1. Introduction
AI integration with enhanced sensing technologies drives the development of smart healthcare systems [
1]. An important aspect of this development is the IoMT, which is a specific subset of IoT that includes wearable and implanted medical devices, including body sensors and ECG monitors. These devices provide improved patient outcomes, early disease identification, and ongoing health monitoring, which are especially important during international emergencies like the most recent COVID-19 pandemic [
2]. Thus, it became clearer that intelligent healthcare solutions were needed. According to projections, the global SHS market is expected to become 461.76 billion USD by 2029 [
3].
The demand for IoMT technology has increased due to the critical need for remote communication between patients and medical personnel. Between 2019 and 2021, the Seha application by the Saudi Ministry of Health processed about two million remote medical consultations [
4]. Effective encryption in IoMT is a critical component that can improve clinical data accuracy and patient care, making it an essential choice for future e-healthcare infrastructures. The main objective is to simplify and secure remote patient monitoring; thus, it could enable the management of chronic illnesses and emergency responses [
5].
IoMT faces a fundamental issue in handling highly sensitive PHI securely, despite its transformational promise. The FDA said that ransomware was responsible for 34% of cyber-attacks, which affected 82% of healthcare systems [
6]. In general, patients are frequently scared of medical or health-related information since it is so sensitive. Many of the IoMT systems in use today have a basic weakness in that they rely on centralized cloud servers for data collecting and processing. These models are simple to use, but they are susceptible to a number of attacks. Furthermore, it can be challenging to track illegal access with these models since they frequently lack auditability and secure access control [
7].
Blockchain technology provides a significant base to develop secure and reliable healthcare systems to address these limitations due to its core features, like decentralization and transparency [
7]. However, many related approaches face critical challenges because they often rely on public blockchains without accurate permission controls, raising concerns about compliance with HIPAA regulations. Other approaches store encrypted health data on the blockchain, resulting in high cost of storage, scalability bottlenecks, and inefficient performance [
8]. Intelligent encryption dynamically adapts encryption schemes based on data sensitivity, user roles, and regulatory requirements as a key improvement to overcome these issues. The IoMT systems can ensure that only authorized users can access specific data segments by using intelligent encryption, ensuring regulatory compliance without sacrificing security or performance.
To ensure privacy protection is commensurate with the risks, this study presents an SDAIPA hybrid classification model to dynamically prioritize data sensitivity in medical IoMT environments. The model integrates the SDAIA four-level sensitivity framework, which categorizes data as public, confidential, secret, and top secret, with HIPAA standards for protected health information, which define features such as age, diagnosis, and biometric identifiers as inherently sensitive. Furthermore, it includes IoMT-specific clinical risk indicators to raise sensitivity levels based on the actual healthcare context. This classification directly informs adaptive encryption policy, where low-sensitivity data is protected with AES encryption, while high-sensitivity records use hybrid OHE-WOA. By leveraging the priority of sensitivity in regulatory standards and clinical relevance, the SDAIPA model enables a system that preserves privacy, which is compliant with the law and medical awareness.
1.1. Study Motivation
The study motivation is related to the need for preserving privacy based on data sensitivity and regulatory compliance to meet the unique requirements of the IoMT. As IoMT devices become increasingly sensitive, traditional security mechanisms are failing to address the dynamic privacy demands and the diverse capabilities of the devices. Due to this gap, the study provides an intelligent encryption approach with IoMT to ensure data integrity and access control while preserving patient privacy. The proposed approach is based on a hybrid SDAIPA classification scheme that integrates the SDAIA with HIPAA standards. This hybrid model provides a dynamic sensitivity assessment of health data based on patient data sensitivity to provide adaptive encryption that aligns with both local and international regulatory requirements.
1.2. The Contribution
The main study objective is to provide an adaptive encryption-based privacy-preserving IoMT that combines hybrid sensitivity-based data classification with bio-inspired optimization of FHE. The SDAIPA classification is used as an intelligent filter, dynamically assigning sensitivity levels to medical data using HIPAA identifiers and SDAIA standards. This allows for an adaptive encryption technique in which processing complexity is only justified for high-risk material. For these sensitive records, the WOA is used to increase the entropy of FHE keys while also improving cryptographic strength.
The secure data is then stored using a hybrid architecture that combines off-chain storage as IPFS for scalability with a blockchain for integrity and auditability. This hierarchical structure provides a balanced solution that maximizes privacy without crippling system performance. Accordingly, the study contributions are highlighted as follows:
- ▪
Enhanced privacy for high-sensitivity data: Use FHE selectively on data classified as secret and top secret to achieve higher privacy preservation.
- ▪
Efficient resource utilization: Use the SDAIPA model to ensure that computationally intensive FHE is applied only for sensitive data and lightweight ciphers for low-sensitivity data, preserving battery life and computational energy on wearable IoMT devices.
- ▪
Developed OHE: Optimize FHE by WOA to maximize entropy and strengthen ciphertext resilience.
- ▪
Comprehensive performance evaluation: Evaluate the proposed hybrid OHE-WOA approach for the IoMT model against other baseline algorithms across multiple metrics.
The results of this study are analyzed using a framework for evaluating privacy, security, and efficiency in IoMT contexts based on the following:
- ▪
Use two real-world datasets for a cardiac monitoring set and a telemetry set for diabetic patients, representing diverse medical conditions and varying sensitivity levels.
- ▪
For each record, the SDAIPA classifier first assigned a sensitivity level, and then the proposed hybrid OHE-WOA scheme for high-sensitivity data was applied. Baseline AES and RSA methods were uniformly applied to all records.
- ▪
Performance was measured by using the sensitivity of privacy index and privacy weighted score with efficiency metrics such as encryption/decryption time, computation energy, and entropy.
The paper sections are organized as follows:
Section 2 provides an IoMT technical background with the concept of security and encryption optimization. The literature review and the proposed model are discussed in
Section 3 and
Section 4, respectively. The methodology discussing the proposed approach is reviewed in
Section 5. The experimental results and discussion are given in
Section 6. Finally, the conclusion is presented in
Section 7.
2. Technical Background
The IoMT network interconnects medical devices to gather, send, and analyze physiological data in real-time applications. The employment of modern technologies in healthcare facilities has seen a considerable increase in attention since the beginning of the COVID-19 pandemic [
9]. The ability to remotely track, identify, and regulate patients made IoMT devices one of the most important weapons used to combat this epidemic. Medical sensors, actuators, mobile devices, and cloud computing have all been integrated to enable real-time vital sign monitoring for patients. IoMT devices may be divided into two main classes depending on their attributes [
10]. An IMD that is medically implanted into a patient with the goal of staying in place to augment, replace, or support the body’s biological processes is the first kind. One type of IMD used to monitor and treat irregular heartbeats is a pacemaker [
11]. IoWDs are a second category of wearable technology, which comprises instruments that are worn or used externally to track health in real time. ECGs, wearable monitors, and smart watches are examples of such gadgets. Millions of connected IoMT devices are being used in healthcare applications, which has accelerated the global adoption of IoMT [
12].
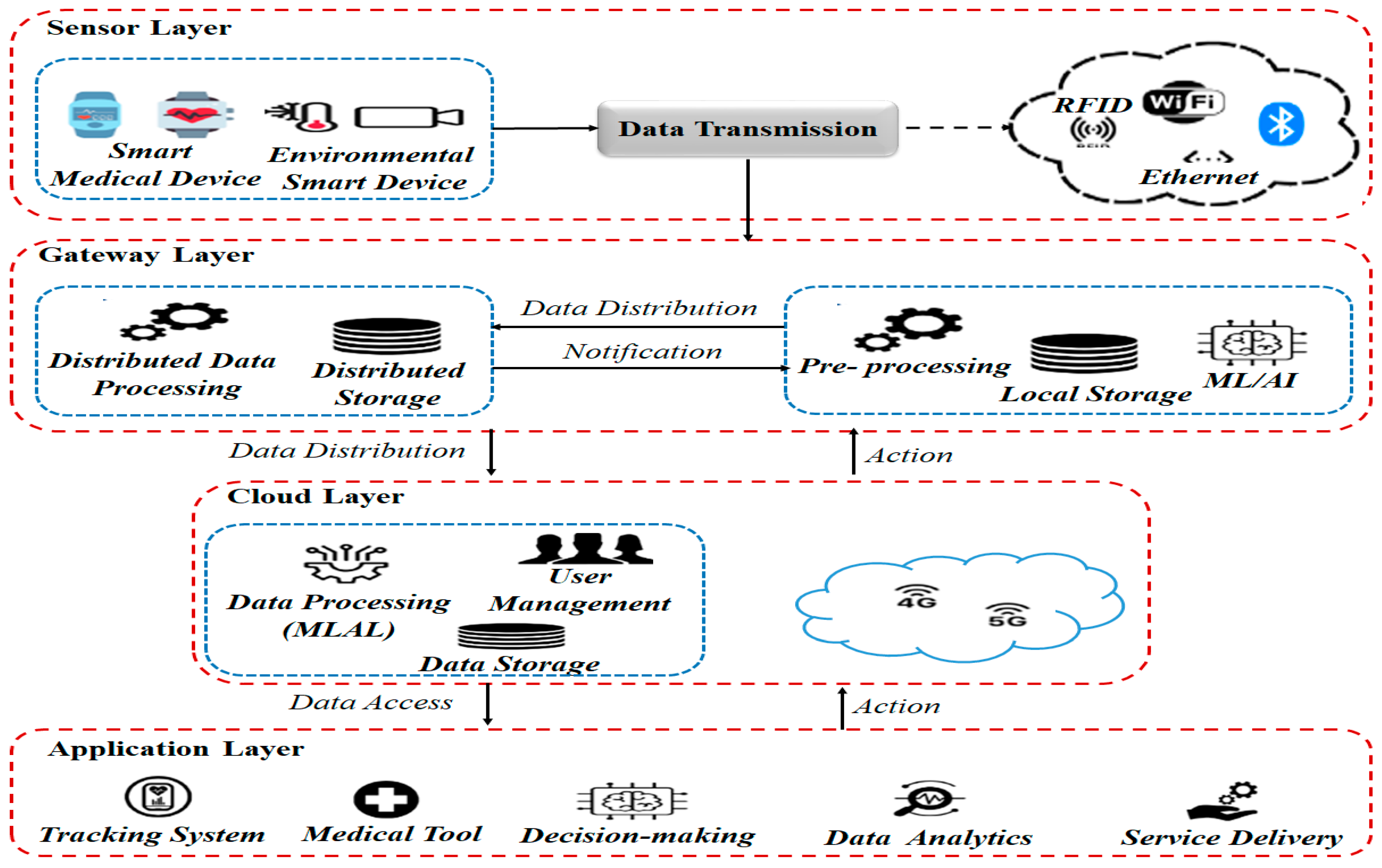
Four layers make up IoMT systems in general: sensors, gateway, cloud, and application layer for IoMT procedures. An IoMT system is depicted in
Figure 1 based on its primary components. Sensors and devices that can record a variety of signals, such as environmental conditions and physiological data, are used by patients to interact with the system [
12]. The gathered data is sent to a gateway by these devices. The gateway gathers and prepares the data to be used according to the requirements of the application. The gateway provides more processing resources by sending the data to the cloud for storage [
13]. The application layer connected to the system can view user data for additional analysis due to the cloud. Depending on their particular requirements, authorized users are able to access the gathered data through the application interfaces.
