1. Introduction
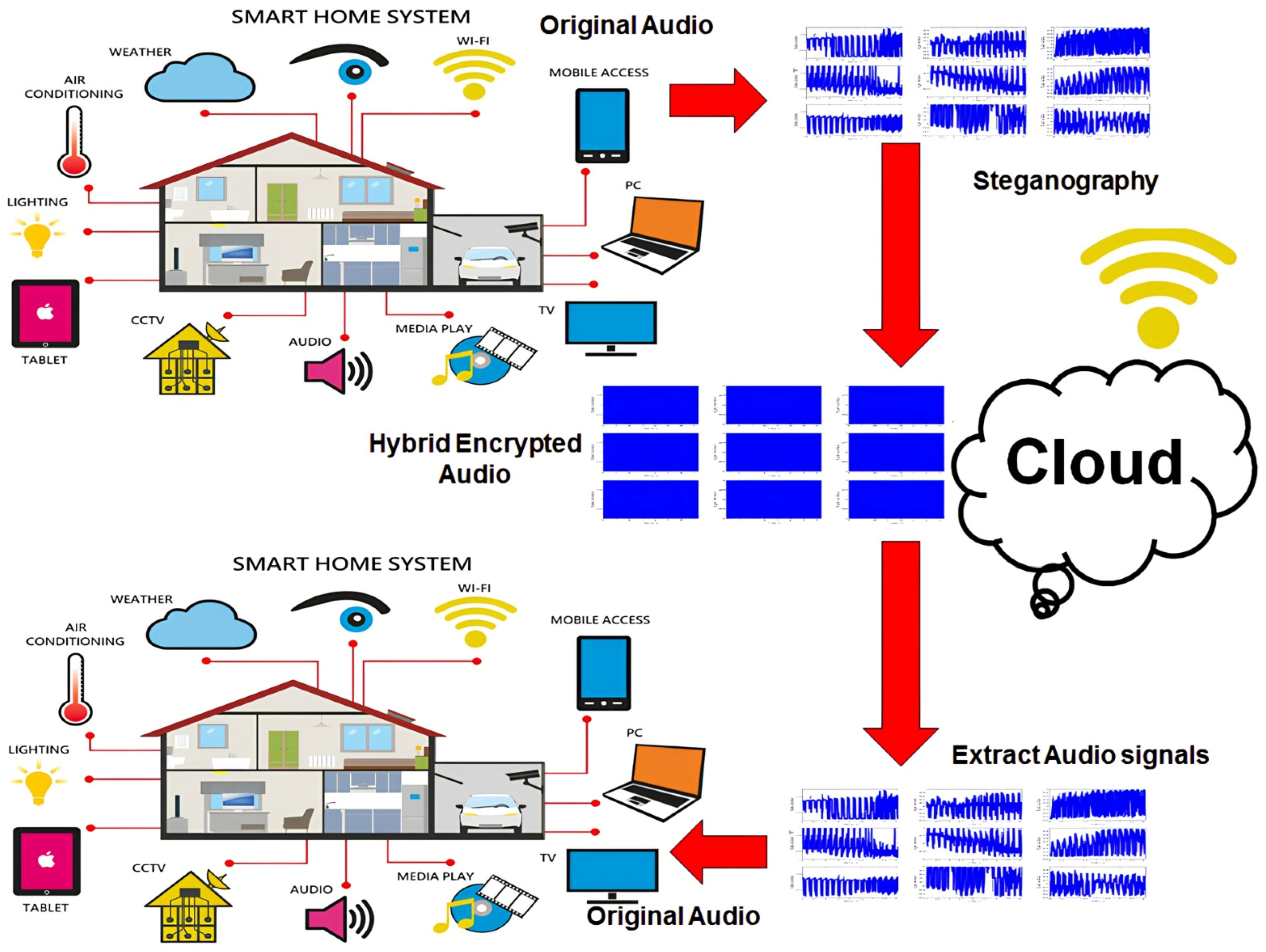
Wireless communication systems play a crucial role in the IoT by enabling seamless data exchange between interconnected devices, business and networks as shown in
Figure 1. These systems eliminate the need for physical wiring, allowing IoT devices such as sensors, smart appliances, and industrial machines to transmit data efficiently over short and long distances. Wireless communication in IoT relies on various technologies, including Wi-Fi, Bluetooth, and cellular networks like 4G and 5G. These technologies ensure IoT devices can function in different environments, from smart homes and industrial automation to healthcare monitoring and smart city infrastructure. A well-structured wireless IoT communication system consists of key components, including edge devices, gateways, cloud platforms, and secure communication protocols. IoT devices collect and transmit data wirelessly to gateways, which act as intermediaries by processing and forwarding the data to cloud servers or edge computing units for real-time analysis. Additionally, security mechanisms like encryption, authentication, and blockchain-based verification safeguard data from cyber threats. These elements collectively enhance the efficiency, scalability, and security of IoT applications, making wireless communication a key enabler of IoT-driven innovations [
1,
2].
Despite its advantages, wireless IoT communication faces challenges such as signal interference, power consumption, cybersecurity threats, and standardization issues. Many IoT devices operate in crowded frequency bands, leading to potential interference that affects performance. Additionally, battery-powered IoT devices require low-energy communication protocols to extend operational life without frequent recharging. Security concerns are also a major challenge, as IoT networks are vulnerable to cyberattacks, requiring advanced encryption and authentication techniques. Future advancements in 5G, artificial intelligence (AI)-driven network optimization, and cryptography will further enhance the reliability and security of wireless IoT communication. As IoT adoption grows, continuous improvements in wireless communication technologies will play a pivotal role in shaping smart environments, industrial automation, and connected healthcare solutions [
3,
4].
