Abstract
The swift evolution of information technology and growing connectivity in critical applications have elevated cybersecurity, protecting and certifying software and designs against rising cyber threats. For example, software and hardware have become highly susceptible to various threats, like reverse engineering, cloning, tampering, and IP piracy. While various techniques exist to enhance software and hardware security, including encryption, native code, and secure server-side execution, obfuscation emerges as a preeminent and cost-efficient solution to address these challenges. Obfuscation purposely converts software and hardware to improve complexity for probable adversaries, targeting obscure realization operations while preserving safety and functionality. Former research has commonly engaged features of obfuscation, deobfuscation, and obfuscation detection approaches. A novel departure from conventional research methodologies, this revolutionary comprehensive article reviews these approaches in depth. It explicates the correlations and dynamics among them. Furthermore, it conducts a meticulous comparative analysis, evaluating obfuscation techniques across parameters such as the methodology, testing procedures, efficacy, associated drawbacks, market applicability, and prospects for future enhancement. This review aims to assist organizations in wisely electing obfuscation techniques for firm protection against threats and enhances the strategic choice of deobfuscation and obfuscation detection techniques to recognize vulnerabilities in software and hardware products. This empowerment permits organizations to proficiently treat security risks, guaranteeing secure software and hardware solutions, and improving user satisfaction for maximized profitability.
1. Introduction
In today’s interconnected world, the distribution of modern software applications is increasingly threatened by financial losses due to reverse engineering [1]. Reverse engineering refers to the process of understanding a system, object, or device by analyzing its structure, behavior, and functionality [2]. Once software is released, it becomes difficult for companies to maintain full control over who accesses and modifies their source code [3]. Competitors or malicious actors can exploit this access to gain unfair advantages, often without investing the same level of resources as the original developers [4]. The effectiveness of reverse engineering depends largely on the time and resources available to the attacker. This reality has driven software and hardware industries to adopt advanced techniques to protect their intellectual property. Among these techniques, code obfuscation stands out as one of the most widely used and cost-effective methods to deter unauthorized access and manipulation [5].
To face these threats, one of the most effective and hugely adopted techniques is code obfuscation. Code obfuscation is recognized to be the most popular and operative to inhibit barred reverse engineering method [6]. Code obfuscation includes executing a set of conversions on software and transforming it to a more difficult form to reverse engineer, which preserves the unmodified software’s working with a feasible overhead [7,8].
The core purpose of code obfuscation extends beyond transformation—it helps safeguard valuable assets within the software. The principal inducement for code obfuscation is to conserve as much as possible any intellectual property, like data structures and algorithms, ingrained in a software application that is being vented and dispensed [2,9]. Promoting the bar for reverse engineering, code obfuscation efforts attempt to stiffen, in terms of resources and time, the taking-apart actions conducted by automated approaches and probable enemies [5].
Given its protective feachers, obfuscation has gained significance across several sectors and use cases. Obfuscation approaches, involving software, hardware, or hybrid techniques, have become progressively vital in several fields of our modern life. In the domain of cybersecurity, software obfuscation has a crucial role in preserving critical data and intellectual possession. It is inclusively implemented in protecting mobile applications [10] and online platforms, prohibiting reverse engineering and prohibited access [11]. It is applied to protect the intellectual property of software companies that spread their applications; obfuscation is usually utilized to preserve sovereign algorithms and inhibit reverse engineering of the code [12].
Beyond cybersecurity, obfuscation also plays important role in commercial and financial software. Software obfuscation is also utilized in financial apps to protect crucial functions like transaction processing from hackers [13]. Moreover, it can be utilized to apply licensing agreements by making it more difficult to change within the application [14]. Distinct commercial software applications like Adobe Photoshop obfuscate parts of their code for license validation. Furthermore, several cryptographic primitives which are low-level cryptographic techniques can also directly originate from software obfuscation [15].
However, software obfuscation can also be utilized with pernicious intent. Cybercriminals usually utilize obfuscation to lash the real target of their malware and avoid discovery by security software like antiviruses [16].
Hardware obfuscation, on the other hand, locates significance in protecting physical components of sensitive systems like IoT devices and smart foundations [17,18]. This confirms to the safety of embedded systems and alleviates risks related to tampering or prohibited manipulation. In the field of smart homes, hardware obfuscation protects connected devices, guaranteeing that they are difficult to tamper with or gain improper access [19]. Additionally, in the domain of consumer electronics, like smartphones, hardware obfuscation confirms the privacy of imperial technologies and advocates against unauthorized access [20]. For automotive systems, hardware obfuscation is primary used for preserving the integrity and protection of smart vehicles, inhibiting pernicious intervention with sensitive functionalities [21].
Hybrid obfuscation approaches, which integrate elements of both software and hardware obfuscation, are especially significant in protecting sophisticated and interconnected systems like smart cities and autonomous vehicles. By integrating these obfuscation approaches, modern life applications profit from improved cybersecurity measures, maintaining confidentiality, preserving crucial infrastructure, and promoting a more flexible digital ecosystem. The general applications of software, hardware, and hybrid obfuscation are explained in Figure 1.
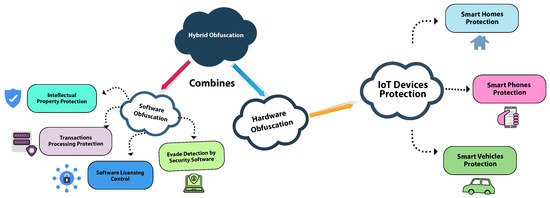
Figure 1.
The general applications of software, hardware, and hybrid obfuscation.
In this article, we introduce a review of the literature covering the divergent classes of obfuscation strategies researchers utilize to protect the intellectual property of software/hardware applications against distinct attacks. These techniques involve software, hardware, and hybrid applications. Moreover, we compare these methods based on obfuscation methodology, testing process, efficiency in protecting intellectual property, disadvantages, usability within the market, and future opportunities for enhancing these techniques.
As a revolutionary departure from traditional research approaches, this seminal comprehensive article investigates obfuscation, deobfuscation, and obfuscation detection in depth. Prior research has frequently concentrated on specific elements of obfuscation, deobfuscation, and obfuscation detection. However, the present study offers a comprehensive viewpoint on the complex interrelationships among these phenomena. The review elucidates the interrelationships and dynamics among obfuscation, deobfuscation, and the detection of obfuscation.
Furthermore, the study is notable for its comparative analysis and valuable insights into research endeavors pertaining to the detection of obfuscation, deobfuscation, and the overall extent of obfuscation. Hybrid obfuscation is among the software and hardware topics examined in the survey. Exploring the complex mechanisms of each domain illuminates the myriad of potential applications, practical implementations, and scientific endeavors within these interrelated fields. Academics, professionals, and fans alike may find this synthesis of concepts beneficial when it comes to obtaining a comprehensive understanding of the extensive domain of obfuscation and its associated subjects.
Deobfuscation, obfuscation, and obfuscation detection are concepts that are notoriously complex. However, this study addresses that knowledge deficit by providing a concise yet thorough synopsis of the principal discoveries derived from meticulous investigation. The survey streamlines the complexities associated with obfuscation, deobfuscation, and obfuscation detection studies, hence facilitating comprehension for persons of varying degrees of competence. We hope that other disciplines will begin to take note of these emerging fields of research, which directly affects their potential effect. Additionally, we review the literature on the diverse kinds of obfuscation, deobfuscation, and detection approaches and compare them.
We are concerned in this research project with providing a comprehensive survey of obfuscation, deobfuscation, and obfuscation detection techniques. This review supports software companies in selecting suitable methods to protect intellectual property, identify potential security gaps, and enhance the reliability and competitiveness of their products [22].
This document is arranged as follows: Section 2 compares and contrasts various software obfuscation techniques and their uses; in Section 3, we learn about hardware obfuscation techniques and how they work. In Section 4, we see examples of hybrid obfuscation techniques and how they work, and we compare them to the other methods. Section 5 also discusses deobfuscation techniques and their implementations with a comparison between them. Section 6 introduces information about the obfuscation detection approaches and their usability, with a comparison between them. At the end, Section 7 will include suggestions for future work for our research project.
2. Methodology for Literature Selection and Analysis
As we aim to provide a comprehensive review of obfuscation techniques in hardware, software, and hybrid domains, we carefully started selecting relevant literature sources from widely recognized academic databases. We searched platforms such as IEEE Xplore, ACM Digital Library, ScienceDirect, SpringerLink, and Google Scholar, using keywords related to hardware obfuscation, software obfuscation, hybrid approaches, detection methods, and deobfuscation techniques. Our search was primarily focused on the literature published between 2010 and 2024 to ensure that the analysis included recent advancements and relevant modern practices.
We refined the selected sections through peer reviewing journal articles and conference papers that focused on obfuscation techniques, their detection or reversal, and their practical usability or related security challenges. We excluded studies with no evaluation or clear methodologies related to the obfuscation techniques. We did not consider publications that were published in languages other than English.
After selecting the suitable literature, we categorized the papers according to their focus area (hardware obfuscation, software obfuscation, or hybrid techniques) or whether they focused on obfuscation, detection, or deobfuscation. We then examined the methodologies and compared their effectiveness, challenges, and usability considerations reported by authors. We organized the information into tables to compare and summarize the findings in narrative form.
To ensure the reliability and consistency in assessing the current state of obfuscation research, we worked in groups of two reviewers to address the methodologies and discussed the disagreements accordingly. Our review aims to highlight the advances and ongoing challenges in this important field.
3. Software Obfuscation
Software obfuscation is the first type concerned with obsecuring the data, control, and layout of the software’s genuine implementation and providing a semantically similar but novel performance [23]. There is no popular official definition for code obfuscation. It is a conversion procedure to change one code into another with the same features as the old code [24]. It can also be handled as an executable that includes encrypted parts and a simple code part to decrypt the encrypted code part [5]. Software obfuscation is grouped into four kinds [25] depending on the objective of obfuscation, as indicated in Figure 2.
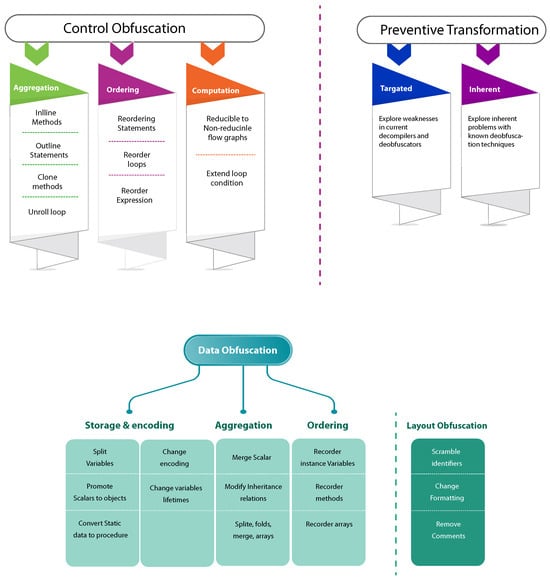
Figure 2.
Categorization of obfuscated communication [25].
- Control Obfuscation: This indicates the obscuring of the control flow of the software. This obfuscation method type is primarily dynamic, depending on self-modulating code.
- Data Obfuscation: It prohibits the extraction of information from data. Data obfuscation methods are variable splitting, array splitting, modifying the range and lifetime of data, etc.
- Layout Obfuscation: It indicates obscuring the software’s layout by, for example, removing comments, variables renaming, modifying the style of the source code, and eliminating debugging information by covering the linguistic structure of the software.
- Preventive Transformation: Based on debuggers’ or disassemblers’ vulnerabilities, this method alters the software such that the code itself will impose the debugger or disassembler to failure.
Many research papers were concerned with implementing software obfuscation techniques. In the following, we will discuss some of these research works, and we will also provide a comparison between the most recent ones.
3.1. Control Flow Obfuscation
The literature reveals a wide range of techniques employed in control flow obfuscation. Some of these previous approaches are discussed below.
A method for controlling flow obfuscation in FJ, with the exception of handling, is presented [26], which is based on a continuation passing style (CPS) source-to-source conversion. The author argued that attackers exploit context-insensitive static examination or context-sensitive examination with a constant call string loss accuracy when using the proposed CPS conversion on Java source codes. In comparison to attacks that employ static control flow analysis, particularly context-insensitive analysis, he claims that control flow obfuscation is the more efficient method.
The power shortage of the Obfuscator-LLVM (OLLVM) obfuscation technique in control flow protection and the cavity in identifier obfuscation is handled by providing two comprehensive classes of improvements [27]. In control flow obfuscation, the authors appended nested switches at the control flow scale and appended the switch structure another time in the flattened code to maximize the complication of the source code while impeding current scripting attacks; then, they suggested in-degree handling for bogus blocks to optimize the distraction of bogus blocks. At the scale of identifier obfuscation, four techniques were provided to bridge the cavity of OLLVM in identifier obfuscation. They compared their approach with OLLVM, which hugely enhanced the genuine control flow complication in obfuscation impact and exchanged 65.2% of custom identifiers while ensuring software performance. Moreover, the time overhead which resulted from obfuscation was nearly frivolous. The overhead of space came out to 1.5 times. Their technique was implemented to source codes against scripting attacks.
One study introduced monitoring to the effect of obfuscation toward protecting against human offensives [28]. The primary goal of this approach was to evaluate how obfuscation prohibits or borders the attacker’s capability to recognize or understand and to change or conduct any adjustment to the code. As part of the study, the control flow type of obfuscation was one that uses opaque predicates baring code offensiveness. The results of their approach’s statistical research revealed that perhaps the presence of source code obfuscation could hinder the ability of an adversary to complete the comprehension mission by sevenfold. Consequently, the control flow obfuscation significantly hindered subjects’ capacity to execute comprehension missions accurately, whereas modulation tasks lacked any crucial variation. Additionally, their methodology demonstrates that source code obfuscation lengthens the time necessary for objects to modify or execute modulation, as well as identify the source code.
A method for obfuscating the system behavior of the software both within and between functions is presented in reference [29]. This method includes separating shows evidence from the actual function and reusing them in distinct functions. To decipher code segments from different functions, it will be necessary to utilize a function-scale scrambled version of the authentic software. Possessing the authentic code complicates software disassembly by a backward engineer. The authors noted that their method distinguishes itself from other control flow obfuscation techniques by permitting a nested obfuscate, which makes engineering more difficult. The results obtained from implementing their method suggest that it effectively withstands automated attacks originating from reverse engineering kits like IDAPro. When contrasting their method with alternative control flow obfuscation techniques, they demonstrated that their approach yields superior results in terms of control flow error and time and space overheads.
A method named TPMDWM is provided in reference [30] to strengthen software copyright enforcement by integrating Trusted Platform Module technology with hash functions, database watermarking, and AES encryption. This technique efficiently restricts unlawful copying during software installation or license updates without changing the genuine code or control structure. The authors indicated that TPMDWM also minimizes dongle costs and enables client identification, granting substitutes for conventional security approaches.
Code Obfuscation through Overloading and Preservation of Semantics (COOPS), a code preservation method founded on ambiguous semantics, was introduced in reference [31]. Software semantics, which consider functions to be a fundamental component of software on a semantic level, forms the basis of COOPS. In situations where the true semantic scale of the software is compromised, a switch interfunction calling establishes a link with the intrafunction control flow. The outcomes of their method demonstrate that COOPS has a higher impedance than propinquity methodological approaches, such as Asm2vec, and has the capability to efficiently modify the control flow architecture of software. The grade difference between the software calling connection prior to and subsequent to obfuscation exceeded ninety percent. The COOPS-manufactured reverse analyzer significantly reduced the expense of reverse engineering code and identified more condensed functional components. In contrast, COOPS is responsible for both outlining and inlining, and the obfuscation technique is not overly complex.
The authors in the following described study proposed the notion of profound control flow [32], wherein an analogous loop model for the linear chain is generated using the callback method. The fundamental component of software functionality is transformed into a method of interprocessing that initiates reverse engineering. The approach they take integrates thorough analysis of control flow to create a resilient callback-method-based control flow obfuscation technique. They provide evidence in support of functional uniformity. By applying the function-calling fusion technique with care, a more intricate function-calling operation is accomplished, thereby augmenting obfuscation. In their conclusion, the authors employed an OpenSSL and SPECint-2000 performance indicator as an evaluative set to demonstrate the potential of the concept, structure, and the interprocess method that initiates reverse engineering and is converted from the fundamental block in the software operation. The callback method was employed to create a corresponding loop structure, and the fundamental software operation block was converted into an interprocess method to facilitate reverse engineering. Their methodology incorporates comprehensive analysis of data flow dependence and control flow, wherein a callback-method-based data flow obfuscation method can be developed that is robust. The authors furnished substantiation of its functional uniformity. A more sophisticated function-calling operation was achieved through the careful application of the function-calling fusion technique, which enhances obfuscation. The authors used the OpenSSL and SPECint-2000 performance indicator as an evaluation set to show how well and how useful the proposed idea could be.
An obfuscation technique is provided depending on the instruction segment variation and control flow randomization [33]; distinct equivalent conversion principles create various instruction segments, and random functions are utilized to choose one fulfillment track from the diverse extensions of software. Then, the software is repeatedly obscured. The outcomes of their approach indicate that various instruction segments and multiway components could maximize the hardness of static reverse interpretation, wherein randomly chosen multipath branches will maximize the obstacle of dynamic instruction tracking, and repeated conversion many times improves the hardness of the control flow graph.
Ref. [34] presents a novel dynamic obfuscation technique known as Control Signal Encryption (CSE), which operates by integrating a management table encryption, control logic, and signals management table (MT). This triplet swaps and conceals the software for the monitoring graph. Subsequently, the MT is produced, which comprises addresses that facilitate the linkage between software instructions. To encrypt the MT, stream cipher symmetric encryption (Spritz) is implemented. To assess the proposed obfuscation technique, two traditional goal functions (cost and Mishra) are taken into account in addition to six performance metrics that support a multigoal method (capacity and flexibility). The proposed multigoal approaches were therefore implemented on a minimal software application dataset. The results suggest that CSE possesses ambitious attributes in comparison to alternative methodologies.
3.2. Data Obfuscation
In the advancing landscape of data protection and privacy, data obfuscation has garnered important attention as a vital technique to protect critical information. Some of the previous research in this field are explained below.
A novel approach for maintaining location secrecy that utilizes a trajectory obfuscation Location Privacy-preserving Mechanism using Trajectory obfuscation (LPMT) was introduced in [35]. The LPMT obtains the obfuscated GPS positions by employing the following steps: first, it elicits the stay positions as path characteristics utilizing the sliding window technique; second, it applies the exponential method to obscure each stay position to a goal obfuscation subarea; finally, it performs Laplace sampling within the goal obfuscation subarea. The outcomes of a comparison between the authors’ method and the baseline techniques indicate that LPMT is capable of reducing data quality degradation by over 20% to keep the same quality results. This demonstrates that LPMT possesses the attributes of a premium service and robust protection.
In reference [36], variational autoencoder (VAE) is proposed as a picture obfuscation method that is used for random non-prepositional pixel density mapping in order secure medical photographs. This method is subsequently applied to the construction of DL-based resolutions. The researchers implemented a classifier model on supervised cardiac angiographic frames in order to assess the benefit of obscured images during model training. Two potential offensive strategies were employed to assess the level of protection in comparison to reconstruction efforts based on artificial intelligence (AI). Protection against human conception was quantified utilizing symmetry metrics. Furthermore, adept readers employed visual estimation to specify the extent to which the reconstructed images remain true to the human concept. The method they have developed effectively enables deep learning models to process obscured images with minimal computational effort while also ensuring protection against AI-based reconstruction attacks and human vision detection.
A consecutive and collusion-elastic data obfuscation technique called PriMask was presented in [37]. This technique enables mobile devices to utilize cloud deduction services. By employing this methodology, the mobile device is solely responsible for executing a reduced-size neural network known as MaskNet in order to hide the deduction data and then send the information that is found to the cloud. This feature enables the safeguarding of specific, unique information that may be present within the deduction data. The authors created a segmented oppositional active learning to train a neurological network and make MaskNet work on multiple mobile platforms. MaskNets come in a lot of different types, which makes them easy for mobile devices and the cloud to work together. PriMask is used for mobile observation tasks: figuring out how drivers act, sensing crowds around civil circumferences, and figuring out how things affect people. The results of their methodology demonstrate that PriMask is highly effective at safeguarding confidentiality while maintaining the precision of cloud deductions.
DP-Shield is an interactive approach for face photo obfuscation under the strict concept of differential privacy; which was introduced in [38]. The authors mentioned that their system offers their newly suggested obfuscation techniques, namely, DP-Pix and Differential Privacy-Singular Value Decomposition (DP-SVD), and involves two substitutional comparison techniques. They also stated that the audience will be capable of understanding current DP techniques by interacting with them by utilizing real-world face image datasets. Moreover, DP-Shield combines exceedingly used photo quality metrics and practical privacy risk metrics to clarify the effectiveness of their approaches.
A technique and experimental research for obfuscating sentences is offered [39]. The obfuscated sentences transmit syntactic information from the genuine sentence. The authors mentioned that their neural approach exceeds a robust random baseline in parsing precision when several words in the sentence are obfuscated. Moreover, their neural technique resorts to exchanging words in the genuine sentence with words that have a nearer syntactic task to the genuine word than a random baseline.
A novel obfuscation method to protect data privacy was developed [40]. The authors stated that their technique achieves a high percentage of protection degree. It takes less time for obfuscation and deobfuscation operation in contrast to current methods, where data are being encrypted and uploaded to an online storage. By using their technique, data privacy is preserved in cloud storage. Therefore, protection is improved using their suggested obfuscation approach.
To enhance cloud data protection, the authors proposed MRADO, a confidentiality-enabled obfuscation method [41]. They used word-by-word and line-by-line obscuration to implement their method in plaintext. When put into practice, their method reduces the amount of obfuscated data in comparison to the existing MONcrypt method. As a result, the lowest amount of data is needed to be sent to the server. The information kept in Google Cloud was used to figure out how much MONcrypt and MRADO encrypted text costs. When compared to the MONcrypt approach, their results showed that their strategy improves the protection of data. It also minimized expenses during cloud uploads.