Several sensors incorporate data from a variety of sources, including smart objects, monitoring devices, and mobile apps. These sensors and devices gather medical data and send it via various communication technologies [
14]. The controllers are used to carry out activities and operate sensing devices. The gateway provides access using short-range communication technologies to aggregate data from various sensors. The gateways are located near the data-collection devices at the edge of the network. These gateways carry out comparatively easy operations like data validation, cleansing, and preprocessing. Fog computing is a decentralized method of computing and storage that is situated near the data source to be accessed by the gateway [
15]. The gateway is in charge of exploiting long-range communication methods to distribute data to the cloud layer.
Cloud computing uses ML to handle data and provides high computational tasks. For long-term data management, both distributed and centralized data storage are used [
15]. The application layer performs data analysis activities by employing AI and ML methods to learn valuable insights from collected data. This layer facilitates the management of patient care by carrying out functions like data visualization, reporting, and decision-making. To ensure a complete approach to healthcare management, application layers offer additional technologies like tracking and remote patient monitoring [
16].
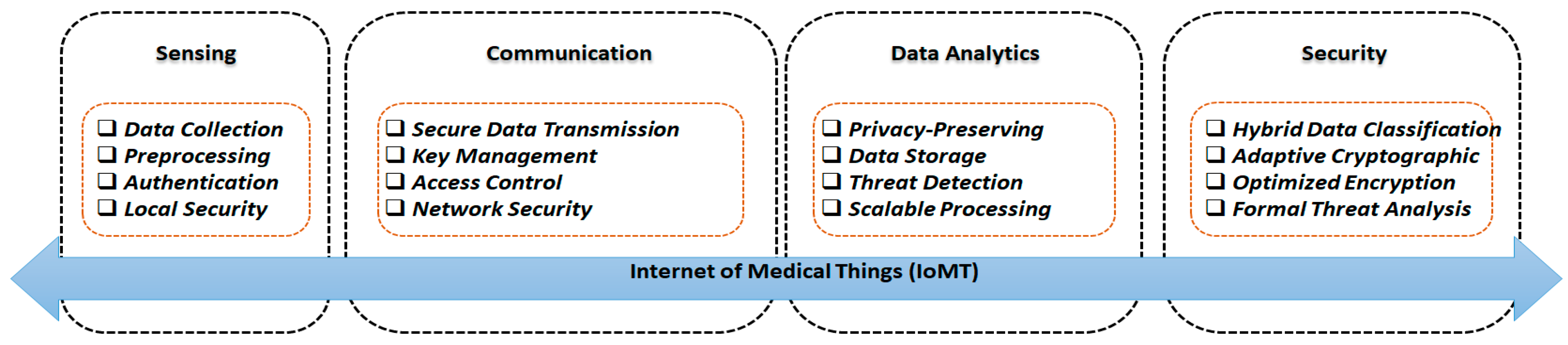
To ensure increased efficacy and dependability, four crucial elements of the IoMT system concept must be prioritized during design and implementation. The IoMT security-based system architecture is depicted in
Figure 2. Layers of data analysis, communication, sensing, and security make up the system [
16]. For patient privacy, the functionality of medical equipment and systems, and the availability, confidentiality, and integrity of sensitive medical data, security is essential to the IoMT paradigm.
2.1. IoMT Data Privacy Challenges
The rising need for smart medical systems to enhance diagnosis and treatment processes through wearable technology based on the IoMT has made remote healthcare more important [
17]. As a result, there are billions of medical Internet-connected sensors, gateways, and networks that are being utilized extensively for remote patient monitoring, patient care, and therapy. However, sharing patient data across several medical platforms raises a number of privacy concerns.
Data privacy is very important in medical devices that are used for remote access during procedures [
18]. Due to the many architectures developed for medical IoT systems, which expose users to privacy problems, medical IoT devices generally currently struggle with effective protection of sensitive information. Furthermore, stored EHR data is susceptible to alteration and illegal access. Additionally, the software used for cloud data analysis must run on third-party servers, which facilitates misuse by unauthorized parties [
19]. This issue may be resolved by recent technical developments like blockchain, edge computing, and fog computing.
2.2. Advanced Privacy-Preserving Approaches
Several advanced technologies can be implemented in IoMT to solve the particular challenges of privacy preservation in distributed healthcare environments with limited resources [
20]. The main security measures supporting the framework are technically summarized in this section. Techniques like SDAIPA, OHE, and permissioned IPFS-based secure hybrid data storage architectures allow for maximizing security and privacy preservation in IoMT [
21].
2.2.1. Hybrid Data Classification
SDAIA and HIPAA formed SDAIPA for personal data protection and produced a hybrid data classification model as a regulatory standard [
22]. The four sensitivity levels—public, confidential, secret, and top secret—are determined by the possible harm of unapproved disclosure. The context-aware security policies that assign a risk level to each data property are made possible by the SDAIPA classification. As an example, heart rate measurements may be considered public, but a patient’s identity is top secret [
23]. The selection of an encryption technique is directly influenced by this qualitative classification, guaranteeing an efficient use of computational resources, lightweight ciphers for low-sensitivity data, and complex cryptography for high-risk data.
2.2.2. Fully Homomorphic Encryption
The IoMT can use FHE as a robust encryption method that allows arbitrary computations on encrypted data without the need for decryption to provide end-to-end privacy throughout data processing [
24]. FHE protects confidentiality in untrusted cloud environments, which is essential for AI-driven diagnostics and federated learning applications. This is in contrast with conventional schemes like AES or RSA, which reveal plaintext during analytics. However, FHE’s performance deteriorates due to ciphertext noise accumulation [
25]. In order to address this, the system uses bootstrapping, a technique that converts noisy ciphertexts into clean equivalents, allowing for infinite computations and improving usability in real-world scenarios.
2.2.3. Encryption Based on Bio-Inspired Optimization
The integration of FHE with bio-inspired optimization techniques like WOA enables increasing key entropy and overcoming attacks [
26]. These meta-heuristic algorithms are used in the FHE scheme’s parameter space to find configurations that produce the strongest ciphertexts. The WOA approach has demonstrated the best convergence and global search capabilities, which makes it perfect for optimizing intricate, non-linear cryptographic algorithms [
27]. The system uses the suggested OHE to work by adjusting the encryption parameters using WOA, which strikes a balance between operational efficiency and security strength.
3. Related Works
IoMT-based privacy preservation has become an important model for solving the issues of data integrity, security, and privacy. Effective IoMT ensures confidentiality, authenticity, and access control, which are necessary due to the amount and sensitivity of generated health data. Blockchain-based frameworks have been proposed in many recent studies as a way to improve control over patient-centric PHI and decentralize trust in IoMT systems [
27]. With an emphasis on how they handle data sensitivity, cryptographic efficiency, and system scalability, these are the three main issues that the proposed hybrid encryption IoMT attempts to address.
Table 1 shows the most recent related works on preserving privacy for IoMT systems.
The authors of [
28] proposed a bi-encryption decryption crypto method based on elliptic curve cryptography that strengthens privacy-preserving measures to safeguard patients’ private medical data. The pair-based cryptography library is used to test the proposed strategy. The proposed approach outperforms the current security approaches in terms of privacy and computing efficiency. In [
29], authors use DL with JSO for IoMT applications to provide an improved security strategy for a human-centered model. The method enables safe transmission of medical information with early identification of health issues by IoT devices in the healthcare industry. For disease identification and classification, the method uses a CNN with LSTM and the min-max normalization approach to convert the input data into a more appropriate format. This strategy provides a higher accuracy value than current methods, according to the results.
In [
30], the authors provide a hybrid SDAIPA IoMT data classification approach that combines dual risk analysis with HIPAA and SDAIA concepts. The value of the proposed method is in providing a useful guide for sensitive IoMT data management by coordinating regulatory guidelines with a systematic classification procedure that has been verified by subject-matter experts. By helping healthcare providers better allocate encryption resources, the proposed SDAIPA can ensure more robust protection for high-risk features. In [
31], the authors proposed a way to use IoT devices that combine the WOA with DCNNs to improve safety in sustainable smart home environments. The proposed method improves safety by effectively spotting and preventing potential attacks in real time. Through thorough testing and analysis, the observations demonstrate that the strategy effectively protects smart home systems from a variety of safety threats. The authors of [
32] proposed an FHE approach for the safe storage of medical data. The method was created using a WOA algorithm based on CCRB machines. The results of the experiments show that the evaluation performs better than the existing e-healthcare solutions.
In [
33], the authors provide a blockchain approach for access control with a key management system created especially for e-healthcare applications based on IoMT. Through the use of mutual authentication and dynamic key generation, it creates safe communication routes between body sensors, personal servers, and cloud platforms. While ensuring end-to-end security, the proposed solution supports lower computational costs than benchmark systems. Adaptive sensitivity-based classification and safe computation on encrypted data are not included in the protocol, which still relies on conventional encryption techniques despite its useful emphasis on effective key exchange.
