Specification and Verification in Integrated Model of Distributed Systems (IMDS)
Abstract
:1. Introduction
Overview of the Formalism
- communication duality: the system can be seen as cooperating servers in the client-server paradigm, or as distributed agents traveling through servers in a remote procedure call model, but each system is unified and can only be distributed to cooperating servers or traveling agents;
- locality of actions performed on the server, which depends only on the local state of the server in a distributed environment, and on messages pending locally;
- autonomy of decisions: server design determines which messages pending locally will be accepted first, i.e., no order predefined between pending messages is assumed;
- asynchrony of actions: received messages are pending and waiting for acceptance. If there is no pending message or none of pending messages may be accepted in a current state, the server waits for the appropriate message; on the other hand, pending messages wait for a proper server state;
- asynchrony of communication: each message is sent along a unidirectional asynchronous channel; the sender does not know when the message will reach the target server and when the reply may be expected (if the calculation provides for a response);
- variety of behavior features: servers communicate using messages and may fall into a communication deadlock; at the same time, agents flow through these messages, and their deadlock is observed over the resource; distributed termination is another way of processing discontinuation, and should be distinguished from deadlocks;
- total and partial features: there are total deadlocks/termination, but especially in a distributed environment, there may be situations in which a subset of system components falls into a deadlock or terminates successfully, while other processes continue their work; both total and partial deadlocks/termination should be possible to find;
- automated verification: the verification should not require any knowledge from the designer of temporal logics or model checking techniques.
2. Related Work
2.1. Asynchrony in Modeling of Distributed Systems
2.2. Deadlock and Termination Checking
3. Integrated Model of Distributed Systems
3.1. Overview
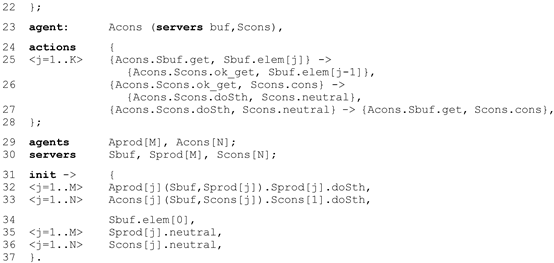
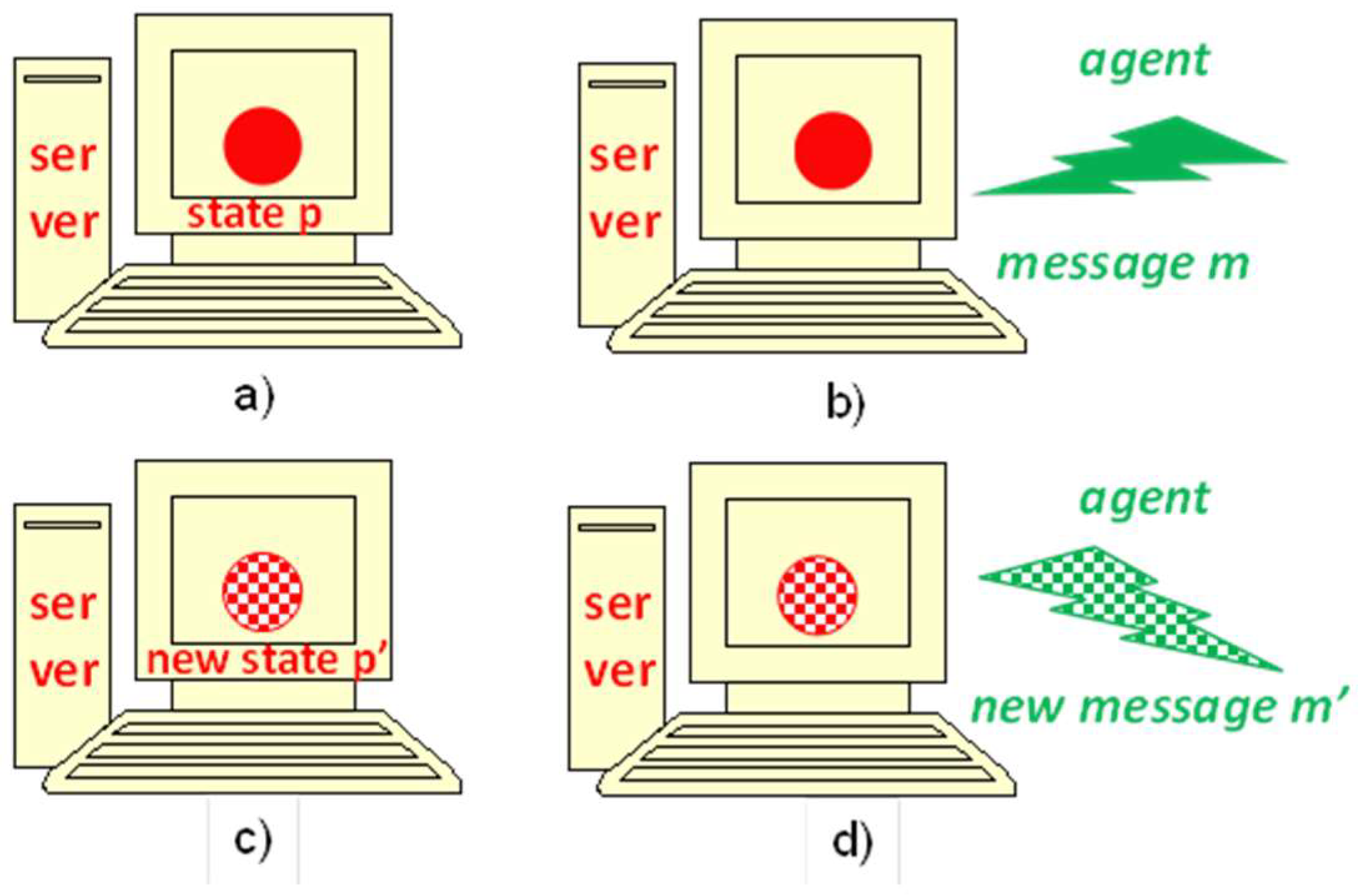
3.2. Basic IMDS Definition
- the pair (m,p) match;
- (m,p) is the input pair; (m’,p’) is the output pair;
- the state p is current; the message m is pending (we use also a term current message);
- p’ is the next state; m’ is the next message.
- P =
- {p_neutral, produce, c_neutral, consume, 0_elem, 1_elem, 2_elem},
- M =
- {p_doSth, put, ok_put, c_doSth, get, ok_get},
- Λ =
- {((p_doSth, p_neutral),(p_doSth, p_neutral)), ((p_doSth, p_neutral),(put, produce)), ((ok_put, produce),(p_doSth, p_neutral)), ((put, 0_elem),(ok_put, 1_elem)), ((put, 1_elem),(ok_put, 2_elem)), ((c_doSth, c_neutral),(c_doSth, c_neutral)), ((c_doSth, c_neutral),(get, consume)), ((ok_get, consume),(c_doSth, c_neutral)), ((get, 1_elem),(ok_get, 0_elem)), ((get, 2_elem),(ok_get, 1_elem))},
- Pini =
- {p_neutral, c_neutral, 0_elem},
- Mini =
- {p_doSth, c_doSth}.
