Design and Implement an Accurate Automated Static Analysis Checker to Detect Insecure Use of SecurityManager
Abstract
1. Introduction
- Although losing a little popularity, Java is still among the most often-used programming languages in the software industry, according to the TIOBE index [9].
- Many applications used in our everyday lives are written in Java, with a long life span. Maintaining these applications and removing their weaknesses is essential.
- SM is common among the Java applications in GitHub repositories, but no practical work or research articles still focus on using it safely.
- Using static analysis techniques is effective in identifying security vulnerabilities and programming weaknesses.
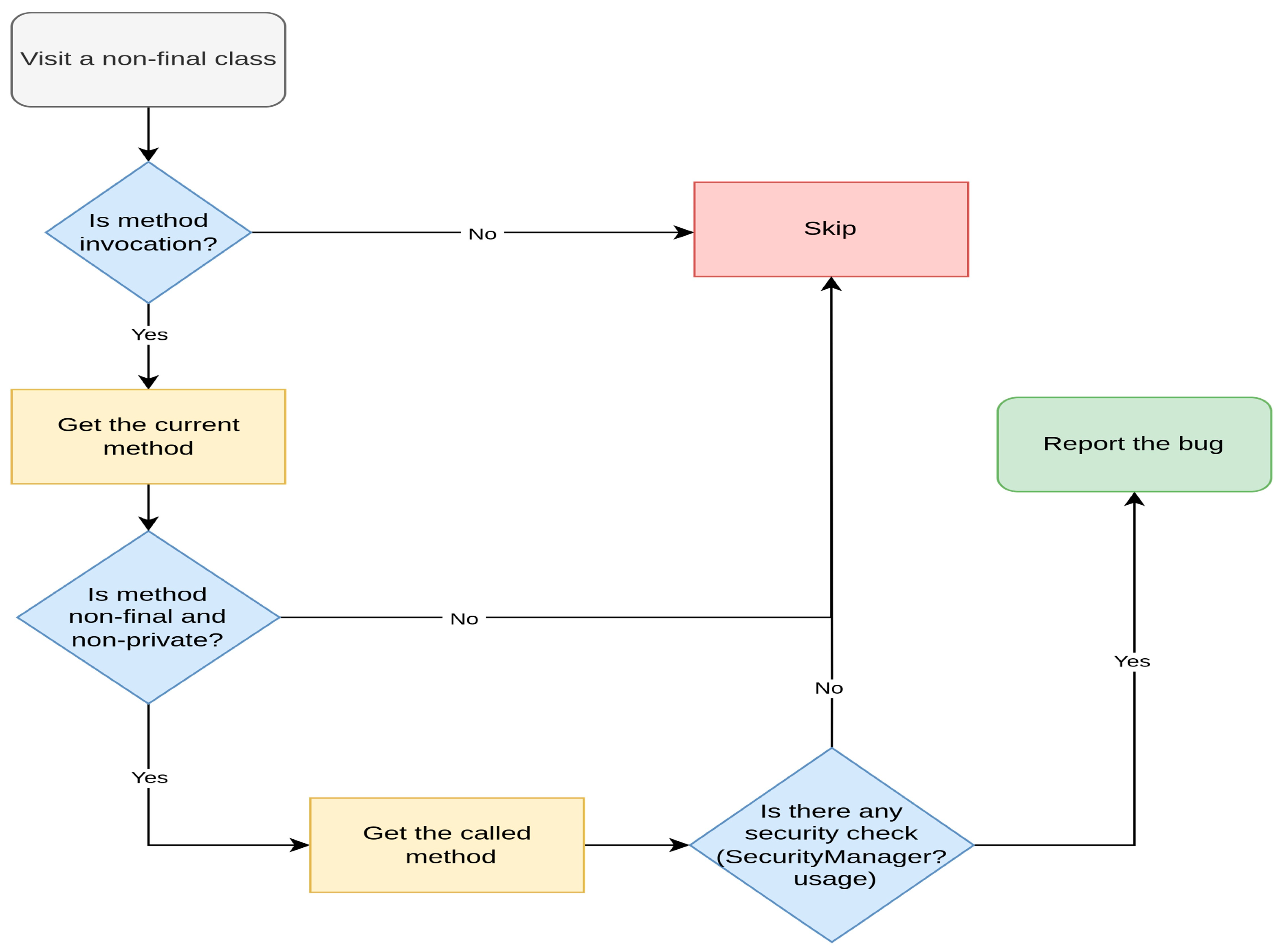
- We build a novel checker named FindVulnerableSecurityCheckMethods under the SpotBugs static analysis tool that raises an issue when calling an overridable method that performs a security check;
- We evaluate our approach on custom test cases and real-world software, and report the evaluation results using four robust metrics: recall, false alarm rate (FAR), precision, and F1-score.