The authors of [
34] proposed a hybrid approach that uses IPFS to combine off-chain storage with blockchain. The system includes a medical chain that stores diagnostic hashes and a hash index of encrypted patient data. Moreover, chain of identification authentication ensures the legitimacy of medical practitioners. Nevertheless, the encryption method is restricted to AES-128 as a symmetric cipher that necessitates decrypting data prior to processing. This fails to provide computation that preserves privacy and exposes sensitive information during analysis. A study in [
35] proposed a healthcare data management system based on IPFS for patient-controlled and decentralized data exchange. The IPFS is used to store encrypted health records off-chain, with only their access logs and content hashes kept on-chain. The proposed method improves patient privacy while successfully reducing the hazards connected to centralized repositories. However, it relies entirely on AES encryption, which is consistent across all data types, regardless of sensitivity.
One significant observation from the related works is that despite advancements in off-chain storage, decentralization, and access control, they still mostly rely on conventional encryption methods like AES and RSA, which need data decryption in order to be processed [
36]. Sensitive personal health information may become accessible to untrusted third parties, especially in cloud analytics environments, which presents a hacking opportunity. Accordingly, a more specialized encryption method, such as FHE, can be utilized in place of a simpler one [
37]. This encryption provides a practical solution while maintaining confidentiality at all parts of the data lifecycle, starting from its collection to analysis, by allowing for random computations on encrypted data without disclosing the plaintext. However, high computational complexity, noise in ciphertexts, and wearable device energy consumption will impact the practical implementation of FHE in IoMT systems. Existing approaches apply FHE uniformly across all data types without considering data sensitivity, resource constraints, or dynamic cryptographic adaptation. There is no existing work that proposes an adaptive hybrid model that integrates sensitivity-based classification with conditional optimized FHE to maximize the privacy–efficiency balance in IoMT systems [
37]. In order to increase key entropy and fortify ciphertext resilience against hard attacks, the proposed adaptive encryption approach for the IoMT system uses bio-inspired optimization methods like WOA.
The existing IoMT models do not offer complete computational privacy despite the fact that they have significantly increased security for IoMT systems through blockchain decentralization, off-chain storage, and enhanced access control. Their capacity to facilitate secure external computing is constrained by their dependence on underlying cryptosystems [
38,
39]. To handle this gap, the proposed IoMT-based privacy-preserving system has enhanced features, like optimizing the OHE with WOA for safe computation on encrypted data with a hybrid SDAIPA data categorization model for regulatory-compliant sensitivity labeling. It also has a scalable hybrid storage architecture that uses IPFS for encrypted payload storage and a permissioned blockchain for transaction recording [
39]. Developing a reliable, effective, and intelligent IoMT system that ensures a compromise between privacy, performance, and compliance is made possible by this integrated approach.
5. Methodology
The study evaluates the performance of hybrid encryption with the proposed adaptive encryption approach for an IoMT model to enhance privacy-preserving in IoMT by integrating hybrid data classification and optimized FHE. This integrated approach is aimed at addressing the challenges of data privacy and system scalability in decentralized healthcare environments [
49]. This methodological section covers the mathematical model, implementation, and analytical approach to simulation, focusing on simulating security operations while recognizing the practical limitations of full system deployment.
The main focus is on quantifying the computational cost of OHE compared to traditional cryptographic methods such as AES-128 and RSA-2048 under varying data loads, unlike prior works that rely on basic ciphers [
49,
50]. The proposed use of FHE enables secure computation on encrypted data without decryption as a crucial capability for AI-driven diagnostics and cloud-based analytics in smart healthcare. However, SHE consumes a lot of resources due to the accumulation of ciphertext noise and the high-complexity computation [
50]. Bootstrapping is used to overcome this issue.
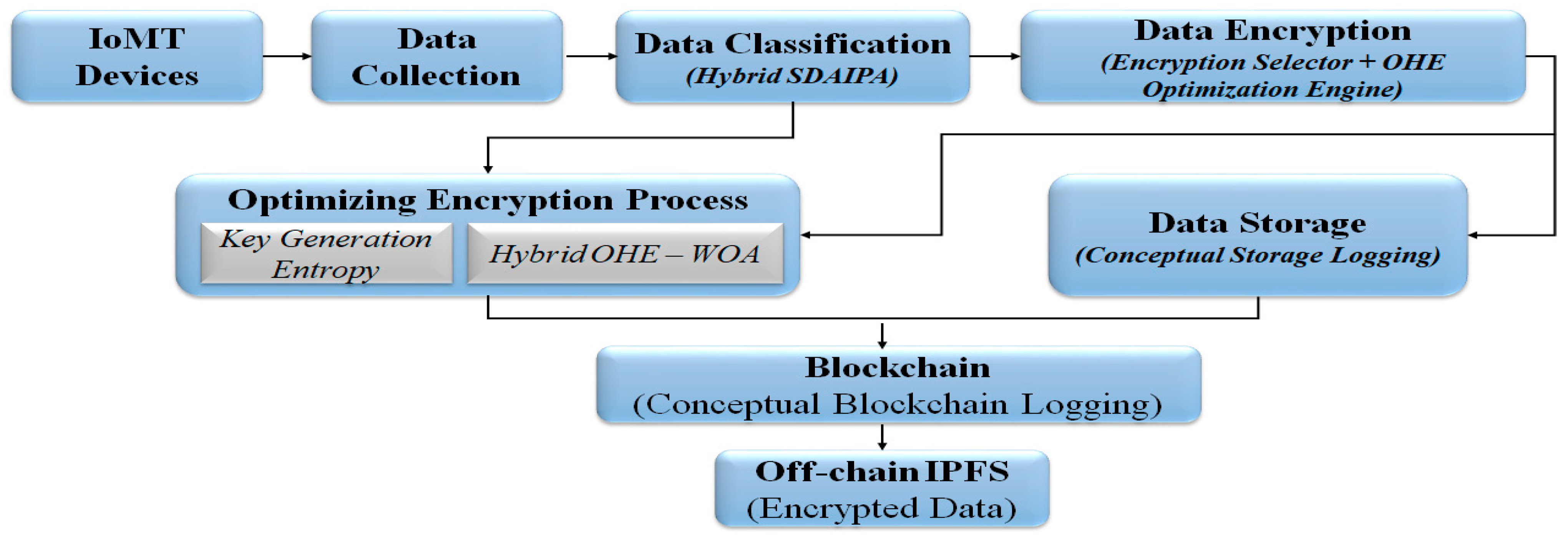
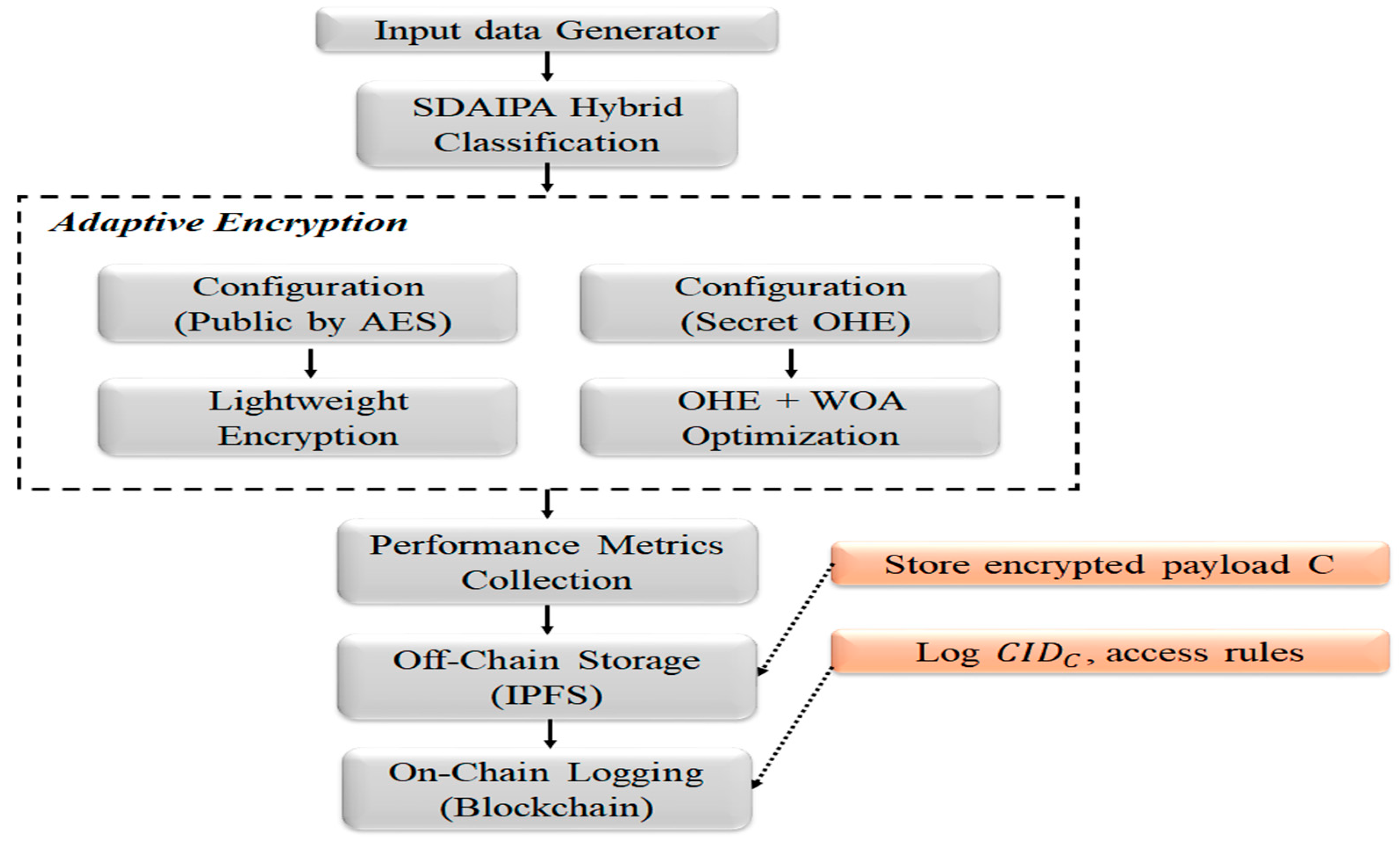
Figure 4 shows the adaptive encryption model used in the simulation. It shows a sequential workflow, represents the medical datasets using SDAIPA classification, and adaptive encryption selection by selecting AES or OHE according to data sensitivity. To represent the process of blockchain, an on-chain logging block is used to simulate the recording of transaction hashes and access rules, while off-chain storage models IPFS content, addressed through hash generation [
51].
