control Conference (IAEAC), Chongqing, China, 12–14 October 2018; pp. 1277–1280. [Google Scholar]
- Guo, H.; Ren, J.; Zhang, D.; Zhang, Y.; Hu, J. A scalable and manageable IoT architecture based on transparent computing. J. Parallel Distrib. Comput. 2018, 118, 5–13. [Google Scholar] [CrossRef]
- Obaidat, M.; Khodiaeva, M.; Obeidat, S.; Salane, D.; Holst, J. Security Architecture Framework for Internet of Things (IoT). In Proceedings of the 2019 IEEE 10th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 10–12 October 2019; pp. 0154–0157. [Google Scholar]
- Zhao, K.; Ge, L. A Survey on the Internet of Things Security. In Proceedings of the 2013 Ninth International Conference on Computational Intelligence and Security, Leshan, Sichuan, China, 14–15 December 2013; pp. 663–667. [Google Scholar]
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A Survey on Internet of Things: Architecture, Enabling Technologies, Security and Privacy, and Applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Anderson, R.; Kuhn, M. Tamper resistance-a cautionary note. In Proceedings of the Second USENIX Workshop on Electronic Commerce, Oakland, CA, USA, 18–21 November 1996; pp. 1–11. [Google Scholar]
- Mahmoud, R.; Yousuf, T.; Aloul, F.; Zualkernan, I. Internet of things (IoT) security: Current status, challenges and prospective measures. In Proceedings of the 2015 10th International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 14–16 December 2015; pp. 336–341. [Google Scholar]
- Chen, K.; Zhang, S.; Li, Z.; Zhang, Y.; Deng, Q.; Ray, S.; Jin, Y. Internet-of-Things Security and Vulnerabilities: Taxonomy, Challenges, and Practice. J. Hardw. Syst. Secur. 2018, 2, 97–110. [Google Scholar] [CrossRef]
- Wolf, M.; Serpanos, D. Safety and Security in Cyber-Physical Systems and Internet-of-Things Systems. Proc. IEEE 2018, 106, 9–20. [Google Scholar] [CrossRef]
- Ali, Q.; Ahmad, N.; Malik, A.; Ali, G.; Rehman, W. Issues, Challenges, and Research Opportunities in Intelligent Transport System for Security and Privacy. Appl. Sci. 2018, 8, 1964. [Google Scholar] [CrossRef]
- Alam, M.M.; Malik, H.; Khan, M.I.; Pardy, T.; Kuusik, A.; Le Moullec, Y. A Survey on the Roles of Communication Technologies in IoT-Based Personalized Healthcare Applications. IEEE Access 2018, 6, 36611–36631. [Google Scholar] [CrossRef]
- Ling, Z.; Liu, K.; Xu, Y.; Jin, Y.; Fu, X. An End-to-End View of IoT Security and Privacy. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Stellios, I.; Kotzanikolaou, P.; Psarakis, M.; Alcaraz, C.; Lopez, J. A Survey of IoT-Enabled Cyberattacks: Assessing Attack Paths to Critical Infrastructures and Services. IEEE Commun. Surv. Tutor. 2018, 20, 3453–3495. [Google Scholar] [CrossRef]
- Sadique, K.M.; Rahmani, R.; Johannesson, P. Towards Security on Internet of Things: Applications and Challenges in Technology. Procedia Comput. Sci. 2018, 141, 199–206. [Google Scholar] [CrossRef]
- Ahanger, T.A.; Aljumah, A. Internet of Things: A Comprehensive Study of Security Issues and Defense Mechanisms. IEEE Access 2019, 7, 11020–11028. [Google Scholar] [CrossRef]
- NIST Computer Security Division. F. I. P. S. Standards for Security Categorization of Federal Information and Information Systems; NIST FIPS 199; NIST: Gaithersburg, MD, USA, 2004. [Google Scholar]
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT Security: An Exhaustive Survey on IoT Vulnerabilities and a First Empirical Look on Internet-Scale IoT Exploitations. IEEE Commun. Surv. Tutor. 2019, 21, 2702–2733. [Google Scholar] [CrossRef]
- Ahmed, A.W.; Khan, O.A.; Ahmed, M.M.; Shah, M.A. A Comprehensive Analysis on the Security Threats and their Countermeasures of IoT. IJACSA 2017, 8, 489–501. [Google Scholar]
- Datta, P.; Sharma, B. A survey on IoT architectures, protocols, security and smart city based applications. In Proceedings of the 2017 8th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Delhi, India, 3–5 July 2017; pp. 1–5. [Google Scholar]
- Rajendran, G.; Ragul Nivash, R.S.; Parthy, P.P.; Balamurugan, S. Modern security threats in the Internet of Things (IoT): Attacks and Countermeasures. In Proceedings of the 2019 International Carnahan Conference on Security Technology (ICCST), Chennai, India, 1–3 October 2019; pp. 1–6. [Google Scholar]
- Internet of Things Global Standards Initiative. Available online: https://www.itu.int/en/ITU-T/gsi/iot/Pages/default.aspx (accessed on 25 March 2020).
- Ghadeer, H. Cybersecurity Issues in Internet of Things and Countermeasures. In Proceedings of the 2018 IEEE International Conference on Industrial Internet (ICII), Bellevue, WA, USA, 21–23 October 2018; pp. 195–201. [Google Scholar]
- Dinker, A.G.; Sharma, V. Attacks and challenges in wireless sensor networks. In Proceedings of the 2016 3rd International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 16–18 March 2016; pp. 3069–3074. [Google Scholar]
- Li, C.; Zhang, L.-J. A Blockchain Based New Secure Multi-Layer Network Model for Internet of Things. In Proceedings of the 2017 IEEE International Congress on Internet of Things (ICIOT), Honolulu, HI, USA, 25–30 June 2017; pp. 33–41. [Google Scholar]
- Singh, M.; Singh, A.; Kim, S. Blockchain: A game changer for securing IoT data. In Proceedings of the 2018 IEEE 4th World Forum on Internet of Things (WF-IoT), Singapore, 5–8 February 2018; pp. 51–55. [Google Scholar]
- Sridhar, S.; Smys, S. Intelligent security framework for IoT devices cryptography based end-to-end security architecture. In Proceedings of the 2017 International Conference on Inve ntive Systems and Control (ICISC), Coimbatore, India, 19–20 January 2017; pp. 1–5. [Google Scholar]
- Zheng, Y.; Dhabu, S.S.; Chang, C.-H. Securing IoT Monitoring Device using PUF and Physical Layer Authentication. In Proceedings of the 2018 IEEE International Symposium on Circuits and Systems (ISCAS), Florence, Italy, 27–30 May 2018; pp. 1–5. [Google Scholar]
