1. Introduction
The continuous growth of the automobile industry, coupled with rapid urbanization, has resulted in a substantial increase in the number of vehicles. Consequently, modern transportation systems are facing different challenges, including a rise in traffic accidents, severe traffic congestion, increased energy consumption, and heightened levels of pollution [
1]. Early applications developed to address these challenges relied on local sensors, such as radar and cameras, to enable vehicle autonomy. While these technologies allowed vehicles to detect and respond to their immediate environment and support real-time decision-making, they offer only a limited level of safety because of the constrained sensing ranges and the complexities of data processing [
2,
3].
To overcome these limitations, additional sources of data were essential to expand surrounding perception across a wider area. Vehicle-to-vehicle (V2V) communication has been introduced as a solution to address these limitations. By enabling vehicles to share critical information on acceleration, speed, position, and trajectory, V2V communication offers a more comprehensive understanding of the surrounding environment [
4]. Therefore, the integration of automated vehicles (AVs) and connected vehicles (CVs) as connected and autonomous vehicles (CAVs) has the potential to address all above-mentioned challenges, resulting in improvements in safety and efficiency and reducing traffic congestion [
5,
6,
7].
Cooperative adaptive cruise control (CACC) as a key feature of CAVs, has enhanced the capabilities of adaptive cruise control (ACC) to improve safety, traffic flow, and energy efficiency through cooperative maneuvers [
8,
9]. In CACC systems, vehicles exchange information with one another within the network via V2V communications, which results in several key benefits including improved reaction times in vehicles, enhanced safety, increased traffic flow efficiency, fuel efficiency and reduced emissions, and string stability in vehicles’ platoons [
9,
10,
11,
12].
Although CAVs and CACC offer numerous benefits, their heavy reliance on V2V communications makes vehicles susceptible to cyber-attacks such as false data injection (FDI) attacks. These threats can compromise the reliability of observations used in decision-making process [
13,
14,
15]. Therefore, it is necessary to develop a secure CACC algorithm to address and mitigate these attacks effectively.
The design of CACC has been widely studied in various studies; each of them has addressed different objectives and operated under different assumptions and conditions. In [
16], the research utilized deep reinforcement learning (DRL) to improve the performance of CACC, comparing its effectiveness to traditional model-based approaches. The research aimed to minimize both distance error and energy consumption while ensuring safety. A model predictive control (MPC) approach for CACC was designed in [
17]. In this study, by predicting traffic and integrating fuel-efficient control, the system minimized fuel usage and prevented collisions. In [
18], a dynamic event-triggered communication mechanism (DECM) approach was introduced for CACC systems. This method was used to conserve constrained V2V communication resources. By implementing DECM, the frequency of measured velocity and acceleration data required for transmission to following vehicles is minimized. In [
19], the researchers concentrated on a different aspect of CACC, specifically string stability. The main objective of this study was to tackle the challenge of maintaining string stability as inter-vehicle time gaps decrease. However, none of the mentioned studies addressed the impact of FDI attacks on the communication channel of the CACC system.
The development of CACC under FDI attacks has been considered in a limited number of studies. A recent study analyzed the effects of FDI attacks on CACC [
20]. This research examined FDI attacks within the CACC communication channel, including ghost vehicle injections aimed at disrupting system performance. To detect and locate these attacks, the authors developed a partial differential equation (PDE)-based model as the dynamic model for vehicles and designed a PDE observer. By leveraging Lyapunov stability theory, they validated the observer’s convergence, ensuring robust detection of attacks even in the presence of noise. The effects of FDI attacks were also considered in [
21]. This research employed a hybrid approach, combining both model-based and learning-based methods to estimate FDI attacks. Additionally, it introduced a Lyapunov-based controller designed to reduce the adverse effects of FDI attacks, measurement noise, and external disturbances in CACC, ensuring the maintenance of a safe distance between vehicles. Further research on CACC under FDI attacks was presented in [
22]. This study addressed the effects of FDI attacks, input time-varying delays, external disturbances, and measurement noise by developing a nonlinear controller, observer, and NN-based attack estimators. However, all of the mentioned papers assumed that the dynamic model of the lead vehicle is known, while accessing the dynamic model of the lead vehicle presents a significant challenge, which is a key focus of this paper.
The contributions of our paper are as follows: (i) A novel observer-based control for CACC was developed that is resilient against injected FDI attacks into both transmitted velocity and control signals. (ii) The proposed approach operates effectively without relying on the dynamic model of the lead vehicle. (iii) The proposed nonlinear observer was designed to estimate FDI attacks in real time. (iv) Additionally, we provided a comprehensive Lyapunov stability analysis for both the proposed nonlinear controller and the observer. (v) Finally, we validated the developed method through simulations to demonstrate its effectiveness.
The structure of the paper is organized as follows:
Section 2 presents a dynamic model of the lead and following vehicles. The problem statement is detailed in
Section 3.
Section 4 presents an overview of the proposed solution, including observer design, control design, and estimation of FDI attacks. The stability analysis of the proposed observer and controller is discussed in
Section 5.
Section 6 demonstrates the results, and the paper concludes with a summary in
Section 7.
