A Control Framework for a Secure Internet of Things within Small-, Medium-, and Micro-Sized Enterprises in a Developing Economy
Abstract
1. Introduction
2. Background to the Study
3. Problem Statement
4. Research Question, Aim, and Objectives
- What are the challenges with IoT adoption in SMEs?
- Develop a control framework that uses the IoT to address security challenges for SMEs in a developing economy (aim).
- Identify IoT-related aspects that ought to be included in a control framework for SME IoT security (Obj1);
- Identify some of the existing IoT frameworks (Obj2).
5. Literature Review
5.1. The Common Definitions of IoT
- The IoT is a collection of physical items that are connected to a network and incorporated with sensors or actuators. Additionally, because the IoT creates advantageous network externalities, broad government use will encourage business adoption [23];
- The platform, which incorporates the shared resources used by ecosystem participants, is the central component of the IoT. An IoT platform’s success depends on the existence of a business ecosystem of organisations where the purchasers, suppliers, and producers of related goods and services, as well as their socioeconomic environment, collectively offer a range of IoT end-user applications, goods, and services [24];
- The “things” are designed to communicate with others, mostly through sensors, systems, and devices (these can be appliances, electronics devices, and cars) [6].
5.2. Why SMEs Need Digitalisation Systems such as the IoT
5.3. The Challenges of SMEs That Have already Embarked Unsuccessfully on the Use of the IoT
5.3.1. Perceived Value of Data
5.3.2. Data Quality and Access
5.3.3. Internet Access
5.4. Challenges for SMEs Entering the IoT World
5.5. Challenges of the IoT in SMEs