A variable encoding data obfuscation technique was provided [42] that utilizes a secret sharing method. Using their method, an integer variable is encoded by utilizing number theory depending on Shamir’s Secret Sharing technique. The authors showed that their obfuscation method is flexible to slicing attacks. It can be used to preserve critical information utilized in military applications and conserve digital content under Digital Rights Management (DRM) preservation.
Nearest Neighbor Data Substitution (NeNDS) is a novel suggested obscuring approach [43]. It has robust privacy-protecting properties and protects data clusters. The authors also determined a property named Reversibility for the classification and examination of data obfuscation tactics, according to their elasticity to reverse engineering. They also confirmed that cluster-protecting geometric conversions, by themselves, are much easier to reverse engineer.
A plain and efficient method for obfuscating data while permitting the efficacious fulfillment of range queries was introduced in [44]. The authors explained that by using their approach, each range query is translated into a series of equivalence queries consisting of two portions. The first portion is logarithmic in the number of database entries and determines the entry closest to the range query border. The second portion is linear with respect to the number of database entries in the coveted range. One by one, it gathers all the components of the query answer. The server cannot differentiate the queries related to the series from other parity queries it may encounter, making the statistical rebuilding of the plaintext value harder.
A framework for obscuring critical information to preserve individual confidentiality and protect the information content needed for cooperative filtering was presented in [45]. The authors demonstrated that their technique depends on covering the user information and ratings information database so that aggregates of identical data are secured while stashing the factual values. Afterward, a centralized CF server receives these obscured data to produce anticipations. An empirical test of the fulfillment of distinct CF mechanisms on the obscured data confirmed that their offered method for confidentiality protection does not affect the precision of the predictions. Several E-commerce platforms can exchange information securely by utilizing their proposed approach. A collaborative CF server is utilized for planning issues such as cold-start circumstances encountered by novel E-commerce sellers. It is also used to plan tendentious outcomes as a result of incomplete users. They depicted a central CF server technique in a way that establishes testaments by fostering the data acquired from several origins. Their technique can only be utilized among an identified community such that an active individual searches for details. It permits supplying users with automated suggestions using a particularity-securing mode, which affirms an individual’s confidentiality. It is also utilized for exchanging data between diverse meta-marketplaces for data for reciprocal earnings.
A confidentiality-conscious obscuring technique for web data was provided in [46]. The researchers utilized a probabilistic approach to anticipate the confidentiality risk of web data that combines all significant confidentiality sides: genuineness, consistency, and linkability. Using their approach, the web data with large anticipated hazards are obfuscated to reduce the particularity hazard by utilizing semantically identical data. Their approach is reluctant versus the enemy, who has information about the datasets and models’ learned risk probabilities using differential confidentiality-based noise extension. The empirical study applied to two actual web datasets supports the importance and effectiveness of their approach. Their outcomes indicated that the average confidentiality risk amounted to 100%, with a minimum of 10 critical web entries. In comparison, at most, 0% confidentiality risk could be achieved with their obfuscation technique at the cost of an average utility loss of 64.3%.
A method for obscuring data in outsourcing grid multiplication to cloud computing was presented in [47]. It mainly depends on dividing the columns and rows of matrices to change their factual scale connected with inserting irregular disturbance and mixing to guarantee particularity and secrecy. Using this technique, obscured grids are submitted to servers lacking cryptography of the public key. The server cannot reduce factual values from obscured arrays or calculated multiplication outcomes during computing matrices. In contrast, clients can mitigate factual calculated values by utilizing a very trivial processing load from outputs generated by the server.
For the cloud–fog–IoT situation, an encryfuscation method has been suggested that uses both obscuring and cryptography methods [48]. The adequate confidentiality protection method for a given service demand is selected based on the fundamentals of the offloading choice. The authors stated that the decision to offload depends on the service’s hazard level. Moreover, the researchers give two ways to hide data and locations to protect privacy. MATLAB R2021a was used to simulate them. The method for hiding data was compared to Base32, Base64, Hexadecimal, and MONcrypt. The method for hiding locations was compared to SLOT and ESOT. Applying their tactic at the Secure Service Offloader (SSO) layer supplies the advantage of not requiring reliance on the fog or cloud. Moreover, reverse engineering the obscured information is a harsh task for opponents because of utilizing the obfuscation technique. It also averts the authorization problems encountered by the masking techniques.
A novel technique for data preservation was provided in [49] by utilizing automated machine decision-making techniques to distinguish data and choose the proper data obfuscation method. The suggested approach uses natural language processing capacities to test input data and choose the best action path. It can also learn from former experiences, enhancing itself and minimizing the risk of erroneous data classification.
A privacy method for safeguarding data saved in the cloud, MONcrypt, was introduced in [50] as an (SSA). Depending on the data obfuscation method, the proposed privacy method changes. Security as a Service (SEaaS) is beneficial to the MONcrypt SSA. Users have the option to utilize SEaaS’s protection service at any time to safeguard their data. To test the safeguarding of the suggested MONcrypt SSA, simulations were run in a cloud environment (Amazon EC2). To compare the proffered and existing obfuscation methods’ preservation levels, a protection testing tool was employed. The authors looked at MONcrypt in comparison to other popular obfuscation methods such as Base64, Base32, and Hexadecimal encoding. The results show that their system is more secure and produces better results. In addition to minimizing the volume of data uploaded to cloud storage, MONcrypt is different from the current approach.
3.3. Software Layout Obfuscation
Software layout obfuscation has evolved as a critical facet, targeting to strengthen applications against reverse engineering and unauthorized access. A review of previous research works in this field is discussed below.
A software-based, economical resolution that reduces the opportunity to activate a multiphase trigger Hardware Trojan was suggested in [51]. The technique depends on a pure-software obfuscation approach, which utilizes an evolutionary method to alter an executable code with no impact on its functionalities. This obfuscation can preserve crucial infrastructures and processes with a minimized and foreseeable lack of performance. The suggested method was tested versus a renowned real-world hardware offensive, obtaining affirmative and hopeful outcomes regarding its efficiency.
A novel obfuscation method that accomplished better identifier scrambling was provided in [52]. Depending on this technique, many methods were presented to generate more challenging to recognize bytecode and, occasionally, produce decompiled code that cannot be recompiled. According to the authors, their main method gives an identifier as much information as possible. When they use their method, an identifier is recognized not only by its name but also by where it is found. This makes the hacker nervous. Another advantage is the bytecode is smaller since it is long, its descriptive names are swapped out for short ones, and they hide the compilation errors. This is will make the process of reverse engineering the bytecode and crack it much harder. These methods and the core technique make it harder to rift a Java bytecode file. In addition, the runtime effectiveness of software that is obscured is also improved.
A method for binary obfuscation using signals was developed in [53]. By making static machine code untangling difficult, it solves the problem of reverse engineering binary programs. Several control transfers are converted into signals, and “junk” instructions are appended after the signs to obfuscate the binary. The code that is generated is still valid, but not even the most advanced disassemblers can decipher forty percent to sixty percent of the instructions within it. The obscured program runs slower than the genuine one, and the disassemblers incorrectly recognize more than half of the control flow edges.
A new obfuscation technique of software is suggested [54]. The authors stated “that even with the help of reverse engineering techniques, it would be harder for an enemy to figure out how to use their app”. As a way to make reverse engineering binary software harder, they came up with a suggestion. The assembly code that the compiler makes was changed using their obfuscation method. To hide the program’s control flow, they used a method that moves pieces of code from different parts of the software to other parts of the code. Moving control from the old code to the new code is more interesting when dynamic junk is added. As a result, the obfuscation method keeps the meaning of the original code. The results of their experiment show that their algorithm works better than other obfuscation techniques and better than reverse engineering tools. Because of how the instructions and program parts are shown by the obfuscation technique, the software is the most time- and space-consuming it can be.
3.4. Preventive Transformation
Preventive transformation has acquired significance as a strategic technique to support digital systems against probable threats before they occur. Some of the prior research works in this field are explained below.
The elementary disassembly stage was studied in [55]. The authors aimed to disturb the static disassembly operation to make the software more difficult to disassemble appropriately. They demonstrated two vastly utilized static disassembly tactics: linear sweep and recursive traversal. They debated methods to disturb each other. Empirical testing using the SPECint-95 benchmark suite shows that essential parts of executables that had been obfuscated by utilizing their methods were disassembled incorrectly, which refers to the efficiency of their techniques.
To produce more sophisticated reverse engineering, a code obfuscation method was proposed in [56]. The authors stated that it is hard to reverse engineer code that uses both design-level obfuscation and self-modifying code at the same time. They put their method to the test by utilizing diverse sorting techniques. The outcomes of their empirical work muddy the waters regarding obfuscation level, code slip, performance time, and code size.
Figure 3 is a summary of the latest studies on software obfuscation, and Figure 4 displays the methods in use today. Table 1 also compares these methods according to their obfuscation category, testing, market usability, and potential future enhancement opportunities.
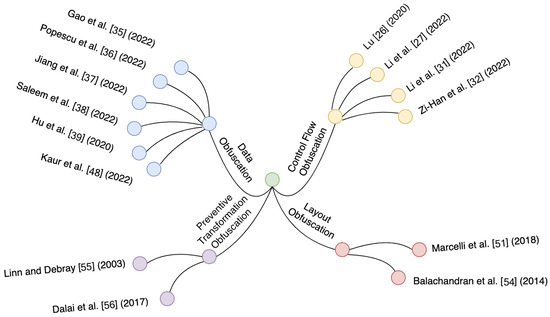
Figure 3.
Most recent software obfuscation research.
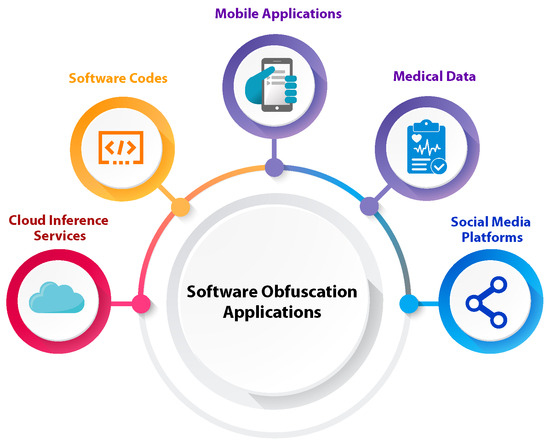
Figure 4.
The current applications of software obfuscation.

Table 1.
Software obfuscation techniques comparison.
Across these methods, recent research continues to explore the tradeoffs between the strength of obfuscation and software performance. The challenge remains to balance protection with usability and ensure that obfuscated software can still operate efficiently across platforms and environments. Notably, recent advancements such as the work by Greco [57] have shifted focus toward enhancing detection capabilities through machine learning rather than solely strengthening obfuscation. Their framework employs eXplainable AI (XAI) with XGBoost and SHAP values to detect common obfuscation techniques—such as control flow flattening and instruction substitution—in large-scale binary datasets. This approach not only achieves high detection accuracy across architectures but also provides interpretable insight into how obfuscation affects code features. By identifying transformation-invariant characteristics in binaries, this line of research reveals opportunities to improve both the detection and design of obfuscation schemes that are resilient yet efficient, pushing the field toward more intelligent and balanced security mechanisms.
3.5. Summary and Challenges
Software obfuscation remains a foundational tool in software security. While control flow and data transformations offer effective deterrents, they also introduce challenges in debugging, maintenance, and cross-platform compatibility. Preventive measures, although strong against reverse engineering, may impair performance or raise false positives during antivirus scans. A major ongoing issue is that once a particular obfuscation method becomes widely understood, tools and techniques evolve quickly to counter it. Furthermore, modern machine learning techniques are increasingly able to identify patterns in obfuscated code, suggesting that future solutions must incorporate dynamic and AI-resistant approaches. There is also a need for standardized benchmarks to evaluate obfuscation strength more consistently across research efforts. Emerging approaches in 2024–2025, such as explainable machine learning models for obfuscation detection and architecture-agnostic binary analysis, demonstrate a shift toward intelligent, interpretable security solutions.
4. Hardware Obfuscation
Hardware obfuscation is an effective solution commonly employed to counter various hardware security threats, such as piracy, reverse engineering, cloning, chip overproduction, and Hardware Trojans [58,59]. This technique offers a robust way to hide the system architecture from potential adversaries, even when the intellectual property (IP) is in an unencrypted format. The security provided by obfuscation lies in the ability to obscure the implementation and system structure [60].
Hardware obfuscation can be categorized into two main types based on the hardware being targeted:
- DSP Core Hardware Obfuscation:This type of obfuscation involves a high-level transformation of the data flow graph representation of a Digital Signal Processing (DSP) core into an obscure format, making the structure unclear at the register transfer level (RTL) or gate level. This technique is known as “Structural Obfuscation”. Another variant of this approach is called “Functional Obfuscation”. Functional obfuscation employs key bits, often using AES and IP core locking blocks (ILBs), to prevent the DSP core from functioning unless the correct key sequence is provided. If the incorrect key is used, the DSP core will either produce incorrect results or not function at all [61].
- Combinational/Sequential Hardware Obfuscation: This type of obfuscation involves making changes to the gate-level configuration within the circuit itself [62,63].
Several studies have focused on implementing hardware obfuscation techniques. In the following sections, we will discuss some of these studies and provide a comparison of the most recent and innovative approaches.
4.1. DSP Core Hardware Obfuscation
Previous research works in this field include a scope of creative approaches targeted at obfuscating the hardware implementation of DSP cores, setting up a basis for improving robust hardware designs in the context of DSP. Some of these research works are described below.
By using improved logic locking and encryption, the authors in [64] presented a contemporary obfuscation operation for DSP cores that, in comparison to cutting-edge strategies, sustains lower design overhead and fulfills diminutive design costs. Their proposed approach integrates PSO-DSE, a design space exploration system, with DSP obfuscation to achieve sustained design costs. Every bit of practical resource data can be securely locked with eight key bits using locking blocks, which provides improved locking protection. Key awareness attacks, such as SAT attacks and removal attacks, are countered by the offered technique. Compared to a modern technique, the findings indicate that the suggested strategy enhanced obfuscation protection by a factor of and reduce design costs by approximately 6.5%.
In [65], the research focused on circuit obfuscation as a hardware protection metric, focusing mainly on DSP circuits, which are inherent in most novel frameworks. The notion includes deploying coveted and unwanted styles to design obscured DSP functions, which are explained through utilizing Fast Fourier Transform (FFT). Choosing the style depends on adding a key to the circuit; with the accurate key, the process operates merely in its coveted style. Unwanted styles are presented in the design to discompose potential adversaries. The strategy to confuse the structure includes control flow modulations and modifying calculations from the desired style. The authors provided simulations and synthesis on a flexible, two-parallel FFT, examining the efficacy of this method. Their suggested technique yielded an adaptable and elastic structure, with an area cost of 8% and a potential excess cost of 10%. However, a criterion to scale the degree of obfuscation in a structure is yet to be developed.
A new technique for obfuscating transient fault-secured circuits was provided in [66]. The method obfuscates fault-protected DSP circuits so that the tasks of the generated hardware become unclear to an enemy. The suggested method implements hybrid conversions in succession like repeated process removal, resource conversion, and connectivity modification by utilizing tree height conversion, reasoning conversion, etc. They are accomplished with no impacts on the operation of the implicit DSP circuits or demanding important maximization in the silicon footprint. The suggested approach merges an improved defect safety characteristic with multicuts which guarantee extreme discovery ability versus temporary abnormalities in the DSP circuit. The outcomes of this technique refer to more powerful obfuscation and improved defect protection at minimum design cost (avg. decrease APPROX. 14%) in contrast to previous research work.
A modern obfuscation technique within the field of error-protected DSP circuits was suggested in [67]. It utilizes hybrid conversions in consecutive layers to completely change the design’s hardware structure at the register transfer (RT) and gate level without stopping its work or adding any structure costs. The results of this method were achieved without carrying any extra structure expenses; the suggested concealment technique accomplishes the necessary structural conversion at the gate level, like the task, and becomes vague to an enemy.
By employing high-degree conversions, a novel method for protecting DSP circuits from obfuscation was suggested in [68]. The strategy is to make DSP circuits that are more complex to decipher. This marks the initial effort to construct a design flow that incorporates intensive conversions of reiterated data flow graphs; these conversions not only accomplish the area–speed–power tradeoffs but also obscure the architectures structurally and practically. The authors mentioned that there are a wide variety of obfuscation methods, each with promising results from a signal processing perspective but that are flawed in practice. Their suggested method fulfills a high degree of obfuscation with relatively little overhead, according to the empirical results.
A modern technique for functional concealment in DSP cores IP locking blocks and key cryptography functional components has been used to show this. It includes a secure hash functions block, ILB key insertion logic, and feed hash buffer logic [69]. This strategy supplies improved protection versus removal attacks and key-sensitization attacks while preserving a low gate count and potential. The outcomes show that the suggested concealment technique supplied a reduction rate of 25.86% in gate count and potential and an average improvement of 43.75% in protection (obfuscation) compared to the current method.
A modern approach for protecting DSP-based IP cores versus the modification of RTL description and IP privateering was proposed in [70] by utilizing hybrid configurational obscuring and encoded chromosomal DNA impression technique. The suggested approach was tested by qualitative and quantitative analysis. It was confirmed to be a more robust and smarter protection than current identical works. It is more powerful than new appearance biometric and steganography-based hardware IP preservation methods for more substantial proof of digital clue and tamper tolerance capability. It also bears zero design cost overhead.
A hardware obfuscation method to conserve DSP IPs versus privateering and reverse engineering while supplying a significant elasticity to key bit faults at small hardware overhead was offered in [71]. This technique allows for exchanging the validity of key bits with outcome Quality of Service (QoS) and supplies agile degeneration in the QoS while maximizing the bit error rate (BER) in the key. The authors also provided a comprehensive technique and built a CAD instrument for the automated obscuring of a structure. They also stated that the consequent obscured structure is preserved versus whole prime renowned offensives. The application outcomes refer to the fact that the overhead of their technique is significantly lower than the error correction code (ECC); despite bit defeats in the key, it continues to supply the proper functional attitude of an obscured design. It gives an adjustable operation that permits using distinct specialty degrees for distinct IP clients. It also secures an IP from unreliable examing utilities by providing them with an obscured structure and a fragmentary key that supplies an unsatisfactory tier.
A cost-effective resolution was introduced in [72] for building DSP circuits that are architecturally and operationally obscured through elevated conversion methods. This approach shows that investigating the equality of DSP circuits by utilizing high-degree transmutations will be more complicated if the solution suggests some switches designed in a way that is harder to track. The authors combined a protected configurable switch design in the proposed design scheme to enhance the preservation. They also provided an whole design flow in the suggested obfuscation technique. The designers can also design the distinction styles and the supplementary obfuscating circuits systematically depending on the degree of conversions.
The authors in [73] executed QR code pattern-driven functional obfuscation and tested protection levels; they then suggested a logic obfuscation technique over FIR DSP digital design with little overheads, which prohibits an enemy from reverse engineering both the gate-degree netlist and the layout-degree geometry of the IP/IC. It also keeps people from copying and exaggerating the IP/IC. Their practical assessments explain why the suggested obfuscation method has low potential, area, and no implementation costs.
A new way to hide the structure of a digital signal processor (DSP) IP core during the architectural synthesis structure phase was described in [74]. The authors offered a technique that primarily aims to protect IP cores that include compound loops. The solution approach utilizes five distinct algorithmic level conversion methods: loop-invariant code motion, loop unrolling, logic transformation, tree height alleviation/raising, and repeated process eradication. Every conversion method of these approaches can produce functionally synonymous concealment designs. Using the suggested method for low-cost obfuscation, the design explored design space using multiphase algorithmic conversion and particle swarm optimization (PSO) (DSE). The outcomes of their suggested technique indicate an improvement in the obfuscation of 22% and a decrease in the cost of the obscured design of 55% in contrast to identical previous state-of-the-art methods. It also supplies rapid execution and simple modification to any CAD instrument.
By utilizing a new IP core locking block (ILB) reasoning, which influences the framework of compositional circuits and flip-flops, the authors in [75] introduced a practical obscuration of the DSP core for client electronic procedures. Integrated logic gates (ILBs) are responsible for motivating the correct functionality in a DSP design and locking its functionality using the correct key series. According to their findings, the appropriate keys can be extracted from a muddled design using existing methods, which only require tedious trials. Implementing their suggested work in the first attempt alone will prevent the elicitation of correct keys even on monotonous trials. The suggested strategy significantly diminishes the likelihood of successfully deciphering a practically obscured structure in tedious experiments. Their study’s empirical results demonstrate that the suggested approach surpasses previous efforts in terms of protection while requiring less design overhead.
A QR pattern-enabled key-driven technique was proposed by the authors in [76] to alleviate privateering challenges in digital design, hardware protection, and reverse engineering (RE) through obfuscation operation. In addition to the fact that structural changes cannot provide sufficient IP preservation for the gate-level netlist cores or the IC compositions, they also noted that these methods can achieve preservation with massive resource employment and potential exhaustion overheads. Structure and functional obfuscations based on FSM were introduced by the authors to limit these cavities. They figured out how to handle keys by utilizing a pattern driven by color QR codes to randomly extract keys and, ideally, by testing the levels of disturbance metrics. Using FIR DSP digital design, they conducted an empirical evaluation to validate the logic obfuscation technique.
Lastly, the enemy from any reverse engineer operation in two levels, the gate-degree, and the RTL-degree structure of IP from privateering and exaggeration was explored. Their empirical assessments explained the achievement’s low potential, area, and trade over the protection level of the suggested obfuscation method.
4.2. Combinational/Sequential Hardware Obfuscation
This kind of obscuration refers to the hardware concealment technique where the structure alteration and locking technique are completely combined [77]. Generally, this obscuration is conducted at the architectural degree of structure. The locking key is derived from outdoor as major input data or extracted from forgery-resistant persistent recollections on a chip. If the key is chosen as input, the quantity of altered elements or added safeguards is relative to the increase in elementary input data. Typically, the key swap is conducted using an exterior secure encryption protocol [78]. Figure 5 indicates an example of a combinational obfuscation approach.