- Ullah, I.; Shah, M.A.; Wahid, A.; Waheed, A. Protection of enterprise resources: A novel security framework. In Proceedings of the 2017 International Conference on Communication Technologies (ComTech), Slamabad, Pakistan, 19–21 April 2017; pp. 98–103. [Google Scholar]
- Mahalle, P.N.; Anggorojati, B.; Prasad, N.R.; Prasad, R. Identity Authentication and Capability Based Access Control (IACAC) for the Internet of Things. J. Cyber Secur. Mob. 2013, 1, 309–348. [Google Scholar]
- Kayes, A.S.M.; Rahayu, W.; Dillon, T.; Chang, E. Accessing Data from Multiple Sources through Context-Aware Access Control. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 551–559. [Google Scholar] [CrossRef]
- Kayes, A.S.M.; Kalaria, R.; Sarker, I.H.; Islam, M.S.; Watters, P.A.; Ng, A.; Hammoudeh, M.; Badsha, S.; Kumara, I. A Survey of Context-Aware Access Control Mechanisms for Cloud and Fog Networks: Taxon. Open Reseach Issues. Sensors 2020, 20, 2464. [Google Scholar] [CrossRef]
- Jaswal, K.; Choudhury, T.; Chhokar, R.L.; Singh, S.R. Securing the Internet of Things: A proposed framework. In Proceedings of the 2017 International Conference on Computing, Communication and Automation (ICCCA), Greater Noida, India, 5–6 May 2017; pp. 1277–1281. [Google Scholar]
- Sedrati, A.; Mezrioui, A. Internet of Things challenges: A focus on security aspects. In Proceedings of the 2017 8th International Conference on Information and Communication Systems (ICICS), Irbid, Jordan, 4–6 April 2017; pp. 210–215. [Google Scholar]
- Florea, I.; Ruse, L.C.; Rughinis, R. Challenges in security in Internet of Things. In Proceedings of the 2017 16th RoEduNet Conference: Networking in Education and Research (RoEduNet), Targu Mures, Romania, 21–23 September 2017; pp. 1–5. [Google Scholar]
- Amadeo, M.; Molinaro, A.; Paratore, S.Y.; Altomare, A.; Giordano, A.; Mastroianni, C. A Cloud of Things framework for smart home services based on Information Centric Networking. In Proceedings of the 2017 IEEE 14th International Conference on Networking, Sensing and Control (ICNSC), Calabria, Italy, 16–18 May 2017; pp. 245–250. [Google Scholar]
- Naoui, S.; Elhdhili, M.E.; Saidane, L.A. Security analysis of existing IoT key management protocols. In Proceedings of the 2016 IEEE/ACS 13th International Conference of Computer Systems and Applications (AICCSA), Agadir, Morocco, 29 November–3 December 2016; pp. 1–7. [Google Scholar]
- Agarwal, Y.; Dey, A.K. Toward Building a Safe, Secure, and Easy-to-Use Internet of Things Infrastructure. Computer 2016, 49, 88–91. [Google Scholar] [CrossRef]
- Lee, J.; Yu, S.; Park, K.; Park, Y.; Park, Y. Secure Three-Factor Authentication Protocol for Multi-Gateway IoT Environments. Sensors 2019, 19, 2358. [Google Scholar] [CrossRef] [PubMed]
- Al Hayajneh, A.; Bhuiyan, M.Z.A.; McAndrew, I. Improving Internet of Things (IoT) Security with Software-Defined Networking (SDN). Computers 2020, 9, 8. [Google Scholar] [CrossRef]
- The History and Future of the Internet of Things. Available online: https://www.itransition.com/blog/iot-history (accessed on 25 March 2020).
- Al Hayajneh, A.; Bhuiyan, M.Z.A.; McAndrew, I. A Novel Security Protocol for Wireless Sensor Networks with Cooperative Communication. Computers 2020, 9, 4. [Google Scholar] [CrossRef]
- Hayajneh, T.; Griggs, K.; Imran, M. Secure and efficient data delivery for fog-assisted wireless body area networks. Peer-to-Peer Netw. Appl. 2019, 12, 1289–1307. [Google Scholar] [CrossRef]
- Tao, H.; Bhuiyan, M.Z.A.; Abdalla, A.N.; Hassan, M.M.; Zain, J.M.; Hayajneh, T. Secured Data Collection with Hardware-Based Ciphers for IoT-Based Healthcare. IEEE Internet Things J. 2019, 6, 410–420. [Google Scholar] [CrossRef]
- Alam, T. A Reliable Communication Framework and Its Use in Internet of Things (IoT). IJSRCSEIT 2018, 3, 450–456. [Google Scholar]
- Broadcom, Symantec, Internet Security Threat Report, Volume 24. Available online: https://www.broadcom.com/support/security-center (accessed on 11 March 2020).
- Broadcom, Symantec, Internet Security Threat Report, Volume 21. Available online: https://www.broadcom.com/support/security-center (accessed on 11 March 2020).
- Ferrag, M.A.; Maglaras, L.A.; Janicke, H.; Jiang, J.; Shu, L. Authentication Protocols for Internet of Things: A Comprehensive Survey. Secur. Commun. Netw. 2017, 2017, 1–41. [Google Scholar] [CrossRef]
- Sfar, A.R.; Natalizio, E.; Challal, Y.; Chtourou, Z. A roadmap for security challenges in the Internet of Things. Digit. Commun. Netw. 2018, 4, 118–137. [Google Scholar] [CrossRef]
- Singh, D.; Pati, B.; Panigrahi, C.R.; Swagatika, S. Security Issues in IoT and their Countermeasures in Smart City Applications. In Advanced Computing and Intelligent Engineering; Pati, B., Panigrahi, C.R., Buyya, R., Li, K.-C., Eds.; Springer: Singapore, 2020; Volume 1089, pp. 301–313. ISBN 9789811514821. [Google Scholar]
- Yassine, A.; Singh, S.; Hossain, M.S.; Muhammad, G. IoT big data analytics for smart homes with fog and cloud computing. Futur. Gener. Comput. Syst. 2019, 91, 563–573. [Google Scholar] [CrossRef]
- Guimaraes, V.G.; de Moraes, R.M.; Obraczka, K.; Bauchspiess, A. A Novel IoT Protocol Architecture: Efficiency through Data and Functionality Sharing across Layers. In Proceedings of the 2019 28th International Conference on Computer Communication and Networks (ICCCN), Valencia, Spain, 29 July–1 August 2019; pp. 1–9. [Google Scholar]
- Xhafa, F.; Kilic, B.; Krause, P. Evaluation of IoT stream processing at edge computing layer for semantic data enrichment. Futur. Gener. Comput. Syst. 2020, 105, 730–736. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Futur. Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Salman, T.; Jain, R. A Survey of Protocols and Standards for Internet of Things. arXiv 2019, arXiv:1903.11549. [Google Scholar] [CrossRef]
- 6 Leading Types of IoT Wireless Tech and Their Best Use Cases. Available online: https://behrtech.com/blog/6-leading-types-of-iot-wireless-tech-and-their-best-use-cases (accessed on 4 April 2020).