To clarify the nature of the audio data addressed in this study, the proposed system is evaluated using standard audio and environmental sound samples. These reflect practical IoT scenarios where audio plays a critical role in device interaction and system monitoring. Application examples include smart home assistants that rely on secure voice command processing, industrial IoT systems that monitor machinery sounds for predictive maintenance, and healthcare devices that detect patient distress through ambient audio. These scenarios demand lightweight, secure, and real-time communication—needs effectively addressed by the proposed chaotic-steganography framework. This context has been integrated into both the introduction and system model sections to align the technical solution with its intended real-world applications.
While protocols such as Transport Layer Security (TLS) are widely used to secure conventional internet communications, their suitability for IoT applications, particularly those involving audio transmission, is limited. TLS operates at the transport layer and introduces significant computational and memory overhead due to its handshake mechanisms, certificate-based authentication, and encryption processes. These requirements often exceed the capabilities of many IoT devices, which are typically constrained in terms of power, processing, and storage. Furthermore, TLS secures the communication channel but does not inherently protect the data payload when it is processed, stored, or relayed through intermediate nodes, such as edge gateways or cloud platforms. In contrast, our proposed approach applies security directly at the data level, encrypting and embedding the audio content itself using lightweight chaotic maps and steganography. This ensures the persistent protection of sensitive audio information, regardless of how or where it is transmitted within an IoT network. By addressing both computational feasibility and data-level confidentiality, the hybrid chaotic-steganography method offers a more adaptable and efficient security solution for advanced IoT systems.
This study focuses on how well the proposed cryp-steganography method handles channel degradation offset issues, where it accomplishes both diffusion and permutation at separate phases, respectively. A stegno-map is used later to achieve additional permutation in the steganography technique, while chaotic is utilized in a pre-processing stage to achieve the permutation of the encryption algorithm [
5,
6]. The primary contributions of this work include the development of a Hybrid Crypto-Steganography Algorithm, which integrates chaotic encryption with steganography to enhance security and data capacity while preserving audio quality. This novel approach mitigates the inherent weaknesses of each technique by leveraging their complementary strengths, significantly increasing the difficulty for intruders to intercept sensitive information in wireless communication systems. Additionally, the study evaluates various OFDM techniques, including Fast Fourier Transform (FFT), Discrete Cosine Transform (DCT), and Discrete Wavelet Transform (DWT), to determine the most suitable modulation method. The research prioritizes achieving high encryption efficiency, robust security, and superior audio fidelity in the received data. Furthermore, it examines the impact of common wireless channel impairments, such as Additive White Gaussian Noise (AWGN) and Rayleigh fading, on the system’s performance. By addressing these challenges, the proposed approach ensures a resilient and reliable communication system under realistic wireless conditions.
These contributions collectively aim to advance secure and efficient wireless communication systems by integrating innovative cryptographic techniques with optimized modulation methods. The rest of this work is arranged as follows.
Section 2 delves into various related works,
Section 3 introduces the steganography architecture,
Section 4 introduces baker chaotic map encryption,
Section 5 introduces Overview of the CBC, CFB, and OFB modes of operation, and
Section 6 introduces the overview of the hybrid crypto-steganography system. In
Section 7, encrypted audio transmission with OFDM is discussed,
Section 8 explains the quality of encryption metrics or (system evaluation metrics), and
Section 9 explains and discusses the simulation results. And finally, the paper reaches conclusions in
Section 10.
Recent research has introduced AI-based intrusion detection systems (IDS) and traffic classification methods to enhance IoT security, particularly in smart city and building applications. While these approaches are effective for detecting anomalies and suspicious behavior at the network or transport layer, they often require high computational resources, continuous training, and extensive labeled data—requirements that are not always practical for real-time, resource-constrained IoT deployments. Moreover, these methods focus on traffic behavior rather than directly securing the transmitted content itself. For sensitive audio data, such as voice commands or healthcare-related sounds, there remains a critical need for lightweight, proactive, and data-centric encryption solutions that ensure content confidentiality, even if a network is compromised. The proposed chaotic-steganography framework addresses this gap by embedding security at the data level, thereby complementing and enhancing the protection provided by AI-based systems.
2. Related Works
Several recent studies have explored AI-based threat detection and network security in IoT environments. For instance, research such as characterizing and classifying IoT traffic in smart cities and campuses and the lightweight intrusion detection for Internet of Things-based smart buildings have demonstrated the effectiveness of machine learning in identifying abnormal traffic patterns and potential intrusions. However, these solutions primarily operate at the infrastructure level, focusing on detecting threats through behavioral analysis rather than securing the data themselves. Furthermore, AI-driven models often face limitations in dynamic IoT contexts due to the need for frequent model retraining, high energy consumption, and latency in decision-making. These factors make them less suitable for IoT applications involving real-time audio transmission, where data must be both lightweight and immediately protected from interception.
In contrast, our proposed approach secures the audio payload directly by integrating chaotic encryption with steganography, offering persistent, low-overhead protection that does not rely on detecting threats post hoc. This data-level security complements existing AI-based frameworks and ensures that, even in the event of a detection failure or network compromise, sensitive audio remains protected. Our work thus fills a critical gap by providing embedded, content-specific security for IoT audio data, an area where traditional AI-based network security models fall short.
