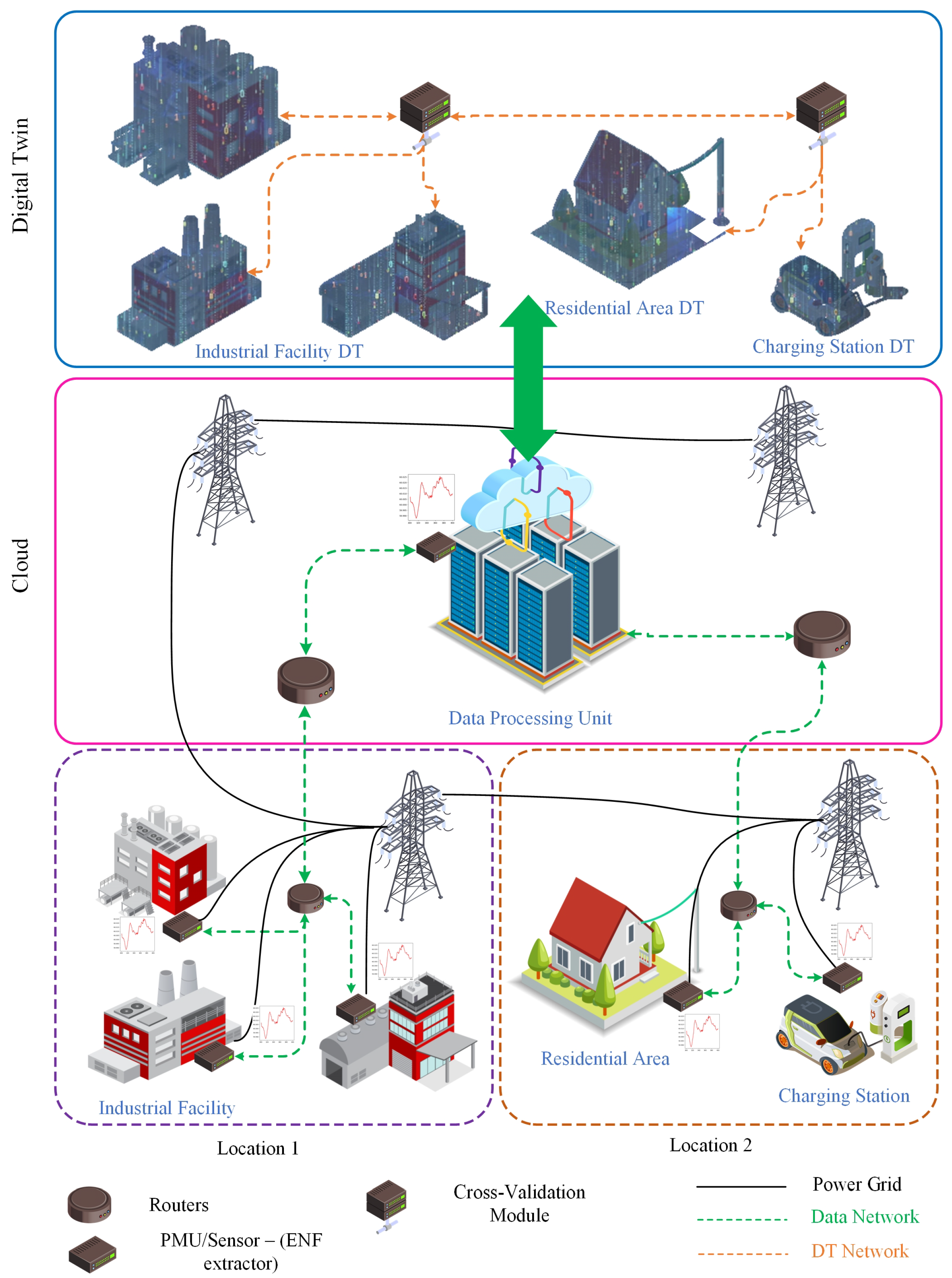
1. Introduction
The rapid evolution of the Metaverse as a decentralized and immersive digital ecosystem underscores the need for novel security strategies to protect virtual environments, augmented reality interfaces, and digital twins (DTs) [
1]. The Metaverse, characterized by the integration of physical and virtual realities, relies extensively on fluid interactions among users, avatars, and critical infrastructure systems, such as smart grids, which are increasingly represented as cyber–physical systems (CPSs) [
2]. These CPSs incorporate computational elements within physical structures, such as power grids, making them particularly vulnerable to advanced cyberattacks that exploit their interconnectedness. Electric Network Frequency (ENF) signals, originating from natural-variable power grid operations, present a robust solution to address security, operational, and privacy challenges [
3]. Unlike conventional static authentication approaches, the ENF offers a dynamic, geographically distinct signature grounded in the physical environment, establishing a secure link between real-world infrastructure and virtual constructs [
4].