- Chi, T.; Chen, M. A frequency hopping method for spatial RFID/WiFi/Bluetooth scheduling in agricultural IoT. Wirel. Netw. 2019, 25, 805–817. [Google Scholar] [CrossRef]
- Kurunathan, H.; Severino, R.; Koubaa, A.; Tovar, E. DynaMO—Dynamic Multisuperframe Tuning for Adaptive IEEE 802.15.4e DSME Networks. IEEE Access 2019, 7, 122522–122535. [Google Scholar] [CrossRef]
- Zandberg, K.; Schleiser, K.; Acosta, F.; Tschofenig, H.; Baccelli, E. Secure Firmware Updates for Constrained IoT Devices Using Open Standards: A Reality Check. IEEE Access 2019, 7, 71907–71920. [Google Scholar] [CrossRef]
- Ammar, M.; Russello, G.; Crispo, B. Internet of Things: A survey on the security of IoT frameworks. J. Inf. Secur. Appl. 2018, 38, 8–27. [Google Scholar] [CrossRef]
- Barki, A.; Bouabdallah, A.; Gharout, S.; Traore, J. M2M Security: Challenges and Solutions. IEEE Commun. Surv. Tutor. 2016, 18, 1241–1254. [Google Scholar] [CrossRef]
- Benzarti, S.; Triki, B.; Korbaa, O. A survey on attacks in Internet of Things based networks. In Proceedings of the 2017 International Conference on Engineering & MIS (ICEMIS), Monastir, Tunisia, 8–10 May 2017; pp. 1–7. [Google Scholar]
- Abdur, M.; Habib, S.; Ali, M.; Ullah, S. Security Issues in the Internet of Things (IoT): A Comprehensive Study. IJACSA 2017, 8, 383–388. [Google Scholar] [CrossRef]
- Hossain, M.M.; Fotouhi, M.; Hasan, R. Towards an Analysis of Security Issues, Challenges, and Open Problems in the Internet of Things. In Proceedings of the 2015 IEEE World Congress on Services, New York, NY, USA, 27 June–2 July 2015; pp. 21–28. [Google Scholar]
- Abomhara, M.; Køien, G.M. Cyber Security and the Internet of Things: Vulnerabilities, Threats, Intruders and Attacks. JCSM 2015, 4, 65–88. [Google Scholar] [CrossRef]
- Dorsemaine, B.; Gaulier, J.-P.; Wary, J.-P.; Kheir, N.; Urien, P. A new approach to investigate IoT threats based on a four layer model. In Proceedings of the 2016 13th International Conference on New Technologies for Distributed Systems (NOTERE), Paris, France, 18 July 2016; pp. 1–6. [Google Scholar]
- Ahmed, E.; Yaqoob, I.; Gani, A.; Imran, M.; Guizani, M. Internet-of-things-based smart environments: State of the art, taxonomy, and open research challenges. IEEE Wirel. Commun. 2016, 23, 10–16. [Google Scholar] [CrossRef]
- Humayed, A.; Lin, J.; Li, F.; Luo, B. Cyber-Physical Systems Security—A Survey. IEEE Internet Things J. 2017, 4, 1802–1831. [Google Scholar] [CrossRef]
- Mosenia, A.; Jha, N.K. A Comprehensive Study of Security of Internet-of-Things. IEEE Trans. Emerg. Topics Comput. 2017, 5, 586–602. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Makhdoom, I.; Abolhasan, M.; Lipman, J.; Liu, R.P.; Ni, W. Anatomy of Threats to the Internet of Things. IEEE Commun. Surv. Tutor. 2019, 21, 1636–1675. [Google Scholar] [CrossRef]
- Miloslavskaya, N.; Tolstoy, A. Internet of Things: Information security challenges and solutions. Cluster Comput. 2019, 22, 103–119. [Google Scholar] [CrossRef]
- Zhou, W.; Jia, Y.; Peng, A.; Zhang, Y.; Liu, P. The Effect of IoT New Features on Security and Privacy: New Threats, Existing Solutions, and Challenges Yet to Be Solved. IEEE Internet Things J. 2019, 6, 1606–1616. [Google Scholar] [CrossRef]
- Akram, H.; Konstantas, D.; Mahyoub, M. A Comprehensive IoT Attacks Survey based on a Building-blocked Reference Model. IJACSA 2018, 9, 090349. [Google Scholar] [CrossRef]
- Obaidat, M.; Khodjaeva, M.; Holst, J.; Ben Zid, M. Security and Privacy Challenges in Vehicular Ad Hoc Networks. In Connected Vehicles in the Internet of Things: Concepts, Technologies and Frameworks for the IoV; Mahmood, Z., Ed.; Springer International Publishing: Cham, Switzerland, 2020; pp. 223–251. ISBN 978-3-030-36167-9. [Google Scholar]
- Khodjaeva, M.; Obeidat, M.; Salane, D. Mitigating Threats and Vulnerabilities of RFID in IoT through Outsourcing Computations Using Public Key Cryptography. In Security, Privacy and Trust in the IoT Environment; Springer: Berlin/Heidelberg, Germany, 2019. [Google Scholar]
- Internet of Things: The Complete Reimaginative Force: TCS Global Trend Study-July 2015. Available online: https://www.criticaleye.com/inspiring/insights-servfile.cfm?id=4255 (accessed on 27 May 2020).
- Patel, C.; Doshi, N. Internet of Things Security: Challenges, Advances, and Analytics, 1st ed.; Auerbach Publications: Boca Raton, FL, USA, 2019; ISBN 9780429454448. [Google Scholar]
- Chaudhuri, A. Internet of Things, for Things, and by Things, 1st ed.; Auerbach Publications; CRC Press/Taylor & Francis Group: Boca Raton, FL, USA, 2018; ISBN 9781315200644. [Google Scholar]
- Urien, P. An innovative security architecture for low cost low power IoT devices based on secure elements: A four quarters security architecture. In Proceedings of the 2018 15th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 12–15 January 2018; pp. 1–2. [Google Scholar]
- Yu, S.; Park, K.; Park, Y. A Secure Lightweight Three-Factor Authentication Scheme for IoT in Cloud Computing Environment. Sensors 2019, 19, 3598. [Google Scholar] [CrossRef]
- Olivier, F.; Carlos, G.; Florent, N. New Security Architecture for IoT Network. Procedia Comput. Sci. 2015, 52, 1028–1033. [Google Scholar] [CrossRef]
- Ling, Z.; Liu, K.; Xu, Y.; Gao, C.; Jin, Y.; Zou, C.; Fu, X.; Zhao, W. IoT Security: An End-to-End View and Case Study. arXiv 2018, arXiv:1805.05853. [Google Scholar]
- Liu, X.; Zhao, M.; Li, S.; Zhang, F.; Trappe, W. A Security Framework for the Internet of Things in the Future Internet Architecture. Future Internet 2017, 9, 27. [Google Scholar] [CrossRef]
- Huang, X.; Craig, P.; Lin, H.; Yan, Z. SecIoT: A security framework for the Internet of Things: SecIoT: A security framework for the Internet of Things. Secur. Comm. Netw. 2016, 9, 3083–3094. [Google Scholar] [CrossRef]
- Colombo, P.; Ferrari, E. Fine-Grained Access Control within NoSQL Document-Oriented Datastores. Data Sci. Eng. 2016, 1, 127–138. [Google Scholar]
- Colombo, P.; Ferrari, E. Enhancing MongoDB with purpose based access control. IEEE Trans. Dependable Secure Comput. 2015, 14, 591–604. [Google Scholar] [CrossRef]
- Colombo, P.; Ferrari, E. Towards virtual private NoSQL datastores. In Proceedings of the 2016 IEEE 32nd International Conference on Data Engineering (ICDE), Helsinki, Finland, 16–20 May 2016; pp. 193–204. [Google Scholar]
- Ulusoy, H.; Colombo, P.; Ferrari, E.; Kantarcioglu, M.; Pattuk, E. GuardMR, fine-grained security policy enforcement for MapReduce systems. In Proceedings of the 10th ACM Symposium on Information, Computer and Communications Security, Singapore, 14–17 April 2015; pp. 285–296. [Google Scholar]
