Abstract
The impressive growth rate of the Internet of Things (IoT) has drawn the attention of cybercriminals more than ever. The growing number of cyber-attacks on IoT devices and intermediate communication media backs the claim. Attacks on IoT, if they remain undetected for an extended period, cause severe service interruption resulting in financial loss. It also imposes the threat of identity protection. Detecting intrusion on IoT devices in real-time is essential to make IoT-enabled services reliable, secure, and profitable. This paper presents a novel Deep Learning (DL)-based intrusion detection system for IoT devices. This intelligent system uses a four-layer deep Fully Connected (FC) network architecture to detect malicious traffic that may initiate attacks on connected IoT devices. The proposed system has been developed as a communication protocol-independent system to reduce deployment complexities. The proposed system demonstrates reliable performance for simulated and real intrusions during the experimental performance analysis. It detects the Blackhole, Distributed Denial of Service, Opportunistic Service, Sinkhole, and Workhole attacks with an average accuracy of 93.74%. The proposed intrusion detection system’s precision, recall, and F1-score are 93.71%, 93.82%, and 93.47%, respectively, on average. This innovative deep learning-based IDS maintains a 93.21% average detection rate which is satisfactory for improving the security of IoT networks.
1. Introduction
The Internet of Things (IoT) has started a new paradigm of computing that is transforming our lives. IoT devices are employed in various applications, including transportation, smart homes, healthcare [1], industrial production, security, and supply-chain management [2], and Blockchain monitoring [3]. According to Zhao, Y., & Lian, Y., IoT devices are projected to hit 30.9 billion units by 2025. This study shows that the number of IoT devices in 2021 was 13.8 billion [4]. It indicates that this industry has a growth rate of more than 55%. This rapid growth, dependency on IoT devices, and business potential have drawn the attention of researchers, innovators, entrepreneurs, business people, and cybercriminals. The utilities provided by IoT devices have created an extensive demand in the market. This demand has drawn the interest of potential investors. Innovators and entrepreneurs are making this field even more attractive by innovating and marketing different applications of IoT devices to make our lives better and easier [5]. However, it has created the scope for cyber criminals to exploit the weaknesses and vulnerabilities of IoT devices. The business growth and financial opportunities have made IoT an attractive domain to practice cyber attacks. This is the root cause behind the rapid growth of cyber-attacks on IoT devices [6].
According to L. P. Rondon et al. [7], IoT device manufacturing with little, to some extent, no attention to cyber security. A study by R. Williams et al. discloses that many IoT devices currently exist in the market, many of which are fully operational in different services and are vulnerable to cyber attacks [8]. Attacks on IoT devices are not confined to the devices. Usually, IoT devices are connected to other appliances, and systems. As a result, they work as attack vectors which attackers exploit to gain access to anything connected to it. The attack on Dyn through imaging IoT devices caused a devastating effect in 2016, resulting in an internet outage for Amazon, Twitter, and Netflix [9]. One of the fastest-growing IoT sectors is Medical IoT (MIoT). MIoTs are sensitive because it is directly related to healthcare. However, The recent cyber-attack trends show that intrusion on MIoT devices is higher than ever, and the rate is increasing at a dangerous rate [1,10].
One of the significant challenges in IoT security is its various vulnerabilities. There are multiple ways to exploit vulnerabilities and attacks on IoT devices [11]. Every cyber-attack is made through network connectivity unless we consider cyber-physical attacks, which is not within the scope of this research. IoT devices are computationally constrained systems. That is why using traditional cyber-security methods to secure vulnerable IoT environments is impractical [12]. Moreover, the diverse multidimensional scope of vulnerabilities takes the IoT environment beyond the scope of conventional rule-based security methods [13]. IoT environments constantly produce large volumes of data. Identifying anomalous data from these streams of data is a challenging task. And Deep Learning (DL)-based approaches are appropriate in these cases. Deep neural networks are effective in analyzing large volumes of data, discovering patterns, and relations among them, and classifying the data according to defined properties [14].
The application of Deep Neural Networks (DNN) in IoT security is a promising solution to network data anomaly-based intrusion detection [15]. IoT devices produce a large volume of data. However, the nature of the data maintains a common pattern. Anything that disrupts the typical way may be considered an outlier which is anomalous. Properly trained DNN is a potential solution to identify and classify anomalous data [16]. Based on this hypothesis, we propose a Deep Neural Network-based IoT intrusion detection system from real-time anomalous data. The objective of this research is to develop a communication protocol-independent DNN-based real-time IoT intrusion detection system for safer and more secure IoT environments.
The proposed Deep Intrusion-Detection (DID) system does not require system attributes, communication protocol adjustment, or network structure virtualization. It is a plug-and-play intrusion detection system that identifies the common and anomalous signal flow through the network. Based on the deviation from the regular signal pattern, it detects intrusions. The core contributions of this paper are:
- Deep Neural Network (DNN) design and optimization for IoT network intrusion detection.
- Designing the intrusion detection system components.
- Discovering the effective dataset features for IoT network intrusion detection.
- Deep analysis of DNN-based intrusion detection system through intrusion model of five frequently occurring attacks.
- Achieving an average intrusion detection rate of 93.21%.
The rest of the paper has been organized into five different sections. The Section 2 presents the relevant literature review. The Section 3 of this paper presents the proposed methodology and implementation of the DID. The implementation details and conceptual assessment are presented in the Section 4. The experimental results and performance evaluation are presented in the Section 5. Finally, the paper is concluded in the Section 6.
2. Literature Review
Our daily life has become easier because of the application of IoT devices. It has revolutionized numerous sectors. Although the growth rate of IoT devices is remarkable, cybersecurity concern has become a significant barrier to the faster adoption of this technology [17]. A successful attack on IoT devices not only affects the device but also allows the attacker to explore other services it provides. IoT devices are used at the application level, which is more connected to the personal aspects of human lives. That is why it has become one of the prime targets of cyber-criminals [18]. Moreover, IoT devices are used as the control unit of different manufacturing facilities [19]. An attacker gets access to the entire control system if there is a security breach. Even connected smart phones are vulnerable to such attacks [20,21]. These exciting features of IoT networks attract more cyber criminals to attack IoT environments. That is why it is more important than ever to develop a Deep Learning-based intrusion detection system to minimize the number and effect of attacks on IoT systems.