Goswami and Gupta (2022) [
7] explored the growing need for lightweight cryptographic techniques and protocols specifically designed for Internet of Things (IoT) environments. Their work emphasized the limitations of conventional cryptographic methods when applied to resource-constrained IoT devices, which often lack the processing power, memory, and energy to support standard security frameworks. The authors reviewed various lightweight encryption algorithms, including block ciphers, stream ciphers, and hash functions, and discussed their applicability across different IoT use cases. They also highlighted emerging lightweight protocols that maintain a balance between security strength and resource efficiency. This contribution provides a foundational understanding of how tailored cryptographic mechanisms can enhance security in IoT without compromising device performance, and it underscores the need for continued innovation in this domain as IoT ecosystems expand.
In [
8], the authors present a comprehensive survey on blockchain-based access control mechanisms specifically tailored for Internet of Things (IoT) environments. The study categorizes and analyzes existing approaches based on their architectural design, consensus mechanisms, and integration strategies. By leveraging blockchain’s decentralized, immutable, and transparent features, these access control models aim to enhance security, reduce reliance on centralized authorities, and improve trust in IoT ecosystems. The authors also discuss the scalability and performance of various blockchain platforms, such as Ethereum and Hyperledger, in managing access control tasks in resource-constrained IoT settings. Their work identifies open research challenges and highlights the need for lightweight blockchain solutions and intelligent access control frameworks, laying a solid foundation for future developments in secure IoT systems.
Thabit et al. [
9] explore a range of cryptographic algorithms designed to enhance security in Internet of Things (IoT) environments, with a focus on lightweight and efficient solutions suitable for resource-constrained devices. The study provides a comparative analysis of symmetric and asymmetric encryption techniques, as well as hybrid models that aim to balance security strength and computational overhead. By evaluating various cryptographic schemes in terms of their energy consumption, latency, and adaptability to IoT-specific threats, the authors offer valuable insights into the selection of appropriate encryption methods for different application contexts. Their work contributes significantly to the understanding of secure data transmission in IoT systems and highlights future directions in the development of optimized cryptographic frameworks.
Recent advancements in IoT security have led to the exploration of novel cryptographic techniques. Notably, S. Aqeel et al. [
10] proposed a DNA-based lightweight cryptography system, leveraging the complexity of DNA sequences to enhance security. Their work, published in Scientific Reports, demonstrated the potential of bio-inspired approaches in developing efficient and secure cryptographic protocols for IoT applications. This study highlights the growing interest in interdisciplinary solutions for securing IoT ecosystems.
3. Steganography Architecture
Steganography is the art and science of hiding secret information within an ordinary, non-secret file, or message to avoid detection. The block diagram of a steganography system typically consists of three main components: the cover media, the embedding algorithm, and the secret message. The cover media is a file or message that will contain hidden information. This can be an image, audio file, video, or any other type of digital media. The embedding algorithm is the process by which the secret message is hidden within the cover media. This can involve modifying the least significant bits of the cover media to encode the secret message, or using more advanced techniques such as spread spectrum or transform domain methods [
5,
11,
12,
13]. The secret message is the information that is being hidden within the cover media. This can be a text message, an audio, a video, or any other type of digital data. The embedding algorithm will ensure that the secret message is imperceptible to the human eye or ear, while still being recoverable by the intended recipient [
6].
Digital audio steganography is the practice of hiding a message within a cover audio file. This is achieved by altering the audio data in such a way that the changes are imperceptible to the human ear. The message data are embedded within the cover audio file and can only be extracted using a specific decoding algorithm. This technique is often used for covert communication and can be applied in various scenarios such as secure communication, watermarking, and copyright protection [
14,
15,
16].
Steganography is applied with chaotic code algorithms by embedding secret information within the chaotic dynamics of the algorithm. This can be achieved by manipulating the parameters of the chaotic system to encode the hidden message, making it difficult for unauthorized parties to detect or decipher the embedded information. The chaotic nature of the algorithm adds an extra layer of security to the stenographic process, making it a powerful tool for covert communication and data protection [
5,
6].
One common method of steganography is using a stego-map, which is a key or code that is used to embed and extract the hidden message from the medium. The relationship between steganography and stego-maps is crucial, as the stego-map is essential for both encoding and decoding the hidden message as shown in
Figure 2. Without the stego-map, it would be nearly impossible to retrieve the concealed information from the medium. Therefore, the stego-map plays a vital role in the practice of steganography, as it is the key to unlocking the hidden message [
17].
4. Baker Chaotic Map Encryption
An outline of each encryption algorithm’s construction will be provided in this section. The encryption techniques listed below are all symmetric block ciphers. Block indicates that the data (information) to be encrypted are separated into blocks of equal length, whereas symmetric means the key used for encryption and decryption is the same [
17,
18]. The behavior of some nonlinear dynamic systems that, under some circumstances, display dynamics that are sensitive to initial conditions is described by chaos theory. The sensitivity to beginning conditions and the mixing property are the two fundamental characteristics of chaotic systems.
In this research, the encryption process is controlled by using chaotic maps to generate the chaotic sequence [
19]. Several chaotic maps are used to create the chaos streams. Out of all the different maps, four are examined and their features are examined. To develop new symmetric block encryption techniques, this algorithm primarily relies on invertible two-dimensional Baker chaotic maps on tours or on a square. By adding parameters and then discrediting them to represent bits, a chaotic map is generalized. The ciphering map is applied iteratively to the N × N audio in order to encrypt it. The two-dimensional Baker map explains the cipher’s construction and security. The permutations caused by the Baker map are demonstrated to behave like normal random permutations [
20,
21,
22].