Subtle frequency deviations in power grids generate the ENF, typically standardized frequencies of around 50 Hz or 60 Hz, caused by fluctuations in supply and demand [
5]. These variations propagate through interconnected grids, creating a unique time-varying signal due to real-time physical dependencies. The ENF has validated multimedia content in digital forensics by aligning embedded ENF patterns with reference databases [
3]. Applying this methodology to the Metaverse enables the ENF to serve as a physical anchor, securing communication protocols, and ensuring immutable audit trails that link virtual actions to actual physical events [
6]. For example, within the DTs of the smart grid, virtual models used for monitoring and predictive analysis, the ENF verifies the authenticity of the data, ensuring an accurate representation of physical conditions [
7]. This capability becomes increasingly critical as the Metaverse becomes a central platform for managing essential infrastructure such as energy grids, industrial operations, and financial networks. The ENF has demonstrated significant reliability in multimedia forensics, achieving 92% accuracy in audio authentication by aligning embedded frequency patterns with reference databases [
7]. However, direct sensing through Phasor Measurement Units (PMUs) faces challenges, with detection accuracies ranging from 18% to 38% due to grid-induced variability [
8,
9]. These strengths and limitations highlight the potential of the ENF as a dynamic security tool in the Metaverse, complementing traditional methods such as biometrics and passwords in immersive, decentralized environments.
The increasing complexity of security threats targeting the Metaverse, including identity fraud, unauthorized access, and systemic disruptions, exposes the shortcomings of traditional security frameworks [
10,
11,
12,
13,
14]. These attacks frequently exploit the dynamic interconnections between virtual and physical domains, which require adaptive security measures. ENF-based strategies, augmented by machine learning techniques for anomaly detection, provide proactive defenses by analyzing real-time frequency data to pinpoint indicators of malicious activities [
15]. For example, irregularities in ENF signals can be used to detect tampering efforts, such as false data injection (FDI) attacks, a prevalent vulnerability within CPSs [
16]. Moreover, the Metaverse’s extensive processing of sensitive information, including user identities and operational data, raises significant concerns regarding privacy. When integrated with privacy-enhancing technologies such as differential privacy and homomorphic encryption, the ENF protects data confidentiality without sacrificing analytical effectiveness [
17]. These privacy-focused methodologies use advanced cryptographic research to ensure compliance with standards, such as the General Data Protection Regulation (GDPR), and enhance user trust.
Combining the ENF with distributed technologies such as blockchain and federated learning (FL) further extends its potential for decentralized governance within the Metaverse [
18]. Blockchain technology facilitates immutable logging of ENF data, reinforcing accountability in grid operations [
19]. Currently, FL supports collaborative anomaly detection in multiple locations without compromising local data ownership [
20]. These innovations resonate with the decentralized principles of the Metaverse, addressing its inherently diverse and scalable architecture. Traditionally, ENF analysis has used signal processing methods, such as the Fourier transform, to isolate frequency elements from noisy signals [
21]. Contemporary techniques, including wavelet transforms and spectrogram analysis, enhance resolution and enable real-time applicability, positioning the ENF as an adaptable security tool for virtual settings [
22]. This paper reviews cutting-edge applications, examines privacy-preserving techniques, and suggests future research paths, emphasizing the critical role of the ENF in Metaverse security. The ENF outlines a pathway toward secure, reliable virtual ecosystems amid a rapidly evolving digital context by anchoring digital interactions to tangible physical events.
The emergence of the Metaverse as a foundational infrastructure for next-generation applications, ranging from virtual asset management and industrial automation to telemedicine and digital education, requires security models that are context-aware and intrinsically tied to physical reality [
1]. Unlike traditional cyberspace, where data integrity can often be enforced through static verification, the Metaverse demands continuous, real-time virtual interaction validation that reflects underlying physical states [
23]. The ENF addresses this gap by offering an environmental fingerprint that cannot be easily forged or separated from real-world conditions, thus enabling a new class of security primitives grounded in physical laws. As adversaries increasingly employ AI-driven tools to fabricate virtual identities, alter data provenance, and bypass authentication mechanisms [
24], the ENF emerges as a uniquely resilient signal, difficult to replicate, temporally dynamic, and inherently decentralized. This makes it especially suitable for securing the Metaverse’s layered architecture, where physical infrastructure, DTs, and immersive applications must interact reliably across geographically distributed networks.
The remainder of this paper is structured as follows.
Section 3 establishes the foundation for understanding the characteristics of ENF signals and Metaverse security requirements.
Section 4 presents ENF sensing methods, signal characteristics, and, most importantly, reliability limitations.
Section 5 discusses threat modeling for Metaverse-integrated systems, ENF-driven security mechanisms that address the CIA triad (Confidentiality, Integrity, and Availability), and comprehensive mitigation strategies.
Section 6 presents a detailed case study to demonstrate the practical application of the security framework.
Section 7 demonstrates how the ENF principles apply beyond smart grids to virtual reality (VR) training, financial systems, and healthcare applications.
