The Integration of the Internet of Things (IoT) Applications into 5G Networks: A Review and Analysis
Abstract
1. Introduction
1.1. Generations of Mobile Networks
1.2. Features and Characteristics of 5G Networks
- High Data Rates and Bandwidth. 5G networks function at considerably higher frequencies (30–300 GHz) than 4G, allowing for greatly increased data rates. They enable data rates of several tens of Gbps, crucial for applications needing rapid data transfer [9].
- Low Latency. A key feature of 5G is its extremely low latency, around 1 millisecond, which is essential for real-time uses like autonomous driving and remote surgical procedures [10].
- High Device Density. 5G networks can support a very high density of devices, with connection densities of millions of devices per square kilometer, facilitating massive Machine-Type Communications (mMTCs). This is particularly important for the Internet of Things (IoT) and smart city applications [10,11].
- Enhanced Mobile Broadband (eMBB). 5G networks can accommodate an exceptionally high concentration of devices, achieving connection densities of millions of devices for every square kilometer, enabling massive Machine-Type Communications (mMTCs) [9,11]. This situation centers on delivering high-speed internet connectivity, facilitating services such as high-definition video streaming and virtual reality. This situation centers on delivering high-speed internet connectivity, facilitating services such as high-definition video streaming and virtual reality.
- Ultra-Reliable Low Latency Communications (URLLCs)
- ○
- ○
- Massive Multiple-Input Multiple-Output (MIMO) and Beamforming. These technologies improve spectral efficiency and network capacity by allowing multiple data signals to be transmitted and received simultaneously [13].
- ○
- Millimeter Wave Spectrum. The utilization of higher-frequency bands (millimeter waves) enables faster data transmission and supports a higher density of devices [16].
- ○
- Network Slicing. This enables the construction of many virtual networks within a single physical 5G network, each customized for unique applications or services, enhancing flexibility and resource management [13].
- ○
- Edge Computing. Enhances the speed of applications that demand real-time data processing by processing data closer to its source [13].
- ○
- Dynamic Spectrum Sharing. This invention makes better use of the existing spectrum by dynamically distributing frequencies based on demand [16].
- ❖
- ❖
- Smart Grids and Energy: In the energy sector, 5G facilitates the development of smart grids by providing high-bandwidth and low-latency communication, essential for the real-time monitoring and management of power systems [12].
- ❖
- Healthcare: Telemedicine and remote surgery benefit from 5G’s low latency and high reliability, allowing for real-time data transmission and the remote control of medical devices [17].
- ❖
- ✓
- ✓
- ✓
- Interoperability: Ensuring compatibility between various IoT devices and existing technologies is crucial for the seamless integration of 5G networks [18].
1.3. IoT in 5G
- Reduced Latency: 5G’s extremely low latency is one of its biggest benefits; this is crucial for real-time applications like remote surgery and driverless cars [22].
- Greater Data Rates: To manage the massive amounts of data produced by IoT devices, 5G provides noticeably faster data transmission rates than its predecessors [23].
- ✓
- Network Slicing: Network slicing, or the creation of several virtual networks inside a single physical 5G network, is made possible by 5G. This makes it possible to provide tailored connectivity options for various IoT applications, guaranteeing top security and performance [21].
- ✓
- Advanced Communication Technologies: 5G’s capacity to serve a variety of IoT applications is enhanced by technologies like visible light communication (VLC), millimeter wave (mmWave), and multiple-input-multiple-output (MIMO) [22].
- ○
- Cost-Benefit Analysis: Although the 5G infrastructure requires a large initial investment, there are long-term advantages, such as increased energy efficiency, lower maintenance costs, and the capacity to accommodate more IoT devices, which lowers overall costs [24].
- ○
- ➢
- ➢
- ▪
- Emerging Technologies. The capabilities and uses of IoT will be further enhanced by the convergence of 5G with emerging technologies such as cloud computing, machine learning, and artificial intelligence (AI) [21].
- ▪
- ▪
- Security Enhancements. There are serious security issues when IoT and 5G are combined. It is essential to provide thorough security frameworks to safeguard IoT devices and data. This entails fixing weaknesses and putting strong security measures in place. In 5G networks, blockchain can offer a decentralized and safe way to manage IoT devices, guaranteeing safe connectivity and thwarting attacks [25,27].
- ▪
- Edge Computing and AI Integration. While edge computing’s close proximity to IoT devices can improve real-time processing and lower latency, which is especially advantageous for applications that need to analyze and respond to data instantly, artificial intelligence (AI) can improve data processing, optimize network management, and improve decision-making processes in 5G-enabled IoT systems [28].
- In the Introduction, there was a thorough examination of the changing role of the IoT in 5G networks. By initially outlining the development and comparative attributes of mobile network generations, the paper creates a foundational understanding of technological progress. It then explores the essential features and advancements of 5G networks, paving the way for an in-depth discussion on the transformative possibilities of IoT integration. Lastly, the paper underscores the potential effects and emerging trends of IoT-enabled 5G systems, providing valuable insights into how this convergence could transform communication, automation, and smart infrastructure.
- The literature review synthesizes recent research on the integration of 5G, IoT, and AI across key sectors—smart cities, industrial automation, healthcare, agriculture, and autonomous vehicles—highlighting their transformative potential, challenges, and real-world implementations. It provides a structured comparison of studies, identifying gaps (e.g., 5G reliability in smart cities, AI-ethics trade-offs) and future directions (e.g., 5G optimization, scalable IoT solutions). The review serves as a comprehensive reference for researchers and practitioners, bridging theoretical advancements with practical applications.
- Regarding the use of IoT in 5G, a comprehensive classification of AI and IoT applications in 5G across various sectors, including education, security, healthcare, and entertainment, is conducted. Moreover, an analysis of sector-specific impacts, emerging trends, and market growth emphasizes how these technologies are driving innovation and enhancing efficiency in industries such as healthcare, agriculture, and smart cities.
- Concerning the security measures needed, we present a comprehensive, multi-layered analysis of security challenges and corresponding countermeasures for integrating IoT applications within 5G networks. Moreover, we highlighted the emerging role of AI-driven security mechanisms in strengthening the resilience of 5G-enabled IoT systems.
- Finally, the challenges facing IoT integration with 5G networks are addressed in this research work since considering that addressing these challenges necessitates collaborative efforts among researchers, industry leaders, and regulatory bodies to develop standardized frameworks, robust security measures, and energy-efficient communication protocols.
- The review offers a comprehensive, sector-specific analysis of IoT applications within 5G networks, supported by structured comparison tables and statistical insights.
- It provides a unique focus on emerging technologies and security challenges, making it a practical and forward-looking reference for researchers and practitioners.
- It delivers a comprehensive and multifaceted analysis of the integration of IoT applications into 5G networks, addressing both technical and economic aspects, real-world applications, network slicing, security concerns, and the integration of emerging technologies.
- This holistic approach sets apart from existing literature and offers valuable insights for stakeholders looking to leverage the full potential of 5G–IoT integration.
2. Literature Review
2.1. Study Selection Criteria
- Relevance to 5G-IoT-AI Integration: Focus on peer-reviewed articles that explicitly address the intersection of 5G, IoT, and AI in the target sectors.
- Technological Scope: Emphasis on studies evaluating real-world implementations, architectural frameworks, or empirical validations (e.g., pilot projects, simulations, or case studies). Theoretical proposals were included only if they offered novel in-sights.
- Impact and Innovation: Prioritization of research demonstrating measurable improvements in scalability, efficiency, or sustainability, or identifying critical challenges (e.g., latency, privacy, interoperability).
- Geographical Diversity: Inclusion of studies from both early-adopter regions (e.g., Singapore, the EU) and emerging economies to capture global trends and deployment disparities.
- Methodological Rigor: Preference for studies with clear methodologies (e.g., systematic reviews, experimental validations, or bibliometric analyses) and reproducible results.
- Rationale for Criteria:
- Relevance and Scope ensure alignment with the paper’s focus on interdisciplinary integration, avoiding indirect work (e.g., standalone AI algorithms unrelated to 5G/IoT).
- Impact-driven selection highlights actionable insights for practitioners, while geographical diversity reveals contextual challenges (e.g., 5G coverage gaps in rural agriculture [29]).
- Methodological rigor safeguards against unreliable evidence, particularly important for emerging technologies where hype may overshadow empirical limitations (e.g., 5G’s uneven performance in smart cities [30]).
2.2. Smart Cities
2.3. Industrial Automation
2.4. Healthcare
2.5. Agriculture
2.6. Transportation and Autonomous Vehicles
3. Application of IoT in 5G Networks
3.1. Implementation of AI and IoT-Driven 5G Solutions
3.2. Statistical Insights and Market Trends
4. Security Measures of Integrating IoT Applications in 5G Networks
4.1. General Overview
4.2. Security Challenges in Integrating IoT Applications in 5G Networks
4.3. Security Measures for Integrating IoT Applications in 5G Networks
4.3.1. Encryption and Data Protection
4.3.2. Secure Authentication Mechanisms
4.3.3. Network Slicing Security
4.3.4. AI-Driven Threat Detection and Response
4.3.5. Secure Firmware and Software Updates
4.3.6. Edge Computing Security
4.3.7. Regulatory Compliance and Standardization
4.3.8. Comparison of Security Measures
4.4. Summary
4.4.1. Overview
4.4.2. Discussion and Recommendations
- General Recommendations:
- For any sector deploying 5G–IoT applications, a layered security architecture combining encryption, secure authentication, and continuous threat monitoring is imperative.
- Regulatory compliance with standards such as GDPR, ISO/IEC 27001, and 3GPP must be maintained across all layers.
- AI-driven SIEM and IDPS systems are highly effective in environments with high data volume and dynamic threat landscapes, such as industrial automation and defense.
5. Challenges Facing the Integration of IoT Applications in 5G Networks
5.1. Network Scalability and Congestion
- Network slicing, which allows multiple virtual networks to be created on a shared physical infrastructure, optimizing resources for specific IoT use cases [162].
5.2. Security and Privacy Concerns
- End-to-end encryption ensures that data remains protected throughout transmission.
- Blockchain technology provides decentralized and tamper-resistant security for IoT transactions.
- AI-based threat detection mechanisms that can identify and mitigate cyber threats in real-time.
5.3. Interoperability Challenges
- Developing universal communication standards to facilitate cross-platform compatibility.
- Implementing middleware solutions that translate protocols and enable seamless data exchange.
- Encouraging industry collaborations and regulatory efforts to establish standardized frameworks for IoT communication.
5.4. Energy Efficiency Constraints
5.5. Meeting Latency Requirements
- Edge computing reduces latency by processing data closer to the source rather than relying on centralized cloud servers [178].
- Network slicing ensures that latency-sensitive applications receive prioritized network resources [179].
- Advanced routing algorithms dynamically optimize data transmission paths for minimal delays [180].
6. Conclusions and Future Directions
- Urban Data Security and Privacy: Developing scalable, real-time encryption and threat detection systems to protect citizen and infrastructure data.
- Sustainable Infrastructure: Creating energy-aware communication and computing systems to support eco-friendly and resilient smart city operations.
- Edge Intelligence: Increasing the utilization of edge and fog computing to minimize latency and enable localized decision-making for essential services such as emergency responses and traffic management.
- Interoperability Standards: Formulating unified frameworks that guarantee seamless integration across devices, vendors, and city departments.