- Colombo, P.; Ferrari, E. Enhancing NoSQL datastores with fine-grained context-aware access control: A preliminary study on MongoDB. Int. J. Cloud Comput. 2017, 6, 292–305. [Google Scholar] [CrossRef]
- Irshad, M. A Systematic Review of Information Security Frameworks in the Internet of Things (IoT). In Proceedings of the 2016 IEEE 18th International Conference on High Performance Computing and Communications; IEEE 14th International Conference on Smart City; IEEE 2nd International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Sydney, Australia, 12–14 December 2016; pp. 1270–1275. [Google Scholar]
- Krishna, B.V.S.; Gnanasekaran, T. A systematic study of security issues in Internet-of-Things (IoT). In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Coimbatore, India, 10–11 February 2017; pp. 107–111. [Google Scholar]
- Ahemd, M.M.; Shah, M.A.; Wahid, A. IoT security: A layered approach for attacks & defenses. In Proceedings of the 2017 International Conference on Communication Technologies (ComTech), Rawalpindi, Pakistan, 19–21 October 2017; pp. 104–110. [Google Scholar]
- 101. Lee, C.; Zappaterra, L.; Kwanghee, C. Hyeong-Ah Choi Securing smart home: Technologies, security challenges, and security requirements. In Proceedings of the 2014 IEEE Conference on Communications and Network Security, San Francisco, CA, USA, 29–31 October 2014; pp. 67–72. [Google Scholar]
- Puthal, D.; Nepal, S.; Ranjan, R.; Chen, J. Threats to Networking Cloud and Edge Datacenters in the Internet of Things. IEEE Cloud Comput. 2016, 3, 64–71. [Google Scholar] [CrossRef]
- Atamli, A.W.; Martin, A. Threat-Based Security Analysis for the Internet of Things. In Proceedings of the 2014 International Workshop on Secure Internet of Things, Wroclaw, Poland, 7–11 September 2014; pp. 35–43. [Google Scholar]
- Andrea, I.; Chrysostomou, C.; Hadjichristofi, G. Internet of Things: Security vulnerabilities and challenges. In Proceedings of the 2015 IEEE Symposium on Computers and Communication (ISCC), Larnaca, Cyprus, 6–9 July 2015; pp. 180–187. [Google Scholar]
- Wang, X.; Chellappan, S.; Gu, W.; Yu, W.; Xuan, D. Search-based physical attacks in sensor networks. In Proceedings of the 14th International Conference on Computer Communications and Networks, ICCCN 2005, San Diego, CA, USA, 17–19 October 2005; pp. 489–496. [Google Scholar]
- Parno, B.; Perrig, A.; Gligor, V. Distributed Detection of Node Replication Attacks in Sensor Networks. In Proceedings of the 2005 IEEE Symposium on Security and Privacy (S&P’05), Oakland, CA, USA, 8–11 May 2005; pp. 49–63. [Google Scholar]
- Zorzi, M.; Gluhak, A.; Lange, S.; Bassi, A. From today’s INTRAnet of things to a future INTERnet of things: A wireless- and mobility-related view. IEEE Wirel. Commun. 2010, 17, 44–51. [Google Scholar] [CrossRef]
- Hernandez, G.; Arias, O.; Buentello, D.; Jin, Y. Smart Nest thermostat: A Smart Spy in Your Home. In Proceedings of the Black Hat, Las Vegas, NV, USA, 6–7 August 2014. [Google Scholar]
- Kaur, D.; Singh, P. Various OSI Layer Attacks and Countermeasure to Enhance the Performance of WSNs during Wormhole Attack. ACEEE Int. J. Netw. Secur. 2014, 5, 1. [Google Scholar]
- Laeeq, K.; Shamsi, J.A. A Study of Security Issues, Vulnerabilities and Challenges in Internet of Things. In Securing Cyber-Physical Systems; Pathan, A.K., Ed.; CRC Press: Boca Raton, FL, USA, 2015; p. 221. [Google Scholar]
- Deogirikar, J.; Vidhate, A. Security attacks in IoT: A survey. In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 10–11 February 2017; pp. 32–37. [Google Scholar]
- Weingart, S.H. Physical Security Devices for Computer Subsystems: A Survey of Attacks and Defenses. In Cryptographic Hardware and Embedded Systems—CHES 2000; Koç, Ç.K., Paar, C., Eds.; Springer: Berlin/Heidelberg, Germany, 2000; Volume 1965, pp. 302–317. ISBN 9783540414551. [Google Scholar]
- Martin, T.; Hsiao, M.; Dong, H.; Krishnaswami, J. Denial-of-service attacks on battery-powered mobile computers. In Proceedings of the Second IEEE Annual Conference on Pervasive Computing and Communications, Orlando, FL, USA, 14–17 March 2004; pp. 309–318. [Google Scholar]
- Khouzani, M.H.R.; Sarkar, S. Maximum Damage Battery Depletion Attack in Mobile Sensor Networks. IEEE Trans. Automat. Contr. 2011, 56, 2358–2368. [Google Scholar] [CrossRef]
- Agah, A.; Das, S.K. Preventing DoS attacks in wireless sensor networks: A repeated game theory approach. IJ Netw. Secur. 2007, 5, 145–153. [Google Scholar]
- Vasserman, E.Y.; Hopper, N. Vampire Attacks: Draining Life from Wireless Ad Hoc Sensor Networks. IEEE Trans. Mob. Comput. 2013, 12, 318–332. [Google Scholar] [CrossRef]
- Li, M.; Koutsopoulos, I.; Poovendran, R. Optimal Jamming Attack Strategies and Network Defense Policies in Wireless Sensor Networks. IEEE Trans. Mob. Comput. 2010, 9, 1119–1133. [Google Scholar]
- Billure, R.; Tayur, V.M.; Mahesh, V. Internet of Things-A study on the security challenges. In Proceedings of the 2015 IEEE International Advance Computing Conference (IACC), Banglore, India, 12–13 June 2015; pp. 247–252. [Google Scholar]
- Halim, T.; Islam, M.R. A Study on the Security Issues in WSN. Int. J. Comput. Appl. 2012, 53. [Google Scholar] [CrossRef]
- Walters, J.P.; Liang, Z.; Shi, W.; Chaudhary, V. Wireless sensor network security: A survey. Secur. Distrib. Grid. Mob. Pervasive Comput. 2007, 1, 367. [Google Scholar]
- Chan, H.; Perrig, A.; Song, D. Random key predistribution schemes for sensor networks. In Proceedings of the 19th International Conference on Data Engineering (Cat. No. 03CH37405), Bangalore, India, 5–8 March 2003; pp. 197–213. [Google Scholar]
- Padmavathi, D.G.; Shanmugapriya, M.D. A Survey of Attacks, Security Mechanisms and Challenges in Wireless Sensor Networks. arXiv 2009, arXiv:0909.0576. [Google Scholar]
- Mohsen Nia, A.; Sur-Kolay, S.; Raghunathan, A.; Jha, N.K. Physiological Information Leakage: A New Frontier in Health Information Security. IEEE Trans. Emerg. Topics Comput. 2016, 4, 321–334. [Google Scholar] [CrossRef]
- Li, L. Study on security architecture in the Internet of Things. In Proceedings of the 2012 International Conference on Measurement, Information and Control, Harbin, China, 18–20 May 2012; pp. 374–377. [Google Scholar]
- Bhattasali, T.; Chaki, R.; Sanyal, S. Sleep Deprivation Attack Detection in Wireless Sensor Network. IJCA 2012, 40, 19–25. [Google Scholar] [CrossRef]
- Burmester, M.; Munilla, J.; Ortiz, A. Comments on “Unreconciled Collisions Uncover Cloning Attacks in Anonymous RFID Systems” . IEEE Trans. Inf. Forensic Secur. 2018, 13, 2929–2931. [Google Scholar] [CrossRef]
- Chen, X.; Liu, J.; Wang, X.; Zhang, X.; Wang, Y.; Chen, L. Combating Tag Cloning with COTS RFID Devices. In Proceedings of the 2018 15th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), Hong Kong, China, 11–13 June 2018; pp. 1–9. [Google Scholar]