Problem Statement
2. Related Work
3. Research Methodology
3.1. Checker Design
3.2. Custom Test Cases Design
- Non-compliant (NC) and compliant (C): we designed flawed and non-flawed test cases to be able to test our checker performance in both true positive (TP) and false positive (FP) aspects;
- Unambiguous: they are written clearly and concisely, leaving no room for misinterpretation;
- Test objective: each test case has a specific objective clearly stating what aspect of the issue is being tested;
- Independence: For better isolation and identification of issues, we designed independent test cases;
- Validated expectations: each test case has an expected outcome defined beforehand.
| public class FindVulnerableSecurityCheckMethodsTest { Logger logger = Logger.getAnonymousLogger(); public void badCallee() { (new FindVulnerableSecurityCheckMethodsTest()).badCalled(); } public void badCalled() { try { SecurityManager sm = System.getSecurityManager(); if (sm! = null) { sm.checkRead(“/temp/tempFile”); } //Access the file } catch (SecurityException se) { logger.log(Level.WARNING, se.toString()); } } } |
| public final class GoodSecurityCheckMethodsTest1 { Logger logger = Logger.getAnonymousLogger(); public void goodSecurityCheckMethodsTestCheck() { try { SecurityManager sm = System.getSecurityManager(); if (sm! = null) {//Check for permission to read file sm.checkRead(“/temp/tempFile”); } //Access the file } catch (SecurityException se) { logger.log(Level.WARNING, se.toString()); } } } |
| public class GoodSecurityCheckMethodsTest2 { Logger logger = Logger.getAnonymousLogger(); public void goodSecurityCheckMethodsTestCheck6() { try { SecurityManager sm = System.getSecurityManager(); if (sm! = null) {//Check for permission to read file if (5 > 10) { sm.checkRead(“/temp/tempFile”); } } //Access the file } catch (SecurityException se) { logger.log(Level.WARNING, se.toString()); } } } |
3.3. Performance Evaluation
4. Results
4.1. Analyzing Custom Test Cases
4.2. Analyzing Real Software
5. Conclusions
6. Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Algarni, A.M. The Historical Relationship between the Software Vulnerability Life cycle and Vulnerability Markets: Security and Economic Risks. Computers 2022, 11, 137. [Google Scholar] [CrossRef]
- Amankwah, R.; Chen, J.; Song, H.; Kudjo, P.K. Bug detection in Java code: An extensive evaluation of static analysis tools using Juliet Test Suites. Softw.-Pract. Exp. 2023, 53, 1125–1143. [Google Scholar] [CrossRef]
- Sun, P.; Kim, D.K.; Ming, H.; Lu, L. Measuring Impact of Dependency Injection on Software Maintainability. Computers 2022, 11, 141. [Google Scholar] [CrossRef]
- Alqaradaghi, M.; Kozsik, T. Inferring the Best Static Analysis Tool for Null Pointer Dereference in Java Source Code. CEUR Workshop Proc. 2022, 3237, 1–12. [Google Scholar]
- Chess, B.; West, J. Secure Programming with Static Analysis; Addison-Wesley: Reading, MA, USA, 2007; p. 11. [Google Scholar]
- Java Documentation, Class SecurityManager. Available online: https://docs.oracle.com/javase/8/docs/api/java/lang/SecurityManager.html (accessed on 30 September 2023).
- SEI CERT Oracle Coding Standard for Java, MET03-J: Methods that Perform a Security Check Must Be Declared Private or Final. Available online: https://wiki.sei.cmu.edu/confluence/display/java/MET03-J.+Methods+that+perform+a+security+check+must+be+declared+private+or+final (accessed on 30 September 2023).
- SpotBugs, Find Bugs in Java Programs. Available online: https://spotbugs.github.io/ (accessed on 20 September 2023).
- TIOBE Index for October 2023. Available online: https://www.tiobe.com/tiobe-index (accessed on 2 November 2023).
- Java Documentation, JEP 411: Deprecate the Security Manager for Removal. Available online: https://openjdk.org/jeps/411 (accessed on 30 September 2023).
- Searching for SecurityManager in GitHub. Available online: https://github.com/search?q=SecurityManager+language%3AJava&type=code (accessed on 2 November 2023).