M. Alajanbi et al. have discussed various methods of intrusion detection in their review paper by emphasizing the effectiveness of these methods [22]. The authors in [23,24,25,26,27,28] exhibit promising performance in intrusion detection. A. Oseni et al. developed an explainable deep learning-based intrusion detection system for IoT networks. They used SHapley Additive exPlanations (SHAP) to explain the network’s operation. One of the main focuses of this method is to comprehend the logical reason behind the decision made by their Deep Learning-based IDS. This framework demonstrates 99.15% accuracy and 98.83% F1 score. However, it is focused on the Internet of Vehicles (IoV), a sub-branch of IoT. Machine learning-based intrusion detection systems work optimally for fog and edge computing environments according to Alzubi et al. [29]. The proposed intrusion detection system is a potential solution to any IoT network regardless of connected devices. At the same time, the 99.15% accuracy achieved by A. Oseni et al. raises suspicion of overfitting which has yet to be addressed through different datasets. The proposed intrusion detection system is much more reliable and robust than this approach.
An explainable Deep Learning-based system developed by M. M. Alani et al. named as DeepIIoT, indented to secure industrial IoT devices, shows 99% accuracy with the testing dataset. They focus on industrial IoT, especially water treatment facilities, nuclear reactors, and power grids. They trained and experimented with the WUSTL-IIOT-2021 dataset [30]. The proposed intrusion detection system is also a deep learning-based approach. However, the innovative intermediate communication system makes it network-independent. The application boundary of the proposed IDS is not confined to industrial IoT only. Moreover, the DeepIIoT depends on the signature and is a rule-based detection system. It suffers from the challenge of frequently updating the signature database. The proposed system has no such limitation. V. Ravi et al. developed an intelligent network intrusion detection system using a recurrent deep learning-based feature fusion approach incorporating an ensemble meta-classifier. This approach achieves 99% accuracy [31]. Although it is superior to the proposed method from the accuracy perspective, the network architecture simplicity makes the proposed system a unique contribution to the intrusion detection research domain. An association rule mining-based Artificial Neural Networks (ANN) dependent intrusion detection methodology developed by F. Safara et al. demonstrates significant improvement in intrusion detection for communication networks [32]. The proposed approach is also based on ANN. However, its network architecture has been specially designed for IoT-network intrusion detection.
M. Abdel-Basset et al. have discussed the scope of applying deep learning techniques in IoT security. They further emphasized the application of deep learning in IoT privacy as well [33]. However, network-specific rule-based intrusion detection systems are easier to develop. They perform well within the intended network. A knowledge-based specific rule-dependent network sinkhole attack intrusion detection system developed by H. G. An et al. [34] demonstrates an attack detection ratio of 81.63%. It performs 7% better than [35], which is a similar approach named INTI. H. Asad et al., in their research on dynamic analysis of variations in rule-based intrusion detection systems for open course networks, discuss the significance of appropriate IDS in diversified configurations [36]. The quantitative analysis presented in this paper aligns with the core idea of the proposed methodology, which is the need for a network protocol-independent intrusion detection system for IoT networks.
3. Methodology
The proposed Deep Learning-based Intrusion Detection (DID) system, illustrated in Figure 1, is an innovative and automatic system that learns from data generated from the host IoT network and detects the intrusion of the network once adequately trained. The dynamic connector of the proposed Intrusion Detection System (IDS) establishes the connection between emulated network and requests from the IoT network. The emulated network communicates with the feature extractor and network classifier through an interface module. The feature extractor extracts the feature of the network packets, which are the dataset for the deep neural network of the proposed methodology. The proposed IDS is dynamic and regularly updated based on newly discovered features through the classifier Updated module. Once the intrusion is detected, the network classifier passes it to the mitigation phase. This phase reduces the impact of the intrusion.
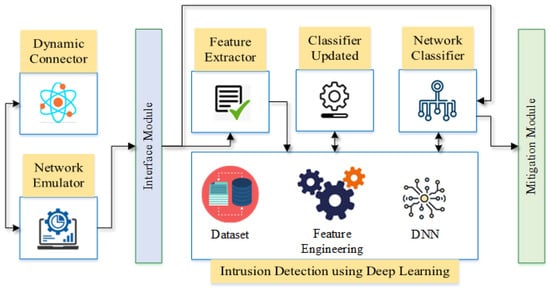
Figure 1.
The overview of the proposed methodology.
3.1. Components of the Detection System
We have developed the proposed intrusion detection system keeping simplicity in design and ease of deployment in mind. That is why the detection system has been developed using a modular approach. The proposed Deep Intrusion Detection (DID) system consists of three primary modules. They are the Communication Module (CM), Intrusion Detection Module (IDM), and Mitigation Module (MM). These three modules work together. The communication module manages the full-duplex communication between the sender and the receiver. Any form of communication passes through the IDM module. If any intrusion is detected, this module passes the packets to the mitigation module.
3.1.1. Communication Module (CM)
The communication module performs its operation through Dynamic Connection, Network Emulator, and Interface module. One of the core contributions of the proposed system is the communication protocol-independent system. The underlying protocol governing communication among IoT devices is not a constraint for the DID system. It has been done through an innovative design in the communication module. The working principle of the communication module has been discussed in this subsection.
Dynamic Connection
The dynamic connector sends probe signals. It also broadcasts beacons to all IoT devices within the defined network. It also analyzes the broadcast beacons, intercepts the handshake packets, and inspects the session requests to discover the communication protocols. It maintains a protocol table that lists the active communication protocols used in the IoT environment. The dynamic connector dynamically maintains functional network interfaces which intercept communication signals from different devices. The dynamic connector translates the packets received from different network interfaces. It uses secondary storage as the cache memory to store the translated packets. When it receives the bit stream from the IoT devices, it uses the appropriate communication protocols stored in the protocol table to convert the bit stream into network packets using the relevant protocol.
Network Emulator
The underlying network protocols governing the IoT networks are listed in the protocol table. It contains all relevant information about the network. Instead of connecting to the network directly, the proposed methodology uses an innovative way to maintain communication. And that is through a network emulator [37]. It has a Virtual Network Client (VNC) module that fetches the packets stored in the cache memory of the dynamic connector, chooses the appropriate network protocol from the protocol table, processes the packets according to the protocols, and finally transmits them to the intended IoT device.
Interface Module
The interface module creates the interface to exchange the data packets. It controls how data are transmitted and received between the communication module and the intrusion detection module. The interface module controls the dynamic connector and the network emulator.
3.1.2. Intrusion Detection Module (IDM)
Feature Extractor Module (FEM)
The IoT devices communicate over the networks through data packets governed by associated communication protocols. Anything anomalous is related to the data packets. The feature extractor module extracts the features listed and explains in Table 1 from the data packets using Algorithm 1. This module intercepts data packets. Features expect , , , and are available in the header of the packets. The information () of the packets is carried in terms of the data field. The transmission rate (), and reception rate () are sent by the interface module of the Communication Module (CM). The transmission to reception ratio () is measured as the ratio of and .