2. Models of Dynamics
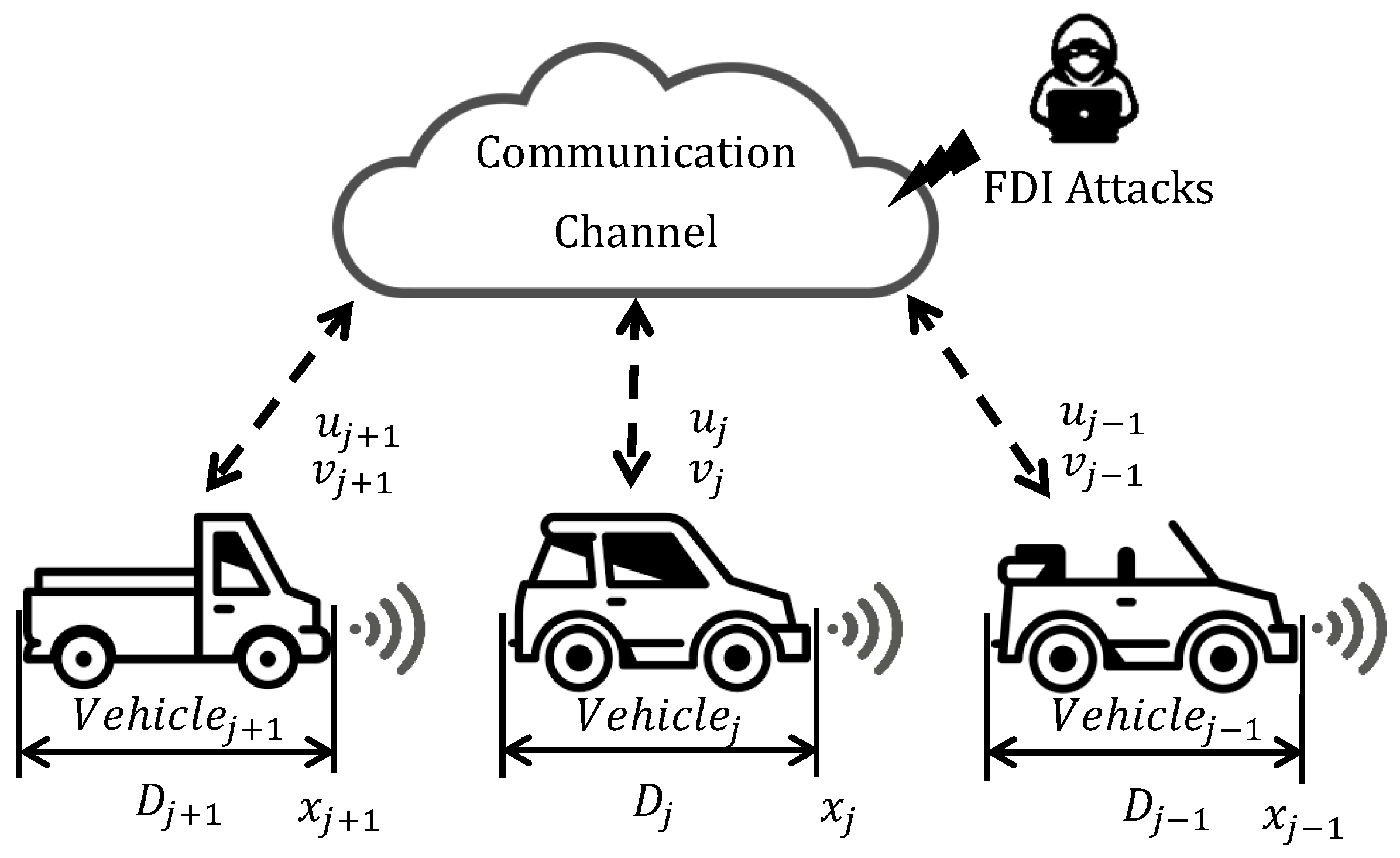
Figure 1 illustrates a string of vehicles, each equipped with the CACC feature. In this configuration, each vehicle follows its respective leader. Here, we assumed
n vehicles in the platoon, where
denotes a following vehicle, while
denotes its respective leader. Each follower vehicle
j receives data from its leader
including the leader’s control and velocity signals. However, during the transmission process via the wireless communication channel, an adversary may gain access and inject falsified data into the control and velocity signals. As a result, the following vehicle receives corrupted data. Additionally, each following vehicle uses a radar sensor to measure the position of its leader. The vehicles in this string are heterogeneous, meaning they are different models and not uniform in design. The dynamic model of followers is described as
where the position, velocity, and control signals of the follower are indicated as
,
, and
, respectively. In addition,
and
are known constants, representing dynamic models of the following vehicle, which are calculated using experimental analysis [
21]. In this paper, we considered that the lead vehicle follows a second-order dynamic model such as
where the position, velocity, and control signals of the leader are indicated as
,
, and
, respectively. The parameters
and
are unknown.
FDI Attacks in Communication Channel
Each vehicle receives the velocity and control signals of its leader through a wireless communication channel while the transmitted data are experiencing FDI attacks. To show the effect of FDI attacks on the control and velocity signals of the leader, we define the below signals:
where
and
are altered control and velocity signals of the leader which are received by follower, and
is the unknown, bounded, time-varying, and continuous FDI attacks.