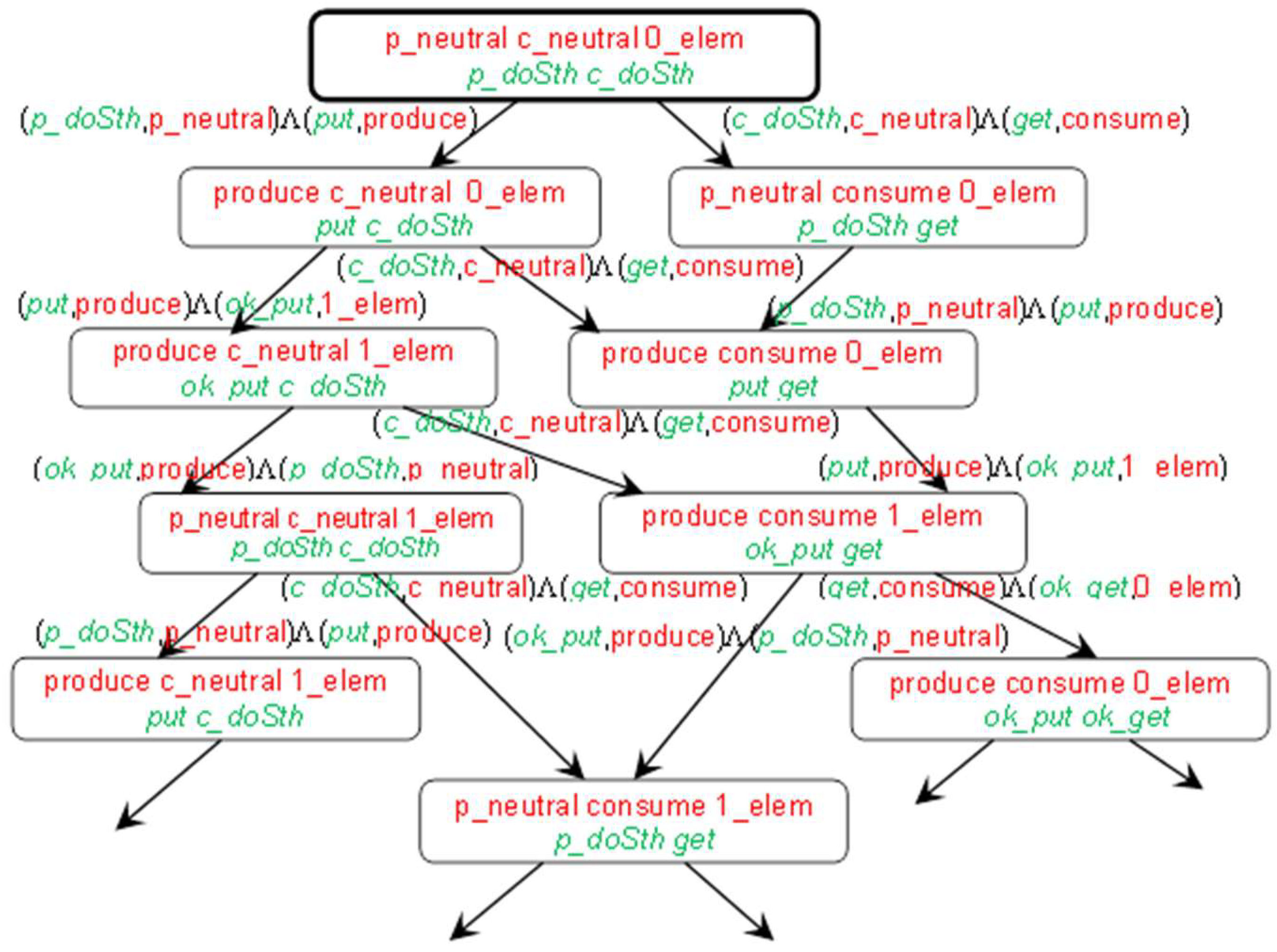
3.3. IMDS System Behavior
- N is a set nodes, N = {n0,n1,…};
- n0 is the root, n0 ∈ N, n0= Tini;
- W is the set of directed labeled transitions, W ⊂ N × Λ × N, W = {(Tinp(λ),λ,Tout(λ))|λ∈Λ}.
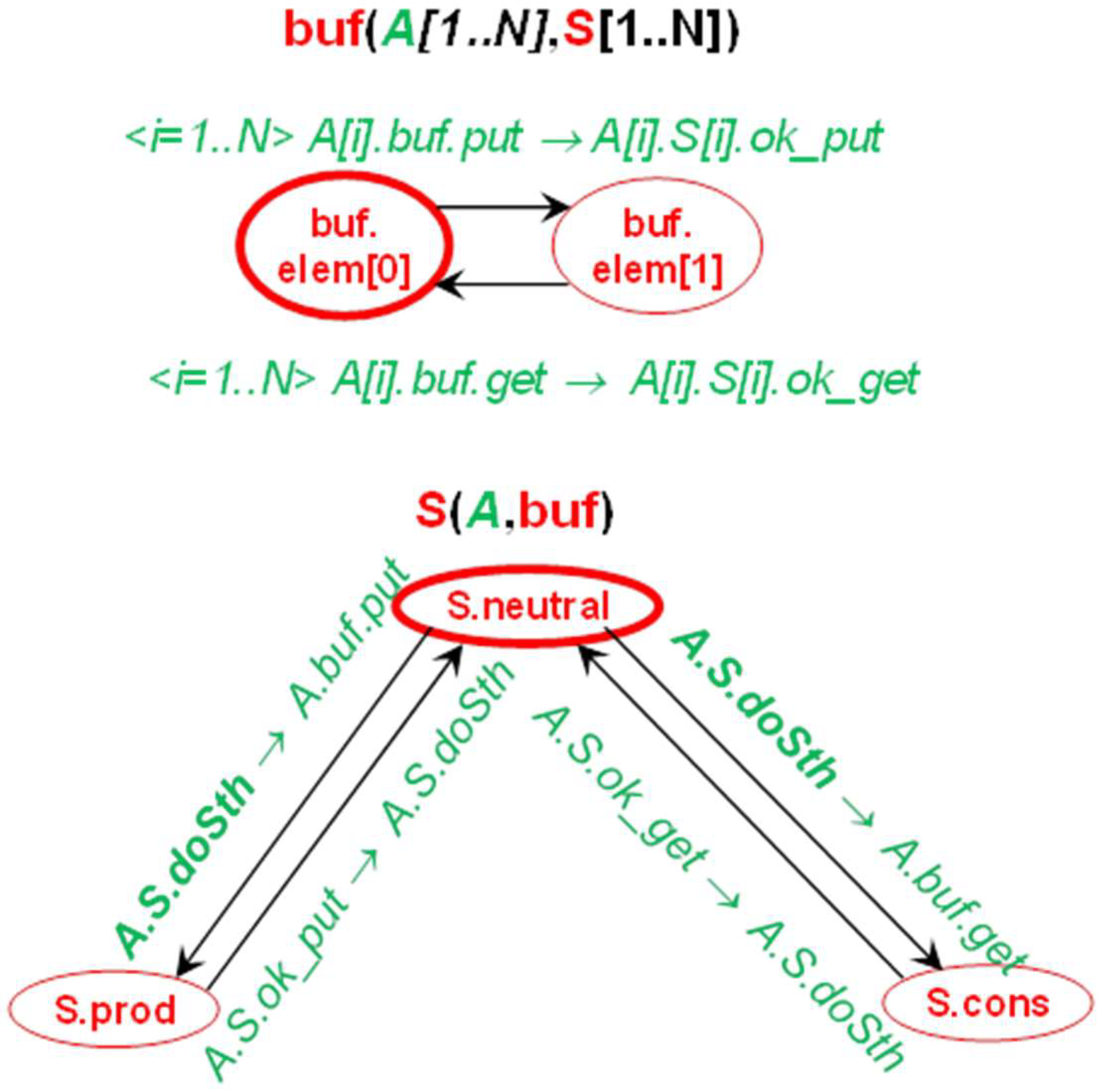
3.4. IMDS Processes
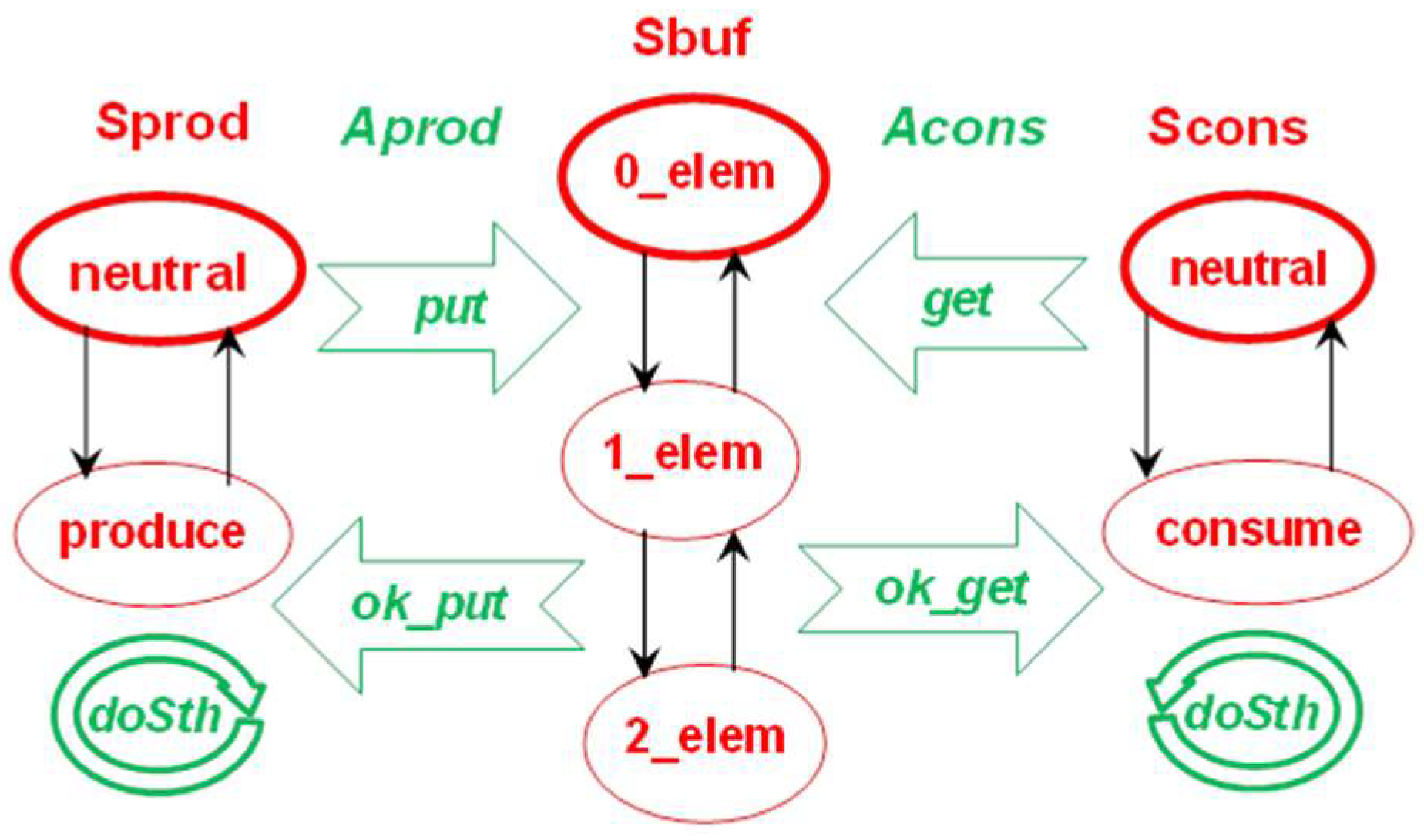
- S = {Sprod, Scons, Sbuf},
- A = {Aprod, Acons},
- P(Sprod) = {p_neutral, produce}, P(Scons) = {c_neutral, consume}, P(Sbuf) = {0_elem, 1_elem, 2_elem},
- M(Aprod) = {p_doSth, put, ok_put}, M(Acons) = {c_doSth, get, ok_get},
- M(Sprod) = {p_doSth, ok_put}, M(Scons) = {c_doSth, ok_get}, M(Sbuf) = {put, get}.
- action sequences come from their definition;
- asynchrony comes from such a feature that always the state of the server is waiting for a message, or a message pending at the server is waiting for the matching state of this server (and, at the same time, the state is waiting for a matching message).
- A process can have more than one starting node if more than one action can appear first in the process.
- The process may be a branched graph if there is non-determinism in the action set: it may be possible to perform multiple actions for a given state or for a given message.
- Some paths in the graph may be finite if there is an action that terminates the agent’s operation, or if no action is defined for a given state / message (this is not considered a process termination).