- Juels, A.; Rivest, R.L.; Szydlo, M. The blocker tag: Selective blocking of RFID tags for consumer privacy. In Proceedings of the 10th ACM Conference on Computer and Communication Security (CCS 2003), Washington, DC, USA, 27–30 October 2003; p. 103. [Google Scholar]
- Weis, S.A.; Sarma, S.E.; Rivest, R.L.; Engels, D.W. Security and Privacy Aspects of Low-Cost Radio Frequency Identification Systems. In Security in Pervasive Computing; Hutter, D., Müller, G., Stephan, W., Ullmann, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2004; Volume 2802, pp. 201–212. ISBN 978-3-540-24646-6. [Google Scholar]
- Mukaddam, A.; Elhajj, I.; Kayssi, A.; Chehab, A. IP Spoofing Detection Using Modified Hop Count. In Proceedings of the 2014 IEEE 28th International Conference on Advanced Information Networking and Applications, Victoria, BC, Canada, 13–16 May 2014; pp. 512–516. [Google Scholar]
- Sopori, D.; Pawar, T.; Patil, M.; Ravindran, R. Internet of Things: Security Threats. IJARCET 2017, 6, 5. [Google Scholar]
- Mitrokotsa, A.; Rieback, M.R.; Tanenbaum, A.S. Classifying RFID attacks and defenses. Inf. Syst. Front. 2010, 12, 491–505. [Google Scholar] [CrossRef]
- Grover, A.; Berghel, H. A Survey of RFID Deployment and Security Issues. J. Inf. Proc. Syst. 2011, 7, 561–580. [Google Scholar] [CrossRef]
- Wallgren, L.; Raza, S.; Voigt, T. Routing Attacks and Countermeasures in the RPL-Based Internet of Things. Int. J. Distrib. Sens. Netw. 2013, 9, 794326. [Google Scholar] [CrossRef]
- Padhy, R.P.; Patra, M.R.; Satapathy, S.C. Cloud computing: Security issues and research challenges. IJCSITS 2011, 1, 136–146. [Google Scholar]
- Li, C.; Qin, Z.; Novak, E.; Li, Q. Securing SDN Infrastructure of IoT–Fog Networks from MitM Attacks. IEEE Internet Things J. 2017, 4, 1156–1164. [Google Scholar] [CrossRef]
- Sehrawat, H.; Singh, Y. Detecting Sinkhole Attack in Wireless Sensor Networks. IJESPR 2018, 47, 6. [Google Scholar]
- Parvathy, K. Security Attacks on Network Layer in Wireless Sensor Networks-An Overview. IJRASET 2017, 5, V. [Google Scholar]
- Ali, S.; Khan, M.A.; Ahmad, J.; Malik, A.W.; Rehman, A. Detection and prevention of Black Hole Attacks in IOT & WSN. In Proceedings of the 2018 Third International Conference on Fog and Mobile Edge Computing (FMEC), Barcelona, Spain, 23–26 April 2018; pp. 217–226. [Google Scholar]
- Hamid, M.A.; Rashid, M.O.; Hong, C.S. Routing Security in Sensor Network: Hello Flood Attack and Defense. IEEE ICNEWS 2006, 2, 2–4. [Google Scholar]
- Lokulwar, P.P.; Deshmukh, H.R. Threat analysis and attacks modelling in routing towards IoT. In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 10–11 February 2017; pp. 721–726. [Google Scholar]
- Karakehayov, Z. Using REWARD to detect team black-hole attacks in wireless sensor networks. In Proceedings of the Workshop Real-World Wireless Sensor Networks, Stockholm, Sweden, 20–21 June 2005; pp. 20–21. [Google Scholar]
- Revathi, B.; Geetha, D. A survey of cooperative black and gray hole attack in MANET. IJ Comput. Sci. Manag. Res. 2012, 1, 2. [Google Scholar]
- Lee, P.; Clark, A.; Bushnell, L.; Poovendran, R. A Passivity Framework for Modeling and Mitigating Wormhole Attacks on Networked Control Systems. IEEE Trans. Automat. Contr. 2014, 59, 3224–3237. [Google Scholar] [CrossRef]
- Newsome, J.; Shi, E.; Song, D.; Perrig, A. The Sybil attack in sensor networks: Analysis & defenses. In Proceedings of the Third International Symposium on Information Processing in Sensor Networks, Berkeley, CA, USA, 26–27 April 2004; pp. 259–268. [Google Scholar]
- Zhang, K.; Liang, X.; Lu, R.; Shen, X. Sybil Attacks and Their Defenses in the Internet of Things. IEEE Internet Things J. 2014, 1, 372–383. [Google Scholar] [CrossRef]
- Farooq, M.U.; Waseem, M.; Khairi, A.; Mazhar, S. A Critical Analysis on the Security Concerns of Internet of Things (IoT). IJCA 2015, 111, 1–6. [Google Scholar] [CrossRef]
- Singh, V.P.; Jain, S.; Singhai, J. Hello flood attack and its countermeasures in wireless sensor networks. IJ Comput. Sci. 2010, 7, 23. [Google Scholar]
- Kim, D.S.; Shin, T.-H.; Lee, B.; Park, J.S. Access Control and Authorization for Security of RFID Multi-domain Using SAML and XACML. In Computational Intelligence and Security; Wang, Y., Cheung, Y., Liu, H., Eds.; Springer: Berlin/Heidelberg, Germany, 2007; Volume 4456, pp. 887–893. ISBN 9783540743767. [Google Scholar]
- Uttarkar, R.; Kulkarni, R. Internet of Things: Architecture and Security. IJ Comput. Appl. 2014, 3, 4. [Google Scholar]
- Khoo, B. RFID as an Enabler of the Internet of Things: Issues of Security and Privacy. In Proceedings of the 2011 International Conference on Internet of Things and 4th International Conference on Cyber, Physical and Social Computing, Dalian, China, 19–22 October 2011; pp. 709–712. [Google Scholar]
- Thakur, B.S.; Chaudhary, S. Content sniffing attack detection in client and server side: A survey. IJACR 2013, 3, 7. [Google Scholar]
- Swamy, S.N.; Jadhav, D.; Kulkarni, N. Security threats in the application layer in IOT applications. In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Coimbatore, India, 10–11 February 2017; pp. 477–480. [Google Scholar]
- Javed, M.A.; Ben Hamida, E. Adaptive security mechanisms for safety applications in Internet of Vehicles. In Proceedings of the 2016 IEEE 12th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), New York, NY, USA, 17–19 October 2016; pp. 1–6. [Google Scholar]
- Zheng, Z.; Jin, S.; Bettati, R.; Reddy, A.L.N. Securing cyber-physical systems with adaptive commensurate response. In Proceedings of the 2017 IEEE Conference on Communications and Network Security (CNS), Las Vegas, NV, USA, 9–11 October 2017; pp. 1–6. [Google Scholar]
- Ogunnaike, R.M.; Lagesse, B. Toward consumer-friendly security in smart environments. In Proceedings of the 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kona, HI, USA, 13–17 March 2017; pp. 612–617. [Google Scholar]
- Sun, G.; Chang, V.; Ramachandran, M.; Sun, Z.; Li, G.; Yu, H.; Liao, D. Efficient location privacy algorithm for Internet of Things (IoT) services and applications. J. Netw. Comput. Appl. 2017, 89, 3–13. [Google Scholar] [CrossRef]
- Koley, S.; Ghosal, P. Addressing Hardware Security Challenges in Internet of Things: Recent Trends and Possible Solutions. In Proceedings of the 2015 IEEE 12th International Conference on Ubiquitous Intelligence and Computing and 2015 IEEE 12th International Conference on Autonomic and Trusted Computing and 2015 IEEE 15th International Conference on Scalable Computing and Communications and Its Associated Workshops (UIC-ATC-ScalCom), Beijing, China, 10–14 August 2015; pp. 517–520. [Google Scholar]