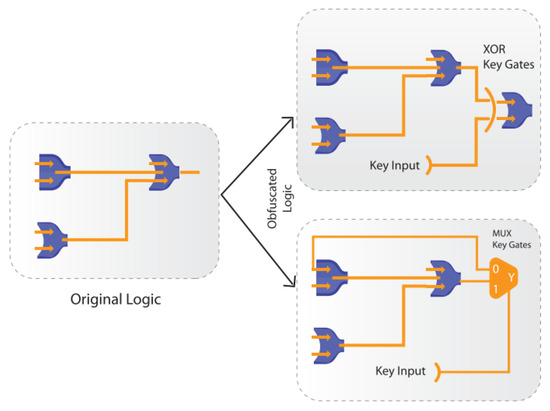
Figure 5.
Example of combinational obfuscation [78].
The sequential obfuscation depends on reasonable alteration of the finite state machine (FSM) in the structure [79]. Scientists provided several techniques to alter the state transition graphs to manage the safeguard key or to conduct configurational modifications [78]. An instance of sequential obscuration is shown in Figure 6.
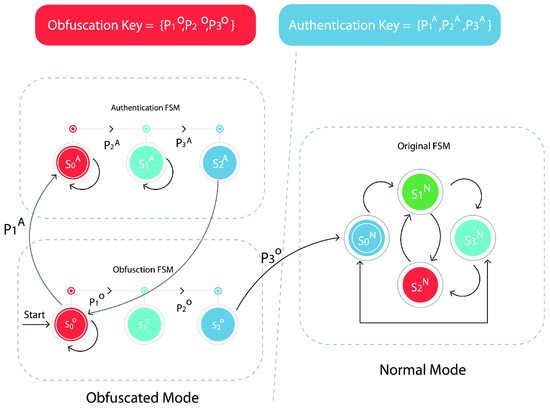
Figure 6.
Example of sequential obfuscation [80].
In the domain of hardware protection, the study of combinational/ sequential hardware obfuscation has been fundamental in fostering digital designs against reverse engineering and intellectual property theft. Previous research works in this field are discussed below.
A method to protect the circuit versus Hardware Trojan insertion was introduced in [81]. It uses a safe reasoning locking technique that relies on the incorporation of key gates during the confusion process. The authors called their method Secure Interference Logic Locking—SILL. Tracks with ultimate fan-out have reduced monitorability. Using their method, circuit obfuscation requires fewer main gates and generates the greatest Hamming distance between typical and ambiguous results. This method uses AES to create the key and adds key gates to the circuit’s confusion.
Their suggested technique, SILL, was emulated in the Vivado emulation environment; the techniques utilized in their approach were intended in VHDL language and prepared to permit concurrent fulfillment and then implemented on the genuine netlist of the ISCAS85 benchmark circuits. After comparing their simulation results with new studies, the quantity of hardware exhaustion dropped (approximately 5% space exhaustion and a 0.15-nanosecond time latency). The authors examined the SAT assault algorithm on ISCAS85 benchmark circuits, which were obscured with SILL. Their suggested technique’s impedance, lower hardware cost, and better rate make it superior against SAT attacks compared to traditional techniques.
A method of logic locking that depends on likelihood to preserve the circuit structure was built in [82]. The suggested method, “ProbLock”, was applied in combinational and sequential circuits by utilizing a crucial chosen operation. The authors employed a screening operation to elect the optimal position of key gates depending on several restrictions. Every stage in the screening operation creates a subgroup of elements for every restriction. They also examined the relationship between each restriction and controlled the intensity of the restrictions prior to adding key gates. They experienced their technique in 40 standards from the ISCAS85 and ISCAS89 suites. They tested ProbLock versus an SAT attack and examined the required duration for the offensive to create a key value successfully. The results indicate that SAT attack demands lengthier durations for most benchmarks by utilizing ProbLock, which confirms practical protection in hardware obfuscation.
The authors in [83] defied the belief that periodic combined circuits are worthless by suggesting periodic combined locking. Then, they suggested polymorphic memristor–CMOS gates to obscure the IC design. Variform gates seem precisely correspondent for anybody with reach to the design involving interior foundry offenders. The structure objective is to have just one practical setup, while the other setups are insignificant.
DFSSD provides a new reasoning locking resolution for FSM and sequential circuits with limited arrival to the testing circuit [84]. The strategy combines Deep Faults and Shallow State Duality, which are two obscuration approaches. They primarily aimed to counter sequential SAT assaults by relying on limited investigation through modeling. Due to the shallow state dualism, sequential SAT assaults cannot employ a tedious unlimited model checker to determine if the offensive can be completed without taking a shortcut for the precocious terminus. In addition, the deep fault provides a way for designers to create deep but recoverable errors that limit model-checker-based attacks, and sequential SAT cannot detect within a practical timeframe. By utilizing a little overhead circuit technique and intentionally making the offensive time too long, the technique enables the designer to accurately manage the fault depth at design time.
Current sequential logic encryption techniques were revisited in [85]. More particularly, the authors presented the protection vulnerabilities of contemporary techniques and introduced various attack approaches to cut off the obfuscation schemes. Elastic sequential logic obfuscation techniques were then argued, outlining the preparatory demands to protect sequential circuits without entire scan-chain access.
A functional reasoning ciphering framework to protect a sequential circuit versus the MC offensive with little circuit modulation was presented in [86]. The authors mentioned in their paper that in the conventional techniques, a circuit within a fault key is planned as a circuit that is fixed wrong, where the consequences of an incorrect key entry may be rapidly discovered at the output. But, using their suggested approach, incorrect key entry guides interrupt mistakes when the circuit arrives at particular states. In this condition, if the offensive does not examine the circuit advisedly, he might incorrectly suppose a that fault key is the proper one.
The authors in [87] confirmed that a series of four processes can achieve any best-probable obfuscation of a sequential circuit: retiming, sweep, resynthesis, and conditional stuttering. Depending on this essential outcome, they also built a key-based obfuscation technique to secure design intellectual properties (IPs) versus privateering. The new obfuscation technique involves a confidential key in the power-up state of the IC that only the IP rights owner recognizes. The IC still works without the key, but its adequacy will be much less. Unlike current IC weight methods, the confidential key in their technique is implicit, so it can also be utilized as an invisible watermark. Prospect attacks and countermeasures were wholly tested on their approach, and the practical outcomes explain the efficiency of their technique.
A modern technique for hindering SAT attacks depending on generating interconnection cyclic ambiguity was provided in [88]. It depends on generating sharply cyclic obscured circuit designs by appending mock tracks to the circuit. The authors mentioned that their technique is viable for IC gild and logic locking. They demonstrated in their research that their approach may be implemented with meager achievement and area overhead. They showed that periodic reasoning locking generated SAT elastic circuits with 40% reduced space and 20% decreased lateness in comparison to an unsteady XOR/XNOR obscuration with a similar key length.
Various polymorphic hybrid memristor–CMOS designs to obscure the IC layout were presented in [89]. These designs seem precisely similar for anybody accessing the IC layout, involving external engineers involved in chip manufacturing. So, the structure objective is to preserve just one operational setup, rendering the other settings insignificant. Empirical outcomes indicate that the overhead of the suggested designs is rational. Then, the authors used the offered polymorphic designs to provide a layered hardware obscuration composed of a test circuit and sequential and combinational obscurations. Their tiered strategy was found to be safe versus non-cyclic and cyclic SAT-based offensives, brute-force attacks on the test circuit, and query-based learning attacks on the entire sequential circuit.
The utilization of three-dimensional incorporation circuit innovation to improve the protection of digital ICs using circuit obscuration was suggested in [90]. The particular three-dimensional technique which was utilized by the authors permits gates and wires on the lowest level and just metal wires on the highest level. By employing a portion of cables on the highest level produced in a credited production facility, they obscured the uniqueness of gates at the lowest level, preventing malign aggressors. They presented an official connotation of protection for three-dimensional incorporation-based circuit obscuration and described the intricacy of computing protection within this connotation. They introduced functional techniques to define the protection degree given a portion of lifted wires and to determine a portion of wires to lift to accomplish a coveted protection degree. Their empirical outcomes on the DES benchmark circuits and c432 permited them to gag the capacity, area, and lateness expenses to fulfill distinct protection degrees. Furthermore, they indicated through a case study including a DES circuit that obfuscation based on three-dimensional incorporation circuits can hugely minimize the capability for an offender to perform a successful assault.
A new approach for hardware obfuscation called dynamic functional obfuscation was provided in [91]. It differs from the present steady obfuscation techniques because the obscuring signals vary throughout time; this generates inconsistent circuit performance when an improper key is entered, making the chip work correctly at times and fail at other times. Their technique generates more powerful obscuration by maximizing the computational complexity of decoding the accurate key by utilizing brute-force attacks, despite more minor keys. Furthermore, the dynamic features of these circuits also render them reluctant to SAT-solver-based offensives and reverse engineering. Their technique was applied to both sequential and combinational circuits. It was tested using protection analysis according to the time intricacy of the aggression and costs related to area, timing, and power.
A novel design approach for hardware IP preservation and authorization by utilizing netlist-level authorization was introduced in [92]. The suggested technique can be incorporated into the SoC structure and production operation to supply hardware preservation to the IP sellers, the designer of the system, and the designer of the chip. Emulation outcomes on ISCAS89 benchmark circuits indicate they can accomplish rising degrees of protection using a well-constructed obfuscation platform at less than 10% area overhead under lateness restriction.
A feasible RTL hardware IP preservation method depending on a key-based obfuscation technique was supplied in [93]. The authors included a small finite state machine (FSM) of a structure to affect its management and data flow. Their method uses CDFG representations of designs and is easily automated. Their proposed obfuscation method protects IP sellers from IP infringement at various stages of integrated circuit design and fabrication while reducing design and processing costs.
A modern, thorough method to end the piracy of integrated circuits (EPIC) was offered in [94]. It demands that each chip be activated by utilizing an exterior key that can be produced by the owner of IP rights and cannot be doubled. The authors stated that their approach depends on automatically produced chip IDs, a new combinational locking technique, and the creative utilization of public key cryptography. Their assessment proposes that the cost of their approach on circuit lateness and power is humble, and the standard flows for investigation and examination do not need modification. They utilized formal techniques to test combinational locking and computational attacks. A thorough protocol analysis indicates that EPIC is amazingly reluctant to several privateering efforts.
Recent work has also explored low-cost implementations that minimize performance overhead while maintaining security, such as using reconfigurable hardware or probabilistic obfuscation techniques. These approaches allow for fine-grained control of design complexity, power consumption, and area overhead—critical factors for embedded and portable systems. Overall, hardware obfuscation is evolving to counter increasingly sophisticated threats. Effective implementations require a balance between security strength, manufacturing cost, and system performance. A notable advancement in this space is the integration of reactive control with obfuscation to enforce privacy through formal guarantees. In particular, a research paper published by Andrew Wintenberg proposes a synthesis-based framework where both control logic and obfuscators are co-designed using formal specifications based on opacity—a property ensuring that adversaries cannot infer confidential behavior from system outputs. His approach models distributed hardware architectures as finite automata and synthesizes control obfuscation strategies that operate jointly to protect sensitive states while preserving the utility of system behavior. By applying this method to cyber–physical systems like networked building access controls, the author demonstrated that structured, low-overhead mechanisms can achieve strong privacy without compromising system responsiveness or observability. This line of research opens new avenues for designing lightweight, secure-by-construction hardware obfuscation schemes with formal correctness guarantees [95].
We have summed up the most novel researches in hardware obfuscation in Figure 7, while Figure 8 refers to the recent applications of these obfuscation techniques. Table 2 provides a comparison of these approaches, focusing on their obfuscation categories, testing methods, market usability, and potential future opportunities for further development and enhancement of these techniques.
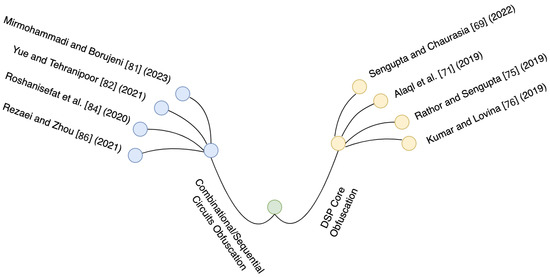
Figure 7.
Most recent hardware obfuscation researches.
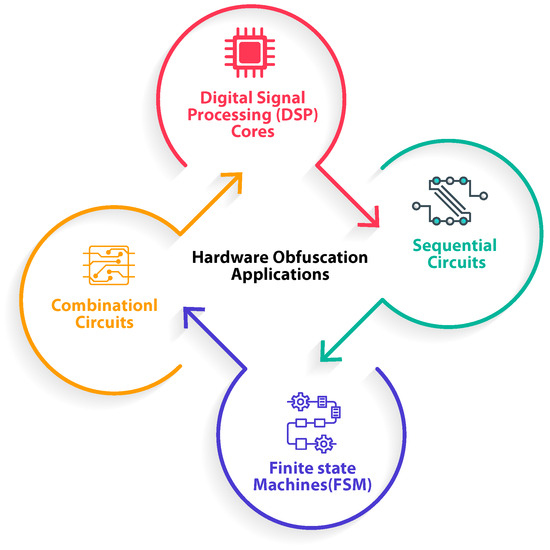
Figure 8.
The current applications of hardware obfuscation.

Table 2.
Hardware obfuscation techniques comparison.
4.3. Summary and Challenges
Hardware obfuscation plays a vital role in safeguarding the intellectual property of integrated circuits, especially in critical domains such as defense systems, automotive technologies, and the Internet of Things (IoT). Techniques like logic locking and FSM (finite state machine) obfuscation provide robust protection but often come with tradeoffs in design complexity and overhead. A central challenge remains in developing schemes that can resist advanced SAT-based attacks and structural reverse engineering techniques, which continue to evolve and expose weaknesses in static or poorly diversified protections.
Notably, Wintenberg et al. (2024) [95] proposed a novel synthesis-based framework that merges reactive control theory with hardware obfuscation. Their approach leverages the concept of opacity to ensure that sensitive system behaviors remain hidden from external observers, even under active monitoring. By modeling hardware interactions as finite automata and jointly synthesizing controllers and obfuscators, the system maintains both utility and confidentiality.
This direction highlights the importance of moving beyond purely structural transformations toward designs that are secure by construction. It underscores the need for scalable, formally verified obfuscation strategies that are adaptable to distributed architectures and cyber–physical systems. Future development should focus on integrating these formal methods into practical toolchains and design flows, enabling privacy-preserving hardware that is not only efficient but provably secure against both theoretical and real-world threats.
5. Hybrid Obfuscation
Hybrid obfuscation indicates the integration of multiple obfuscation methods. The idea behind this technique is that by benefiting both software- and hardware-based obfuscation methods, the resulting preservation is more powerful and challenging to breach than depending on a single technique. It joins the features and strengths of distinct obfuscation methods to generate a more efficient defense versus several kinds of attacks. We can group hybrid obfuscation into three categories depending on the utilized obfuscation techniques.
5.1. Software–Software Obfuscation
This type of obfuscation refers to implementing obfuscation methods within the software field to preserve software implementations from reverse engineering and prohibited analysis. It includes converting the software’s source code or binary representation to make it harder for attackers to recognize and edit critical information or alter the software. Several researchers were interested in applying this kind of hybrid obfuscation. In the following, we will discuss some of these research works.
A novel hybrid obfuscation method to inhibit unauthorized reverse engineering was provided in [6]. This approach involves three techniques; the first technique is string encryption. Appending an arithmetic equation with matrices and loops to code strings stores meaning. Second, it renames system keywords to Unicode to make code harder and more confusing. Third, it converts identifiers to garbage code to store meaning and increase code complexity. The authors tried their hybrid obfuscation method. First, instruments were reverse engineered against Java applications without preservation to define their ability to extract compiled code. The second stage reverse engineered the suggested approach to test its efficacy. The outcomes of their study show good and hopeful results such that it is almost unattainable for the reversing instrument to extract the obscured code.
A hybrid obfuscation approach was presented in [96]. It involves three techniques of renaming, which are the UNICODE Renaming Approach, String Encryption, and Identifiers Renaming to Junk Code. The authors conducted experiments to examine the efficiency of their suggested approach. The outcomes show a promising result, where the reversing tools could not read the code.
A hybrid approach of two signals and encryption obfuscation was provided in [97] to stash the behavior program and prohibit hackers from rebuilding the standard code. The authors mentioned in their research that the expected signal technique is powerful enough for obfuscation. Still, its trouble is a significant complication because of many calls and return instructions. To solve the signal technique problem, they added a modern controller to the source code to rebuild the real control flow graph from the invisible one. Controller code was encrypted to prevent offender access. Using their technique, the power that makes the obfuscation robust was maximized, and the flexibility that makes the obfuscation pauper was reduced. The outcomes of comparing the parity among the obscure data with its genuine code and with obtainable proficient techniques show an effectiveness feature of the suggested hybrid obfuscation technique.
5.2. Hardware–Hardware Obfuscation
This kind of obfuscation indicates the utilization of obfuscation tactics at the hardware level to preserve the employment and design of hardware systems from intellectual property stealing, reverse engineering, and other malignant activities. It includes implementing several hardware-level conversions or modulations to make hardware employees more reluctant to analyze and extract critical information.
Many research works have been concerned with applying this type of hybrid obfuscation. In the following, we will discuss some of them.
ReTrustFSM, a modern and thorough FSM obfuscation technique at the register transfer (RT) level, was introduced in [98], which not only permits the creator to have more monitoring and focus on the semantics of the design while extending the impression of the menace frameworks but also supplies firmness versus a more extensive range of menaces. ReTrustFSM depends on three kinds of privacy: clear exterior privacy via an exterior key, imbedded exterior privacy depending on the particular clock cycles, and interior privacy using a hidden FSM transmission method. It also determines a strong connection between the characteristics of Boolean troubles and the time needed for deobfuscation. Several attacks were applied to examine ReTrustFSM’s solidness, involving machine learning and structural attacks, FSM, and practical I/O queries (BMC) offensives. The authors also tested the venality and cost of design under obfuscation. Their empirical outcomes explain the solidness of ReTrustFSM at reasonable cost/depravity while combating menace frameworks.
The obfuscation of digital FIR filters was studied in [99]. The authors demonstrated that the previously suggested methods for obfuscation of digital Finite Impulse Response (FIR) filters are exposed to their SAT-based query offensive that implements many queries and confirmed that the found key bit value is the real value of the associated key bit in the confidential key. After that, to protect the design of the FIR filter, they suggested the hybrid preservation approach, which involves both obfuscation and locking with a point function. Their suggested method was implemented to parallel direct and transferred forms of the FIR filter and its tucked application. The empirical outcomes of their approach indicate that the hybrid preservation method rivals the outstanding logic locking methods according to hardware intricacy and yields obfuscated designs elastic to renowned offensives. The results also indicate that the direct form FIR filter is a perfect nominee for safe filter application.
The authors in [100] mentioned the importance of static logic locking and structural obfuscation such that they are some of the obfuscation methods primarily examined in the past. They endure brute-force, Boolean satisfiability (SAT), and removal offensives. The authors also stated that dynamic logic locking is a hopeful replacement that is safe versus the offensives mentioned above but endures feasible perplexities, routing, expandability, and adjustability, to name but a few. So, a new hybrid approach was suggested in their research, which provides a fugacious key-based hardware obfuscation with less resource exploitation. Their suggested hybrid system incorporates static and dynamic combinational logic locking that supplies improved protection with minimized intricacy. The primary achievement of their suggested hybrid method is a black box solution flexible to any rationalistic possession, with a resource cost of approximately 1%.
5.3. Software–Hardware Obfuscation
This type of obfuscation refers to incorporating software obfuscation methods with hardware obfuscation techniques to promote the preservation and security of software systems. It includes joining software-based and hardware-based measurements to make the software and its implicit hardware more resistant to tampering, reverse engineering, and attacks. Many research papers were concerned with implementing this type of obfuscation. Some of these research projects are mentioned below.
A hybrid obfuscation technique that involves hardware-degree and software-degree obfuscation conversions to prohibit diverse disclosure attacks was introduced in [101]. The authors incorporated the obfuscation conversions with devoted hardware booby snares to reveal and comply with manipulation efforts.
They also explained a new assessment method to test the twofold variegation. Their approach supplies a quantitative technique to qualify the advantages of their techniques. A performance assessment of their prototype employment explains a minor hardware cost of up to 14% for a plain, inexpensive incorporated processor.
Obfuscating control flow with hardware was suggested. The authors said that cryptography cannot prevent control flow information infiltration. The wastage of control flow can compromise code and data encryption [102].
Software control flow conversion can reduce information waste with some obfuscation methods. Due to its lack of notional institutions and massive fulfillment overhead from sophisticated conversions, software-based obfuscation cannot protect software IP. Thus, the authors in the study above used software encryption and hardware obfuscation to dynamically obscure control flow information.
Changing memory reach series on the fly hides frequent instruction reach series from recognition. They hindered the offender’s ability to gather useful information.
They found that secondary performance punishment can preserve safety. In conclusion, their method can be used in embedded systems with low hardware overhead.
A software preservation approach that incorporates the hardware server with software obfuscation was introduced in [103]. The authors stated that, using their technique, the connection between the hardware and the preserved software includes two hashing functions.
Their approach obfuscates the communication between the variables and the locations where they are utilized. The server part can stay in a dongle, a little chip, or a remote machine on the same network. In this way, the mission of an attacker will be more brutal to crack the security even if the source is visual to the offender.
Unlike other obfuscation methods that alter variable names or insert dummy functions—which can often be detected through static analysis—this approach significantly increases the difficulty for attackers by integrating both hardware and software techniques.
State-of-the-art locking to preserve hardware accelerator IP was found to be inefficient. To make the idle accelerator chip task useless, the authors suggested hardware–software co-design-based obfuscation [104]. This HSCOA approach uses sovereign SDK as the source of confidence to produce a locked program binary that is deobfuscated in hardware.
Results from a regression implementation on an OpenTPU emulator demonstrate the efficiency of this obfuscation method. It provides robust, elastic designs for modern SAT formulation-based attacks and bypass-type offenses.
In their paper, the authors in [105] noted that software-only code obfuscation is still uncertain and dependent on attacker patience and available resources. Hardware-based software preservation techniques offer a significantly higher level of security than software analysis. Their research revealed that there is a dearth of systematic studies examining the interaction between preservation strategies based on hardware and software.
To make Intel’s AES-NI instruction set more proper for use in software preservation conditions and to clarify how it is integrated into a control flow obfuscation method, their study proposed certain modifications to it.