Assumption 1. An FDI attack is assumed to be bounded and differentiable such that , where and is a positive known constant [22]. Considering (
3), the following vehicle receives altered signals. To estimate the control and velocity signals of the lead vehicle, we define the below signals:
where
,
, and
are an estimation of the leader’s control signal, an the estimation of leader’s velocity signal, and an estimation of the FDI attacks, respectively.
3. Problem Statement and Error Signals
The primary focus of this work is to develop a secure controller for CACC to mitigate the effects of FDI attacks, therefore ensuring a safe inter-vehicle distance. The CACC algorithm relies on real-time control and velocity signals from the lead vehicle. However, adversarial manipulations pose a significant challenge to this process, potentially leading to collisions. In addition, the lead vehicle’s model is unknown, which introduces further complexity in secure controller design. Therefore, a secondary purpose of this study is to develop an observer capable of estimating FDI attacks and the unknown parameters of the lead vehicle in real time. To quantify these objectives, we defined error signals as distance error, velocity error, and acceleration error.
The distance error signal
is defined as
where
is the length of lead vehicle which is constant, and
is the desired inter-vehicle distance.
Assumption 2. The desired distance, as well as its first and second derivatives, is assumed to remain within the limits of predefined positive constants, [23]. The velocity error signal
is introduced as
using (
1) and (
2), (
6) changes to
In addition, the acceleration error signal
is introduced as
using (
1) and (
2), (
8) changes to
we can write (
9) as
where
is the combination of all unknown terms in (
9) and is defined as
where the control and velocity signals of leader are unknown under FDI attacks. In addition, since the dynamic model of the lead vehicle is unknown,
and
are unknown.
To streamline the design process and stability analysis of the second-order system, an auxiliary error equation is introduced to derive the control signal as
where
is a known gain specified by the user,
shows the estimation of
, and
is the estimation of
.
To obtain the velocity and acceleration errors and address the unknown terms, we introduced newly defined state variables as
The defined state variables are estimated using an observer. To quantify the observer accuracy, we need to define estimations errors
,
, and
as
where
,
, and
are the estimation of
,
, and
, respectively.
Here, we use (
13) and (
14) to update (
12) as
6. Results
This section provides a comprehensive analysis of the results obtained from testing the proposed secure nonlinear controller and nonlinear observer through MATLAB Simulink R2024b (MathWorks, Natick, MA, USA) and an experimental setup. The evaluation focuses on key performance metrics, including inter-vehicular distance, the velocities of both the leader and follower vehicles, and the estimation of FDI attacks. To quantify performance, we also present the Root Mean Square Error (RMSE) for both distance and FDI attack estimation. To demonstrate the robustness of the proposed method, we analyze seven distinct scenarios. The first three scenarios examine different types of FDI attacks, highlighting the controller’s ability to estimate and mitigate them. The remaining scenarios include a comparative analysis with an alternative method, a platoon scenario, the impact of different FDI attacks on control and velocity signals, and, finally, the experimental validation through real-world testing. In scenarios, we selected
m, which is the desired inter-vehicle distance for simplicity. The model parameters of the follower vehicle were obtained from the experimental setup in [
21] as
and
. In addition, disturbance and noise are added to the system to show robustness of our developed CACC. In the first three scenarios, the term secure controller refers to our proposed nonlinear controller, while the baseline controller refers to the controller described in [
6]. The baseline controller lacks compensation for FDI attacks and does not address the unknown dynamic model of the lead vehicle.
6.1. One-Step Function FDI Attack
In
Figure 3, the first subplot illustrates the FDI attack, modeled as a step function with a step time of 50 s. The step function begins with an initial value of 0 and increases to a final value of 0.6. Additionally, the subplot includes the corresponding estimation of the attack. As derived from (
27), the estimation is obtained from the difference between the estimated velocity of the leader and the faulty leader’s velocity. Minor estimation errors occur during periods when the leader changes its velocity.
The second subplot shows the velocity profiles of both the lead and following vehicles. It is evident that under the proposed secure controller, the follower vehicle closely tracks the leader’s velocity. However, under the baseline controller, the follower fails to follow the leader’s velocity during the period of FDI attack injection. This causes the follower’s velocity to exceed that of the lead vehicle, leading to a dangerously reduced inter-vehicle distance and increasing the likelihood of a collision.
The third subplot demonstrates the distance between the vehicles. Under the secure controller, the adverse effects of the FDI attack are mitigated, maintaining a safe distance between the vehicles. Although small deviations occur, the inter-vehicle distance remains close to the desired 5 m, preventing any issues. In contrast, with the baseline controller, which lacks attack compensation, the follower receives corrupted data during the FDI attacks. This results in an increase in velocity and a dangerously close distance to the leader vehicle, with the distance dropping to 2 m at s significantly increasing the risk of a collision.
6.2. Two-Step Function FDI Attack
The second scenario for the FDI attacks involves two step functions: the first is initiated at 30 s, increasing to 0.3, followed by a second increase to 0.6 at 60 s. The results, including the estimation of the FDI attacks, the velocity profiles of both the lead and following vehicles, and the inter-vehicle distance, are presented in
Figure 4.