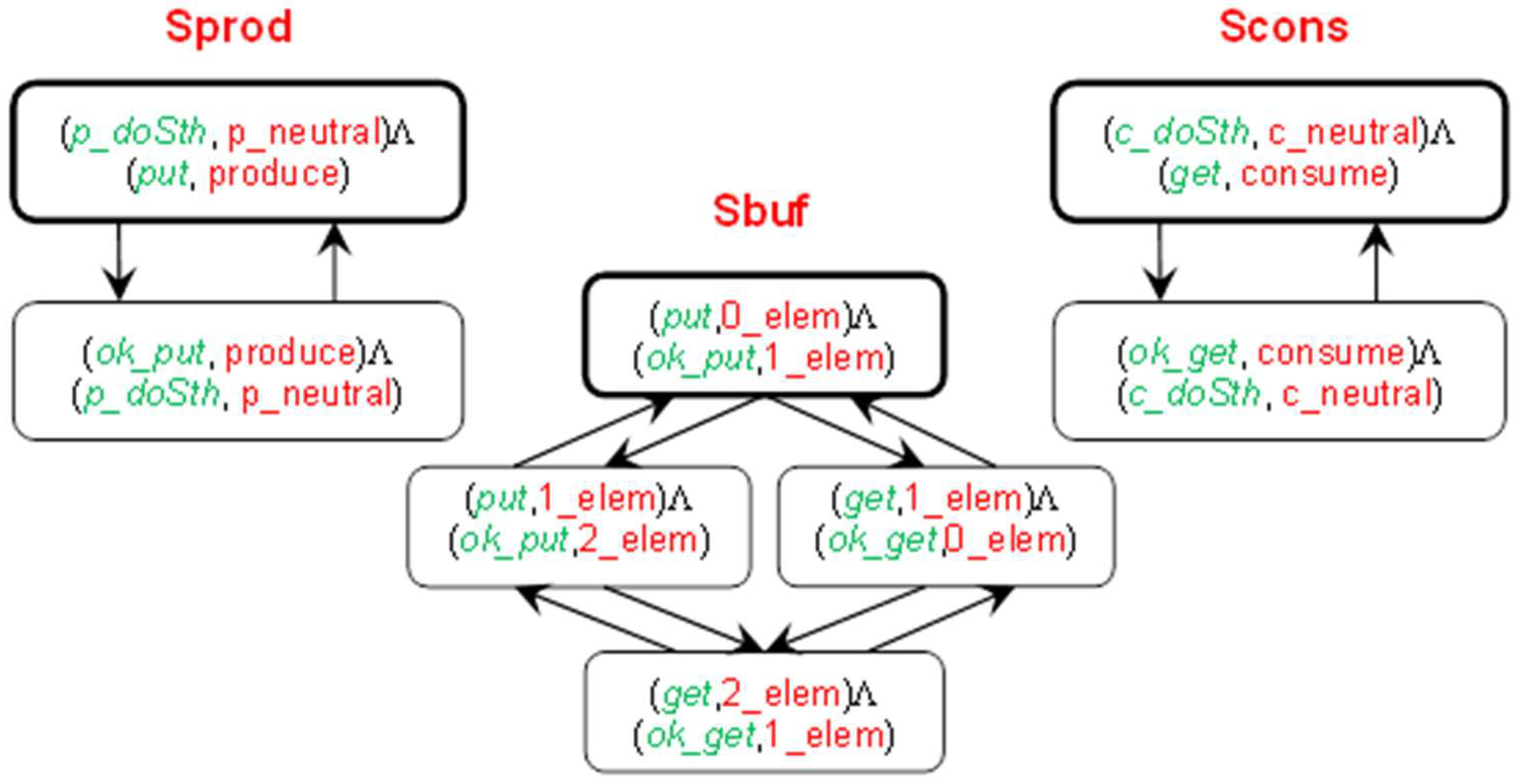
3.5. Views of a Distributed System
- B(Sprod) = {(p_doSth, p_neutral)Λ(p_doSth, p_neutral), (p_doSth, p_neutral)Λ(put, produce), (ok_put, produce)Λ(p_doSth, p_neutral)},
- B(Scons) = {(c_doSth, c_neutral)Λ(p_doSth, p_neutral), (c_doSth, c_neutral)Λ(get, consume), (ok_get, consume)Λ(c_doSth, c_neutral)},
- B(Sbuf) = {(put, 0_elem)Λ(ok_put, 1_elem), (put, 1_elem)Λ(ok_put, 2_elem), (get, 1_elem)Λ(ok_get, 0_elem), (get, 2_elem)Λ(ok_get, 1_elem)},
- C(Aprod) = {(p_doSth, p_neutral)Λ(p_doSth, p_neutral), (p_doSth, p_neutral)Λ(put, produce), (put, 0_elem)Λ(ok_put, 1_elem), (put, 1_elem)Λ(ok_put, 2_elem), (ok_put, produce)Λ(p_doSth, p_neutral)},
- C(Acons) = {(c_doSth, c_neutral)Λ(c_doSth, c_neutral), (c_doSth, c_neutral)Λ(get, consume), (get, 1_elem)Λ(ok_get, 0_elem), (get, 2_elem)Λ(ok_get, 1_elem), (ok_get, consume)Λ(c_doSth, c_neutral)}.
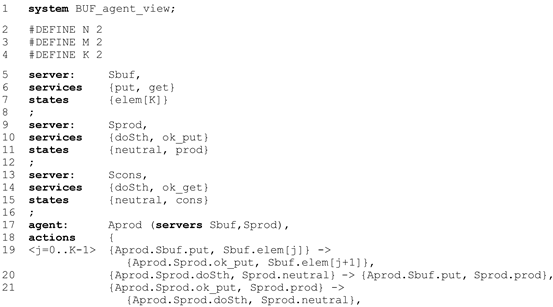
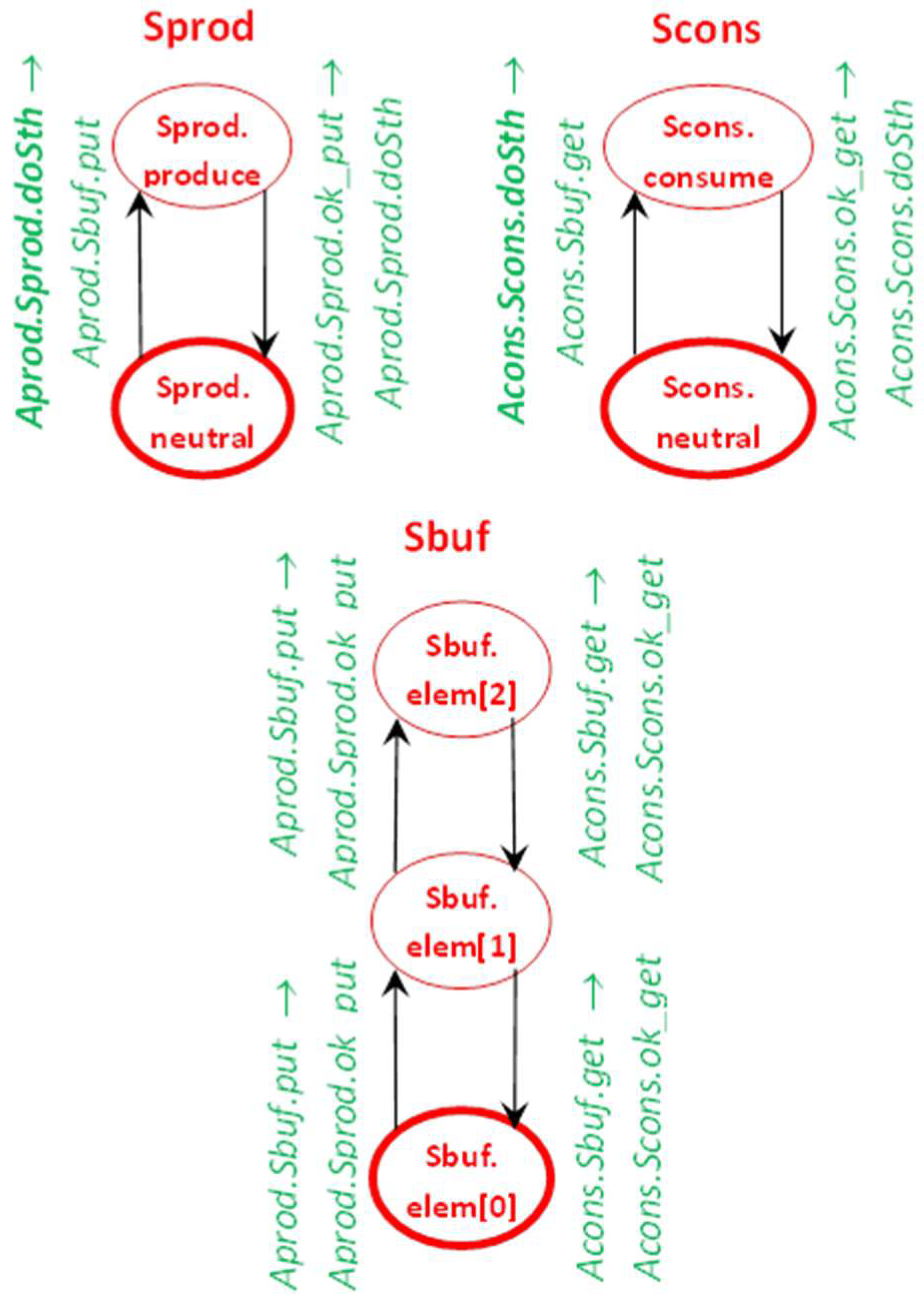
3.6. IMDS as a Programming Language
- every server is depicted as separate automaton-like graph of Mealy type [56],
- nodes of an automaton are the server’s states,
- initial node (initial state) is surrounded by bold ellipse,
- initial messages of the agents are in bold font,
- transitions are actions,
- transitions are labeled by input message→output message.