Their cutting-edge method not only supplies sturdy hardware-software committing, but also delimits the offensive context to clear dynamic examination, two essential determinants on the boundary of reverse engineering, and the offense of successfully attacking a program.
McDonald et al. devised a modern technique to software known as Man-at-the-End (MATE) preservation [106]. It influences gate-level hardware presentation, called software-based hardware abstraction (SBHA), and relies on converting point functions in C programs to hardware abstractions.
It supplies a typical framework where standard software obfuscation can be joined with preservations inspired by hardware circuit obfuscation, such as anti-BDD and anti-SAT, making deobfuscation more complex, since it demands a dual software–hardware experience. Empirical outcomes refer to the efficiency of SBHA in beating DSE-based attacks, with comparatively large elasticity and low overhead.
A new secure HW/SW resolution was introduced in [107]. The authors stated that by using their approach, the hardware employment depends on responsible RISC-V-based RTL preserved versus malicious modulations by utilizing logic locking.
SeL4 supports the software stack; a safe OS needs the best microkernel. Integrating these two parts creates a responsible platform for protecting sensitive applications. A large crowd can supervise, examine, and repair HW and SW basic units because they have their roots in the open-source community.
To prove the protection power of their suggested platform, they tested the total protection of their approach, its allowance for error intromissions, and the power of the logic locking scheme. They mentioned that the result of their examinations will shape the foundation for the next reproduction of their stack.
We abbreviated the most current researches in hybrid obfuscation in Figure 9, while Figure 10 indicates the current applications of these obfuscation approaches.
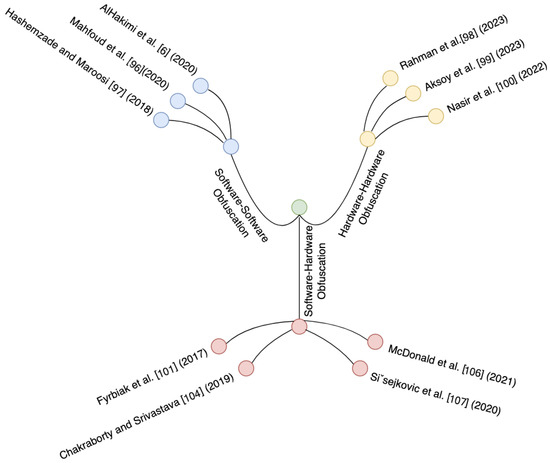
Figure 9.
Most recent hybrid obfuscation research.
Figure 10.
The current applications of hybrid obfuscation.
Table 3 presents a comparison of these approaches, evaluating their obfuscation categories, testing methods, market usability, and future potential for advancing and promoting these techniques.

Table 3.
Hybrid obfuscation techniques comparison.
5.4. Summary and Challenges
Hybrid obfuscation offers a holistic defense strategy by uniting software and hardware protection mechanisms. Its key advantage lies in increasing the complexity of potential attacks, often requiring expertise and tools across multiple domains. However, this integration also introduces new challenges. Synchronization issues, cost and complexity of implementation, and the lack of standardized integration frameworks can limit widespread adoption.
Another concern is ensuring consistency between obfuscated layers during updates or patches, especially in distributed or large-scale deployments. Additionally, current research lacks a cohesive methodology for evaluating the combined effectiveness of software–hardware schemes.
6. Deobfuscation
With more publicity about obfuscation, the research on ways to defeat it has increased. Here, we review some deobfuscation methods proposed by researchers.
A general technique for deobfuscation of executable code was demonstrated in [108]. Rather than creating robust propositions about the obfuscation, like the structure of the emulator, the authors were concerned with the semantics of the software in terms of the input-to-output conversion it applies and were interested in recognizing, extracting, and facilitating the code that executes this conversion. They tested their technique on simulation-based obfuscation and return-oriented software. Experiments using complicated trade obfuscation methods show that their technique is efficient in stripping out the obfuscation and eliciting the logic of the genuine code.
An automated approach to simplify the deobfuscation process of native binary code in Android apps was provided in [109]. Particularly obfuscated by Obfuscator-LLVM, this approach, which is called DiANa, can retrieve the genuine control flow graph. It utilizes the taint test to perform semantic-level deobfuscation and influences an improved flow-sensitive symbolic fulfillment to reconstruct the earnestly obscured control flow. The authors mentioned in their research that DiANa is the first technique that targets tackling the trouble of native Android binary deobfuscation. They implemented DiANa in distinct conditions, and the empirical outcomes explain that the efficiency of DiANa depends on general symmetry comparison measures. They stated that their technique can be a helpful method for protection testers and researchers to perform studies involving malware discovery and program tests.
A VM, JS code editor, and Python int to str() method were used to simplify pretrained word deep features in a study by [110]. The researchers also performed deobfuscation, unpacking, and decoding (DUD preprocessing) by utilizing the method of redetermination. After that, a classification technique was fed the learned feature vectors and told to determine whether the JS code was malicious. They used the SRILAB dataset for hidden malicious JS codes, the Hynek Petrak dataset for hidden harmful JS codes, and the top 10,000 websites from the Majestic Million service for hidden benign JS codes in their achievement testing. Following that, they examined the efficacy of alternative methods for revealing malicious JS codes that had been DUD-preprocessed and obscured. Results from their experiments show that the method they proposed improves feature learning and increases the accuracy with which hidden malicious JS codes can be located.
A technique called Kandi able to effectively decrypt embedded malware obscured by utilizing Vigenère ciphers was provided in [111]. It implements a probable plaintext attack from traditional cryptography by utilizing strings that probably existed in malware binaries, like library names, header signatures, and code bits. The authors explained the performance of their technique in distinct tests. In a striped setting, Kandi shattered obfuscations by utilizing ADD, XOR, and ROL instructions with keys reaching 13 bytes in less than a second per file. On a group of real-world malware in PowerPoint, Word, and RTF files, Kandi was capable of disclosing obscured malware from each fourth document without implicated parsing. On the other hand, their approach limitation includes that it targets a particular form of obfuscation and so cannot reveal arbitrarily obscured code in documents.
The potential of deobfuscating third-party libraries in Android applications was tested in [112] by utilizing current library discovery methods, particularly off-the-shelf library disclosure techniques. The author estimated this technique and compared it to the current deobfuscation technique depending on statistical learning. He found that library discovery methods can be successfully utilized for rapidly deobfuscating third-party libraries. Compared to procedures that rely on statistical learning, the recall was hugely lower. A prominent feature of his technique is that it does not need considerable computational resources like DeGuard. That is because library discovery techniques depend on more straightforward matching methods versus the computationally costly CRF model utilized in DeGuard. Another feature of his technique is that additional training samples can be added simply, while this is not achieved with DeGuard. DeGuard must be retrained for all modifications in the dataset.
A new automated deobfuscation approach was introduced in [113]. It first builds a CFG by offline track test to discover controller and operator methods and emblematically implement the operators to produce emblematic expressions. Then, emblematic expressions are transformed into C code, and the bytecode is transformed into invocations of the C methods that are then improved by compilers to retrieve abbreviated and contextually equal code. The authors achieved a prototype system and tested it versus common trade obfuscators. The empirical outcome of their approach refers to the fact that their approach can successfully retrieve brief code from virtualization-obscured code. Their work shows that compilation refinement is an efficient and general technique for tackling virtualization obfuscation.
A novel pretraining target, DOBF, which influences the structural side of programming languages and pretrains a model to retrieve the genuine version of obscured code, was provided in [114]. The authors indicated that models pretrained with DOBF hugely surpass current techniques in various downstream missions, supplying comparative enhancements of up to 12.2% in unsupervised code interpretation and 5.3% in natural language code searches. Indiscriminately, they found that their pretrained model can deobfuscate completely obscured source files and propose descriptive variable names.
A new deobfuscation technique that depends on semantic equivalence, called DoSE, was suggested in [115]. It aims to enhance and complement DSE-based deobfuscation methods by statically removing obfuscation conversions. This enhances the code covering. The novelty of this technique hails from the change of the current binary diffing methods, called semantic equivalence checking, to the objective of the deobfuscation of unprocessed methods, like two-way opaque structures, which are faced in secret software. The authors also mentioned that to defy DoSE, they utilized known malware like Cryptowall, Flame, WannaCry, and BitCoin-Miner and obscured code samples. Their empirical outcomes indicate that DoSE is a practical approach to discovering obfuscation conversions depending on code reutilize with low averages of false positive or false negative outcomes practically, reaching a 63% code decrease on particular malware.
An efficient and lightweight deobfuscation technique for PowerShell scripts was introduced in [116]. The authors proposed a new subtree-based deobfuscation technique that implements obfuscation discovery and emulation-based retrieval at the degree of subtrees to handle the vital need to accurately recognize the recoverable script parts. Based on their novel deobfuscation technique, they also implemented a semantic-aware PowerShell Offensive discovery approach with 31 recently identified OOA principles. Depending on a group of 6483 PowerShell script paradigms, their deobfuscation technique was found to be productive and influential. Moreover, with their deobfuscation implemented, the attack discovery averages for Windows Defender and VirusTotal was maximized from 0.3% and 2.65% to 75.0% and 90.0%. On the other hand, their semantic-aware attack discovery approach exceeded Windows Defender and VirusTotal, with a 92.3% true positive ratio and a 0% false positive ratio.
A group of methods for automatically undoing the mission of obfuscators to assist with reverse engineering of malware was introduced in [117]. The authors implemented their methods to two broadly publicized instances of malware: Aurora and Conficker. They also indicated that their methods in the heavily obscured Conficker P2P protocol can detect the whole logic of the protocol, permitting reverse engineering of the worm. Their job is easily obtainable as a plug-in for the common IDA disassembler to support reverse engineers in their position.
A modern, general framework for code deobfuscation called SEEAD, aiming at malware discovery, was provided in [118]. It utilizes dynamic taint and control dependency tests to direct the software implementation path across profiling cautiously runs to maximize the code coverage. After that, it facilitates the instruction traces of the objective binary to conduct code deobfuscation. SEEAD is entirely automatic and needs little human participation. The authors tested their approach on a scope of benign and virulent obfuscated programs. The empirical outcomes indicate that their technique can successfully retrieve the genuine logic from obscured binaries.
A hidden Markov model (HMM) technique for spam deobfuscation was suggested in [119]. It can be utilized to deobfuscate an email before implementing a content-based filter. It takes an obscured word or sentence as input and generates the deobfuscated word or sentence as output. The lexicon tree HMM version of this approach showed notable achievement for distinct obfuscation methods involving substitutions, insertions, misspellings, and segmentations.
A string deobfuscation method that aims at malicious code that utilizes string encryption obfuscation was provided in [120]. It can automatically decrypt at the platform degree without previous knowledge of the encryption key. The authors confirmed their scheme’s performance precisely through experiments. They expect that their suggested technique could be more efficiently used in malware tests with many uncounted malware abusing obfuscations.
The authors in [121] introduced an automatic and general technique depending on emblematic path reconnaissance, taint, and recompilation permitting to retrieve, from a virtualized code, a devirtualized code semantically similar to the genuine one and close in size. They determined criteria and measures to test the relation of the deobfuscated outcomes in terms of correctness and accuracy. Lastly, they suggested an open-source setup permitting testing the suggested technique versus distinct forms of virtualization.
A novel approach called ARBDroid that automatically deobfuscates obscured Android malicious code was suggested in [122]. It dynamically tests implementations to detect classes, encrypted strings, and hidden API calls. The authors indicate that modern malicious code actively utilizes obfuscation methods to hide virulent attitudes and can efficiently test obscured malicious code with ARBDroid by utilizing in-the-wild malicious code. Their test outcomes utilizing real-world malicious code explained the efficacy of ARBDroid. They deobfuscated it by utilizing ARBDroid to locate hidden data.
The authors in [123] provided a framework for deobfuscating software that briefs the input software as a mathematical technique of its attitude by controlling each operation conducted through the malware execution. Also, the software is directed to execute automatically through its distinct run paths to combine as much knowledge as possible in the shortest time. That supports finding invisible logic and deobfuscating distinct obfuscation methods without relying on their particular specifics. The resulting technique is recorded as a C code without the artificially appended complications. It is named a twin code and conducts similarly to the obscured binary. Their suggested framework was applied to confirm their concept, and its efficiency was tested on obscured binaries. Software control flow graphs were investigated as a measure of successful code retrieval. The performance of their suggested framework was tested by utilizing the set of SPEC test programs. It can be utilized for distinct use cases, like recognizing the interior logic of malware, production of inclusive behavioral signatures for grouping malware in associated families, debugging obscured benign programs to test the validity of the utilized obfuscation conversion, and testing close-sourced and obscured programs for the existence of probable backdoors [124].
A novel technique for layout deobfuscation of Android APKs was introduced in [125]. The essential idea of this approach is to phrase the trouble of reversing obscured names as structured anticipation in a probabilistic graphical technique and to influence the large availability of non-obfuscated Android software to teach this technique. The authors applied their method in a system named DeGuard. They explained that DeGuard can successfully and with large accuracy reverse obfuscations conducted by ProGuard, a mission beyond the arrival of current systems. They thought that their work referred to the commitment to benefiting probabilistic techniques over the “Big Code” for handling significant challenges in protection.
The authors in [126] supplied MACNETO, which influences topic modeling on instructions and deep learning methods to deobfuscate software automatically. By conducting two massive scale tests, they implemented MACNETO to deobfuscate 1600+ Android APKs, which were obfuscated using two renowned obfuscators. Their test outcomes indicate that MACNETO fulfilled 96 + % precision on retrieving obfuscated software by ProGuard that renamed identifiers in APKs. Their technique also presented high accuracy in retrieving software obfuscated by a sophisticated obfuscator, Allatori, that alters control flow, adds extra techniques into APKs, and renames identifiers. It yielded up to a 200% rise in the deobfuscation accuracy compared to a naïve technique that depends on instruction allocation of the obfuscated technique to find the most identical genuine version in the codebase.
A novel technique called ReDex optimizer was implemented in [127]. It was used for reversing the control flow obfuscation conducted by the Obfuscapk procedure on open-source Android implementations. The authors tested the efficiency and restrictions of ReDex according to its deobfuscation capability to reverse the control flow obfuscation for Android applications. Their empirical outcomes indicate that ReDex could retrieve 1089 of 1108 apps obscured with control flow obfuscation methods of the Obfuscapk obfuscator. By enhancing the bytecode, ReDex minimizes the number of techniques and domains hugely. At the same time, it has a restriction in eliminating dead codes associated with both worthless goto instructions and random nop instructions.
A pair of techniques for circuit deobfuscation from power side streams using pseudo-Boolean SAT solving was introduced in [128]. The authors explained their implementation versus fabricated and actual hardware trails and supplied a binary of the instrument and the trail group framework to the research society. Their techniques, in addition to demonstrating that current locking approaches do not automatically realize side-channel elasticity, can be utilized in benign reverse engineering and hardware solidity examination.
A deobfuscator that can efficiently discover and deobfuscate the source codes appended by the control flow obfuscation of DexGuard was built in [129]. It tests variable utilization paradigms to assert global opaque variables are utilized just in opaque predicates. The authors tested its achievement regarding ReDex and explained the efficiency by indicating that the apps deobfuscated by their technique can execute typically on both an actual device and the AVD. They provided the source code of their technique at the public repository GitHub, which supports malicious code testers to reverse control-flow-obscured virulent Android applications.
The authors in [130] argued a general technique for deobfuscation and recompilation of obscured source code depends on the compiler scheme LLVM. They demonstrated the process of lifting back a binary code into the compiler intermediate language LLVM-IR. They showed how they retrieved the control flow graph of an obscured binary method with a recursive control flow graph creation technique depending on compiler improvements and resolving satisfiability modulo theories (SMTs). Their technique does not make any presumptions about the obscured code but instead utilizes robust compiler refinements obtainable in LLVM and Souper Optimizer to facilitate the obfuscation. Their empirical outcomes indicate that their technique is efficient in reducing or even eliminating the implemented obfuscation approaches, such as particular arithmetic-based opaque expressions, constant unfolding, dead code injections, dummy control flow, or integer encoding located in public and trade obfuscators. Their introduced work was applied in a deobfuscation method named SATURN.
A general, efficient, and lightweight deobfuscation technique for PowerShell scripts was developed in [131]. The authors suggested a new technique depending on the effect on ASTs to locate the obscured bits of scripts precisely. Their outcomes indicate that their new technique achieved better results than the current techniques with nearly no false positives and covered sophisticated, multilayer, and even anonymous obfuscations. They suggested emulation-based restoration at the AST degree to retrieve the obscured scripts. Their technique could retrieve the scripts completely, particularly at the script-block level, for which it realized 100% sameness. Depending on the test of more than 6483 obscured PowerShell scripts, they confirmed that their technique is effective, influential, and general. With the support of their deobfuscation technique, the discovery averages of current virulent script detectors involving Windows Defender and the sensors in VirusTotal were greatly enhanced. Their discovery approach achieved better results than both Windows Defender and VirusTotal. The OOA principles elicited by their detector can be utilized immediately by other testers and scanners to enhance semantic-aware test and discovery costs.
A modern technique for FPGA design deobfuscation was suggested in [132]. It depends on assuring the entire monitorability of every instantiated LUT input in a design by recursive LUT modulation at a bitstream scale. The authors applied the suggested technique in a software package and explained its probability on the instance of a SNOW 3G stream cipher FPGA application. By supplying a new technique for evaluating the impedance of obfuscation methods, their outcomes were predicted to assist the assertion of FPGA design protection. Their technique can overcome obfuscation depending on steady values and possibly open bitstreams locked by utilizing combinational logic locking. It is not affected by the degree of secrecy of the continuous values or the circuit that produces them. So, it can be utilized to eliminate obfuscation using steady factors produced by hardware opaque predicates regardless of their confidentiality.
A technique for deobfuscating binaries depending on program structure was demonstrated in [133]. It demonstrated an accurate obfuscation identification for finding obscured code snippets using machine learning, with a precision of 99.29%. Moreover, it integrates the software structure and a heuristic search technique of the Nested Monte Carlo Search. The authors implemented a prototype application of their notions to data obfuscation in distinct methods involving OLLVM and Tigress. Their empirical outcomes propose that their technique is mainly efficient in finding and deobfuscating the binaries with data obfuscation, with a precision of at least 90.34%.
By comparing their approach with other deobfuscation techniques, their success rate was maximized by 5% and efficacy was maximized by 75%. So, their experiments indicate that their technique is efficient in facilitating obscured binaries with data obfuscation.
A novel technique called MPScan was provided in [134] as a scanner that merges dynamic JavaScript deobfuscation and static malicious code discovery. By connecting the Adobe Reader’s native JavaScript engine, JavaScript code and op code can be elicited rapidly after the code is parsed and then accomplished. They also conducted a hierarchical test on the generated JavaScript strings and op code to discover malicious code. The authors evaluated their approach and indicated that despite obfuscation methods, MPScan could efficiently deobfuscate and discover 98% of virulent PDF samples.
A new technique called WordAdjust was presented in [135] as a frontend deobfuscation strainer for the state-of-the-art anti-spam instrument SpamAssassin. The authors stated that their deobfuscation strainer can deobfuscate three obfuscation techniques: scrambling, Unicode, and intentional misspelling. The Misspell deobfuscation technique depends on N-gram fuzzy search methods. SpamAssassin deals with spam emails that are obscured by these three techniques. Experimentations explained how WordAdjust maximized the rate of the SpamAssassin score by 56% on intended obscured spam emails. More examinations explained how WordAdjust authorizes SpamAssassin to capture 10% of the spam mails that commonly would end up in the user’s inbox.
A modern approach called TIRO was provided in [136] as a deobfuscation system for Android by utilizing a method known as Target-Instrument-Run-Observe. It supplies a united framework that can deobfuscate malware and utilizes a collection of conventional and newer runtime-based obfuscation methods. The authors tested and utilized their technique on a dataset of new Android malware samples and found that it can automatically discover and reverse-language-based and runtime-based obfuscation. They also tested it on a corpus of 2000 malware patterns from VirusTotal. They found that runtime-based obfuscation methods existed in 80% of the patterns, explaining that runtime-based obfuscation is a crucial instrument utilized by Android malware authors today.
The authors in [137] suggested the AppSAT offensive, a convergent deobfuscation technique, depending on the SAT offensive and arbitrary analysis. They explained how their technique can deobfuscate 68 out of the 71 benchmark circuits, obscured with state-of-the-art SAT offensive protections with precision of 1/2, with n being the number of inputs. Their approach was evaluated on 71 ISCAS and MCNC benchmark circuits obscured with the anti-SAT complicated framework. Their technique demonstrates that with present SAT attack protections, there would be a tradeoff between pinpoint offensive and estimation elasticity.
6.1. Deobfuscation Technique Comparison
In our comprehensive survey, we thoroughly compared the most recent deobfuscation techniques to shed light on their efficacy and applicability across various scenarios. Our analysis encompassed several critical aspects, including the proposed technique’s novelty and uniqueness, whether it is intended for software or hardware obfuscation, the deobfuscation process, the evaluation method used to assess its performance, as well as the advantages, disadvantages, usability within the market, and future opportunities for improving these techniques.
One of the critical dimensions of our comparison was the proposed deobfuscation technique itself. We evaluated the ingenuity and innovation behind each method, considering its potential to tackle novel obfuscation challenges. Additionally, we examined whether the technique was more suited for software or hardware obfuscation scenarios, recognizing that the nature of obfuscation may vary significantly between these two domains.
The deobfuscation process was another crucial factor in our analysis. We scrutinized the steps involved in each technique, emphasizing the level of automation versus manual intervention required. Furthermore, our evaluation method focused on assessing each deobfuscation approach’s practical performance and real-world applicability, allowing us to gauge its effectiveness in breaking obfuscated code or systems. By considering the pros and cons, we aimed to provide a holistic view of each technique’s strengths and weaknesses. We identified the specific target domains or use cases for which each deobfuscation method was intended, thereby helping users choose the most suitable approach for their unique requirements. Finally, we provided future opportunities and directions for enhancing these approaches. Figure 11 refers to the most recent deobfuscation research works, while Table 4 provides a comparison of these approaches, focusing on their deobfuscation categories, testing methods, market usability, and potential future opportunities for advancing these techniques.
Figure 11.