As with the previous scenario, the first subplot shows the estimation of the FDI attack, while the second subplot illustrates the follower vehicle’s ability to track the leader’s velocity. Under the secure controller, the follower closely tracks the leader’s velocity. In contrast, under the baseline controller, the follower fails to maintain accurate tracking during the FDI attack. The final subplot highlights how the baseline controller is unable to mitigate the effects of the attack, resulting in a dangerously reduced distance between the vehicles and a heightened risk of collision. However, the secure controller successfully maintains a safe distance between the vehicles, even under FDI attack injection.
6.3. Step and Sinusoidal FDI Attack
To further validate and demonstrate the effectiveness of the proposed method, we introduce an additional scenario involving sinusoidal FDI attacks. This attack is modeled using a step function with a step time of 30 s, an initial value of 0, and a final value of 0.4, combined with a sinusoidal function applied at 50 s, represented as:
. As demonstrated in
Figure 5, similar to the previous scenarios, the observer accurately estimates the FDI attack, while the proposed secure controller effectively mitigates the adverse effects of FDI attacks, disturbances, and noise. This allows the follower vehicle to track the leader’s velocity and maintain a safe inter-vehicle distance.
To quantify the performance,
Table 1 presents RMSE values to illustrate the efficacy of the developed secure controller. As illustrated in the table, the RMSE between the desired and actual distances under the secure controller is minimal. In contrast, the baseline controller fails to maintain the desired distance, resulting in significantly higher RMSE values across all FDI attack scenarios when compared to the secure controller.
Additionally,
Table 2 demonstrates the performance of the proposed observer and estimation approach in estimating FDI attacks. The low RMSE values across all FDI attack scenarios indicate the method’s effectiveness in accurately estimating these attacks.
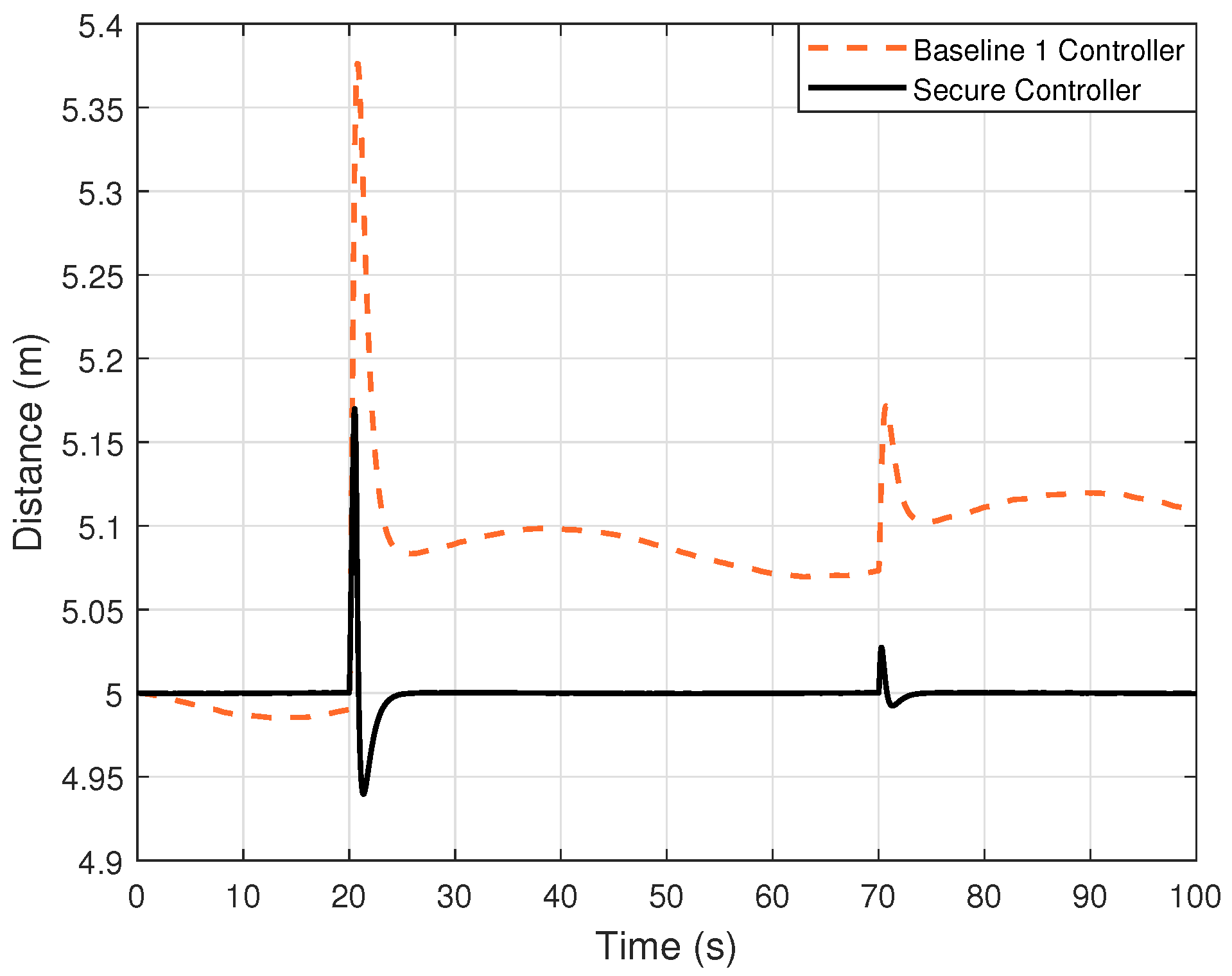
6.4. Comparison Scenario
In this subsection, the effectiveness of the proposed secure controller is further validated by comparing its performance with the baseline 1 controller, as introduced in [
22]. The control method presented in this paper incorporates an FDI attack estimator and employs a hybrid approach that integrates model-based and learning-based techniques. In addition, the controller design does not rely on the leader’s model.