To improve the encryption process, a WOA approach is applied to maximize the key entropy of the FHE secret key. WOA searches within the space of secret key seeds to identify configurations that give keys with higher randomness within a specific search space of 1024–8192 bits. This represents a new method compared to using traditional key generation, as the encryption strength is dynamically optimized rather than set statically [
51]. The hardware specifications to simulate the proposed approach are shown in
Table 2.
5.1. Data Description
The evaluation of the proposed preserving-privacy approach is conducted by using two datasets in [
52,
53]. Dataset 1 consists of recorded data for vital signs and risk assessments for pregnant women, which is available online at (
https://www.kaggle.com/datasets/drmbsharma/maternal-health-risk-data-set) (accessed on 16 September 2025). Dataset 2 recorded the patient monitoring during sleep, and it is available at (
https://www.kaggle.com/datasets/laavanya/human-stress-detection-in-and-through-sleep) (accessed on 23 September 2025). This dataset provides a realistic foundation for simulating wearable IoMT devices, as it includes key health parameters such as age, heart rate, blood pressure, body temperature, blood oxygen, blood sugar, eye movement, etc., which are commonly monitored in remote patient care systems.
For evaluating the proposed approach, 806 records were used to simulate a diverse workload of IoMT sensor data. Each record represents a single patient observation, and its sensitivity level is determined using the hybrid SDAIPA classification model, which combines HIPAA identifiers with Saudi SDAIA data protection regulations. The classification logic assigns sensitivity levels to the two datasets, which are given in
Table 3.
The content-based classification, as shown in
Table 4, ensures adaptive encryption. The hybrid OHE-WOA standard is used only for confidential and top-secret data, while the AES-128 standard is used for general and confidential data, thus improving the balance between privacy and efficiency. To analyze system performance under increasing workloads, the dataset of 806 records was divided into six sets, as shown in
Table 4. This grouping allows for an assessment of how encryption time, power consumption, throughput, and privacy metrics correlate with data size and sensitivity distribution.
5.2. Data Preprocessing
The experimental evaluation leverages two real-world IoMT datasets to ensure broad applicability across clinical domains. The first is a dataset containing features including age, blood pressure, blood sugar, body temperature, and heart rate, along with a clinical label of high risk or low risk [
52]. The second is the sleep monitoring dataset with records of physiological indicators such as sleep duration, snoring range, respiration rate, heart rate, blood oxygen level, and stress state categorized as low, medium, or high [
53]. The preprocessing was performed through a unified rule-based sensitivity mapping that assigns each record to an SDAIA-compliant sensitivity level based on its risk context. For dataset 1, the risk level is low or high, and the data are classified as public, confidential, or secret. For dataset 2, the stress status is classified as confidential, secret, or top secret. This classification map conforms to the principles of SDAIA and HIPAA, ensuring that higher clinical or physiological risks result in stronger privacy protection. No feature normalization or transformation was applied to the raw sensor values, as the classification relies solely on interpretable and domain-specific thresholds, as given in
Table 3. The combined dataset records were processed record-by-record without splitting, reflecting real-time IoMT operational constraints. This rule-driven preprocessing ensures cryptographic intensity AES for lower sensitivity and WOA-optimized FHE for high-risk data, which is dynamically and transparently aligned with medical context.
5.3. SDAIPA Classification Model and Encryption Selection
This study proposes an SDAIPA that integrates the SDAIA and the HIPAA to provide context-aware privacy preservation in IoMT systems. This integration is appropriate for deployment within Saudi Arabia’s digital health infrastructure since it ensures compliance with both national data governance principles and international healthcare privacy requirements [
53].
Table 4 shows how the SDAIPA model is used to divide medical data into four sensitivity categories, which are defined by the possible harm that could result from unapproved access, as they are classified in sets to be simulated.
To model the IoMT sensor feeds, classified data volumes from the datasets are used to represent the typical workloads. Let D = {
,
,...,
} be the set of data sizes used in the evaluation [
53]. These values simulate the number of records collected from wearable devices such as heart rate readings or blood pressure measurements over time. The data are used as indicators rather than features of the content’s personal health information [
54]. This allows for controlled experiments but is limited in its ability to fully replicate the variability of real-world data. The final sensitivity label for the entire record (
is determined by the highest sensitivity among its indicators, as follows:
Each indicator
∈
is mapped to sensitivity level S(
). The simulation method uses a proxy-based classification strategy to process raw data sets as a PHI proccess [
55]. This approach uses data size as a proxy for complexity and sensitivity, assuming that larger datasets are more likely to contain sensitive information due to increased feature dimensions and longitudinal monitoring.
Based on the output of the SDAIPA classifier, an adaptive encryption policy is applied to balance security and efficiency. An encryption method is selected according to the selection criteria (
) as follows:
where an
AES type of 128 s is used for low-sensitivity data due to its high speed, low energy consumption, and widespread hardware support. The
OHE refers to an optimized FHE scheme enhanced by bio-inspired optimization, like
WOA, which allows for secure computation on encrypted data without decryption.
The selection criteria enable context-aware security and ensure resource efficiency without compromising protection for critical data. This method operates on the principle of proportional protection, where encryption strength is proportional to data sensitivity [
56,
57]. This prevents the overuse of computationally intensive, high-precision FHE cryptographic analyses on non-critical data while ensuring the protection of highly sensitive information.
5.4. Encryption Optimization Based on Hybrid OHE-WOA Approaches
The WOA algorithm is based on an idea that was affected by humpback whales’ hunting technique, which includes the phases of prey search, bubble-net fishing maneuvers, and prey encirclement [
58]. The WOA matches humpback whales’ capacity to find and circle prey during the initial step of the process, which is known as the prey encirclement phase. The behavior is defined mathematically as in Equation (3) with the optimal solution
(
t), which takes on the role of the leader, being the target prey in each iteration (
t) [
59].
where
and
are the coefficient vectors of WOA. The coefficient
controls exploitation and exploration, and
is a prey-weighting coefficient.
and
range between [0, 1].
D represents the distance between the current whale and the best solution. α is a linearly decreasing coefficient that controls the balance between exploration and exploitation during the search process. The bubble net attack maneuver employs the spiral position update approach and was inspired by humpback whale hunting behavior. Whale displacement toward the prey’s position imitates humpback whales’ spiral motion [
59]. The WOA maximizes cryptographic strength by optimizing key parameters, which improves the security and effectiveness of FHE.
To perform secure computations on encrypted data without decryption, this approach uses the WOA algorithm with FHE as the base encryption tool, which allows for random operations on ciphertexts. The FHE data is encoded and encrypted within a polynomial ring structure to allow for homomorphic operations [
60]. The security, correctness, and performance of an FHE scheme depend critically on the choice of three primary parameters as the ciphertext coefficient (
q), the plaintext modulus (
t), and the noise standard deviation (
σ). The ciphertext coefficient (
q) defines the size of the integer space in which ciphertext polynomials are computed. It directly affects both the security level and the computational overhead of the encryption scheme [
61]. By setting message (
m) ϵ
to be a plaintext vector encoded into a polynomial ring, this gives the following:
where
represents the integer’s modulus
q.
x is the indeterminate (variable) of the polynomial ring.
N is the ring dimension. The
q represents the size of the ring that allows more multiplicative depth before noise overwhelms the signal. The bit length of
q is denoted by log
2(
q), which is a major contributor to the total computational complexity of FHE operations. Under the public key, the data is encrypted by
(m).
The FHE is calculated using mathematical models that reflect its quasi-polynomial time complexity [
61]. Letting n be the number of data records, the encryption time (
) and decryption time (
) with the number of data records (
n) are given by the following:
where
N represents the ring dimension.
C(
n) is the number of ciphertexts required to encrypt n records.
B is given by
N/2 as a maximum batch size.
α and
β are positive constants that represent the performance characteristics of the encryption/decryption execution. To enhance cryptographic strength, the WOA approach is used to find an FHE key configuration that maximizes entropy
H(
k) by calculating the objective function as follows:
where |
k| is the effective key size in bits.
r(
k) is an assumed randomness score between [0, 1].
The proposed framework employs a CKKS-FHE emulation. While the theoretical model uses general FHE parameters representing ciphertext modulus, plaintext modulus, and noise standard deviation, the CKKS scheme uses a scaling factor instead of plaintext modulus to support approximate arithmetic on real numbers.
Algorithms 1 and 2 represent the proposed risk-proportional privacy framework procedures, where Algorithm 1 shows an adaptive encryption setup, and Algorithm 2 shows the improved entropy-based keys.
| Algorithm 1: Adaptive encryption based on hybrid OHE-WOA approaches |
| Input: data sizes () = [, , ….. ] % Array of data recorded counts |
| Input: sensitivity levels % for public, confidential, secret, and top secret |
| Output: encryption time ( , decryption time (, energy (, entropy ( |
Set device power ), optimal key (, optimal entropy () Set classification thresholds () for Set n= [] Calculate = discretize(n, ) ; = max(1, min(, length ()) Calculate Check selection criteria () by Equation (2) if ∈ { public, confidential} then Initialize process of AES-128 for low-sensitivity data Calculate set% Symmetric encryption calculate Calculate else if ∈ { secret, top secret} then Initialize process of OHE for high-sensitivity data Initialize Optimize FHE Key using WOA approach find by Algorithm 2 calculate repeat step 15 end if end for
|
| Algorithm 2: Key entropy maximization by whale optimization algorithm |
| Input: key bounds ( and (; population size ; (T) |
| Output: Optimal key (), optimal entropy () |
Initialize whale positions randomly in [, ] Evaluate fitness () = H() for each whale Set optimal key () = argmax() for t = 1 to T do calculate α = 2 − t (2/T) % Decreasing coefficient for i = 1 todo Set , = rand() % Random numbers in [0, 1] Set p = rand(); if p < 0.5 then calculate WOA , coffecients in Equation (5) if abs() < 1 then Find next solutions byEquation (3) else calculate D = abs( − whales(i)) Find next solutions by whales(i) = − D end if else Initialize spiral updating position calculate distance D by Equation (4); L = −1 + 2 rand() % [−1, 1] Find next solutions by Equation (10) end if set whales(i) = max(min(whales(i), ), ) set = H(whales(i)) If > fitness () then find = whales(i) calculate fitness(i) of if > H() then set = end if end if end for end for return , H(
|
Algorithm 1 uses a sensitivity-aware encryption to align encryption strength with data risk. Based on a set of data workloads (
ds) and predefined sensitivity levels, the algorithm first assigns each workload size (
n) to sensitivity levels (
sL). It selects the encryption type, where for low-sensitivity data it applies AES-128 and gains symmetric encryption for efficiency [
62]. For high-sensitivity data, it uses hybrid OHE-WOA and delegates key generation to Algorithm 2. This ensures that only high-risk records accept the computational overhead of FHE with entropy-optimized keys for enhanced security. This adaptive method avoids the inefficiency of uniform encryption schemes and ensures proportional privacy protection.