Probable IoT Challenges
5.6. Security Challenges in the IoT
5.6.1. Communication Challenges in the IoT
5.6.2. IoT Security Threats
5.6.3. IoT Systems and Supply Chain
5.6.4. Smart SMEs and Security
5.6.5. Cyber Security, Intellectual Property, and Sensitive Information
5.6.6. Challenges in Securing IoT Products
5.7. Managerial, Financial, Legal, Labour, and Environmental IoT Challenges in SMEs
5.7.1. Financial Instability (FiS)
5.7.2. Financial Loans (FL)
5.7.3. Managerial Inexperience (MiE)
5.7.4. Lack of Innovation Performance (LIP)
5.7.5. Regulatory Licenses and Taxes (RLT)
5.7.6. Competitive Environment (CE)
5.7.7. Increased Production Cost (IPC)
5.7.8. Rights of Employees (ER)
5.8. SME Requirements
5.8.1. Transforming the Customer–Provider Relationship
5.8.2. Technical Skills Needed in the IoT World
5.8.3. Understanding the Ecosystem around IoT Products
5.9. The IoT in Manufacturing SMEs
5.10. Training within SMEs
5.11. Supporting South African SMEs
5.12. The Need for Supporting Institutions’ Services
5.13. Existing IoT Frameworks for SMEs
5.13.1. IoT Framework for Rapid Integration of IoT Systems in SMEs
5.13.2. Track-and-Trace Supply Chain Conceptual Framework for the IoT in SMEs
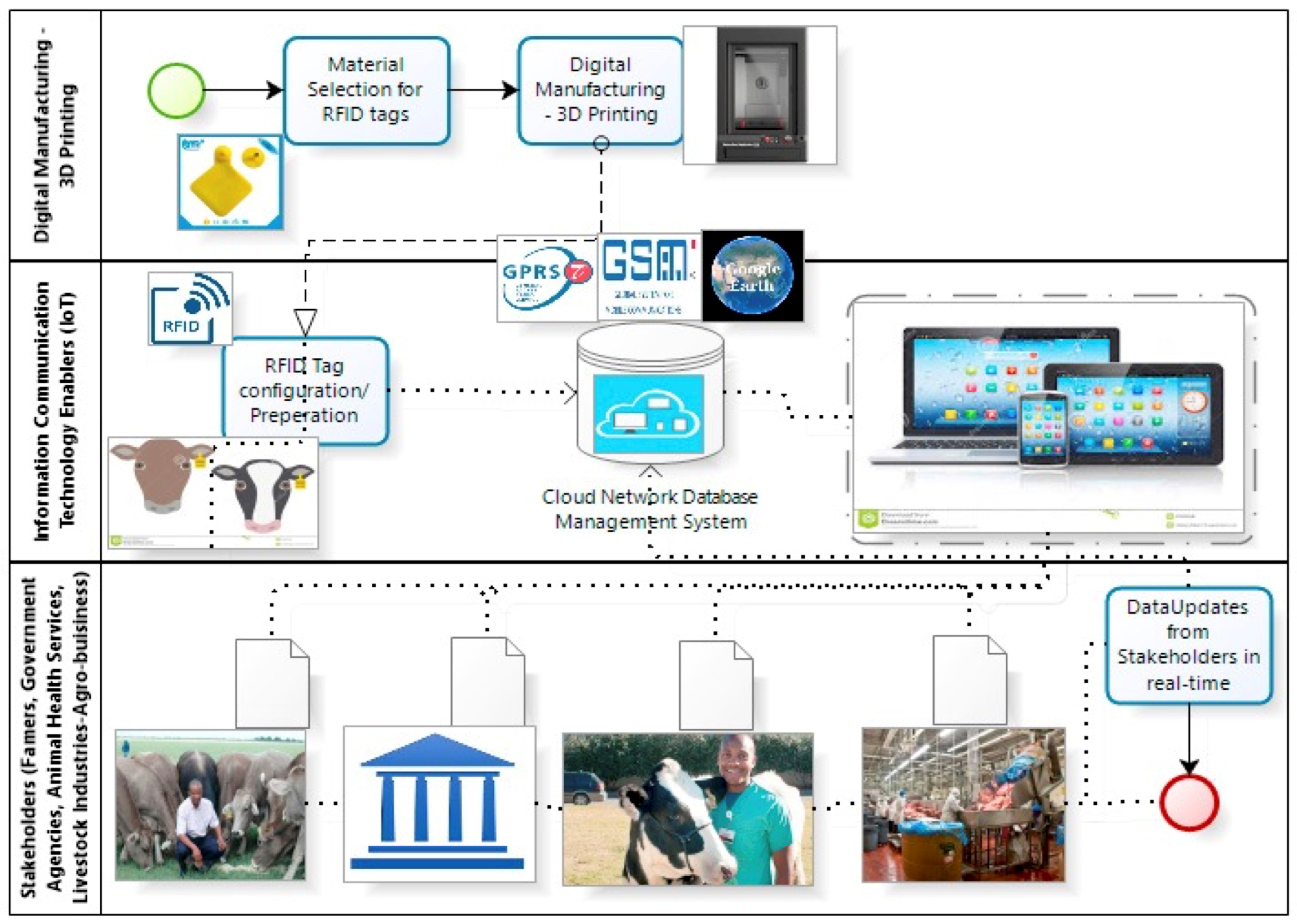
5.13.3. IoT Conceptual Framework in Agriculture (SME) for an Advanced Animal Track-and-Trace Business Process Model (BPM)
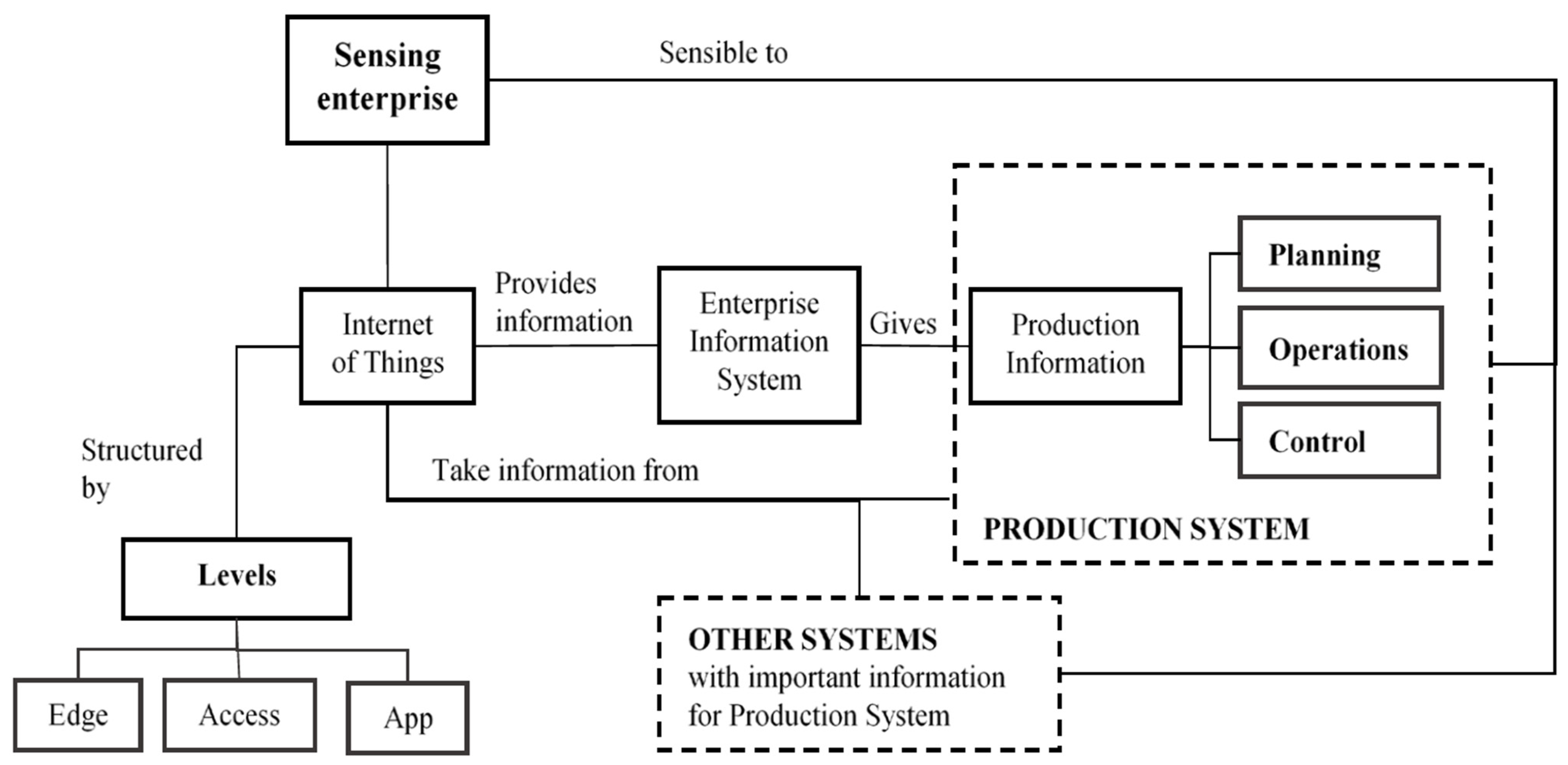
5.13.4. Existing IoT Conceptual Framework in Production Systems
6. Data Collection
7. Materials and Methods
Research Methodology
8. Results
9. Discussion
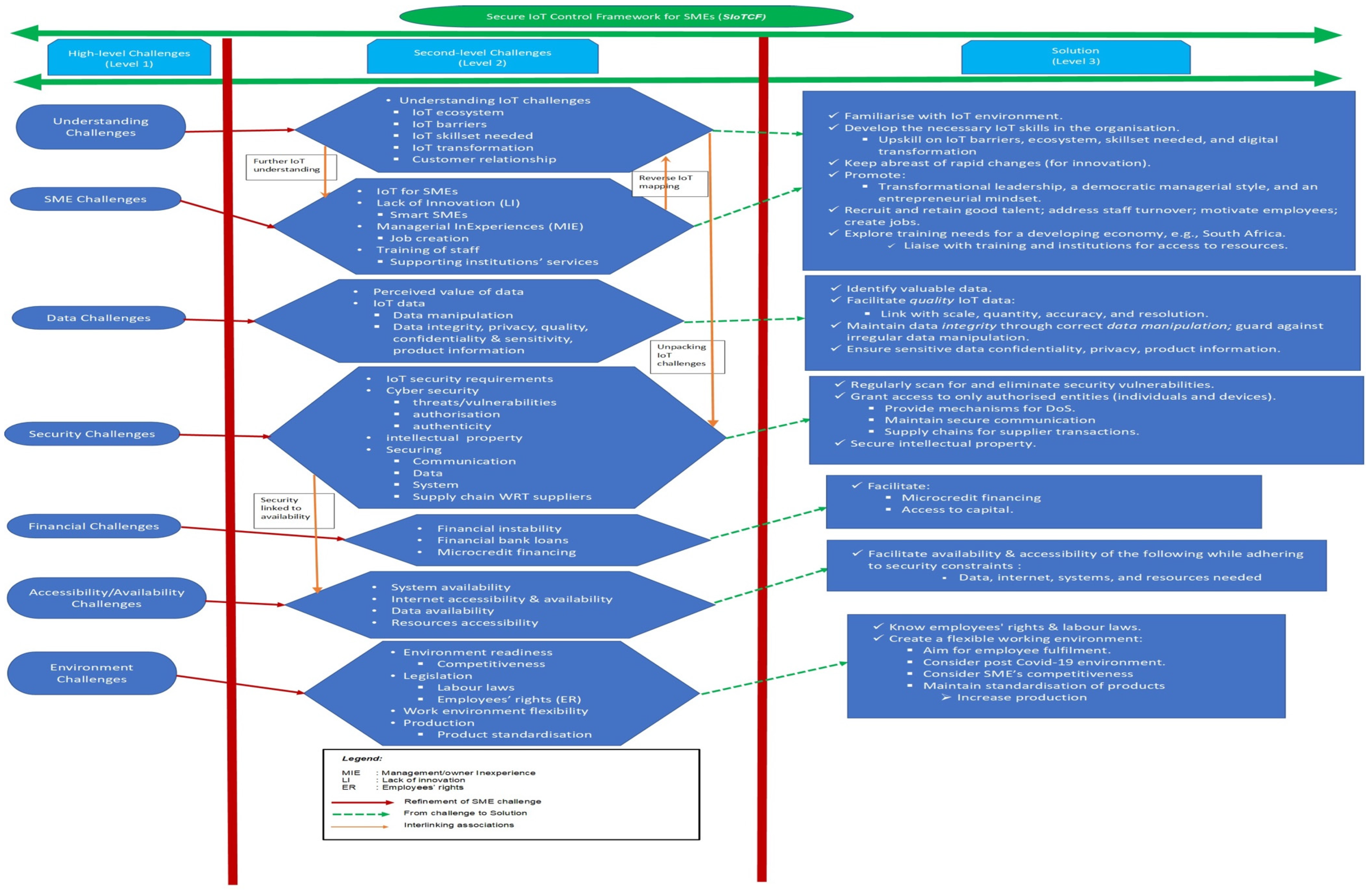
10. Contributions of the Research
11. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Gartner Says 6.4 Billion Connected “Things” Will Be in Use in 2016, Up 30 Percent From 2015. Available online: http://www.gartner.com/newsroom/id/3165317 (accessed on 7 October 2021).