The Baker map, B, is described with the following equations:
In Equations (1) and (2) of the Baker map, the variables x and y represent normalized spatial coordinates within a unit square [0, 1] for both of them.
Where x is the horizontal coordinate of a point in the unit square and y is the vertical coordinate of the same point. Together, (x, y) identifies a specific point in a 2D space (or grid), which corresponds to a data element, such as a pixel in an image or a sample point in audio, depending on the application.
As shown in
Figure 3, a similarly discretized form of the fundamental map must be generated because an audio is specified on a lattice of finitely many points (bits). Specifically, a bit must be bijectively assigned to another bit using the discretized map. As the number of bits increases to infinity, the discretized map should get closer to the continuous basic map since it is intended that the discretized map inherit the properties of the basic map [
22].
5. Overview of the CBC, CFB, and OFB Modes of Operation
To regulate the relationship between the various blocks that need to be encrypted, the encryption process might employ a variety of modes of operation. This work examines the Cipher Block Chaining (CBC), CFB, and Output Feed Back (OFB) modes [
23,
24] because they all have data blocks that are dependent on one another.
where P
i is the original, unencrypted data block at position i. C
i is the encrypted version of P
i, E
k(⋅) is the block cipher encryption algorithm applied using key k. D
k(⋅) is the inverse of E
k used to recover the plaintext from the ciphertext. And
K is the shared key between sender and receiver in symmetric encryption
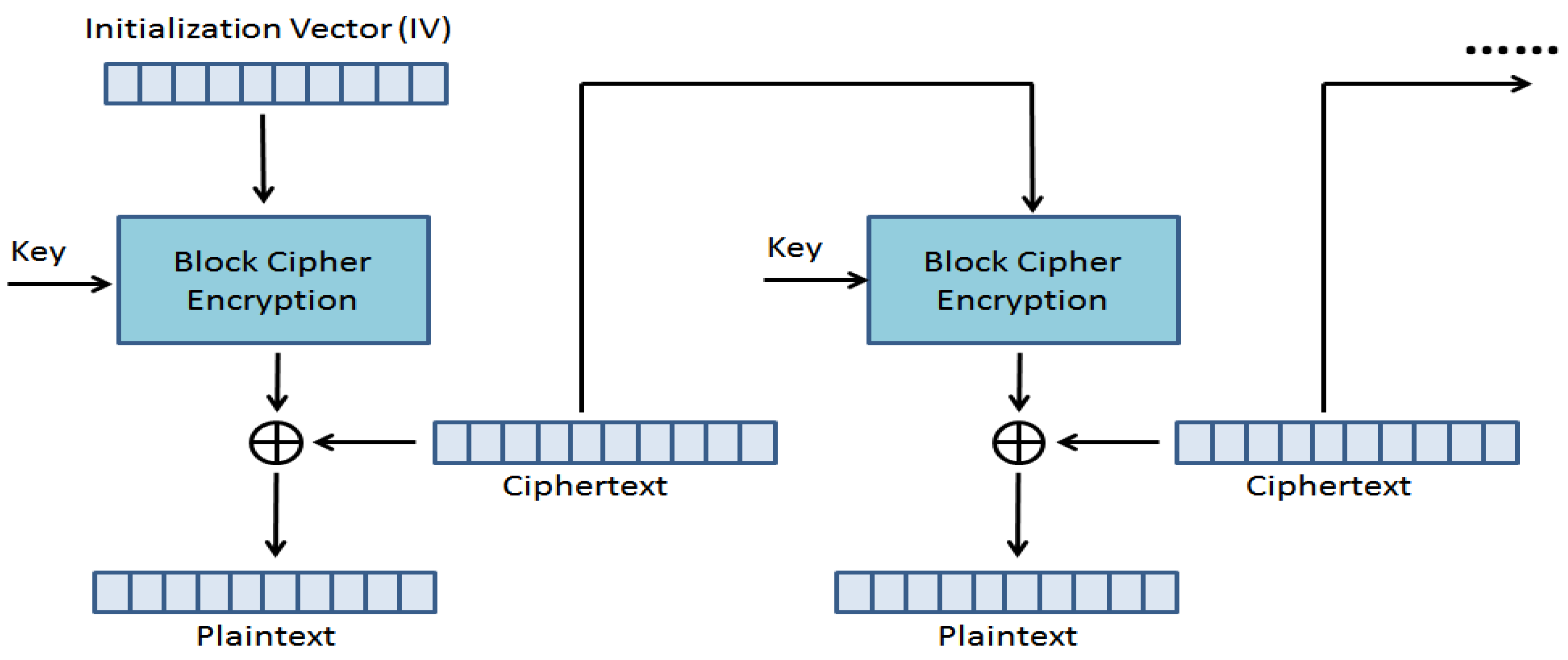
The CBC mode is a block cipher technique that encrypts each block or individual unit of input data using a cipher key. A cipher block chaining uses an Initial Vector (IV) of a specific key length. A chaining key technique that relies on every previous cipher-text block is used to decrypt a block cipher of the ciphertext [
24,
25,
26,
27]. In
Figure 4, the CBC process is displayed.
For CBC encryption, IV is the random or pseudorandom value used to initiate the encryption process, ensuring variability and the bitwise XOR operation (⊕) used to combine two binary sequences, commonly used in block cipher modes to mix plaintext and ciphertext.