- SEI CERT Oracle Coding Standard for Java, MET04-J. Do Not Increase the Accessibility of Overriden or Hidden Methods. Available online: https://wiki.sei.cmu.edu/confluence/display/java/MET04-J.+Do+not+increase+the+accessibility+of+overridden+or+hidden+methods (accessed on 1 November 2023).
- Parasoft Jtest, Automated Java Software Testing and Static Analysis. Available online: https://www.parasoft.com/ (accessed on 1 November 2023).
- PVS-Studio, Static Analyzer on Guard of Code Quality, Security (SAST), and Code Safety. Available online: https://pvs-studio.com/en/ (accessed on 1 November 2023).
- SonarQube, A Self-Managed, Automatic Code Review Tool that Systematically Helps You Deliver Clean Code. Available online: https://docs.sonarsource.com/sonarqube/latest/ (accessed on 1 November 2023).
- SEI CERT Oracle Coding Standard for Java, MET05-J. Ensure that Constructors Do Not Call Overridable Methods. Available online: https://wiki.sei.cmu.edu/confluence/display/java/MET05-J.+Ensure+that+constructors+do+not+call+overridable+methods (accessed on 1 November 2023).
- SEI CERT Oracle Coding Standard for Java, MET05-J. Don Not Invoke Overridable Methods in Clone(). Available online: https://wiki.sei.cmu.edu/confluence/pages/viewpage.action?pageId=88487921 (accessed on 1 November 2023).
- Herzog, A.; Shahmehri, N. Performance of the Java security manager. Comput. Secur. 2005, 24, 192–207. [Google Scholar] [CrossRef]
- Joseph, A.B. Java Security, Computer Based Learning Unit. University of Leeds, Leeds, UK, 8 December 1995. Available online: https://groups.csail.mit.edu/mac/users/jbank/javapaper/javapaper.html (accessed on 1 November 2023).
- Sterbenz, A. An evaluation of the java security model. In Proceedings of the IEEE Proceedings 12th Annual Computer Security Applications Conference, San Diego, CA, USA, 9–13 December 1996. [Google Scholar]
- Paul, N.; Evans, D. Comparing Java and .NET security: Lessons learned and missed. Comput. Secur. 2006, 25, 338–350. [Google Scholar] [CrossRef]
- Cabri, G.; Ferrari, L.; Leonardi, L. Applying security policies through agent roles: A JAAS based approach. Sci. Comput. Program. 2006, 59, 127–146. [Google Scholar] [CrossRef][Green Version]
- Clemente, P.J.; Hernández, J.; Conejero, J.M.; Ortiz, G. Managing crosscutting concerns in component based systems using a model driven development approach. J. Syst. Softw. 2011, 84, 1032–1053. [Google Scholar] [CrossRef]
- Tekinerdogan, B.; Aksit, M.; Henninger, F. Impact of Evolution of Concerns in the Model-Driven Architecture Design Approach. Electron. Notes Theor. Comput. Sci. 2007, 163, 45–64. [Google Scholar] [CrossRef]
- Yero, F.I.H.; De Oliveira Lucchese, F.; Sambatti, F.S.; Von Zuben, M.; Henriques, M.A.A. JoiN: The implementation of a Java-based massively parallel grid. Futur. Gener. Comput. Syst. 2005, 21, 791–810. [Google Scholar] [CrossRef]
- Little, M.C. Constructing reliable Web applications using atomic actions. Comput. Networks 1997, 29, 1281–1290. [Google Scholar] [CrossRef]
- MET03-J Checker. Available online: https://github.com/NazirMuhammadZafarIqbal/spotbugs/tree/MET03 (accessed on 15 October 2023).
- Public Review of MET03-J Checker. Available online: https://github.com/spotbugs/spotbugs/pull/2447 (accessed on 25 September 2023).
- Elasticsearch: Free and Open, and Distributed, RESTful Search and Analytics Engine at the Heart of the Elastic Stack. Available online: https://github.com/elastic/elasticsearch (accessed on 20 October 2023).
- Alphaloop Selective Security Manager: Demonstrates How to Create a Java SecurityManager that Can Be Enabled and Disabled Programmatically on Specific Threads. Available online: https://github.com/alphaloop/selective-security-manager (accessed on 20 October 2023).
- Lottie Android, Render After Effects Animations Natively on Android and iOS, Web, and React Native. Available online: https://github.com/airbnb/lottie-android (accessed on 20 October 2023).