Algorithm 2 addresses vulnerability in FHE when weak and predictable secret keys are used with sensitive data. It formulates key generation as an optimization problem where the objective is to maximize the entropy-based fitness function
H(
k). The algorithm initializes a population of candidate keys as whales within cryptographic bounds [
62,
63]. Over iterations, it evolves this population using the WOA approach. It refines solutions near the current best key, enabling local exploitation, then jumps to distant regions via a randomly selected leader, ensuring global exploration. And after, it enables traversing diverse paths toward the optimum using a logarithmic spiral balancing exploration and exploitation. After each position update, the algorithm evaluates the new key’s entropy and updates the global optimum (
k*) if improvement is found and finally gives the secret key with maximized entropy [
63].
The optimization by the WOA algorithm shows its ability to balance exploration when searching for new regions in the solution space with exploitation to improve solutions near promising regions. As shown in Algorithm 2, the population of whales represents sets of candidate FHE parameters distributed over a limited search space defined by key boundaries, which typically range from 1024 to 8192 bits to reflect practical key size ranges. Each whale’s location is updated iteratively based on three key factors: prey encirclement, spiral update movement, and prey search [
64]. These factors are governed by control parameters such as A, C, and L, which evolve over iterations to guide the search toward the overall optimal results.
The prey search mechanism activates during the prey encirclement phase when ∣A∣ ≥ 1, adding unpredictability to the search procedure. As in the case of humpback whales traveling to far-off ocean areas, a randomly chosen whale serves as the leader [
64]. In contrast to a gradient-only method, this step improves the algorithm’s capacity to find potentially better parameter combinations and go beyond the local optimum. During the whale position update phase, each whale swims in unison towards the optimal solution along a certain logarithmic spiral path, which may be computed by Equation (10), when
p > 0.5 [
65].
where
B is a constant that describes the logarithmic spiral motion, and L is a random number in [−1, 1]. The optimum solution by this approach is due to integrating the radial approach, and a spiral trajectory enables a more diverse and robust search pattern, which increases the likelihood of locating the global maximum of the entropy function [
66].
Each whale’s fitness is evaluated by using Equation (9) based on the objective function. By optimizing this entropy, the algorithm guarantees that the final FHE system is impervious to side-channel flaws, statistical analysis, and attacks [
67]. The whale population is iteratively refined for a predetermined number of repetitions before the configuration with the highest entropy is chosen as the ideal set of parameters. In case of the random parameter
p < 0.5 and ∣A∣ < 1, the WOA assumes that the current is the best solution, indicating the whale with the highest entropy is close to the optimal configuration. It then updates the position of each whale by moving it toward this most common solution using vectors A and C [
68]. This method allows the algorithm to fine-tune promising FHE configurations without prematurely converging to local extrema.
6. Experimental Results and Discussion
The proposed adaptive encryption approach-based IoMT model is evaluated by MATLAB 2023a-based simulations to measure the performance of the full system model with an integrated architecture combining hybrid data classification and blockchain with IPFS storage. The proposed framework was evaluated with two datasets: a cardiac monitoring dataset and a telemetry dataset for diabetic patients with 806 records. The analysis was performed as follows:
- ▪
A hybrid SDAIPA classification module assigned each data record to one of four sensitivity levels—public, confidential, secret, or top secret—based on predefined feature rules.
- ▪
An adaptive encryption engine implementing the AES-128 was simulated using the symmetric encryption MATLAB function for low-sensitivity data [
69]. The FHE was simulated for high-sensitivity data by a function that represents the symmetry properties of the ciphertexts using numerical computational capabilities.
- ▪
The WOA was implemented to optimize the FHE key entropy, where key randomness was determined using Shannon entropy. All performance metrics, including encryption/decryption time, ciphertext size, and key entropy, were calculated and stored directly in MATLAB workspace variables and local files.
- ▪
The blockchain and IPFS file system layers were not deployed; instead, their roles were represented by a structured file registry where encrypted data and associated metadata, such as sensitivity ratings, timestamps, and access policies, were stored in local files to simulate secure and auditable storage.
Accordingly, the current implementation focuses on simulating the underlying computational operations, specifically the performance impact of the Hybrid OHE-WOA approach for encryption with the proposed model. This section discusses the simulation assumptions, key parameters, and results, providing a realistic assessment of the framework’s feasibility.
Table 5 summarizes the key parameters used in the simulation.
The evaluation considers different metrics, such as entropy, privacy preservation index, computation overhead, energy efficiency ratio, and privacy gain factor.
Table 6 and
Table 7 show the description of metrics and corresponding symbols to evaluate the proposed approaches, respectively.
The metrics in
Table 7 are used to evaluate the proposed approach to privacy-based performance. The two important metrics are SPI and PWS. In SPI, the entropy-based model and sensitivity-weighting approach are driven by studies [
69,
70]. The cryptographic strength and sensitivity weight are adapted depending on data classification, and the results are given as a normalized privacy score. The PWS is computed as a weighted and normalized sum of the SPI, cryptographic strength, and encryption throughput [
71]. The weighted sum of normalized privacy-based components is computed to produce the IoMT system encryption ranking approach.
To assess the privacy-preserving performance of encryption strategies in IoMT environments, two metrics are proposed in
Table 7: the SPI and PWS. These metrics reflect the multi-objective nature of IoMT security as balancing privacy strength, cryptographic robustness, and computational efficiency. The SPI uses logarithmic scaling, which reflects the diminishing returns of entropy in privacy utility and aligns with the information-theoretic concept. The PWS weights are assigned based on the following:
reflects the degree of data sensitivity based on the SDAIA and HIPAA, where privacy is the most important aspect in processing medical data; this justifies giving it the highest degree of importance.
reflects the key entropy level as the key element of cryptographic resilience, where a moderate weight ensures that security is prioritized without compromising privacy.
reflects the need for low-latency, energy-efficient operation in resource-constrained devices. These weights reflect the priority ranking in healthcare of privacy, security, and efficiency.
The simulation operates under several key assumptions that reflect its role as a realistic, data-driven performance model for evaluating the proposed IoMT cryptographic approach. The following assumptions are based on two publicly available datasets:
- ▪
The simulation uses two datasets provided by [
52,
53], which contain important signs such as age, blood pressure, sugar, temperature, heart rate, and risk level. This dataset provides sensor data inputs from wearable monitoring devices, ensuring the evaluation reflects real-world conditions.
- ▪
Sensitivity classification: The SDAIPA classification model assigns sensitivity levels based on data volume, not content, and larger datasets are assumed to be more sensitive.
- ▪
The choice of encryption method is dynamically determined by the SDAIPA classification. OHE-WOA is applied only to secret and top-secret records. AES-128 is used for public and confidential data.
All experiments were conducted using MATLAB to evaluate the relative performance of the OHE-WOA enhanced encryption system under controlled conditions. The execution time and energy consumption are linearly proportional to the number of records, reflecting an encryption model per record without batch processing.
6.1. Quantitative Performance Analysis
A comparative analysis of the proposed OHE-WOA compared with AES-128 and RSA-2048 shows the balance between computational efficiency and cryptographic strength in the contribution of the proposed IoMT-based privacy preservation.
Table 8 shows the quantitative analysis results in terms of encryption/decryption times, computation energy, and entropy for datasets in [
52,
53]. The results show that while traditional encryption methods provide high speed and energy efficiency, they are limited in their ability to provide robust privacy for sensitive medical data. The hybrid OHE-WOA approach, despite its computational intensity, offers an unprecedented level of security due to its extremely high entropy.
As shown in
Table 8, the OHE-WOA approach gives execution times of 0.0152 s for encryption and 0.0168 s for decryption, which are significantly higher than AES-128. This gap is due to the nature of FHE, which is due to complex computations of operations such as polynomial arithmetic over large loops, noise management, and smoothing, all of which are absent in traditional block ciphers like AES. Similarly, RSA-2048, with an encryption time of 0.017 s and a decryption time of 0.013 s, performs at a similar latency to OHE-WOA, but for different reasons; its performance bottleneck is with large prime numbers. The proposed approach introduces this additional computational cost but strategically reduces it through the SDAIPA classification model, ensuring that the resource-intensive OHE-WOA is selectively applied only to data classified as secret or top secret, thus maintaining overall system efficiency without compromising critical privacy requirements.
OHE-WOA consumes significantly more energy than AES and RSA. This significant energy cost is due to the large CPU cycles required for FHE computations, which places a high load on wearable devices. However, it offers increased security and reliability for its implementation. By dedicating OHE-WOA to highly sensitive data, the system ensures that the energy cost is justified by the corresponding increase in privacy, in line with the principle of adaptive security. This approach is clearly different from encryption standard strategies, where all data is effectively secured or sensitive information is left vulnerable.