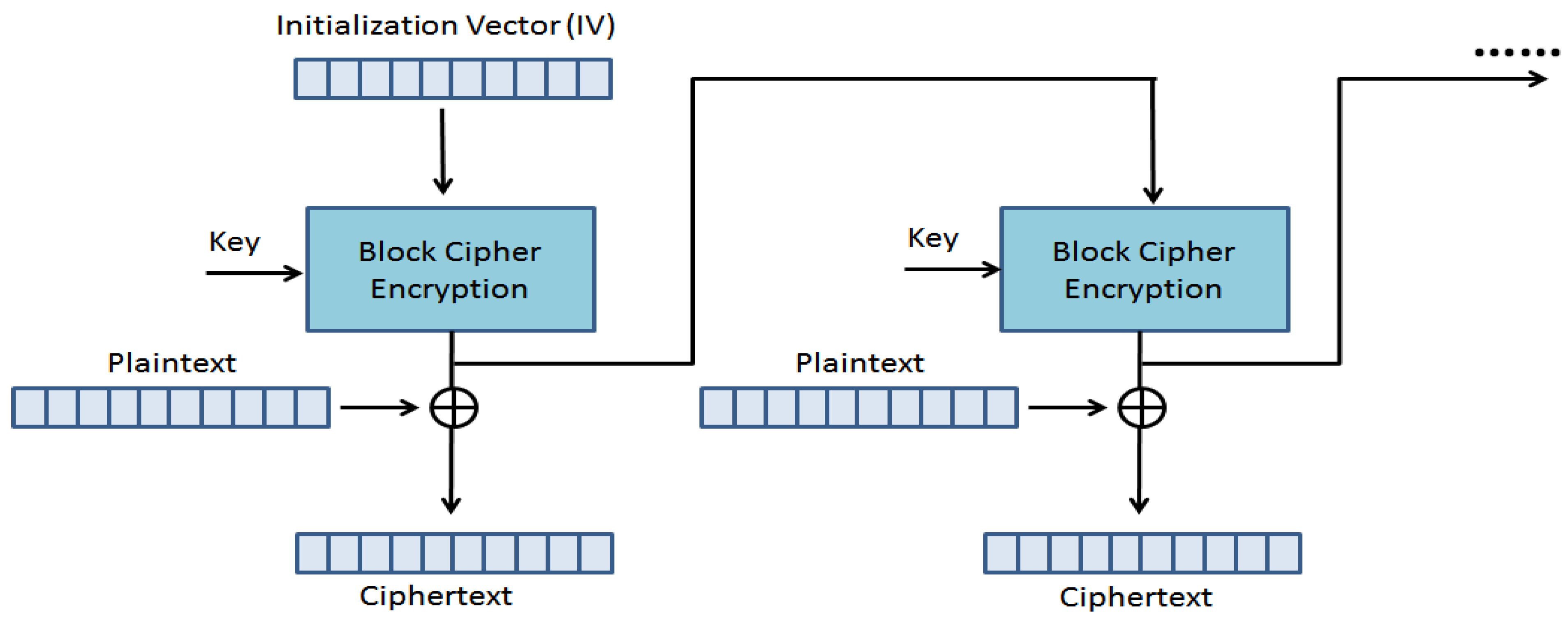
The CFB is implemented as shown in
Figure 5 [
27],
where, C
j is the ciphertext block at position j, P
j is the plaintext block at position j, I
j = E
k(C
j − 1) is the encrypted output of the previous ciphertext block, C
0 = IV is the initialization vector used to start the process, E
k(⋅) denotes the encryption function with secret key k, and ⊕ represents the bitwise XOR operation. This configuration ensures that each ciphertext block depends on all previous plaintext blocks, providing strong diffusion and enhancing security.
The OFB mode is illustrated in
Figure 6. In the OFB mode, the encryption concept is described by Equation (9) and the decryption concept is described as [
27],
6. Overview of the Hybrid Crypto-Steganography System
Crypto-steganography is a method of hiding encrypted messages within non-secret text or data. It involves embedding a secret message within an innocent-looking cover message in such a way that it is difficult for an outsider to detect the presence of the hidden message. The steps involved in crypto-steganography include selecting a cover message, encrypting the secret message, embedding the encrypted message within the cover message, and then transmitting the combined message to the intended recipient. The recipient can then extract the hidden message using the appropriate decryption key. The benefits of crypto-steganography include the ability to securely transmit sensitive information without drawing attention to the fact that a secret message is being sent [
28]. This can be particularly useful in situations where privacy and confidentiality are paramount, such as in military communications, intelligence operations, or corporate espionage. Additionally, crypto-steganography can be used to protect digital assets and communications from unauthorized access or interception [
29].
The audio signals in the hybrid crypto-steganography system are first encrypted using the hybrid encryption framework, which may be chaotic. Later, they are concealed in the steganography stage by using the chaotic map method once more on the multi-audio map, as shown in
Figure 7. The following is a summary of the overall procedures:
Use a chaotic technique to encrypt the audio signals (Cryptography stage).
To create an additional degree of encryption, various audio signals are encrypted and then mapped into a single audio sample.
Use a chaotic map mechanism to randomly generate the new encrypted audio map (Steganography stage).
Figure 7.
Overview of the Crypto-steganography system.
Figure 7.
Overview of the Crypto-steganography system.