Table 1.
Feature extraction and their roles.
Network Classifier
One reason behind the proposed system’s outstanding performance is the anomalous network before intrusion detection using Deep Learning. We used machine learning-based anomaly detection to classify malignant and benign networks. A Support Vector Machines (SVM) model has been used in this paper to classify the network. The loss function of the SVM model is defined by Equation (1).
To prevent the SVM from overfitting, a regularization parameter has been added to the cost function of the Equation (1), which is expressed using the Equation (2).
Finally, the gradient of the SVM is updated using Equations (3) and (4) for correct and incorrect prediction, respectively.
The weights are updated during the training phase of the SVM model. The model is trained using the dataset created from the experimenting network based on the features explained in Table 1. Training the model is a manual process. The dataset has been prepared by manual observation over various intervals of time. During the observation, the dataset is labeled malignant and benign.
| Algorithm 1 Feature Extraction Algorithm |
| Require:
Extract Divide the for each Layer for every Layer in packet do if then end if for every F do Add the F to feature list end for Assign the features to Layer end for |
Classifier Updater
One of the innovative approaches of this proposed intrusion detection system is the Classifier Updated. This module has been designed to reduce the necessity of human intervention to update the network classifier. This module has tasks. The first task is to keep track of the signals from the network which are not part of the training dataset. And the second task is to monitor the accuracy of the SVM constantly. When the accuracy of the SVM falls below 90% multiple times, the Classifier Updated raises the alarm. After it receives the labeled dataset, it automatically updates the SVM on the dataset that caused performance degradation along with the previous dataset.
3.1.3. Mitigation Module
The proposed intrusion detection system detects the intrusion using a deep neural network, and it mitigates the attack. At the same time, it generates a system response to generate an alert. The entire process consists of two activities. The first activity is sensing the nature of the attack, and the second phase prompts a relevant scheme to minimize the impact of the intrusion. There are two components to these two activities. The first component is the proposed deep neural network that classifies the attack and the second component is a controller that chooses an appropriate option from a set of options to mitigate the impact of the attack. The set of options is defined by Equation (5).
The in Equation (5) is an `intrusion-mitigation’ pair that is pre-selected during the deployment of the proposed IDS. The `intrusion-mitigation’ pair changes depending on the need, goal, and priority of the network. This experiment deals with five sets of intrusions defined in the intrusion model of Section 4.1.
3.2. Intrusion Detection Using Deep Learning
3.2.1. Dataset
A dataset with 25,000 instances has been prepared for and used in this experiment. The Regular () and Malicious () instance ratio of the dataset is 82:18. That means 82% of 25,000 instances are regular data, and 18% instances are malicious data. The and are randomly mixed, and there is no intentional pattern has been created. This dataset has been divided into training, testing, and validation dataset with a ratio of 70:15:15. The training and validation datasets have been used during the training phase. The testing dataset is untouched during the training and validation phase and used during the experimental evaluation only. Proper feature selection and feature reduction are two essential phases in automatic intrusion detection systems [38]. That is why the dataset for this experiment contains the features mentioned in Table 1, which are considered the most influential features in detecting intrusion using machine learning algorithms.
3.2.2. Feature Engineering
The features listed in Table 1 consist of qualitative and quantitative features. In the IoT network, there are senders and receivers. IoT devices are resource constraint devices. That is why they are designed to communicate in the simplest possible way. Usually, the transmission rate of the senders and receivers are the same to avoid the necessity of installing extended buffer memory. A significant difference between the transmission and distribution rates indicates a Denial-of-Service (DoS) attack [39].
The IoT network is safe if the transmission-to-reception ratio is close to unity. However, significant deviation from unity means the sender is not sending the data to the correct destination or the receiver is not receiving the data from the intended source. It is an indication of spoofing. There is a possibility that some intermediate device, which is not enlisted in the network, has breached the network security and manipulated the sender and the receiver. The transmission mode determines the communication protocol, the current status of the communication cycle, and the next phase of the cycle. A Deep Neural Network trained on the nature of communication at different transmission modes identifies an intrusion if any device behaves differently under a certain transmission mode. The quantitative analysis leads to qualitative results used to determine the intrusion in an IoT network. The features listed in Table 1 are used to perform the quantitative analysis to generate qualitative results. The proposed system uses the cache memory of the Communication Module to temporarily store these features and process them to detect intrusion if there is any. The process starts with the probability distribution calculation using Equation (6).
Here is Equation (6), is the probability of each data packet value of unity observed in the feature. If the is greater than 50% of the mean, the data is benign or otherwise malignant.
3.2.3. Deep Neural Network Design
A six-layer deep neural network has been designed and optimized to detect intrusion in this experiment. We started with a network architecture with 2 hidden layers. However, the experimental observation shows that the network performance is not satisfactory with 2 hidden layers. That is why we experimented with different numbers of hidden layers, and the six-layer deep neural network generates the best result. We used a Fully Connected Feed Forward Neural Network (FCFFN) architecture [40], which is illustrated in Figure 2. Every neuron of a layer is connected to every other neuron of the subsequent layer in FCFFN architecture. There is no additional implementation complexity of emphasizing and omitting connections. We used the FCFFN architect for simplicity and ease of implementation. It has eight input nodes for the eight features listed in Table 1. Each input node receives one feature. The features are extracted using the feature extraction module. The features are stored in the dataset, each row containing eight features. These rows are transposed using the Equation (7) before being transmitted to the proposed network.
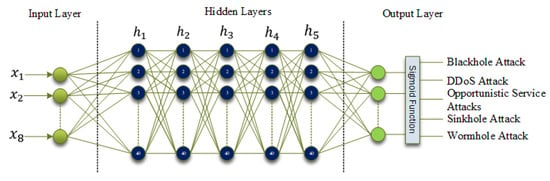
Figure 2.
Deep Neural Network Architecture.
The output vector of the network is defined by Equation (8) where is the output vector, represents the activation function, is the bias vector, and represents the previous layer to layer l.
We used the Rectified Linear Activation Unit (ReLU) function for the hidden nodes [41] and the Sigmoid function for the output nodes [42]. These two activation functions are defined by Equations (9) and (10).
The Gradient Descent algorithm has been used as the loss function of the proposed network to minimize the error defined by Equation (11) [43]. Based on the loss function, the weight of the hidden nodes of the hidden layers of the network is updated. The back-propagation algorithm governed by Equation (12) has been used to update weights of the hidden nodes [44].
4. Implementation and Result Evaluation
The proposed Deep Learning-based Intrusion Detection (DID) system for IoT networks has been implemented in python using the TensorFlow library. We used Cooja Network Simulator (CNS) [45] and experimented with it in Contiki Operating System (COS) [46]. The Raspberry Pi 4 Model B with 2 GB primary memory has been used as the IoT device.