Table 8 also shows the high performance of the proposed approach in the entropy metric. Entropy is a quantitative measure of the randomness and unpredictability of a cryptographic key and is directly related to its resistance to attacks. The OHE-WOA approach achieves an entropy of 4758.56 with dataset 1 in [
52], and 7372.8 for dataset 2 in [
53], compared with 115.2 bits of AES-128 and the 1843.2 bits of RSA-2048. This impressive entropy is due to the use of WOA, which is used to search for the optimal key configuration within the FHE parameter space. The biologically inspired optimization process in WOA maximizes the key entropy, producing significantly more secure encryption than its predecessors. The results show the potential for the benefits of advanced optimization techniques to enhance the security of next-generation cryptographic systems.
The high entropy of OHE-WOA enables completely secure computations on encrypted data, allowing for analysis and processing without revealing the plaintext, especially when used with blockchains, which is a capability not offered by AES and RSA. This validates the fundamental theory that fully symmetric encryption, when optimized and intelligently applied, provides a radical solution for preserving privacy in the IoMT environment.
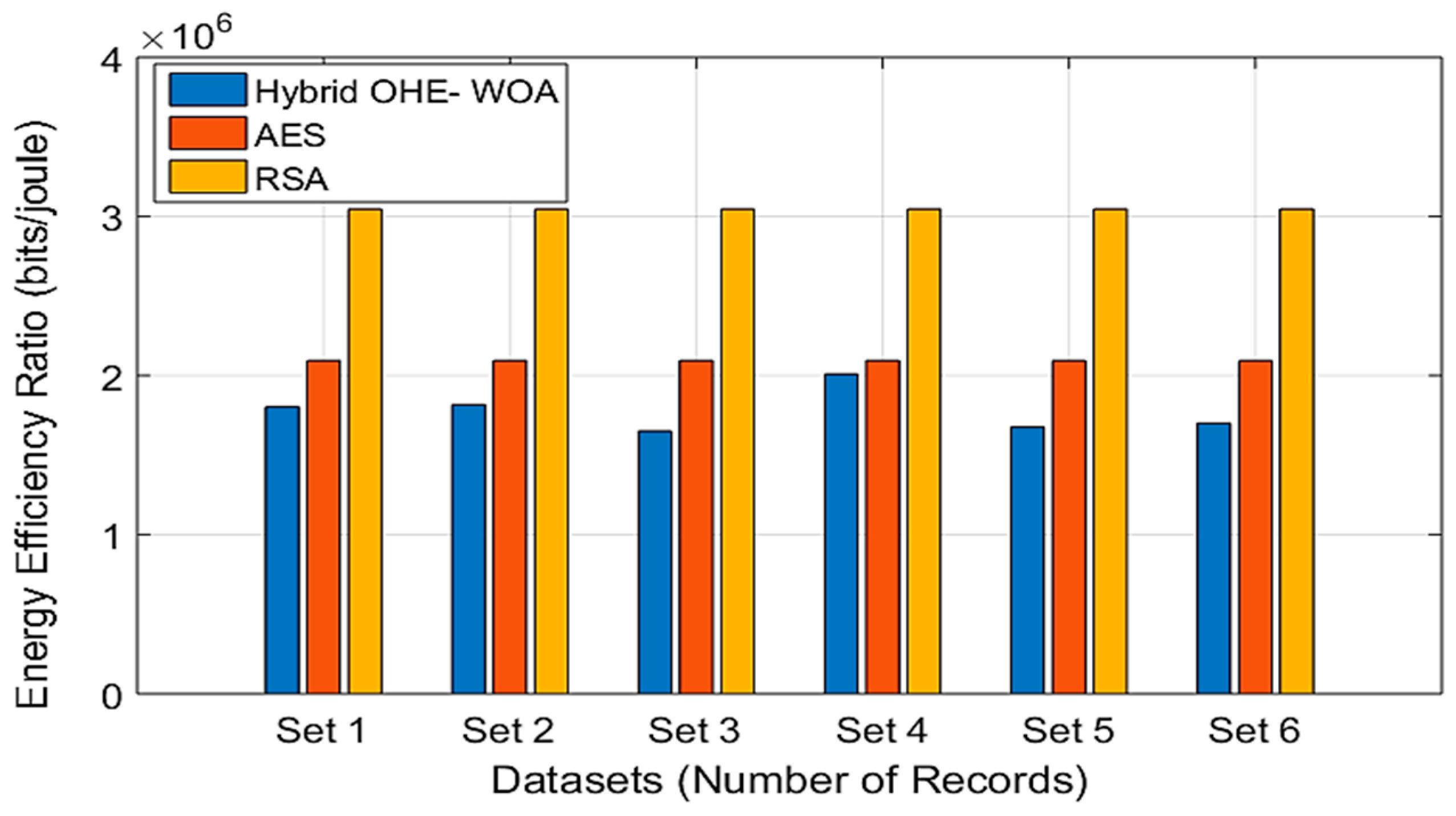
Figure 5 and
Figure 6 show a comparative analysis of the energy efficiency ratio across the two datasets in an IoMT environment [
52,
53]. The EER quantifies the ratio of effective cryptographic strength to the total energy consumed during encryption and decryption. As in
Figure 5, RSA achieves the highest values, reflecting its high entropy; however, its computation time and energy overhead are much higher. AES provides moderate performance, balancing reasonable security with low energy consumption. The Hybrid OHE–WOA model, showing lower values, provides an essential trade-off, delivers enhanced privacy preservation and adaptive key optimization through the WOA, and improves cryptographic robustness without excessive energy expenditure.
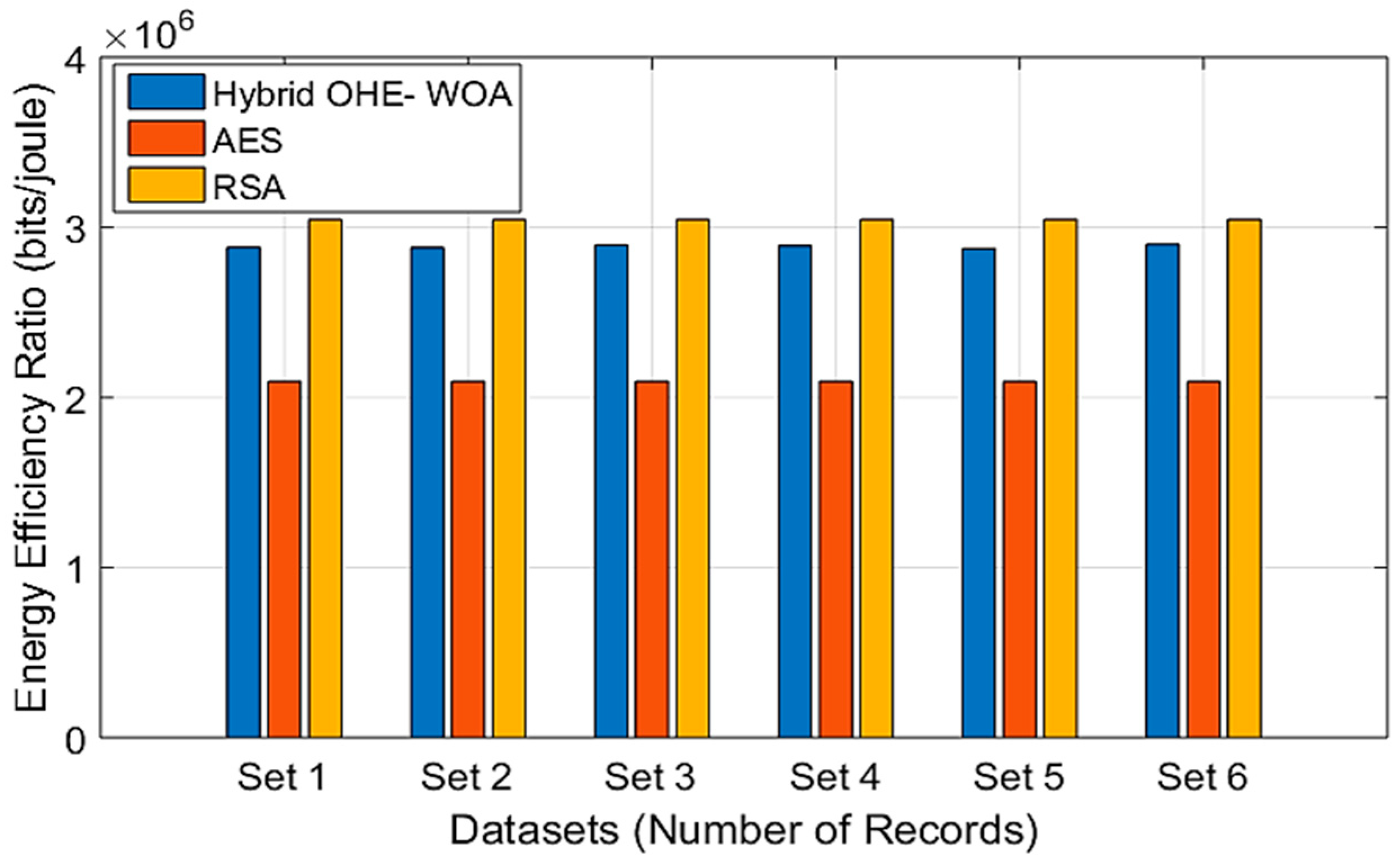
In
Figure 6, RSA still achieves the highest EER values, and AES provides lower values in all sets. The Hybrid OHE–WOA model gives a moderate performance when used with the datasets in [
52,
53]. The OHE-WOA approach has the highest entropy by 7372.8 bits but also the highest energy consumption by 0.0028 J. It gives higher values than AES but lower values than RSA because it relies on maximizing the level of security. This balanced approach confirms that the proposed approach with the IoMT system provides the best balance for privacy-sensitive data. The adaptive SDAIPA model ensures that this balanced encryption is used only in cases where a high level of security is justified, making the system both secure and practical.
The results observed that, while OHE-WOA provides the highest level of privacy through secure computation on encrypted data, its high energy makes it not suitable for all data. To solve this issue, the SDAIPA classification model is used by selecting OHE-WOA for only the most sensitive data classified by secret and top-secret records, while using the more energy-efficient RSA or AES for routine or low-sensitivity data. This strategic allocation ensures that the system maintains overall operational efficiency without compromising the critical protection of patient privacy.