Using the inverse first steganography stage, which can be thought of as a chaotic decryption process, the receiver side applies the inverse of crypto-steganography to extract the original audio signals. The inverse of the cryptography stage will also be a chaotic decryption process.
7. Encrypted Audio Transmission over IoT System
The integration of OFDM in IoT applications has transformed wireless communication by significantly enhancing spectral efficiency, data transmission rates, and overall reliability. As a widely adopted multicarrier modulation technique, OFDM divides the available spectrum into multiple orthogonal subcarriers, enabling simultaneous data transmission while minimizing interference. This capability is particularly advantageous for IoT networks, where devices demand low-latency and high-throughput communication. By leveraging OFDM, wireless connectivity becomes more efficient, facilitating seamless data exchange among numerous smart devices in applications such as home automation, smart industries, and remote healthcare monitoring [
28].
To evaluate the practical effectiveness of the proposed secure audio communication system, we integrate the hybrid chaotic-steganography encryption scheme with an Orthogonal Frequency Division Multiplexing (OFDM)-based transmission system. OFDM is a well-established multi-carrier modulation technique used in many modern wireless standards due to its ability to manage channel interference, multipath fading, and spectral efficiency.
In this work, OFDM serves as a testbed for assessing how well the encrypted audio data withstands real-world wireless communication impairments. The encrypted audio signals, generated by the proposed chaotic-steganography framework, are modulated using OFDM and transmitted through simulated wireless channels including Additive White Gaussian Noise (AWGN) and Rayleigh fading conditions.
Key performance indicators such as Peak Signal-to-Noise Ratio (PSNR), bit-level deviation, and correlation are used to measure how well the encrypted data are preserved and recovered after transmission. This approach allows us to demonstrate not only the theoretical security of the proposed encryption technique but also its resilience and robustness in practical IoT transmission scenarios.
Thus, OFDM is not a focal point of innovation in this work but rather a realistic wireless environment used to validate the performance of the proposed secure communication solution.
A key advantage of OFDM in IoT environments is its resilience to multipath fading, a common challenge in wireless communication. IoT devices, often deployed in complex settings such as urban landscapes and industrial facilities, face signal degradation due to reflections and physical obstructions. OFDM effectively mitigates these issues by incorporating cyclic prefixes and subcarrier diversity, ensuring stable and reliable data transmission. Additionally, OFDM supports adaptive modulation and coding schemes, allowing IoT devices to dynamically adjust transmission parameters based on real-time network conditions. This adaptability enhances network performance, improving resistance to interference and congestion, thereby making IoT communications more robust and efficient [
22,
28,
29,
30].
Figure 8 shows the System Model for OFDM [
22]. In the context of encrypted audio, OFDM can be used to transmit audio data securely over a wireless channel. By encrypting the audio data before they are modulated and transmitted using OFDM, the confidentiality and integrity of the audio can be maintained. This is particularly important in applications such as secure communication systems, where sensitive information needs to be transmitted over a wireless channel. By combining OFDM with encryption techniques such as chaotic encryption algorithm, the audio data can be securely transmitted and received, ensuring that only authorized parties can access and decode the audio.
The block diagram of an IoT based OFDM system comprises several essential components that facilitate the transmission and reception of data. The process begins with the Data Source, where the original data, such as audio or video, are generated. These data are then passed through an Encoder, which applies error correction coding to ensure reliable transmission. Next, the encoded data are fed into a Modulator, where they are divided into multiple parallel streams and modulated onto separate subcarriers using the OFDM technique. The modulated subcarriers are combined using an Inverse Fast Fourier Transform (IFFT) to generate the OFDM signal, which is then prepared for transmission by the RF Front End, including components like amplifiers, filters, and mixers. The OFDM signal is transmitted through a Channel, which may introduce noise and impairments, and is received by the Receiver. At the receiver, the signal is processed by the RF front end and demodulated using FFT to recover the subcarriers. The demodulated data are then passed through a Decoder to correct any transmission errors and reconstruct the original data. Finally, the recovered data are sent to the Data Sink for further processing or playback. This block diagram outlines the sequential flow of data in an OFDM system, highlighting its key stages from data generation to transmission, reception, and recovery [
22,
30,
31,
32].
8. Proposed System Evaluation
One of the important parameters in examining the encrypted audio is the tonal distribution inspection where the highly disappeared features of the audio, the better the encryption algorithm. But the tonal distribution inspection dependence only is not enough to judge the complete hiding of the content of the audio signal. So, other calculating and measuring metrics are considered to evaluate the degree of encryption quantitatively [
33,
34,
35,
36]. Bit values vary in comparison to their pre-encryption values when an encryption scheme is implemented. This implies that the quality of crypto-steganography (PSNR) and, consequently, the effectiveness of audio encryption, will increase with the change in bit values. Thus, a number of phrases can be used to describe the quality of encryption:
Spectrogram and Histogram
The deviation (variations) in bit values between the encrypted and original audio.
The correlation coefficient.
Noise immunity.
8.1. The Spectrogram and Histogram Analysis
It provides a time-frequency representation, allowing a detailed inspection of how signal frequencies vary across the duration of the audio. This method is particularly useful for evaluating the effectiveness of audio encryption algorithms. By comparing the spectrograms of original and encrypted audio files, one can observe how much the frequency content has been altered.
Each bar graph in a histogram shows the frequency of each intensity level in an audio signal, with the vertical axis representing the occurrence density and the horizontal axis representing the intensity-level values. From zero to the number of intensity levels, the horizontal one begins. The frequency with which the intensity level appears in the given audio stream is shown by each bar on the vertical axis [
33,
34,
35,
36]. Two characteristics of the histogram for the encrypted audio signal are necessary for audio encryption or the crypto-steganography algorithm:
Total difference from the histogram of the original audio signal.