- Citizen Engagement and Accessibility: Building inclusive platforms enables residents to interact with and derive benefits from smart city services through user-friendly interfaces and personalized data features. As cities progress and embrace digital technologies, the synergistic potential of 5G and the IoT will be vital in crafting urban settings that are not only smarter but also more habitable, secure, and attuned to the needs of their residents.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Kumar, B.A.; Rao, P.T. Overview of advances in communication technologies. In Proceedings of the 2015 13th International Conference on Electromagnetic Interference and Compatibility (INCEMIC), Visakhapatnam, India, 22–23 July 2015; pp. 102–106. [Google Scholar] [CrossRef]
- Zreikat, A.I.; Al-abed, S. Performance Modelling and Analysis of LTE/Wi-Fi Coexistence. Electronics 2022, 11, 1035. [Google Scholar] [CrossRef]
- Sanneck, H. 5G Network Slicing Management for Challenged Network Scenarios. In Proceedings of the 12th Workshop on Challenged Networks (CHANTS ‘17), Snowbird, UT, USA, 20 October 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 19–20. [Google Scholar] [CrossRef]
- Zreikat, A.I.; Mathew, S. Performance Evaluation and analysis of Urban-Suburban 5G Cellular Networks. Computers 2024, 13, 108. [Google Scholar] [CrossRef]
- Li, X.; Gani, A.; Salleh, R.; Zakaria, O. The Future of Mobile Wireless Communication Networks. In Proceedings of the 2009 International Conference on Communication Software and Networks, Chengdu, China, 25–27 July 2009; pp. 554–557. [Google Scholar] [CrossRef]
- Zhao, L.; Zhao, Y.; Zhou, S.; Yu, P.; Dong, Q.; Wang, L.; Li, J. Discuss the Key Development Direction of 6G Key Technology Based on 5G Technology. In Proceedings of the 2023 2nd International Conference on Artificial Intelligence and Computer Information Technology (AICIT), Yichang, China, 15–17 September 2023; pp. 1–3. [Google Scholar] [CrossRef]
- Mshvidobadze, T. Evolution mobile wireless communication and LTE networks. In Proceedings of the 2012 6th International Conference on Application of Information and Communication Technologies (AICT), Tbilisi, Georgia, 17–19 October 2012; pp. 1–7. [Google Scholar] [CrossRef]
- Fall, M.; Balboul, Y.; Fattah, M.; Mazer, S.; Bekkali, M.E.; Kora, A.D. Towards Sustainable 5G Networks: A Proposed Coordination Solution for Macro and Pico Cells to Optimize Energy Efficiency. IEEE Access 2023, 11, 50794–50804. [Google Scholar] [CrossRef]
- Das, M.; Kumar, A. Introduction to 5G Telecommunication Network. In CMOS Analog IC Design for 5G and Beyond; Singh, S., Arya, R., Singh, M.P., Iyer, B., Eds.; Lecture Notes in Electrical Engineering; Springer: Singapore, 2021; Volume 719. [Google Scholar] [CrossRef]
- Routray, S.K.; Javali, A.; Sharma, L.; Ghosh, A.D.; Ninikrishna, T. Advanced Features and Specifications of 5G Access Network. In Intelligent Data Communication Technologies and Internet of Things. ICICI 2019; Hemanth, D., Shakya, S., Baig, Z., Eds.; Lecture Notes on Data Engineering and Communications Technologies; Springer: Cham, Switzerland, 2020; Volume 38. [Google Scholar] [CrossRef]
- Varsier, N.; Dufrène, L.; Dumay, A.; Lampin, M.Q.; Schwoerer, J. A 5G New Radio for Balanced and Mixed IoT Use Cases: Challenges and Key Enablers in FR1 Band. IEEE Commun. Mag. 2021, 59, 82–87. [Google Scholar] [CrossRef]
- Zhang, N.; Yang, J.; Wang, Y.; Chen, Q.; Kang, Z. 5G Communication for the Ubiquitous Internet of Things in Electricity:Technical Principles and Typical Applications. Proc. CSEE 2019, 39, 4015–4025. [Google Scholar] [CrossRef]
- Senthilkumar, C.; Vijay, J.; Sankar, R.; Akula, A.; Supriya, S.; Purushothaman, V. Innovative Communication Protocols And Network Architectures in 5G Technologies. In Proceedings of the 2024 3rd International Conference for Advancement in Technology (ICONAT), Goa, India, 6–8 September 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Ekta, D.; Shalli, R. Integrated Trends, Opportunities, and Challenges of 5G and Internet of Things. In Current and Future Cellular Systems: Technologies, Applications, and Challenges; John Wiley & Sons: New York, NY, USA, 2025; pp. 139–152. [Google Scholar] [CrossRef]
- Yew, H.T.; Dasuki, A.; Asmat, A.E.; Syaqir Japarudin, M.; Hafiy Herifian, M.N.; Mamat, M. Internet-of-Things: Role of 5G Wireless Communications. In Proceedings of the 2023 12th International Conference on Awareness Science and Technology (iCAST), Taichung, Taiwan, 9–11 November 2023; pp. 335–339. [Google Scholar] [CrossRef]
- Borkar, S.; Pande, H. Application of 5G next generation network to Internet of Things. In Proceedings of the 2016 International Conference on Internet of Things and Applications (IOTA), Pune, India, 22–24 January 2016; pp. 443–447. [Google Scholar] [CrossRef]
- Attaran, M. The impact of 5G on the evolution of intelligent automation and industry digitization. J. Ambient. Intell. Hum. Comput. 2023, 14, 5977–5993. [Google Scholar] [CrossRef]
- Pradeep, S.; Venkatesh, K.; Bhagavatula, S.; Roy, R.; Bhargavi, P.; Gupta, A. The Impact of 5G on Real-Time IoT Data Processing: Exploring Challenges and Innovative Solutions. In Proceedings of the 2024 International Conference on Electrical Electronics and Computing Technologies (ICEECT), Greater Noida, India, 29–31 August 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Mohseni, M.; Kanwer, B.; Singh, N.; Krishna, M.H.; Rajalakshmi, B.; Alkhafaji, M.A. A Comprehensive Analysis of the Internet of Things (IOT) in the Context of 5G Wireless Systems. In Proceedings of the 2024 4th International Conference on Innovative Practices in Technology and Management (ICIPTM), Noida, India, 21–23 February 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Amale, S.S.; Kotkar, A.N.; Jadhav, D. Exploring Impact of 5G on IoT. In Proceedings of the 2023 Second International Conference on Augmented Intelligence and Sustainable Systems (ICAISS), Trichy, India, 23–25 August 2023; pp. 1478–1485. [Google Scholar] [CrossRef]
- Mahmood, A.; Beltramelli, L.; Abedin, S.F.; Zeb, S.; Mowla, N.I.; Hassan, S.A.; Sisinni, E.; Gidlund, M. Industrial IoT in 5G-and-Beyond Networks: Vision, Architecture, and Design Trends. IEEE Trans. Ind. Inform. 2022, 18, 4122–4137. [Google Scholar] [CrossRef]
- Chettri, L.; Bera, R. A Comprehensive Survey on Internet of Things (IoT) Toward 5G Wireless Systems. IEEE Internet Things J. 2020, 7, 16–32. [Google Scholar] [CrossRef]
- Kaven, S.; Skwarek, V. Poster: Attribute Based Access Control for IoT Devices in 5G Networks. In Proceedings of the 28th ACM Symposium on Access Control Models and Technologies (SACMAT ‘23), Trento, Italy, 7–9 June 2023; Association for Computing Machinery: New York, NY, USA, 2023; pp. 51–53. [Google Scholar] [CrossRef]
- Jassim, M.M.; Mosa, M.M.; Okbi, Z.A.I.; Abdullah, S.B.; Taha, S.W.; Migo, P.; Kondakova, S. Cost-Effectiveness Analysis of IoT Deployment in 5G Networks. In Proceedings of the 2024 36th Conference of Open Innovations Association (FRUCT), Lappeenranta, Finland, 30 October–1 November 2024; pp. 493–502. [Google Scholar] [CrossRef]
- Girma, A.; Barrett, A.P. Security Challenges and Solutions in 5G-Enabled IoT Networks. In Proceedings of the Future Technologies Conference (FTC) 2024, Volume 4. FTC 2024; Arai, K., Ed.; Lecture Notes in Networks and Systems; Springer: Cham, Switzerland, 2024; Volume 1157. [Google Scholar] [CrossRef]
- Qiu, Q.; Du, X.; Yu, S.; Wang, C.; Liu, S.; Zhao, B.; Chang, L. Research on IoT Security Technology and Standardization in the 5G Era. In Security and Privacy in New Computing Environments. SPNCE 2020; Wang, D., Meng, W., Han, J., Eds.; Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering; Springer: Cham, Switzerland, 2021; Volume 344. [Google Scholar] [CrossRef]
- Montaño-Blacio, M.; Briceño-Sarmiento, J.; Pesántez-Bravo, F. 5G Network Security for IoT Implementation: A Systematic Literature Review. In International Conference on Innovation and Research; Springer International Publishing: Cham, Switzerland, 2020; pp. 28–40. [Google Scholar] [CrossRef]
- Babu, E.S.; Barthwal, A.; Kaluri, R. Sec-edge: Trusted blockchain system for enabling the identification and authentication of edge based 5G networks. Comput. Commun. 2023, 199, 10–291. [Google Scholar] [CrossRef]
- Rehman, W.U.; Koondhar, M.A.; Afridi, S.K.; Albasha, L.; Smaili, I.H.; Touti, E.; Aoudia, M.; Zahrouni, W.; Mahariq, I.; Ahmed, M. The role of 5G network in revolutionizing agriculture for sustainable development: A comprehensive review. Energy Nexus 2025, 17, 100368. [Google Scholar] [CrossRef]
- Banerjee, A.; Costa, B.; Forkan, A.R.M.; Kang, Y.-B.; Marti, F.; McCarthy, C.; Ghaderi, H.; Georgakopoulos, D.; Jayaraman, P.P. 5G enabled smart cities: A real-world evaluation and analysis of 5G using a pilot smart city application. Internet Things 2024, 28, 101326. [Google Scholar] [CrossRef]
- Huseien, G.F.; Shah, K.W. A review on 5G technology for smart energy management and smart buildings in Singapore. Energy AI 2022, 7, 100116. [Google Scholar] [CrossRef]
- Fan, W.Q.; Ismail, A.S.; Mohammed, F.; Mukred, M. AI-Driven Smart City Security and Surveillance System: A Bibliometric Analysis. In Current and Future Trends on AI Applications; Al-Sharafi, M.A., Al-Emran, M., Mahmoud, M.A., Arpaci, I., Eds.; Studies in Computational Intelligence; Springer Nature Switzerland: Cham, Switzerland, 2025; Volume 1178, pp. 305–328. [Google Scholar] [CrossRef]
- Sandhu, M.; Malhotra, R.; Singh, J. IoT Enabled -Cloud based Smart Parking System for 5G Service. In Proceedings of the 2022 1st IEEE International Conference on Industrial Electronics: Developments & Applications (ICIDeA), Bhubaneswar, India, 15–16 October 2022; pp. 202–207. [Google Scholar] [CrossRef]
- Sahu, T.; Narad, D.; Javvaji, N.K.C.; Radhapuram, S.C.T. Location based portable 5G enabled Internet of Things IoT EDGE device to measure, monitor and manage environment sensor data. In Proceedings of the 2024 5th International Conference on Computing, Networks and Internet of Things, Tokyo, Japan, 24–26 May 2024; ACM: New York, NY, USA, 2024; pp. 436–442. [Google Scholar] [CrossRef]