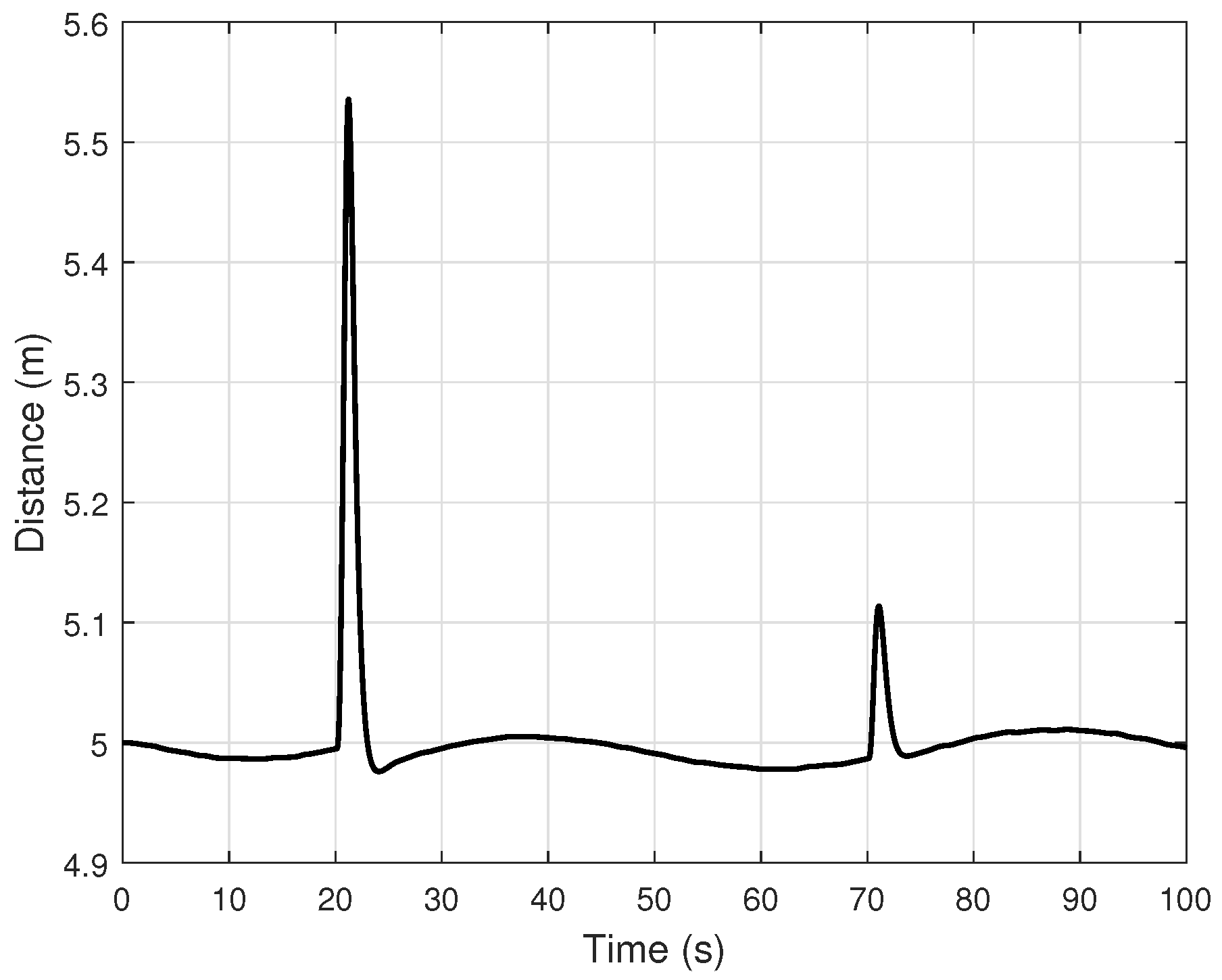
Figure 6 and
Figure 7 illustrate that while the baseline 1 controller successfully maintains the desired distance and estimates the FDI attack, our proposed method demonstrates superior performance. To quantify this improvement,
Table 3 presents the RMSE values for distance and FDI attack estimation, providing a clear comparative assessment. Although the baseline 1 controller achieves low RMSE values, indicative of its good performance, our proposed controller exhibits even lower RMSE values, further confirming its enhanced accuracy and effectiveness.