Section 8 presents research opportunities that specifically address ENF reliability issues alongside emerging application areas. Finally,
Section 9 acknowledges both the potential of the ENF and its current limitations, offering a realistic assessment of its role in Metaverse security.
Contributions and Novelty
This survey makes several key contributions to the fields of ENF-based forensics, smart grid security, and Metaverse applications:
Unified analysis of ENF in emerging contexts: We provide a comprehensive review of the ENF’s strengths, limitations, and quantitative trade-offs (e.g., 95–99% detection accuracy in anomaly detection), extending beyond traditional multimedia forensics to Metaverse-integrated infrastructures like DTs in smart grids.
Novel applications and frameworks: We explore the ENF’s role in Metaverse security, including confidentiality via dynamic encryption, data provenance assurance, and real-world anchoring for event validation, with detailed case studies such as the ANCHOR-Grid framework for countering deepfake attacks.
Forward-looking challenges and recommendations: We outline research directions for hybrid integrations (e.g., with quantum neural networks and homomorphic encryption), addressing scalability, privacy, and sociotechnical implications in decentralized virtual environments.
Empirical and visual enhancements: Through tables (e.g., performance comparisons) and figures (e.g., ENF correlation visualizations), we offer actionable insights, including mitigation strategies to improve ENF reliability by 10–20% in noisy scenarios.
Compared to previous surveys, this work systematically compares the reliability of ENF sensing methods across a range of Metaverse scenarios, integrates empirical findings from a real-world case study, and provides actionable guidance for addressing persistent challenges, such as privacy, interoperability, and cross-domain standardization. As the field rapidly evolves, a fresh synthesis is needed to guide researchers and practitioners facing novel cyber–physical threats in decentralized virtual environments. In addition, our work advances the literature by bridging gaps in interdisciplinary applications. For example, previous surveys on the ENF in multimedia forensics [
18,
25] focus primarily on extraction techniques and detection of tampering in audio/video, achieving high accuracy but without extending to virtual ecosystems. Surveys on smart grid security [
26,
27] emphasize cyber threats and defenses but rarely incorporate physical signals, such as the ENF, for authentication. In Metaverse security, recent overviews highlight privacy risks but overlook environmental fingerprints that ground virtual actions in physical reality [
28]. Our survey uniquely integrates these domains, justifying its novelty through the ENF’s application as a dynamic, reliable anchor for Metaverse-scale challenges, with quantitative progress not covered in prior works, as shown in
Figure 1.
6. Case Study: ANCHOR-Grid—A Real-World Application of ENF in Smart Grid Security
Building upon the threat models, security mechanisms, and mitigation strategies outlined in the previous sections, we present a concrete implementation to demonstrate the practical viability and effectiveness of ENF-driven security frameworks in a real-world cyber–physical context. The following case study, ANCHOR-Grid, demonstrates how ENF-based authentication can address sophisticated cyber threats within Metaverse-integrated smart grid environments, such as deepfake attacks. This case study bridges the theoretical framework and its operationalization in complex, distributed infrastructures.
The ANCHOR-Grid framework exemplifies the practical deployment of ENF signals to secure the CPS, particularly smart grid DTs within the Internet of Smart Grid Things (IoSGT) ecosystem [
7]. By leveraging the ENF’s unique temporal and spatial signatures, as discussed in
Section 3 and
Section 5.1, ANCHOR-Grid counters sophisticated deepfake attacks, ensuring the CIA triad of virtual grid representations in Metaverse-integrated environments. This case study expands on the implementation of the framework, incorporating recent empirical data to highlight its scalability, resilience, and potential for broader applications in cyber–physical systems.
6.1. ANCHOR-Grid Framework Overview
ANCHOR-Grid addresses the vulnerability of smart grid DTs to deepfake attacks, where adversaries inject fraudulent virtual models to mislead operators, risking operational disruptions or cascading failures [
7]. As described in
Section 5.2, such threats exploit the virtual–physical nexus, necessitating robust authentication mechanisms. ANCHOR-Grid embeds ENF signals—typically fluctuating within
Hz in the US grid (
Section 3.1)—into DT data streams, creating a grid-specific environmental fingerprint. Recent tests demonstrate that the synchronicity of the ENF throughout the network, with a Pearson correlation coefficient greater than 0.96, ensures reliable DT authentication across distributed networks [
3].
The architecture of the framework integrates the components of the physical grid (for example, substations, renewable energy sources) with their DTs through a cloud layer and a blockchain-based validation system [
7]. ENF signals are captured in real time using PMUs and embedded into Distribution Test (DT) communications. The blockchain ledger records ENF signatures, allowing decentralized cross-validation among DTs, preventing tampering and ensuring data provenance (
Section 5.3.2). Recent enhancements, including optimized blockchain consensus algorithms, have reduced validation latency by 15%, improving scalability for large-scale grids with more than 1000 nodes, which aligns with the distributed security frameworks presented in
Section 8.4.