Most recent deobfuscation research.

Table 4.
Deobfuscation techniques comparison.
6.2. Summary and Challenges
Deobfuscation continues to evolve as obfuscation methods grow more complex and widespread. While SAT solvers and symbolic execution remain core techniques in both domains, attackers now supplement these with AI-based inference and adversarial training methods. Meanwhile, defenders must account for this rising sophistication by designing obfuscation schemes that go beyond surface-level transformations.
One major challenge lies in measuring the resilience of obfuscation against modern deobfuscation methods, as no universal metric currently exists. In software, the line between benign complexity and suspicious behavior is also blurring, particularly when using obfuscation for malware evasion. In hardware, formal tools are still catching up to the creative diversity of obfuscation logic seen in recent chip designs.
Future work must focus on adaptive, context-aware obfuscation schemes, formal security proofs of resistance, and the development of publicly benchmarked datasets for standardized deobfuscation testing. Cross-disciplinary collaboration, especially with the AI and formal methods communities, will be essential for advancing defense capabilities.
7. Obfuscation Detection
Detecting obfuscated code is a critical issue in cybersecurity, as pernicious actors usually utilize obfuscation to stash malware, employ vulnerabilities, or avert discovery by defense tools. Machine learning methods have become influential tools for recognizing and identifying obfuscated code from legal software. These methods leverage the capacity of artificial intelligence to detect patterns, characteristics, and features that distinguish between obfuscated and non-obfuscated code [138]. This section reviews some of the obfuscation detection techniques proposed by researchers.
A novel approach called DaDiDroid was introduced in [139]. The purpose of this technique is to find hidden Android apps that contain malware by using the properties of weighted directed graphs of API calls. According to the author’s findings, DaDiDroid was found to be far superior to MaMaDroid, which is a recently proposed malware recognition technique that has confirmed to be highly efficacious in detecting malware in an uncluttered, light-filled setting. Using various datasets for 43,262 good apps and 20,431 bad apps, they compared DaDiDroid’s accuracy and endurance to different elusion methods. In addition, they detailed how, with the help of a hidden app training set, their method accurately identified 91% of Android malware instances.
A novel approach targeted at recognizing automatically whether a pernicious sample under test has been changed using obfuscation methods was suggested in [140]. It depends on instituted supervised binary classification methods (SVM, Multilayer Perceptron, and Random Forest) working on ad hoc characteristics originating from the static analysis that has already been displayed to be proper for categorization of Android malware; as a second choice, the authors also examined the utilization of Long Short-Term Memory frequent neural networks that can work immediately on the series of opcodes. They examined the suggested technique on a dataset of tangible Android implementations changed using the following obfuscation methods: identifier renaming, modifying package name, code reordering, data encoding, and junk code injection. The outcomes of their approach are promising: for some methods, a nearly typical discovery is probable, whereas for others, the discovery is more difficult.
A rapid, scalable, and precise technique for Android malware discovery and family recognition depending on lightweight static tests was provided in [141]. It utilizes deep examination of Android malware to develop operative and solid metrics for computational learning. The empirical outcomes of this approach indicate that static tests for Android can succeed even when faced with obfuscation approaches like encryption, reflection, and dynamically loaded native code. While substantial changes in malware attributes remain hugely open trouble, the authors explained that DroidSieve stays elastic versus state-of-the-art obfuscation methods and can be utilized to deduce modern and syntactically distinct malware variants quickly.
In their work, the authors in [142] presented a method for dealing with difficulties in classifying and finding harmful hidden variants. Their classification and disclosure system makes use of both static and dynamic tests through crew electing method. Not only that, but their research reveals a cruel shift in the proportional significance of these metrics in obfuscating precious and malicious software implementations after implementing a new feature-based obfuscation technique. Before, a small group of metrics performed permanently well when they were originated from the base malicious code (non-obscured). Consequently, they presented a real-world and emulator-based method for quickly and accurately detecting hidden Android malware using a deep learning technique. In addition to identifying metrics that malware attackers often obfuscate, their empirical results show that their proposed method effectively and precisely discovers malware.
A novel machine-learning-based disclosure technique targeting overcoming malware avoidance efforts was supplied in [143]. Dynamic fulfillment traces are registered to catch all behaviors conducted by the malignant script involving the dynamically produced code.
The authors also utilized semantic-based deobfuscation to facilitate the traces to obtain more brief and primary instructions. Non-ordered and non-concessive trace paradigms were elicited from the deobfuscated traces to perform the essential metrics for malignant scripts. They tested their technique with a huge dataset gathered from the Internet. The experimental outcomes of their approach explain that their technique can efficiently discover obscured malignant JavaScript code without bearing too much overhead.
In their work, the authors in [144] summed the obfuscation approaches and suggested an obfuscated macro code discovery technique by utilizing five machine learning techniques, which were Random forest (RF), Linear Discriminant Analysis (LDA), Support Vector Machine (SVM), Bernoulli Naive Bayes (BNB) and MultiLayer Perceptron (MLP). To train these models, their suggested approach utilized 15 distinctive static metrics considering the features of the Visual Basic for Applications (VBA) macros. They tested their technique by utilizing a tangible dataset of obscured and non-obscured VBA macros elicited from Microsoft Office document files. The empirical outcomes of their approach explain that their discovery technique accomplished an F2 score enhancement of larger than 23% in contrast to those of associated researches.
A novel technique called Obfusifier was presented by the authors in [145]. This machine-learning-based malware detector is produced by utilizing characteristics from unobfuscated malware samples but can supply precise and solid discovery outcomes when obscured samples are introduced for discovery. Their main idea is that there are parts of codes that cannot be obscured since obfuscation of them will breach their work. One of these parts is the API invocations into the framework of Android. So, their chosen metric concentrates primarily on the utilization of Android APIs. Their technique then elicits metrics that are associated with such utilization. Overall, they elicited 28 metrics to build their model by utilizing 4300 innocuous applications and 4300 malicious code paradigms gained from VirusShare; these applications were not obscured. They then evaluated their technique by utilizing 568 obscured malware. The outcome shows that their system could accomplish 95% accuracy, recall, and F-measure, enhancing the obfuscation elasticity of Obfusifier.
A technique for adaptive malware was provided in [146] depending on their obfuscation metrics examination. The obfuscation metrics were gained based on the equal functional blocks search in the dubious software and its altered version. As an output of the contrast, the following measurable obfuscation metrics were gained: the the Damaerau–Levenstein distance; the number of deletions, transpositions, and insertions; and the matches of opcodes. The empirical outcomes for this approach explain that the discovery adequacy is based on selecting the similarity features at the search phases and the option improvement of the equal functional blocks. The best outcomes of the adaptive malware discovery are completed with the utilization of the taxicab feature at the phase of the EFBs search and the Chebyshev feature at the phase of the option improvement of the EFBs. This process permitted growing adequacy from 79% to 94% in comparison with prior research.
A novel static analysis approach to handle the troubles of obfuscating and native malware implementations was presented in [147]. The suggested technique supplies a united method for eliciting facets from implementations and native libraries by utilizing a picking technique that can elicit a small group of exclusive and influential metrics for discovering malware implementations quickly and with a large discovery proportion. Testing by utilizing massive Android malicious code discovery datasets from several sources proved that the suggested technique accomplished very hopeful outcomes according to enhanced precision, low false positive rate, and high discovery proportion.
A JavaScript code obfuscation discovery technique was proposed by the authors in [148]. It utilizes an attention technique with the artificial neural network as a classifier method. In their work, a group of samples of obscured and unobscured code was gained by utilizing projects and repositories hosted on github.com. Then, an artificial neural network technique with an attention method was adapted to resolve the issue of script categorization on the obfuscation foundation. According to the outcomes of their experiments, their technique can probably be applied with some enhancements in pernicious code detection approaches, mobile device fingerprint collection systems, browsers, or other software that utilizes obfuscation assessment.
7.1. Obfuscation Detection Technique Comparison
In our extensive survey, we comprehensively compared eight obfuscation detection techniques, aiming to shed light on their relative strengths and weaknesses in identifying and countering obfuscated codes or systems. Our evaluation considered several critical dimensions, including the proposed technique’s novelty and uniqueness, any suggested methods for improvement or enhancement, the underlying processes involved in obfuscation detection, the methodology used for assessing detection performance, as well as the pros and cons of these obfuscation detection techniques. Table A5 in Appendix E shows a comparison between these techniques.
One of the primary facets of our comparison was the proposed obfuscation detection technique itself. We assessed the level of innovation and originality inherent in each method, analyzing whether it introduced novel approaches or enhancements to obfuscation detection. Additionally, we noted any suggested techniques or modifications that could potentially enhance the comprehensive effectiveness of the identification process, acknowledging the importance of ongoing research and development in this field.
The obfuscation detection processes constituted a central focus of our analysis. We scrutinized the steps and methodologies employed by each technique to identify and combat obfuscated code or systems, which encompassed both static and dynamic analysis approaches and any hybrid techniques that combined multiple methods for more robust detection. Understanding the intricacies of these processes allowed us to assess the suitability of each technique for different types of obfuscation challenges.
Our methodology for assessing obfuscation detection performance emphasized real-world applicability and practicality. We evaluated each technique’s ability to effectively identify and counteract obfuscation in various scenarios, including assessing detection accuracy, false positive rates, and the computational resources required for efficient execution. By considering both the advantages and disadvantages of each technique, we aimed to provide a comprehensive overview to assist practitioners and researchers in selecting the most appropriate approach for their needs. Table A5 in Appendix E shows a comparison between these techniques.
7.2. Summary and Challenges
Detecting obfuscation is a non-trivial task due to the wide variety of transformation techniques and the lack of clear indicators in some cases. While static analysis offers speed, it struggles against dynamic obfuscation or encryption layers. Dynamic analysis is more robust but costly in terms of time and resources.
One major challenge is evasion: sophisticated obfuscation can mimic benign complexity or delay activation until after initial inspection. In addition, hardware detection must contend with physical access limitations and the increasing use of probabilistic design elements that defy deterministic validation.
8. Summary and Analysis Discussion
This section provides a comprehensive analysis of the obfuscation landscape, synthesizing findings from the previous sections and presenting key insights into the current state of software, hardware, and hybrid obfuscation methods. Unlike the conclusion, which offers a closing reflection, this discussion is designed to highlight specific challenges, trends, and opportunities for future development.
8.1. Key Analysis Points
- Obfuscation Effectiveness vs. Performance Tradeoffs: Across all categories—software, hardware, and hybrid—there is a recurring theme: stronger obfuscation generally leads to reduced efficiency. Techniques like control flow flattening, logic locking, and encrypted management tables offer increased protection but often at the cost of runtime speed, memory usage, and energy consumption. This tradeoff remains a core challenge, especially for real-time systems and embedded platforms.
- Dynamic vs. Static Obfuscation Approaches: While static obfuscation continues to be the foundation in commercial tools, dynamic approaches—such as those using runtime control flow reconstruction (e.g., CSE with MT)—demonstrate higher resilience against static analysis and reverse engineering. However, they require careful engineering to ensure compatibility and runtime integrity.
- Interoperability and Integration Gaps: Hybrid obfuscation presents promising security benefits by linking software and hardware protections, but in practice, many systems are developed in silos. Cross-layer coordination remains underdeveloped. Effective integration will require toolchains and co-design frameworks capable of generating and managing unified obfuscation policies.
- Vulnerability of Traditional Techniques: Many traditional techniques, especially those in tools like OLLVM, have been extensively studied and partially defeated by modern analysis methods. Their use alone is no longer sufficient, and they must be supplemented with more unpredictable or adaptive techniques such as probabilistic logic, dynamic relocation, or AI-assisted transformations.
- Emergence of Machine Learning in Both Attack and Defense: Deep learning models are increasingly capable of identifying patterns even in highly obfuscated code or hardware. This presents a significant challenge to current obfuscation techniques but also an opportunity—using adversarial training and reinforcement learning to generate more resilient obfuscation strategies.
- Ethical Ambiguity and Legal Frameworks: As obfuscation is also used by malicious actors (e.g., in malware or software piracy), the ethical and legal boundaries surrounding its use are still evolving. Research into auditability, compliance, and the creation of secure but transparent obfuscation mechanisms will be critical.
- Opportunities in Post-Quantum Obfuscation: With quantum computing threatening traditional cryptographic assumptions, there is an emerging research opportunity to design obfuscation methods that remain secure in post-quantum environments. Techniques leveraging lattice-based encryption or quantum-safe logic primitives are still in early stages and warrant deeper exploration.
- Data-Driven and Domain-Specific Obfuscation: Obfuscation tailored to specific data types or application domains (e.g., medical imaging, location privacy, and industrial control systems) can provide more effective protection than general-purpose methods. VAE-based image obfuscation and LPMT for trajectory protection are early examples of this specialization.
8.2. Discussion
The survey reveals that while foundational obfuscation techniques remain relevant, they are increasingly insufficient in isolation. The evolution of attack tools, especially those powered by AI and large-scale automation, demands a shift toward more dynamic, intelligent, and integrated protection models.
Addressing the challenge of maintaining functionality and usability while enhancing resistance to reverse engineering is not a one-size-fits-all problem. It requires careful threat modeling, context-aware designs, and the adoption of hybrid architectures where obfuscation is not a final layer but a deeply embedded component of the system’s security model.
Additionally, more collaborative benchmarks and reproducibility standards are needed to evaluate obfuscation strategies fairly and rigorously. The lack of widely accepted testing frameworks hampers the ability to compare techniques and advance the field.
Overall, the obfuscation domain is at an inflection point. With increasingly adaptive threats, the opportunity lies in building systems that can evolve alongside them—embracing unpredictability, formal assurance, and multilayer resilience as core principles.
9. Conclusions and Future Works
Lately, there has been a notable dissemination of software code in an architecturally-independent pattern, which increases the capability to reverse engineer source code from the executable. This challenge has raised serious concerns for software companies seeking to protect their intellectual property. While several approaches exist for protecting software, such as encryption, native code execution, and server-side processing, obfuscation is an outstanding and cost-effective solution to this growing challenge. It is primarily the process of transforming software code in a manner that renders it harder for prospective offenders to comprehend while maintaining its main functionality intact. In this research project, we surveyed the literature on the several kinds of obfuscation approaches, including software, hardware, and hybrid. We compared these distinct techniques regarding their obfuscation process, testing methodology, efficiency in protecting intellectual property, disadvantages, usability within the market, and future opportunities for improving these approaches.
Furthermore, we surveyed the literature on the distinct types of deobfuscation approaches for defeating these obfuscation techniques and compared them. Moreover, we surveyed the literature on machine-learning-based techniques for discovering these obfuscation methods. Our results reveal that software-based obfuscation techniques are the most widely adopted due to their flexibility and cost efficiency. At the same time, hybrid methods provide promise for balancing security and performance. Machine-learning-based discovery approaches are evolving fast but still face obstacles in generalizing across obfuscation kinds. This survey paper serves as a worthy resource that supports software companies in choosing the proper obfuscation approaches for improving the protection of their software products against possible threats. Additionally, it assists in the informed choice of efficient deobfuscation and obfuscation detection techniques, enabling the recognition of weaknesses and vulnerabilities within their products. Therefore, supporting them to efficiently control security risks and supply products that are more protected and reliable will improve general customer satisfaction, eventually leading to maximized profitability for the company.
In the future, we are concerned with studying the human factors included in the usability and approval of obfuscation approaches. This could include investigating the comprehension of developers, system administrators, and end users to recognize probable obstacles or facilitators to the implementation of obfuscation. We will also develop standardized benchmarks for assessing the efficiency and performance of obfuscation and deobfuscation methods.
Author Contributions
Conceptualization, K.S. and D.D.; methodology, O.D.; validation, K.S., D.D. and O.D.; formal analysis, O.D.; investigation, D.D.; resources, E.H.; writing—original draft preparation, K.S.; writing—review and editing, F.A.; visualization, D.D.; supervision, E.H.; project administration, E.H. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
No new data were created or analyzed in this study.
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A

Table A1.
Detailed comparison of software obfuscation techniques.
Table A1.
Detailed comparison of software obfuscation techniques.
| Ref. | Proposed Technique | Obfuscation Processes | Evaluation Methodology | Benefits of Current Research | Cons of Current Research | Usability Within the Market | Future Opportunities and Directions |
|---|---|---|---|---|---|---|---|
| Category: Control Flow Obfuscation | |||||||
| Li et al. [31] (2022) | Code protection method based on obscure semantics (COOPS) | It depends on the obscure semantics, where functions are considered as basic semantic units. | Tested on OpenSSL and SpecInt-2000 test sets. | 1. By comparing with O-LLVM, it shows robust impedance to Asm2vec and other program similarity analysis methods. 2. It enhances the degree of software preservation instead of necessitating time-consuming and heavyweight problems. | Performance degradation of obfuscated code. | Applied on source codes written in C/C++. | This approach only performs inlining and outlining conversion, and the obfuscation method is comparatively simple and needs to be improved by maximizing the variation of its obfuscation approaches. |
| Zi-Han et al. [32] (2022) | A deep control flow obfuscation model based on callback function | It applies deep control flow: as for the loop structure, the the callback function is used to build an equal loop method, and the basic block in the software operation is transformed into an interprocess function calling to resist reverse technology. | Verified on OpenSSL and SPECint-2000 benchmark suite test set. | It provides improved protection against reverse engineering by utilizing a function calling fusion algorithm. | Performance degradation of obfuscated code. | Applied to source codes against reverse engineering | N/A |
| Lu [26] (2020) | CPS-based control flow obfuscation for FJ with exception handling | It depends on a source-to-source transformation by utilizing a continuation passing style (CPS). | Tested by empirical analysis. | 1. CPS conversion leads malicious attacks to lose accuracy. 2. Efficient against attacks that utilize static control flow analysis. | Performance degradation of obfuscated code. | Applied on Java source codes against reverse engineering. | This research work is an extension of Lu’s work [148] and is inspired by Kelsey’s work [147]. It is in the process of implementation. |
| Li et al. [27] (2022) | IOLLVM (Enhanced version of OLLVM) | It improves OLLVM obfuscation at the control flow and identifier levels. | Verified by experimental analysis. | 1. It can replace 65.2% of custom identifiers while ensuring software functionality. 2. The time overhead from obfuscation is nearly negligible. 3. Space overhead is at 1.5 times. | 1. Its efficiency in huge projects remains to be tested. 2. Performance degradation of obfuscated code. | Applied to source codes against scripting attacks. | This work can be enhanced by creating more secure opaque predicates that are not restricted to the number-theoretic model. |
| Category: Data Obfuscation | |||||||
| Gao et al. [35] (2022) | Location privacy-preserving mechanism based on trajectory obfuscation (LPMT) | It extracts the stay points of a trajectory depending on the sliding window technique and then obscures every stay point to a goal obfuscation subregion using the exponential technique. | Tested by comparing with baseline mechanisms. | It minimizes data quality loss by more than 20% while supplying the same degree of obfuscation quality, which means that LPMT has the features of robust protection and high Quality of Service. | 1. Increased computational overhead due to the need for exponential techniques to obfuscate trajectories effectively. 2. Degraded data utility due to adding noise into the obfuscated trajectories. | Applied in mobile applications that depend on location data while aiming to preserve users’ privacy. | LPMT is proper for near real-time and non-real-time MCS scenarios. Future improvements to this research may include researching the location secrecy preservation in real-time MCS scenarios. |
| Popescu et al. [36] (2022) | Obfuscation algorithm for privacy-preserving deep-learning-based medical image analysis | It joins a variational autoencoder (VAE) with random non-bijective pixel intensity mapping to preserve medical image content that is thereafter utilized in building DL-based solutions. | Tested using binary classifier to test the advantage of obfuscated images in the context of model training. | It authorizes DL model training on obfuscated images with no important computational overhead while guaranteeing preservation against human eye conception and AI-based rebuilding attacks. | Degradation in precision is noted when the model is trained on obfuscated images. | Utilized for obfuscating sensitive data like medical images. | Improvements to this research may involve employing distinct datasets and DL solutions to accomplish a precise separation of the confidentiality and accuracy levels according to the obfuscation method specifications. |
| Jiang et al. [37] (2022) | PriMask (Cascadable and Collusion-Resilient Data Masking for Mobile Cloud Inference) | It permits the mobile device to utilize a secret small-scale neural network named MaskNet to mask the data before submission. | Tested by implementing to three mobile sensing jobs of human activity. | It achieves good generalizability and Performance in protecting privacy while preserving the cloud inference precision. | It does not regard the problem of protecting the privacy contained in the training data utilized by the ISP to pretrain the InferNet. | Applied for mobile devices to utilize the cloud inference services. | This research considers a PSP trusted by the ISP and therefore does not consider preserving the secrecy contained in the ISP’s training data versus a curious PSP. Improving PriMask to handle a PSP that is not trusted by ISP is an important point for future research. |
| Saleem et al. [38] (2022) | DP-Shield (Face Obfuscation with Differential Privacy) | It is based on two obfuscation techniques, called DP-Pix and DP-SVD, and also involves two substitutional techniques for comparison. | Tested by performing experimental analysis. | It is efficient at prohibiting facial-recognition-based attacks. | Reduction in precision of face analysis tasks like face recognition or emotion detection. | Applied to social media platforms or online services that depend on face analysis like photo. | Future opportunities for this research may involve open sourcing the DP image obfuscation techniques, releasing the face reidentification attacks as a standard test group, and enhancing the utilization of DP-Shield for mobile implementations. |
| Hu et al. [39] (2020) | A model and an empirical study for obfuscating sentences | It depends on the properties of natural language where a given text is obfuscated by utilizing a neural model that aims to protect the syntactic connections of the genuine sentence so that the obscured sentence can be parsed instead of the genuine one. | Evaluated on two parsers, which are the biaffine dependency parser and the constituency parser. | 1. It excels in parsing precision against a robust random baseline when several of the words in the sentence are obscured. 2. It tends to exchange words in the genuine sentence with words which have a closer syntactic function to the genuine word than a random baseline. | 1. Reduction in parsing accuracy 2. The parsed result may become less informative or less beneficial. | Applied for obfuscating natural language input like sentences. | N/A |
| Kaur et al. [48] (2022) | An encryfuscation model for preserving data and location privacy in fog-based IoT scenarios | It employs obfuscation and encryption methods. It is based on implementing a data obfuscation technique for obscuring the sensed data and a location obfuscation technique for obscuring location information. | Verified by experimental analysis. | 1. It is implemented over the data at the Secure Service Offloader (SSO) layer itself, so there is no demand to trust the fog or cloud. 2. It is hard for the attacker to reverse engineer the obscure information because of using obfuscation technique. | It utilizes just one factor like severity for making the offloading decision. Other factors like the kind of IoT service and anticipated completion time should be considered. | Applied to cloud–fog–IoT scenario. | This research can be improved by developing a convenient encryption technique for the model. |
| Category: Layout Obfuscation | |||||||
| Marcelli et al. [51] (2018) | Defeating Hardware Trojan in microprocessor cores through software obfuscation | It depends on a pure-software obfuscation technique that utilizes an evolutionary algorithm to change an executable program without influencing its functionalities. | Tested against renowned real-world hardware attacks. | 1. It reduces the probability of activation of a multistage trigger Hardware Trojan. 2. It is utilized to conserve crucial infrastructures and processes with a decreased and predictable loss of performances. | Similarly to other protection solutions that depend on a probabilistic method, this technique cannot be considered entirely dependable. | Applied to integrated circuit industry against Hardware Trojan. | This approach is inefficient versus single-stage triggers and inefficient versus triggers activated by a functional behavior. Future opportunities for this research work may include resolving these problems. |
| Balachandran et al. [54] (2014) | Obfuscation by code fragmentation to evade reverse engineering | It depends on shifting code bits from distinct parts of the program to a new code part, thus obfuscating the control flow of the program. | Tested by experimental analysis. | It performs well versus reverse engineering tools and performs better than other obfuscation techniques. | The time and space complexity of the software is maximized due to the introduction of instructions and code parts by the obfuscation technique. | Applied to binary programs. | This research can be improved by reducing the time and space complexity of the obfuscated software using the obfuscation approach. |
| Category: Preventive Transformation Obfuscation | |||||||
| Linn and Debray [55] (2003) | Obfuscation of executable code to improve resistance to static disassembly | It concentrates on the initial disassembly step. It is based on disturbing the static disassembly operation to make programs more difficult to disassemble properly. | Tested experimentally using the SPECint-95 benchmark suite. | It prevents disassembly tools from disassembling code instructions properly. | Performance degradation of obfuscated code. | Applied to executable codes against static disassembly. The system applies techniques such as inserting junk instructions and converting unconditional jumps into branch function calls to obstruct reverse engineering. Further conversions like jump table spoofing could be applied to improve the current approach. | |
| Dalai et al. [56] (2017) | A code obfuscation technique to prevent reverse engineering | It depends on hiding the proprietary code part by using preventive design obfuscation and injection of self-modifying code at the binary level. | Tested experimentally using distinct sorting algorithms. | The incorporation of design-level obfuscation and the injection of self-modifying code changes the code into a semantically equal one that makes it complicated to reverse engineer. | It is not completely consistent with parallel processing where both data and code can be shared between several threads. | Applied to software codes against reverse engineering. | This research can be improved in the future by concentrating on code obfuscation along with code parallelism. |
Appendix B

Table A2.