4.1. Intrusion Model
The most frequent and damaging attacks on IoT networks are Blackhole Attack, Distributed Denial-of-Service (DDoS) Attack, Opportunistic Service Attacks, Sinkhole Attack, and Wormhole Attack [47]. The performance of the proposed intrusion detection system has been evaluated based on these five attacks. A. Thakkar and R. Lohiya have conducted a rigorous study and presented the different aspects of the intrusion detection model in their review paper. This review, published in 2022, shows the gradual fall in intrusion detection rate for the five attacks mentioned in our attack model. The reason behind it is the change in the nature of the data. The rate of data flow, nature of the attack, and target of the attackers have changed. As a result, traditional rule-based systems are no longer as effective as they used to be before the revolution of IoT [48]. That is why this paper proposes deep neural networks, which are state-of-the-art techniques to handle big data, discover patterns, and make appropriate predictions.
Blackhole Attack (BHA)
In a blackhole attack, the malicious device first advertises erroneously that it is on the quickest route to the target, and then it drops all packets that are traveling along its path in silence, therefore creating a blackhole in the network [49].
Distributed Denial-of-Service (DDoS) Attack
A distributed denial-of-service attack, also known as a DDoS attack, is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. This type of attack is known as a distributed denial-of-service attack (DDoS) [50].
Opportunistic Service Attacks (OSA)
In an opportunistic service attack, the malicious device builds up its trustworthiness by first providing services that are extremely trustworthy, but it subsequently switches to offering services that are of lower quality for the purpose of increasing its own profits [51].
Sinkhole Attack (SHA)
A sinkhole attack is a form of attack in which a hacked node attempts to attract network traffic by advertising its own bogus routing update. Sinkhole attacks have a number of negative effects, one of which is that they may be used to launch further attacks, such as selective forwarding attacks, acknowledgment spoofing attacks, drops, or attacks that modify routing information [52].
Wormhole Attack (WHA)
Using a virtual private connection, two attacking devices communicate with one other in order to carry out an attack known as a wormhole tunnel attack. The network packets that are received by the victim device are initially sent via the wormhole, and then they are replayed at a later time. This causes the routes to be less efficient [53].
4.2. Evaluation Metrics
The state-of-the-art machine learning evaluation metrics have been used in this experiment to evaluate the performance of the proposed intrusion detection system. It has been observed from the literature review that accuracy, precision, recall, and F1-score are the most widely used ML evaluation metrics. These metrics have been defined by Equations (13)–(16), respectively. These evaluation metrics are measured from True Positive (TP), True Negative (TN), False Positive (FP), and False Negative (FN) [54]. These values are retrieved from the confusion matrix analysis, which is presented in the next subsection. We have also evaluated the performance of the proposed network based on the Intrusion Detection Rate (IDR) of the system, which is defined by the Equation (17) where DI stands for Detected Intrusion and TI stands for Total Intrusion.
4.3. Confusion Matrix Analysis
A confusion matrix is a table that defines the performance of a machine learning classifier with True Positive (TP), True Negative (TN), False Positive (FP), and False Negative (FN). These values are further used to measure accuracy, precision, recall, and F1-score, which are considered as state-of-the-art machine learning evaluation metrics.
4.3.1. Performance on BHA
The performance of the proposed deep neural network on BHA has been analyzed using the confusion matrix illustrated in Figure 3. The precision and recall on BHA are 88.4% and 96.9%. It demonstrates an accuracy of 96.5% with a specificity of 89.6%. The proposed intrusion detection system classifies 435 negative classes and 492 positive classes correctly. However, 16 negative classes were predicted as positive, and 57 positive class was predicted as negative. That is why the precision of the proposed IDE on the performance of Blackhole attack detection is 88.4%. However, the overall accuracy of the proposed IDS on BHA attack is satisfactory.
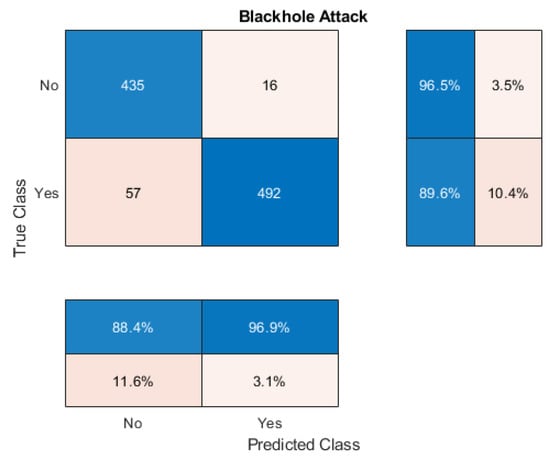
Figure 3.
Confusion Matrix Analysis on Blackhole Attack.
4.3.2. Performance on DDoS Attack
The DDOs attack is one of the common attacks. A successful DDoS attack can cause serious harm to business and customer satisfaction. If an IoT network is unavailable for an extended period of time, all dependent services will collapse, which downloads the overall Quality of Service (QoS) and ignites customer dissatisfaction [55]. The proposed deep neural network demonstrate better performance in classifying DDoS attack, which has been illustrated in the confusion matrix of Figure 4. It shows that the network correctly classifies 485 positive and 444 negative classes. However, 48 negative class was predicted as positive, and 23 positive class was predicted as negative. Overall, the network has achieved 92.2% precision and 95.5% recall. The accuracy of the network is 95.1%, and the sensitivity is 91.0%. According to the observation on the confusion of Figure 4, the proposed intrusion detection system is good at detecting DDoS attacks.
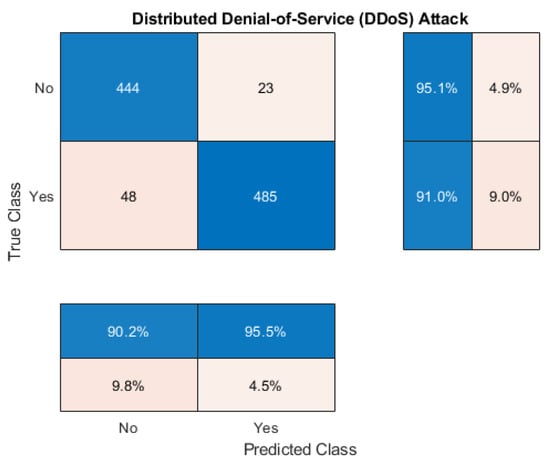
Figure 4.
Confusion Matrix Analysis on DDoS Attack.