- Pons, M.; Valenzuela, E.; Rodríguez, B.; Nolazco-Flores, J.A.; Del-Valle-Soto, C. Utilization of 5G Technologies in IoT Applications: Current Limitations by Interference and Network Optimization Difficulties—A Review. Sensors 2023, 23, 3876. [Google Scholar] [CrossRef] [PubMed]
- Chandra Shekhar Rao, V.; Kumarswamy, P.; Phridviraj, M.S.B.; Venkatramulu, S.; Subba Rao, V. 5G Enabled Industrial Internet of Things (IIoT) Architecture for Smart Manufacturing. In Data Engineering and Communication Technology; Reddy, K.A., Devi, B.R., George, B., Raju, K.S., Eds.; Lecture Notes on Data Engineering and Communications Technologies; Springer: Singapore, 2021; Volume 63, pp. 193–201. [Google Scholar] [CrossRef]
- Giannakidou, S.; Radoglou-Grammatikis, P.; Koussouris, S.; Pertselakis, M.; Kanakaris, N.; Lekidis, A.; Kaltakis, K.; Koidou, M.P.; Metallidou, C.; Psannis, K.E.; et al. 5G-Enabled NetApp for Predictive Maintenance in Critical Infrastructures. In Proceedings of the 2022 5th World Symposium on Communication Engineering (WSCE), Nagoya, Japan, 16–18 September 2022; pp. 129–132. [Google Scholar] [CrossRef]
- Oyekanlu, E.A.; Smith, A.C.; Thomas, W.P.; Mulroy, G.; Hitesh, D.; Ramsey, M.; Kuhn, D.J.; Mcghinnis, J.D.; Buonavita, S.C.; Looper, N.A.; et al. A Review of Recent Advances in Automated Guided Vehicle Technologies: Integration Challenges and Research Areas for 5G-Based Smart Manufacturing Applications. IEEE Access 2020, 8, 202312–202353. [Google Scholar] [CrossRef]
- Teoh, Y.K.; Gill, S.S.; Parlikad, A.K. IoT and Fog-Computing-Based Predictive Maintenance Model for Effective Asset Management in Industry 4.0 Using Machine Learning. IEEE Internet Things J. 2023, 10, 2087–2094. [Google Scholar] [CrossRef]
- Taj, S.; Imran, A.S.; Kastrati, Z.; Daudpota, S.M.; Memon, R.A.; Ahmed, J. IoT-based supply chain management: A systematic literature review. Internet Things 2023, 24, 100982. [Google Scholar] [CrossRef]
- Tanegue, H.B.D.; De Paula Ferreira, W.; De Assis, R.F.; Brodeur, D. Synergies Between Virtual Commissioning and Digital Twins. Eng. Proc. 2025, 89, 12. [Google Scholar] [CrossRef]
- Javaid, M.; Haleem, A.; Singh, R.P.; Suman, R. 5G technology for healthcare: Features, serviceable pillars, and applications. Intell. Pharm. 2023, 1, 2–10. [Google Scholar] [CrossRef]
- Georgiou, K.E.; Georgiou, E.; Satava, R.M. 5G Use in Healthcare: The Future is Present. JSLS J. Soc. Laparosc. Robot. Surg. 2021, 25, e2021.00064. [Google Scholar] [CrossRef]
- Li, C.; Wang, J.; Wang, S.; Zhang, Y. A review of IoT applications in healthcare. Neurocomputing 2024, 565, 127017. [Google Scholar] [CrossRef]
- Kumar, A.; Nanthaamornphong, A.; Selvi, R.; Venkatesh, J.; Alsharif, M.H.; Uthansakul, P.; Uthansakul, M. Evaluation of 5G techniques affecting the deployment of smart hospital infrastructure: Understanding 5G, AI and IoT role in smart hospital. Alex. Eng. J. 2023, 83, 335–354. [Google Scholar] [CrossRef]
- Peralta-Ochoa, A.M.; Chaca-Asmal, P.A.; Guerrero-Vásquez, L.F.; Ordoñez-Ordoñez, J.O.; Coronel-González, E.J. Smart Healthcare Applications over 5G Networks: A Systematic Review. Appl. Sci. 2023, 13, 1469. [Google Scholar] [CrossRef]
- Picozzi, P.; Nocco, U.; Puleo, G.; Labate, C.; Cimolin, V. Telemedicine and Robotic Surgery: A Narrative Review to Analyze Advantages, Limitations and Future Developments. Electronics 2023, 13, 124. [Google Scholar] [CrossRef]
- Assimakopoulos, F.; Vassilakis, C.; Margaris, D.; Kotis, K.; Spiliotopoulos, D. AI and Related Technologies in the Fields of Smart Agriculture: A Review. Information 2025, 16, 100. [Google Scholar] [CrossRef]
- Mehannaoui, R.; Mouss, K.N.; Aksa, K. IoT-based food traceability system: Architecture, technologies, applications, and future trends. Food Control 2023, 145, 109409. [Google Scholar] [CrossRef]
- Shang, Z.; Li, Z.; Wei, Q.; Hao, S. Livestock and poultry posture monitoring based on cloud platform and distributed collection system. Internet Things 2024, 25, 101039. [Google Scholar] [CrossRef]
- Liu, J.; Shu, L.; Lu, X.; Liu, Y. Survey of Intelligent Agricultural IoT Based on 5G. Electronics 2023, 12, 2336. [Google Scholar] [CrossRef]
- Lagorio, A.; Cimini, C.; Pinto, R.; Cavalieri, S. 5G in Logistics 4.0: Potential applications and challenges. Procedia Comput. Sci. 2023, 217, 650–659. [Google Scholar] [CrossRef]
- Biswas, A.; Wang, H.-C. Autonomous Vehicles Enabled by the Integration of IoT, Edge Intelligence, 5G, and Blockchain. Sensors 2023, 23, 1963. [Google Scholar] [CrossRef]
- Hakak, S.; Gadekallu, T.R.; Maddikunta, P.K.R.; Ramu, S.P.; Parimala, M.; De Alwis, C.; Liyanage, M. Autonomous vehicles in 5G and beyond: A survey. Veh. Commun. 2023, 39, 100551. [Google Scholar] [CrossRef]
- Guevara, L.; Auat Cheein, F. The Role of 5G Technologies: Challenges in Smart Cities and Intelligent Transportation Systems. Sustainability 2020, 12, 6469. [Google Scholar] [CrossRef]
- Shakir, M.A.; Hussain, R.T.; Al-Hamadani, B.T.R.; Salih, M.M.; Salman, H.M.; Kozubtsov, I.; Aram, E. Vehicle-to-Everything (V2X) Communication in IoT via 5G. In Proceedings of the 2024 36th Conference of Open Innovations Association (FRUCT), Lappeenranta, Finland, 30 October–1 November 2024; pp. 76–87. [Google Scholar] [CrossRef]
- Kumar, A.; Albreem, M.A.; Gupta, M.; Alsharif, M.H.; Kim, S. Future 5G Network Based Smart Hospitals: Hybrid Detection Technique for Latency Improvement. IEEE Access 2020, 8, 153240–153249. [Google Scholar] [CrossRef]
- Chen, B.; Qiao, S.; Zhao, J.; Liu, D.; Shi, X.; Lyu, M.; Chen, H.; Lu, H.; Zhai, Y. A Security Awareness and Protection System for 5G Smart Healthcare Based on Zero-Trust Architecture. IEEE Internet Things J. 2021, 8, 10248–10263. [Google Scholar] [CrossRef] [PubMed]
- Siriwardhana, Y.; De Alwis, C.; Gür, G.; Ylianttila, M.; Liyanage, M. The Fight Against the COVID-19 Pandemic with 5G Technologies. IEEE Eng. Manag. Rev. 2020, 48, 72–84. [Google Scholar] [CrossRef]
- Chamola, V.; Hassija, V.; Gupta, V.; Guizani, M. A Comprehensive Review of the COVID-19 Pandemic and the Role of IoT, Drones, AI, Blockchain, and 5G in Managing its Impact. IEEE Access 2020, 8, 90225–90265. [Google Scholar] [CrossRef]
- Ahmad, I.; Asghar, Z.; Kumar, T.; Li, G.; Manzoor, A.; Mikhaylov, K.; Shah, S.A.; Höyhtyä, M.; Reponen, J.; Huusko, J.; et al. Emerging Technologies for Next Generation Remote Health Care and Assisted Living. IEEE Access 2022, 10, 56094–56132. [Google Scholar] [CrossRef]
- Jiménez, A.C.; Martínez, J.P. 5G networks in eHealth services in Spain: Remote patient monitoring system. In Proceedings of the IEEE Engineering International Research Conference (EIRCON), Lima, Peru, 21–23 October 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Cerqueira, J.; da Silva, F.V.; Vilaça, A.; Mendes, J. IoT monitoring system for post-operated patients with degenerative cervical disc herniation. In Proceedings of the International Symposium on Sensing and Instrumentation in 5G and IoT Era (ISSI), Lagoa, Portugal, 29–30 August 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Balasundaram, A.; Routray, S.; Prabu, A.V.; Krishnan, P.; Malla, P.P.; Maiti, M. Internet of Things (IoT)-Based Smart Healthcare System for Efficient Diagnostics of Health Parameters of Patients in Emergency Care. IEEE Internet Things J. 2023, 10, 18563–18570. [Google Scholar] [CrossRef]
- Khatun, M.A.; Memon, S.F.; Eising, C.; Dhirani, L.L. Machine Learning for Healthcare-IoT Security: A Review and Risk Mitigation. IEEE Access 2023, 11, 145869–145896. [Google Scholar] [CrossRef]
- Anglano, C.; Canonico, M.; Desimoni, F.; Guazzone, M.; Savarro, D. The HealthTracker System: App and Cloud-Based Wearable Multi-Sensor Device for Patients Health Tracking. Appl. Sci. 2024, 14, 887. [Google Scholar] [CrossRef]
- Humayun, M.; Almufareh, M.F.; Al-Quayed, F.; Alateyah, S.A.; Alatiyyah, M. Improving Healthcare Facilities in Remote Areas Using Cutting-Edge Technologies. Appl. Sci. 2023, 13, 6479. [Google Scholar] [CrossRef]
- Mazloomi, A.; Sami, H.; Bentahar, J.; Otrok, H.; Mourad, A. Reinforcement Learning Framework for Server Placement and Workload Allocation in Multiaccess Edge Computing. IEEE Internet Things J. 2023, 10, 1376–1390. [Google Scholar] [CrossRef]
- Li, C.H.; Mak, S.L.; Lee, C.C.; Lee, T.T.; Yuen, N.H.Y.; Tang, W.F. A Review of 5G Building Management Technologies and Applications in Smart Campus. In Proceedings of the IEEE 21st International Conference on Industrial Informatics (INDIN), Lemgo, Germany, 18–20 July 2023; pp. 1–5. [Google Scholar] [CrossRef]
- Pang, Z.; Zhao, H.; Tang, Z.; Kong, F. A Digital Twins-Based Smart Classroom Monitoring System. In Proceedings of the IEEE International Conference on Advanced Learning Technologies (ICALT), Orem, UT, USA, 10–13 July 2023; pp. 347–349. [Google Scholar] [CrossRef]
- Memos, V.A.; Minopoulos, G.; Stergiou, C.; Psannis, K.E.; Ishibashi, Y. A Revolutionary Interactive Smart Classroom (RISC) with the Use of Emerging Technologies. In Proceedings of the 2nd International Conference on Computer Communication and the Internet (ICCCI), Nagoya, Japan, 26–29 June 2020; pp. 174–178. [Google Scholar] [CrossRef]
- Yadav, P.M.; Patra, I.; Mittal, V.; Nagorao, C.G.; Udhayanila, R.; Saranya, A. Implementation of IOT on English Language Classroom Management. In Proceedings of the 3rd International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE), Greater Noida, India, 12–13 May 2023; pp. 1686–1690. [Google Scholar] [CrossRef]
- Kitkowska, A.; Brodén, K.; Abdullah, L. The Requirements, Benefits, and Barriers of IoT Solutions to Support Well-Being in Elementary Schools. IEEE Access 2024, 12, 144965–144981. [Google Scholar] [CrossRef]
- Lu, G.; Dai, J.; Qin, Z.; Guo, T.; Han, Y.; Wei, M. Research on Intelligent Monitoring and Irrigation System for Farmland Based on IoT and 5GTechnology. In Proceedings of the 8th International Conference on Automation, Control and Robotics Engineering (CACRE), Hong Kong, China, 13–15 July 2023; pp. 24–28. [Google Scholar] [CrossRef]
- Dumitrascu, M.; Hnatiuc, M.; Iov, C.J. Sensors System Based on Fuzzy Logic for Irrigation. In Proceedings of the International Symposium on Sensing and Instrumentation in 5G and IoT Era (ISSI), Lagoa, Portugal, 29–30 August 2024; pp. 1–5. [Google Scholar] [CrossRef]