Detailed comparison of hardware obfuscation techniques.
Table A2.
Detailed comparison of hardware obfuscation techniques.
| Ref. | Proposed Technique | Obfuscation Processes | Evaluation Methodology | Benifits of Current Research | Cons of Current Research | Usability Within the Market | Future Opportunities and Directions |
|---|---|---|---|---|---|---|---|
| Category: DSP Core Obfuscation | |||||||
| Sengupta and Chaurasia [69] (2022) | Securing IP cores for DSP applications using structural obfuscation and chromosomal DNA impression | It is based on utilizing multilevel structural obfuscation to protect against changing register transfer level (RTL) descriptions as well as utilizing secret chromosomal DNA impression to protect against IP privateering. | Verified by applying qualitative and quantitative analysis. | 1. It is stronger than modern facial biometric and steganography-based hardware IP protection methods in terms of more powerful proof of digital clue as well as tamper tolerance capability. 2. It affords zero design cost overhead. | N/A | Applied to DSP-based IP cores versus modification of register transfer level (RTL) description and IP privateering. | N/A |
| Alaql et al. [71] (2019) | A key-error-tolerant obfuscation approach | It is based on permitting the exchanging validity of key bits with output Quality of Service (QoS) and provides agile degradation in QoS while maximizing bit error rate (BER) in the key. A CAD tool for automatic obfuscation of a design is utilized. | Tested by experimental analysis. | 1. It supplies proper functional behavior of an obfuscated design in the existence of bit failures in the key. 2. It supplies a controllable operation that permits distinct degrees of quality to be utilized for distinct IP customers. 3. It preserves an IP from untrusted examing facilities. | N/A | Applied to DSP IPs against privateering and reverse engineering. | This research work can be enhanced by tolerating a higher failure ratio in sensitive partitions, studying the efficiency of obfuscation to generic designs and more decrease in overhead. |
| Rathor and Sengupta [75] (2019) | Enhanced functional obfuscation of DSP core using flip-flops and combinational logic | It is based on a functional obfuscation of the digital signal processing (DSP) core by implementing a modern IP core locking block (ILB) logic, which impacts the structure of flip-flops and combinational circuits. These ILBs conduct the locking of the functionality of a DSP design and motivate the proper functionality just on implementation of an adequate key series. | Tested by experimental analysis. | 1. It minimizes the probability of acquiring the correct key of a functionally obfuscated design in wearisome trials. 2. It provides higher protection and lower design overhead than prior works. | N/A | Applied to digital signal processing (DSP) cores against hardware menaces like Trojan insertion, privateering, and overbuilding. | N/A |
| Kumar and Lovina [76] (2019) | Hardware obfuscation driven by QR pattern using high-level transformations | It uses FSM-based structural and functional obfuscation and key handling by utilizing color QR code pattern-driven random key extraction and accurately tests disruption metric levels. | Evaluated by experimental analysis. | 1. It achieves low potential, area, and trades off the accomplishment over protection level. 2. It prohibits the enemy from any reverse engineer operation in two degrees: the gate-degree and the RTL-degree geometry of IP from privateering and exaggeration. | N/A | Applied to digital signal processing (DSP) circuits against reverse engineering. | N/A |
| Category: Combinational/Sequential Circuits Obfuscation | |||||||
| Mirmohammadi and Borujeni [81] (2023) | Secure interference logic locking (SILL) | It depends on minimal monitorability in paths with extreme fan-out. It minimizes the number of key gates demanded for circuit obfuscation and produces the farthest Hamming distance between normal and obscure results. The key gates are appended to the circuit’s entire confusion, and the AES algorithm is utilized to produce the key. | Tested by examining SAT attack technique on ISCAS85 benchmark circuits that are obscured by SILL. | 1. It minimizes the hardware overhead while preserving its quality. 2. It minimizes the delay with the parallel application of techniques utilized in SILL. 3. It maximizes the resistance against well-known attacks like SAT. | N/A | Applied to combinational circuits against Hardware Trojan insertion. | By testing the outcomes of the application of SILL against the SAT attack, this technique meets the gauge of long attack run time, but the gauge of the number of different input styles should be considered in the future to improve this approach. |
| Yue and Tehranipoor [82] (2021) | A probability-based logic locking technique: ProbLock | It is based on utilizing a filtering operation to choose the best location of key gates based on distinct restrictions. Each stage in the filtering operation produces a subgroup of nodes for each restriction. | Evaluated on 40 obfuscated sequential and combinational benchmarks from the ISCAS85 and ISCAS89 suites against SAT attack. | It achieves strong resistance against SAT attacks. | 1. Large complexity and lack of empirical data required for comparison. 2. It utilizes the same technique and test approaches when compared to other logic locking techniques. | Applied to combinational and sequential circuits against privateering. | This technique can be strengthened against SAT attacks by combining SAT-resistant logic near the key gate locations. |
| Roshanisefat et al. [84] (2020) | Deep Faults and Shallow State Duality (DFSSD) | It depends on using two techniques to combat SAT attacks based on bounded model checking. These techniques are deep faults and shallow state dualism. | Evaluated by experimental analysis. | It permits the designer to accurately manage the depth of the fault at design time by utilizing a low overhead circuit technique and producing the attack time to be too long. | It can just preserve the design against enemies trying to completely reverse engineer an existing ASIC, and it does not preserve the IP versus an untrustworthy manufacturing facility. | Applied to FSM and sequential circuits with constrained access to the scan chain. | N/A |
| Rezaei and Zhou [86] (2021) | Sequential logic encryption against model-checking attack | It is based on logic encryption. | Tested by applying experiments on about fifty benchmarks. | It protects sequential circuits against the model-checking attack. | N/A | Applied to sequential circuits against the model-checking attacks. | N/A |
Appendix C

Table A3.
Detailed comparison of hybrid obfuscation techniques.
Table A3.
Detailed comparison of hybrid obfuscation techniques.
| Ref. | Proposed Technique | Obfuscation Processes | Evaluation Methodology | Benefits of Current Research | Cons of Current Research | Usability Within the Market | Future Opportunities and Directions |
|---|---|---|---|---|---|---|---|
| Category: Software–Software Obfuscation | |||||||
| AlHakimi et al. [6] (2020) | Hybrid obfuscation technique to protect source code from prohibited software reverse engineering | It is based on three techniques, which are string encryption, renaming, and converting identifiers to junk code to stash the meaning and maximize the intricacy of the code. | Tested by comparing the outcomes of two experiments; the first one performed reverse engineering versus Java applications which do not utilize any preservation. The second stage performed reverse engineering versus the suggested approach. | It achieves good and promising outcomes such that it is almost impossible for the reversing tool to read the obfuscated code. | N/A | Applied to Java applications against reverse engineering. | This research can be enhanced by building a framework for the automation of this approach and supplying a plug-in to assist developers in customizing the technique of obfuscation. It can also applied for huge-scale software preservation and enhancement. |
| Mahfoud et al. [96] (2020) | Hybrid obfuscation technique for reverse engineering problems | It is based on three methods of renaming, which are UNICODE Renaming Approach, String Encryption, and Identifiers Renaming to Junk Code. | Evaluated by experimental analysis. | It is efficient, as it embarrasses the compiler while reversing, and it embarrasses the reversing tool while reversing and analyzing. | This method does not prohibit reverse engineering; it embarrasses the reverser and the reversing instrument. | Applied to Java applications against reverse engineering. | Future opportunities for this research may involve enhancing this technique to prevent reverse engineering, not just embarrassing the reverser or the reversing tool. |
| Hashemzade and Maroosi [97] (2018) | A hybrid signal and encryption obfuscation technique | It depends on inserting a dispatcher into the program that changes the signal program to the genuine control flow graph. In this way, the trouble of the signal technique that involves a large number of call and return instructions is solved. This dispatcher is encrypted to keep it safe from hackers. | Tested by making a comparison of the similarity among the obscure data with its actual code and with obtainable efficient techniques. | It achieves better performance when compared to the other techniques regarding preventing reconstruction of the normal code by hackers. | N/A | Applied to C++ applications against reverse engineering. | N/A |
| Category: Hardware–Hardware Obfuscation | |||||||
| Aksoy et al. [99] (2023) | Hybrid protection of digital FIR filters | It is based on two methods which are obfuscation and locking with a point function. It is implemented to parallel direct and transferred forms of the FIR filter and its tucked application. | Evaluated by experimental analysis. | 1. It rivals prominent logic locking methods according to hardware complexity and leads to obfuscated designs that are elastic to renowned attacks. 2. It also showed that the direct form FIR filter is a perfect nominee for safe filter application. | N/A | Applied to digital Finite Impulse Response (FIR) filter against piracy. | Studying side-channel analysis (SCA) and its effectiveness in conquering obfuscation techniques keeps an enormous path for future research. |
| Nasir et al. [100] (2022) | Ephemeral key-based hybrid hardware obfuscation | It presents an ephemeral key-based hardware obfuscation with minimum resource utilization that depends on integrating static and dynamic combinational logic locking. | Evaluated by experimental analysis. | 1. It provides a black box settlement adjustable to any intellectual property, with a resource overhead of 1%. 2. It supplies reinforced preservation with minimized complexity. | N/A | Applied to ASIC ecosystem against reverse engineering (RE), IP overuse, IP piracy, and Hardware Trojan insertion. | N/A |
| Rahman et al. [98] (2023) | A register transfer (RT)-level finite state machine (FSM) obfuscation technique (ReTrustFSM) | It is based on three kinds of privacy: explicit external privacy via an exterior key, implicit external privacy depending on particular clock cycles, and internal privacy through a hidden FSM transmission function. It also determines a solid connection between the features of Boolean troubles and the needed time for deobfuscation. | Evaluated by utilizing several attacks such as machine learning, structural attacks, FSM, and functional I/O queries (BMC) attacks. | 1. It permits the designer to have more monitoring and focus on the semantics of the design, extending the nature of the menace models. 2. It provides firmness versus a larger range of menaces. 3. It achieves solidness protection at acceptable overhead/corruption while combating like-threat models. | N/A | Applied to IC manufacturing against piracy. | N/A |
| Category: Software–Hardware Obfuscation | |||||||
| Fyrbiak et al. [101] (2017) | Hybrid obfuscation to protect against disclosure attacks on embedded microprocessors | It is based on both hardware-level and software-level obfuscation conversions to prohibit several disclosure attacks. It integrates obfuscation conversions with devoted hardware booby snares to detect and comply with manipulation efforts. | Tested by providing a new statistical evaluation technique that provides protection metrics for hybrid obfuscated programs. | 1. It is efficient against a large set of potential information disclosure attacks. 2. It provides a minor hardware. 3. Overhead of up to 14% for a plain, low-cost embedded processor. | The security analysis of these techniques for processors with dedicated cache memories is not examined. | Applied for embedded processors against reverse engineering. | This research can be improved by analyzing more obfuscation conversions like code tamper-proofing anti-emulation, and self-modifying code in association with application-specific instruction-set processor methods to reduce software performance overhead. |
| McDonald et al. [106] (2021) | Software-based hardware abstraction (SBHA) | It is based on converting point functions in C programs to hardware abstractions. It supplies a normal framework where standard software obfuscation can be integrated with preservations inspired by hardware circuit obfuscation. | Tested by experimental analysis. | It is efficient in beating DSE-based attacks, with comparatively large elasticity and low overhead. | N/A | Applied to software against piracy. | Future opportunities for this research work may involve extended study of SBHA in bigger software contexts and spontaneous study of human-based reverse engineering restrictions when facing SBHA diversity. |
| Chakraborty and Srivastava [104] (2019) | A hardware–software co-design-based accelerator obfuscation (HSCAO) | It is based on utilizing proprietary SDK as the origin of confidence for producing locked program binary that is thereafter deobfuscated in the hardware. | Evaluated by experimental analysis. | It provides robust designs that are elastic to state-of-the-art SAT formulation-based attacks as well as removal or bypass-type attacks. | N/A | Applied to hardware accelerator platforms against piracy. | N/A |
| Šišejković et al. [107] (2020) | A secure hardware–software solution depending on RISC-V, logic locking, and microkernel | It is based on the integration of two parts to produce a trustworthy platform for protection-sensitive applications. The hardware part employment depends on trustworthy RISC-V-based RTL that is secured against malicious alterations using logic locking. The software stack part is supported by seL4; a secure OS depends on the most trustworthy microkernel obtainable. | Evaluated by experimental analysis. | It supplies a trusted computing base for protection-sensitive applications. It is directed toward implementing protection by design of both hardware (HW) and software (SW). | N/A | Applied to critical applications against piracy. | The result of testing the overall protection of this technique, its leniency to fault injections, and the power of the logic locking scheme can specify the foundation for future research improvements. |
Appendix D

Table A4.
Detailed comparison of deobfuscation techniques.
Table A4.
Detailed comparison of deobfuscation techniques.
| Ref. | Proposed Technique | Deobfuscation Process | Evaluation Methodology | Benifits of Current Research | Cons of Current Research | Usability Within the Market | Future Opportunities and Directions |
|---|---|---|---|---|---|---|---|
| Category: Software Deobfuscation | |||||||
| Hoekstra [112] (2021) | Deobfuscating third-party libraries in Android applications by utilizing library discovery tools | It depends on utilizing off-the-shelf library disclosure techniques for deobfuscating third-party libraries. | Tested by comparing with DeGuard deobfuscation technique that depends on statistical learning. | 1. It deobfuscates third-party libraries with huge precision. 2. It does not require a huge amount of computational resources like DeGuard. 3. Additional training samples can be added simply, while this does not occur with DeGuard. | This research utilizes a basic type of obfuscation that does not alter the structure of programs. It is not evaluated on more inclusive obfuscation types. | Deobfuscation of third-party libraries in Android apps. | This research work concentrates on handling identifier obfuscation. Future research is required to adjust and test this technique on more profound obfuscation types like class repackaging. |
| Roziere et al. [114] (2021) | A Deobfuscation Pretraining Objective for Programming Languages (DOBF) | It depends on affecting the structural aspect of programming languages and pretraining a model to return the genuine version of obscured source code. | Evaluated by experimental analysis. | 1. Models pretrained with this approach largely exceed recent techniques on several downstream functions. 2. Pretrained model is capable of deobfuscating completely obscured source files and offering descriptive variable names. | Models pretrained on source code profit from structured noise need to be tested if they can be implemented to natural languages. | Deobfuscation of obfuscated source code. | This research can be enhanced by profiting from the dependency parse trees of sentences to assist in building better pretraining objectives for natural languages. |
| Lee et al. [122] (2022) | Deobfuscating mobile malware for recognizing hidden behaviors (ARBDroid) | It depends on dynamically testing implementations to expose encrypted strings, classes, and hidden API calls. | Evaluated by analyzing obfuscated real-world malware. | It deobfuscates obscured applications efficiently depending on dynamic test outcomes. | This approach is deobfuscating using dynamic analysis, and therefore, deobfuscation is unattainable for the unexecuted code. | Deobfuscation of mobile malware applications. | Future improvements to this research can be achieved by automating the execution of Android malware to examine all probable execution approaches to deobfuscate obfuscated code in an application to the maximum extent. |
| You et al. [129] (2022) | Defeating sophisticated control flow obfuscation by utilizing Android Runtime (ART) | It performs its deobfuscation in two phases: it defines whether a control flow obfuscation method is implemented and then deobfuscates the obscured codes. | Tested by experimental analysis. | 1. It efficiently discovers and deobfuscates the codes appended by the control flow obfuscation of DexGuard. 2. It helps malware testers to reverse control-flow-obfuscated malignant Android apps. | This approach can only treat control flow obfuscation by DexGuard and does not examine control flow obfuscation by other obfuscators involving DashO and Allatori. | Deobfuscation of Android apps. | The research work on apps with anti-tampering preservation is out of the domain of this research, and this can be considered as an opportunity for future improvements of this research. |
| XIONG [131] (2022) | A general, efficient, and lightweight deobfuscation technique for PowerShell scripts | It depends on emulation-based recovery at the abstract syntax tree (AST) level to retrieve the obscured scripts. | Tested on more than 6483 obscured PowerShell scripts. | 1. It is efficacious, influential, and general. 2. It enhances the discovery rates of current virulent script detectors involving Windows Defender and the detectors in VirusTotal. | N/A | Deobfuscation of PowerShell scripts. | N/A |
| Zhao et al. [133] (2021) | A technique for the deobfuscation of binaries depend on program synthesis | It is based on obfuscating binaries depending on program synthesis and utilizes a precise obfuscation detection for finding obscured code snippets using machine learning. | Evaluated by experimental analysis. | 1. It is greatly influential in finding and deobfuscating the binaries with data obfuscation, with precision reaching at least 90.34%. 2. Its success rate was maximized by 5% and efficacy maximized by 75% by comparing with other deobfuscation techniques. | 1. It is constrained to synthesizing only straight-line programs. 2. The experiments conducted in this research only concentrate on two open-source obfuscation materials, which are still lacking in terms of being convincing. | Deobfuscation of binaries with data obfuscation. | This technique is limited to synthesizing only straight-line programs. Future improvements for this research may involve expanding this technique by synthesizing the program with a loop. |
| Category: Hardware Deobfuscation | |||||||
| Moraitis and Dubrova [132] (2023) | FPGA design deobfuscation through iterative LUT transformation at bitstream level | It depends on guaranteeing the complete controllability of every instantiated LUT input in a design via iterative LUT alteration at bitstream degree. | Tested on the example of an obscured SNOW 3G design applied on a Xilinx 7-series FPGA. | 1. It can conquer obfuscation based on constant values and probably unlock bitstreams locked by utilizing combinational logic locking. 2. It is not also influenced by the degree of privacy of the constant values or the circuit that produces them. | This approach might not be capable of deobfuscating constructions, including triple modular redundancy or other kinds of functional duplication which cover the impact of errors. | Deobfuscation of SRAM FPGA design. | N/A |
| Shamsi and Jin [128] (2021) | Circuit deobfuscation from power side channels by utilizing pseudo-Boolean SAT | It is based on utilizing a pair of attack techniques named PowerSAT attacks, which take in randomly keyed circuits and analyze key information by reacting adaptively with a side-channel “oracle”. | Tested versus simulated and real hardware traces. | It can be utilized in benign reverse engineering and hardware safety examinations. | The runtime and reliability of the PowerSAT attacks still need to be improved. | Deobfuscation of curcuits. | Enhancing the runtime and precision of the PowerSAT attacks is a significant topic for future improvements of this research. |
| Shamsi et al. [137] (2017) | AppSAT: Approximately Deobfuscating Integrated Circuits | It is based on the SAT attack augmented with random querying and medium error speculation. | Examined on 71 ISCAS and MCNC benchmark circuits obscured with the AntiSAT compound scheme. | It achieved high accuracy in deobfuscating benchmark circuits that were obscured with state-of-the-art SAT attack protections. | N/A | Deobfuscation of integrated circuits. | N/A |
Appendix E

Table A5.
Detailed comparison of obfuscation detection techniques.
Table A5.