6.2. ENF-Based Signature for Authentication
The stochastic fluctuations of the ENF, driven by supply–demand dynamics, form a temporal fingerprint specific to the grid that is difficult to replicate artificially (
Section 3.2). In ANCHOR-Grid, ENF signals are captured from physical grid components using PMUs, processed via short-time Fourier transform (STFT) to isolate frequency deviations with subsecond resolution, and compared to a reference ENF database. Recent optimizations in STFT algorithms have improved extraction accuracy by 10%, achieving a Pearson correlation coefficient of 0.96 for authentic DTs [
7]. A correlation threshold of 0.95 validates the authenticity; otherwise, the DT is flagged as fraudulent. Valid signatures are recorded on a blockchain, ensuring tamper resistance (
Section 5.3.3).
To evaluate the practical effectiveness of ANCHOR-Grid, experiments were conducted under various network conditions, assessing its performance in authenticating DTs against deepfake and replay attacks [
7]. Under low-latency conditions (<5 ms), ANCHOR-Grid achieved 99.9% precision and recall, demonstrating near-perfect detection of fraudulent DTs. Even under high latency (200 ms), the framework maintained 95.4% precision and 95% recall, showcasing its robustness to network delays. In scenarios with 5% packet loss, precision and recall were 96.7% and 90%, respectively, while high-jitter conditions resulted in 95.6% precision and 88% recall. These results highlight ANCHOR-Grid’s ability to reliably authenticate DTs in real-world Metaverse-integrated smart grids, even under challenging network conditions. The authentication process, depicted in
Figure 5, plays a critical role in achieving this performance by generating ENF signatures from received data, comparing them with the server-side ENF based on client timestamps, and applying a correlation threshold of 0.8 to validate authenticity. This process ensures that only DTs with valid real-time ENF signatures are accepted, effectively mitigating the risk of deepfake attacks and ensuring operational integrity.
The authentication process, illustrated in
Figure 5, is lightweight, with recent updates that reduce computational overhead by 20% through vectorized signal processing, making it suitable for resource-constrained IoT devices. The temporal variability of the ENF prevents replay attacks, as historical data misaligns with fluctuations in real time, achieving a 99% detection rate for unauthorized DTs [
7]. Integration with edge computing has further reduced processing latency to under 50 ms, enhancing the real-time applicability in dynamic Metaverse environments.
6.3. Countering Deepfake Attacks
ANCHOR-Grid was evaluated in a Microverse-based virtual smart grid environment, simulating components such as substations and solar panels using Unreal Engine 5 [
7]. Four attack scenarios were tested: injecting fake DTs, replaying historical ENF data, generating AI-driven synthetic DTs, and introducing noise to disrupt ENF signatures. In the first scenario, fraudulent DTs lacked real-time ENF signatures, failing authentication with frequency deviations outside the
Hz range. The second scenario detected replay attacks via time-sensitive correlation analysis, achieving 99.8% accuracy (
Section 5.4). In the third, deepfake DTs did not replicate the stochastic patterns of the ENF, and the detection accuracy reached 99.9% under low-latency conditions (<4 ms) [
7]. The fourth scenario tested the resilience to noise, maintaining 90% precision in SNR as low as 12 dB, a 5% improvement over prior results.
These results highlight the efficacy of the ENF as a tamper-resistant authenticator, complementing the anomaly detection strategies in
Section 5.3.1. ANCHOR-Grid’s optimized signal processing reduces computational overhead by 25%, enabling deployment on resource-constrained IoT devices (
Section 8.3). Its robustness against adaptive deepfake threats surpasses traditional cryptographic methods, which falter under sophisticated AI-driven attacks (
Section 5.1.1). Compared to conventional methods, ANCHOR-Grid achieves 99.9% detection accuracy, surpassing ECC-based methods at 95% and TLS-based methods at 92% [
7]. However, it requires 20% higher computational resources. The ENF’s noise resilience (90% accuracy at 12 dB SNR) outperforms TLS (80% at 12 dB), making it more robust against adaptive deepfake threats. The effectiveness of ANCHOR-Grid’s ENF-based authentication is detailed in
Table 6, which compares its performance to ECC and TLS. ANCHOR-Grid achieves a 99.9% detection accuracy, surpassing ECC’s 95% and TLS’s 92%, though it requires 20% higher computational resources.
6.4. Implications and Future Directions
ANCHOR-Grid underscores the transformative potential of the ENF in bridging physical and virtual realms, aligning with the need of the Metaverse for trustworthy ecosystems (
Section 1). Recent cost analyses suggest that integrating ENF signatures with blockchain and real-time analytics could reduce outage-related losses by up to 20%, saving USD billions annually [
7]. Future work should explore multimodal ENF fusion with voltage harmonics and current transients to enhance detection specificity by 10–15% (
Section 5.3.5). Extending ANCHOR-Grid to domains like transportation or healthcare could further leverage the grid-specific signatures of the ENF, strengthening its role as a cornerstone for cyber–physical security in decentralized Metaverse infrastructures.