- Bostani, A.; Baniamerian, A.; Zaher, A.; Shammari, M.A. Smart City Connectivity: Integrating LEO Satellites with 5G/6G for IoT and PV Monitoring. In Proceedings of the IEEE Smart Cities Futures Summit (SCFC), Marrakech, Morocco, 29–31 May 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Makondo, N.; Kobo, H.I.; Mathonsi, T.E.; Plessis, D.P.D. Implementing an Efficient Architecture for Latency Optimisation in Smart Farming. IEEE Access 2024, 12, 140502–140526. [Google Scholar] [CrossRef]
- Bhatia, S.; Mallikarjuna, B.; Gautam, D.; Gupta, U.; Kumar, S.; Verma, S. The Future IoT: The Current Generation 5G and Next Generation 6G and 7G Technologies. In Proceedings of the International Conference on Device Intelligence, Computing and Communication Technologies, (DICCT), Dehradun, India, 17–18 March 2023; pp. 212–217. [Google Scholar] [CrossRef]
- Louta, M.; Banti, K.; Karampelia, I. Emerging Technologies for Sustainable Agriculture: The Power of Humans and the Way Ahead. IEEE Access 2024, 12, 98492–98529. [Google Scholar] [CrossRef]
- Shaikh, F.K.; Karim, S.; Zeadally, S.; Nebhen, J. Recent Trends in Internet-of-Things-Enabled Sensor Technologies for Smart Agriculture. IEEE Internet Things J. 2022, 9, 23583–23598. [Google Scholar] [CrossRef]
- Xiang, W.; Yu, K.; Han, F.; Fang, L.; He, D.; Han, Q.-L. Advanced Manufacturing in Industry 5.0: A Survey of Key Enabling Technologies and Future Trends. IE Trans. Ind. Inform. 2024, 20, 1055–1068. [Google Scholar] [CrossRef]
- Humayun, M.; Jhanjhi, N.; Alruwaili, M.; Amalathas, S.S.; Balasubramanian, V.; Selvaraj, B. Privacy Protection and Energy Optimization for 5G-Aided Industrial Internet of Things. IEEE Access 2020, 8, 183665–183677. [Google Scholar] [CrossRef]
- Moloudian, G.; Hosseinifard, M.; Kumar, S.; Simorangkir, R.B.V.B.; Buckley, J.L.; Song, C.; Fantoni, G.; O’fLynn, B. RF Energy Harvesting Techniques for Battery-Less Wireless Sensing, Industry 4.0, and Internet of Things: A Review. IEEE Sens. J. 2024, 24, 5732–5745. [Google Scholar] [CrossRef]
- Hoang, T.M.; Dinh-Van, S.; Barn, B.; Trestian, R.; Nguyen, H.X. RIS-Aided Smart Manufacturing: Information Transmission and Machine Health Monitoring. IEEE Internet Things J. 2022, 9, 22930–22943. [Google Scholar] [CrossRef]
- Kabir, S.; Gope, P.; Mohanty, S.P. A Security-Enabled Safety Assurance Framework for IoT-Based Smart Homes. IEEE Trans. Ind. Appl. 2022, 59, 6–14. [Google Scholar] [CrossRef]
- Wanasinghe, T.R.; Gosine, R.G.; James, L.A.; Mann, G.K.I.; de Silva, O.; Warrian, P.J. The Internet of Things in the Oil and Gas Industry: A Systematic Review. IEEE Internet Things J. 2020, 7, 8654–8673. [Google Scholar] [CrossRef]
- Modina, N.; El-Azouzi, R.; De Pellegrini, F.; Menasche, D.S.; Figueiredo, R. Joint Traffic Offloading and Aging Control in 5G IoT Networks. IEEE Trans. Mob. Comput. 2022, 22, 4714–4728. [Google Scholar] [CrossRef]
- Honda, K.; Shibata, N.; Harada, R.; Ishida, Y.; Akashi, K.; Kaneko, S.; Miyachi, T.; Terada, J. Cooperated Traffic Shaping with Traffic Estimation and Path Reallocation to Mitigate Microbursts in IoT Backhaul Network. IEEE Access 2021, 9, 162190–162196. [Google Scholar] [CrossRef]
- Tomas, J.; Pavel, Š. Autonomous Smart Sensors for Efficient Urban Waste Management. In Proceedings of the 47th International Conference on Telecommunications and Signal Processing (TSP), Prague, Czech Republic, 10–12 July 2024; pp. 294–297. [Google Scholar] [CrossRef]
- Cao, B.; Chen, X.; Lv, Z.; Li, R.; Fan, S. Optimization of Classified Municipal Waste Collection Based on the Internet of Connected Vehicles. IEEE Trans. Intell. Transp. Syst. 2020, 22, 5364–5373. [Google Scholar] [CrossRef]
- Segura-Garcia, J.; Calero, J.M.A.; Pastor-Aparicio, A.; Marco-Alaez, R.; Felici-Castell, S.; Wang, Q. 5G IoT System for Real-Time Psycho-Acoustic Soundscape Monitoring in Smart Cities With Dynamic Computational Offloading to the Edge. IEEE Internet Things J. 2021, 8, 12467–12475. [Google Scholar] [CrossRef]
- Palattella, M.R.; Dohler, M.; Grieco, A.; Rizzo, G.; Torsner, J.; Engel, T.; Ladid, L. Internet of Things in the 5G Era: Enablers, Architecture, and Business Models. IEEE J. Sel. Areas Commun. 2016, 34, 510–527. [Google Scholar] [CrossRef]
- Prasad, A.R.; Lakshminarayanan, S.; Arumugam, S. Market Dynamics and Security Considerations of 5G. J. ICT Stand. 2018, 5, 225–250. [Google Scholar] [CrossRef]
- Gomes, J.F.; Iivari, M.; Ahokangas, P.; Isotalo, L.; Niemelä, R. Cybersecurity Business Models for IoT-Mobile Device Management Services in Futures Digital Hospitals. J. ICT Stand. 2017, 5, 107–128. [Google Scholar] [CrossRef]
- Ali Al-Samawi, M.A.; Singh, M. Effect of 5G on IOT and Daily Life Application. In Proceedings of the 3rd International Conference for Emerging Technology (INCET), Belgaum, India, 27–29 May 2022; pp. 1–5. [Google Scholar] [CrossRef]
- Dutkiewicz, E.; Jayawickrama, B.A.; He, Y. Radio spectrum maps for emerging IoT and 5G networks: Applications to smart buildings. In Proceedings of the International Conference on Electrical Engineering and Computer Science (ICECOS), Palembang, Indonesia, 22–23 August 2017. [Google Scholar] [CrossRef]
- Zhang, L.; Hao, J.; Zhao, G.; Wen, M.; Hai, T.; Cao, K. Research and Application of AI Services Based on 5G MEC in Smart Grid. In Proceedings of the IEEE Computing, Communications and IoT Applications (ComComAp), Beijing, China, 20–22 December 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Saleem, M.U.; Usman, M.R.; Yaqub, M.A.; Liotta, A.; Asim, A. Smarter Grid in the 5G Era: Integrating the Internet of Things With a Cyber-Physical System. IEEE Access 2024, 12, 34002–34018. [Google Scholar] [CrossRef]
- Daas, M.J.; Jubran, M.; Hussein, M. Energy Management Framework for 5G Ultra-Dense Networks Using Graph Theory. IEEE Access 2019, 7, 175313–175323. [Google Scholar] [CrossRef]
- Israr, A.; Yang, Q.; Israr, A. Renewable Energy Provision and Energy-Efficient Operational Management for Sustainable 5G Infrastructures. IEEE Trans. Netw. Serv. Manag. 2023, 20, 2698–2710. [Google Scholar] [CrossRef]
- Morato, A.; Frigo, G.; Tramarin, F. 5G-Enabled PMU-Based Distributed Measurement Systems: Network Infrastructure Optimization and Scalability Analysis. IEEE Trans. Instrum. Meas. 2024, 73, 1–12. [Google Scholar] [CrossRef]
- Sotres, P.; Santana, J.R.; Sanchez, L.; Lanza, J.; Munoz, L. Practical Lessons From the Deployment and Management of a Smart City Internet-of-Things Infrastructure: The SmartSantander Testbed Case. IEEE Access 2017, 5, 14309–14322. [Google Scholar] [CrossRef]
- Lee, Y.; Hwang, E.; Choi, J. A Unified Approach for Compression and Authentication of Smart Meter Reading in AMI. IEEE Access 2019, 7, 34383–34394. [Google Scholar] [CrossRef]
- Ahmadzadeh, S.; Parr, G.; Zhao, W. A Review on Communication Aspects of Demand Response Management for Future 5G IoT- Based Smart Grids. IEEE Access 2021, 9, 77555–77571. [Google Scholar] [CrossRef]
- Wang, R.; Yu, C.; Wang, J. Construction of Supply Chain Financial Risk Management Mode Based on Internet of Things. IEEE Access 2019, 7, 110323–110332. [Google Scholar] [CrossRef]
- Ahmad, A.Y.A.B.; Verma, N.; Sarhan, N.M.; Awwad, E.M.; Arora, A.; Nyangaresi, V.O. An IoT and Blockchain-Based Secure and Transparent Supply Chain Management Framework in Smart Cities Using Optimal Queue Model. IEEE Access 2024, 12, 51752–51771. [Google Scholar] [CrossRef]
- Vanmathi, C.; Farouk, A.; Alhammad, S.M.; Mangayarkarasi, R.; Bhattacharya, S.; Kasyapa, M.S.B. The Role of Blockchain in Transforming Industries Beyond Finance. IEEE Access 2024, 12, 148845–148867. [Google Scholar] [CrossRef]
- Suneesh, S.; Priya, A.S.; Abirami, K.; Dhruva, T.; Rajesh, A. Design of Flexible and Wearable Antenna for 5G IoT Application. In Proceedings of the3rd International Conference on Smart Electronics and Communication (ICOSEC), Trichy, India, 20–22 October 2022; pp. 402–407. [Google Scholar] [CrossRef]
- Patzold, M. The Benefits of Smart Wireless Technologies [Mobile Radio]. IEEE Veh. Technol. Mag. 2017, 12, 5–12. [Google Scholar] [CrossRef]
- Wu, D.; Yang, Z.; Zhang, P.; Wang, R.; Yang, B.; Ma, X. Virtual-Reality Interpromotion Technology for Metaverse: A Survey. IEEE Internet Things J. 2023, 10, 15788–15809. [Google Scholar] [CrossRef]
- Kusuma, H.M.; Shukla, V.K.; Gupta, S. Enabling VR/AR and Tactile through 5G Network. In Proceedings of the International Conference on Communication information and Computing Technology (ICCICT), Mumbai, India, 25–27 June 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Muhammad, K.; Khan, S.; Elhoseny, M.; Ahmed, S.H.; Baik, S.W. Efficient Fire Detection for Uncertain Surveillance Environment. IEEE Trans. Ind. Inform. 2019, 15, 3113–3122. [Google Scholar] [CrossRef]
- Quintana-Ramirez, I.; Sequeira, L.; Ruiz-Mas, J. An Edge-Cloud Approach for Video Surveillance in Public Transport Vehicles. IEEE Lat. Am. Trans. 2021, 19, 1763–1771. [Google Scholar] [CrossRef]
- Gravina, R.; Fortino, G. Wearable Body Sensor Networks: State-of-the-Art and Research Directions. IEEE Sens. J. 2020, 21, 12511–12522. [Google Scholar] [CrossRef]
- Putra, K.T.; Arrayyan, A.Z.; Hayati, N.; Firdaus; Damarjati, C.; Bakar, A.; Chen, H.-C. A Review on the Application of Internet of Medical Things in Wearable Personal Health Monitoring: A Cloud-Edge Artificial Intelligence Approach. IEEE Access 2024, 12, 21437–21452. [Google Scholar] [CrossRef]
- Gao, J.; Agyekum, K.O.-B.O.; Sifah, E.B.; Acheampong, K.N.; Xia, Q.; Du, X.; Guizani, M.; Xia, H. A Blockchain-SDN-Enabled Internet of Vehicles Environment for Fog Computing and 5G Networks. IEEE Internet Things J. 2019, 7, 4278–4291. [Google Scholar] [CrossRef]
- Zhang, J.; Wang, Y.; Li, S.; Shi, S. An Architecture for IoT-Enabled Smart Transportation Security System: A Geospatial Approach. IEEE Internet Things J. 2020, 8, 6205–6213. [Google Scholar] [CrossRef]
- MarketsandMarkets. Telehealth Market by Component, Mode of Delivery—Global Forecast to 2025. [Online]. Available online: https://www.marketsandmarkets.com/Market-Reports/telehealth-market-201868927.html (accessed on 13 June 2025).