- communication protocols,
- train scheduling,
- distributed production cell,
- automatic vehicles guidance,
- patrol robots swarm,
- distributed systems for access control,
- business processes.
3.7. Deadlock and Termination
- on the server there is a matching pair (message, state)—the action is prepared; the process runs;
- there are pending messages or not, but there is no matching pair on the server; a matching pair can happen in the future, so the server process waits;
- there are no pending messages, and in the future, no message will arrive at the server; the process is idle;
- there are pending messages in the server, but there is no matching pair, and such a pair cannot occur on the server in the future; the process is deadlocked.
- the agent message is pending at the server and it matches the current state of this server—the action is prepared; the agent runs;
- the agent message is pending at a server but it does not match the current state of this server; a matching pair containing this message may occur in the future; the agent is waiting;
- the agent message is pending at the server and it will never match any state of this server—neither now nor in the future; the process is deadlocked;
- the agent-terminating action was executed and the agent’s message is not present (and will not occur in the future)—the process is terminated.
4. Model Checking of the IMDS Specifications in the Dedan Environment
- Ds—true in all configurations where at least one message is pending at the server s,
- Es—true in all configurations where at least one action is prepared in the server s.
- Da—true in all configurations in which agent a message is pending,
- Ea—true in all configurations in which the action with agent a message on input is prepared,
- Fa—true in all configurations where the terminating action (with the agent a message on input) is prepared.
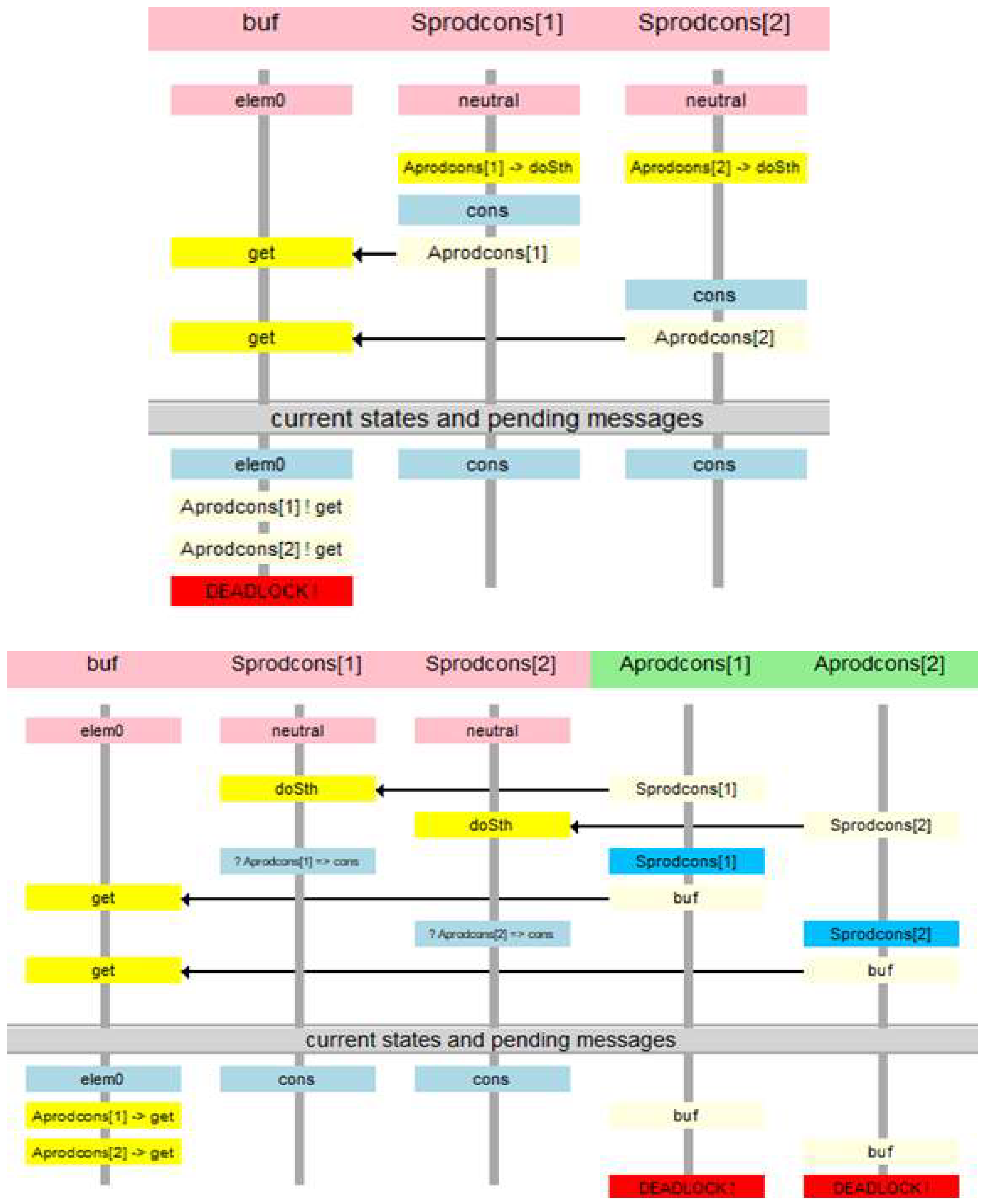
5. Example Verification
6. Conclusions
- Communication duality: any system can be decomposed into server processes communicating through messages, or into agent processes communicating via servers’ states.
- Locality: each action on the server is performed based on the current state of this server and the set of messages pending at this server. No external event (except messages received by the server) affects the behavior of the server.
- Autonomy: each server decides by itself which of the prepared actions will be executed and when. In other words, the servers decide autonomously whether and when communication will be accepted and what actions will result.
- Asynchrony: the server accepts the message when it is ready for it (its state matches the message); otherwise, the message is waiting; there is no synchrony in the model, i.e., no simultaneous activities of servers or agents.
- Asynchronous channels: the communication between the servers is unidirectional; the possible communication in the opposite direction has its own channel.
- Automated verification: the temporal formulas are used to locate communication deadlocks in individual server processes, resource deadlocks in agent processes, servers’ idleness, and agents termination.
- Reachability space reduction and symbolic representation.
- Checking for assertions expressed in terms of states and messages.
- Code mobility—equipping the agents with their own sets of actions, carried in their “backpacks”, parameterizing the behavior of individual agents. This will allow the modeling of agents with mobile code and avoiding many server types in the specification, differing slightly [73].
- Dynamic creation of processes—a state of a new server and/or a message of a new agent created in action [10], some problems with the calculation of the reachability space of such a system must first be solved. In order to be statically verified, the LTS of the Petri net corresponding to the IMDS system should be limited, e.g., restricting markings to a certain limit [74].