Detailed comparison of obfuscation detection techniques.
| Ref. | Proposed Technique | Obfuscation Detection Processes | Evaluation Methodology | Benefits of Current Research | Cons of Current Research | Usability Within the Market | Future Opportunities and Directions |
|---|---|---|---|---|---|---|---|
| Ikram et al. [139] (2019) | DaDiDroid: An Android malware app detection technique | It leverages features of the weighted directed graphs of API calls to disclose the existence of malware code in obscured Android applications. | Evaluated against several elusion techniques by utilizing distinct datasets for a total of 43,262 benign and 20,431 malware apps. | 1. It is solid versus distinct code obfuscation approaches. 2. It achieved high accuracy in the classification of benign and malicious apps, reaching 96.5%. | N/A | Discovering Android malwares. | This research can be enhanced in the future by complementing characteristics originating from dynamic runtime examination of apps. |
| Bacci et al. [140] (2018) | A technique to detect whether a sample of code is modified by means of one or more obfuscation methods | It is based on instituted supervised binary classification methods (SVM, Multilayer Perceptron, and Random Forest) running on ad hoc attributes originating from static test. | Tested on a real-world dataset of Android implementations (morphed and genuine). | It is utilized for recognizing whether a mobile application is changed using one or more metamorphosis approaches. | It does not achieve high accuracy in detection for all types of obfuscation. | Detecting of obfuscated codes in mobile environments (Android). | This research achieved promising outcomes for some obfuscation methods, whereas for others, the discovery looks more difficult, which needs to be resolved in future research enhancements. |
| Aurangzeb and Aleem [142] (2023) | Assessment and categorization of obscured Android malware through deep learning | It utilizes both static and dynamic analysis by utilizing an ensemble voting approach and depends on a deep learning method using real and emulator-based platforms. | Tested by experimental analysis. | It is rapid, scalable, and rigorous in detecting obscured Android malware. | N/A | Detecting obfuscated Android malware. | Future opportunities of this research may involve testing the packed Android applications in association with implementing distinct kinds of obfuscations considering the least important features too. |
| Kim et al. [144] (2018) | Obfuscated VBA macro discovery using machine learning technique | It depends on training five machine learning techniques on 15 distinctive static metrics considering the features of the Visual Basic for Applications (VBA) macros. | Tested by utilizing a real-world dataset of obfuscated and non-obfuscated VBA macros elicited from Microsoft Office document files. | It achieved F2 score enhancement in detecting obfuscated macro code larger than 23% compared to other related studies. | This technique is used for obfuscation detection, not pernicious code detection. | Detecting obfuscated Visual Basic for Applications (VBA) macro codes. | This research can be improved in the future to handle malicious code detection. |
| Li et al. [145] (2019) | Obfusifier: obfuscation-resistant Android malware discovery technique | The training of this technique depends on obfuscation-resistant metrics elicited from unobfuscated applications, while the model retains large effectiveness for discovering obfuscated malware. | Evaluated empirically on 568 obfuscated malware. | It accomplished the accuracy, recall, and F-measure results that surpassed 95% for discovering obfuscated Android malware, well surpassing any of the prior techniques. | 1. This technique cannot treat the malware converted by the obfuscation on the native code. 2. It depends on the static test of the DEX code, but if the DEX code is encrypted and then decrypted at runtime, it cannot hold its method graph and pernicious attitudes. | Detecting obfuscated Android malware. | Future enhancements for this research may involve examining the integration of a dynamic analyzer in Obfusifier. |
| Ouk and Pak [147] (2022) | A novel technique for discovering malware residing in either native code or bytecode | It is based on supplying an integrated method for eliciting metrics from applications and native libraries by utilizing a pick algorithm that can elicit a small group of unique and efficient metrics for discovering malware applications quickly and with a high discovery rate. | Evaluated by utilizing massive Android malware detection datasets gained from several sources. | It is efficient in terms of enhanced precision, low false positive rate, and high discovery rate. | This technique considers fewer factors for the detection process of malware than other approaches. | Detecting obscured and native Android malware. | This research can be enhanced in the future by involving more factors in the detection process of malware existing in either bytecode or native code. |
| Ponomarenko and Klyucharev [148] (2020) | JavaScript code obfuscation discovery by utilizing artificial neural network with attention technique | It is based on adapting an artificial neural network model with an attention technique to resolve the trouble of script classification on the obfuscation foundation. | Evaluated by experimental analysis. | It can be applied with some enhancements in pernicious code discovery systems, mobile device fingerprint collection approaches, or browsers. | This technique achieved worse performance than the approach suggested by Tellenbach et al. [149]. | Detecting obfuscated JavaScript codes. | This research may be improved by utilizing metrics reflecting the frequencies of JavaScript keywords and other statistical computations to enhance the performance of this technique. |
References
- Asher, S.W.; Jan, S.; Tsaramirsis, G.; Khan, F.Q.; Khalil, A.; Obaidullah, M. Reverse Engineering of Mobile Banking Applications. Comput. Syst. Sci. Eng. 2021, 38, 265–278. [Google Scholar] [CrossRef]
- Eilam, E.; Chikofsky, E.J. Reversing: Secrets of Reverse Engineering; Wiley: Hoboken, NJ, USA, 2005. [Google Scholar]
- Danesh, A.S.; Saybani, M.R.; Danesh, S.Y.S. Software release management challenges in industry: An exploratory study. Afr. J. Bus. Manag. 2011, 5, 8050. [Google Scholar]
- Wang, W. Reverse Engineering: Technology of Reinvention; CRC Press: Boca Raton, FL, USA, 2010. [Google Scholar]
- Chen, C.; Pomonis, M.; Tang, A. CONFUSE: LLVM-Based Code Obfuscation. 2013. Available online: http://www.cs.columbia.edu/~aho/cs4115_Spring-2013/lectures/13-05-16_Team11_Confuse_Paper.pdf (accessed on 23 April 2025).
- Alhakimi, A.M.; Sultan, A.B.B.M.; Ali, N.M.; Ghani, A.A.A. Hybrid Obfuscation Technique to Protect Source Code From Prohibited Software Reverse Engineering. IEEE Access 2020, 8, 187326–187342. [Google Scholar] [CrossRef]
- Marius, P. Techniques of Program Code Obfuscation for Secure Software. J. Mobile Embed. Distrib. Syst. 2011, 3, 205–219. [Google Scholar]
- Sebastian, S.; Malgaonkar, S.; Shah, P.; Kapoor, M.; Parekhji, T. A Study and Review on Code Obfuscation. In Proceedings of the 2016 World Conference on Futuristic Trends in Research and Innovation for Social Welfare (WCFTR’16), Coimbatore, India, 29 February–1 March 2016. [Google Scholar]
- Ogiso, T.; Sakabe, Y.; Soshi, M.; Miyaji, A. Software Obfuscation on a Theoretical Basis and Its Implementation. Ieice Trans. Fundam. Electron. Commun. Comput. Sci. 2003, E86-A, 176–186. [Google Scholar]
- Wang, P.; Bao, Q.; Wang, L.; Wang, S.; Chen, Z.; Wei, T.; Wu, D. Software Protection on the Go: A Large-Scale Empirical Study on Mobile App Obfuscation. In Proceedings of the ICSE ’18: Proceedings of the 40th International Conference on Software Engineering, Gothenburg, Sweden, 27 May 2018–3 June 2018. [Google Scholar]
- Chen, T.; Boreli, R.; Kaafar, M.A.; Friedman, A. On the Effectiveness of Obfuscation Techniques in Online Social Networks. In Proceedings of the International Symposium on Privacy Enhancing Technologies Symposium, Amsterdam, The Netherlands, 16–18 July 2014. [Google Scholar]
- Drape, S. Intellectual Property Protection Using Obfuscation; OUCL: Oxford, UK, 2010. [Google Scholar]
- Sanz, M.G. Software Obfuscation Theory and Practice; Universidad Politécnica de Madrid: Madrid, Spain, 2023. [Google Scholar]
- Yuan, M.; Mu, Y.; Rezaeibagha, F.; Xu, L.; Huang, X. Controllable software licensing system for sub-licensing. J. Inf. Secur. Appl. 2022, 64, 103061. [Google Scholar] [CrossRef]
- Apon, D.; Huang, Y.; Katz, J.; Malozemoff, A.J. Implementing Cryptographic Program Obfuscation. IACR Cryptol. ePrint Arch. 2014, 779, 1–19. [Google Scholar]
- Asghar, H.J.; Zhao, B.Z.H.; Ikram, M.; Nguyen, G.; Kaafar, D.; Lamont, S. Use of Cryptography in Malware Obfuscation. arXiv 2023, arXiv:2212.04008v3. [Google Scholar] [CrossRef]
- Vijayakumar, A.; Patil, V.C.; Holcomb, D.E.; Paar, C.; Kundu, S. Physical Design Obfuscation of Hardware: A Comprehensive Investigation of Device- and Logic-Level Techniques. IEEE Trans. Inf. Forensics Secur. 2017, 12, 64–77. [Google Scholar] [CrossRef]
- Sidhu, S.; Mohd, B.J.; Hayajneh, T. Hardware Security in IoT Devices with Emphasis on Hardware Trojans. J. Sens. Actuator Netw. 2019, 8, 42. [Google Scholar] [CrossRef]
- Park, Y.; Dill, R.; Mullins, B.E. IoTAMU: Protecting Smart Home Networks via Obfuscation and Encryption. In Proceedings of the SECURWARE 2019: The Thirteenth International Conference on Emerging Security Information, Systems and Technologies, Nice, France, 27–31 October 2019. [Google Scholar]
- Chakraborty, S.; Tripp, O. Eavesdropping and obfuscation techniques for smartphones. In Proceedings of the MOBILESoft ’16: Proceedings of the International Conference on Mobile Software Engineering and Systems, Austin, TX, USA, 16–17 May 2016. [Google Scholar]
- Xie, C.; Cao, Z.; Long, Y.; Yang, D.; Zhao, D.; Li, B. Privacy of Autonomous Vehicles: Risks, Protection Methods, and Future Directions. arXiv 2022, arXiv:2209.04022. [Google Scholar]
- Nagaraju, P.; Rao, N.N. Obfuscation Techniques in Cloud Computing: A Systematic Survey. Int. J. Sci. Technol. Res. 2019, 8, 1097–1102. [Google Scholar]
- Balachandran, V. Software Protection Through Obfuscation. Doctoral Thesis, Nanyang Technological University, Singapore, 2014. [Google Scholar]
- Madou, M.; Anckaert, B.; Bus, B.D.; Bosschere, K.D. On the Effectiveness of Source Code Transformations for Binary Obfuscation. In Proceedings of the International Conference on Software Engineering Research and Practice and Conference on Programming Languages and Compilers, Las Vegas, NV, USA, 26–29 June 2006. [Google Scholar]
- Kumar, K.; Kaur, P. A Thorough Investigation of Code Obfuscation Techniques for Software Protection. Int. J. Comput. Sci. Eng. 2015, 3, 158–164. [Google Scholar]
- Lu, K.Z.M. Control Flow Obfuscation for FJ using Continuation Passing. arXiv 2020, arXiv:2012.06340. [Google Scholar]
- Li, C.; Huang, T.; Chen, X.; Xie, C.; Wen, W. IOLLVM: Enhance version of OLLVM. arXiv 2022, arXiv:2203.03169. [Google Scholar]
- BinShamlan, M.; Bamatraf, M.; Zain, A. The Impact of Control Flow Obfuscation Technique on Software Protection Against Human Attacks. In Proceedings of the 2019 First International Conference of Intelligent Computing and Engineering (ICOICE), Hadhramout, Yemen, 15–16 December 2019. [Google Scholar]
- Balachandran, V.; Keong, N.W.; Emmanuel, S. Function Level Control Flow Obfuscation for Software Security. In Proceedings of the 2014 Eighth International Conference on Complex, Intelligent and Software Intensive Systems (CISIS), Birmingham, UK, 2–4 July 2014. [Google Scholar]
- Al-Kushari, A.A.; Zahary, A.; Alkhawlani, M.M. Online Software Copyright Protection Using Trust Platform Module and Database Watermarking. J. Sci. Technol. 2013, 18. [Google Scholar] [CrossRef]
- Li, Y.; Kang, F.; Shu, H.; Xiong, X.; Sha, Z.; Sui, Z. COOPS: A Code Obfuscation Method Based on Obscuring Program Semantics. Secur. Commun. Netw. 2022, 2022, 6903370. [Google Scholar] [CrossRef]
- Sha, Z.H.; Shu, H.; Wu, C.-G.; Xiong, X.-B.; Kang, F. Deep Control Flow Obfuscation Model Based on Callback Function. J. Softw. 2021, 33, 1833–1848. [Google Scholar]
- Xie, X.; Liu, F.; Lu, B.; Xiang, F. An Iteration Obfuscation Based on Instruction Fragment Diversification and Control Flow Randomization. Int. J. Comput. Theory Eng. 2016, 8, 303–312. [Google Scholar] [CrossRef]
- Hashemzade, B.; Abdolrazzagh-Nezhad, M. CSE: A Novel Dynamic Obfuscation Based on Control Flow, Signals and Encryption. J. Comput. Secur. 2019, 6, 53–63. [Google Scholar]
- Gao, Z.; Huang, Y.; Zheng, L.; Lu, H.; Wu, B.; Zhang, J. Protecting Location Privacy of Users Based on Trajectory Obfuscation in Mobile Crowdsensing. IEEE Trans. Ind. Inform. 2022, 18, 6290–6299. [Google Scholar] [CrossRef]
- Popescu, A.B.; Taca, I.A.; Vizitiu, A.; Nita, C.I.; Suciu, C.; Itu, L.M.; Scafa-Udriste, A. Obfuscation Algorithm for Privacy-Preserving Deep Learning-Based Medical Image Analysis. Appl. Sci. 2022, 12, 3997. [Google Scholar] [CrossRef]
- Jiang, L.; Song, Q.; Tan, R.; Li, M. PriMask: Cascadable and Collusion Resilient Data Masking for Mobile Cloud Inference. arXiv 2022, arXiv:2211.06716. [Google Scholar]
- Saleem, M.U.; Reilly, D.; Fan, L. DP-Shield: Face Obfuscation with Differential Privacy. In Proceedings of the 25th International Conference on Extending Database Technology (EDBT), Edinburgh, UK, 29 March–1 April 2022. [Google Scholar]
- Hu, Z.; Havrylov, S.; Titov, I.; Cohen, S.B. Obfuscation for Privacy-preserving Syntactic Parsing. In Proceedings of the 16th International Conference on Parsing Technologies and the IWPT 2020 Shared Task, Seattle, WA, USA, 9 July 2020; pp. 62–72. [Google Scholar]
- Oli, S.A.; Arockiam, L. Enhanced Obfuscation Technique for Data Confidentiality in Public Cloud Storage. In Proceedings of the 2015 International Conference on Mechanical Engineering and Electrical Systems (ICMES 2015), Singapore, 16–18 December 2015; Volume 40. [Google Scholar]
- Amalarethinam, G.; Mary, B.F. Confidentiality technique for enhancing data security in public cloud storage using data obfuscation. IJCTA 2016, 8, 1–10. [Google Scholar]
- Sidhardhan, M.; Praveen, K. Data Obfuscation Using Secret Sharing. In Advanced Informatics for Computing Research; Springer: Cham, Switzerland, 2019; pp. 183–191. [Google Scholar]
- Parameswaran, R.; Blough, D. A Robust Data-obfuscation Approach for Privacy Preservation of Clustered Data. In Proceedings of the Workshop on Privacy and Security Aspects of Data Mining, Atlantic City, NJ, USA, 14–17 November 2015; pp. 18–25. [Google Scholar]
- Damiani, E.; di Vimercati, S.D.C.; Paraboschi, S.; Samarati, P. Computing Range Queries on Obfuscated Data. 2004. Available online: https://spdp.di.unimi.it/papers/ipmu04.pdf (accessed on 23 April 2025).