Uniform distribution, which means equal probability for all intensity levels.
The effectiveness of the proposed crypto-steganography algorithm is evaluated in
Figure 9 using a comparative analysis that includes both spectrogram and histogram visualization techniques. A simulation study was conducted on two distinct datasets, each consisting of nine audio samples, as illustrated in
Figure 9. For each audio signal, steganographic and chaotic map keys were utilized as IVs. The spectrogram analysis provides a time-frequency representation of the audio signals, allowing for detailed observation of how encryption alters their spectral content. In the spectrogram of the original audio, clear and continuous frequency components are visible, reflecting the structured nature of unencrypted audio. In contrast, the spectrograms of encrypted signals, particularly those processed using the hybrid crypto-steganography method, exhibit significant spectral distortion or complete destruction of frequency information. This indicates that the proposed algorithm effectively disrupts the original signal’s spectral features, thereby enhancing security and making unauthorized interpretation virtually impossible. Complementing the spectrogram analysis, the histogram evaluation illustrates the distribution of intensity levels in the audio signals. The original audio histograms display distinct, non-uniform patterns indicative of natural audio structure. However, the encrypted audio histograms, especially those produced by the proposed hybrid method, show near-uniform distributions. This flattening effect demonstrates the algorithm’s ability to eliminate detectable patterns and increase randomness. Together, the spectrogram and histogram results confirm the robustness of the proposed crypto-steganography framework in concealing both the time-frequency and amplitude characteristics of the audio, ensuring high-quality encryption and secure transmission.
Figure 9 presents the spectrograms and histograms of audio signals processed using both chaotic encryption algorithms and the proposed hybrid crypto-steganography approach. The spectrogram analysis provides a detailed view of the frequency content of the audio signals over time, allowing for evaluation of how the encryption alters their spectral structure. In the original audio, the spectrogram reveals clear, continuous, and structured frequency patterns, characteristic of an intelligible signal. However, after applying the hybrid crypto-steganography algorithm, the spectrograms display significant distortion and a complete breakdown of these patterns, indicating that the original frequency components have been effectively concealed. This spectral disruption highlights the algorithm’s strength in obscuring the audio content. Complementing the spectrogram analysis, the histogram evaluation illustrates the distribution of amplitude or intensity levels within the audio signals. The original audio exhibits distinct, non-uniform histogram patterns that reflect the natural structure of the signal. In contrast, the histograms of the encrypted audio, particularly when processed using the hybrid crypto-steganography method, appear nearly uniform across all tested scenarios. This flattening of the histogram reflects increased randomness and reduced predictability—key attributes of a robust encryption scheme. Together, the spectrogram and histogram analyses confirm the effectiveness of the proposed framework, demonstrating that the integration of steganography with chaotic encryption significantly enhances the security and imperceptibility of audio data, making it highly suitable for secure transmission in sensitive applications.
8.2. The Deviation Measuring Factor
By maximizing the difference between each value in the original audio signal and its corresponding value in the encrypted audio, the deviation value assesses the strength of the encryption or the cryp-to-steganography process [
32,
33,
34,
35,
36]. The following is a description of the deviation measurement:
- (1)
Histogram estimation of both original and encrypted audios.
- (2)
Estimation of the absolute difference between both histograms.
- (3)
Estimation of the area under the difference curve as follows:
where
is the difference curve’s amplitude expressed as an absolute value at
i.
Table 1 displays the deviation results for the various chaotic modes with and without steganography [
32,
33,
34,
35,
36]. To put it simply,
D rises as the encrypted audio deviates more from the original audio.
Table 1 presents the deviation values for three encryption modes—CBC, CFB, and OFB—applied alone and in combination with steganography, tested on two audio files. Across all methods, the deviation slightly increases when steganography is added, with marginally higher values when using different audio files for embedding. Among the encryption modes, CFB combined with steganography (with similar audios) yields the highest deviation, suggesting a slightly greater distortion, while CBC shows the lowest deviation overall.
8.3. Correlation Coefficient Measuring Factor
The stronger the encryption system, the lower the value of the Correlation Coefficient
C.C in the encryption process or in the crypto-steganography technique.
where (
) and
x and
y are the intensity values of the original and encrypted audios. Measuring the
C.C is done through running the
C.C built in function using MATLAB 2014software (Corr2).
Table 2 shows the deviation result after simulation of the different chaotic modes with and without steganography [
27].
Table 2 shows the correlation values for three encryption algorithms (CBC, CFB, and OFB) applied with and without steganography across two audio files. Across all cases, correlation values remain close to zero, indicating minimal statistical dependence between the original and encrypted audio, which is desirable for secure encryption. The addition of steganography introduces slight variations, but no significant correlation is observed. Notably, CFB with steganography (similar audios) yields a small positive correlation for Audio 1, while all other cases exhibit weak negative or near-zero correlations, confirming that encryption and steganography effectively obscure the audio data.
8.4. The Processing Time
According to
Table 3 Results, the chaotic with steganography approach requires less processing time. The steganography itself has a very brief actual time. Parallel processing can greatly cut down on this turbulent time.
8.5. Noise Immunity
This test is used to examine the Noise immunity of the algorithm by following the following steps:
- (1)
Encrypt the plaintext audio.