- Mybatis—3, MyBatis SQL Mapper Framework for Java. Available online: https://github.com/mybatis/mybatis-3 (accessed on 15 October 2023).
- Tomcat, Apache Tomcat Fork that Allows Tomcat Web Applications to Be Written and Run as Jigsaw Modules. Available online: https://github.com/pjBooms/tomcat (accessed on 15 October 2023).
- Intellij—Community, IntelliJ IDEA Community Edition. Available online: https://github.com/Randgalt/intellij-community (accessed on 15 October 2023).
- Tutorials, Just Announced—“Learn Spring Security Oauth”. Available online: https://github.com/virtuoushub/tutorials (accessed on 15 October 2023).
- Netty, Netty Project—An Event-Driven Asynchronous Network Application Framework. Available online: https://github.com/derklaro/netty (accessed on 10 October 2023).
| The Issue | Tools Target It |
|---|---|
| Increasing the accessibility of overridden or hidden method | Parasoft Jtest |
| Calling an overridable method by a constructor | SpotBugs, SonarQube, PVS-Studio |
| Calling an overridable method by the method clone | SpotBugs, Parasoft Jtest |
| Calling an overridable method that performs a security check | Our checker, under SpotBugs |
| References | Concern About | Use the SM in Implementing Their Ideas | Research Conclusions | |
|---|---|---|---|---|
| Java Security | SM | |||
| [18,21] | Yes | Yes
| No |
|
| [19,20] | Yes | No | No |
|
| [22,23,24,25,26] | No | No | Yes
|
|
| Current | No | Yes
| Yes
|
|
| Test Cases | Description |
|---|---|
| T1 | Using a named SM object |
| T2 | Using a nameless SM |
| T3 | Using a protected method |
| T4 | Calling a vulnerable method from another method. |
| T5 | Using obvious true if statement (ex: if (5 > 3)) |
| T6 | Using arbitrary if statement (if (ex: x < 12), when the value of x is unknown) |
| Test Cases | Description |
|---|---|
| T1 | Using a final method |
| T2 | Using a private method |
| T3 | Creating a SM object without using it |
| T4 | Performing the security check in an obvious false branch (like if (5 > 10)) |
| T5 | Calling a method of SM that does not perform any security checks |
| T6 | Using a user-defined SM instead of java.lang.SecurityManager |
| Metrics | Value |
|---|---|
| NC test cases | 6 |
| C test cases | 18 |
| TP | 6 |
| FP | 0 |
| Recall | 1.00 |
| FAR | 0.00 |
| Precision | 1.00 |
| F1-score | 1.00 |
| Metrics | SpotBugs | Elasticsearch | Selective-Security-Manager | Lottie Android | Mybatis-3 | Tomcat | Intellij-Community | Tutorials | Netty |
|---|---|---|---|---|---|---|---|---|---|
| NC | 6 | 8 | 4 | 1 | 1 | 7 | 6 | 2 | 0 |
| C | 0 | 7 | 0 | 0 | 0 | 1 | 4 | 1 | 2 |
| TP | 6 | 8 | 4 | 1 | 1 | 7 | 6 | 2 | 0 |
| FP | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| Recall | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | N/A |
| FAR | 0.0 | 0.0 | 0.0 | 0.0 | 0.0 | 0.0 | 0.0 | 0.0 | 0.00 |
| Precision | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | N/A |
| F1-score | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | N/A |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alqaradaghi, M.; Nazir, M.Z.I.; Kozsik, T. Design and Implement an Accurate Automated Static Analysis Checker to Detect Insecure Use of SecurityManager. Computers 2023, 12, 247. https://doi.org/10.3390/computers12120247
Alqaradaghi M, Nazir MZI, Kozsik T. Design and Implement an Accurate Automated Static Analysis Checker to Detect Insecure Use of SecurityManager. Computers. 2023; 12(12):247. https://doi.org/10.3390/computers12120247
Chicago/Turabian StyleAlqaradaghi, Midya, Muhammad Zafar Iqbal Nazir, and Tamás Kozsik. 2023. "Design and Implement an Accurate Automated Static Analysis Checker to Detect Insecure Use of SecurityManager" Computers 12, no. 12: 247. https://doi.org/10.3390/computers12120247
APA StyleAlqaradaghi, M., Nazir, M. Z. I., & Kozsik, T. (2023). Design and Implement an Accurate Automated Static Analysis Checker to Detect Insecure Use of SecurityManager. Computers, 12(12), 247. https://doi.org/10.3390/computers12120247