4.3.3. Performance on OSA
Attackers with the intention to penetrate into the IoT network without proper authorization usually attempt Opportunistic Service Attacks (OSA). The proposed deep learning-based intrusion detection system demonstrates up to the mark performance in detecting OSA. The confusion matrix analysis presented in Figure 5 demonstrates that the proposed deep neural network has been well-trained to classify Opportunistic Service Attacks (OSA). The intrusions are successfully detected with 94.8% precision and 95.5% recall. The classification accuracy is 95.2% with a sensitivity of 95.2% as well. The overall F1-score of the network in OSA detection is 95.04%. The experimenting IDS detects 952 attacks out of 1000 attacks correctly. Only 23 negative class was predicted as positive, and 25 positive class was predicted as negative class. It is evident from this observation that the proposed deep learning-based intrusion detection system detects Opportunistic Service attacks effectively.
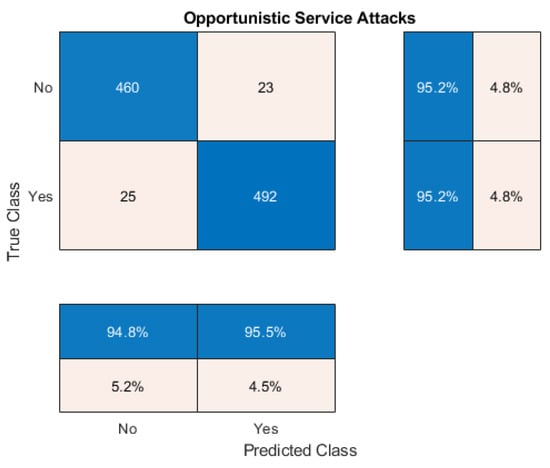
Figure 5.
Confusion Matrix Analysis on OSA.
4.3.4. Performance on SHA
The Sinkhole attack is a dangerous routing attack. In this attack, a neighboring IoT node is targeted. After that, the routing information is manipulated so that the requests expecting the received service from the IoT network are diverted to other destinations. It results in improper and, in many cases, no response to requests from the IoT devices. And the extended period of successful Sinkhole attacks can mislead a large volume of authentic requests. The performance of the proposed deep neural network-based intrusion detection system has been analyzed using the confusion matrix illustrated in Figure 6. It shows that the network correctly identifies 483 positive intrusions and 450 negative intrusions. However, the network predicts 35 benign events as intrusions. At the same time, it fails to predict 32 malignant classes correctly. The proposed network detects intrusion with 92.8% precision and 93.8% recall. The system’s overall accuracy is 93.4%, and the specificity is 93.2%. Out of 1000 instances, the proposed IDS detects 952 instances correctly. That means the proposed intrusion detection system is good at detecting Sinkhole attacks.
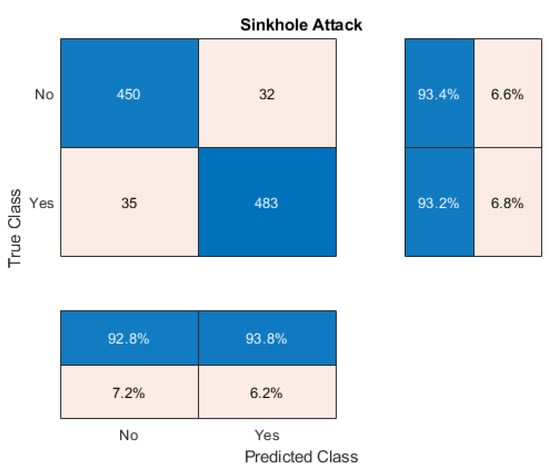
Figure 6.
Confusion Matrix Analysis on OSA.
4.3.5. Performance on WHA
The Wormhole Attack (WHA) is the fifth intrusion in our attack model prepared for this experiment. One of the common bandwidth optimization tactics is to route the packets through the shortest path and store them in buffer memory to minimize the delay. The Wormhole Attack (WHA) manipulates the routing optimization information resulting longer delay routing delay. At the same time, it leads the packets through a longer route. The confusion matrix illustrated in Figure 7 demonstrates that the proposed network detects the WHA with 94.5% precision and 94.6% recall. The overall accuracy of the network is 94.2%, and the specificity is 95.0%. The network detects the intrusion with an F1-score of 94.36%. That means the deep learning-based intrusion detection system efficiently detect Wormhole attacks.
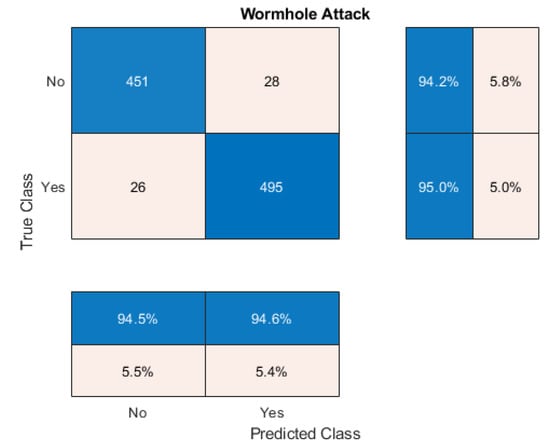
Figure 7.
Confusion Matrix Analysis on Wormhole Attack.
4.4. Overall Performance
The network’s overall performance on five different types of intrusions has been listed in Table 2. The overall performance has been analyzed based on a live random attack on the system. Because of security and confidentiality issues, we were not allowed to open the system and invite unknown attackers to attack the system. However, a realistic intrusion model has been created to study the performance of the system. In this model, the system has been observed for 24 h. During this time, multiple attacks were made randomly. We preserved an attack log to compare with the detected intrusion by the system.

Table 2.
Overall performance on random attack.
The overall performance is illustrated in Figure 8. It has been observed that the proposed deep learning-based intrusion detection system is best at detecting Opportunistic Service Attacks (OSA). However, it does not indicate that the system is not good at detecting other intrusions. The average accuracy for all intrusion detection is 93.74%, precision is 93.172%, recall is 93.824%, and the F1-score is 93.472%. The intrusion detection rate has been observed for each type of attack. The average IDS is 93.11% which assures protection against most experimenting attacks.
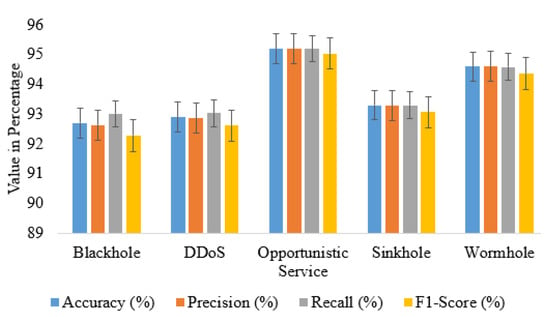
Figure 8.