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of things (IoT): Avision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Tobias, R.J. Wireless communication of real-time ultrasound data and control. SPIE Med. Imaging Int. Soc. Opt. Photonics 2015, 9419, 120–128. [Google Scholar]
- Anuar, A.R.; Mansor, W.N.J.W.; Din, B. Cabaran Meningkatkan Produktiviti Syarikat Berskala Kecil dan Sederhana di Malaysia: Kajian Mengenai isu Kemahiran Buruh. Malays. J. Soc. Space 2016, 12, 26–33. Available online: http://www.ukm.my/geografia/images/upload/3x.geografia-mac16-abdulrahim-edam.pdf (accessed on 14 May 2022).
- Islam, A.; Wahab, S.A.; Latiff, A.S.A. Annexing a smart sustainable business growth model for small and medium enterprises (SMEs). World J. Entrep. Manag. Sustain. Dev. 2022, 18, 1–24. [Google Scholar] [CrossRef]
- Lu, Y.; Cecil, J. An Internet of Things (IoT)-based collaborative framework for advanced manufacturing. Int. J. Adv. Manuf. Technol. 2016, 84, 1141–1152. [Google Scholar] [CrossRef]
- Sandu, R. An analysis of SMEs customer behavior in cloud-based e-commerce environment. Acad. J. Sci. 2017, 7, 281–292. [Google Scholar]
- Sicari, S.; Rizzardi, A.; Grieco, L.; CoenPorisini, A. Security, privacy and trust in internet of things: The road ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Liu, J.; Sun, W. Smart attacks against intelligent wearables in people-centric Internet of Things. IEEE Commun. Mag. 2016, 54, 44–49. [Google Scholar] [CrossRef]
- Hinks, J. 5 Things You Should Know about Industry 4.0. Tecradar.Pro. IT Insights for Business. 2015. Available online: http://www.techradar.com/news/world-of-tech/future-tech/5-things-you-should-know-about-industry-4-0-1289534 (accessed on 1 May 2022).