- Lee, C.; Fumagalli, A. Internet of Things Security—Multilayered Method for End to End Data Communications Over Cellular Networks. In Proceedings of the 2019 IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019; pp. 24–28. [Google Scholar]
- Rudd, E.M.; Rozsa, A.; Günther, M.; Boult, T.E. A Survey of Stealth Malware Attacks, Mitigation Measures, and Steps Toward Autonomous Open World Solutions. IEEE Commun. Surv. Tutor. 2017, 19, 1145–1172. [Google Scholar] [CrossRef]
- Shah, S.A.; Simnani, S.S.; Banday, M.T. A Study of Security Attacks on Internet of Things and Its Possible Solutions. In Proceedings of the 2018 International Conference on Automation and Computational Engineering (ICACE), Great Noida, India, 3–5 October 2018; pp. 203–209. [Google Scholar]
- Asplund, M.; Nadjm-Tehrani, S. Attitudes and Perceptions of IoT Security in Critical Societal Services. IEEE Access 2016, 4, 2130–2138. [Google Scholar] [CrossRef]
- Spathoulas, G.; Karageorgopoulou, A. Security and Privacy in the Internet of Things Using Blockchain Technology. In Proceedings of the 2019 15th International Conference on Distributed Computing in Sensor Systems (DCOSS), Santorini Island, Greece, 20–31 May 2019; pp. 284–290. [Google Scholar]
- Narang, S.; Nalwa, T.; Choudhury, T.; Kashyap, N. An efficient method for security measurement in internet of things. In Proceedings of the 2018 International Conference on Communication, Computing and Internet of Things (IC3IoT 2018), Chennai, India, 15–17 February 2018; pp. 319–323. [Google Scholar]
- El Hajjar, A. Securing the Internet of Things Devices Using Pre-Distributed Keys. In Proceedings of the 2016 IEEE International Conference on Cloud Engineering Workshop (IC2EW), Berlin, Germany, 4–8 April 2016; pp. 198–200. [Google Scholar]
- Banerjee, S.; Odelu, V.; Das, A.K.; Srinivas, J.; Kumar, N.; Chattopadhyay, S.; Choo, K.-K.R. A Provably Secure and Lightweight Anonymous User Authenticated Session Key Exchange Scheme for Internet of Things Deployment. IEEE Internet Things J. 2019, 6, 8739–8752. [Google Scholar] [CrossRef]
- Negalign, W.H.; Xiong, H.; Assefa, A.A.; Gemechu, A.Y.; Geresu, D.M. Outsourced Attribute-Based Signcryption in the Cloud Computing. In Proceedings of the 2018 15th International Computer Conference on Wavelet Active Media Technology and Information Processing (ICCWAMTIP), Chengdu, China, 14–18 December 2018; pp. 40–44. [Google Scholar]
- Muthavhine, K.D.; Sumbwanyambe, M. An analysis and a comparative study of cryptographic algorithms used on the Internet of Things (IoT) based on avalanche effect. In Proceedings of the 2018 International Conference on Information and Communications Technology (ICOIACT), Yogyakarta, Indonesia, 6–7 March 2018; pp. 114–119. [Google Scholar]
- Khan, Z.A.; Herrmann, P. A Trust Based Distributed Intrusion Detection Mechanism for Internet of Things. In Proceedings of the 2017 IEEE 31st International Conference on Advanced Information Networking and Applications (AINA), Taipei, China, 27–29 March 2017; pp. 1169–1176. [Google Scholar]
- Pu, C.; Carpenter, L. Digital Signature Based Countermeasure Against Puppet Attack in the Internet of Things. In Proceedings of the 2019 IEEE 18th International Symposium on Network Computing and Applications (NCA), Cambridge, UK, 25–28 September 2019; pp. 1–4. [Google Scholar]
- Gupta, N.; Naik, V.; Sengupta, S. A firewall for Internet of Things. In Proceedings of the 2017 9th International Conference on Communication Systems and Networks (COMSNETS), Bengaluru, India, 4–8 January 2017; pp. 411–412. [Google Scholar]
- Liu, C.; Zhang, Y.; Li, Z.; Zhang, J.; Qin, H.; Zeng, J. Dynamic Defense Architecture for the Security of the Internet of Things. In Proceedings of the 2015 11th International Conference on Computational Intelligence and Security (CIS), Shenzhen, China, 19–20 December 2015; pp. 390–393. [Google Scholar]
- Anthi, E.; Williams, L.; Burnap, P. Pulse: An adaptive intrusion detection for the Internet of Things. In Proceedings of the Living in the Internet of Things: Cybersecurity of the IoT-2018, London, UK, 28–29 March 2018; pp. 1–4. [Google Scholar]
- Surnin, O.; Hussain, F.; Hussain, R.; Ostrovskaya, S.; Polovinkin, A.; Lee, J.; Fernando, X. Probabilistic Estimation of Honeypot Detection in Internet of Things Environment. In Proceedings of the 2019 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 17–20 February 2019; pp. 191–196. [Google Scholar]
- Liu, Y.; Kuang, Y.; Xiao, Y.; Xu, G. SDN-Based Data Transfer Security for Internet of Things. IEEE Internet Things J. 2018, 5, 257–268. [Google Scholar] [CrossRef]
- Bhattarai, S.; Wang, Y. End-to-End Trust and Security for Internet of Things Applications. Computer 2018, 51, 20–27. [Google Scholar] [CrossRef]
- Li, D.-Y.; Xie, S.-D.; Chen, R.-J.; Tan, H.-Z. Design of Internet of Things System for Library Materials Management using UHF RFID. In Proceedings of the 2016 IEEE International Conference on RFID Technology and Applications (RFID-TA), Shunde, China, 21–23 September 2016; pp. 44–48. [Google Scholar]
- Zhang, P.; Nagarajan, S.G.; Nevat, I. Secure Location of Things (SLOT): Mitigating Localization Spoofing Attacks in the Internet of Things. IEEE Internet Things J. 2017, 4, 2199–2206. [Google Scholar] [CrossRef]
- Ahmad, M.; Farid, M.A.; Ahmed, S.; Saeed, K.; Asharf, M.; Akhtar, U. Impact and Detection of GPS Spoofing and Countermeasures against Spoofing. In Proceedings of the 2019 2nd International Conference on Computing, Mathematics and Engineering Technologies (iCoMET), Sukkur, Sindh, Pakistan, 30–31 January 2019; pp. 1–8. [Google Scholar]
- Kaur, K. A Survey on Internet of Things—Architecture, Applications, and Future Trends. In Proceedings of the 2018 First International Conference on Secure Cyber Computing and Communication (ICSCCC), Jalandhar, India, 15–17 December 2018; pp. 581–583. [Google Scholar]
- Conoscenti, M.; Vetrò, A.; De Martin, J.C. Peer to Peer for Privacy and Decentralization in the Internet of Things. In Proceedings of the 2017 IEEE/ACM 39th International Conference on Software Engineering Companion (ICSE-C), Buenos Aires, Argentina, 20–28 May 2017; pp. 288–290. [Google Scholar]
- Urien, P. Blockchain IoT (BIoT): A New Direction for Solving Internet of Things Security and Trust Issues. In Proceedings of the 2018 3rd Cloudification of the Internet of Things (CIoT), Paris, France, 2–4 July 2018; pp. 1–4. [Google Scholar]
- IEEE Draft Standard for an Architectural Framework for the Internet of Things (IoT). IEEE P2413/D0.4.5, December 2018, 1–264. Available online: https://standards.ieee.org/standard/2413-2019.html#Standard (accessed on 28 May 2020).