Overall performance of the IDS.
The average accuracy, precision, recall, and F1-score show the marginal difference, illustrated in Figure 9. The average value range of the evaluation metrics is between 93% to 94%, marked in yellow color. That means the proposed intrusion detection system is accurate, stable, and suitable for practical application to secure IoT networks by automatically detecting intrusions.
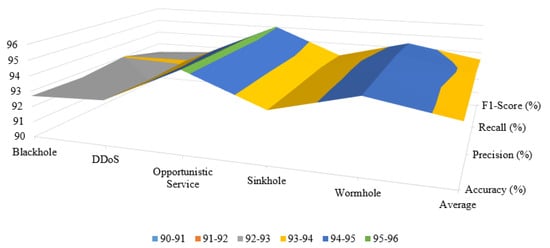
Figure 9.
Performance variation at different evaluation metrics.
5. Limitation & Future Scope
The proposed Deep Learning-based Intrusion Detection (DID) system demonstrates outstanding experimental results and analysis performance. The experimental results support the claim that it is both an effective and practical solution to automatically detect intrusion in IoT networks. However, like any computing system, the proposed intrusion detection system has some weaknesses. These limitations have been highlighted in this section. These limitations pave the path to conducting more research in the future and further developing the proposed system.
5.1. Intrusion Model Limitation
The proposed system is effective only for the intrusion model presented in this paper. There are five types of intrusions in the model. These are the most frequently occurring intrusions. However, many other intrusions still need to be addressed in this paper. This is one of the limitations and also an opportunity for further experimentation. The proposed deep neural network can be trained for other attacks. In our future research, we will explore more attacks and publish an analysis based on the findings.
5.2. Absence of Comparison
The innovative deep learning-based intrusion detection system proposed in this paper and the context of performance analysis need to have inclusive commonalities with the literature explored by the author of this paper. The proposed approach is yet to be compared with other published methodologies. A numeric comparison of the performance of one method with others requires some common grounds. That is why no numeric performance comparison has been presented in this paper. This limitation of this research leads to an opportunity to discover common ground among different intrusion detection systems and compare their performance.
5.3. System Dependent Dataset
The intrusion detection system proposed in this paper has been trained with the dataset produced by the experimenting system. Every new deployment of the DID system requires retraining the model with the dataset exclusive to that particular system. Although the DID system protocol is independent and is deployable in any network, it requires re-training for every new IoT network. It is a significant limitation of the proposed intrusion detection system. However, this limitation opens a future scope of research. The development of a massive dataset from different IoT networks followed by proper feature engineering has the potential to be the solution to this limitation.
The limitations of the proposed deep learning-based intrusion detection system open the door to further research. This research may overcome the limitations and further strengthen the system and ensure better security for IoT networks.
6. Conclusions
We are experiencing a new paradigm shift in communication technology where devices communicate among themselves. The projection of 30.9 billion active Inter of Things (IoT) devices by 2025 clearly indicates this new paradigm. This 55% growth in the IoT industry draws the attention of business people, entrepreneurs, and cybercriminals. Because of a resource-constrained computing environment, manufacturers pay attention to developing IoT devices with maximum service quality and little attention to security. However, attacks on IoT is not an attack on isolated devices; it is a doorway to intruding on many other connected services. This is why cybercriminals find it attractive and beneficial to attack IoT devices and which is why it is essential to detect intrusion on IoT networks right after an attempt. IoT network consists of thousands of IoT nodes transmitting and receiving massive voluminous data, making detecting the intrusion complicated. The innovative deep learning-based intrusion detection system presented in this paper identifies the most common and frequently attempted attacks on IoT networks with an average accuracy of 93.74%. Deep Neural Networks (DNNs) are dependent on datasets. A deep learning-based intrusion detection system trained for a particular network performs well for that network only because of the heterogeneous nature of different IoT networks. The innovative approach of this paper solves this complication by collecting the dataset from the experimenting network. This innovative approach is a game changer that makes the proposed system a robust and scalable intrusion detection system that can learn from any IoT network and detect intrusion automatically. In the future, the scope of developing a platform-independent framework from the deep learning-based intrusion detection system for IoT networks will be explored. It is expected that a lightweight version of the proposed framework will be more efficient and effective in intrusion detection.
Funding
This research received no external funding.
Data Availability Statement
Not available.
Conflicts of Interest
The author declare no conflict of interest.
References
- Faruqui, N.; Yousuf, M.A.; Whaiduzzaman, M.; Azad, A.; Barros, A.; Moni, M.A. LungNet: A hybrid deep-CNN model for lung cancer diagnosis using CT and wearable sensor-based medical IoT data. Comput. Biol. Med. 2021, 139, 104961. [Google Scholar] [CrossRef]
- Wójcicki, K.; Biegańska, M.; Paliwoda, B.; Górna, J. Internet of Things in Industry: Research Profiling, Application, Challenges and Opportunities—A Review. Energies 2022, 15, 1806. [Google Scholar] [CrossRef]
- Hasan, M.K.; Akhtaruzzaman, M.; Kabir, S.R.; Gadekallu, T.R.; Islam, S.; Magalingam, P.; Hassan, R.; Alazab, M.; Alazab, M.A. Evolution of industry and blockchain era: Monitoring price hike and corruption using BIoT for smart government and industry 4.0. IEEE Trans. Ind. Inform. 2022, 18, 9153–9161. [Google Scholar] [CrossRef]
- Zhao, Y.; Lian, Y. Event-driven Circuits and Systems: A Promising Low Power Technique for Intelligent Sensors in AIoT Era. IEEE Trans. Circuits Syst. II Express Briefs 2022, 69, 3122–3128. [Google Scholar] [CrossRef]
- Soldatos, J.; Gusmeroli, S.; Malo, P.; Di Orio, G. Internet of things applications in future manufacturing. In Digitising the Industry Internet of Things Connecting the Physical, Digital and Virtual Worlds; River Publishers: Delft, The Netherlands, 2022; pp. 153–183. [Google Scholar]
- Sharma, R.; Arya, R. Security threats and measures in the Internet of Things for smart city infrastructure: A state of art. Trans. Emerg. Telecommun. Technol. 2022, 1, e4571. [Google Scholar] [CrossRef]
- Rondon, L.P.; Babun, L.; Aris, A.; Akkaya, K.; Uluagac, A.S. Survey on enterprise Internet-of-Things systems (E-IoT): A security perspective. Ad Hoc Netw. 2022, 125, 102728. [Google Scholar] [CrossRef]
- Williams, R.; McMahon, E.; Samtani, S.; Patton, M.; Chen, H. Identifying vulnerabilities of consumer Internet of Things (IoT) devices: A scalable approach. In Proceedings of the 2017 IEEE International Conference on Intelligence and Security Informatics (ISI), Beijing, China, 22–24 July 2017; IEEE: New York, NY, USA, 2017; pp. 179–181. [Google Scholar]
- Hilton, S. Dyn Analysis Summary of Friday October 21 Attack. Dyn Blog. 2016. Available online: https://dyn.com/blog/dyn-analysis-summary-of-friday-october-21-attack (accessed on 1 January 2023).