- Fortune Business Insights. Precision Farming Market Size, Share & COVID-19 Impact Analysis. [Online]. Available online: https://www.fortunebusinessinsights.com/precision-farming-market-102019 (accessed on 5 April 2025).
- Business Insider. The Internet of Things in Finance. [Online]. Available online: https://www.businessinsider.com/artificial-intelligence (accessed on 13 June 2025).
- Narciandi-Rodriguez, D.; Aveleira-Mata, J.; García-Ordás, M.T.; Alfonso-Cendón, J.; Benavides, C.; Alaiz-Moretón, H. A cybersecurity review in IoT 5G networks. Internet Things 2024, 30, 101478. [Google Scholar] [CrossRef]
- Hasan, M.K.; Ghazal, T.M.; Saeed, R.A.; Pandey, B.; Gohel, H.; Eshmawi, A.A.; Abdel-Khalek, S.; Alkhassawneh, H.M. A review on security threats, vulnerabilities, and counter measures of 5G enabled Internet-of-Medical-Things. IET Commun. 2021, 16, 421–432. [Google Scholar] [CrossRef]
- Moudoud, H.; Khoukhi, L.; Cherkaoui, S. Prediction and Detection of FDIA and DDoS Attacks in 5G Enabled IoT. IEEE Netw. 2020, 35, 194–201. [Google Scholar] [CrossRef]
- Basin, D.; Dreier, J.; Hirschi, L.; Radomirovic, S.; Sasse, R.; Stettler, V. A formal analysis of 5G authentication. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Mumbai, India, 25–27 June 2021; pp. 1383–1396. [Google Scholar] [CrossRef]
- Valadares, D.C.; Will, N.C.; Sobrinho, Á.Á.C.; Lima, A.C.; Morais, I.S.; Santos, D.F. Security challenges and recommendations in 5G-IoT scenarios. In Advanced Information Networking and Applications, Proceedings of the 37th International Conference on Advanced Information Networking and Applications (AINA-2023), Volume 3; Springer International Publishing: Cham, Switzerland, 2023; pp. 558–573. [Google Scholar] [CrossRef]
- Rachakonda, L.P.; Siddula, M.; Sathya, V. A comprehensive study on IoT privacy and security challenges with focus on spectrum sharing in Next-Generation networks (5G/6G/beyond). High-Confid. Comput. 2024, 4, 100220. [Google Scholar] [CrossRef]
- Dritsas, E.; Trigka, M. A Survey on Cybersecurity in IoT. Futur. Internet 2025, 17, 30. [Google Scholar] [CrossRef]
- Zafir, E.I.; Akter, A.; Islam, M.; Hasib, S.A.; Islam, T.; Sarker, S.K.; Muyeen, S. Enhancing security of Internet of Robotic Things: A review of recent trends, practices, and recommendations with encryption and blockchain techniques. Internet Things 2024, 28, 101357. [Google Scholar] [CrossRef]
- Nguyen, V.-L.; Lin, P.-C.; Cheng, B.-C.; Hwang, R.-H.; Lin, Y.-D. Security and privacy for 6G: A survey on prospective technologies and challenges. IEEE Commun. Surv. Tutorials 2021, 23, 2384–2428. [Google Scholar] [CrossRef]
- Bernstein, D.J.; Lange, T. Post-quantum cryptography. Nature 2017, 549, 188–194. [Google Scholar] [CrossRef]
- Almarri, S.; Frikha, M. Authentication and Access Control Mechanisms to Secure IoT Environments: A comprehensive SLR. Preprints 2024. [Google Scholar] [CrossRef]
- Al-Aqrabi, H.; Lane, P.; Hill, R. Performance evaluation of multiparty authentication in 5G IIoT environments. In Cyberspace Data and Intelligence, and Cyber-Living, Syndrome, and Health, Proceedings of the International 2020 Cyberspace Congress, CyberDI/CyberLife 2020, Beijing, China, 10–12 December 2020; Springer: Singapore, 2019; pp. 169–184. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Shetty, S.; Gope, P.; Rodrigues, J.J.P.C. Security in 5G-enabled internet of things communication: Issues, challenges, and future research roadmap. IEEE Access 2020, 9, 4466–4489. [Google Scholar] [CrossRef]
- Fang, H.; Wang, X.; Tomasin, S. Machine learning for intelligent authentication in 5G and beyond wireless networks. IEEE Wirel. Commun. 2019, 26, 55–61. [Google Scholar] [CrossRef]
- Ahmad, I.; Shahabuddin, S.; Kumar, T.; Okwuibe, J.; Gurtov, A.; Ylianttila, M. Security for 5G and beyond. IEEE Commun. Surv. Tutorials 2019, 21, 3682–3722. [Google Scholar] [CrossRef]
- Zhang, J.; Li, G.; Marshall, A.; Hu, A.; Hanzo, L. A New frontier for IoT security emerging from three decades of key generation relying on wireless channels. IEEE Access 2020, 8, 138406–138446. [Google Scholar] [CrossRef]
- Olimid, R.F.; Nencioni, G. 5G network slicing: A security overview. IEEE Access 2020, 8, 99999–100009. [Google Scholar] [CrossRef]
- Ahmad, I.; Pinola, J.; Harjula, I.; Suomalainen, J.; Harjula, E.; Huusko, J.; Kumar, T. An overview of the security landscape of virtual mobile networks. IEEE Access 2021, 9, 169014–169030. [Google Scholar] [CrossRef]
- Manda, J.K. AI-powered Threat Intelligence Platforms in Telecom: Leveraging AI for Real-time Threat Detection and Intelligence Gathering in Telecom Network Security Operations. Int. J. Multidiscip. Curr. Educ. Res. (IJMCER) SSRN 2024, 6, 333–340. [Google Scholar] [CrossRef]
- Gilbert, C.; Gilbert, M. AI-driven threat detection in the internet of things (IoT), exploring opportunities and vulnerabilities. Int. J. Res. Publ. Rev. 2024, 5, 219–236. [Google Scholar] [CrossRef]
- Rahman, A.-U.; Mahmud, M.; Iqbal, T.; Saraireh, L.; Kholidy, H.; Gollapalli, M.; Musleh, D.; Alhaidari, F.; Almoqbil, D.; Ahmed, M.I.B. Network Anomaly Detection in 5G Networks. Math. Model. Eng. Probl. 2022, 9, 397–404. [Google Scholar] [CrossRef]
- Benzaid, C.; Taleb, T. AI for beyond 5G networks: A cyber-security defense or offense enabler? IEEE Netw. 2020, 34, 140–147. [Google Scholar] [CrossRef]
- El Jaouhari, S.; Bouvet, E. Secure firmware Over-The-Air updates for IoT: Survey, challenges, and discussions. Internet Things 2022, 18, 100508. [Google Scholar] [CrossRef]
- Bettayeb, M.; Nasir, Q.; Talib, M.A. Firmware update attacks and security for IoT devices: Survey. In Proceedings of the ArabWIC 6th Annual International Conference Research Track, Rabat, Morocco, 7–9 March 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Falas, S.; Konstantinou, C.; Michael, M.K. A modular end-to-end framework for secure firmware updates on embedded systems. ACM J. Emerg. Technol. Comput. Syst. 2021, 18, 1–19. [Google Scholar] [CrossRef]
- Fazeldehkordi, E.; Grønli, T.-M. A survey of security architectures for edge computing-based IoT. IoT 2022, 3, 332–365. [Google Scholar] [CrossRef]
- Xiao, Y.; Jia, Y.; Liu, C.; Cheng, X.; Yu, J.; Lv, W. Edge computing security: State of the art and challenges. Proc. IEEE 2019, 107, 1608–1631. [Google Scholar] [CrossRef]
- Nguyen, T.; Nguyen, H.; Gia, T.N. Exploring the integration of edge computing and blockchain IoT: Principles, architectures, security, and applications. J. Netw. Comput. Appl. 2024, 226, 103884. [Google Scholar] [CrossRef]
- Zhukabayeva, T.; Zholshiyeva, L.; Karabayev, N.; Khan, S.; Alnazzawi, N. Cybersecurity Solutions for Industrial Internet of Things–Edge Computing Integration: Challenges, Threats, and Future Directions. Sensors 2025, 25, 213. [Google Scholar] [CrossRef] [PubMed]
- ISO/IEC 27001:2022; Information Security, Cybersecurity and Privacy Protection, Information Security Management Systems Requirements. ISO/IEC: Geneva, Switzerland, Edition 3. 2022. Available online: https://www.iso.org/standard/27001 (accessed on 13 June 2025).
- Alshar’e, M. Cyber security framework selection: Comparision of NIST and ISO27001. Appl. Comput. J. 2023, 1, 245–255. [Google Scholar] [CrossRef]
- Cisco. What Is Network Segmentation? Cisco. n.d. Available online: https://www.cisco.com/c/en/us/products/security/what-is-network-segmentation.html (accessed on 17 March 2025).