- Liebi, M. Industry 4.0 and the Impact on Cybersecurity. United Security Providers. 2016. Available online: https://www.united-security-providers.com/blog/industry-4-0-and-the-impact-on-cybersecurity/ (accessed on 1 May 2022).
- DiMaggio. The Black Vine Cyberespionage Group. Symantec. 2015. Available online: http://www.symantec.com/content/en/us/enterprise/media/security_response/whitepapers/the-black-vine-cyberespionage-group.pdf (accessed on 5 June 2022).
- Abazi, B. An Approach to the Impact of Transformation from the Traditional Use of ICT to the Internet of Things: How Smart Solutions Can Transform SMEs. IFAC-PapersOnLine 2016, 49, 148–151. Available online: https://doi.org/10.1016/j.ifacol.2016.11.091 (accessed on 5 June 2020). [CrossRef]
- Singh, J.; Pasquier, T.; Bacon, J.; Ko, H.; Eyers, D. Twenty security considerations for cloud-supported internet of things. IEEE Internet Things J. 2016, 3, 269–284. [Google Scholar] [CrossRef]
- Zanella, A. Internet of Things for Smart Cities. IEEE Internet Things 2014, 1, 1. [Google Scholar] [CrossRef]
- Alur, R.; Berger, E.; Drobnis, A.W.; Fix, L.; Fu, K.; Hager, G.D.; Lopresti, D.; Nahrstedt, K.; Mynatt, E.; Patel, S.; et al. Systems Computing Challenges in the Internet of Things. arXiv 2016, arXiv:1604.02980. [Google Scholar]
- Verdouw, C.; Vucic, N.; Sundmaeker, H.; Beulens, A. Future internet as adriver for virtualisation, connectivity and intelligence of agri-food supply chain networks. Int. J. Food Syst. Dyn. 2013, 4, 261–272. [Google Scholar]
- Borgia, E. The internet of things vision: Key features, applications and open issues. Comput. Commun. 2014, 54, 1–31. [Google Scholar] [CrossRef]
- Whitmore, A.; Agarwal, A.; Da Xu, L. The internet of things—A survey of topics and trends. Inf. Syst. Front. 2015, 17, 261–274. [Google Scholar] [CrossRef]
- Castro, D.; New, J. Everything the US Government is Doing to Help the Private Sector Build. The Internet of Things. 2016. Available online: http://www2.datainnovation.org/2016-federal-support-iot.pdf (accessed on 29 April 2022).
- Mineraud, J.; Mazhelis, O.; Su, X.; Tarkoma, S. A gap analysis of internet-ofthings platforms. Comput. Commun. 2016, 89, 5–16. [Google Scholar] [CrossRef]
- World Trade Organization. Levelling the Trading Field for SMEs (pp. 1–177). Geneva: WTO. 2016. Available online: https://www.wto.org/english/res_e/publications_e/wtr16_e.htm (accessed on 28 May 2022).
- World Bank. Improving SMEs’ Access to Finance and Finding Innovative Solutions to Unlock Sources of Capital. Geneva: WB. 2018. Available online: https://www.worldbank.org/en/topic/smefinance (accessed on 28 August 2021).
- Rotar, L.J.; Pamić, R.K.; Bojnec, Š. Contributions of small and medium enterprises to employment in the European Union countries. Econ. Res.-Ekon. Istraživanja 2019, 32, 3302–3314. [Google Scholar] [CrossRef]
- Cass, S. A chip to protect the internet of things [Resources_Beyond the datasheet]. IEEE Spectr. 2017, 54, 1–7. [Google Scholar] [CrossRef]
- Hossain, M.; Hasan, R.; Skjellum, A. Securing the internet of things: A meta study of challenges, approaches, and open problems. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems Workshops, Atlanta, GA, USA, 5–8 June 2017; pp. 220–225. [Google Scholar]
- Bello, O.; Zeadally, S. Intelligent device-to-device communication in the internet of things. IEEE Syst. J. 2016, 10, 1172–1182. [Google Scholar] [CrossRef]
- Bröring, A.; Schmid, S.; Schindhelm, C.K.; Khelil, A.; Käbisch, S.; Kramer, D.; Le Phuoc, D.; Mitic, J.; Anicic, D.; Teniente, E.; et al. Enabling IoT ecosystems through platform interoperability. IEEE Softw. 2017, 34, 54–61. [Google Scholar] [CrossRef]
- George, G.; Merrill, R.K.; Schillebeeckx, S.J. Digital sustainability and entrepreneurship: How digital innovations are helping tackle climate change and sustainable development. Entrep. Theory Pract. 2020, 45, 999–1027. [Google Scholar] [CrossRef]
- Ross, J.W.; Beath, C.M.; Sebastian, I.M. How to develop a great digital strategy. MIT Sloan Manag. Rev. 2017, 58, 7–9. [Google Scholar]
- Kane, G.C.; Phillips, A.N.; Copulsky, J.; Andrus, G. How digital leadership is (n’t) different. MIT Sloan Manag. Rev. 2019, 60, 34–39. [Google Scholar]
- Caputo, F.; Cillo, V.; Candelo, E.; Liu, Y. Innovating through digital revolution: The role of soft skills and Big Data in increasing firm performance. Manag. Decis. 2019, 58, 2032–2051. [Google Scholar] [CrossRef]
- De Haes, S.; Van Grembergen, W. Analysing the impact of enterprise governance of IT practices on business performance. Int. J. IT/Bus. Alignment Gov. (IJITBAG) 2010, 1, 14–38. [Google Scholar] [CrossRef]