6.2. Comprehensive Privacy-Based Performance
This section presents composite scores that prioritize security and sensitivity. The results of these analyses provide conclusive confirmation of the superiority of the proposed approach used with the IoMT model.
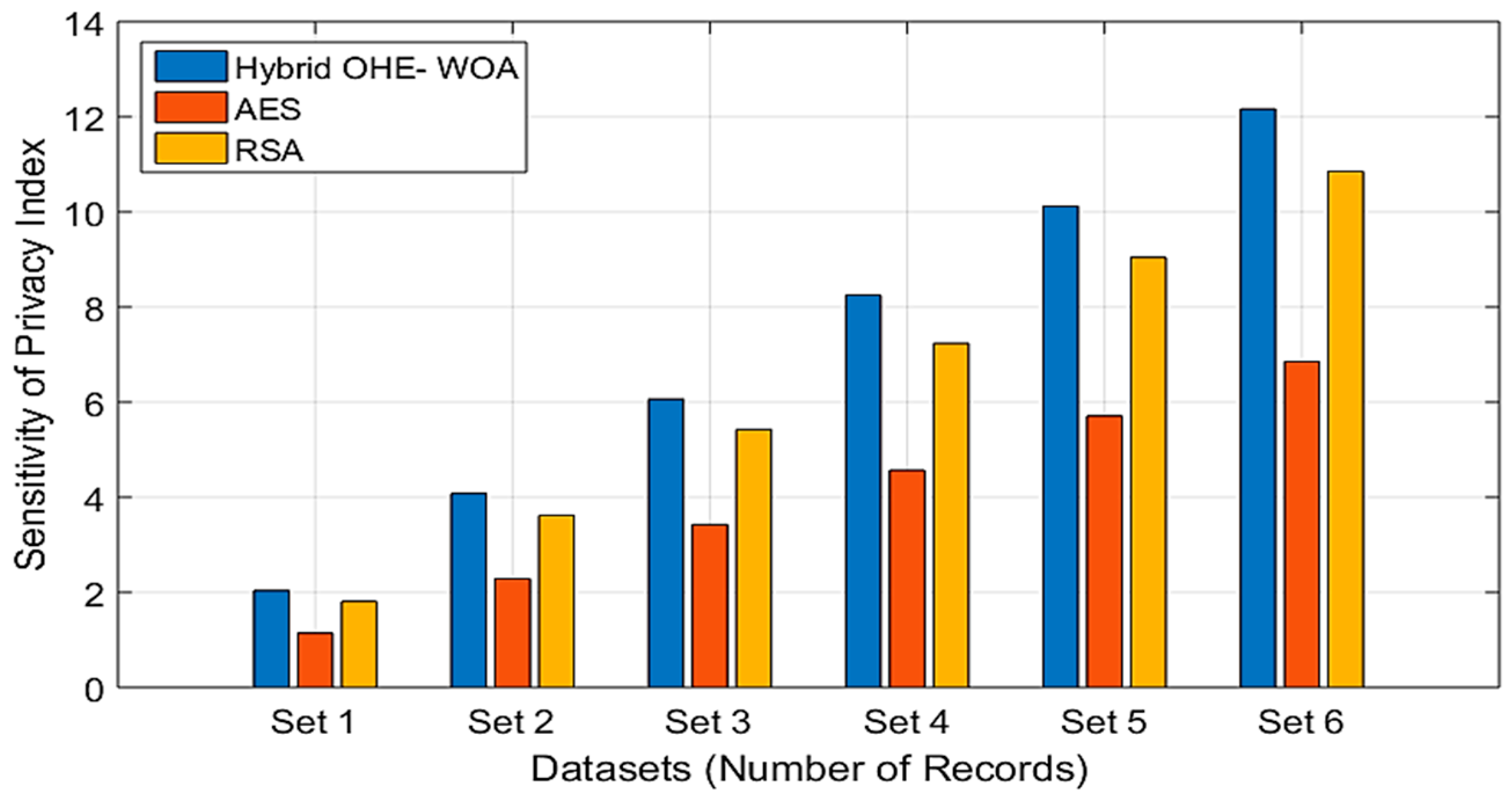
Figure 7 shows the SPI comparison of the proposed approach with AES and RSA algorithms for both datasets, providing a compelling and quantifiable validation of the core contribution of the proposed IoMT model. It reflects the performance of the proposed approaches with six sets, each containing records from the datasets in [
52,
53]. This reflects a scenario of how the proposed approach with an IoMT model handles increasing amounts of patient data over time against an SPI. This formulation explicitly prioritizes privacy by weighting the strength of encryption as entropy against the context of data use.
The performance of the hybrid OHE-WOA approach on two datasets shows close values of SPI, significantly higher than both AES and RSA. For example, in set 6, the largest and most sensitive dataset, the SPI of OHE-WOA rises between 12 and 12.5, while RSA peaks at around 11.0, and AES lags far behind at around 6.8. This trend is a direct result of the adaptive nature of the system. As the dataset grows and the proportion of highly sensitive records increases, the proposed SDAIPA classification model with OHE-WOA can accommodate more data points. Since OHE-WOA has the highest entropy in both datasets, which is significantly higher than the entropy of 115.2 bits of AES or 1843.2 bits of RSA, its SPI increases significantly. The sensitivity weighting further enhances this effect, ensuring the highest level of privacy when needed.
The high SPI of OHE-WOA shows the validity of the proposed approach when using a hybrid adaptive encryption-based IoMT system of FHE-WOA guided by the SDAIPA model. This approach ensures the protection of patient data without compromising the operational efficiency required for real-world deployment in modern healthcare systems.
According to the results obtained, using hybrid data classification before encryption helps improve privacy. Combined with the intelligent, context-aware implementation of FHE using the SDAIPA model, this approach delivers the best possible results. The continuous low SPI scores of AES and RSA are because of the expected outcomes based on their processes. Their primary function is speed and efficiency; they are not for maximizing entropy. The fact that OHE-WOA outperforms them on this particular metric highlights the need for a different paradigm in privacy-critical applications such as healthcare.
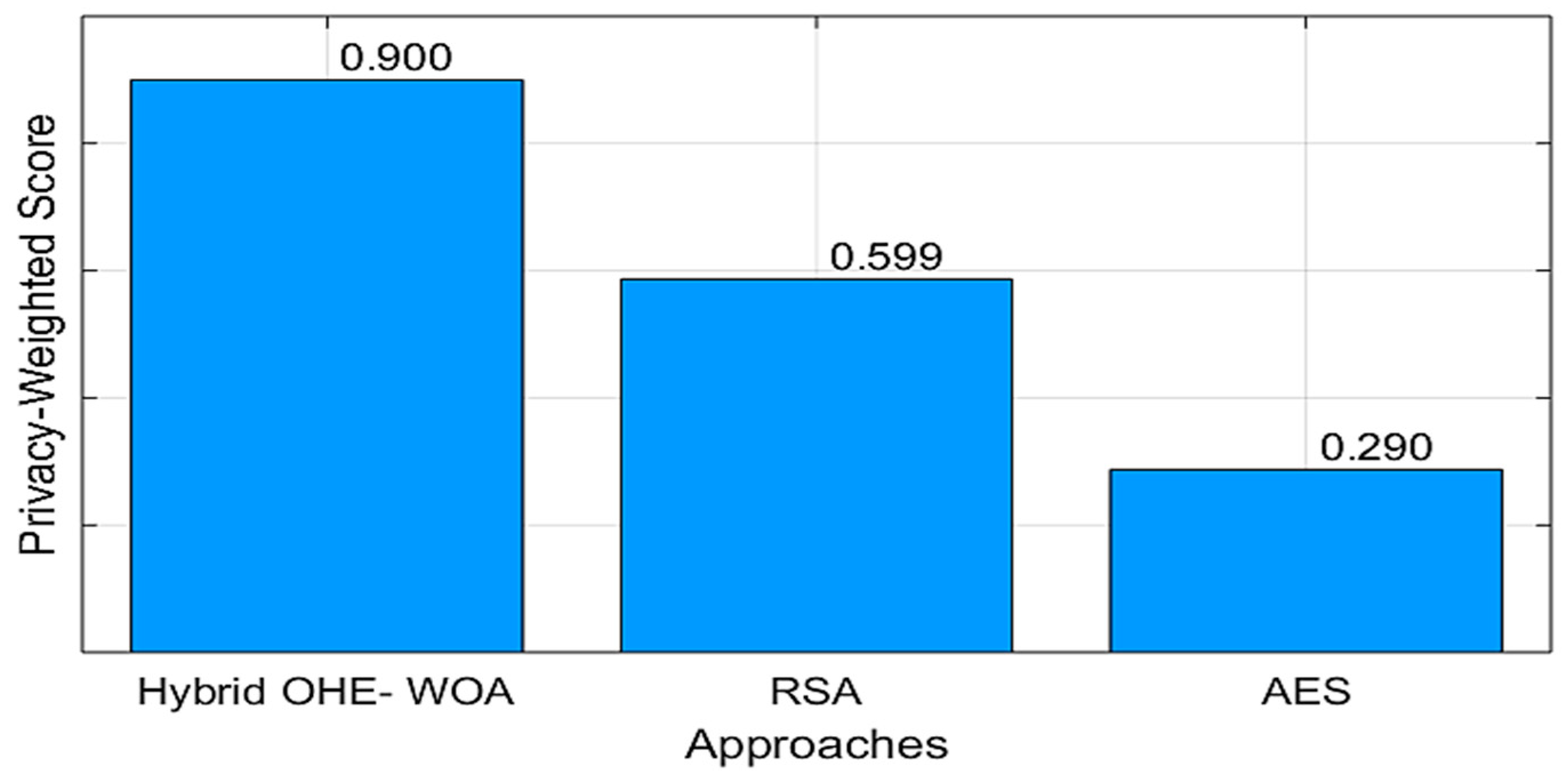
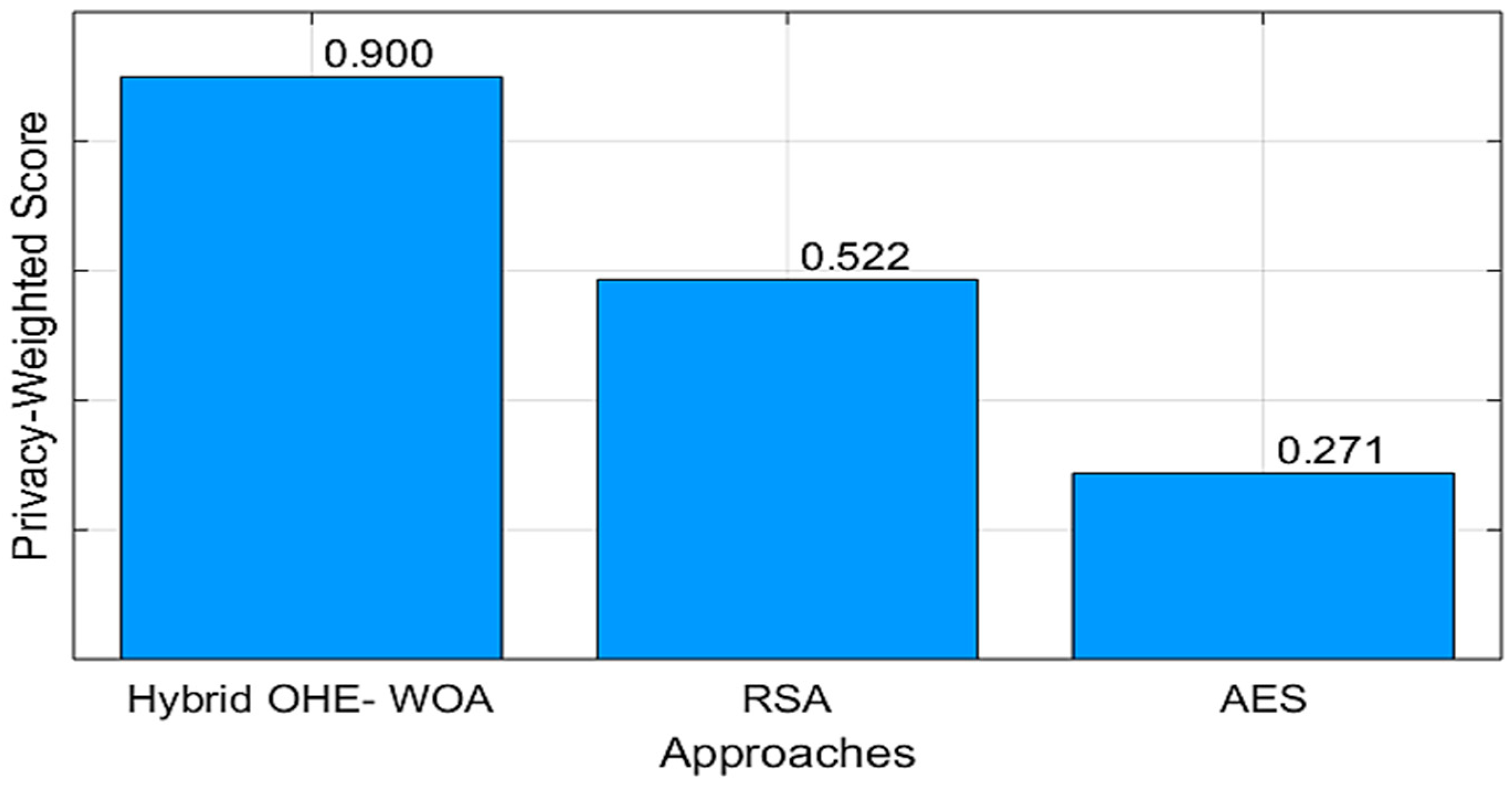
Figure 8 and
Figure 9 show the privacy evaluation for each encryption approach for the two datasets in [
52,
53]. It evaluates the entire performance in a single metric that reflects the priority of patient privacy. The results show that the hybrid OHE-WOA approach provides the optimal solution for securing sensitive medical data in medical datasets. The weighted privacy score is a composite measure that reflects the true value of an encryption system in the context of a privacy-focused healthcare system. It reflects a weighted and standardized average of the key performance indicators discussed throughout the study, with a strong focus on entropy and the SPI, as these are the key measures of encryption strength and privacy protection.
The results show that the hybrid OHE-WOA approach outperforms the other approaches by achieving a high score of 0.900 with the two datasets. This result reflects the capabilities of its underlying architecture, which consists of FHE enhanced by the WOA optimization algorithm. With an entropy of 4758.56 and 7372.8 for the two datasets, respectively, this is significantly higher than the 115.2 bits in AES or the 1843.2 bits in RSA. This high entropy translates to increased data confidentiality, and with the high score, they reflect the adaptive nature of the IoMT system with the proposed approach. By applying OHE-WOA only to data classified as secret/top secret via the SDAIPA model, the system ensures that its maximum security potential is achieved when needed.
The low scores of the two datasets for RSA (0.559, 0.522) and AES (0.290, 0.273) are due to their focus on efficiency and speed, and they are weak in providing maximum entropy. The proposed approach was compared to showcasing the inherent contradictions in any secure IoMT system. AES, with its low computational costs, is ideal for low-sensitivity data, while RSA offers a compromise. However, neither can match the privacy provided by FHE. It also shows that the proposed system promises improved privacy and high performance of the entire IoMT model for protecting patient data.
Table 9 shows the privacy performance of the OHE-WOA framework across the two datasets. Dataset 1 shows a slightly higher privacy level than dataset 2, which indicates a slightly higher level of sensitivity-weighted cryptographic entropy, but dataset 2 achieves a significantly higher privacy value. This contrast highlights a key strength of the privacy value metric, as it comprehensively integrates privacy and encryption ability with energy efficiency, while the privacy level only reflects the sensitivity rate entropy metric. The higher privacy value for dataset 2 indicates that, regardless of its slightly lower SPI index, the OHE-WOA optimization provides a significantly greater encryption strength with comparable energy efficiency, leading to a more robust overall privacy protection configuration.