- Savage, L.; McLaughlin, P. Getting the Most Out of Your Counsel When Implementing a Mobile Computing Strategy, Including Thorny Issues Like Privacy, Reimbursement, and Standard of Care. In Mobile Medicine; Productivity Press: New York, NY, USA, 2021; pp. 133–150. [Google Scholar]
- Sarkar, S.; Choudhary, G.; Shandilya, S.K.; Hussain, A.; Kim, H. Security of zero trust networks in cloud computing: A comparative review. Sustainability 2022, 14, 11213. [Google Scholar] [CrossRef]
- He, Y.; Huang, D.; Chen, L.; Ni, Y.; Ma, X.; Huo, Y. A Survey on zero trust architecture: Challenges and future trends. Wirel. Commun. Mob. Comput. 2022, 2022, 6476274. [Google Scholar] [CrossRef]
- Ahmed, M.; Raza, S.; Soofi, A.A.; Khan, F.; Khan, W.U.; Xu, F.; Chatzinotas, S.; Dobre, O.A.; Han, Z. A survey on reconfigurable intelligent surfaces assisted multi-access edge computing networks: State of the art and future challenges. Comput. Sci. Rev. 2024, 54, 100668. [Google Scholar] [CrossRef]
- Zhang, D. Research on 5G System Security in Ultra-Reliable Low-Latency Communication Scenario. In Proceedings of the 2023 3rd International Conference on Communication Technology and Information Technology (ICCTIT), Xi’an, China, 24–26 November 2023; pp. 34–38. [Google Scholar] [CrossRef]
- Moon, S.; Lee, J.-W. Integrated Grant-Free Scheme for URLLC and mMTC. 5G World Forum 2020, 3, 98–102. [Google Scholar] [CrossRef]
- Saravanan, N.; Jothi Lakshmi, G.R. Revolutionizing Connectivity: Unveiling Next-Gen Efficiency with 6G’s Ultra-Reliable Low Latency Communications Resource Allocation. In Proceedings of the 2024 First International Conference on Pioneering Developments in Computer Science & Digital Technologies (IC2SDT), Delhi, India, 2–4 August 2024; pp. 451–455. [Google Scholar] [CrossRef]
- Guo, X.; Dong, Z.; Yang, H. Research on the Standardization Direction of 5G and IoT Integration. In Proceedings of the 2023 International Conference on Intelligent Computing and Next Generation Networks (ICNGN), Hangzhou, China, 17–18 November 2023; pp. 1–5. [Google Scholar] [CrossRef]
- Dlamini, B.M.; Migabo, E.M.; Kurien, A.M. A Multi-Layer Strategy for Reducing Network Congestion and Enhancing Performance in 5G IoT Networks. In Proceedings of the 2024 4th International Multidisciplinary Information Technology and Engineering Conference (IMITEC), Vanderbijlpark, South Africa, 27–29 November 2024; pp. 39–46. [Google Scholar] [CrossRef]
- Tufeanu, L.-M.; Vochin, M.-C.; Paraschiv, C.-L.; Li, F.Y. Enabling Reinforcement Learning for Network Slice Management in Multi-Agent 5G Networks. In Proceedings of the 2023 IEEE 9th World Forum on Internet of Things (WF-IoT), Aveiro, Portugal, 12–27 October 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Lanka, S.; Win, T.A.; Eshan, S. A Review on Edge Computing and 5G in IoT: Architecture & Applications. In Proceedings of the 2021 5th International Conference on Electronics, Communication and Aerospace Technology (ICECA), Coimbatore, India, 2–4 December 2021; pp. 532–536. [Google Scholar] [CrossRef]
- Arun, V.; Azhagiri, M. Design of Long-Term Evolution Based Mobile Edge Computing Systems to Improve 5G Systems. In Proceedings of the 2023 2nd International Conference on Edge Computing and Applications (ICECAA), Namakkal, India, 19–21 July 2023; pp. 160–165. [Google Scholar] [CrossRef]
- Zhang, Q.; Wu, B.; Zheng, M.; Ni, L.; Xue, B. IoT Device Attack Surface Feature Identification Using Differentiated Dynamic Monitoring. In Proceedings of the 2022 IEEE 5th International Conference on Automation, Electronics and Electrical Engineering (AUTEEE), Shenyang, China, 18–20 November 2022; pp. 435–440. [Google Scholar] [CrossRef]
- Jemal, I.; Cheikhrouhou, O.; Haddar, M.A. IoT DoS and DDoS Attacks Detection Using an Effective Convolutional Neural Network. Cyberworlds 2023, 1, 373–379. [Google Scholar] [CrossRef]
- Mann, P.; Tyagi, N.; Gautam, S.; Rana, A. Classification of Various Types of Attacks in IoT Environment. In Proceedings of the 2020 12th International Conference on Computational Intelligence and Communication Networks (CICN), Bhimtal, India, 25–26 September 2020; pp. 346–350. [Google Scholar] [CrossRef]
- Thankappan, M.; Rifà-Pous, H.; Garrigues, C. A Signature-Based Wireless Intrusion Detection System Framework for Multi-Channel Man-in-the-Middle Attacks Against Protected Wi-Fi Networks. IEEE Access 2024, 12, 23096–23121. [Google Scholar] [CrossRef]
- Balfaqih, M. Enhancing Security and Flexibility in Smart Locker Systems: A Multi-Authentication Approach with IoT Integration. In Proceedings of the 2024 21st Learning and Technology Conference (L&T), Jeddah, Saudi Arabia, 15–16 January 2024; pp. 325–329. [Google Scholar] [CrossRef]
- Alfaw, A.; Elmedany, W.; Sharif, M.S. Risk Management for 5G-Enabled Internet of Things by Using Machine Learning: A Survey. In Proceedings of the 2024 Arab ICT Conference (AICTC), Manama, Bahrain, 27–28 February 2024; pp. 87–94. [Google Scholar] [CrossRef]
- Bhatnagar, R.; Sinha, D.; Rawat, P. An Intelligent Fog Node Solution for Application Interoperability in 5G Enabled Fog-IoT Paradigm. In Proceedings of the 2022 IEEE Delhi Section Conference (DELCON), New Delhi, India, 11–13 February 2022; pp. 1–5. [Google Scholar] [CrossRef]
- Chahar, S.; Kaur, K. Internet of Things with 5G Technology: A Critical Review. In Proceedings of the 2023 3rd International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE), Greater Noida, India, 12–13 May 2023; pp. 1402–1406. [Google Scholar] [CrossRef]
- Choi, M.; Ha, S.; Lim, J. Methods to Improve Energy Efficiency and Availability of IoT Devices in Wireless Environments. In Proceedings of the 2024 15th International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Republic of Korea, 16–18 October 2024; pp. 376–378. [Google Scholar] [CrossRef]
- Yildirim, D.U.; Jung, J.; Elsakka, A.; Moschetti, G.; Lopez, M.M.; Hansryd, J.; Palacios, T.; Chandrakasan, A.P. A 0.7 cm2, 3.5 GHz, −31 dBm Sensitivity Battery-Free 5G Energy-Harvester Backscatterer With 20s Cold-Start Wake-Up Time for IoT-Enabled Warehouses. IEEE JSSC 2024, 1–11. [Google Scholar] [CrossRef]
- Sanchez-Gomez, J.; Carrillo, D.G.; Sanchez-Iborra, R.; Hernandez-Ramos, J.L.; Granjal, J.; Marin-Perez, R.; Zamora-Izquierdo, M.A. Integrating LPWAN Technologies in the 5G Ecosystem: A Survey on Security Challenges and Solutions. IEEE Access 2020, 8, 216437–216460. [Google Scholar] [CrossRef]
- Oliveira, A.; Pinto, M.F.; Lopes, F.; Leal, A.; Teixeira, C.A. Classifier Combination Supported by the Sleep-Wake Cycle Improves EEG Seizure Prediction Performance. IEEE Trans. Biomed. Eng. 2024, 71, 2341–2351. [Google Scholar] [CrossRef] [PubMed]
- Kar, S.; Mishra, P.; Wang, K.-C. 5G-IoT Architecture for Next Generation Smart Systems. 5G World Forum 2021, 4, 241–246. [Google Scholar] [CrossRef]
- Alqahtani, A.M. Real-time Resource Management Mechanism for Mobile IoT Devices in 5G-enabled Edge Computing. In Proceedings of the 2024 13th International Conference on Computer Technologies and Development (TechDev), Huddersfield, UK, 9–11 October 2024; pp. 85–90. [Google Scholar] [CrossRef]
- Bandara, E.; Shetty, S.; Rahman, A.; Mukkamala, R.; Liang, X. Moose: A Scalable Blockchain Architecture for 5G Enabled IoT with Sharding and Network Slicing. In Proceedings of the 2022 IEEE Wireless Communications and Networking Conference (WCNC), Austin, TX, USA, 10–13 April 2022; pp. 1194–1199. [Google Scholar] [CrossRef]
- Wang, W.; Zhu, H.; Jiang, C.; Zhang, N.; Wang, Y.; Yang, Y. Adaptive Dynamic Routing Algorithm for 5G Integrated Networks Based on Virtual Routing Plane. In Proceedings of the 2023 IEEE 7th Information Technology and Mechatronics Engineering Conference (ITOEC), Chongqing, China, 14–16 December 2018; pp. 2283–2288. [Google Scholar] [CrossRef]
- Ahmed, S.F.; Alam, M.S.B.; Afrin, S.; Rafa, S.J.; Taher, S.B.; Kabir, M.; Muyeen, S.M.; Gandomi, A.H. Toward a Secure 5G-Enabled Internet of Things: A Survey on Requirements, Privacy, Security, Challenges, and Opportunities. IEEE Access 2024, 12, 13125–13145. [Google Scholar] [CrossRef]
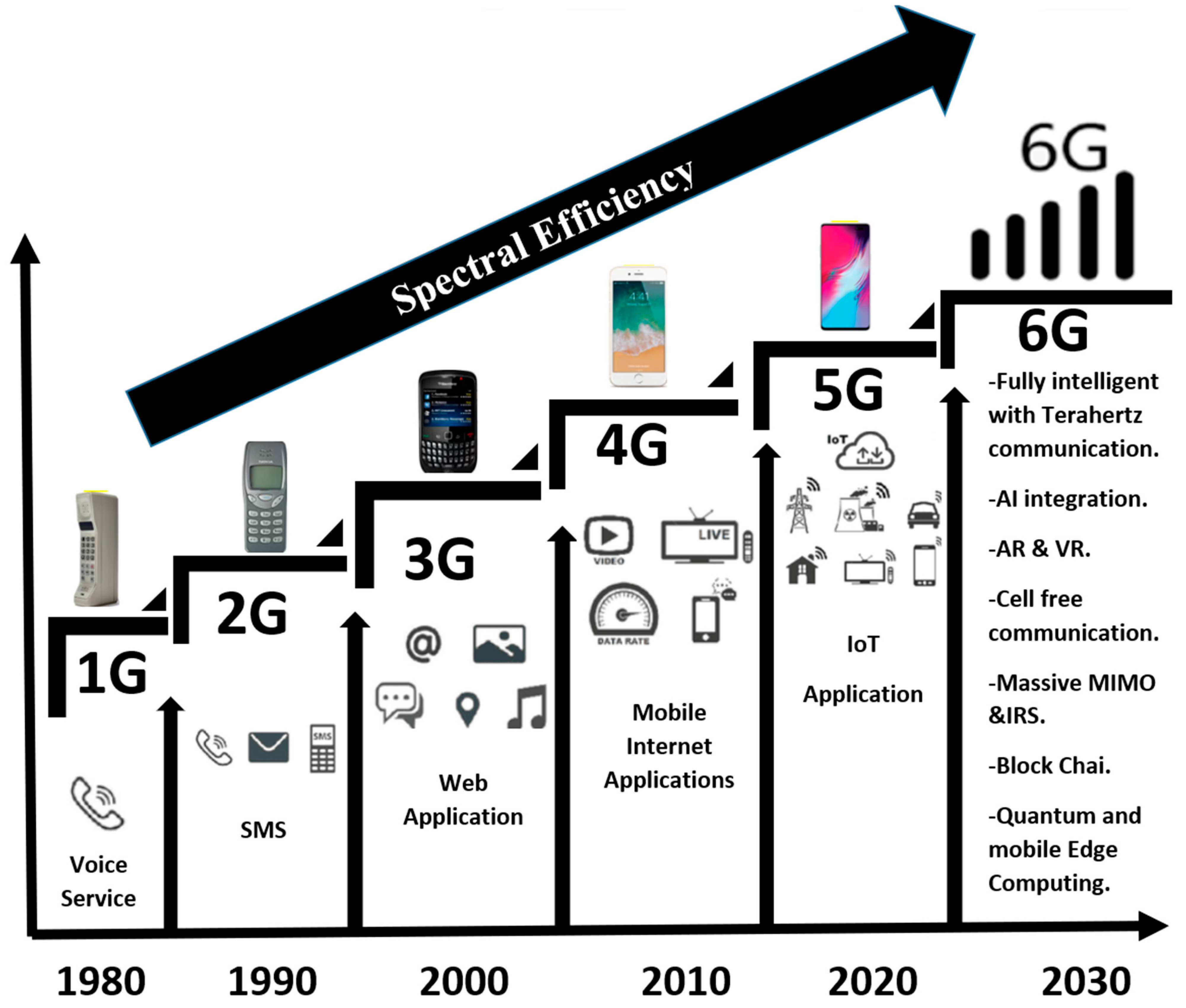

| Generation | Introduction Year | Key Features | Technologies/Standards | Applications | Data Rate | Latency |
|---|---|---|---|---|---|---|
| 1G | 1980s | Analog voice | AMPS, TACS | Voice calls | 2.4 kbps | High |
| 2G | 1990s | Digital voice, SMS | GSM, CDMA, TDMA | Voice calls, text messaging | 64 kbps | High |
| 3G | 2000s | Mobile data, video calls | UMTS, CDMA2000 | Video calls, mobile internet | 2 Mbps | Medium |
| 4G | 2010s | High-speed internet, IP-based | LTE, WiMAX | HD video streaming, video conferencing | 100 Mbps–1 Gbps | Low |
| 5G | 2020s | Ultra-fast internet, IoT, low latency | NR (New Radio), mmWave | IoT, smart cities, AR/VR | 1–10 Gbps | Ultra-low |
| 6G | 2030s (expected) | AI integration, extremely high data rates | Under development | Seamless integration of billions of IoT devices, AI, and smart cities | 1 Tbps | Near-zero |
| Paper | Focus Area | Key Contributions | Methodology/Approach | Findings/Limitations | Technology Highlighted |
|---|---|---|---|---|---|
| [30] | 5G for Smart City IoT | Evaluates 5G performance in real-world smart city applications (road asset monitoring) | 6-month pilot project with IoT-based monitoring using waste collection trucks | 5G shows potential but has performance variations; it may not meet real-time demands fully | 5G, IoT |
| [31] | 5G for Smart Buildings | Examines 5G’s role in sustainable smart buildings (Singapore case study) | Review of global trends, R&D, and Singapore’s 5G test bed initiatives | 5G enhances construction/management; serves as a benchmark for future smart city projects | 5G, Smart Buildings |
| [32] | Smart City Security | Bibliometric analysis of security/surveillance in smart cities (745 Scopus articles) | Co-citation, co-occurrence, and bibliographic coupling analyses (1977–2023) | Highlights AI-privacy tension; calls for ethical AI governance in urban surveillance | AI, Surveillance, Ethics |
| [33] | IoT-based Smart Parking | Proposes a cloud-based smart parking system with real-time spot optimization | Mobile apps and 5G-enabled IoT sensors for cloud connectivity | Improves parking efficiency, scalability, and low-cost data transmission | IoT, 5G, Cloud |
| [34] | IoT Environmental Monitoring | Real-time environmental data visualization via web app (air quality, weather, etc.) | Hardware–software integration with edge-to-cloud connectivity | Scalable, user-friendly solution for remote monitoring and data analysis | IoT, Edge/Cloud, Web App |
| [35] | 5G-IoT Integration | Analyzes interference challenges in 5G-IoT systems and optimization techniques | Review of architecture, implementations, and interference mitigation strategies | Interference issues critical; optimization needed for reliable IoT business applications | 5G, IoT, Interference Mitigation |
| Paper | Focus Area | Key Contributions | Methodology/Approach | Findings/Limitations | Technology Highlighted |
|---|---|---|---|---|---|