- Bruins, T.E.; van Veen, M.M.; Werker, P.M.; Dijkstra, P.U.; Broekstra, D.C. Associations between clinician-graded facial function and patient-reported quality of life in adults with peripheral facial palsy: A systematic review and meta-analysis. JAMA Otolaryngol.-Head Neck Surg. 2021, 147, 717–728. [Google Scholar] [CrossRef]
- Metcalf, L.; Benn, S. Leadership for sustainability: An evolution of leadership ability. J. Bus. Ethics 2013, 112, 369–384. [Google Scholar] [CrossRef]
- Bharadwaj, A.; El Sawy, O.A.; Pavlou, P.A.; Venkatraman, N. Digital business strategy: Toward a next generation of insights. MIS Q. 2013, 37, 471–482. [Google Scholar] [CrossRef]
- Fitzgerald, M.; Kruschwitz, N.; Bonnet, D.; Welch, M. Embracing digital technology: A new strategic imperative. MIT Sloan Manag. Rev. 2014, 55, 1–16. [Google Scholar]
- Khin, S.; Ho, T.C. Digital technology, digital capability and organisational performance. Int. J. Innov. Sci. 2019, 11, 177–195. [Google Scholar] [CrossRef]
- Bughin, J. The best response to digital disruption. MIT Sloan Manag. Rev. 2017, 58, 80–86. [Google Scholar]
- IDC. Worldwide Spending on Digital Transformation. Framingham: IDC Corp USA. 2019. Available online: https://www.idc.com/getdoc.jsp?containerId=prUS45612419 (accessed on 12 April 2021).
- OECD. The OECD Digital for SMEs Global Initiative: Harnessing the Digital Revolution for SMEs and Entrepreneurs. Paris, France: Author. 2019. Available online: https://www.oecd.org/cfe/smes/digital-smes.htm (accessed on 12 April 2021).
- Hori, M.; Kawashima, E.; Yamazaki, T. Application of cloud computing to agriculture and prospects in other fields. Fujitsu Sci. Tech. J. 2010, 46, 446–454. [Google Scholar]
- Bossen, H.; Ingemansson, J. Digitalisering Avsvensk Industri—Kartläggning av Svenska Styrkor Ochutmaningar (Digitalization of Swedish Industry—Inventory of Swedish Strenghts and Challenges. In Swedish), Swedish Governmental Agency for Innovation Systems, 2016. Available online: http://www2.vinnova.se/sv/Aktuellt--publicerat/Publikationer/Produkter/Digitalisering-avsvensk-industri/ (accessed on 1 May 2022).
- Van Kranenburg, R.; Bassi, A. IoT challenges. Commun. Mob. Comput. 2012, 1, 9. [Google Scholar] [CrossRef]
- Ben-Daya, M.; Hassini, E.; Bahroun, Z. Internet of Things and Supply Chainmanagement: A Literature Review. Int. J. Prod. Res. 2017. [Google Scholar] [CrossRef]
- Liu, J.; Tao, J.P. Research and application of agricultural greenhouse intelligence platform based on IoT (Internet of Things) and cloud computing. Int. J. Simul. Syst. Sci. Technol. 2016, 17, 58–67. [Google Scholar]
- Vermesan, O.; Friess, P. Internet of Things: Converging Technologies for Smart Environments and Integrated Ecosystems; River Publishers Series in Communications: London, UK, 2013. [Google Scholar]
- Holm, C.; Stenstrand, M. Digital Disconnect: Plugging into Disruption in Sweden, Accenture High Performance Business Forum Point of View January 2015, Accenture, 2015; p. 1. Available online: https://doi.org/10.1145/3131542.3131547 (accessed on 10 March 2020).
- Bi, Z.; Xu, L.; Wang, L.C. Internet of things for enterprise systems of modernmanufacturing. IEEE Trans. Ind. Inform. 2014, 10, 1537–1546. [Google Scholar]
- Lee, I.; Lee, K. The Internet of Things (IoT): Applications, investments and challenges for enterprises. Bus. Horiz. 2015, 58, 431–440. [Google Scholar] [CrossRef]
- Mohd Selamat, S.A.; Prakoonwit, S.; Sahandi, R.; Khan, W.; Ramachandran, M. Big data analytics—A review of data-mining models for small and medium enterprises in the transportation sector. Wiley Interdiscip. Rev. Data Min. Knowl. Discov. 2018, 8, e1238. [Google Scholar] [CrossRef]
- CTIA. Mobile Cybersecurity and the Internet of Things; CTIA: Washington, DC, USA, 2015. [Google Scholar]
- Nasser, J. Cyber physical systems in the context of Industry 4.0. In Proceedings of the 2014 IEEE International Conference on Automation, Quality and Testing, Robotics, Cluj-Napoca, Romania, 22–24 May 2014. [Google Scholar]
- Pereira, T.; Barreto, L.; Amaral, A. Network and information security challenges within Industry 4.0 paradigm. Procedia Manuf. 2017, 13, 1253–1260. [Google Scholar] [CrossRef]
- Geissbauer, R.; Vedso, J.; Schrauf, S. Industry 4.0: Building the Digital Enterprise [Online]. 2016. Available online: https://www.pwc.com/gx/en/industries/industries-4.0/landing-page/industry-4.0-building-your-digital-enterprise-april-2016.pdf (accessed on 27 May 2020).