Dataset 1 is collected from a maternal health risk context with features such as blood pressure, body temperature, and blood sugar, and the SDAIPA model likely assigned higher sensitivity weights to these features, hence its higher privacy level. In contrast, dataset 2, comprising physiological and system-level metrics such as signal reliability, respiration rate, and oxygen saturation, may have lower sensitivity per record but allows for more effective optimization of encryption and energy parameters by OHE-WOA, resulting in superior composite privacy performance.
Accordingly, the results show that maximizing the raw privacy level alone is insufficient, since the multi-objective normalized privacy value provides a more comprehensive and applicable assessment of privacy protection effectiveness. While the use of OHE-WOA with dataset 1 gives a higher SPI, with dataset 2, it achieves a higher privacy value due to the OHE-WOA converging to a higher-entropy solution. In dataset 2, the higher privacy value is possibly due to smoother gradients in its continuous feature space, which enables more effective WOA optimization. Moreover, the lower energy consumption during encryption/decryption for dataset 2 is due to simpler data structures or fewer high-risk records requiring intensive anonymization. Therefore, the high sensitivity of dataset 1 requires strict transformations to protect privacy, which increases computational burden and energy consumption. Dataset 2 has lower per-record sensitivity, allowing OHE-WOA to prioritize cryptographic robustness and energy efficiency. Based on the overall results, the OHE-WOA approach shows adaptability to different datasets, improving the Pareto front between privacy, security, and energy efficiency based on the constraints of each dataset.
6.3. Observations and Limitations
The evaluation results discussed the proposed approach performance and show how the proposed IoMT cryptographic model overcomes the traditional balance between privacy and performance in IoMT environments. Given the primary challenge of traditional cryptographic methods being too weak for sensitive data, the results demonstrate that this challenge can only be mitigated by implementing a context-aware intelligent system.
The SDAIPA classification model acts as a strategic filter, ensuring that the high-cost OHE-WOA system, which features significantly higher encryption/decryption time, and energy consumption with 0.0028 joules can be applied exclusively to data classified as secret or top secret. This selective implementation prevents the system from being subjected to significant computational stress while providing an unprecedented level of security, as shown by the OHE-WOA algorithm’s superior entropy value of 7372.8 bits. This entropy enables completely secure computation of encrypted data as a critical feature for cloud analytics without compromising patient confidentiality.
Furthermore, the WOA addresses the challenge of suboptimal key generation by actively searching for the strongest possible encryption keys, enhancing the effectiveness of the FHE process. Composite metrics such as the EER and PWS show that this hybrid approach delivers superior overall value. By prioritizing privacy for high-risk data and efficiency for routine monitoring, the proposed framework successfully addresses the central challenge of the IoMT for healthcare.
Although the proposed approach presents a robust strategy for preserving privacy in healthcare systems, it inherently faces challenges due to its reliance on advanced, computationally intensive technologies. The most significant challenge is the high computational cost of FHE. As shown in the performance evaluation, the hybrid OHE-WOA approach shows an encryption time of 0.015 s and a decryption time of 0.016 s, both significantly higher than AES. This high latency is directly attributed to the complex polynomial calculations and noise management operations in FHE, which pose a challenge in applications with limited processing energy and resources. However, the SDAIPA classification model mitigates the energy load by selectively applying OHE-WOA to highly sensitive data.
Secondly, there are issues related to the complexity and scalability. The proposed approach with the IoMT system integrates the permissioned blockchain with off-chain storage, which increases the complexity of the system. To reduce the system complexity, a multi-layered infrastructure requires specific coordination between the classification engine, the FHE optimization process, and the blockchain network. By using a permissioned blockchain with enhanced security through access control, it increases the load on consensus mechanisms, potentially impacting transaction throughput and system responsiveness. Furthermore, the use of IPFS for off-chain storage, while beneficial for scalability, adds another layer of complexity in terms of data retrieval, consistency, and network reliability.
Finally, the real-world validation of the proposed approach with the IoMT system may face computational power challenges, as the current evaluation relies on simulations. The benefits of using WOA to find the key with maximum entropy under real-time hardware constraints and network conditions may also face some limitations. The dynamic nature of the IoMT system in fluctuating network connectivity with varying device capabilities and unpredictable data loads can impact the performance of both OHE-WOA operations and blockchain parameters.