6.5. Platoon Scenario
In this subsection, we present an additional simulation involving a platoon of five vehicles, where the fourth vehicle is designated as the leader (
) and the fifth vehicle as the follower (
i). In this scenario, an FDI attack is introduced as a step function with a step time of 50 s. The FDI attack function begins at an initial value of 0 and increases to a final value of 0.6, targeting the communication channels of all five vehicles. To further evaluate system robustness, we incorporated external disturbances modeled as
to the model of vehicles and a time-varying communication delay represented by (
) into the transmitted control and velocity signals of the leader vehicle. Additionally, measurement noise was included in the Simulink model for a realistic evaluation. For the following figures, we used
and
. As illustrated in
Figure 8, the velocities of all five vehicles are depicted, demonstrating that even under the influence of FDI attack, external disturbances, measurement noise, and time-varying communication delays, the vehicles maintain harmonic movement, with each follower closely tracking its respective leader. Furthermore,
Figure 9 shows the distance between the fourth and fifth vehicles. While minor deviations from the desired 5 m spacing are observed, the vehicles consistently maintain a safe inter-vehicle distance, significantly reducing the risk of collisions. To quantify the impact of disturbances and delays,
Table 4 presents the RMSE value for inter-vehicle distance. The results clearly indicate that increasing the values of
and
leads to higher RMSE values, reflecting the greater effects of larger disturbances and communication delays.
6.6. FDI Attacks on Control and Velocity Signals
In this subsection, we present a new scenario of the attacks on the communication between vehicles. A sophisticated attacker gains access to the communication channel and injects different types of FDI attacks into the transmitted data. Specifically, the velocity signal is disrupted by a uniform random disturbance signal, characterized by a minimum value of 0, a maximum value of 0.5, and a fixed seed of 1 to ensure repeatability. Concurrently, the control signal is subjected to two distinct step-function FDI attacks: the first initiates at 30 s, transitioning from an initial value of 0 to a final value of 0.3, while the second begins at 60 s with a similar transition from 0 to 0.3.
Additionally, the simulation includes a noise and a disturbance defined as
. As shown in