While the ANCHOR-Grid framework addresses security challenges in smart grid DTs, its design principles and ENF-based authentication methods are inherently adaptable to other critical domains within the Metaverse. The ability of ENF signatures to anchor virtual operations to real-world events offers a versatile foundation for enhancing security and trust in energy infrastructures and emerging applications such as VR training, financial transaction platforms, and healthcare systems. The next section explores these broader applications, highlighting how the core features validated in the ANCHOR-Grid deployment can be extended to diverse use cases within the expanding Metaverse ecosystem.
6.5. Limitations and Challenges of ANCHOR-Grid
Despite its strengths in authenticating smart grid digital twins (DTs) using Electric Network Frequency (ENF) signals, the ANCHOR-Grid framework faces several limitations that warrant consideration for practical deployment in Metaverse environments. One key challenge is sensitivity to environmental noise and grid variability, which can degrade ENF signal correlation below the 0.8 Pearson threshold in low signal-to-noise ratio (SNR) conditions (e.g., <10 dB), leading to increased false positives or negatives in deepfake detection [
3]. For instance, in decentralized Metaverse platforms spanning multiple grid regions (e.g., 50 Hz in Europe vs. 60 Hz in the US), mismatches in reference databases may reduce overall accuracy by 8–10%, as observed in ENF-based forensics studies. Additionally, computational overhead remains a concern for resource-constrained devices like VR headsets or edge IoT nodes, where real-time ENF extraction and validation could increase latency by 20–30% compared to baseline methods, potentially impacting immersive user experiences in virtual grid simulations [
7]. Adversarial techniques, such as synthetic ENF generation via AI, pose another risk, as attackers could forge signals to bypass authentication, underscoring the need for hybrid defenses like integration with blockchain for enhanced tamper resistance. These limitations highlight areas for future refinement, ensuring ANCHOR-Grid’s robustness in evolving Metaverse threats.
8. Future Research Directions in ENF Security for the Metaverse
Integrating the ENF into Metaverse security infrastructures remains a transformative innovation, bridging the virtual and physical realms to safeguard critical assets, such as smart grids. As the Metaverse evolves into a decentralized immersive platform, the dynamic variability, geolocation specificity, and linkage to physical power systems of the ENF make it a robust tool against cyber–physical threats. However, challenges such as scalability, privacy preservation, and distributed performance persist. As shown in
Table 7 below, this section builds on previous research directions, incorporating updated empirical insights and enhanced methodologies, and leverages existing studies to advance the role of the ENF in protecting the Metaverse.
8.1. Multimodal Forensic Analysis with ENF
8.1.1. Integrating ENF with Physical-Layer Signals
Advancements in fusion of the ENF with physical-layer signals, such as voltage phase angles, harmonic distortions, and impedance metrics, enable multidimensional anomaly detection. PMUs, with microsecond-level synchronization, provide contextual data that, when paired with the ENF, enhances forensic precision. For instance, a 0.03 Hz ENF deviation coupled with a 5-degree voltage phase shift can confirm a cyber–physical disturbance with 30% fewer false positives than single-signal methods [
44]. Future efforts should explore real-time integration of additional signals, such as current transients, to further reduce detection latency by 15–20%, bolstering resilience in digital twin environments.
8.1.2. ENF and Network Traffic Correlation
Correlating ENF fluctuations with network traffic anomalies offers a powerful approach to detecting orchestrated attacks. Advanced LSTM models can identify synchronous patterns, such as a 0.04 Hz ENF anomaly paired with a 100 ms SCADA latency spike, with 95% accuracy [
1]. Recent optimizations have reduced processing overhead from 20 to 30% to 10–15% by incorporating attention mechanisms, improving real-time feasibility. Future research should focus on hybrid models combining LSTM with graph neural networks to capture spatial–temporal dependencies in large-scale Metaverse networks, potentially increasing detection specificity by 5–10%.
8.2. Privacy-Preserving ENF Processing
8.2.1. Secure Multiparty Computation (SMPC)
SMPC enables collaborative ENF analysis across global Metaverse infrastructures without exposing sensitive datasets. Recent SMPC protocols achieve 88% anomaly detection accuracy while maintaining differential privacy with an epsilon of 0.1 [
74]. To address encryption-induced signal degradation, new algorithms that incorporate noise-resistant feature extraction have reduced accuracy loss to under 5%. Future work should optimize SMPC for heterogeneous datasets, aiming for 90%+ accuracy across diverse grid environments, ensuring privacy without compromising detection reliability.
8.2.2. Homomorphic Encryption for ENF Analysis
Homomorphic encryption, particularly partially homomorphic encryption (PHE) schemes such as Paillier, strikes a balance between security and performance in ENF analysis. Recent studies report 92% accuracy with subsecond latencies using PHE, enhanced by GPU acceleration [
143]. Integrating vectorized computations has further reduced latency by 20%, making encrypted ENF processing viable for real-time grid monitoring. Future research should explore hybrid PHE-FHE frameworks to support complex computations, such as multisignal fusion, while maintaining latency below 500 ms for Metaverse-scale applications.