| [36] | 5G-IIoT for Smart Manufacturing | Proposes 5G-enabled IIoT architecture for CPMS (eMBB, mMTC, URLLC, NB-IoT) | Integrates 5G features to overcome 3G/4G limitations in industrial automation | Enhances real-time monitoring, collaboration, and efficiency in smart factories | 5G, IIoT, CPMS |
| [37] | AI/5G for Predictive Maintenance | AI-driven 5G NetApp for fault detection in energy infrastructures (autoencoder-based) | Containerized data collection and anomaly detection in power plants | Improves equipment reliability; enables real-time monitoring and maintenance | 5G, AI, Autoencoders |
| [38] | AGV/AMR Communication | Reviews wireless challenges for AGV/AMR fleet management in smart factories | Analyzes latency/reliability gaps; proposes 5G slicing, tactile Internet, VR solutions | Current tech falls short; 5G integration needed for coordination in Industry 4.0 | AGV, AMR, 5G Slicing |
| [39] | Fog Computing in Industry 4.0 | GA and ML for predictive maintenance and resource optimization in fog computing | Compares GA with MinMin/MaxMin/FCFS/RoundRobin via FogWorkflowSim | GA outperforms: 0.48% faster, 5.43% cheaper, 28.1% less energy; 95% prediction accuracy | GA, ML, Fog Computing |
| [40] | IoT in Supply Chain Management | SLR on IoT-based SCM (2018–2022): tracking, asset management, efficiency | Reviews GPS/RFID/NFC applications, challenges, and economic impacts | IoT enhances real-time SCM but faces integration and scalability hurdles | IoT, RFID, GPS, NFC |
| [41] | VC & Digital Twins | Explores VC-DT synergy for Industry 4.0; proposes integration strategies | Identifies shared components (digital models) and collaboration frameworks | Combined use boosts model reusability and process optimization | Virtual Commissioning, Digital Twins |
| Paper | Focus Area | Key Contributions | Methodology/Approach | Findings/Limitations | Technology Highlighted |
|---|---|---|---|---|---|
| [42] | 5G in Smart Healthcare | Outlines 5G’s role in remote monitoring, AI integration, and resource allocation | Reviews 5G features (eMBB, URLLC) and healthcare applications | Improves accessibility but faces coverage challenges in obstructed areas | 5G, AI, IoMT |
| [43] | 5G Adoption in Healthcare | Advocates for awareness to accelerate 5G adoption in clinical/research settings | Analyzes 13 studies on 5G’s clinical/administrative potential | Nontechnical barriers (e.g., awareness) delay implementation | 5G, Telemedicine |
| [44] | IoT in Healthcare | Examines IoT sensors for remote monitoring and personalized care | Reviews real-world IoT applications (e.g., wearables) and challenges | Highlights data security and interoperability issues | IoT, Wearables |
| [45] | 5G–IoT-AI in Smart Hospitals | Proposes PAPR reduction algorithm for 5G waveforms (NOMA, FBMC, OFDM) | Optimizes signal detection/spectrum sensing for throughput/efficiency gains | Enhances power efficiency, remote care, and cost reduction | 5G, AI, IoT, NOMA |
| [46] | 5G Smart Healthcare Review | PRISMA-based review of 5G’s role in IoMT and remote care | Analyzes 56.81% proposals vs. 15.91% implementations due to ongoing 5G deployment | eMBB/URLLC enables low-latency care but face security challenges | 5G, IoMT, PRISMA |
| [47] | Telesurgery | Assesses robotic telesurgery’s potential to overcome geographical barriers | Reviews benefits (cost reduction) and adoption challenges (latency, ethics) | Limited clinical adoption despite technological readiness | Robotics, 5G, ICT |
| Paper | Focus Area | Key Contributions | Methodology/Approach | Findings/Limitations | Technology Highlighted |
|---|---|---|---|---|---|
| [48] | IoT/AI/ML in Agriculture | Comprehensive review of smart farming, precision livestock, and regenerative agriculture | Synthesizes research, innovations, and case studies | Boosts productivity/sustainability; addresses food security and SDGs | IoT, AI, ML |
| [49] | IoT-based Food Traceability | Proposes simplified FTS definition and new IoT–FTS architecture and classification | Classifies technologies into IMT, CT, DMT; explores 5G/DLT applications | Improves food safety/consumer confidence; gaps in standardization | IoT, 5G, DLT |
| [50] | Livestock Monitoring | IoT-based system for real-time livestock health inspection (posture analysis) | Distributed master-slave hardware with RS485/MQTT protocols and cloud/mobile integration | Effective for remote monitoring in large-scale farming; meets accuracy requirements | IoT, MQTT, Cloud Computing |
| [51] | 5G-IoT in Smart Agriculture | Conceptual framework for 5G-IoT architecture/applications in agriculture | Reviews 5G–IoT developments and use cases; identifies challenges | Enhances production/sustainability; needs research to address implementation hurdles | 5G, IoT |
| [29] | 5G in Smart Farming | Examines 5G’s role in UAVs, AI analytics, and SDG-aligned farming | Discusses challenges (infrastructure, security) and AI/AR/VR applications | Promotes sustainable farming; calls for stakeholder collaboration | 5G, AI, UAVs, AR/VR |
| Paper | Focus Area | Key Contributions | Methodology/Approach | Findings/Limitations | Technology Highlighted |
|---|---|---|---|---|---|
| [52] | 5G in Logistics 4.0 | Maps 5G’s role in Smart Logistics (IoT/AI/big data integration) | Systematic literature review of 5G applications in logistics | Optimizes efficiency but faces adoption challenges (e.g., infrastructure, cost) | 5G, IoT, AI, Big Data |
| [53] | AV Tech Integration | Reviews IoT/edge/5G/blockchain for AV safety and sustainability | Comprehensive review of enabling technologies and implementation challenges | Highlights the need for seamless integration of heterogeneous technologies | AVs, 5G, Blockchain, Edge AI |
| [54] | 5G/B5G for AVs | Analyzes 5G’s URLLC/massive connectivity for AV deployment | Surveys AV automation levels, 5G integration, and security/standardization efforts | Identifies security concerns and the need for B5G advancements | 5G, B5G, Autonomous Vehicles |
| [55] | 5G for Smart Cities/ITS | Examines 5G’s role in IoT/IoV for dense/high-speed environments | Discusses technical/economic/legal challenges of 5G deployment | Overcomes 4G limitations but faces regulatory hurdles | 5G, IoV, ITS |
| [56] | 5G–V2X Communication | Evaluates 5G’s impact on V2X (safety, traffic, energy efficiency) | Compares 5G-V2X with older networks; explores edge/AI/blockchain synergies | Enhances low-latency V2V/V2I/V2P but requires infrastructure upgrades | 5G, V2X, Edge Computing, AI |
| Sector | Application | References |
|---|---|---|
| Health | Smart hospital | Kumar [57], Chen [58], Siriwardhana [59] |
| Telemedicine | Chen [58], Chakola [60], Ahmad [61] | |
| Patient monitoring | Jiménez [62], Cerqueira [63], Balasundaram [64] | |
| Treatment | Khatun [65], Anglano [66], Humayun [67] | |
| Education | Distance learning | Mazloomi [68], Li [69] |
| Smart classroom | Pang [70], Memos [71], Yadav [72] | |
| Security | Kitkowska [73] | |
| Agriculture | Irrigation | Lu [74], Dumitrascu [75] |
| Monitoring | Bostani [76], Makondo [77] | |
| Prediction | Bhatia [78] | |
| Decision making | Louta [79], Shaikh [80] | |
| Industry | Manufacturing | Xiang [81], Humayun [82] |
| Maintenance | Moloudian [83], Hoang [84] | |
| Safety | Kabir [85], Wanasinghe [86] | |
| City Development | Transportation | Modina [87], Honda [88] |
| Waste management | Tomas [89], Cao [90] | |
| Monitoring | Segura-Garcia [91], Palattella [92] | |
| Retail | Marketing | Prasad [93], Gomez [94] |
| Smart shopping | Al-Samawi [95], Dutkiewicz [96] | |
| Energy | Smart grids | Zhang [97], Saleem [98] |
| Energy management | Daas [99], Israr [100] | |
| Infrastructure monitoring | Morato [101], Sotres [102] | |
| Smart meters | Lee [103], Ahmadzadeh [104] | |
| Finance | Risk monitoring | Wang [105], Ahmed [106] |
| Smart applications | Vanmathi [107] | |
| Entertainment | Smart Tv | Suneesh [108], Patzold [109] |
| Virtual reality | Wu [110], Kusuma [111] | |
| Defense | Surveillance | Muhammad [112], Quintana-Ramirez [113] |
| Wearable devices | Gravina [114], Gravina [115] | |
| Smart vehicles | Gao [116], Zhang [117] |
| Sector | Application | Statistics |
|---|---|---|
| Health [57,58,116] | -5G remote patient monitoring via IoT -Telemedicine | 31% of patients in the USA had remote monitoring in 2021. AI integration will increase this number. |
| Education [69,70,71,118,119] | -Distance learning, especially virtual reality/augmented reality-based learning -Smart classrooms | -The 5G-enabled education market will reach $404 billion by 2026. -VR in the education market will grow 40.7% by 2027. |
| Smart cities [76,118,119,120] | -Real-time traffic monitoring -Surveillance and automated response systems for public safety | -By 2026, there will be over 60 million 5G smart city connections globally. -60% of devices will have smart city applications by 2026. -Market size is expected to be $820.7 by 2027. |
| Agriculture [74,77,120] | -IoT sensors monitor soil conditions, crop health, and weather patterns. -Monitoring with wearable devices | The smart farming market is growing, which is $21.8 billion in 2024 and is expected 113.16$ billion by 2034. |
| Industry [81,82,119] | -Enhancing automation and real-time communication -IoT-based maintenance and early detection | The IoT and AI-based 5G technology market will reach $263.4 billion by 2027. |
| Finance [106,107,118] | -Smart ATM: Real-time monitoring and maintenance in ATM machines -Fraud detection | -Finance sectors reach $2.03 billion in the 2023 market via 5G. -Finance technology in the IoT and AI market will reach $309.98 billion by 2028. |
| Defense [105,118,119,120] | -AI-based 5G has more reliable communication technologies in the military -IoT-based drones and other technologies improve monitoring capabilities | -The global market is expected to reach $90 billion in 2025. -AI based 5G defense technology market increased 28% from 2020 to 2025. |
| Energy [98,101,119] | -Smart grids increase energy consumption, increase energy efficiency, and reliability | -The global smart energy market will reach $60 billion by 2027. -5G based grid market is expected to increase by 24% from 2022 to 2030. |
| Region | IoT in 4G | IoT in 5G |
|---|---|---|
| China | 3B+ IoT devices (4G) | 900M+ 5G IoT (30% of global share by 2025) |
| USA | 1.5B+ 4G IoT connections | 100M+ 5G IoT devices (smart cities, agriculture) |
| EU | ~700M total IoT devices over 4G | 150M+ 5G IoT devices by 2023, esp. in Germany & NL |
| South Korea | 4G-based wearables and mobile IoT | 15M+ 5G IoT devices (autonomous driving, hospitals) |
| UAE/KSA | Minimal 4G IoT in 2015 | 100M+ 5G devices planned for 2025 (smart cities, security) |
| Encryption Technique | Description | Advantages | Limitations | Reference |
|---|---|---|---|---|
| Advanced Encryption Standard (AES) | A symmetric encryption algorithm is widely used for securing data. | High efficiency and strong security for data at rest and in transit. | Require secure key management; not inherently suitable for end-to-end encryption. | [127] |