Figure 10, the proposed method effectively mitigates the adverse effects of these diverse FDI attacks, disturbances, and measurement noise, ensuring that the desired safe distance between vehicles is maintained. Furthermore,
Figure 11 illustrates how the following vehicle successfully tracks the leader vehicle, maintaining the same velocity profile despite the injected attacks and external disturbances. It is important to note that in this scenario, the estimation of FDI attacks is not performed when the injected attacks on the control and velocity signals are different. Our proposed method is designed to estimate FDI attacks effectively when the same attack is applied to both control and velocity signals.
6.7. Experimental Results
The experimental setup was designed to validate the results obtained from MATLAB Simulink by integrating the lead vehicle and controller within the Simulink environment while using the Ford Fusion as the follower vehicle. During testing, the control signal was generated within MATLAB Simulink and subsequently converted into a controller area network (CAN) message using dedicated Simulink blocks. This CAN message was then transmitted to the actual vehicle via CAN communication. The vehicle’s CAN bus interface facilitated both the reception and transmission of these messages. To establish seamless communication between Simulink on the computer and the vehicle’s CAN bus interface, Kvaser USB interfaces were employed. Once the control signal was received by the vehicle, its velocity data were extracted as CAN messages and sent back to MATLAB Simulink.
In this scenario, the FDI attack is modeled as a step function, starting at zero and increasing to 0.6 at 35 s. Additionally, a disturbance, represented as
, and measurement noise were introduced in the Simulink model to better simulate real-world conditions. The lead vehicle, initially positioned 10 m ahead of the follower, begins moving at the start of the test and increases its speed at the 50 s mark.
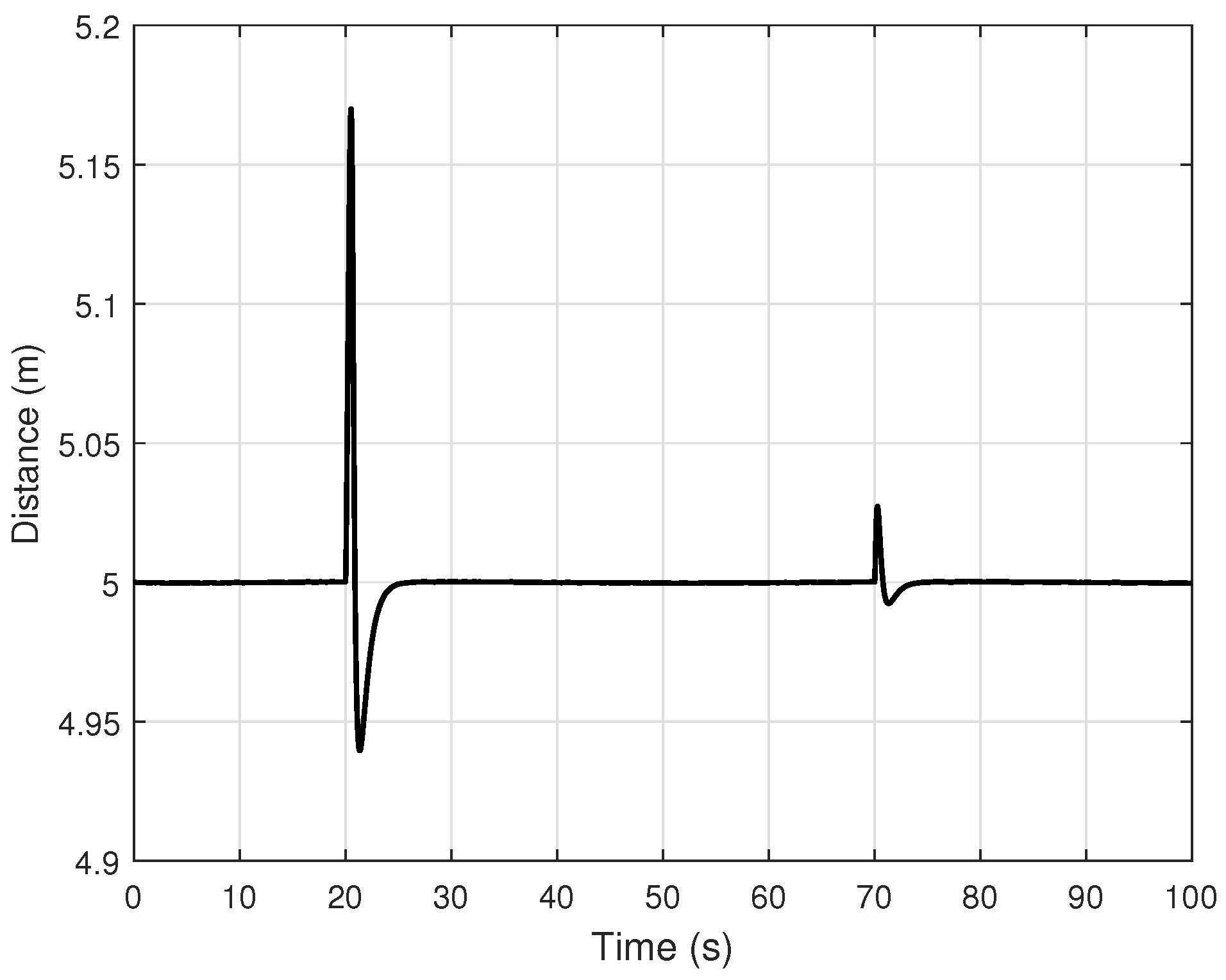
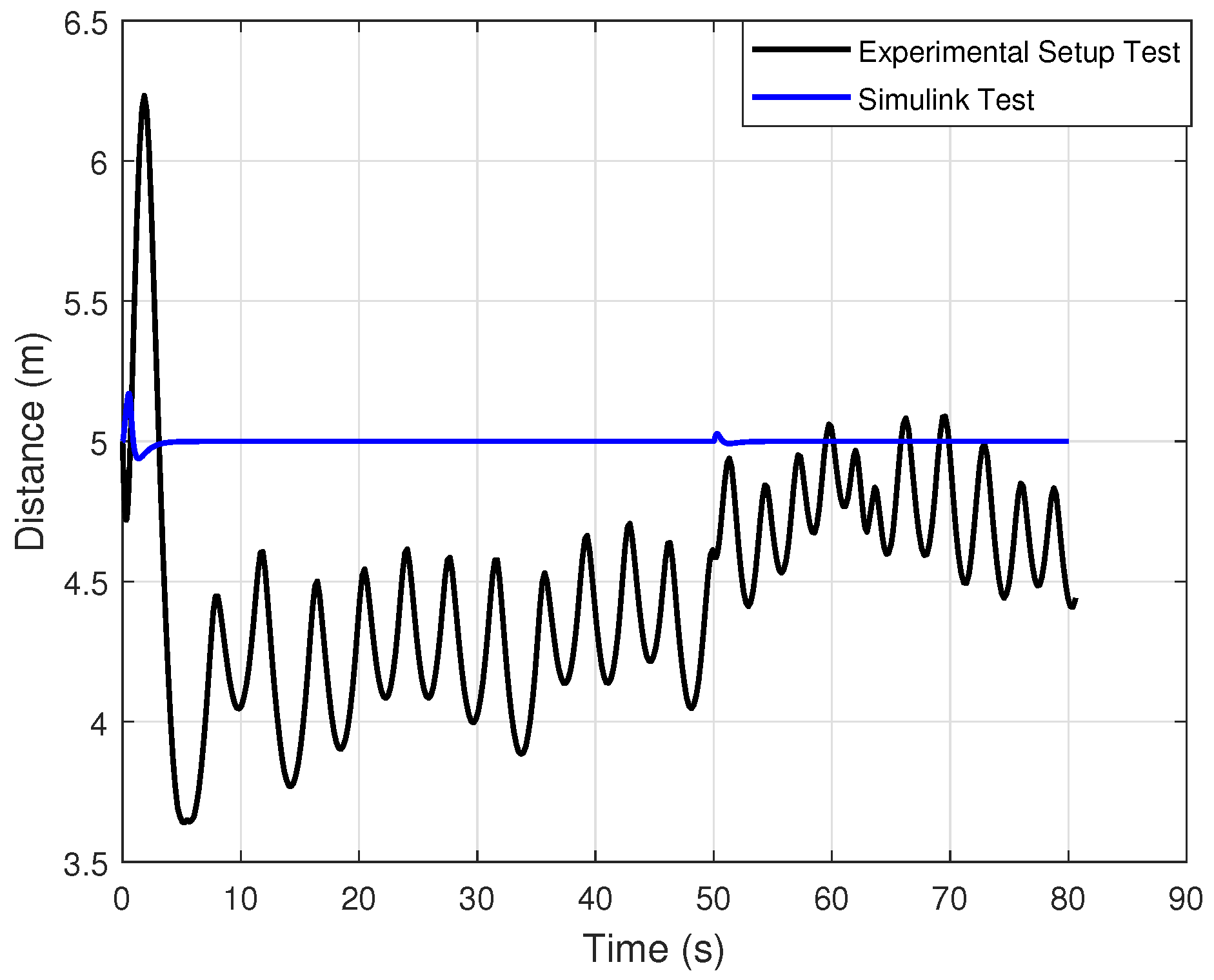
Figure 12 shows the distance between the vehicles in both the Simulink simulation and the experimental setup. In the simulation, the desired inter-vehicle distance is well maintained throughout the test. In the experimental setup, some overshoots and undershoots appear when the lead vehicle changes its velocity. Despite these fluctuations, the minimum observed distance remains above 3.5 m, ensuring a low risk of collision.