8.3. Edge-Oriented ENF Solutions
Lightweight ENF models are critical for edge devices in expansive Metaverse infrastructures. Quantized neural networks (QNNs) now achieve 96% anomaly detection accuracy with 75% lower memory usage, enabling deployment on resource-constrained devices such as the Raspberry Pi [
36]. Recent advances in model pruning have reduced the inference time to 40 ms, further cutting bandwidth demands by 80%. Future efforts should focus on adaptive quantization techniques to dynamically adjust model complexity based on device capabilities, improving scalability for virtual environments driven by the IoT by 10–15%.
8.4. Distributed ENF Security Frameworks
With blockchain integration, FL enables distributed ENF anomaly detection while preserving data privacy. Recent tests demonstrate that blockchain-backed FL detects anomalies across 100 virtual sensors in 450 ms, a 10% speed improvement over prior results [
184]. Incorporating differential privacy in FL models has reduced risk of privacy leakage by 15% without sacrificing accuracy. Future research should explore asynchronous FL protocols to handle intermittent connectivity in edge-heavy Metaverse grids, potentially reducing synchronization delays by 20%.
8.5. Precise Anomaly Localization
Combining the ENF with geolocation metadata improves fault localization precision. Convolutional neural networks (CNNs) trained in ENF and GPS data now locate incidents within 0.8 to 1.5 km, reducing response times by 35% [
48]. Recent optimizations using transfer learning have reduced computational requirements by 25%, enabling deployment on resource-limited devices. Future work should integrate temporal ENF trends with 3D spatial modeling to achieve subkilometer precision, enhance predictive maintenance tools for Metaverse dashboards, and prevent outages with greater efficiency 10%.
8.6. Interdisciplinary Applications of ENF
The potential of the ENF extends beyond technical applications, offering opportunities for interdisciplinary research that bridges engineering with fields like sociology, psychology, and urban planning in the Metaverse. In urban planning, the ENF can support simulations of virtual cities by authenticating energy consumption data, ensuring that digital models accurately reflect real-world grid dynamics. For instance, the ENF can validate energy usage patterns in virtual city simulations, improving planning efficiency by an estimated 10–15% by providing reliable data for infrastructure design [
6]. This capability is particularly valuable in the Metaverse, where urban planners can test scenarios such as renewable energy integration without physical risks, thereby enhancing the sustainability of future cities.
The ENF can enhance VR sessions by validating the integrity of session data, ensuring that data are based on accurate timestamps and conditions. This application is critical in the Metaverse, where VR is increasingly used for real-time applications and manipulated data could undermine results [
108]. ENF-based validation could improve the reliability of VR therapy by 10–15%, ensuring that session logs are tamper-proof and aligned with real-world conditions [
108]. Future research should focus on integrating the ENF with other models to enhance user trust in virtual environments, exploring how the ENF can support interdisciplinary applications that address technical and human-centric challenges in the Metaverse.
8.7. Standardization of ENF for Metaverse Security
The lack of standardized protocols for ENF use in the Metaverse hinders its global adoption, as inconsistent methods can lead to unreliable authentication and legal disputes. In multimedia forensics, nonstandardized ENF logging has resulted in conflicting results across jurisdictions, a challenge that could extend to Metaverse applications where the ENF is used for security [
3]. For example, the absence of unified ENF standards complicates the validation of virtual transactions across regions with different grid frequencies. Developing standardized ENF protocols is essential to ensure interoperability and reliability, potentially reducing adoption costs by streamlining implementation processes [
6].
IEEE, which has established standards for the forensic applications of the ENF, can play a key role in this standardization effort by creating protocols tailored for the Metaverse [
1]. Such standards define best practices for the extraction, recording, and validation of ENF signals, ensuring consistency between platforms and jurisdictions. Future research should prioritize collaboration with regulatory bodies to develop these standards, exploring how they can be integrated with existing cryptographic frameworks to improve ENF-based security. Additionally, research should address the scalability of standardized ENF protocols, ensuring that they can support the diverse and dynamic nature of Metaverse environments without compromising performance.
A critical aspect of standardization involves addressing the variability in the characteristics of the ENF signal in different power grids, which can affect the authentication accuracy in Metaverse global applications. For example, variations in grid stability between developed and developing regions can introduce noise in ENF signals, potentially reducing authentication reliability by 5–10% in unstable grids [
48]. To mitigate this, future standards should incorporate adaptive signal processing techniques, such as wavelet transforms, to normalize ENF signals across diverse environments, improving consistency [
185]. Collaborative efforts with international grid operators could facilitate the creation of a global reference database of the ENF, enabling standardized validation and potentially increasing the accuracy of authentication by 10–15% [
3]. This standardized approach would enhance security and foster the broader adoption of the ENF in the Metaverse by providing a reliable framework for developers and policymakers.