- (2)
Add the noise to the encrypted audio by increasing Bit Error Rate (BER), in our test; we have used the BER with various values as the following.
- (3)
Sending encrypted audio over OFDM channel.
- (4)
Calculating PSNR of each chaotic mode and comparing the results with the previous ones.
Figure 10 illustrates how sensitive chaotic encryption with various modes of operation is to the BER. Compared to the other modes, the chaotic-OFB mode is more resilient to noise, while at large value of BER OFB Mode + steganography is the best.
9. Simulation Results
9.1. Simulation Parameters
To evaluate the effectiveness of the proposed secured audio transmission framework, a simulation model was developed that integrates chaotic encryption, steganography, and OFDM-based wireless transmission. The goal is to mimic real-world conditions in IoT environments, particularly under channel impairments such as fading and noise. The system processes audio signals through several stages: encryption using chaotic modes (e.g., CBC), steganographic embedding, modulation via OFDM using various transforms (FFT, DCT, DWT), and transmission over a Rayleigh fading channel. The receiver performs demodulation and decryption to recover the original audio signal, allowing for a quantitative performance assessment using PSNR.
We use the aforementioned modes for audio encryption in our simulations. After encryption, the audio samples are converted to binary and utilized for OFDM modulation. The simulations take Rayleigh fading channels into account. QPSK and 128 subcarriers are employed in all trials.
Table 4 provides a summary of the simulation parameters.
We employ the
PSNR between the original and decrypted audios, which is defined as follows, to assess the quality of the decrypted audios at the receive
where the Mean Square Error (
MSE) is defined as:
where
is the original audio of dimensions
U and
is the decrypted audio.
9.2. Chaotic with Steganography Algorithm Based on Similar Audios
The simulation results demonstrate that integrating steganography with chaotic encryption techniques significantly enhances the security and performance of multiplexed audio transmission in OFDM-based IoT systems.
Table 5 presents the average PSNR performance for encrypted multiplexed audio streams using hybrid chaotic encryption techniques, both with and without steganography, transmitted over FFT, DCT, and DWT-based OFDM systems under AWGN and fading channels. The analysis covers two levels of Eb/No: 6 dB and 10 dB. The results indicate that higher Eb/No values, particularly at 10 dB, significantly enhance PSNR, often resulting in infinite (Inf) values, which suggest nearly lossless audio transmission. Among the encryption modes, OFB consistently delivers superior performance compared to CBC and CFB, especially in fading environments and when used in conjunction with steganography. Although the inclusion of steganography slightly reduces PSNR at lower Eb/No levels, it maintains high audio quality at 10 dB, demonstrating good noise resilience. Furthermore, DWT-OFDM outperforms FFT and DCT variants in most cases, especially when paired with OFB encryption and steganography, making it the most robust configuration for secure and reliable audio transmission.
9.3. Chaotic with Steganography Algorithm Based on Different Audios
The simulation results demonstrate the effectiveness of the proposed Chaotic-Steganography Algorithm for securing audio transmission in IoT systems across various OFDM configurations (FFT, DCT, and DWT). The PSNR values reveal that integrating steganography with chaotic encryption significantly enhances the transmission quality, particularly under Rayleigh fading conditions.
Table 6 presents the average PSNR values for the transmission of nine different encrypted audio streams using the proposed hybrid encryption techniques, with and without steganography, over FFT, DCT, and DWT-based OFDM systems. The results are evaluated under both AWGN and fading channels for two Eb/No levels: 6 dB and 10 dB. As seen in the table, higher Eb/No values (10 dB) consistently yield significantly improved PSNR performance, often reaching infinite values, which indicates near-perfect reconstruction of the audio at the receiver. Among the encryption methods, OFB combined with any OFDM variant—particularly under AWGN—demonstrates the highest PSNR, highlighting its strong resilience to channel noise. The addition of the steganography technique shows a minimal impact on performance at high Eb/No but can slightly reduce PSNR at lower noise conditions. In fading channels, all encryption modes show reduced PSNR compared to AWGN, however, OFB encryption still maintains a clear advantage in signal integrity. Overall, these results confirm that the hybrid approach is robust for transmitting varied audio signals, especially when using OFB mode with DWT-OFDM in low-noise environments.
10. Conclusions
This paper presented a hybrid secure audio transmission system designed specifically for resource-constrained IoT environments. By integrating chaotic encryption with steganography, the system provides dual-layered protection, ensuring both cryptographic security and covert data embedding. This synergy enhances confidentiality, increases resistance to interception, and improves overall communication security. Secured audio transmission framework for IoT systems was proposed, combining chaotic encryption techniques with audio steganography to enhance confidentiality and robustness. The hybrid approach ensures that audio signals are both encrypted for security and embedded with hidden data for an additional layer of protection, making it highly suitable for environments where data integrity and privacy are critical.
To evaluate real-world applicability, the encrypted audio was transmitted over an OFDM-based wireless channel, a standard in modern communication systems. Through extensive testing across various encryption modes and transmission scenarios, the framework demonstrated strong resistance to noise, effective concealment of data, and high audio quality even in challenging channel conditions. The integration of steganography with chaotic systems proved to be an efficient method for concealing information without significantly compromising performance or increasing computational load beyond practical limits. Overall, the proposed framework offers a secure, efficient, and scalable solution for audio communication in IoT applications, ensuring the safe transmission of sensitive audio data over potentially insecure wireless networks. This work lays the groundwork for further development of lightweight, real-time security mechanisms tailored for resource-constrained IoT environments.