- Probabilistic automata to identify the probability deadlocks, if the alternative actions in system processes are equipped with probabilities [75].
- Non-exhaustive search for model checking large systems. The own algorithm for partial deadlock detection is elaborated, and the algorithm for timed systems is under development.
Funding
Acknowledgments
Conflicts of Interest
References
- Schaefer, I.; Hahnle, R. Formal Methods in Software Product Line Engineering. Computer 2011, 44, 82–85. [Google Scholar] [CrossRef]
- Mieścicki, J. The use of model checking and the COSMA environment in the design of reactive systems. Ann. UMCS Inform. 2006, 4, 244–253. [Google Scholar] [CrossRef]
- Mieścicki, J.; Baszun, M.; Daszczuk, W.B.; Czejdo, B. Verification of Concurrent Engineering Software Using CSM Models. In Proceedings of the 2nd World Conference on Integrated Design and Process Technology, Austin, TX, USA, 1–4 December 1996; pp. 322–330. [Google Scholar]
- Daszczuk, W.B. Evaluation of temporal formulas based on “Checking By Spheres”. In Proceedings of the Euromicro Symposium on Digital Systems Design, Warsaw, Poland, 4–6 September 2001; pp. 158–164. [Google Scholar] [CrossRef]
- Daszczuk, W.B.; Grabski, W.; Mieścicki, J.; Wytrębowicz, J. System modeling in the COSMA environment. In Proceedings of the Euromicro Symposium on Digital Systems Design, Warsaw, Poland, 4–6 September 2001; pp. 152–157. [Google Scholar] [CrossRef] [Green Version]
- Daszczuk, W.B.; Mieścicki, J.; Nowacki, M.; Wytrębowicz, J. System Level Specification and Verification Using Concurrent State Machines and COSMA Environment. In Proceedings of the 8th International Conference on Mixed Design of Integrated Circuits and Systems (MIXDES’01), Zakopane, Poland, 21–23 June 2001; pp. 525–532. [Google Scholar]
- Mieścicki, J.; Czejdo, B.; Daszczuk, W.B. Model Checking in the COSMA Environment as a Support for the Design of Pipelined Processing. In Proceedings of the European Congress on Computational Methods in Applied Sciences and Engineering (ECCOMAS 2004), Jyväskylä, Finland, 24–28 July 2004; pp. 24–28. [Google Scholar]
- Mieścicki, J.; Daszczuk, W.B. Behavioral and real-time verification of a pipeline in the COSMA environment. Ann. UMCS Inform. 2006, 4, 254–265. [Google Scholar] [CrossRef]
- Lee, G.M.; Crespi, N.; Choi, J.K.; Boussard, M. Internet of Things. In Evolution of Telecommunication Services; LNCS 7768; Springer: Berlin/Heidelberg, Germany, 2013; pp. 257–282. [Google Scholar]
- Chrobot, S.; Daszczuk, W.B. Communication Dualism in Distributed Systems with Petri Net Interpretation. Theor. Appl. Inform. 2006, 18, 261–278. [Google Scholar]
- Daszczuk, W.B. Communication and Resource Deadlock Analysis using IMDS Formalism and Model Checking. Comput. J. 2017, 60, 729–750. [Google Scholar] [CrossRef]
- Reniers, M.A.; Willemse, T.A.C. Folk Theorems on the Correspondence between State-Based and Event-Based Systems. In Proceedings of the 37th Conference on Current Trends in Theory and Practice of Computer Science, Nový Smokovec, Slovakia, 22–28 January 2011; pp. 494–505. [Google Scholar] [CrossRef]
- Jia, W.; Zhou, W. Distributed Network Systems: From Concepts to Implementations; Springer: New York, NY, USA, 2005. [Google Scholar]
- Kessler, C.; Keller, J. Models for Parallel Computing: Review and Perspectives. In PARS-Mitteilungen; Gesellschaft für Informatik: Bonn, Germany, 2007; pp. 13–29. [Google Scholar]
- Milner, R. Calculi for synchrony and asynchrony. Theor. Comput. Sci. 1983, 25, 267–310. [Google Scholar] [CrossRef]
- Savoiu, N.; Shukla, S.K.; Gupta, R.K. Automated concurrency re-assignment in high level system models for efficient system-level simulation. In Proceedings of the 2002 Design, Automation and Test in Europe Conference and Exhibition, Paris, France, 4–8 March 2002; pp. 875–881. [Google Scholar] [CrossRef] [Green Version]
- van Glabbeek, R.; Goltz, U.; Schicke, J.-W. On Synchronous and Asynchronous Interaction in Distributed Systems. In Proceedings of the 33rd International Symposium (MFCS 2008), Toruń, Poland, 25–29 August 2008; pp. 16–35. [Google Scholar]
- Rosa, N.S.; Cunha, P.R.F. A Software Architecture-Based Approach for Formalising Middleware Behaviour. Electron. Notes Theor. Comput. Sci. 2004, 108, 39–51. [Google Scholar] [CrossRef]
- Holzmann, G.J. Tutorial: Proving properties of concurrent systems with SPIN. In Proceedings of the 6th International Conference on Concurrency Theory (CONCUR’95), Philadelphia, PA, USA, 21–24 August 1995; pp. 453–455. [Google Scholar] [CrossRef]
- Clarke, E.M.; Grumberg, O.; Peled, D. Model Checking; MIT Press: Cambridge, MA, USA, 1999; ISBN 0-262-03270-8. [Google Scholar]
- Zielonka, W. Notes on finite asynchronous automata. RAIRO Theor. Inform. Appl. Inform. Théor. Appl. 1987, 21, 99–135. [Google Scholar] [CrossRef]
- Alur, R.; Dill, D.L. A theory of timed automata. Theor. Comput. Sci. 1994, 126, 183–235. [Google Scholar] [CrossRef]
- Hoare, C.A.R. Communicating sequential processes. Commun. ACM 1978, 21, 666–677. [Google Scholar] [CrossRef]
- Behrmann, G.; David, A.; Larsen, K.G.; Pettersson, P.; Yi, W. Developing UPPAAL over 15 years. Softw. Pract. Exp. 2011, 41, 133–142. [Google Scholar] [CrossRef]
- Milner, R. A Calculus of Communicating Systems; Springer: Berlin/Heidelberg, Germany, 1984; ISBN 0387102353. [Google Scholar]
- May, D. OCCAM. ACM SIGPLAN Not. 1983, 18, 69–79. [Google Scholar] [CrossRef]
- Johnsen, E.B.; Blanchette, J.C.; Kyas, M.; Owe, O. Intra-Object versus Inter-Object: Concurrency and Reasoning in Creol. Electron. Notes Theor. Comput. Sci. 2009, 243, 89–103. [Google Scholar] [CrossRef]
- Bollig, B.; Leucker, M. Message-Passing Automata Are Expressively Equivalent to EMSO Logic. In Proceedings of the 15th International Conference CONCUR 2004—Concurrency Theory, London, UK, 31 August—3 September 2004; pp. 146–160. [Google Scholar] [CrossRef]
- Balan, M.S. Serializing the Parallelism in Parallel Communicating Pushdown Automata Systems. Electron. Proc. Theor. Comput. Sci. 2009, 3, 59–68. [Google Scholar] [CrossRef] [Green Version]
- Sandhu, K.K. Specification and description language (SDL). In IEE Tutorial Colloquium on Formal Methods and Notations Applicable to Telecommunications; IET: London, UK, 1992; pp. 3/1–3/4. [Google Scholar]
- Broy, M.; Fox, J.; Hölzl, F.; Koss, D.; Kuhrmann, M.; Meisinger, M.; Penzenstadler, B.; Rittmann, S.; Schätz, B.; Spichkova, M.; et al. Service-Oriented Modeling of CoCoME with Focus and AutoFocus. In The Common Component Modeling Example; Shaker: Berlin/Heidelberg, Germany, 2007; pp. 177–206. [Google Scholar]
- Holzmann, G.J. The model checker SPIN. IEEE Trans. Softw. Eng. 1997, 23, 279–295. [Google Scholar] [CrossRef]