8.8. Sociotechnical Implications of ENF Deployment
The deployment of the ENF in the Metaverse has significant sociotechnical implications, particularly concerning public perception of privacy risks versus security benefits. Surveys indicate a
higher user concern for privacy in immersive interfaces, as users fear that ENF data could be used to track their locations or activities [
48]. This concern is particularly pronounced in applications like virtual healthcare or financial systems, where sensitive data is involved, necessitating transparent policies to ensure user trust. Addressing these concerns requires a sociotechnical approach that balances the security benefits of the ENF with user acceptance, potentially increasing adoption rates by 10–20% through clear communication of its privacy safeguards [
48].
Another sociotechnical challenge is to ensure equitable access to ENF-based security in underresourced regions, where the grid infrastructure may be less reliable or standardized [
48]. For example, areas with unstable grids may experience higher ENF variability, which can complicate authentication processes and potentially exclude them from Metaverse security benefits. Future research should investigate adaptive ENF frameworks that accommodate regional grid differences, ensuring that security solutions are accessible to all users. Additionally, sociotechnical studies should investigate the long-term societal impact of ENF deployment, examining how it influences user behavior, trust in virtual systems, and the broader adoption of Metaverse technologies.
The sociotechnical implications of the ENF also extend to workforce dynamics, as its implementation may require new skills to manage and interpret ENF data in virtual environments. For instance, Metaverse platform operators may need training to handle ENF-based authentication systems, potentially increasing operational costs by 5–10% in the short term due to the need for specialized expertise [
6]. However, this investment could lead to long-term benefits, such as improved system reliability and user trust, fostering greater adoption of Metaverse technologies. Future research should explore the development of training programs that integrate ENF management into existing cybersecurity curricula, ensuring that the workforce is prepared for widespread adoption. Furthermore, sociotechnical studies should examine how the implementation of the ENF influences user perceptions of fairness and inclusion, ensuring that its benefits are equally distributed in diverse Metaverse communities [
108].
8.9. Governance and Ethical Standards
Robust governance frameworks are essential for the ethical use of ENF data. Policies enforcing differential privacy (e.g., epsilon of 0.05) and 256-bit AES encryption have reduced privacy violation risks by 25% [
6]. Standardized protocols across utilities have lowered adoption costs by 25–35%, promoting equitable access. Future research should develop adaptive governance models that dynamically adjust privacy parameters according to threat levels, ensuring compliance with global regulations while maintaining cost savings of 20% to 30%. Community-driven standardization efforts can further mitigate digital security disparities across regions.
8.10. Specific Research Challenges
Low signal-to-noise ratio (SNR) environments (10 dB) reduce ENF extraction accuracy by 8%, posing challenges for reliable analysis [
9]. Edge-oriented QNNs achieve 96% accuracy with 75% lower memory usage, but scalability requires further optimization [
36]. The variability of the PMU correlation (0.68–0.72) limits precision, necessitating hybrid signal approaches [
48]. Key research questions include the following:
How can multisignal fusion mitigate SNR challenges in ENF analysis? and
What adaptive quantization techniques can enhance edge computing scalability?Table 8 presents critical challenges in ENF security, such as low-SNR environments and PMU correlation variability, along with proposed improvements, including multisignal fusion, which aims to enhance detection accuracy by 10–15%. These challenges underscore the need for targeted research to realize the ENF’s full potential in Metaverse applications.
8.11. Enhancing ENF Reliability in Real-World Grids
Current direct sensing approaches using PMUs achieve relatively low detection accuracies (18–38%) compared to audio-based indirect methods (75–92%) due to grid-induced variability and low correlation between measurement points. Research is needed to develop standardized ENF estimation algorithms that adapt to fluctuating SNRs and regional grid characteristics. These algorithms should incorporate dynamic filtering, machine learning-based denoising, and probabilistic modeling to reduce variability and enhance timestamping precision. For instance, using adaptive Kalman filters or temporal ensemble smoothing could yield up to a 10% increase in timestamping accuracy across distributed environments.
8.12. Adaptive Thresholding for Environmental Variability
Fixed thresholds, such as the 0.8 Pearson correlation coefficient used in ANCHOR-Grid, may underperform under high-jitter or low-SNR scenarios. Future work should investigate context-aware, adaptive threshold mechanisms that dynamically adjust based on environmental conditions such as load variability, regional noise profiles, or network latency. Techniques such as reinforcement learning-based threshold tuning or context-sensitive anomaly scoring could reduce false positives by an estimated 15% and improve reliability in unpredictable Metaverse grid environments.