- Parameswaran, R.; Blough, D.M. Privacy Preserving Collaborative Filtering using Data Obfuscation. In Proceedings of the 2007 IEEE International Conference on Granular Computing, San Jose, CA, USA, 1–4 November 2007. [Google Scholar]
- Masood, R.; Vatsalan, D.; Ikram, M.; Kaafar, M.A. Incognito: A Method for Obfuscating Web Data. In Proceedings of the 2018 World Wide Web Conference (WWW ’18), International World Wide Web Conferences Steering Committee, Lyon, France, 23–27 April 2018; pp. 267–276. [Google Scholar]
- Khan, K.M.; Shaheen, M. Data Obfuscation for Privacy and Confidentiality in Cloud Computing. In Proceedings of the 2015 IEEE International Conference on Software Quality, Reliability and Security-Companion, Vancouver, BC, Canada, 3–5 August 2015; pp. 195–196. [Google Scholar]
- Kaur, J.; Agrawal, A.; Khan, R.A. Encryfuscation: A model for preserving data and location privacy in fog based IoT scenario. J. King Saud Univ.-Comput. Inf. Sci. 2022, 34, 6808–6817. [Google Scholar] [CrossRef]
- Ogigau-Neamtiu, F. Automating the Data Security Process. J. Def. Resour. Manag. 2017, 8, 91–100. [Google Scholar]
- Monikandan, S.; Arockiam, L. Confidentiality Technique to Enhance Security of Data in Public Cloud Storage using Data Obfuscatio. Indian J. Sci. Technol. 2015, 8, 1. [Google Scholar] [CrossRef]
- Marcelli, A.; Sanchez, E.; Squillero, G.; Jamal, M.U.; Imtiaz, A.; Machetti, S.; Mangani, F.; Monti, P.; Pola, D.; Salvato, A.; et al. Defeating hardware Trojan in microprocessor cores through software obfuscation. In Proceedings of the 2018 IEEE 19th Latin-American Test Symposium (LATS), Sao Paulo, Brazil, 12–14 March 2018; pp. 1–6. [Google Scholar]
- Chan, J.-T.; Yang, W. Advanced obfuscation techniques for java bytecode. J. Syst. Softw. 2004, 71, 1–10. [Google Scholar] [CrossRef]
- Popov, I.V.; Debray, S.K.; Andrews, G.R. Binary Obfuscation Using Signals. In Proceedings of the 16th USENIX Security Symposium on USENIX Security Symposium, Boston, MA, USA, 6–10 August 2007. [Google Scholar]
- Balachandran, V.; Emmanuel, S.; Keong, N.W. Obfuscation by Code Fragmentation to Evade Reverse Engineering. In Proceedings of the 2014 IEEE International Conference on Systems, Man, and Cybernetics (SMC), San Diego, CA, USA, 5–8 October 2014. [Google Scholar]
- Linn, C.; Debray, S. Obfuscation of Executable Code to Improve Resistance to Static Disassembly. In Proceedings of the 10th ACM Conference on Computer and Communications Security, Washington, DC, USA, 27–31 October 2003. [Google Scholar]
- Dalai, A.K.; Das, S.S.; Jena, S.K. A code obfuscation technique to prevent reverse engineering. In Proceedings of the 2017 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 22–24 March 2017. [Google Scholar]
- Greco, C.; Ianni, M.; Guzzo, A.; Fortino, G. Enabling Obfuscation Detection in Binary Software through eXplainable AI. IEEE Trans. Emerg. Top. Comput. 2024. [Google Scholar] [CrossRef]
- Sumathi, G.; Srivani, L.; Murthy, D.T.; Kumar, A.; Madhusoodanan, K. Hardware Obfuscation Using Different Obfuscation Cell Structures for PLDs. In Proceedings of the 2nd Singapore Cyber Security R and D Conference, Singapore, 21–22 February 2017; Volume 15. [Google Scholar]
- Shakya, B.; Tehranipoor, M.; Bhunia, S.; Forte, D. Introduction to Hardware Obfuscation: Motivation, Methods and Evaluation. In Hardware Protection Through Obfuscation; Springer International Publishing AG: New York, NY, USA, 2017. [Google Scholar]
- Amir, S.; Shakya, B.; Xu, X.; Jin, Y.; Bhunia, S.; Tehranipoor, M.; Forte, D. Development and Evaluation of Hardware Obfuscation Benchmarks. J. Hardw. Syst. Secur. 2018, 2, 142–161. [Google Scholar] [CrossRef]
- Sengupta, A.; Kachave, D.; Roy, D. Low Cost Functional Obfuscation of Reusable IP Cores used in CE Hardware through Robust Locking. IEEE Trans. Comput. Des. Integr. Circuits Syst. 2018, 38, 604–616. [Google Scholar] [CrossRef]
- Sengupta, A.; Roy, D. Protecting an Intellectual Property Core during Architectural Synthesis using High-Level Transformation Based Obfuscation. IET Electron. Lett. 2017, 53, 849–851. [Google Scholar] [CrossRef]
- Yasin, M.; Rajendran, J.; Sinanoglu, O.; Karri, R. On improving the security of logic locking. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2016, 35, 1411–1424. [Google Scholar] [CrossRef]
- Sengupta, A.; Mohanty, S. Functional Obfuscation of DSP cores using Robust Logic Locking and Encryption. In Proceedings of the 2018 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Hong Kong, China, 8–11 July 2018. [Google Scholar]
- Koteshwara, S.; Kim, C.H.; Parhi, K.K. Mode-based Obfuscation using Control-Flow Modifications. In Proceedings of the Third Workshop on Cryptography and Security in Computing Systems, Prague, Czech Republic, 20 January 2016; pp. 19–24. [Google Scholar]
- Sengupta, A.; Mohanty, S.P.; Pescador, F.; Corcoran, P. Multi-Phase Obfuscation of Fault Secured DSP Designs with Enhanced Security Feature. IEEE Trans. Consum. Electron. 2018, 64, 356–364. [Google Scholar] [CrossRef]
- Sengupta, A.; Neema, S.; Sarkar, P.; Mohanty, S.H.P.S.P.; Naskar, M.K. Obfuscation of Fault Secured DSP Design through Hybrid Transformation. In Proceedings of the 2018 IEEE Computer Society Annual Symposium on VLSI, Hong Kong, China, 8–11 July 2018. [Google Scholar]
- Lao, Y.; Parhi, K.K. Protecting DSP Circuits through Obfuscation. In Proceedings of the 2014 IEEE International Symposium on Circuits and Systems (ISCAS), Melbourne, VIC, Australia, 1–5 June 2014. [Google Scholar]
- Sengupta, A.; Rathor, M. Security of Functionally Obfuscated DSP Core Against Removal Attack Using SHA-512 Based Key Encryption Hardware. IEEE Access 2018, 7, 4598–4610. [Google Scholar] [CrossRef]
- Sengupta, A.; Chaurasia, R. Securing IP Cores for DSP Applications Using Structural Obfuscation and Chromosomal DNA Impression. IEEE Access 2022, 10, 50903–50913. [Google Scholar] [CrossRef]
- Alaql, A.; Hoque, T.; Forte, D.; Bhunia, S. Quality Obfuscation for Error-Tolerant and Adaptive Hardware IP Protection. In Proceedings of the 2019 IEEE 37th VLSI Test Symposium (VTS), Monterey, CA, USA, 23–25 April 2019. [Google Scholar]
- Priya, A.; Lakshmi, S. Obfuscating DSP Circits via High Level Transformations. IEEE Trans. Very Large Scale Integr. (Vlsi) Syst. 2015, 23, 819–830. [Google Scholar]
- Aparna, C.; Lavanya, S.; Kumaran, M.E. Obfuscating DSP Circuits Through QR Based Key Driven High- Level Transformations. In Proceedings of the International Conference on Innovative Trends in Engineering and Technology 2017, Antalya, Turkey, 21–23 August 2017. [Google Scholar]
- Sengupta, A.; Roy, D.; Mohanty, S.P. DSP Design Protection in CE through Algorithmic Transformation Based Structural Obfuscation. IEEE Trans. Consum. Electron. 2017, 63, 467–476. [Google Scholar] [CrossRef]
- Rathor, M.; Sengupta, A. Enhanced Functional Obfuscation of DSP core using Flip-Flops and Combinational logic. In Proceedings of the 2019 IEEE 9th International Conference on Consumer Electronics (ICCE-Berlin), Berlin, Germany, 8–11 September 2019. [Google Scholar]
- Kumar, D.R.V.A.S.; Lovina, P.A. Hardware Obfuscation Driven by QR Pattern using High Level Transformations. Int. J. Adv. Trends Comput. Sci. Eng. 2019, 8, 38–41. [Google Scholar]
- Blocklove, J. Hardware Intellectual Property Protection Through Obfuscation Methods. Master’s Thesis, Rochester Institute of Technology, Rochester, NY, USA, 2020. [Google Scholar]
- Amir, S.; Shakya, B.; Forte, D.; Tehranipoor, M.; Bhunia, S. Comparative Analysis of Hardware Obfuscation for IP Protection. In Proceedings of the GLSVLSI ’17: Proceedings of the on Great Lakes Symposium on VLSI 2017, Banff, AB, Canada, 10–12 May 2017. [Google Scholar]
- Karmakar, R.; Jana, S.S.; Chattopadhyay, S. A Cellular Automata Guided Obfuscation Strategy For Finite-State-Machine Synthesis. In Proceedings of the 2019 56th ACM/IEEE Design Automation Conference (DAC), Las Vegas, NV, USA, 2–6 June 2019. [Google Scholar]
- Chakraborty, R.S.; Bhunia, S. HARPOON: An obfuscation-based soc design methodology for hardware protection. IEEE Trans. Cad Integr. Circuits Syst. 2009, 28, 1493–1502. [Google Scholar] [CrossRef]
- Mirmohammadi, Z.; Borujeni, S.E. A New Optimal Method for the Secure Design of Combinational Circuits against Hardware Trojans Using Interference Logic Locking. Electronics 2023, 12, 1107. [Google Scholar] [CrossRef]
- Yue, M.; Tehranipoor, S. A Novel Probability-Based Logic-Locking Technique: ProbLock. Sensors 2021, 21, 8126. [Google Scholar] [CrossRef] [PubMed]
- Rezaei, A.; Shen, Y.; Kong, S.; Gu, J.; Zhou, H. Cyclic Locking and Memristor-based Obfuscation Against CycSAT and Inside Foundry Attacks. In Proceedings of the 2018 Design, Automation and Test in Europe Conference and Exhibition (DATE), Dresden, Germany, 19–23 March 2018. [Google Scholar]
- Roshanisefat, S.; Kamali, H.M.; Azar, K.Z.; Dinakarrao, S.M.P. DFSSD: Deep Faults and Shallow State Duality, A Provably Strong Obfuscation Solution for Circuits with Restricted Access to Scan Chain. In Proceedings of the 2020 IEEE 38th VLSI Test Symposium (VTS), San Diego, CA, USA, 5–8 April 2020. [Google Scholar]
- Meade, T.; Zhao, Z.; Zhang, S.; Pan, D.; Jin, Y. Revisit Sequential Logic Obfuscation: Attacks and Defenses. In Proceedings of the 2017 IEEE International Symposium on Circuits and Systems (ISCAS), Baltimore, MD, USA, 28–31 May 2017. [Google Scholar]
- Rezaei, A.; Zhou, H. Sequential Logic Encryption Against Model Checking Attack. In Proceedings of the 2021 Design, Automation and Test in Europe Conference and Exhibition (DATE), Virtually, 1–5 February 2021. [Google Scholar]
- Li, L.; Zhou, H. Structural Transformation for Best-Possible Obfuscation of Sequential Circuits. In Proceedings of the 2013 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Austin, TX, USA, 2–3 June 2013. [Google Scholar]
- Shamsi, K.; Li, M.; Meade, T.; Zhao, Z.; Pan, D.Z.; Jin, Y. Cyclic Obfuscation for Creating SAT-Unresolvable Circuits. In Proceedings of the on Great Lakes Symposium on VLSI 2017, Banff, AB, Canada, 10–12 May 2017; pp. 173–178. [Google Scholar]
- Rezaei, A.; Gu, J.; Zhou, H. Hybrid Memristor-CMOS Obfuscation Against Untrusted Foundries. In Proceedings of the 2019 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Miami, FL, USA, 15–17 July 2019. [Google Scholar]
- Imeson, F.; Emtenan, A.; Garg, S.; Tripunitara, M.V. Securing Computer Hardware Using 3D Integrated Circuit (IC) Technology and Split Manufacturing for Obfuscation. In Proceedings of the SEC’13: Proceedings of the 22nd USENIX Conference on Security, Washington, DC, USA, 14–16 August 2013; pp. 495–510. [Google Scholar]
- Koteshwara, S.; Kim, C.H.; Parhi, K.K. Key-Based Dynamic Functional Obfuscation of Integrated Circuits using Sequentially-Triggered Mode-Based Design. IEEE Trans. Inf. Forensics Secur. 2018, 13, 79–93. [Google Scholar] [CrossRef]
- Chakraborty, R.S.; Bhunia, S. Hardware protection and authentication through netlist level obfuscation. In Proceedings of the 2008 IEEE/ACM International Conference on Computer-Aided Design, San Jose, CA, USA, 10–13 November 2008. [Google Scholar]
- Chakraborty, R.S.; Bhunia, S. RTL Hardware IP Protection Using Key-Based Control and Data Flow Obfuscation. In Proceedings of the 2010 23rd International Conference on VLSI Design, Bangalore, India, 3–7 January 2010. [Google Scholar]
- Roy, J.A.; Koushanfar, F.; Markov, I.L. EPIC: Ending piracy of integrated circuits. In Proceedings of the 2008 Design, Automation and Test in Europe, Munich, Germany, 10–14 March 2008. [Google Scholar]
- Wintenberg, A.; Ozay, N.; Lafortune, S. Integrating Obfuscation and Control for Privacy. IEEE Trans. Autom. Control. 2025. [Google Scholar] [CrossRef]
- Mahfoud, A.; Sultan, A.B.M.; Abd, A.A.; Ali, N.M.; Admodisastro, N. Hybrid Obfuscation Technique for Reverse Engineering Problems. J. Comput. Sci. Comput. Math. 2020, 10, 55–59. [Google Scholar] [CrossRef]
- Hashemzade, B.; Maroosi, A. Hybrid Obfuscation Using Signals and Encryption. J. Comput. Netw. Commun. 2018, 2018, 6873807. [Google Scholar] [CrossRef]
- Rahman, M.S.; Guo, R.; Kamali, H.M.; Rahman, F.; Farahmandi, F.; Tehranipoor, M. ReTrustFSM: Toward RTL Hardware Obfuscation-A Hybrid FSM Approach. IEEE Access 2023, 11, 19741–19761. [Google Scholar] [CrossRef]
- Aksoy, L.; Nguyen, Q.L.; Almeida, F.; Raik, J.; Flottes, M.L.; Dupuis, S.; Pagliarini, S. Hybrid Protection of Digital FIR Filters. arXiv 2023, arXiv:2301.11115. [Google Scholar] [CrossRef]
- Nasir, N.; Malik, A.A.; Tahir, I.; Masood, A.; Riaz, N. Ephemeral Key-based Hybrid Hardware Obfuscation. In Proceedings of the 2022 19th International Bhurban Conference on Applied Sciences and Technology (IBCAST), Islamabad, Pakistan, 16–20 August 2022; pp. 646–652. [Google Scholar]
- Fyrbiak, M.; Rokicki, S.; Bissantz, N.; Tessier, R.; Paar, C. Hybrid Obfuscation to Protect against Disclosure Attacks on Embedded Microprocessors. IEEE Trans. Comput. 2017, 67, 307–321. [Google Scholar] [CrossRef]
- Zhuang, X.; Zhang, T.; Lee, H.H.S.; Pande, S. Hardware Assisted Control Flow Obfuscation for Embedded Processors. In Proceedings of the 2004 International Conference on Compilers, Architecture, and Synthesis for Embedded Systems, Washington, DC, USA, 22–25 September 2004. [Google Scholar]
- Fu, B.; Aravalli, S.K.; Abraham, J. Software Protection by Hardware and Obfuscation. In Proceedings of the 2007 International Conference on Security and Management, Las Vegas, NA, USA, 25–28 June 2007. [Google Scholar]
- Chakraborty, A.; Srivastava, A. Hardware-Software Co-Design Based Obfuscation of Hardware Accelerators. In Proceedings of the 2019 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Miami, FL, USA, 15–17 July 2019. [Google Scholar]
- Schrittwieser, S.; Katzenbeisser, S.; Merzdovnik, G.; Kieseberg, P.; Weippl, E. AES-SEC: Improving Software Obfuscation through Hardware-Assistance. In Proceedings of the 2014 Ninth International Conference on Availability, Reliability and Security, Fribourg, Switzerland, 8–12 September 2014; pp. 184–191. [Google Scholar]
- McDonald, J.T.; Manikyam, R.K.; Bardin, S.; Bonichon, R.; Andel, T.R. Program Protection through Software-based Hardware Abstraction. In Proceedings of the 18th International Conference on Security and Cryptography (SECRYPT 2021), Rome, Italy, 10–12 July 2021; pp. 247–258. [Google Scholar]
- Šišejković, D.; Merchant, F.; Reimann, L.M.; Leupers, R.; Giacometti, M.; Kegreiß, S. A Secure Hardware-Software Solution Based on RISC-V, Logic Locking and Microkernel. In Proceedings of the 23th International Workshop on Software and Compilers for Embedded Systems (SCOPES ’20), St. Goar, Germany, 25–26 May 2020; pp. 62–65. [Google Scholar]
- Yadegari, B.; Johannesmeyer, B.; Whitely, B.; Debray, S. A Generic Approach to Automatic Deobfuscation of Executable Code. In Proceedings of the 2015 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 18–20 May 2015; pp. 674–691. [Google Scholar]
- Kan, Z.; Wang, H.; Wu, L.; Guo, Y.; Luo, D. Automated Deobfuscation of Android Native Binary Code. arXiv 2019, arXiv:1907.06828. [Google Scholar]
- Ndichu, S.; Kim, S.; Ozawa, S. Deobfuscation, Unpacking, and Decoding of Obfuscated Malicious JavaScript for Machine Learning Models Detection Performance Improvement. Caai Trans. Intell. Technol. 2020, 5, 184–192. [Google Scholar] [CrossRef]
- Wressnegger, C.; Boldewin, F.; Rieck, K. Deobfuscating Embedded Malware Using Probable-Plaintext Attacks. In International Workshop on Recent Advances in Intrusion Detection; Springer: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Hoekstra, A.S. Deobfuscating Third Party Libraries in Android Applications Using Library Detection Tools. Master’s Thesis, University of Twente, Enschede, The Netherlands, 2021. [Google Scholar]
- Liang, M.; Li, Z.; Zeng, Q.; Fang, Z. Deobfuscation of Virtualization-Obfuscated Code Through Symbolic Execution and Compilation Optimization. In Information and Communications Security, Proceedings of the 19th International Conference, Beijing, China, 6–8 December 2017; Springer International Publishing: Cham, Switzerland, 2018; pp. 313–324. [Google Scholar]
- Roziere, B.; Lachaux, M.; Szafraniec, M.; Lample, G. DOBF: A Deobfuscation Pre-Training Objective for Programming Languages. arXiv 2021, arXiv:2102.07492. [Google Scholar]
- Tofighi-Shirazi, R.; Christofi, M.; Elbaz-Vincent, P.; Le, T. DoSE: Deobfuscation based on Semantic Equivalence. In Proceedings of the 8th Software Security, Protection, and Reverse Engineering Workshop, San Juan, Puerto Rico, 3–4 December 2018. [Google Scholar]
- Li, Z.; Chen, Q.A.; Xiong, C.; Chen, Y.; Zhu, T.; Yang, H. Effective and Light-Weight Deobfuscation and Semantic-Aware Attack Detection for PowerShell Scripts. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security (CCS ’19), London, UK, 11–15 November 2019. [Google Scholar]
- Säıdi, H.; Porras, P.A.; Yegneswaran, V. Experiences in Malware Binary Deobfuscation. Virus Bull. 2010, 1, 1. [Google Scholar]
- Tang, Z.; Kuang, K.; Wang, L.; Xue, C.; Gong, X.; Chen, X. SEEAD: A Semantic-Based Approach for Automatic Binary Code De-obfuscation. In Proceedings of the 2017 IEEE Trustcom/BigDataSE/ICESS, Sydney, Australia, 1–4 August 2017; pp. 261–268. [Google Scholar]
- Lee, H.; Ng, A. Spam Deobfuscation using a Hidden Markov Model. In Proceedings of the CEAS 2005—Second Conference on Email and Anti-Spam, Stanford, CA, USA, 21–22 July 2005. [Google Scholar]
- Yoo, W.; Ji, M.; Kang, M.; Yi, J.H. String Deobfuscation Scheme based on Dynamic Code Extraction for Mobile Malwares. IT Converg. Pract. 2016, 4, 1–8. [Google Scholar]
- Salwan, J.; Bardin, S.; Potet, M.L. Symbolic Deobfuscation: From Virtualized Code Back to the Original. In Proceedings of the International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, Saclay, France, 28–29 June 2018. [Google Scholar]
- Lee, D.; Jeon, G.; Lee, S.; Cho, H. Deobfuscating Mobile Malware for Identifying Concealed Behaviors. Comput. Mater. Contin. 2022, 72, 5909–5923. [Google Scholar] [CrossRef]
- Momeni, B.; Kharrazi, M. Twinner: A Framework for Automated Software Deobfuscation. Sci. Iran. 2019, 26, 3485–3509. [Google Scholar] [CrossRef]
- Saeed-uz-zaman; Li, B.; Hamid, M.; Saleem, M.; Aman, M. A4FL: Federated Adversarial Defense via Adversarial Training and Pruning Against Backdoor Attack. IEEE Access 2025, 13, 91070–91088. [Google Scholar] [CrossRef]
- Bichsel, B.; Raychev, V.; Tsankov, P.; Vechev, M. Statistical Deobfuscation of Android Applications. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security (CCS ’16), Vienna, Austria, 24–28 October 2016; pp. 343–355. [Google Scholar]
- Su, F.; Bell, J.; Kaiser, G.; Ray, B. Deobfuscating Android Applications Through Deep Learning. 2017. Available online: https://mice.cs.columbia.edu/getTechreport.php?techreportID=1632 (accessed on 23 April 2025).
- You, G.; Kim, G.; Park, J.; Cho, S.; Park, M. Reversing Obfuscated Control Flow Structures in Android Apps using ReDex Optimizer. In Proceedings of the SMA 2020: The 9th International Conference on Smart Media and Applications, Jeju, Republic of Korea, 17–19 September 2020; pp. 272–276. [Google Scholar]
- Shamsi, K.; Jin, Y. Circuit Deobfuscation from Power Side-Channels using Pseudo-Boolean SAT. In Proceedings of the 2021 IEEE/ACM International Conference On Computer Aided Design (ICCAD), Munich, Germany, 1–4 November 2021; pp. 1–9. [Google Scholar]
- You, G.; Kim, G.; Han, S.; Park, M.; Cho, S.-J. Deoptfuscator: Defeating Advanced Control-Flow Obfuscation Using Android Runtime (ART). IEEE Access 2022, 10, 61426–61440. [Google Scholar] [CrossRef]
- Garba, P.; Favaro, M. SATURN—Software Deobfuscation Framework Based On LLVM. In Proceedings of the 3rd ACM Workshop on Software Protection, London, UK, 15 November 2019; pp. 27–38. [Google Scholar]
- Xiong, C.; Li, Z.; Chen, Y.; Zhu, T.; Wang, J.; Yang, H.; Ruan, W. Generic, efficient, and effective deobfuscation and semantic-aware attack detection for PowerShell scripts. Front. Inform. Technol. Electron. Eng. 2022, 23, 361–381. [Google Scholar] [CrossRef]
- Moraitis, M.; Dubrova, E. FPGA Design Deobfuscation by Iterative LUT Modification at Bitstream Level. J. Hardw. Syst. Secur. 2023, 7, 11–24. [Google Scholar] [CrossRef]
- Zhao, Y.; Tang, Z.; Ye, G.; Gong, X.; Fang, D. Input-Output Example-Guided Data Deobfuscation on Binary. Secur. Commun. Netw. 2021, 2021, 4646048. [Google Scholar] [CrossRef]
- Lu, X.; Zhuge, J.; Wang, R.; Cao, Y.; Chen, Y. De-obfuscation and Detection of Malicious PDF Files with High Accuracy. In Proceedings of the 2013 46th Hawaii International Conference on System Sciences, Wailea, HI, USA, 7–10 January 2013. [Google Scholar]
- Sørensen, L.T.; Larsen, M.M. WordAdjust—A Deobfuscation Frontend to Content-Aware Anti-Spam Tools. 2018. Available online: https://vbn.aau.dk/ws/files/61072996/1213098364.pdf (accessed on 23 April 2025).
- Wong, M.Y.; Lie, D. Tackling runtime-based obfuscation in Android with TIRO. In Proceedings of the SEC’18: Proceedings of the 27th USENIX Conference on Security Symposium, Baltimore, MD, USA, 15–17 August 2018. [Google Scholar]
- Shamsi, K.; Li, M.; Meade, T.; Zhao, Z.; Pan, D.Z.; Jin, Y. AppSAT: Approximately deobfuscating integrated circuits. In Proceedings of the 2017 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), McLean, VA, USA, 1–5 May 2017; pp. 95–100. [Google Scholar]
- Dhanya, K.; Dheesha, O.; Kumar, T.; Vinod, P. Detection of Obfuscated Mobile Malware with Machine Learning and Deep Learning Models. In Machine Learning and Metaheuristics Algorithms, and Applications; Springer: Singapore, 2021. [Google Scholar]
- Ikram, M.; Beaume, P.; Kaafar, M.A. DaDiDroid: An Obfuscation Resilient Tool for Detecting Android Malware via Weighted Directed Call Graph Modelling. arXiv 2019, arXiv:1905.09136. [Google Scholar] [CrossRef]
- Bacci, A.; Bartoli, A.; Martinelli, F.; Medvet, E.; Mercaldo, F. Detection of Obfuscation Techniques in Android Applications. In Proceedings of the ARES 2018: Proceedings of the 13th International Conference on Availability, Reliability and Security, Hamburg, Germany, 27–30 August 2018. [Google Scholar]
- Suarez-Tangil, G.; Dash, S.K.; Ahmadi, M.; Kinder, J.; Giacinto, G.; Cavallaro, L. DroidSieve: Fast and Accurate Classification of Obfuscated Android Malware. In Proceedings of the Conference on Data and Application Security and Privacy (CODASPY), Scottsdale, AZ, USA, 22–24 March 2017. [Google Scholar]
- Aurangzeb, S.; Aleem, M. Evaluation and classifcation of obfuscated Android malware through deep learning using ensemble voting mechanism. Sci. Rep. 2023, 13, 3093. [Google Scholar] [CrossRef] [PubMed]
- Pan, J.; Mao, X. Obfuscated Malicious JavaScript Detection by Machine Learning. In Proceedings of the 2nd International Conference on Advances in Mechanical Engineering and Industrial Informatics, Hangzhou, China, 9–10 April 2016. [Google Scholar]
- Kim, S.; Hong, S.; Oh, J.; Lee, H. Obfuscated VBA Macro Detection Using Machine Learning. In Proceedings of the 2018 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, Luxembourg, 25–28 June 2018. [Google Scholar]
- Li, Z.; Sun, J.; Yan, Q.; Srisa-an, W.; Tsutano, Y. Obfusifier: Obfuscation-Resistant Android Malware Detection System. In Proceedings of the International Conference on Security and Privacy in Communication Systems, Orlando, VA, USA, 23–25 October 2019; pp. 214–234. [Google Scholar]
- Markowsky, G.; Savenko, O.; Lysenko, S.; Nicheporuk, A. The Technique for Metamorphic Viruses’ Detection Based on its Obfuscation Features Analysis. In Proceedings of the 14th International Conference on ICT in Education, Research and Industrial Applications, Kyiv, Ukraine, 14–17 May 2018; Volume 2104, pp. 680–687. [Google Scholar]
- Ouk, P.; Pak, W. Unified Detection of Obfuscated and Native Android Malware. Comput. Mater. Contin. 2022, 70, 3099–3116. [Google Scholar]
- Ponomarenko, G.; Klyucharev, P. JavaScript Programs Obfuscation Detection Method that Uses Artificial Neural Network with Attention Mechanism. In Proceedings of the Secure Information Technologies 2019 (BIT 2019), Moscow, Russia, 20–23 February 2019. [Google Scholar]
- Tellenbach, B.; Paganoni, S.; Rennhard, M. Detecting obfuscated JavaScripts from known and unknown obfuscators using machine learning. Int. J. Adv. Secur. 2016, 9, 196–206. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).