- Hassan, Q.F. On Standardizing the Internet of Things and Its Applications. In Internet of Things A to Z: Technologies and Applications; IEEE: Piscataway, NJ, USA, 2018; pp. 191–218. [Google Scholar]
- Sahni, N.; Bose, J.; Das, K. Web APIs for Internet of Things. In Proceedings of the 2018 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Bangalore, India, 19–22 September 2018; pp. 2175–2181. [Google Scholar]
- Gomez, C.; Arcia-Moret, A.; Crowcroft, J. TCP in the Internet of Things: From Ostracism to Prominence. IEEE Internet Comput. 2018, 22, 29–41. [Google Scholar] [CrossRef]
- Chopra, K.; Gupta, K.; Lambora, A. Future Internet: The Internet of Things-A Literature Review. In Proceedings of the 2019 International Conference on Machine Learning, Big Data, Cloud and Parallel Computing (COMITCon), Faridabad, India, 14–16 February 2019; pp. 135–139. [Google Scholar]
- Celia, L.; Cungang, Y. (WIP) Authenticated Key Management Protocols for Internet of Things. In Proceedings of the 2018 IEEE International Congress on Internet of Things (ICIOT), Seattle, WA, USA, 25–30 June 2018; pp. 126–129. [Google Scholar]
- Shahzad, M.; Singh, M.P. Continuous Authentication and Authorization for the Internet of Things. IEEE Internet Comput. 2017, 21, 86–90. [Google Scholar] [CrossRef]
- Wei, X.; Wu, L. A New Proposed Sensor Cloud Architecture Based on Fog Computing for Internet of Things. In Proceedings of the 2019 International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Piscataway, NJ, USA, 14–17 July 2019. [Google Scholar]
- Zhu, X.; Badr, Y. Fog Computing Security Architecture for the Internet of Things Using Blockchain-Based Social Networks. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018. [Google Scholar]
- Popovic, I.T.; Rakic, A.Z. The Fog-Based Framework for Design of Real-Time Control Systems in Internet of Things Environment. In Proceedings of the 2018 International Symposium on Industrial Electronics (INDEL), Banja Luka, Bosnia and Herzegovina, 1–3 November 2018. [Google Scholar]
- Olaniyan, R.; Maheswaran, M. Multipoint Synchronization for Fog-Controlled Internet of Things. IEEE Internet Things J. 2019, 6, 9656–9667. [Google Scholar] [CrossRef]
- Ziegler, S. Considerations on IPv6 scalability for the Internet of Things—Towards an intergalactic Internet. In Proceedings of the 2017 Global Internet of Things Summit (GIoTS), Geneva, Switzerland, 6–9 June 2017; pp. 1–4. [Google Scholar]
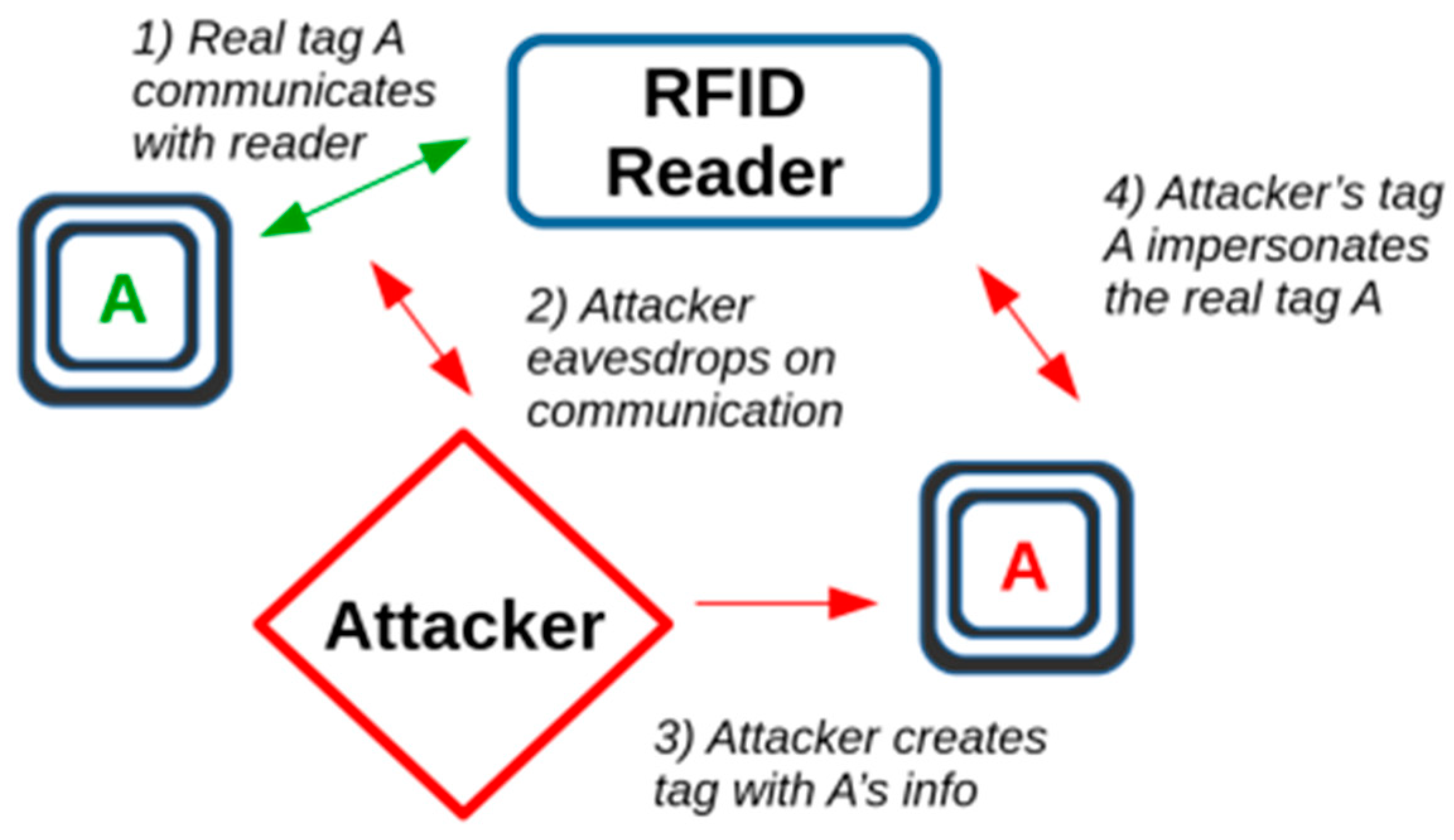

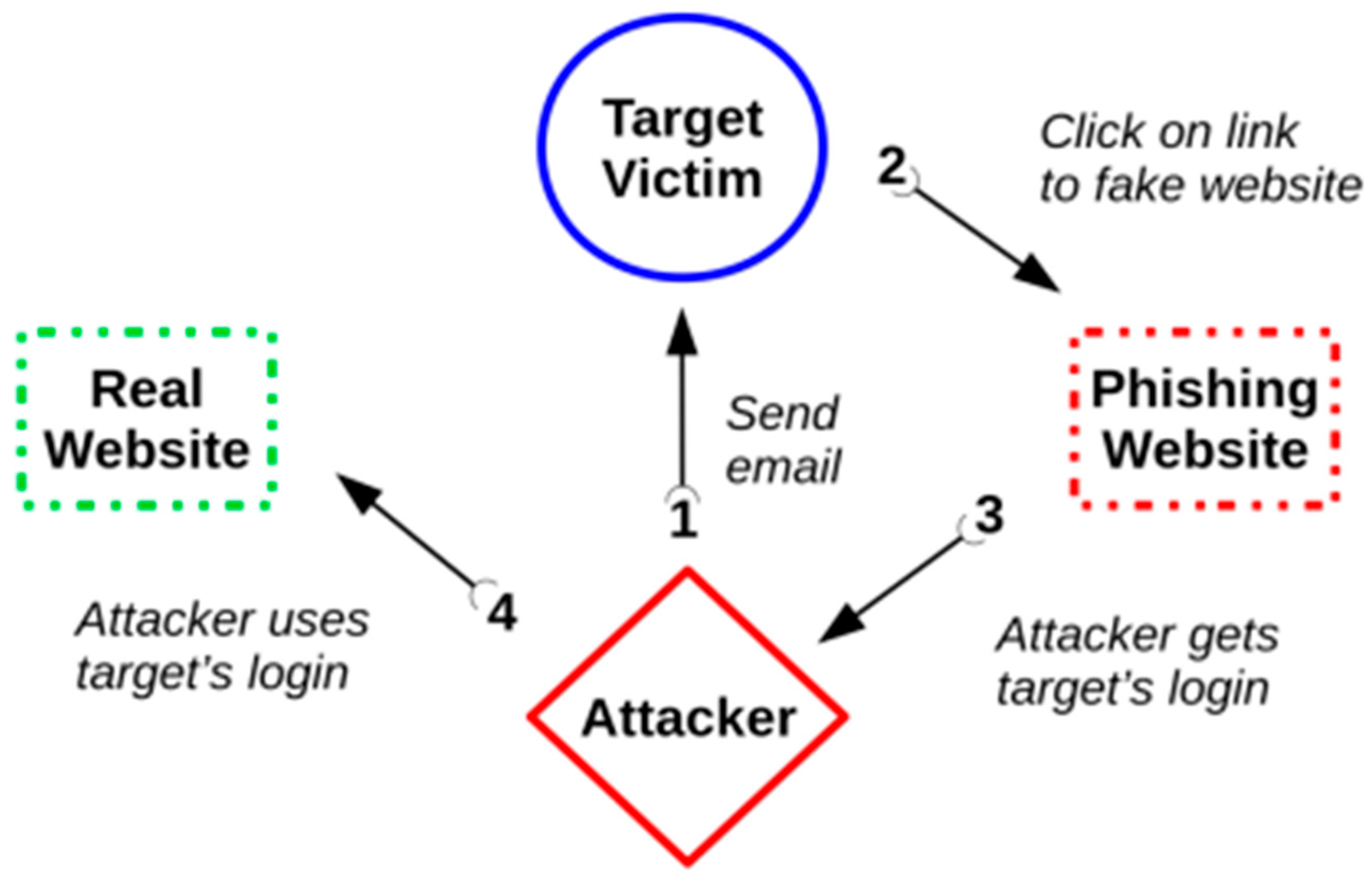
| Device Type | Vulnerability Possible Exploits/Attacks |
|---|---|
| Cars | Chrysler car company had to recall 1.4 million vehicles after researchers proofed that attackers are able take control of the vehicle remotely |
| Smart home devices | Millions of homes are affected. Multiple vulnerabilities in a lot of commercially smart home devices such as smart door lock that could be hacked and opened remotely without using a password |
| Medical devices | Multiple vulnerabilities in medical devices such as insulin-pumps, Xray and CT-scanners devices, and implantable sensors |
| Smart TVs | Millions of Internet-connected televisions are vulnerable multiple attacks such as click fraud, data theft, and ransomware |
| Embedded devices | Everyday devices such as routers, watches, cameras, and smart phones using the same hard embedded code SSH and HTTPS server certificates left by manufactures leaving other millions of devices vulnerable to attacks such as interception and interruption |
| Layer/Function | Privacy Concerns |
|---|---|
| Application |
|
| |
| Transportation/Network |
|
| |
| Perception/ Sensor |
|
| Phase | Layer | Process |
|---|---|---|
| Phase 1 | Perception layer | Data perception and collection from the sensors |
| Phase 2 | Perception layer | Data storage on sensors |
| Phase 3 | Perception layer | Data processing on the sensors |
| Phase 4 | Transporting/Network layer | Data transmission |
| Phase 5 | Application layer | Data delivery, data presentation for end users, output devices |
| Layer | Protocols |
|---|---|
| Application and Message Layer | JSON, HTTP, RESTFUL, XML, FTP, Etc… |
| Network and Transport Layer | IPv6, TLS, 6LoWPAN, 6lo, TCP/UDP, Etc… |
| Datalink Layer | Bluetooth, ZigBee, WiFi, 4G/5G/LTE, IEEE 802.15.4e, Etc… |
| Functionality | Description |
|---|---|
| Upgrading | Updates to IoT-device (thing) firmware |
| Pairing | The process of connecting a controller, e.g., a mobile app, to the IoT thing. |
| Binding | Configuring the thing through the controller once pairing is done. |
| Local Authentication | Takes place when the controller resides on the same local network as the thing. Thing may provide an open port for the controller to connect to. Thing should authenticate user to allow for further actions from user. |