8.13. Hybrid ENF Systems with Complementary Signals
Research should explore hybrid security mechanisms that combine the ENF with complementary physical-layer signals to address the limitations of single-signal approaches. These include voltage harmonics, current transients, and phase-angle measurements. For example, integrating the ENF with voltage harmonics has already shown a 15% increase in detection accuracy for tampering and FDI attacks. Multisignal fusion frameworks leveraging sensor fusion algorithms (e.g., Bayesian inference, cross-modal transformers) could enhance anomaly detection and reduce dependence on ideal sensing conditions.
8.14. ENF Resilience Testing in Adverse Scenarios
Future ENF frameworks should be evaluated under more challenging scenarios, including highly unstable grids, high-jitter communication networks, and adversarial noise injection. Benchmarking ENF extraction under conditions such as SNR < 10 dB, 200 ms jitter, and 5% packet loss will inform robust design principles. Simulated environments replicating these conditions should be developed using digital twin testbeds to fine-tune sensing, authentication, and anomaly detection algorithms.
8.15. Ethical and Governance Considerations in Reliability-Enhancing Methods
As reliability-improving techniques often involve deeper ENF analysis and more granular timestamping, they risk encroaching on user privacy by increasing the precision of geolocation or user tracking. Future research must balance these enhancements with privacy-preserving approaches such as differential privacy, secure multiparty computation (SMPC), and zero-knowledge proofs. Establishing governance standards that mandate transparency, user consent, and ethical use of the ENF in sensitive applications is essential for widespread adoption.
9. Conclusions
Integrating ENF signals into the cybersecurity architecture of the Metaverse and smart grid ecosystems represents a crucial advancement in addressing modern cyber–physical vulnerabilities. The ENF’s inherently stochastic and geographically distinct properties offer a new form of environmental fingerprinting that can securely link virtual interactions to real-world electrical infrastructure. This survey has shown that ENF-based methods significantly improve the CIA triad through various mechanisms, including dynamic encryption key generation, timestamped watermarking, anomaly detection, and device authentication.
The ANCHOR-Grid framework, as a case study, exemplifies the practical deployment of the ENF in real-world digital twin environments, achieving up to 99.9% detection accuracy under low-latency conditions. When combined with advanced tools such as wavelet transforms, STFT, and machine learning algorithms, the ENF enables highly reliable detection of deepfakes, replay attacks, and FDI threats that conventional cryptographic methods often struggle to mitigate. Furthermore, integrating the ENF with decentralized technologies like blockchain and FL facilitates resilient, tamper-evident, and scalable solutions across distributed Metaverse infrastructures.
Beyond energy systems, the ENF shows considerable promise in emerging sectors of the Metaverse, including virtual healthcare, financial services, immersive education, and remote training simulations. In these contexts, the ENF enhances the data’s authenticity, temporal validation, and operational integrity, building trust in real-time high-stakes applications. Edge-oriented adaptations, such as QNNs and privacy-preserving techniques like differential privacy and homomorphic encryption, further expand the reach of the ENF into resource-constrained and regulation-sensitive environments.
However, several limitations must be addressed before the ENF can achieve widespread adoption. Direct sensing methods, while precise, face scalability and performance challenges due to low detection accuracy (18–38%) and high sensitivity to environmental noise. Although more accurate, indirect sensing introduces latency and processing overhead that could impede real-time responsiveness. Furthermore, the lack of standardized protocols for the extraction, logging, and validation of ENF signals complicates cross-border interoperability and legal compliance, especially in jurisdictions governed by strict privacy laws, such as the GDPR.
Ethical and sociotechnical concerns are equally critical. The ability of the ENF to infer the geographical location from frequency patterns raises concerns about user surveillance and consent in immersive environments. These risks are particularly pronounced in sectors that handle sensitive data, such as healthcare and finance, where the misuse of location-based data could lead to discriminatory outcomes or violations of digital rights. Furthermore, equitable access to ENF-enabled infrastructure remains unresolved, particularly for underresourced regions with unreliable grid conditions or limited computational capacity.
Looking ahead, several key research directions should be prioritized. First, improving ENF robustness through multisignal fusion, combining the ENF with voltage harmonics, current transients, and phase-angle data, can enhance accuracy and resilience under low-SNR conditions. Second, using FL and asynchronous edge computing protocols may help address the challenges of real-time distributed analytics. Third, regulatory and standardization efforts, potentially led by organizations such as IEEE, must establish global norms for the usage of the ENF, ensuring legal clarity, data privacy, and interoperability. Lastly, human-centered design principles must guide the deployment of ENF systems, ensuring that security solutions are inclusive, transparent, and ethically aligned with the diverse needs of the users.
In conclusion, the ENF represents a powerful physics-based security primitive that uniquely connects virtual operations to tangible physical phenomena. Although not a standalone solution, the ENF will play a critical role in a multi-layered, context-aware, and ethically grounded cybersecurity paradigm. As the Metaverse continues to evolve into a decentralized nexus for industrial operations, financial transactions, and human interaction, the ENF provides a viable and verifiable mechanism to ensure that these environments remain secure, trustworthy, and resilient.