- Nayak, J.; Meher, S.K.; Souri, A.; Naik, B.; Vimal, S. Extreme learning machine and bayesian optimization-driven intelligent framework for IoMT cyber-attack detection. J. Supercomput. 2022, 78, 14866–14891. [Google Scholar] [CrossRef]
- Husnain, M.; Hayat, K.; Cambiaso, E.; Fayyaz, U.U.; Mongelli, M.; Akram, H.; Ghazanfar Abbas, S.; Shah, G.A. Preventing MQTT Vulnerabilities Using IoT-Enabled Intrusion Detection System. Sensors 2022, 22, 567. [Google Scholar] [CrossRef]
- Zheng, Y.; Li, Z.; Xu, X.; Zhao, Q. Dynamic defenses in cyber security: Techniques, methods and challenges. Digit. Commun. Netw. 2022, 8, 422–435. [Google Scholar] [CrossRef]
- Nimbalkar, P.; Kshirsagar, D. Analysis of rule-based classifiers for IDS in IoT. In Data Science and Security; Springer: New York, NY, USA, 2021; pp. 461–467. [Google Scholar]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.K.; Du, X.; Ali, I.; Guizani, M. A survey of machine and deep learning methods for internet of things (IoT) security. IEEE Commun. Surv. Tutor. 2020, 22, 1646–1685. [Google Scholar] [CrossRef]
- Amanullah, M.A.; Habeeb, R.A.A.; Nasaruddin, F.H.; Gani, A.; Ahmed, E.; Nainar, A.S.M.; Akim, N.M.; Imran, M. Deep learning and big data technologies for IoT security. Comput. Commun. 2020, 151, 495–517. [Google Scholar] [CrossRef]
- Li, Y.; Zuo, Y.; Song, H.; Lv, Z. Deep learning in security of internet of things. IEEE Internet Things J. 2021, 9, 22133–22146. [Google Scholar] [CrossRef]
- Alferidah, D.K.; Jhanjhi, N. Cybersecurity impact over bigdata and iot growth. In Proceedings of the 2020 International Conference on Computational Intelligence (ICCI), Bandar Seri Iskandar, Malaysia, 8–9 October 2020; IEEE: New York, NY, USA, 2020; pp. 103–108. [Google Scholar]
- Yılmaz, H.E.; Sirel, A.; Esen, M.F. The impact of internet of things self-security on daily business and business continuity. In Research Anthology on Business Continuity and Navigating Times of Crisis; IGI Global: Hershey, PA, USA, 2022; pp. 695–712. [Google Scholar]
- Harada, R.; Shibata, N.; Kaneko, S.; Honda, K.; Terada, J.; Ishida, Y.; Akashi, K.; Miyachi, T. Quick Suppression of DDoS Attacks by Frame Priority Control in IoT Backhaul with Construction of Mirai-based Attacks. IEEE Access 2022, 10, 22392–22399. [Google Scholar] [CrossRef]
- Batten, L.M.; Moonsamy, V.; Alazab, M. Smartphone applications, malware and data theft. In Computational Intelligence, Cyber Security and Computational Models; Springer: New York, NY, USA, 2016; pp. 15–24. [Google Scholar]
- Alazab, M.; Batten, L.M. Survey in smartphone malware analysis techniques. In New Threats and Countermeasures in Digital Crime and Cyber Terrorism; IGI Global: Hershey, PA, USA, 2015; pp. 105–130. [Google Scholar]
- Alajanbi, M.; Mohd Arfian Ismail, R.A.H.; Sulaiman, J. Intrusion Detection: A Review. Mesopotamian J. Cybersecur. 2021, 2021, 4. [Google Scholar]
- Alazab, A.; Khraisat, A.; Alazab, M.; Singh, S. Detection of Obfuscated Malicious JavaScript Code. Future Internet 2022, 14, 217. [Google Scholar] [CrossRef]
- Alazab, M.; Abu Khurma, R.; Awajan, A.; Wedyan, M. Digital Forensics Classification Based on a Hybrid Neural Network and the Salp Swarm Algorithm. Electronics 2022, 11, 1903. [Google Scholar] [CrossRef]
- Alazab, M.; Alazab, A.; Batten, L. Smartphone malware based on synchronisation vulnerabilities. In Proceedings of the ICITA 2011: Proceedings of the 7th International Conference on Information Technology and Applications, Washington, DC, USA, 5–8 December 2011; ICITA: Washington, DC, USA, 2011; pp. 1–6. [Google Scholar]
- Alazab, M.A. Analysis on Smartphone Devices for Detection and Prevention of Malware; Deakin University: Melbourne, Australia, 2014. [Google Scholar]
- Alazab, M.; Khurma, R.A.; Awajan, A.; Camacho, D. A new intrusion detection system based on moth–flame optimizer algorithm. Expert Syst. Appl. 2022, 210, 118439. [Google Scholar] [CrossRef]
- Alazab, M.; Alazab, M.; Shalaginov, A.; Mesleh, A.; Awajan, A. Intelligent mobile malware detection using permission requests and API calls. Future Gener. Comput. Syst. 2020, 107, 509–521. [Google Scholar] [CrossRef]
- Alzubi, O.A.; Alzubi, J.A.; Alazab, M.; Alrabea, A.; Awajan, A.; Qiqieh, I. Optimized Machine Learning-Based Intrusion Detection System for Fog and Edge Computing Environment. Electronics 2022, 11, 3007. [Google Scholar] [CrossRef]
- Alani, M.M.; Damiani, E.; Ghosh, U. DeepIIoT: An Explainable Deep Learning Based Intrusion Detection System for Industrial IOT. In Proceedings of the 2022 IEEE 42nd International Conference on Distributed Computing Systems Workshops (ICDCSW), Hong Kong, China, 18–21 July 2022; IEEE: New York, NY, USA, 2022; pp. 169–174. [Google Scholar]
- Ravi, V.; Chaganti, R.; Alazab, M. Recurrent deep learning-based feature fusion ensemble meta-classifier approach for intelligent network intrusion detection system. Comput. Electr. Eng. 2022, 102, 108156. [Google Scholar] [CrossRef]
- Safara, F.; Souri, A.; Serrizadeh, M. Improved intrusion detection method for communication networks using association rule mining and artificial neural networks. IET Commun. 2020, 14, 1192–1197. [Google Scholar] [CrossRef]
- Abdel-Basset, M.; Moustafa, N.; Hawash, H.; Ding, W. Deep Learning Techniques for IoT Security and Privacy; Springer: New York, NY, USA, 2022; Volume 997. [Google Scholar]