- Gilchrist, A. Industry 4.0—The Industrial Internet of Things; Springer: New York, NY, USA, 2016. [Google Scholar]
- Koch, V.; Kuge, S.; Geissbauer, R.; Schrauf, S. Industry 4.0: Opportunities and Challenges of the Industrial Internet. 2014. Available online: http://www.strategyand.pwc.com/reports/industry-4-0 (accessed on 18 May 2022).
- Tavana, M.; Puranam, K. Handbook of Research on Cloud Infrastructures for Big Data Analytics. In Handbook of Research on Organizational Transformations through Big Data Analytics; IGI Global: Hershey, PA, USA, 2014. [Google Scholar]
- Tao, F.; Zuo, Y.; Da Xu, L.; Zhang, L. IoT-based intelligent perception and access of manufacturing resource toward cloud manufacturing. IEEE Trans. Ind. Inform. 2014, 10, 1547–1557. [Google Scholar]
- Andalib, T.W.; Halim, H.A. Convergence of conceptual innovation model to reduce challenges faced by the small and medium sized enterprises’ (SMEs) in Bangladesh. J. Open Innov. Technol. Mark. Complex. 2019, 5, 63. [Google Scholar] [CrossRef]
- Baron, R.; Scott, S. Entrepreneurship: A Process Perspective; Nelson Education: Scarborough, ON, Canada, 2007. [Google Scholar]
- Hoque, A.S.M.M.; Awang, Z.; Salam, S. The Effects of Relationship Marketing on Firm Performance: Small and Medium Enterprises (SMEs) in Bangladesh. In Proceedings of the 1st International Conference on Business and Management (ICBM-2017), BRAC Business School (BBS), BRAC University, Dhaka, Bangladesh, 21–22 September 2017. [Google Scholar]
- Hillary, R. Small and Medium-Sized Enterprises and the Environment: Business Imperatives; Routledge: London, UK, 2017; ISBN 9781351282840. [Google Scholar]
- Omerzel, D.G.; Antoncic, B. Critical entrepreneur knowledge dimensions for the SME performance. Ind. Manag. Data Syst. 2008, 108, 1182–1199. [Google Scholar] [CrossRef]
- Rahman, M.N. The Challenges and Barriers Faced by SME Entrepreneurs: A Study on Bangladesh SME Sector. Available online: https://www.researchgate.net/publication/332471475_The_Challenges_and_Barriers_Faced_by_SME_Entrepreneurs_A_Study_on_Bangladesh_SME_Sector (accessed on 28 May 2022).
- Idar, R.; Mahmood, R. Entrepreneurial and Marketing Orientation Relationship to Performance: The SME Perspectives. Interdiscip. Rev. Econ. Manag. 2011, 1, 1–8. [Google Scholar]
- Fumo, N.D.G.; Jabbour, C.J.C. Barriers faced by MSEs: Evidence from Mozambique. Ind. Manag. Data Syst. 2011, 111, 849–868. [Google Scholar] [CrossRef]
- Mahmood, M. Labour productivity and employment in Australian manufacturing SMEs. Int. Entrep. Manag. J. 2008, 4, 51–62. [Google Scholar] [CrossRef]
- Jahur, M.S.; Azad, A.S. A study on small business enterprises in Bangladesh: Searching for growth factors and obstacles. J. Inst. Bank. Bangladesh 2004, 51, 73–89. [Google Scholar]
- Mutula, S.M.; Van Brakel, P. ICT Skills Readiness for the Emerging Global Digital Economy among Small Businesses in Developing Countries: Case Study of Botswana. Libr. HiTech 2016, 25, 231–245. [Google Scholar] [CrossRef]
- Uddin, R.; Bose, T.K. Factors a ect the success of SME in Bangladesh: Evidence from Khulna City. J. Manag. Sustain. 2013, 3, 166. [Google Scholar]
- Martinsons, M.G. Relationship-based e-commerce: Theory and evidence from China. Inf. Syst. J. 2008, 18, 331–356. [Google Scholar] [CrossRef]
- Skarzynski, P.; Gibson, R. Innovation to the Core: A Blueprint for Transforming the Way Your Company Innovates; Harvard Business School Press: Boston, MA, USA, 2008. [Google Scholar]
- Okpara, J. Factors constraining the growth and survival of SMEs in Nigeria Implications for poverty alleviation. Manag. Res. Rev. 2011, 34, 156–171. [Google Scholar] [CrossRef]
- Zaman, K.; Qureshi, M.; Bhatti, M. The impact of culture and gender on leadership behavior: Higher education and management. Manag. Sci. Lett. 2011, 1, 531–540. [Google Scholar]
- Tushabomwe-Kazooba, C. Causes of small business failure in Uganda: A case study from Bushenyi and Mbarara Towns. Afr. Stud. Q. 2006, 8, 27–35. [Google Scholar]
- Zhang, Y.; Zhang, X. The e_ect of entrepreneurial orientation on business performance A role of network capabilities in China. J. Chin. Entrep. 2012, 4, 132–142. [Google Scholar]
- Hoque, A.S.M.M.; Awang, Z. Does gender difference play moderating role in the relationship between entrepreneurial marketing and Bangladeshi SME performance? Accounting 2018, 5, 35–52. [Google Scholar] [CrossRef]
- Ocloo, C.E.; Akaba, s.; Worwui-Brown, D.K. Globalization and competitiveness: Challenges of small and medium enterprises (SMEs) in Accra, Ghana. Int. J. Bus. Soc. Sci. 2014, 5, 287–296. [Google Scholar]
- Michelino, F.; Caputo, M.; Cammarano, A.; Lamberti, E. Inbound and outbound open innovation: Organisation and performances. J. Technol. Manag. Innov. 2014, 9, 65–82. [Google Scholar] [CrossRef]
- Andalib, T.W. A Study on Convergence of International Employee Rights within Human Resources Management Practices in Bangladesh. Ph.D. Thesis, Universiti Bangladesh Pahang, Pahang, Malaysia, November 2018. [Google Scholar]
- Bangladesh Employees’ Federation. The Bangladesh Labour Act 2006; Bangladesh Employees’ Federation: Dhaka, Bangladesh, 2009. [Google Scholar]
- International Labour Organisation. Handbook of Procedures Relating to International Labour Conventions and Recommendations; International Labour Organisation: Geneva, Switzerland, 2012. [Google Scholar]
- Alexander, S. Inefficiency in the German Mechanical Engineering Sector (27 November 2009). DIW Berlin Discussion Paper No. 949. 27 November. Available online: https://ssrn.com/abstract=1514278 (accessed on 9 May 2021).