| Transport Layer Security (TLS) | A cryptographic protocol designed to provide secure communication over a computer network. | Ensures data integrity and privacy between applications and users. | Vulnerable to certain attacks if not properly configured; relies on PKI for certificate management. | [128] |
| Datagram Transport Layer Security (DTLS) | An adaptation of TLS for datagram-based applications, such as those using UDP. | Provides similar security guarantees to TLS for applications requiring low latency. | Susceptible to packet loss and reordering; complexity in implementation. | [128] |
| Homomorphic Encryption | Allows computations to be performed on ciphertexts, generating an encrypted result that, when decrypted, matches the result of operations performed on the plaintext. | Enables data processing without exposing sensitive information; it is beneficial for cloud computing and data analytics. | Computationally intensive; overhead performance currently limits practical applications. | [129] |
| Quantum-Resistant Cryptography | Cryptographic algorithms are designed to be secure against attacks by quantum computers. | Provides long-term security in the advent of quantum computing; essential for future-proofing cryptographic systems. | Many algorithms are still under research and standardization, with potential performance trade-offs. | [130] |
| Authentication Mechanism | Description | Advantages | Limitations | Reference |
|---|---|---|---|---|
| Multi-Factor Authentication (MFA) | Combines two or more authentication factors (e.g., passwords, biometrics, tokens) to verify user identity. | Enhances security by requiring multiple forms of verification; reduces reliance on passwords alone. | May introduce usability challenges; requires additional infrastructure. | [131] |
| Biometric Verification | Utilizes unique biological traits (e.g., fingerprints, facial recognition) for authentication. | Provides high security due to the uniqueness of biometric data; convenient for users. | Privacy concerns, potential for false positives/negatives; requires specialized hardware. | [131] |
| Blockchain-Based Identity Management | Employs decentralized ledger technology to manage and verify identities securely. | Tamper-resistant; eliminates single points of failure; enhances transparency. | Scalability issues, high computational requirements, and regulatory uncertainties. | [132] |
| Public Key Infrastructure (PKI) | Uses asymmetric cryptography to issue and manage digital certificates for authentication. | Establishes a trusted environment; widely adopted standard. | Complex certificate management; potential vulnerabilities if private keys are compromised. | [133] |
| Zero Trust Architecture (ZTA) | Assumes no implicit trust within the network; continuously verifies every user and device attempting to access resources. | Minimizes attack surfaces; adaptable to modern threats; enforces strict access controls. | Implementation complexity may require significant changes to existing infrastructure. | [134] |
| Security Mechanism | Description | Advantages | Limitations | Reference |
|---|---|---|---|---|
| Micro-Segmentation | Divides the network into smaller, isolated segments to limit the lateral movement of threats. | Enhances security by containing breaches within segments; provides granular security controls. | Complexity in implementation requires comprehensive network visibility. | [135] |
| Access Control Lists (ACLs) | Rules that permit or deny traffic flow based on predefined security policies. | Simple to implement; effective in controlling traffic and enforcing policies. | It can become unmanageable in large-scale networks; it lacks the intelligence to adapt to new threats. | [136] |
| Real-Time Monitoring | Continuous observation of network traffic to detect and respond to anomalies. | Enables prompt threat detection and response; improves situational awareness. | High resource consumption; potential for false positives. | [137] |
| Secure Access Service Edge (SASE) | Converges networking and security functions into a unified, cloud-delivered service model. | Simplifies security management; provides consistent security policies across all network slices. | Dependence on cloud providers; integration challenges with existing infrastructure. | [138] |
| AI-Driven Security System | Description | Advantages | Limitations | Reference |
|---|---|---|---|---|
| AI-Powered Threat Intelligence Platforms | Utilize AI to gather and analyze threat data, providing real-time insights and proactive defense strategies. | Enhances situational awareness; enables swift response to emerging threats. | Dependence on data quality; potential for high false-positive rates. | [139] |
| AI-Driven Intrusion Detection and Prevention Systems (IDPSs) | Employ ML algorithms to identify and mitigate unauthorized access attempts and network anomalies. | Adaptive learning capabilities improve detection accuracy over time. | Requires continuous training; may struggle with novel attack vectors. | [140] |
| AI-Based Anomaly Detection Systems | Analyze patterns in network traffic to identify deviations indicative of potential threats. | Effective in detecting unknown threats; reduces reliance on signature-based detection. | High computational requirements; potential for false alarms. | [141] |
| AI-Enhanced Security Information and Event Management (SIEM) Systems | Integrate AI to process and correlate security events from various sources, facilitating comprehensive threat analysis. | Streamlines incident response; improves threat visibility across the network. | Complexity in integration; potential data overload without proper filtering. | [142] |
| Security Mechanism | Description | Advantages | Limitations | Reference |
|---|---|---|---|---|
| Secure Over-the-Air (OTA) Updates | Enables wireless delivery of firmware and software updates to IoT devices, ensuring timely patching of vulnerabilities. | Facilitates efficient and widespread deployment of updates; reduces the need for physical access to devices. | Requires robust security protocols to prevent unauthorized access during transmission. | [143] |
| Code Signing | Utilizes digital signatures to verify the authenticity and integrity of firmware and software before installation. | Prevents installation of malicious or tampered code; ensures that only code from trusted sources is executed. | Relies on secure key management; compromised signing keys can undermine security. | [143] |
| Firmware Integrity Verification | Employs checksums or cryptographic hashes to validate firmware integrity during boot or update processes. | Detects unauthorized modifications; enhances trust in device operation. | May not prevent initial compromise; requires secure storage of integrity metrics. | [144] |
| Trusted Platform Modules (TPMs) | Hardware-based security components that store cryptographic keys and perform secure operations. | Provides hardware-rooted security; enhances protection against software-based attacks. | Increases hardware complexity and cost; integration with existing systems. | [145] |
| Security Mechanism | Description | Advantages | Limitations | Recent Research Reference |
|---|---|---|---|---|
| Data Encryption | Encrypts data to prevent unauthorized access during transmission and storage. | Ensures confidentiality and integrity of data; protects against eavesdropping and tampering. | Requires effective key management; may introduce computational overhead. | [146] |
| Secure Hardware Enclaves | Utilizes hardware-based isolated execution environments to protect sensitive data and code. | Provides strong security against physical and software attacks; enhances trust in edge devices. | Increases hardware complexity and cost; limited scalability. | [147] |
| Decentralized Identity Management | Employs distributed ledger technologies like blockchain for identity verification without central authorities. | Enhances privacy and security; reduces single points of failure; improves scalability. | Faces challenges in standardization and interoperability; potential performance issues. | [148] |
| Confidential Computing with Trusted Execution Environments (TEEs) | Uses TEEs to process data securely within protected areas of processors, ensuring code and data confidentiality. | Protects data in use; mitigates risks of data exposure during processing; enhances overall security posture. | Limited availability across devices; potential overhead performance. | [149] |
| Security Measure | Description | Advantages | Challenges | Reference |
|---|---|---|---|---|
| Network Segmentation | Dividing the network into smaller, isolated segments | Limits the spread of attacks and contains breaches | Requires careful planning and management | [152] |
| Strong Authentication | Implementing MFA and digital certificates | Ensures only authorized devices can access the network | It can be complex to implement and manage | [153] |
| Encryption | Encrypting data in transit and at rest | Protects sensitive information from unauthorized access | Can introduce latency, requires key management | [153] |
| Regular Updates | Regularly updating firmware and software | Addresses known vulnerabilities, enhances security | Requires automated mechanisms, can be resource-intensive | [153] |
| IDPS | Deploying intrusion detection and prevention systems | Detects and prevents malicious activities | Can generate false positives, requires continuous monitoring | [154] |
| SIEM | Implementing security information and event management | Provides real-time analysis of security alerts | Requires integration with multiple systems, and can be complex to configure | [154] |
| Zero Trust Architecture | Assuming no device or user should be trusted by default | Prevents unauthorized access, limits potential damage | Requires a cultural shift, can be complex to implement | [155] |
| Edge Computing | Processing data closer to the source of generation | Reduces data exposure, enhances security | Requires investment in edge infrastructure, can be complex to manage | [156] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zreikat, A.I.; AlArnaout, Z.; Abadleh, A.; Elbasi, E.; Mostafa, N. The Integration of the Internet of Things (IoT) Applications into 5G Networks: A Review and Analysis. Computers 2025, 14, 250. https://doi.org/10.3390/computers14070250
Zreikat AI, AlArnaout Z, Abadleh A, Elbasi E, Mostafa N. The Integration of the Internet of Things (IoT) Applications into 5G Networks: A Review and Analysis. Computers. 2025; 14(7):250. https://doi.org/10.3390/computers14070250
Chicago/Turabian StyleZreikat, Aymen I., Zakwan AlArnaout, Ahmad Abadleh, Ersin Elbasi, and Nour Mostafa. 2025. "The Integration of the Internet of Things (IoT) Applications into 5G Networks: A Review and Analysis" Computers 14, no. 7: 250. https://doi.org/10.3390/computers14070250
APA StyleZreikat, A. I., AlArnaout, Z., Abadleh, A., Elbasi, E., & Mostafa, N. (2025). The Integration of the Internet of Things (IoT) Applications into 5G Networks: A Review and Analysis. Computers, 14(7), 250. https://doi.org/10.3390/computers14070250