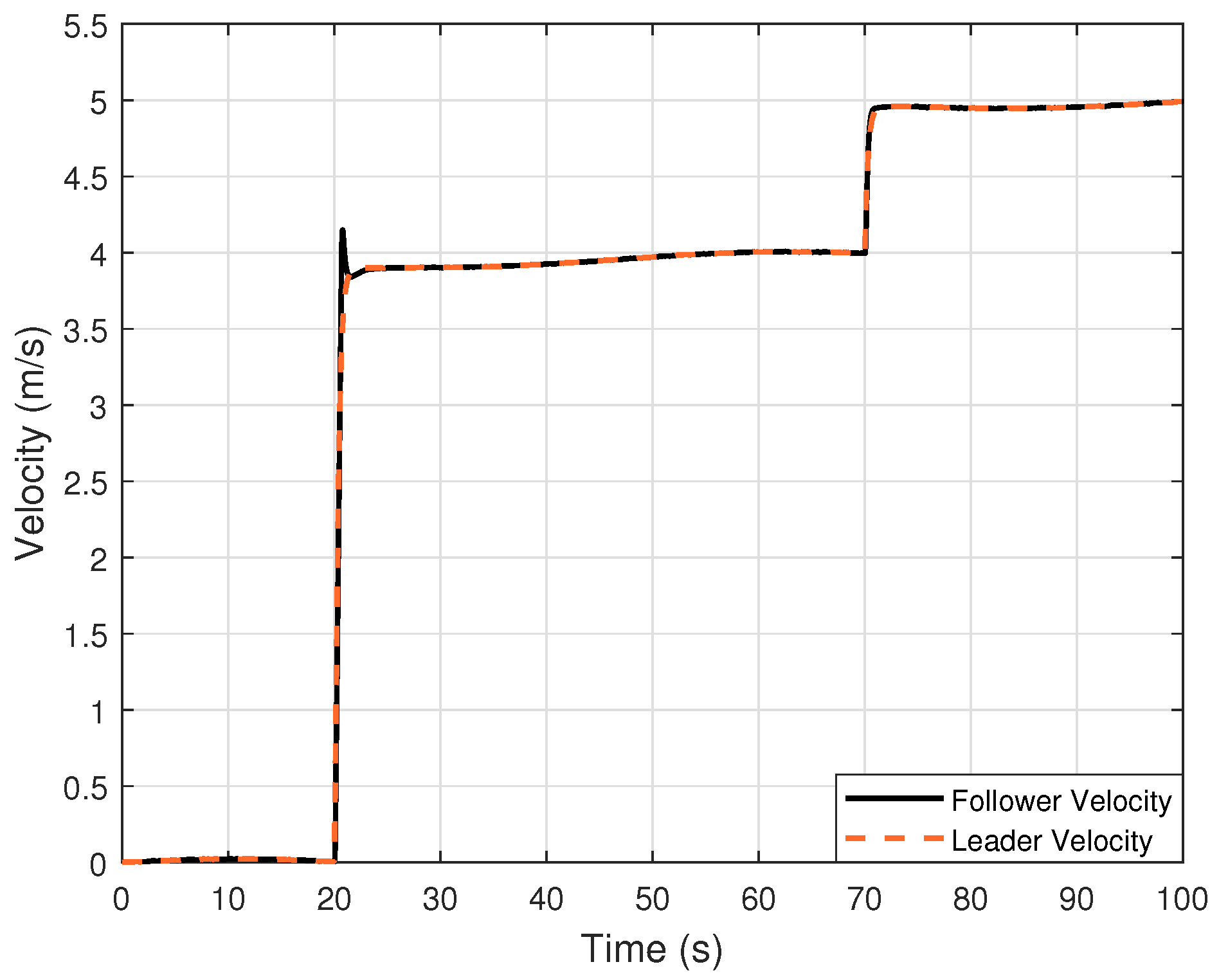
Figure 13 illustrates the velocity profile of the vehicles. As shown, the follower vehicle initially tries to match the movement of the leader, maintaining the 10 m gap. When the lead vehicle accelerates at 50 s, the follower responds accordingly. These results confirm that the follower successfully tracks the leader while maintaining a safe distance, demonstrating the effectiveness of the control strategy.