- Liu, Y.; Jiang, J. Analysis and Modeling for Interaction with Mobility Based on Pi-Calculus. In Proceedings of the 2016 IEEE 14th International Conference on Dependable, Autonomic and Secure Computing, 14th International Conference on Pervasive Intelligence and Computing and 2nd International Conference on Big Data Intelligence and Computing and Cyber Science and Technology Congress (DASC/PiCom/DataCom/CyberSciTech), Auckland, New Zealand, 8–12 August 2016; pp. 141–146. [Google Scholar] [CrossRef]
- Moy, Y.; Ledinot, E.; Delseny, H.; Wiels, V.; Monate, B. Testing or Formal Verification: DO-178C Alternatives and Industrial Experience. IEEE Softw. 2013, 30, 50–57. [Google Scholar] [CrossRef]
- Hirshorn, S.R. NASA Systems Engineering Handbook; NASA: Washington, DC, USA, 2007; ISBN 978-0-16-079747-7. [Google Scholar]
- Miller, S.P.; Whalen, M.W.; Cofer, D.D. Software model checking takes off. Commun. ACM 2010, 53, 58–64. [Google Scholar] [CrossRef] [Green Version]
- Fahland, D.; Favre, C.; Koehler, J.; Lohmann, N.; Völzer, H.; Wolf, K. Analysis on demand: Instantaneous soundness checking of industrial business process models. Data Knowl. Eng. 2011, 70, 448–466. [Google Scholar] [CrossRef] [Green Version]
- Huang, S.-T. Detecting termination of distributed computations by external agents. In Proceedings of the 9th International Conference on Distributed Computing Systems, Newport Beach, CA, USA, 5–9 June 1989; pp. 79–84. [Google Scholar] [CrossRef]
- Isloor, S.S.; Marsland, T.A. The Deadlock Problem: An Overview. Computer 1980, 13, 58–78. [Google Scholar] [CrossRef]
- Puhakka, A.; Valmari, A. Livelocks, Fairness and Protocol Verification. In Proceedings of the 16th World Conference on Software: Theory and Practice, Beijing, China, 21–25 August 2000; International Federation for Information Processing (IFIP): Laxenburg, Austria, 2000; pp. 471–479. [Google Scholar]
- Havelund, K.; Pressburger, T. Model checking JAVA programs using JAVA PathFinder. Int. J. Softw. Tools Technol. Transf. 2000, 2, 366–381. [Google Scholar] [CrossRef] [Green Version]
- Arcaini, P.; Gargantini, A.; Riccobene, E. AsmetaSMV: A model checker for AsmetaL models—Tutorial. 2009. Available online: https://air.unimi.it/retrieve/handle/2434/69105/96882/Tutorial_AsmetaSMV.pdf (accessed on 24 October 2018).
- Sharma, N.K.; Bhargava, B. A Robust Distributed Termination Detection Algorithm; Report 87-726; Purdue University Press: West Lafayette, IN, USA, 1987; Available online: http://docs.lib.purdue.edu/cgi/viewcontent.cgi?article=1626&context=cstech (accessed on 21 November 2018).
- Kern, C.; Greenstreet, M.R. Formal verification in hardware design: A survey. ACM Trans. Des. Autom. Electron. Syst. 1999, 4, 123–193. [Google Scholar] [CrossRef]
- Ma, G. Model Checking Support for CoreASM: Model Checking Distributed Abstract State Machines Using Spin. Master’s Thesis, Simon Fraser University, Burnaby, BC, Canada, 2007. [Google Scholar]
- Yang, Y.; Chen, X.; Gopalakrishnan, G. Inspect: A Runtime Model Checker for Multithreaded C Programs; Report UUCS-08-004; University of Utah: Salt Lake City, UT, USA, 2008. [Google Scholar]
- Attie, P.C. Synthesis of large dynamic concurrent programs from dynamic specifications. Form. Methods Syst. Des. 2016, 47, 1–54. [Google Scholar] [CrossRef]
- Baier, C.; Katoen, J.-P. Principles of Model Checking; MIT Press: Cambridge, MA, USA, 2008; ISBN 9780262026499. [Google Scholar]
- Joosten, S.J.C.; Julien, F.V.; Schmaltz, J. WickedXmas: Designing and Verifying on-chip Communication Fabrics. In Proceedings of the 3rd International Workshop on Design and Implementation of Formal Tools and Systems (DIFTS’14), Lausanne, Switzerland, 20 October 2014; Technische Universiteit Eindhoven: Eindhoven, The Netherlands, 2014; pp. 1–8. [Google Scholar]
- Martens, M. Establishing Properties of Interaction Systems. PhD. Thesis, University of Mannheim, Mannheim, Germany, 2009. [Google Scholar]
- Guan, X.; Li, Y.; Xu, J.; Wang, C.; Wang, S. A Literature Review of Deadlock Prevention Policy Based on Petri Nets for Automated Manufacturing Systems. Int. J. Digit. Content Technol. Its Appl. 2012, 6, 426–433. [Google Scholar] [CrossRef]
- Czejdo, B.; Bhattacharya, S.; Baszun, M.; Daszczuk, W.B. Improving Resilience of Autonomous Moving Platforms by real-time analysis of their Cooperation. Autobusy-TEST 2016, 17, 1294–1301. [Google Scholar]
- Daszczuk, W.B. Asynchronous Specification of Production Cell Benchmark in Integrated Model of Distributed Systems. In Studies in Big Data: 23rd International Symposium on Methodologies for Intelligent Systems (ISMIS 2017), Warsaw, Poland, 26–29 June 2017; Bembenik, R., Skonieczny, L., Protaziuk, G., Kryszkiewicz, M., Rybinski, H., Eds.; Springer International Publishing: Cham, Switzerland, 2019; Volume 40, pp. 115–129. [Google Scholar]
- Penczek, W.; Szreter, M.; Gerth, R.; Kuiper, R. Improving Partial Order Reductions for Universal Branching Time Properties. Fundam. Inform. 2000, 43, 245–267. [Google Scholar] [CrossRef]
- Chandy, K.M.; Lamport, L. Distributed snapshots: Determining global states of distributed systems. ACM Trans. Comput. Syst. 1985, 3, 63–75. [Google Scholar] [CrossRef]
- Dick, G.; Yao, X. Model representation and cooperative coevolution for finite-state machine evolution. In Proceedings of the 2014 IEEE Congress on Evolutionary Computation (CEC), Beijing, China, 6–11 July 2014; pp. 2700–2707. [Google Scholar] [CrossRef]
- Daszczuk, W.B. Threefold Analysis of Distributed Systems: IMDS, Petri Net and Distributed Automata DA3. In Proceedings of the 37th IEEE Software Engineering Workshop, Federated Conference on Computer Science and Information Systems (FEDCSIS’17), Prague, Czech Republic, 3–6 September 2017; pp. 377–386. [Google Scholar] [CrossRef]
- Daszczuk, W.B.; Bielecki, M.; Michalski, J. Rybu: Imperative-style Preprocessor for Verification of Distributed Systems in the Dedan Environment. In Proceedings of the KKIO’17—Software Engineering Conference, Rzeszów, Poland, 14–16 September 2017. [Google Scholar]
- Tai, K. Definitions and Detection of Deadlock, Livelock, and Starvation in Concurrent Programs. In 1994 International Conference on Parallel Processing (ICPP’94), Raleigh, NC, 15–19 August 1994; Agrawal, D.P., Ed.; CRC Press: Boca Raton, FL, USA, 1994; pp. 69–72. [Google Scholar]
- Masticola, S.P.; Ryder, B.G. Static Infinite Wait Anomaly Detection in Polynomial Time. In Proceedings of the 1990 International Conference on Parallel Processing, Urbana-Champaign, IL, USA, 13–17 August 1990; pp. 78–87. [Google Scholar]
- Dedan. Available online: http://staff.ii.pw.edu.pl/dedan/files/DedAn.zip (accessed on 24 October 2018).