- Wuest, T.; Thoben, K.D. Information Management for Manufacturing SMEs September IFIP International Conference on Advances in Production Management; Springer: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Wadhwa, R. Flexibility in manufacturing automation: A living lab case study of Norwegian metal casting SMEs. J. Manuf. Syst. 2012, 31, 444–454. [Google Scholar] [CrossRef]
- Wuest, T.; Schmid, P.; Lego, B.; Bowen, E. Overview of Smart Manufacturing in West Virginia; WVU Bureau of Business & Economic Research: Morgantown, WV, USA, 2018. [Google Scholar]
- Nagy, D. International collaboration tools for Industrial development. In Proceedings of the 6th CSIR Conference: Ideas that Work for Industrial Development, Pretoria, South Africa, 5–6 October 2017; CSIR International Convention Centre: Pretoria, South Africa, 2017. [Google Scholar]
- EC. SME 4.0—Smart Manufacturing and Logistics for SMEs in an X-to-Order and Mass Customisation Environment. Available online: http://www.sme40.eu (accessed on 5 August 2019).
- Kshetri, N. The evolution of the internet of things industry and market in China: An interplay of institutions, demands and supply. J. Telecommun. Policy 2014, 41, 49–67. [Google Scholar] [CrossRef]
- Ehie, I.C.; Chilton, M.A. Understanding the influence of IT/OT Convergence on the adoption of Internet of Things (IoT) in manufacturing organizations: An empirical investigation. Comput. Ind. 2020, 115, 103166. [Google Scholar] [CrossRef]
- Gold, J. Skunk Works with Tractors: Inside John Deere’sIoT-Innovation Unit. Network World. 2017. Available online: https://www.networkworld.com/article/3198744/internet-of-things/a-skunk-works-with-tractors-inside-john-deere-s-high-tech-iot-innovation-unit.html (accessed on 1 May 2022).
- Horwitz, L. UPS IoT Strategy is Fuelled by Analytics to bring Business Insight. 2018. Available online: https://www.cisco.com/c/en/us/solutions/internet-of-things/iot-strategy.html (accessed on 27 March 2022).
- Buyukozkan, G.; Gocer, F. Digital supply chain: Literature review and proposed framework for future research. Comput. Ind. 2018, 97, 157–177. [Google Scholar] [CrossRef]
- Ng, I.; Scharf, K.; Pogrebna, G.; Maull, R. Contextual Variety, Internet-of-Thingsand the Choice of Tailoring over Platform: Mass Customisation Strategy in Supply Chain Management. Int. J. Prod. Econ. 2015, 159, 76–87. [Google Scholar] [CrossRef]
- Yu, J.; Kim, M.; Bang, H.-C.; Bae, S.-H.; Kim, S.-J. Iot as a applications: Cloud- based building management systems for the internet of things. Multimed. Tools Appl. 2016, 75, 14583–14596. [Google Scholar] [CrossRef]
- Decker, C.; Berchtold, M.; Chaves, L.W.F.; Beigl, M.; Roehr, D.; Riedel, T.; Beuster, M.; Herzog, T.; Herzig, D. Cost-Benefit Model for Smart Items in the SupplyChain. Internet Things Lect. Notes Comput. Sci. 2008, 4952, 155–172. [Google Scholar]
- Agarwal, N.; Brem, A. Strategic business transformation through technology convergence: Implications from General Electric’s industrial internet initiative. Int. J. Technol. Manag. 2015, 67, 196–214. [Google Scholar] [CrossRef]
- Gartner, I.T. Operational Technology: Convergence, Alignment and Integration. February 2014. Available online: https://www.gartner.com/newsroom/id/2905717 (accessed on 22 May 2022).
- Tuul, O.; Bing, S.J. Employee Training in Small and Medium-Sized Enterprises in Mongolia. 2019. Available online: https://www.mongoliajol.info/index.php/PMAS/article/view/1140 (accessed on 14 May 2022).
- Mazanai, M.; Ngirande, H. Training and Development: Towards Sustainable Career Management and Talent Management. Mediterr. J. Soc. Sci. 2014, 5, 44–52. [Google Scholar]
- Maluleke, A. Challenges Faced by SEDA in Providing Training and Mentoring Support Services to SMMEs. Master’s Dissertation, University of Witwatersrand, Johannesburg, South Africa, 2013. [Google Scholar]
- Egelser, S.; Rena, R. An evaluation of the effectiveness of training on entrepreneurship development in Windhoek. Econ. Soc. S. Afr. 2013. [Google Scholar]
- Mahembe, E.; Underhill Corporate Solution (UCS). Literature Review on Small and Medium Enterprises’ Access to Credit and Support in South Africa. Pretoria. 2011. Available online: http://www.ncr.org.za/pdfs/LiteratureReviewonSMEAccesstoCreditinSouthAfrica_FinalReport_NCR_Dec2011.pdf (accessed on 22 May 2022).