| Local Control | Ability to locally control thing through sending user-commands after authentication. |
| Remote Authentication | When the controller is away from the home network, it may not be able to connect directly to the thing because the latter is probably behind NAT. In this case, it must use a cloud service to authenticate. |
| Remote Control | Ability to control thing while away from the home network through the cloud. |
| Relay | Cloud is to relay the authentication and control messages between the thing and controller. Cloud may need to authenticate both thing and controller using its own authentication servers. |
| Big Data Analytics | The cloud may collect data from the thing, the user, and may also contact other clouds for data on other things. |
| Sensing and Notification | A thing may report on environment or actions, e.g., room temperatures or number of login attempts. |
| Security Framework | Policies, Standards, Process Adaption and Secure IOT Components | Security | Service Level Agreement | Applicability |
|---|---|---|---|---|
| Cisco Security Framework | Authentication | Threat Detection, | X | Infrastructure |
| Authorization | Anomaly Detection, | Framework | ||
| Network Enforced Policy | Predictive Analysis | |||
| Secure Analytics: | contextual- Awareness | |||
| Risk and Assurance | ||||
| Floodgate Security Framework | Software APIs to enable secure boot | Runtime Integrity Validation (RTIV) | Identify the threats and Floodgate firewall IDS Supp | Best Fit in |
| Hardware root of trust integration | Application Guarding APIs Internet security (DDOS) | Compliance support Security Evaluation | Infrastructure | |
| Software based vTPM for legacy systems | Security | |||
| Integration for secure remote firmware updates. | Framework | |||
| Constrained Application Protocol Framework (COAP) | IoT Smart Objects | X | X | Best Fit in |
| Protocol suites. | Application | |||
| CoAP, UDP, 6LoWPAN | Security | |||
| IEEE 802.15.4e provide the easy mapping to HTTP at the gateway | Framework | |||
| Object Security Framework for IoT (OSCAR) | Technological Trends and Design Goals | Access Control | Analyzed and extracted risks of utilizing cloud computing by using the Risk Breakdown | Based on Object Security Approaches |
| Producer-Consumer Model | Confidentiality | Structure (RBS) method. | Best Fit in application Security | |
| Fitting the Concept with the REST Architecture and CoAP Object Security Approaches | Authenticity | |||
| Availability |
| Sample Attacks | Potential Impact on Confidentiality of User Information | Potential Impact on Integrity of User Information | Potential Impact on Availability of User Information | |||
|---|---|---|---|---|---|---|
| Smart Home Heating Control | Smart Health Monitor | Smart Home Heating Control | Smart Health Monitor | Smart Home Heating Control | Smart Health Monitor | |
| RFID tag tracking | Low/Mod | Low/Mod | Low | Low/Mod | Low | Low/Mod |
| Denial of Service (DoS) | Low | Low/Mod | Low | Low | Low | Mod/High |
| Man in the Middle | Low/Mod | Low/Mod | Low | Mod/High | Low | Mod/High |
| Traffic analysis | Low/Mod | Low/Mod | Low | Low | Low | Low/Mod |
| Phishing | Low/Mod | Low/Mod | Low | Low/Mod | Low | Low |
| Malicious virus/worm | Low/Mod | Low/Mod | Low | Low/Mod | Low | Mod/High |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Obaidat, M.A.; Obeidat, S.; Holst, J.; Al Hayajneh, A.; Brown, J. A Comprehensive and Systematic Survey on the Internet of Things: Security and Privacy Challenges, Security Frameworks, Enabling Technologies, Threats, Vulnerabilities and Countermeasures. Computers 2020, 9, 44. https://doi.org/10.3390/computers9020044
Obaidat MA, Obeidat S, Holst J, Al Hayajneh A, Brown J. A Comprehensive and Systematic Survey on the Internet of Things: Security and Privacy Challenges, Security Frameworks, Enabling Technologies, Threats, Vulnerabilities and Countermeasures. Computers. 2020; 9(2):44. https://doi.org/10.3390/computers9020044
Chicago/Turabian StyleObaidat, Muath A., Suhaib Obeidat, Jennifer Holst, Abdullah Al Hayajneh, and Joseph Brown. 2020. "A Comprehensive and Systematic Survey on the Internet of Things: Security and Privacy Challenges, Security Frameworks, Enabling Technologies, Threats, Vulnerabilities and Countermeasures" Computers 9, no. 2: 44. https://doi.org/10.3390/computers9020044
APA StyleObaidat, M. A., Obeidat, S., Holst, J., Al Hayajneh, A., & Brown, J. (2020). A Comprehensive and Systematic Survey on the Internet of Things: Security and Privacy Challenges, Security Frameworks, Enabling Technologies, Threats, Vulnerabilities and Countermeasures. Computers, 9(2), 44. https://doi.org/10.3390/computers9020044