- Daszczuk, W.B. Fairness in Temporal Verification of Distributed Systems. In 13th International Conference on Dependability and Complex Systems DepCoS-RELCOMEX, Brunów, Poland, 2–6 July 2018; Zamojski, W., Mazurkiewicz, J., Sugier, J., Walkowiak, T., Kacprzyk, J., Eds.; Springer International Publishing: Cham, Switzerland, 2018; Volume 761, pp. 135–150. [Google Scholar]
- Cimatti, A.; Clarke, E.; Giunchiglia, E.; Giunchiglia, F.; Pistore, M.; Roveri, M.; Sebastiani, R.; Tacchella, A. NuSMV 2: An OpenSource Tool for Symbolic Model Checking. In CAV 2002: Computer Aided Verification, Copenhagen, Denmark, 27–31 July 2002; Brinksma, E., Larsen, K.G., Eds.; Springer: Berlin/Heidelberg, Germany, 2002; Volume 2404, pp. 359–364. [Google Scholar]
- Schnoebelen, P. The complexity of temporal logic model checking. In 4th Conference Advances in Modal Logic (AiML’2002), Toulouse, France, 30 September—2 October 2004; Advances in Modal Logic; Balbiani, P., Suzuki, N.-Y., Wolter, F., Zakharyaschev, M., Eds.; King’s College Publications: London, UK, 2003; Volume 4, pp. 437–459. [Google Scholar]
- Dedan Examples. Available online: http://staff.ii.pw.edu.pl/dedan/files/examples.zip (accessed on 24 October 2018).
- Lewerentz, C.; Lindner, T. (Eds.) Formal Development of Reactive Systems; LNCS 891; Springer: Berlin/Heidelberg, Germany, 1995. [Google Scholar]
- Daszczuk, W.B.; Zuberek, W.M. Deadlock Detection in Distributed Systems Using the IMDS Formalism and Petri Nets. In 12th International Conference on Dependability and Complex Systems, DepCoS-RELCOMEX 2017, Brunów, Poland, 2–6 July 2017; Zamojski, W., Mazurkiewicz, J., Sugier, J., Walkowiak, T., Kacprzyk, J., Eds.; AISC; Springer International Publishing: Cham, Switzerland, 2018; Volume 582, pp. 118–130. [Google Scholar]
- Daszczuk, W.B. Siphon-based deadlock detection in Integrated Model of Distributed Systems (IMDS). In Proceedings of the Federated Conference on Computer Science and Information Systems, 3rd Workshop on Constraint Programming and Operation Research Applications (CPORA’18), Poznań, Poland, 9–12 September 2018; pp. 421–431. [Google Scholar] [CrossRef]
- Heiner, M.; Heisel, M. Modeling Safety-Critical Systems with Z and Petri Nets. In SAFECOMP ’99 Proceedings of the 18th International Conference on Computer Safety, Reliability and Security, Toulouse, France, 27–29 September 1999; Felici, M., Kanoun, K., Pasquini, A., Eds.; Springer: Berlin/Heidelberg, Germany, 1999; Volume 1698, pp. 361–374. [Google Scholar]
- Heiner, M.; Schwarick, M.; Wegener, J.-T. Charlie—An Extensible Petri Net Analysis Tool. In Proceedings of the 36th International Conference, PETRI NETS 2015, Brussels, Belgium, 21–26 June 2015; pp. 200–211. [Google Scholar] [CrossRef]
- Bérard, B.; Cassez, F.; Haddad, S.; Lime, D.; Roux, O.H. Comparison of the Expressiveness of Timed Automata and Time Petri Nets. In Proceedings of the Third International Conference, FORMATS 2005, Uppsala, Sweden, 26–28 September 2005; pp. 211–225. [Google Scholar] [CrossRef]
- Popescu, C.; Martinez Lastra, J.L. Formal Methods in Factory Automation. In Factory Automation; Silvestre-Blanes, J., Ed.; InTech: Rijeka, Croatia, 2010; pp. 463–475. [Google Scholar]
- Dijkstra, E.W. A note on two problems in connexion with graphs. Numer. Math. 1959, 1, 269–271. [Google Scholar] [CrossRef] [Green Version]
- van der Aalst, W.M.P. The Application of Petri Nets to Workflow Management. J. Circuits Syst. Comput. 1998, 8, 21–66. [Google Scholar] [CrossRef]
- Kwiatkowska, M.; Norman, G.; Parker, D. PRISM 4.0: Verification of Probabilistic Real-Time Systems. In Proceedings of the 23rd International Conference, CAV 2011, Snowbird, UT, USA, 14–20 July 2011; pp. 585–591. [Google Scholar] [CrossRef]

| Property | CTL Formula | Meaning |
|---|---|---|
| communication deadlock in server s | EF AG (Ds ⋀ ¬Es) | Eventually always (Ds ⋀ ¬Es) |
| server s is idle | AF AG (¬Ds) | In every run eventually always (¬Ds) |
| resource deadlock in agent a | EF AG (Da ⋀ ¬Ea) | Eventually always (Da ⋀ ¬Ea) |
| termination of agent a | AF (Fa) | In every run eventually (Fa) |
© 2018 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Daszczuk, W.B. Specification and Verification in Integrated Model of Distributed Systems (IMDS). Computers 2018, 7, 65. https://doi.org/10.3390/computers7040065
Daszczuk WB. Specification and Verification in Integrated Model of Distributed Systems (IMDS). Computers. 2018; 7(4):65. https://doi.org/10.3390/computers7040065
Chicago/Turabian StyleDaszczuk, Wiktor B. 2018. "Specification and Verification in Integrated Model of Distributed Systems (IMDS)" Computers 7, no. 4: 65. https://doi.org/10.3390/computers7040065
APA StyleDaszczuk, W. B. (2018). Specification and Verification in Integrated Model of Distributed Systems (IMDS). Computers, 7(4), 65. https://doi.org/10.3390/computers7040065