- Global Entrepreneurship Monitor Report (GEM). Tracking Entrepreneurship in South Africa: A Gem Perspective; Global Entrepreneurship Monitor: London, UK, 2009. [Google Scholar]
- Chetty, A. A Critical Analysis of Current Approaches to SMME Development and Support within the eThekwini Municipal Area. Ph.D. Thesis, University of KwaZulu-Natal, Durban, South Africa, 2009. [Google Scholar]
- Ngcobo, S.; Sukdeo, R. Challenges Facing SMMEs during their First Two Years of Operation in KwaZulu-Natal. Mediterr. J. Soc. Sci. 2014, 5, 434–441. [Google Scholar]
- Muzondi, L. Women’s Small-Medium and Micro Enterprises as Engines for Income-Poverty Alleviation: A Renewed Approach to Tackling Urban Poverty in South Africa. Mediterr. J. Soc. Sci. 2014, 5, 632–638. [Google Scholar] [CrossRef]
- Nenzhelele, T.E. Competitive Intelligence Location in Small and Medium-Sized Enterprises. Mediterr. J. Soc. Sci. 2014, 5, 608. [Google Scholar] [CrossRef]
- Denby, S. The importance of training needs analysis. Ind. Commer. Train. 2010, 42, 147–150. [Google Scholar] [CrossRef]
- Ahmad, Z.S.; Xavier, S.R. Entrepreneurial environments and growth: Evidence from Malaysia GEM data. J. Chin. Entrep. 2012, 4, 50–69. [Google Scholar]
- Meltzer, A.H. Market Failure or Government Failure. Wall Str. J. East. Ed. 2010, 255, A19. [Google Scholar]
- Khoase, R.G.; Govender, K.K. Enhancing Small, Medium and Micro Enterprise Development: Exploring Selective Interventions by the Lesotho Government. Dev. South. Afr. 2013, 30, 596–615. [Google Scholar] [CrossRef]
- Ghobakhloo, M.; Arias-aranda, D.; Benitez-amado, J. Adoption of e-commerce applications in SMEs. J. Ind. Manag. Data Syst. 2011, 111, 1238–1269. [Google Scholar] [CrossRef]
- Lesáková, L. The Role of Business Incubators in Supporting the SME Start-up. Acta Polytech. Hung. 2012, 9, 85–95. [Google Scholar]
- Wright, M.; Marlow, S. Entrepreneurial activity in the venture creation and development process. Int. Small Bus. J. 2012, 30, 107–114. [Google Scholar] [CrossRef]
- Herrington, M.; Kew, J. GEM South Africa 2013 Report. 2014. Available online: http://www.gemconsortium.org/docs/3335/gem-south-africa-2013-report (accessed on 17 May 2022).
- Vakaloudis, A.; O’Leary, C. A framework for rapid integration of IoT Systems with industrial environments. In Proceedings of the 2019 IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019. [Google Scholar] [CrossRef]
- Bandyopadhyay, D.; Sen, J. Internet of things: Applications and Challenges in technology and standardisation. Wirel. Pers. Commun. 2011, 58, 49–69. [Google Scholar] [CrossRef]
- Addo-Tenkorang, R.; Gwangwava, N.; Ogunmuyiwa, E.N.; Albert, U. Advanced Animal Track-&-Trace Supply-Chain Conceptual Framework- An Internet of Things Approach. In Proceedings of the 14th Global Congress on Manufacturing and Management (GCMM-2019), Procedia Manufacturing, Brisbane, Australia, 5–7 December 2018; Volume 30, pp. 56–63. [Google Scholar]
- Boza, A.; Cortés-Santamaría, B.; Alemany Díaz MD, M.; Cuenca, L. Conceptual Framework for Applying Internet of Things in Production Systems for Sensing Enterprises. Braz. J. Oper. Prod. Manag. 2016, 13, 66. [Google Scholar] [CrossRef]
- Saunders, M.N.K.; Lewis, P.; Thornhill, A. Research Methods for Business Students, 8th ed.; Pearson: London, UK; Harlow, UK, 2019. [Google Scholar]
- Kashora, T.; van der Poll, H.M.; van der Poll, J.A. E-Learning and Technologies for Open Distance Learning in Management Accounting. Afr. Educ. Rev. 2016, 13, 1–19. Available online: https://www.learntechlib.org/p/195025/ (accessed on 22 March 2023). [CrossRef]
- van der Poll, J.A. Problematizing the Adoption of Formal Methods in the 4IR–5IR Transition. Appl. Syst. Innov. 2022, 5, 127. [Google Scholar] [CrossRef]



Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mhlongo, T.; van der Poll, J.A.; Sethibe, T. A Control Framework for a Secure Internet of Things within Small-, Medium-, and Micro-Sized Enterprises in a Developing Economy. Computers 2023, 12, 127. https://doi.org/10.3390/computers12070127
Mhlongo T, van der Poll JA, Sethibe T. A Control Framework for a Secure Internet of Things within Small-, Medium-, and Micro-Sized Enterprises in a Developing Economy. Computers. 2023; 12(7):127. https://doi.org/10.3390/computers12070127
Chicago/Turabian StyleMhlongo, Tebogo, John Andrew van der Poll, and Tebogo Sethibe. 2023. "A Control Framework for a Secure Internet of Things within Small-, Medium-, and Micro-Sized Enterprises in a Developing Economy" Computers 12, no. 7: 127. https://doi.org/10.3390/computers12070127
APA StyleMhlongo, T., van der Poll, J. A., & Sethibe, T. (2023). A Control Framework for a Secure Internet of Things within Small-, Medium-, and Micro-Sized Enterprises in a Developing Economy. Computers, 12(7), 127. https://doi.org/10.3390/computers12070127