- An, G.H.; Cho, T.H. Improving Sinkhole Attack Detection Rate through Knowledge-Based Specification Rule for a Sinkhole Attack Intrusion Detection Technique of IoT. Int. J. Comput. Netw. Appl. (IJCNA) 2022, 9, 169–178. [Google Scholar] [CrossRef]
- Cervantes, C.; Poplade, D.; Nogueira, M.; Santos, A. Detection of sinkhole attacks for supporting secure routing on 6LoWPAN for Internet of Things. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; IEEE: New York, NY, USA, 2015; pp. 606–611. [Google Scholar]
- Asad, H.; Gashi, I. Dynamical analysis of diversity in rule-based open source network intrusion detection systems. Empir. Softw. Eng. 2022, 27, 1–30. [Google Scholar] [CrossRef]
- Hou, D.; Zhao, K.; Li, W.; Du, S. A Realistic, Flexible and Extendible Network Emulation Platform for Space Networks. Electronics 2022, 11, 1236. [Google Scholar] [CrossRef]
- Naeemullah Khan, I.K.; Daghighi, E. Improved feature selection method for features reduction in intrusion detection systems. Mesopotamian J. Cybersecur. 2021, 2021, 15. [Google Scholar]
- Sharafaldin, I.; Lashkari, A.H.; Hakak, S.; Ghorbani, A.A. Developing realistic distributed denial of service (DDoS) attack dataset and taxonomy. In Proceedings of the 2019 International Carnahan Conference on Security Technology (ICCST), Chennai, India, 1–3 October 2019; IEEE: New York, NY, USA, 2019; pp. 1–8. [Google Scholar]
- Gao, M.; Liao, T.; Lu, Y. Fully connected feedforward neural networks based CSI feedback algorithm. China Commun. 2021, 18, 43–48. [Google Scholar] [CrossRef]
- Agarap, A.F. Deep learning using rectified linear units (relu). arXiv 2018, arXiv:1803.08375. [Google Scholar]
- Han, J.; Moraga, C. The influence of the sigmoid function parameters on the speed of backpropagation learning. In Proceedings of the International Workshop on Artificial Neural Networks, Sitges, Spain, 9–11 June 1995; Springer: New York, NY, USA, 1995; pp. 195–201. [Google Scholar]
- Ruder, S. An overview of gradient descent optimization algorithms. arXiv 2016, arXiv:1609.04747. [Google Scholar]
- Phansalkar, V.V.; Sastry, P.S. Analysis of the back-propagation algorithm with momentum. IEEE Trans. Neural Netw. 1994, 5, 505–506. [Google Scholar] [CrossRef]
- Mansfield, S.; Veenstra, K.; Obraczka, K. TerrainLOS: An outdoor propagation model for realistic sensor network simulation. In Proceedings of the 2016 IEEE 24th International Symposium on Modeling, Analysis and Simulation of Computer and Telecommunication Systems (MASCOTS), London, UK, 19–21 September 2016; IEEE: New York, NY, USA, 2016; pp. 463–468. [Google Scholar]
- Gupta, V.; Tovar, E.; Pereira, N. CoS: A New Perspective of Operating Systems Design for the Cyber-Physical World. In Proceedings of the Operating Systems Platforms for Embedded Real-Time Applications Workshop, Modena, Italy, 7 July 2012. [Google Scholar]
- Abdullahi, M.; Baashar, Y.; Alhussian, H.; Alwadain, A.; Aziz, N.; Capretz, L.F.; Abdulkadir, S.J. Detecting Cybersecurity Attacks in Internet of Things Using Artificial Intelligence Methods: A Systematic Literature Review. Electronics 2022, 11, 198. [Google Scholar] [CrossRef]
- Thakkar, A.; Lohiya, R. A survey on intrusion detection system: Feature selection, model, performance measures, application perspective, challenges, and future research directions. Artif. Intell. Rev. 2022, 55, 453–563. [Google Scholar] [CrossRef]
- Ali, S.; Khan, M.A.; Ahmad, J.; Malik, A.W.; ur Rehman, A. Detection and prevention of Black Hole Attacks in IOT & WSN. In Proceedings of the 2018 Third International Conference on Fog and Mobile Edge Computing (FMEC), Barcelona, Spain, 23–26 April 2018; IEEE: New York, NY, USA, 2018; pp. 217–226. [Google Scholar]
- Islam, U.; Muhammad, A.; Mansoor, R.; Hossain, M.S.; Ahmad, I.; Eldin, E.T.; Khan, J.A.; Rehman, A.U.; Shafiq, M. Detection of distributed denial of service (DDoS) attacks in IOT based monitoring system of banking sector using machine learning models. Sustainability 2022, 14, 8374. [Google Scholar] [CrossRef]
- Fernando, N.; Loke, S.W.; Avazpour, I.; Chen, F.F.; Abkenar, A.B.; Ibrahim, A. Opportunistic fog for IoT: Challenges and opportunities. IEEE Internet Things J. 2019, 6, 8897–8910. [Google Scholar] [CrossRef]
- Liu, Y.; Ma, M.; Liu, X.; Xiong, N.N.; Liu, A.; Zhu, Y. Design and analysis of probing route to defense sink-hole attacks for Internet of Things security. IEEE Trans. Netw. Sci. Eng. 2018, 7, 356–372. [Google Scholar] [CrossRef]
- Goyal, M.; Dutta, M. Intrusion detection of wormhole attack in IoT: A review. In Proceedings of the 2018 International Conference on Circuits and Systems in Digital Enterprise Technology (ICCSDET), Kottayam, India, 21–22 December 2018; IEEE: New York, NY, USA, 2018; pp. 1–5. [Google Scholar]
- Neu, D.A.; Lahann, J.; Fettke, P. A systematic literature review on state-of-the-art deep learning methods for process prediction. Artif. Intell. Rev. 2022, 55, 801–827. [Google Scholar] [CrossRef]
- Mihoub, A.; Fredj, O.B.; Cheikhrouhou, O.; Derhab, A.; Krichen, M. Denial of service attack detection and mitigation for internet of things using looking-back-enabled machine learning techniques. Comput. Electr. Eng. 2022, 98, 107716. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).